| File name: | setup.msi |
| Full analysis: | https://app.any.run/tasks/f8c63056-af94-4e03-b0a3-1c941af8ed10 |
| Verdict: | Malicious activity |
| Analysis date: | May 10, 2025, 06:01:04 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
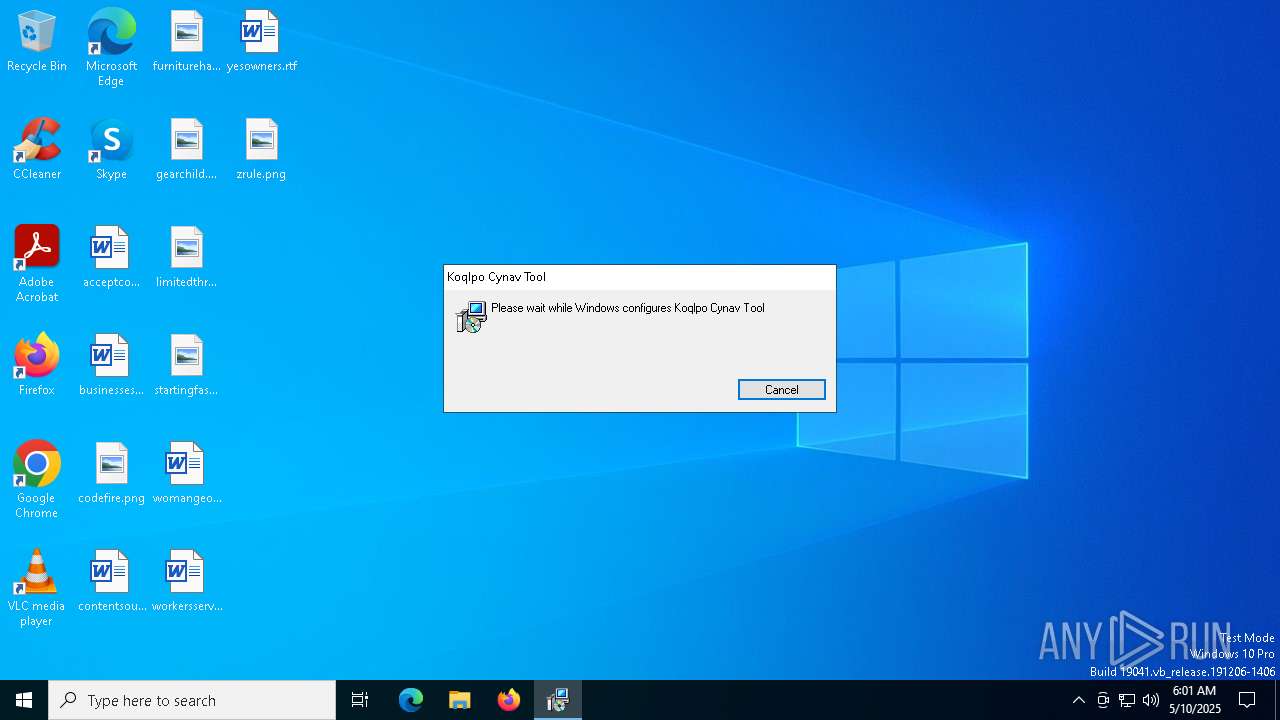
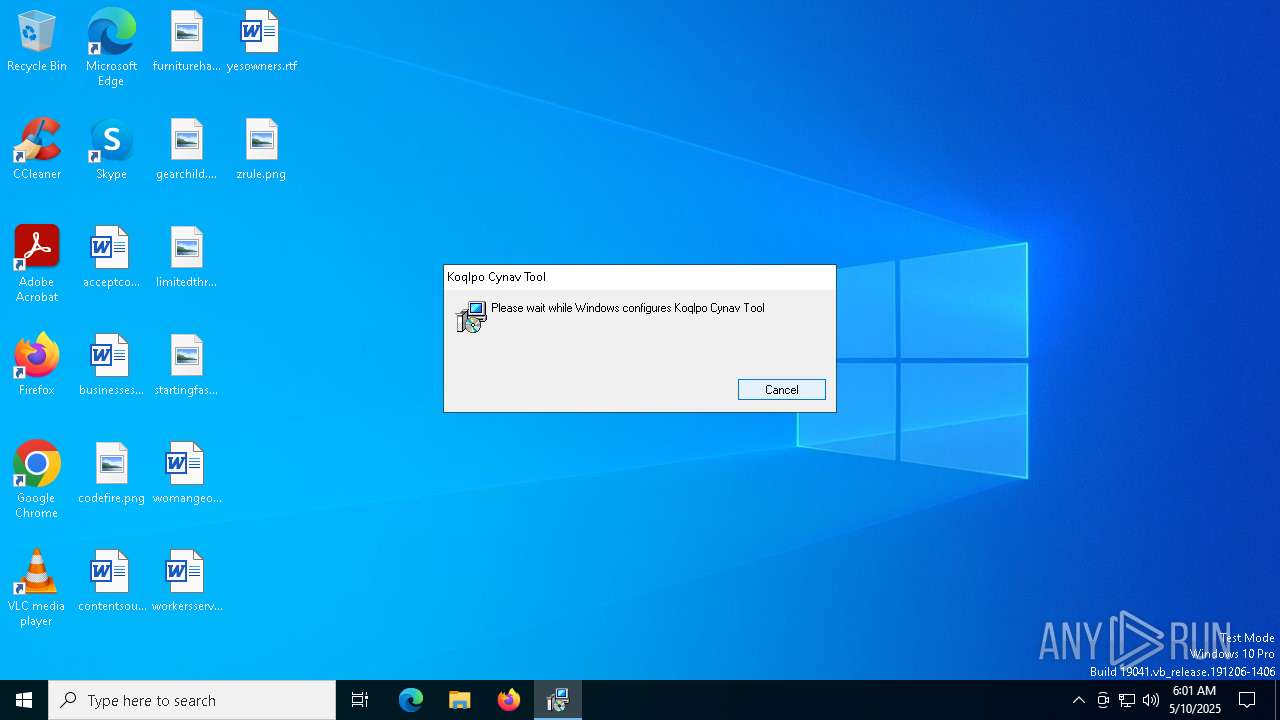
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Security: 0, Code page: 1252, Revision Number: {C4AECC88-FF41-4120-9146-AA02B0EF7CD1}, Number of Words: 10, Subject: Koqlpo Cynav Tool, Author: Niviqol Raisox, Name of Creating Application: Koqlpo Cynav Tool, Template: x64;1033, Comments: This installer database contains the logic and data required to install Koqlpo Cynav Tool., Title: Installation Database, Keywords: Installer, MSI, Database, Create Time/Date: Thu May 8 20:06:16 2025, Last Saved Time/Date: Thu May 8 20:06:16 2025, Last Printed: Thu May 8 20:06:16 2025, Number of Pages: 450 |
| MD5: | 674652BA6A8E5BFF5F9566BB4A68B649 |
| SHA1: | 950ACCB24DE4BBC9B3F29FB462311DCB54E6E6B2 |
| SHA256: | 9B59AA79432EE430A8D11A809F5E1DE7234BBCCFD0AAD23F53C86ADD18184B41 |
| SSDEEP: | 393216:yJ6AhndyL/8/aDzj9U82/PVoATjN2h0objZMdmYxIg2hzd:udij9RcVoATjN2h0objZB2IfR |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the Windows owner or organization settings
- msiexec.exe (PID: 7836)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 7888)
Process drops python dynamic module
- msiexec.exe (PID: 7836)
Process drops legitimate windows executable
- msiexec.exe (PID: 7836)
The process drops C-runtime libraries
- msiexec.exe (PID: 7836)
Drops 7-zip archiver for unpacking
- msiexec.exe (PID: 7836)
There is functionality for taking screenshot (YARA)
- taskcoach.exe (PID: 2384)
INFO
Checks supported languages
- msiexec.exe (PID: 7836)
- msiexec.exe (PID: 7888)
- taskcoach.exe (PID: 2384)
An automatically generated document
- msiexec.exe (PID: 7744)
Executable content was dropped or overwritten
- msiexec.exe (PID: 7836)
Reads Environment values
- msiexec.exe (PID: 7888)
The sample compiled with english language support
- msiexec.exe (PID: 7836)
Reads the computer name
- msiexec.exe (PID: 7836)
- msiexec.exe (PID: 7888)
- taskcoach.exe (PID: 2384)
Checks proxy server information
- msiexec.exe (PID: 7888)
- taskcoach.exe (PID: 2384)
- slui.exe (PID: 5204)
Creates files or folders in the user directory
- msiexec.exe (PID: 7888)
- taskcoach.exe (PID: 2384)
- msiexec.exe (PID: 7836)
Reads the software policy settings
- msiexec.exe (PID: 7888)
- slui.exe (PID: 5204)
Create files in a temporary directory
- taskcoach.exe (PID: 2384)
Reads the machine GUID from the registry
- msiexec.exe (PID: 7888)
- taskcoach.exe (PID: 2384)
Creates a software uninstall entry
- msiexec.exe (PID: 7836)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (88.6) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (10) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| Security: | None |
|---|---|
| CodePage: | Windows Latin 1 (Western European) |
| RevisionNumber: | {C4AECC88-FF41-4120-9146-AA02B0EF7CD1} |
| Words: | 10 |
| Subject: | Koqlpo Cynav Tool |
| Author: | Niviqol Raisox |
| LastModifiedBy: | - |
| Software: | Koqlpo Cynav Tool |
| Template: | x64;1033 |
| Comments: | This installer database contains the logic and data required to install Koqlpo Cynav Tool. |
| Title: | Installation Database |
| Keywords: | Installer, MSI, Database |
| CreateDate: | 2025:05:08 20:06:16 |
| ModifyDate: | 2025:05:08 20:06:16 |
| LastPrinted: | 2025:05:08 20:06:16 |
| Pages: | 450 |
Total processes
134
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2320 | "C:\Users\admin\AppData\Roaming\Koqlpo Cynav Tool\tpm2emu.exe" 0 | C:\Users\admin\AppData\Roaming\Koqlpo Cynav Tool\tpm2emu.exe | — | msiexec.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225781 Modules
| |||||||||||||||
| 2384 | "C:\Users\admin\AppData\Roaming\Koqlpo Cynav Tool\taskcoach.exe" | C:\Users\admin\AppData\Roaming\Koqlpo Cynav Tool\taskcoach.exe | msiexec.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Your friendly task manager Version: 1.4.6 Modules
| |||||||||||||||
| 4880 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | tpm2emu.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5204 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7744 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\setup.msi | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7836 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7888 | C:\Windows\syswow64\MsiExec.exe -Embedding 6DB08EB4DC28A069EF48464237128095 | C:\Windows\SysWOW64\msiexec.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 741
Read events
3 415
Write events
317
Delete events
9
Modification events
| (PID) Process: | (7836) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 9C1E0000EFFF5EF870C1DB01 | |||
| (PID) Process: | (7836) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 4AFB17A4CFBF6B1BD17CF677E340DF1FBE4D0392536D990A1CB51B7855EFD8F9 | |||
| (PID) Process: | (7836) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (7888) msiexec.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7888) msiexec.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7888) msiexec.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (7836) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Folders |
| Operation: | write | Name: | C:\Config.Msi\ |
Value: | |||
| (PID) Process: | (7836) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | write | Name: | C:\Config.Msi\10cdd3.rbs |
Value: 31179120 | |||
| (PID) Process: | (7836) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | write | Name: | C:\Config.Msi\10cdd3.rbsLow |
Value: | |||
| (PID) Process: | (7836) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Components\42F0865697CD28440AD3B5A00E8D7F5B |
| Operation: | write | Name: | B0C3D3F08660A474AAF46D317F1A5A5F |
Value: C:\Users\admin\AppData\Roaming\Koqlpo Cynav Tool\w9xpopen.exe | |||
Executable files
117
Suspicious files
297
Text files
71
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7836 | msiexec.exe | C:\Windows\Installer\10cdd1.msi | — | |
MD5:— | SHA256:— | |||
| 7836 | msiexec.exe | C:\Windows\Installer\MSID024.tmp | executable | |
MD5:379F76E2FA6EEF4C2116C2A3AE6896BE | SHA256:C54F8A0CC280A9A0C934B8B23BBD530BA739E79AD686121CC8B659882CEB60FD | |||
| 7888 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:E192462F281446B5D1500D474FBACC4B | SHA256:F1BA9F1B63C447682EBF9DE956D0DA2A027B1B779ABEF9522D347D3479139A60 | |||
| 7836 | msiexec.exe | C:\Windows\Installer\MSID092.tmp | executable | |
MD5:379F76E2FA6EEF4C2116C2A3AE6896BE | SHA256:C54F8A0CC280A9A0C934B8B23BBD530BA739E79AD686121CC8B659882CEB60FD | |||
| 7836 | msiexec.exe | C:\Windows\Installer\MSICF19.tmp | executable | |
MD5:379F76E2FA6EEF4C2116C2A3AE6896BE | SHA256:C54F8A0CC280A9A0C934B8B23BBD530BA739E79AD686121CC8B659882CEB60FD | |||
| 7836 | msiexec.exe | C:\Windows\Installer\MSID0E1.tmp | executable | |
MD5:379F76E2FA6EEF4C2116C2A3AE6896BE | SHA256:C54F8A0CC280A9A0C934B8B23BBD530BA739E79AD686121CC8B659882CEB60FD | |||
| 7888 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:BBBD2D5A765C72BE92B195A8F64057F2 | SHA256:FBD96017D5E6FB7AAD87362FBE462365735F20F1EE7E40A5A9361D7F3EFD9DF1 | |||
| 7836 | msiexec.exe | C:\Windows\Installer\MSID1DC.tmp | executable | |
MD5:379F76E2FA6EEF4C2116C2A3AE6896BE | SHA256:C54F8A0CC280A9A0C934B8B23BBD530BA739E79AD686121CC8B659882CEB60FD | |||
| 7888 | msiexec.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\diagnostics[1].htm | binary | |
MD5:CFCD208495D565EF66E7DFF9F98764DA | SHA256:5FECEB66FFC86F38D952786C6D696C79C2DBC239DD4E91B46729D73A27FB57E9 | |||
| 7888 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\842C55B5A55A5D6DEAFE1ADE04420CD9 | binary | |
MD5:FDEEBE334B8321A494A408CEF878D7D2 | SHA256:62A3FB721AB97ED6C9C14E37A5DD2D28E7CCEE4EB5E1D3E283F8F0B6C3FB1F1C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
27
DNS requests
21
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7888 | msiexec.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7888 | msiexec.exe | GET | 200 | 65.9.66.41:80 | http://r11.c.lencr.org/26.crl | unknown | — | — | whitelisted |
2384 | taskcoach.exe | GET | 301 | 51.158.149.82:80 | http://taskcoach.org/messages.txt | unknown | — | — | unknown |
2384 | taskcoach.exe | GET | 301 | 51.158.149.82:80 | http://taskcoach.org/version.txt | unknown | — | — | unknown |
7356 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7356 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7888 | msiexec.exe | 169.150.247.37:443 | cbsnaturalway.com | — | GB | unknown |
7888 | msiexec.exe | 23.209.209.135:80 | x1.c.lencr.org | PT. Telekomunikasi Selular | ID | whitelisted |
7888 | msiexec.exe | 65.9.66.41:80 | r11.c.lencr.org | AMAZON-02 | US | whitelisted |
6544 | svchost.exe | 20.190.160.132:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
cbsnaturalway.com |
| unknown |
x1.c.lencr.org |
| whitelisted |
r11.c.lencr.org |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2384 | taskcoach.exe | Attempted Information Leak | ET INFO Python-urllib/ Suspicious User Agent |
2384 | taskcoach.exe | Attempted Information Leak | ET INFO Python-urllib/ Suspicious User Agent |