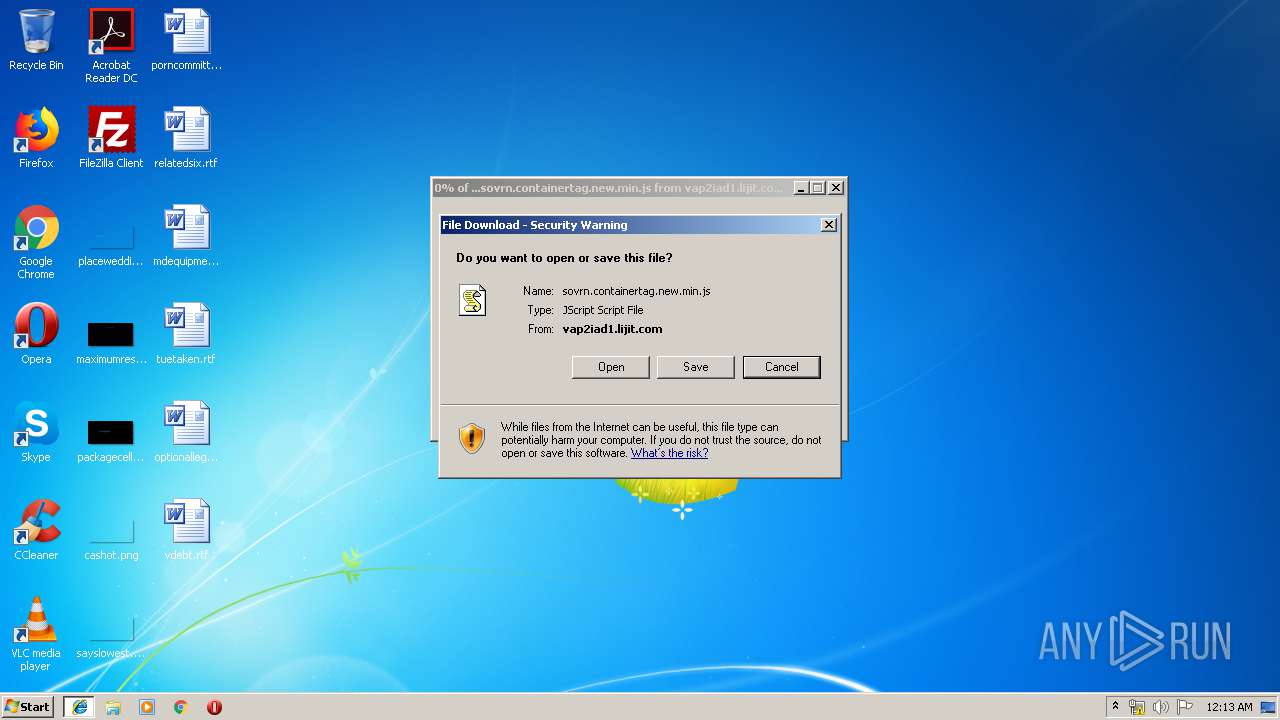
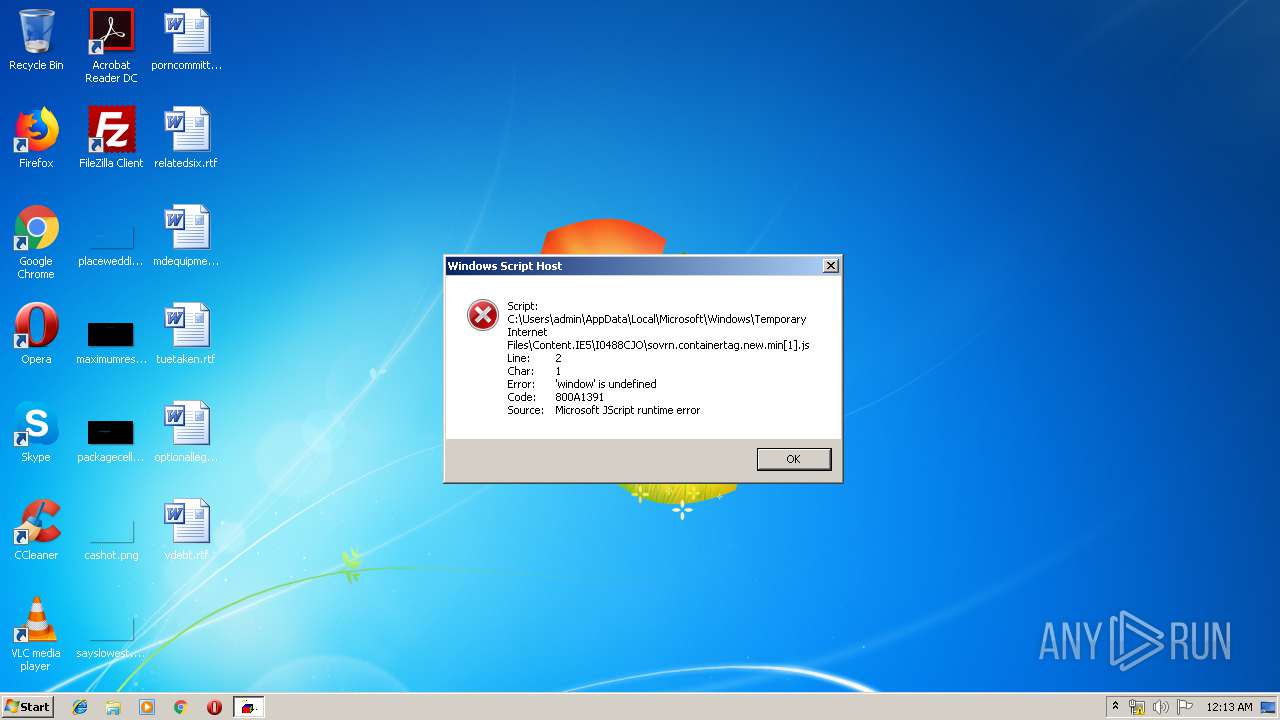
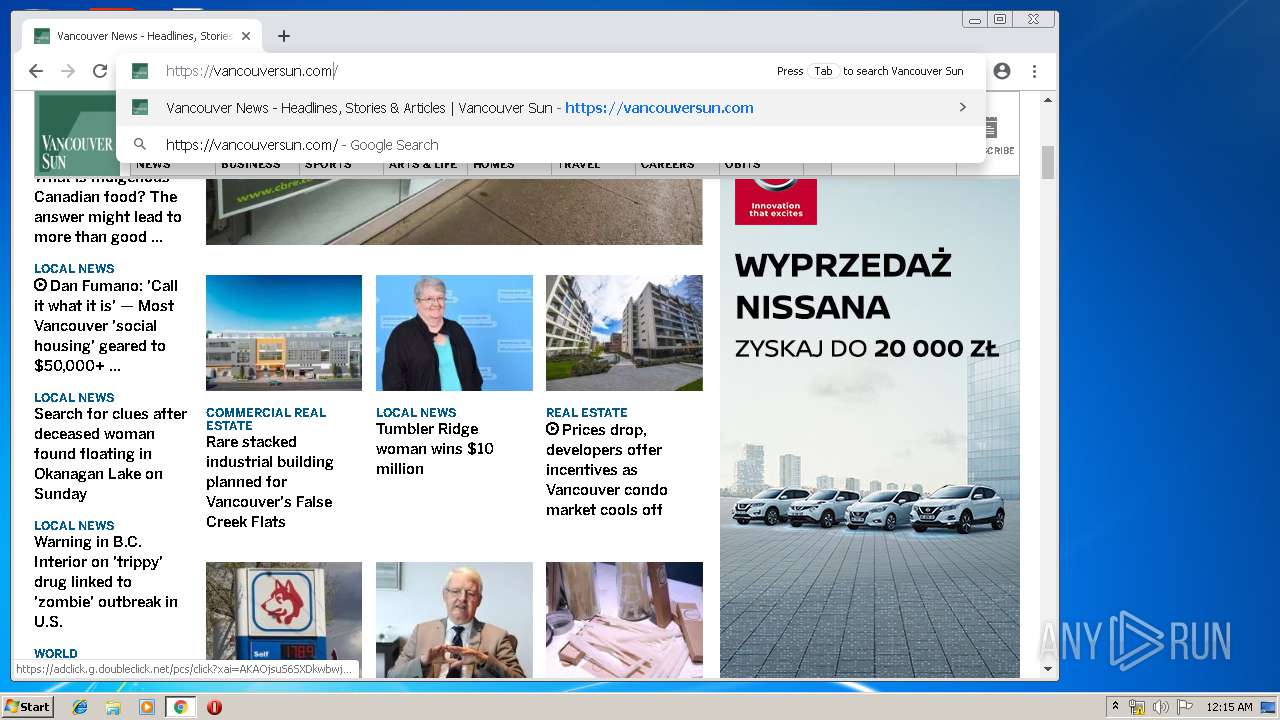
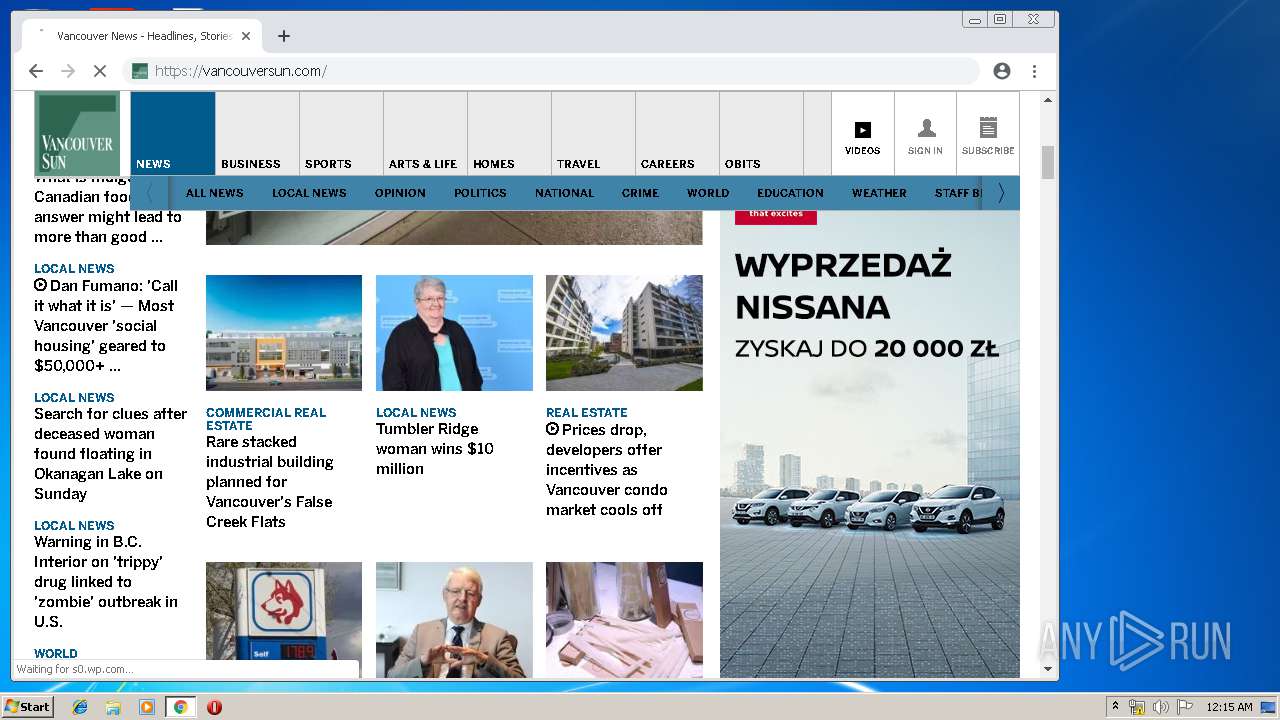
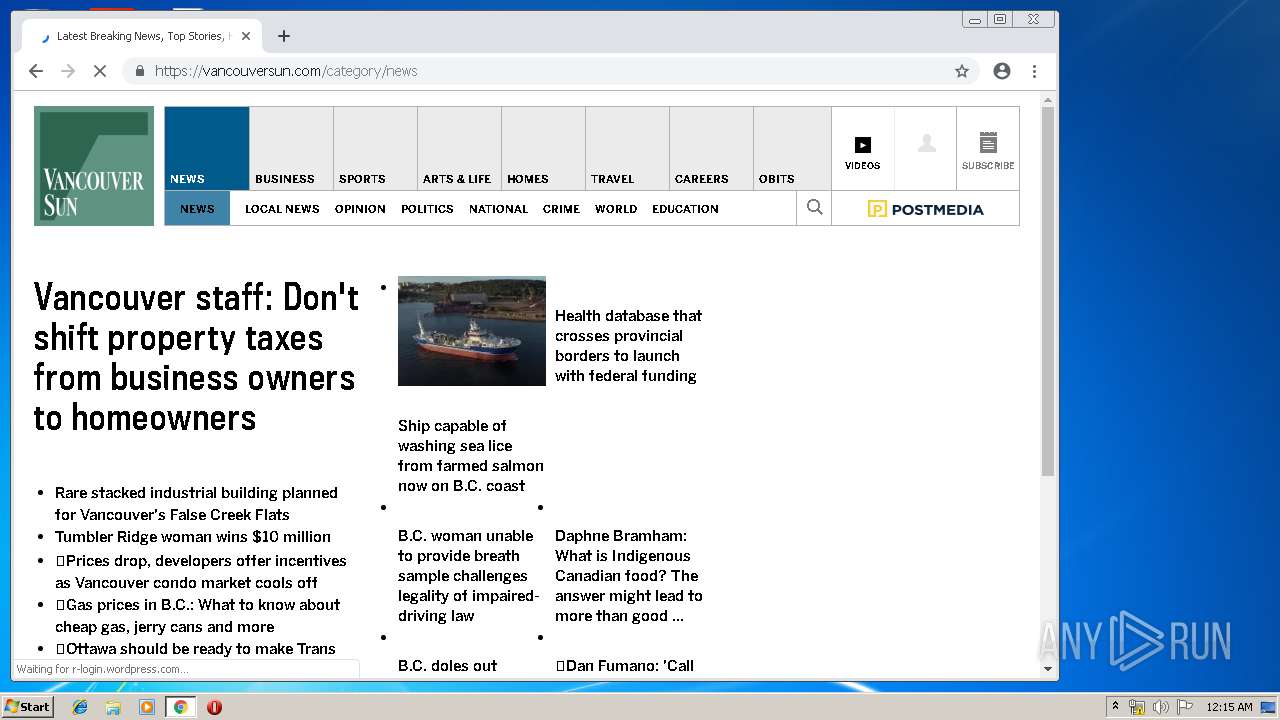
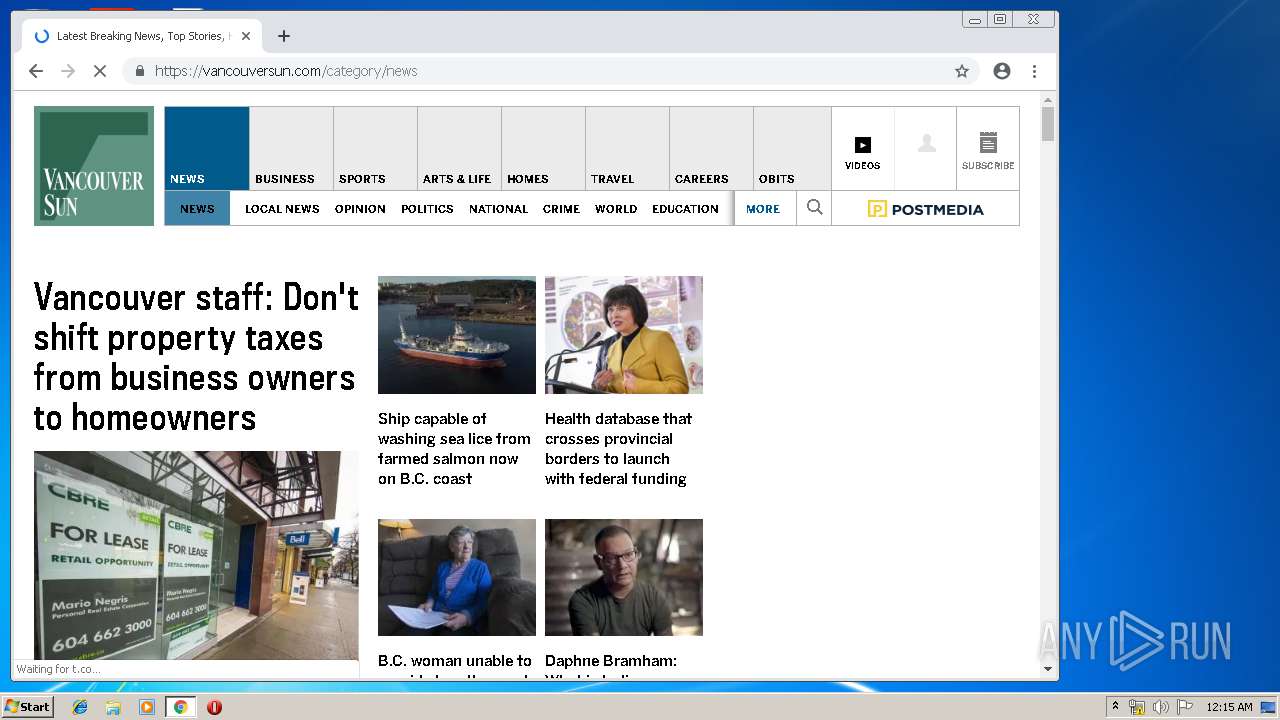
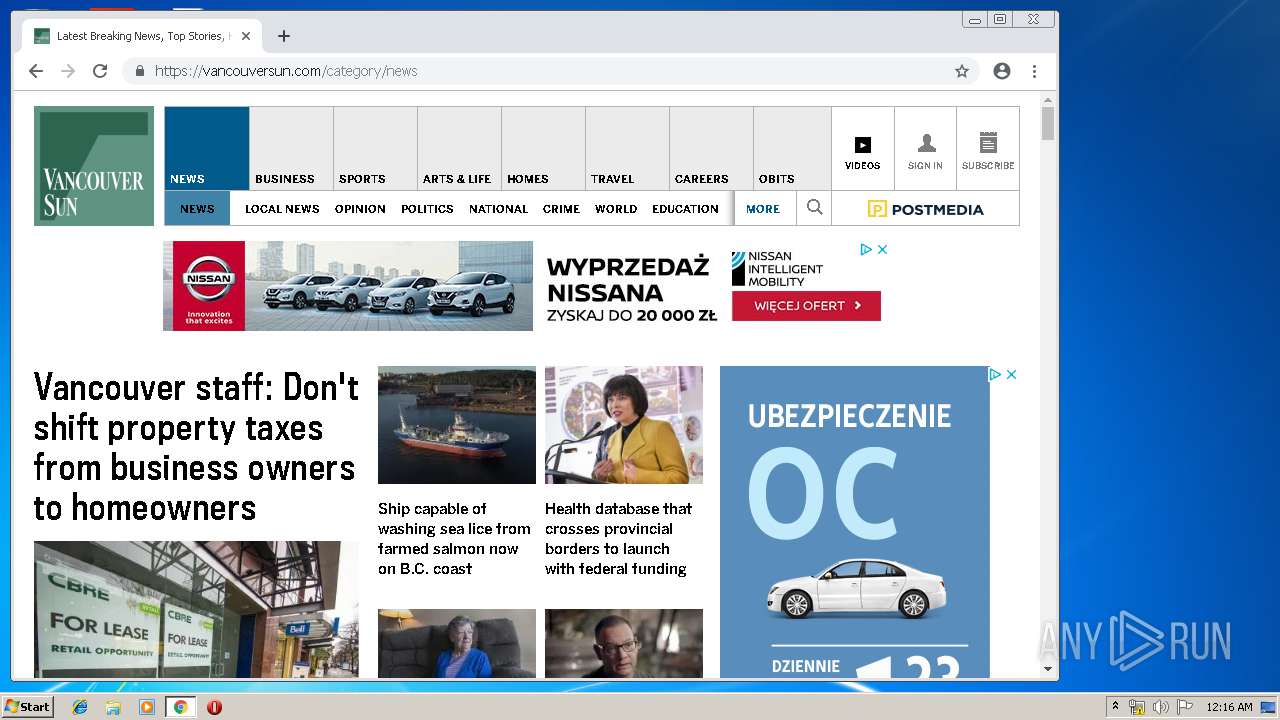
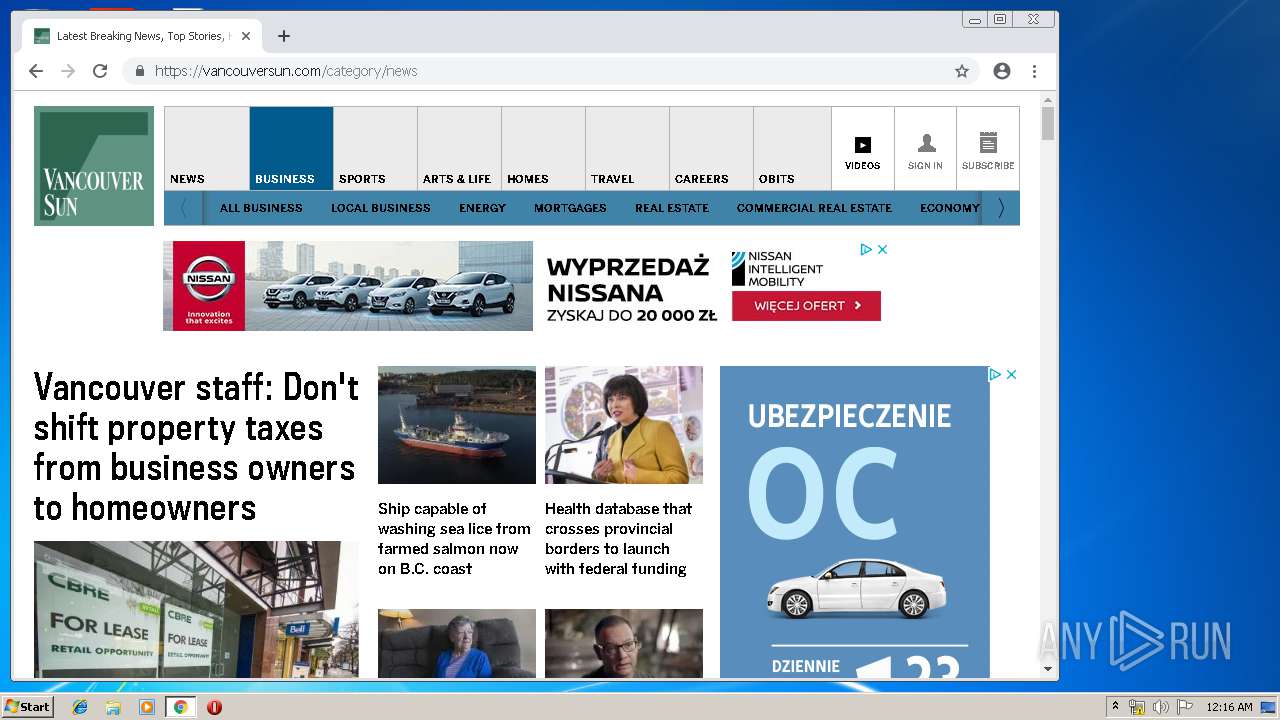
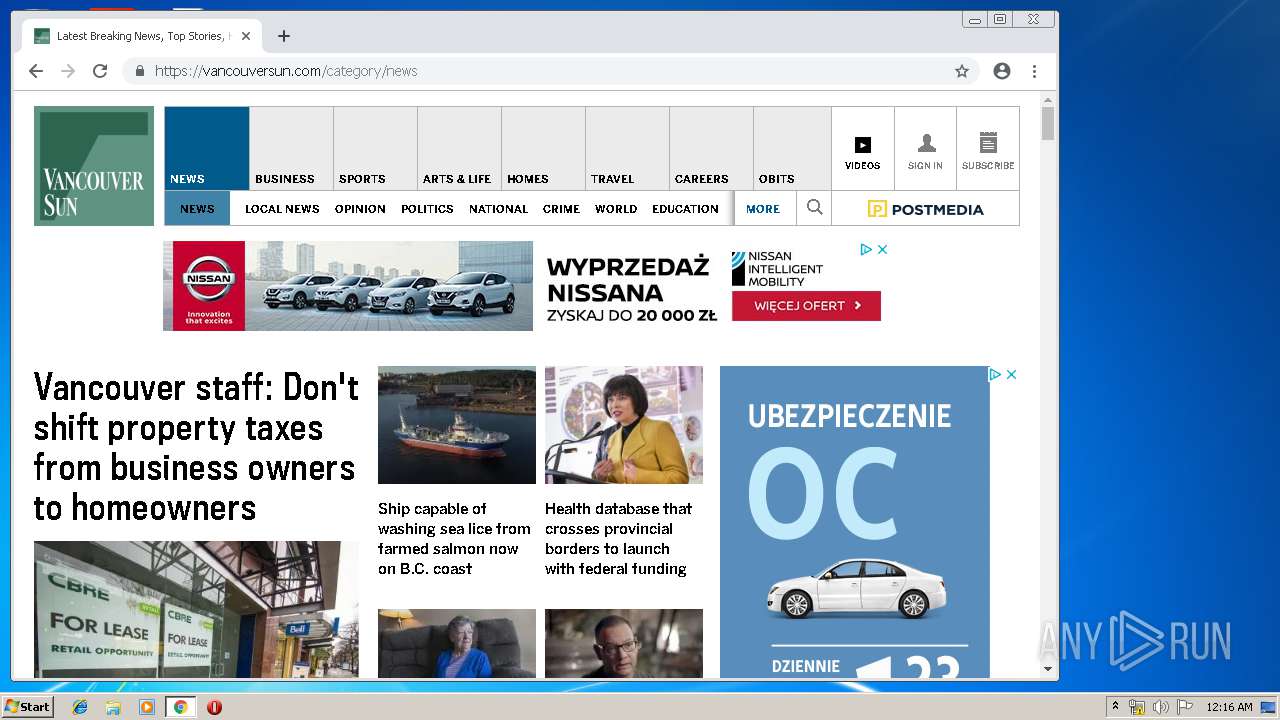
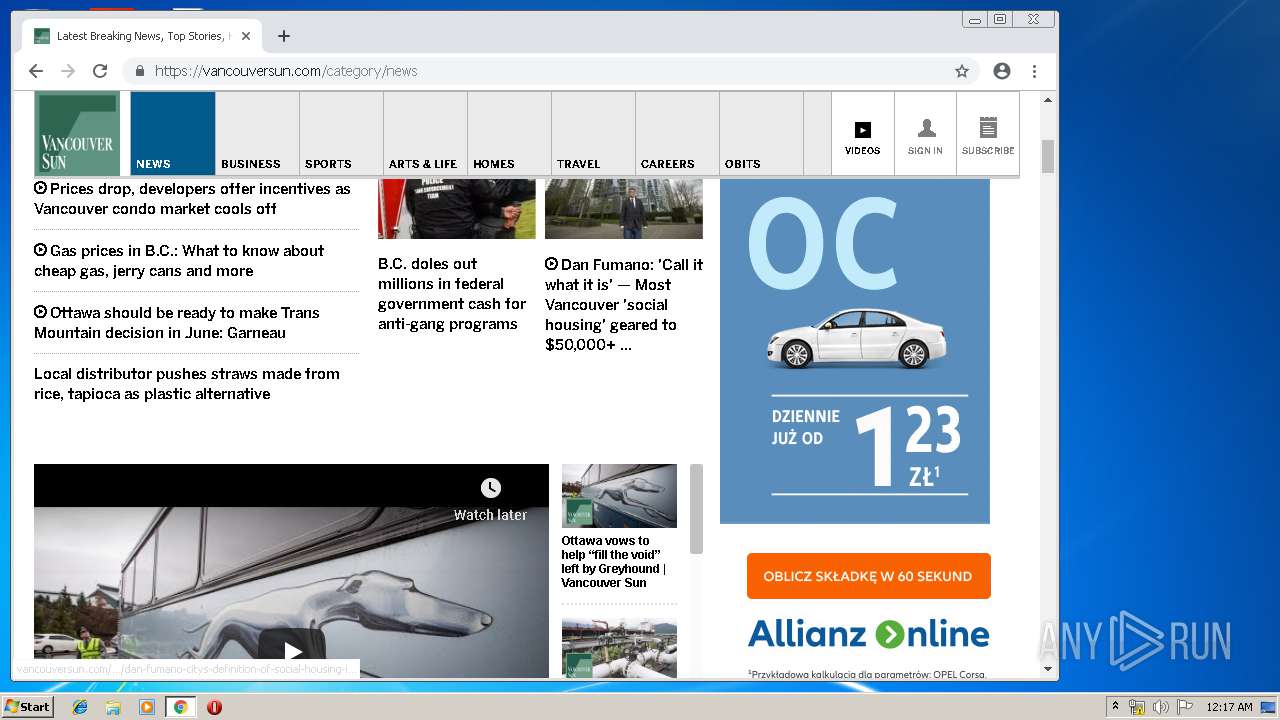
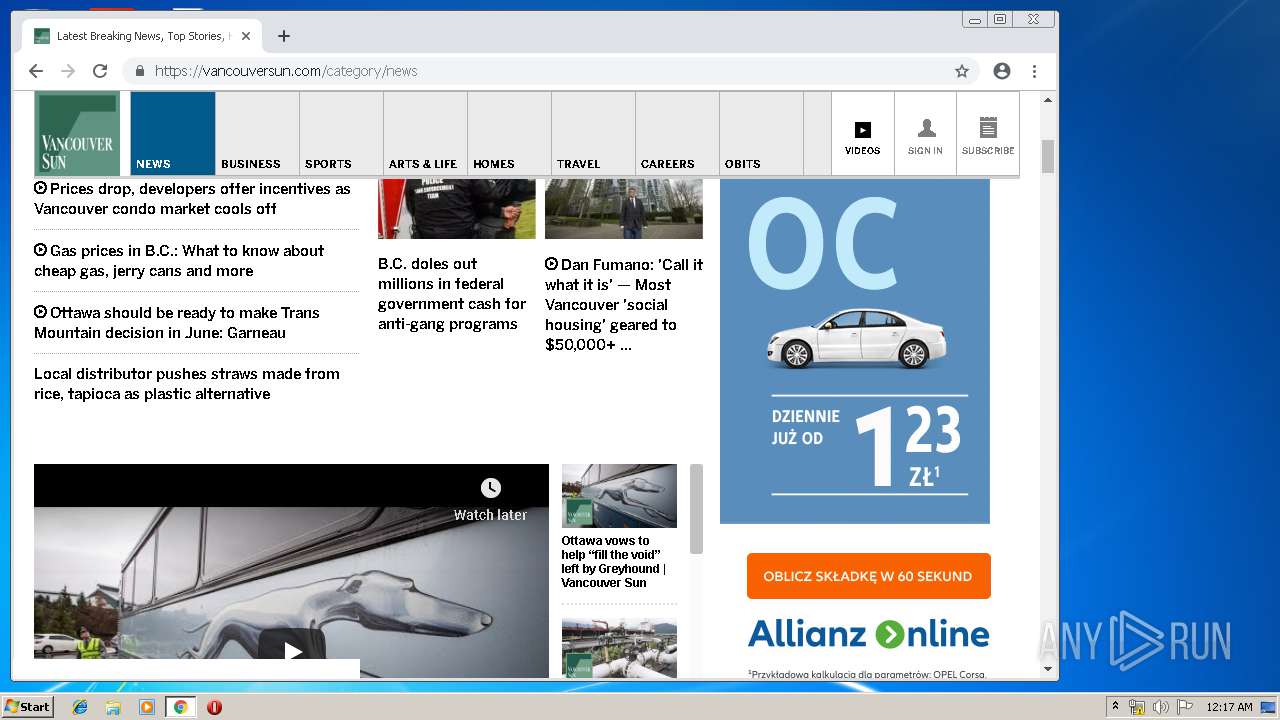
| URL: | https://vap2iad1.lijit.com/res/sovrn.containertag.new.min.js?cid=3&zid=523631&v=4&tid=a_523631_d6a6d553c1b24d908495fa5864637e4d&loc=http://vancouversun.com/news/local-news/warning-in-b-c-interior-on-trippy-drug-linked-to-zombie-outbreak-in-u-s |
| Full analysis: | https://app.any.run/tasks/f988f855-bdbd-452a-8a84-75e0ecf29f6a |
| Verdict: | Malicious activity |
| Analysis date: | April 23, 2019, 23:12:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | B90CE7C1B84C3797033F524E640CB640 |
| SHA1: | B7B4EB28A7EE82B68B2F5DCE59EF20F1D653A319 |
| SHA256: | 9B2C53BD532F8834F7C41D3485FA2DCE29B7D88F083CED1B26D8E899365AB20D |
| SSDEEP: | 3:N8i1oJMoyKIPQXh/7IQuaGAYWQf/a+6J/9TOUEjOJ8QXryc3W5YAlKbMU+xaX0T9:2RMBTPm7CDy+YTOU78SE5Y+UEoVVaaC9 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executes scripts
- iexplore.exe (PID: 2524)
Modifies files in Chrome extension folder
- chrome.exe (PID: 3156)
INFO
Changes internet zones settings
- iexplore.exe (PID: 2524)
Application launched itself
- iexplore.exe (PID: 2524)
- chrome.exe (PID: 3156)
Reads settings of System Certificates
- iexplore.exe (PID: 596)
- chrome.exe (PID: 3156)
Creates files in the user directory
- iexplore.exe (PID: 596)
Reads Internet Cache Settings
- iexplore.exe (PID: 596)
Changes settings of System certificates
- chrome.exe (PID: 3156)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
103
Monitored processes
72
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 288 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=964,10457373429408411250,4873783124551450101,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=17216886468833788639 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=17216886468833788639 --renderer-client-id=46 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=6808 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 456 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=964,10457373429408411250,4873783124551450101,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=11172068875285181377 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=11172068875285181377 --renderer-client-id=58 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=8172 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 596 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2524 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 676 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=964,10457373429408411250,4873783124551450101,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=1097690335296800220 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=1097690335296800220 --renderer-client-id=23 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3680 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 692 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=964,10457373429408411250,4873783124551450101,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=17552764696536622573 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=17552764696536622573 --renderer-client-id=19 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4920 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 904 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=964,10457373429408411250,4873783124551450101,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=16925417311882715031 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=16925417311882715031 --renderer-client-id=55 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=5668 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 912 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=964,10457373429408411250,4873783124551450101,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=1323328811908686070 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=1323328811908686070 --renderer-client-id=63 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=8308 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1008 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=964,10457373429408411250,4873783124551450101,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=8175321598190414339 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=8175321598190414339 --renderer-client-id=59 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2276 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1016 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=964,10457373429408411250,4873783124551450101,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=5036027087293058456 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=5036027087293058456 --renderer-client-id=45 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=5984 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1240 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=964,10457373429408411250,4873783124551450101,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=18120984213733936616 --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=18120984213733936616 --renderer-client-id=15 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2596 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
Total events
1 307
Read events
1 124
Write events
177
Delete events
6
Modification events
| (PID) Process: | (2524) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2524) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2524) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2524) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2524) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2524) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000071000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2524) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {5E532DAB-661D-11E9-A09E-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (2524) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (2524) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 1 | |||
| (PID) Process: | (2524) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E30704000200170017000D000F001300 | |||
Executable files
0
Suspicious files
519
Text files
285
Unknown types
21
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2524 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2524 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2524 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF08B44FEAB09FE7F3.TMP | — | |
MD5:— | SHA256:— | |||
| 2524 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFE8E4DB4480287EED.TMP | — | |
MD5:— | SHA256:— | |||
| 2524 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\RecoveryStore.{5E532DAB-661D-11E9-A09E-5254004A04AF}.dat | — | |
MD5:— | SHA256:— | |||
| 596 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3156 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\index | — | |
MD5:— | SHA256:— | |||
| 3156 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_0 | — | |
MD5:— | SHA256:— | |||
| 3156 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
| 3156 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_2 | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
346
DNS requests
226
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3156 | chrome.exe | GET | 200 | 194.9.25.78:80 | http://r3---sn-5uh5o-f5fs.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjJlQUFXRC12Ny1ldUFnMXF3SDlXZDlFZw/7319.128.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mip=212.7.219.109&mm=28&mn=sn-5uh5o-f5fs&ms=nvh&mt=1556060681&mv=u&pl=24&shardbypass=yes | PL | crx | 842 Kb | whitelisted |
3156 | chrome.exe | GET | 302 | 216.58.206.14:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjJlQUFXRC12Ny1ldUFnMXF3SDlXZDlFZw/7319.128.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 508 b | whitelisted |
3156 | chrome.exe | GET | 301 | 192.0.78.12:80 | http://vancouversun.com/ | US | html | 178 b | whitelisted |
3156 | chrome.exe | GET | 200 | 205.185.216.42:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 55.6 Kb | whitelisted |
3156 | chrome.exe | GET | 200 | 143.204.208.228:80 | http://x.ss2.us/x.cer | US | der | 1.27 Kb | whitelisted |
3156 | chrome.exe | GET | 200 | 91.199.212.52:80 | http://crt.comodoca.com/COMODORSAAddTrustCA.crt | GB | der | 1.37 Kb | whitelisted |
3156 | chrome.exe | GET | 200 | 188.121.36.239:80 | http://ocsp.godaddy.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQdI2%2BOBkuXH93foRUj4a7lAr4rGwQUOpqFBxBnKLbv9r0FQW4gwZTaD94CAQc%3D | NL | der | 1.69 Kb | whitelisted |
3156 | chrome.exe | GET | 200 | 205.185.216.42:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/47BEABC922EAE80E78783462A79F45C254FDE68B.crt | US | der | 969 b | whitelisted |
3156 | chrome.exe | GET | 200 | 23.111.11.204:80 | http://repository.certum.pl/ctnca.cer | US | der | 959 b | whitelisted |
3156 | chrome.exe | GET | 200 | 143.204.208.42:80 | http://x.ss2.us/x.cer | US | der | 1.27 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2524 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
596 | iexplore.exe | 169.55.70.244:443 | vap2iad1.lijit.com | SoftLayer Technologies Inc. | US | unknown |
3156 | chrome.exe | 172.217.23.173:443 | accounts.google.com | Google Inc. | US | whitelisted |
3156 | chrome.exe | 216.58.207.67:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3156 | chrome.exe | 172.217.16.163:443 | www.google.com.ua | Google Inc. | US | whitelisted |
3156 | chrome.exe | 216.58.208.46:443 | clients1.google.com | Google Inc. | US | whitelisted |
3156 | chrome.exe | 216.58.205.238:443 | clients2.google.com | Google Inc. | US | whitelisted |
3156 | chrome.exe | 172.217.18.163:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3156 | chrome.exe | 216.58.206.3:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
3156 | chrome.exe | 194.9.25.78:80 | r3---sn-5uh5o-f5fs.gvt1.com | ATM S.A. | PL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
vap2iad1.lijit.com |
| unknown |
clientservices.googleapis.com |
| whitelisted |
www.google.com.ua |
| whitelisted |
accounts.google.com |
| shared |
clients1.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
clients2.google.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
redirector.gvt1.com |
| whitelisted |