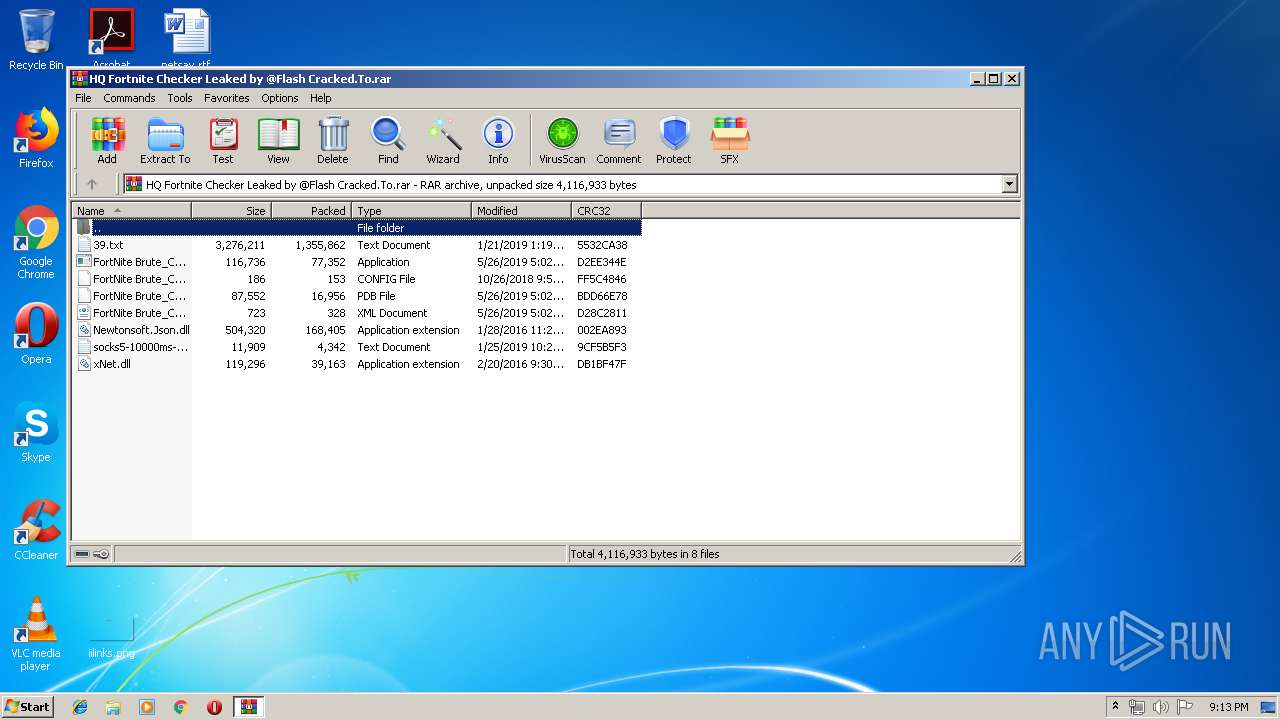
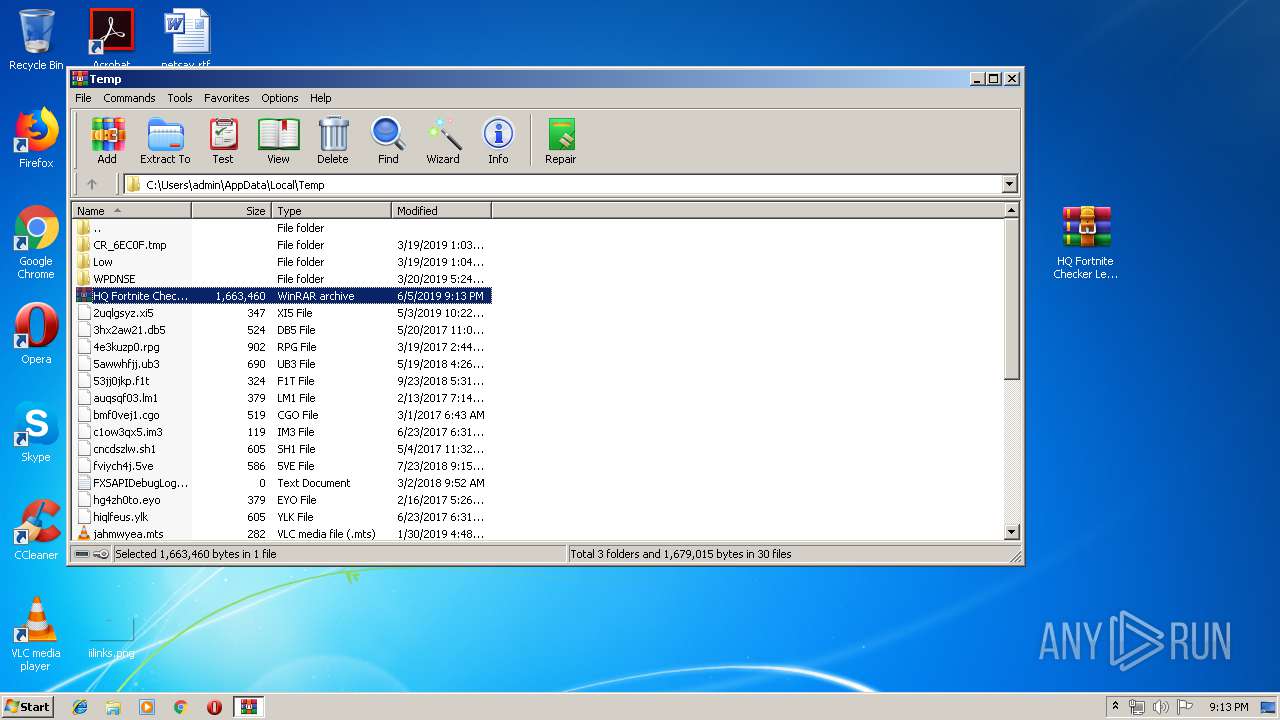
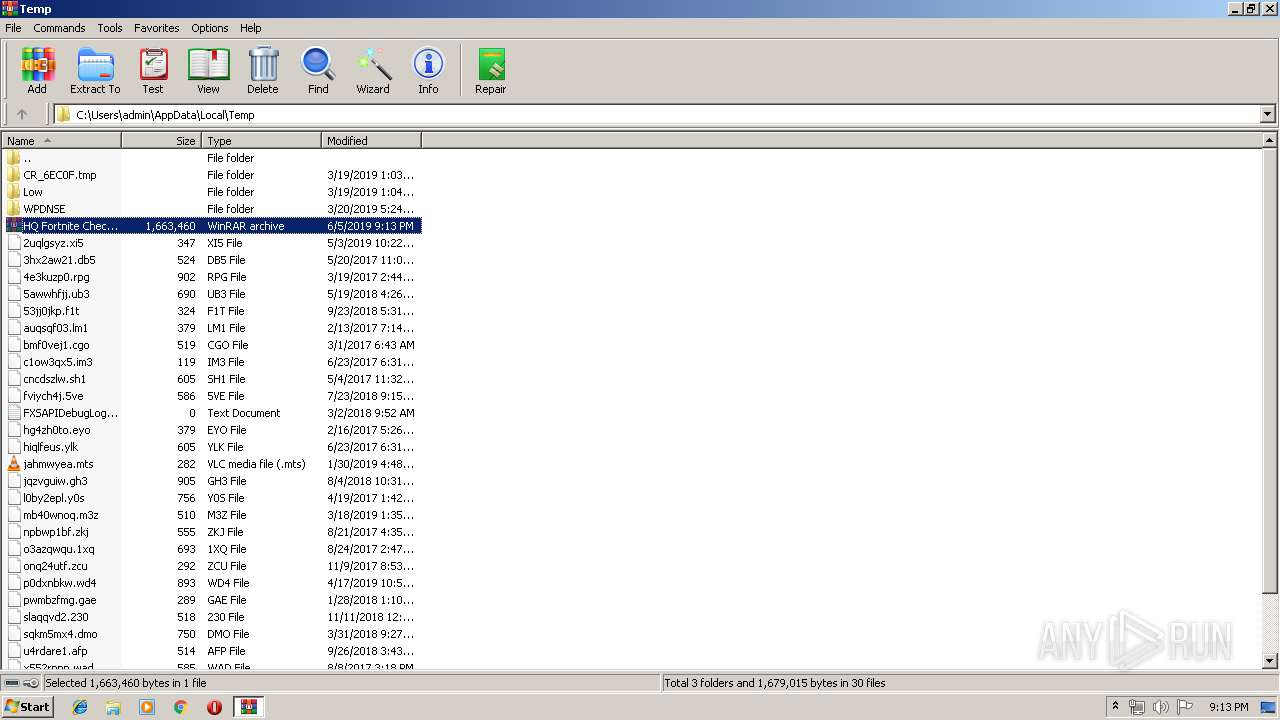
| File name: | HQ Fortnite Checker Leaked by @Flash Cracked.To.rar |
| Full analysis: | https://app.any.run/tasks/2d3e2626-3acb-4084-90b4-2e44c9543f9d |
| Verdict: | Malicious activity |
| Analysis date: | June 05, 2019, 20:13:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 1143972D1ED37060BF22DD610C228267 |
| SHA1: | 71C2FC2C52032807744493F5935634E30477454C |
| SHA256: | 9B563257C2C680331E2B7559CC60643B26C446B9BC260BFD8F9B20AB547EF900 |
| SSDEEP: | 49152:ru1e7Xk96bEbbM8YWlCt/KryLTfo1XztX:rO6XksbEOQCt/YyL8RztX |
MALICIOUS
Loads dropped or rewritten executable
- FortNite Brute_Checker.exe (PID: 3972)
- SearchProtocolHost.exe (PID: 3572)
Application was dropped or rewritten from another process
- FortNite Brute_Checker.exe (PID: 3972)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2100)
Reads Internet Cache Settings
- FortNite Brute_Checker.exe (PID: 3972)
Reads Environment values
- FortNite Brute_Checker.exe (PID: 3972)
INFO
Manual execution by user
- FortNite Brute_Checker.exe (PID: 3972)
- WinRAR.exe (PID: 2100)
Reads settings of System Certificates
- FortNite Brute_Checker.exe (PID: 3972)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
37
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1520 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\HQ Fortnite Checker Leaked by @Flash Cracked.To.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2100 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\HQ Fortnite Checker Leaked by @Flash Cracked.To.rar" "C:\Users\admin\Desktop\HQ Fortnite Checker Leaked by @Flash Cracked.To\" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3572 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe4_ Global\UsGthrCtrlFltPipeMssGthrPipe4 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
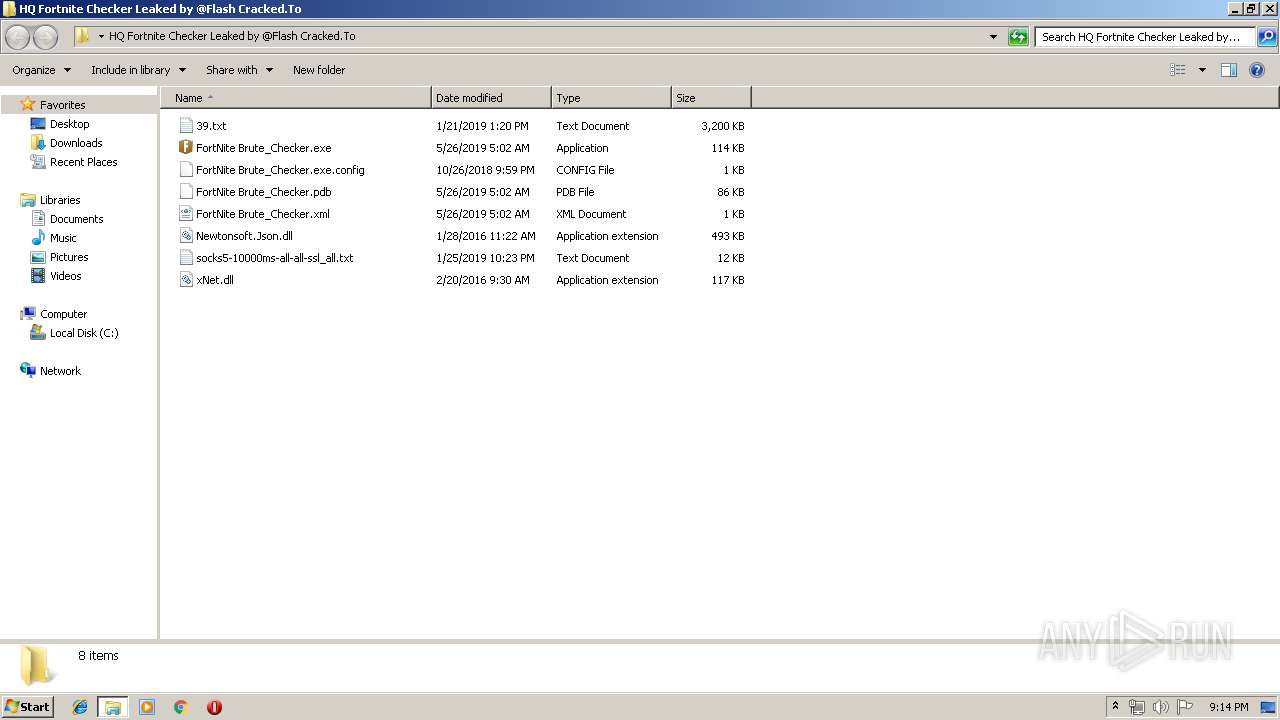
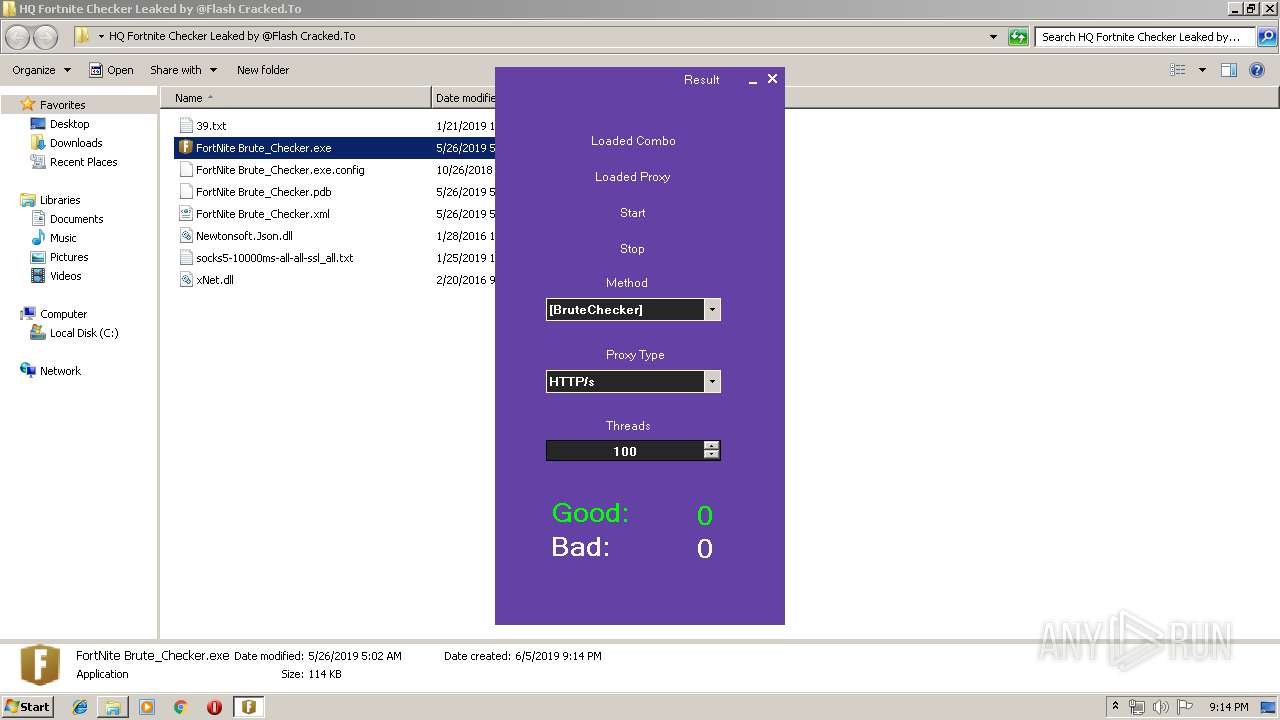
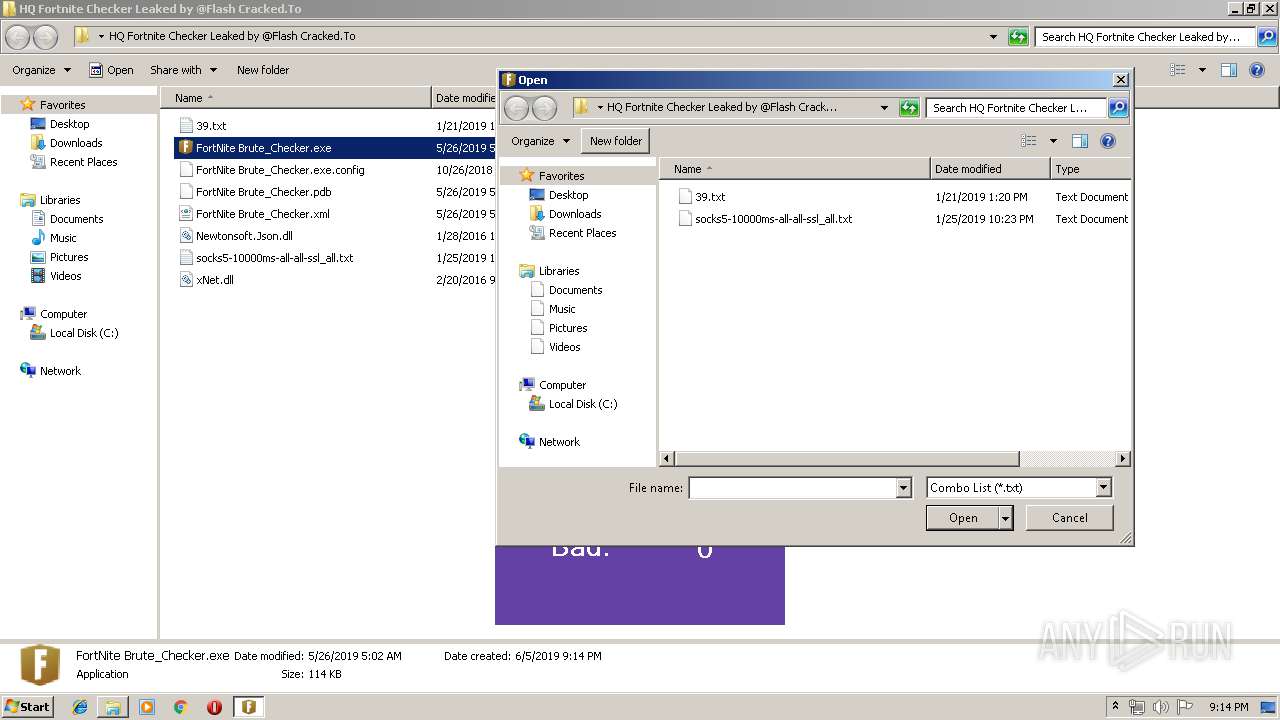
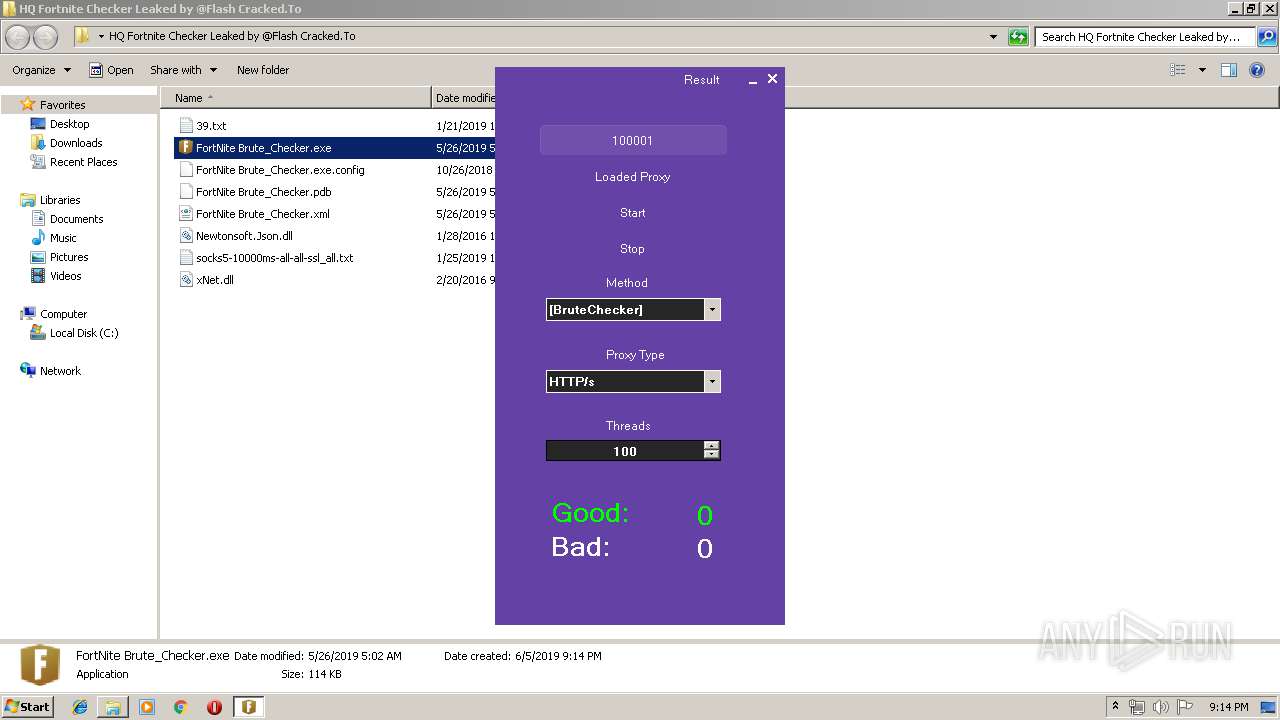
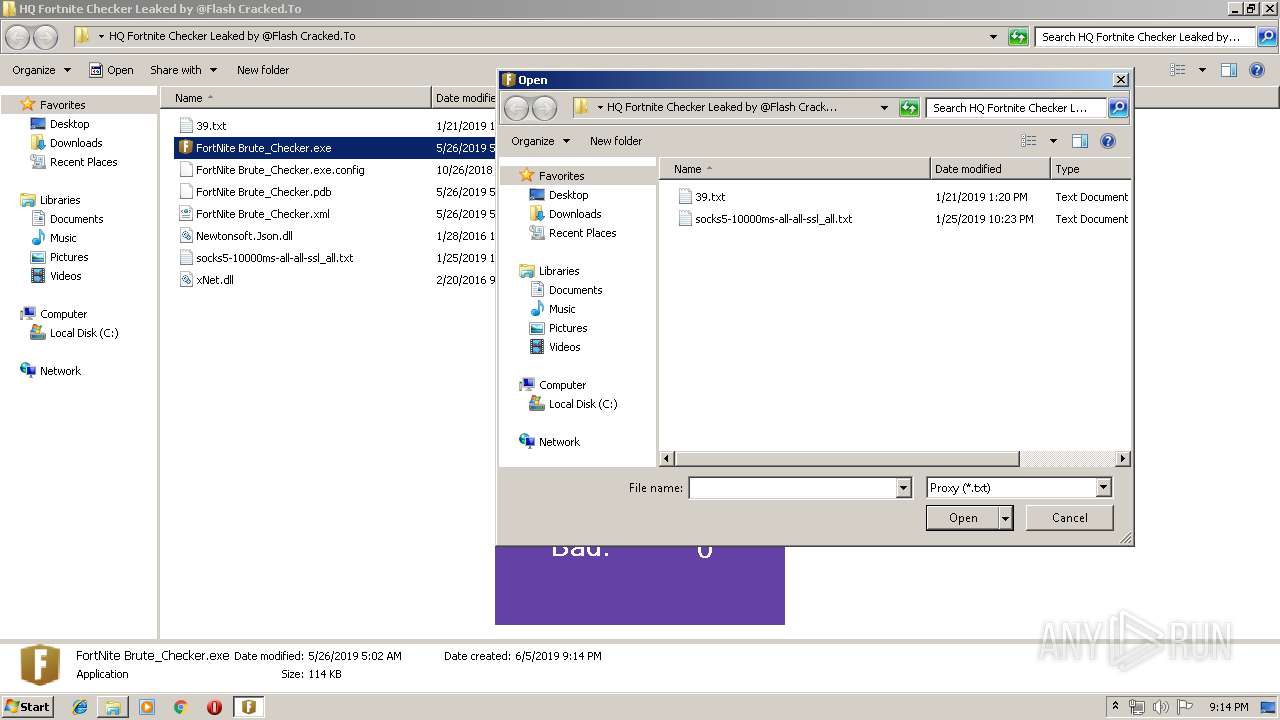
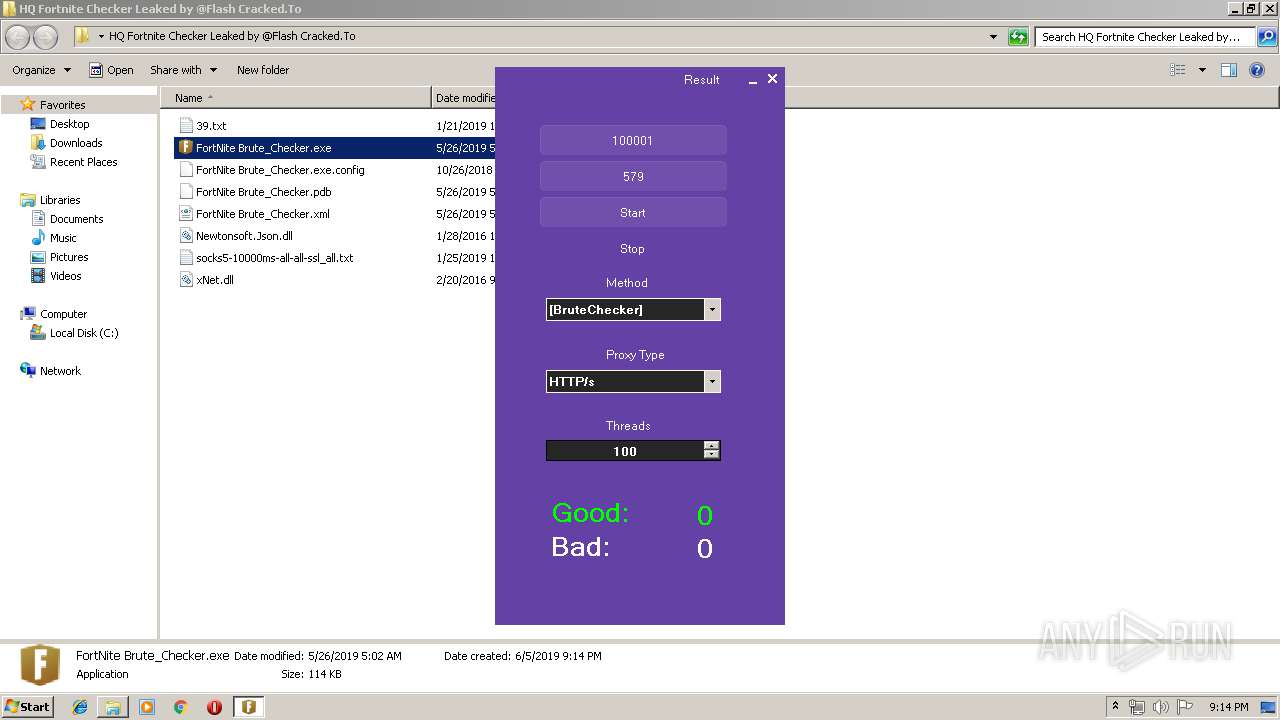
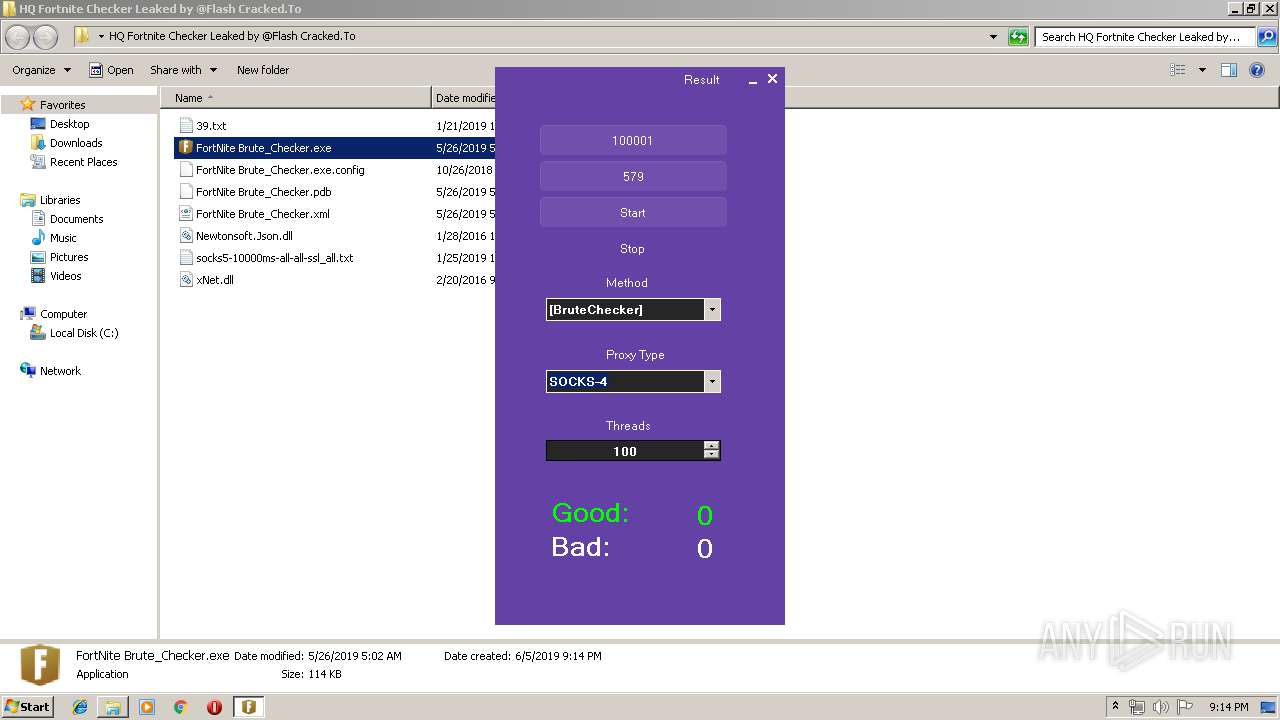
| 3972 | "C:\Users\admin\Desktop\HQ Fortnite Checker Leaked by @Flash Cracked.To\FortNite Brute_Checker.exe" | C:\Users\admin\Desktop\HQ Fortnite Checker Leaked by @Flash Cracked.To\FortNite Brute_Checker.exe | explorer.exe | ||||||||||||
User: admin Company: FortNite Brute_Checker Integrity Level: MEDIUM Description: FortNite Brute_Checker Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
1 471
Read events
1 356
Write events
111
Delete events
4
Modification events
| (PID) Process: | (1520) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1520) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1520) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1520) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\HQ Fortnite Checker Leaked by @Flash Cracked.To.rar | |||
| (PID) Process: | (1520) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1520) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1520) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1520) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1520) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
| (PID) Process: | (1520) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
Executable files
3
Suspicious files
5
Text files
4
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3972 | FortNite Brute_Checker.exe | C:\Users\admin\AppData\Local\Temp\CabA550.tmp | — | |
MD5:— | SHA256:— | |||
| 3972 | FortNite Brute_Checker.exe | C:\Users\admin\AppData\Local\Temp\TarA551.tmp | — | |
MD5:— | SHA256:— | |||
| 3972 | FortNite Brute_Checker.exe | C:\Users\admin\AppData\Local\Temp\CabA581.tmp | — | |
MD5:— | SHA256:— | |||
| 3972 | FortNite Brute_Checker.exe | C:\Users\admin\AppData\Local\Temp\TarA582.tmp | — | |
MD5:— | SHA256:— | |||
| 3972 | FortNite Brute_Checker.exe | C:\Users\admin\AppData\Local\Temp\CabA67D.tmp | — | |
MD5:— | SHA256:— | |||
| 3972 | FortNite Brute_Checker.exe | C:\Users\admin\AppData\Local\Temp\TarA67E.tmp | — | |
MD5:— | SHA256:— | |||
| 2100 | WinRAR.exe | C:\Users\admin\Desktop\HQ Fortnite Checker Leaked by @Flash Cracked.To\socks5-10000ms-all-all-ssl_all.txt | text | |
MD5:— | SHA256:— | |||
| 2100 | WinRAR.exe | C:\Users\admin\Desktop\HQ Fortnite Checker Leaked by @Flash Cracked.To\FortNite Brute_Checker.xml | xml | |
MD5:— | SHA256:— | |||
| 2100 | WinRAR.exe | C:\Users\admin\Desktop\HQ Fortnite Checker Leaked by @Flash Cracked.To\FortNite Brute_Checker.exe | executable | |
MD5:— | SHA256:— | |||
| 2100 | WinRAR.exe | C:\Users\admin\Desktop\HQ Fortnite Checker Leaked by @Flash Cracked.To\FortNite Brute_Checker.pdb | pdb | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
252
DNS requests
7
Threats
162
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3972 | FortNite Brute_Checker.exe | GET | 200 | 205.185.216.42:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 56.2 Kb | whitelisted |
3972 | FortNite Brute_Checker.exe | GET | 200 | 52.222.146.167:80 | http://x.ss2.us/x.cer | US | der | 1.27 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3972 | FortNite Brute_Checker.exe | 46.105.57.150:26026 | — | OVH SAS | FR | suspicious |
3972 | FortNite Brute_Checker.exe | 70.168.93.218:17026 | — | Cox Communications Inc. | US | suspicious |
3972 | FortNite Brute_Checker.exe | 138.128.118.100:59776 | — | ColoCrossing | CA | unknown |
3972 | FortNite Brute_Checker.exe | 157.119.207.36:6667 | — | — | IN | suspicious |
3972 | FortNite Brute_Checker.exe | 192.169.136.149:8545 | — | GoDaddy.com, LLC | US | unknown |
— | — | 178.128.90.237:8080 | — | Forthnet | GR | suspicious |
3972 | FortNite Brute_Checker.exe | 41.191.204.80:9999 | — | VODACOM-LESOTHO | LS | suspicious |
3972 | FortNite Brute_Checker.exe | 132.148.130.46:4329 | — | GoDaddy.com, LLC | US | suspicious |
3972 | FortNite Brute_Checker.exe | 122.116.161.100:30127 | — | Data Communication Business Group | TW | unknown |
3972 | FortNite Brute_Checker.exe | 192.169.232.12:19030 | — | GoDaddy.com, LLC | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
account-public-service-prod03.ol.epicgames.com |
| suspicious |
x.ss2.us |
| whitelisted |
www.download.windowsupdate.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3972 | FortNite Brute_Checker.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] Socks4 Connection |
3972 | FortNite Brute_Checker.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] Socks4 Connection |
3972 | FortNite Brute_Checker.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] Socks4 Connection |
3972 | FortNite Brute_Checker.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] Socks4 Connection |
3972 | FortNite Brute_Checker.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] Socks4 Connection |
3972 | FortNite Brute_Checker.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] Socks4 Connection |
3972 | FortNite Brute_Checker.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] Socks4 Connection |
3972 | FortNite Brute_Checker.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] Socks4 Connection |
3972 | FortNite Brute_Checker.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] Socks4 Connection |
3972 | FortNite Brute_Checker.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] Socks4 Connection |