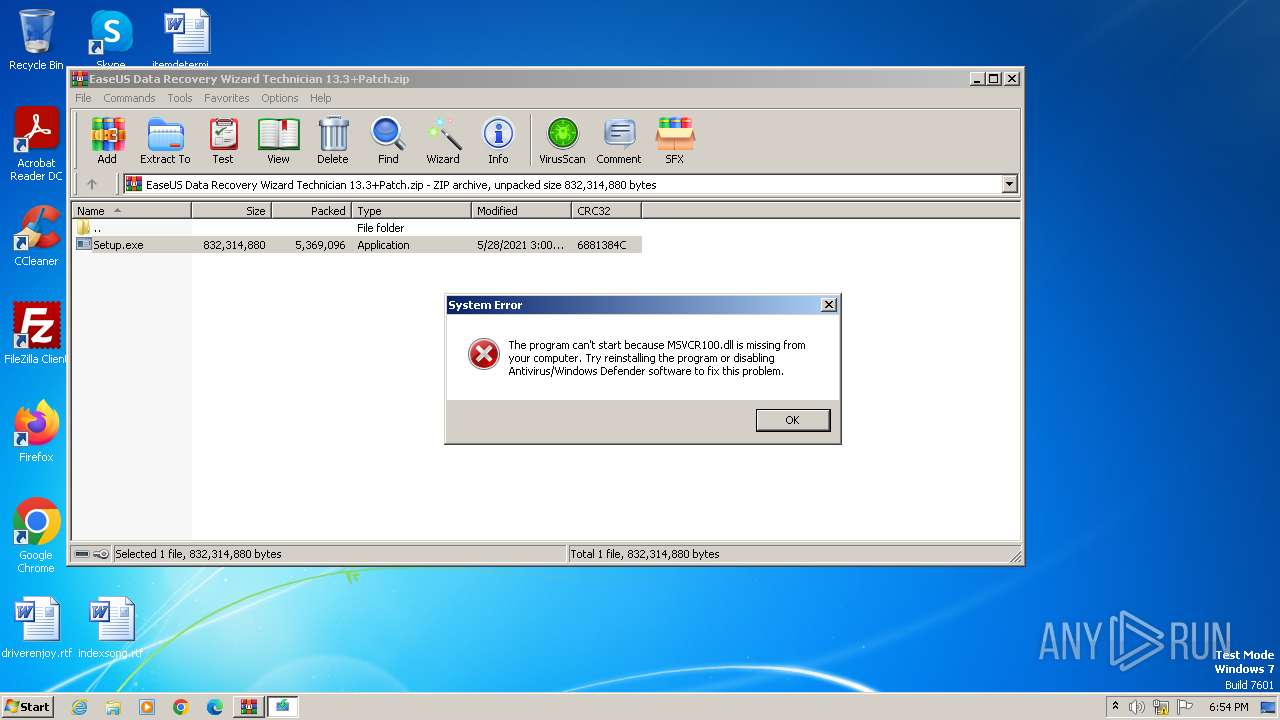
| File name: | EaseUS Data Recovery Wizard Technician 13.3+Patch.zip |
| Full analysis: | https://app.any.run/tasks/e49ad1d1-8e6d-4cd6-9a02-5b6d3548940b |
| Verdict: | Malicious activity |
| Analysis date: | May 24, 2024, 17:53:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | CEF3C6CBE55D593D1513830EB74C69AC |
| SHA1: | 75C7B09A92B936EC920DECBFA55DF4A567FFC9C8 |
| SHA256: | 9B6188115EFB3C65FA996B0ED552C0D56C2F03E2B2CC10088D79221AE60EA59B |
| SSDEEP: | 98304:7D2kMQppKa3bVvglS5+n3kGWYh0y04DoOR0kl4lR1q0FTlAG:7Fhe8bNgow5FhEORyDkElF |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3984)
- Setup.exe (PID: 748)
Application launched itself
- Setup.exe (PID: 1116)
- Setup.exe (PID: 2284)
Reads the Internet Settings
- Setup.exe (PID: 748)
Potential Corporate Privacy Violation
- Setup.exe (PID: 748)
Checks for external IP
- Setup.exe (PID: 748)
INFO
Checks supported languages
- Setup.exe (PID: 748)
- Setup.exe (PID: 1116)
- wmpnscfg.exe (PID: 1764)
- Setup.exe (PID: 2284)
- Setup.exe (PID: 2268)
Reads the computer name
- Setup.exe (PID: 748)
- wmpnscfg.exe (PID: 1764)
Checks proxy server information
- Setup.exe (PID: 748)
Reads the machine GUID from the registry
- Setup.exe (PID: 748)
Creates files or folders in the user directory
- Setup.exe (PID: 748)
Creates files in the program directory
- Setup.exe (PID: 748)
Manual execution by a user
- wmpnscfg.exe (PID: 1764)
- Setup.exe (PID: 2064)
- Setup.exe (PID: 2284)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2021:05:28 17:00:52 |
| ZipCRC: | 0x6881384c |
| ZipCompressedSize: | 5369096 |
| ZipUncompressedSize: | 832314880 |
| ZipFileName: | Setup.exe |
Total processes
49
Monitored processes
8
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 748 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3984.4095\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3984.4095\Setup.exe | Setup.exe | ||||||||||||
User: admin Company: Ilya Morozov Integrity Level: HIGH Description: Balabolka Version: 2.15.0.783 Modules
| |||||||||||||||
| 1116 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3984.4095\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3984.4095\Setup.exe | WinRAR.exe | ||||||||||||
User: admin Company: Ilya Morozov Integrity Level: HIGH Description: Balabolka Exit code: 0 Version: 2.15.0.783 Modules
| |||||||||||||||
| 1764 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2064 | "C:\Users\admin\Desktop\Setup.exe" | C:\Users\admin\Desktop\Setup.exe | — | explorer.exe | |||||||||||
User: admin Company: Ilya Morozov Integrity Level: MEDIUM Description: Balabolka Exit code: 3221226540 Version: 2.15.0.783 Modules
| |||||||||||||||
| 2268 | "C:\Users\admin\Desktop\Setup.exe" | C:\Users\admin\Desktop\Setup.exe | — | Setup.exe | |||||||||||
User: admin Company: Ilya Morozov Integrity Level: HIGH Description: Balabolka Exit code: 0 Version: 2.15.0.783 Modules
| |||||||||||||||
| 2284 | "C:\Users\admin\Desktop\Setup.exe" | C:\Users\admin\Desktop\Setup.exe | explorer.exe | ||||||||||||
User: admin Company: Ilya Morozov Integrity Level: HIGH Description: Balabolka Exit code: 0 Version: 2.15.0.783 Modules
| |||||||||||||||
| 3984 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\EaseUS Data Recovery Wizard Technician 13.3+Patch.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4032 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3984.4095\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3984.4095\Setup.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Ilya Morozov Integrity Level: MEDIUM Description: Balabolka Exit code: 3221226540 Version: 2.15.0.783 Modules
| |||||||||||||||
Total events
4 353
Read events
4 308
Write events
39
Delete events
6
Modification events
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\EaseUS Data Recovery Wizard Technician 13.3+Patch.zip | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
0
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3984 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3984.4095\Setup.exe | — | |
MD5:— | SHA256:— | |||
| 3984 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3984.10064\Setup.exe | — | |
MD5:— | SHA256:— | |||
| 748 | Setup.exe | C:\ProgramData\krosqm.txt | text | |
MD5:7787094374F3843C9E3050F408CE77AA | SHA256:— | |||
| 748 | Setup.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\7IOA9531.txt | text | |
MD5:7787094374F3843C9E3050F408CE77AA | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
263
DNS requests
1
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
748 | Setup.exe | GET | 200 | 104.26.12.205:80 | http://api.ipify.org/?format=xml | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
748 | Setup.exe | 104.26.12.205:80 | api.ipify.org | CLOUDFLARENET | US | unknown |
748 | Setup.exe | 45.93.201.181:80 | — | IT Resheniya LLC | RU | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.ipify.org |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1088 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
748 | Setup.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup (ipify .org) |
— | — | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] Received IP address from server as result of HTTP request |