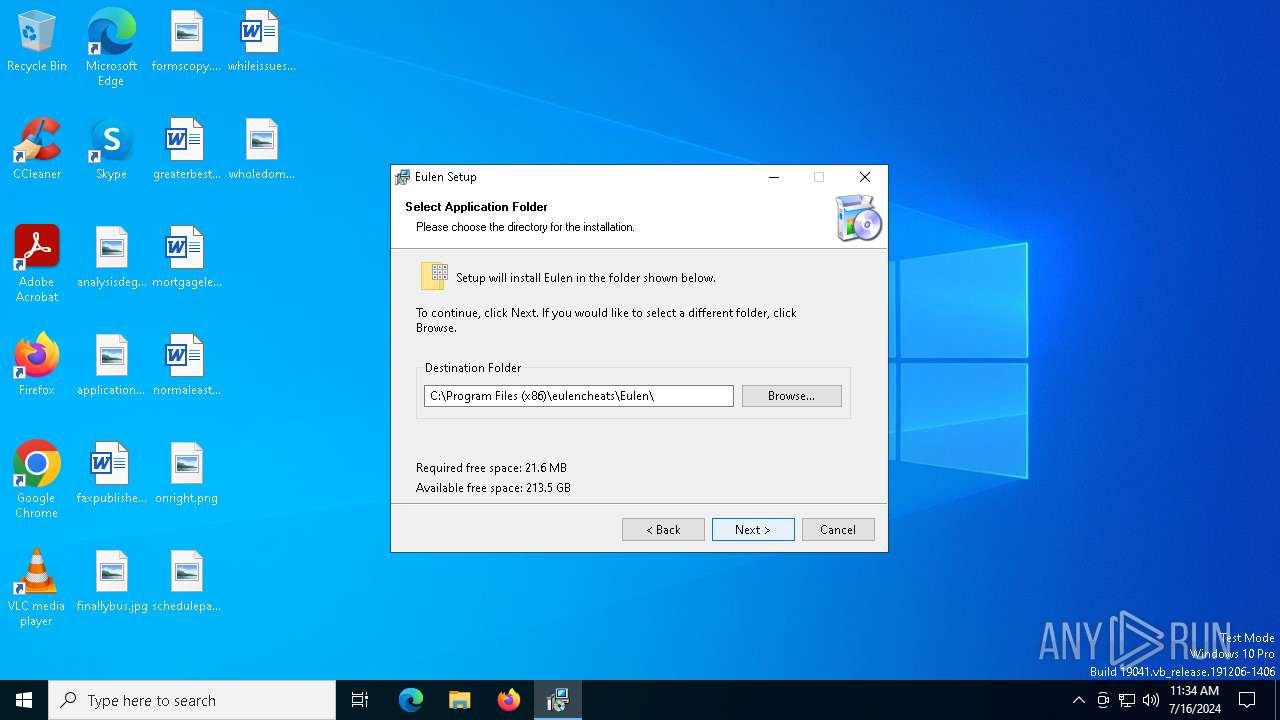
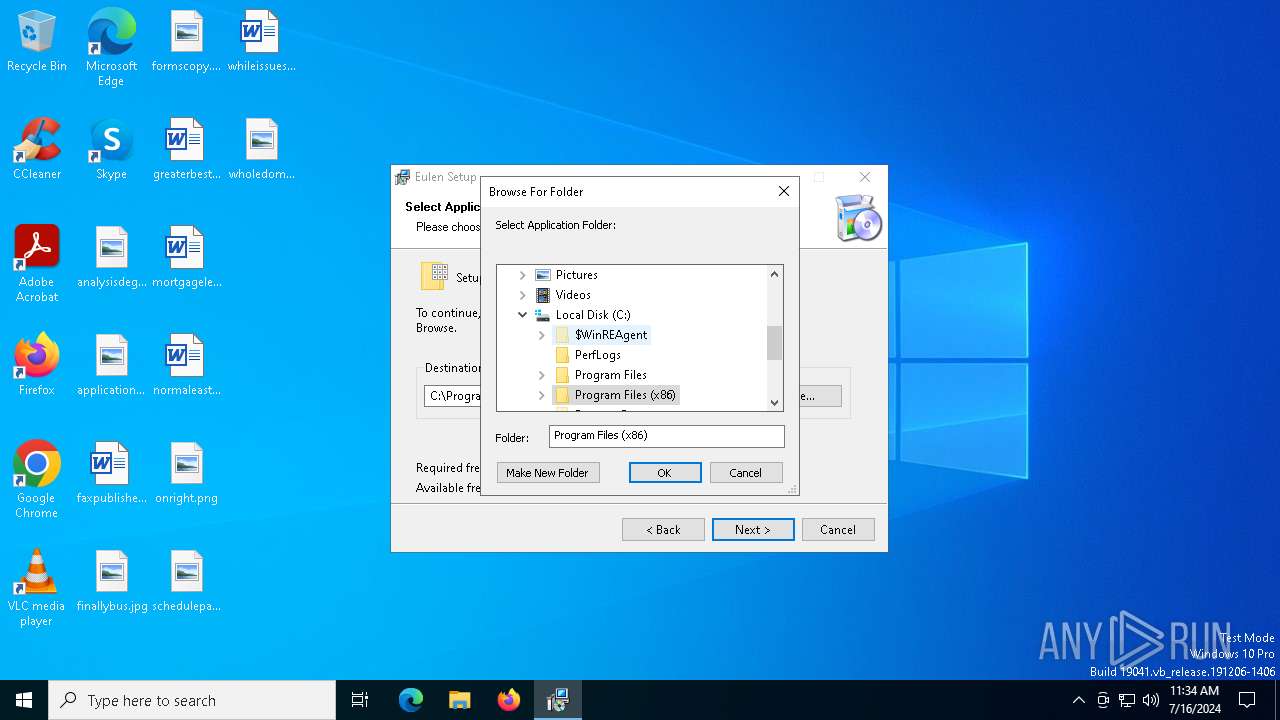
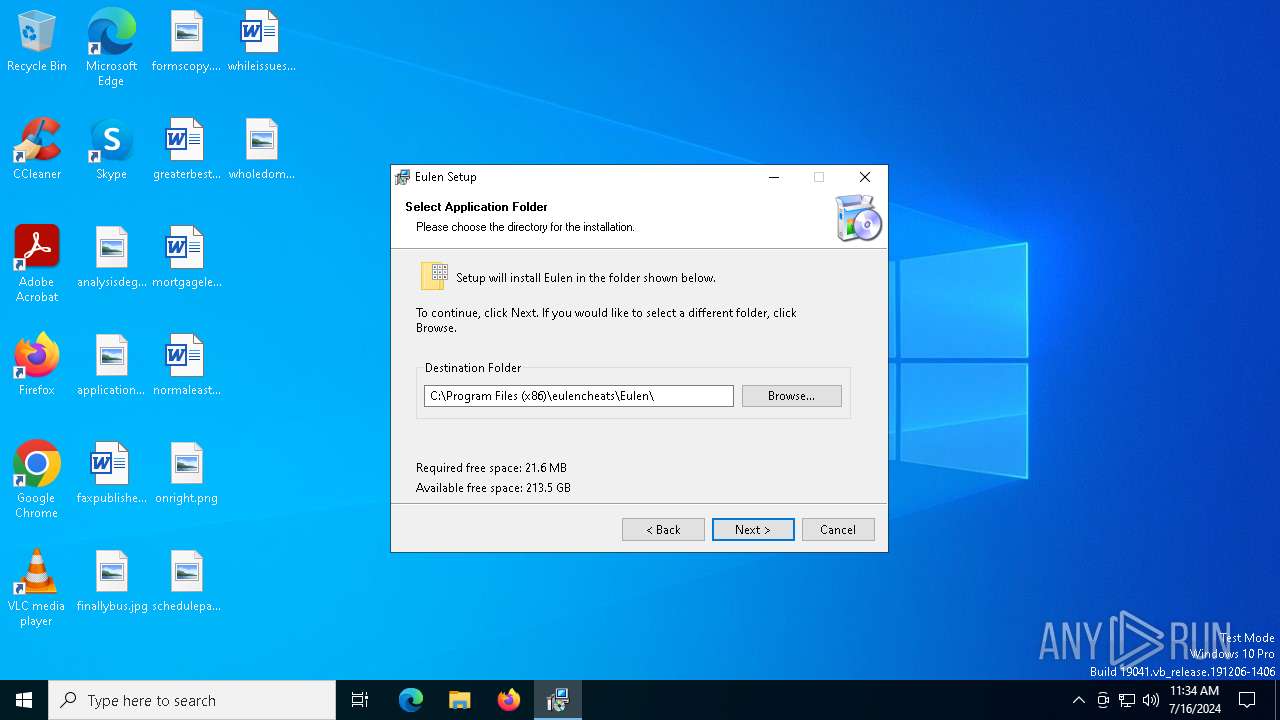
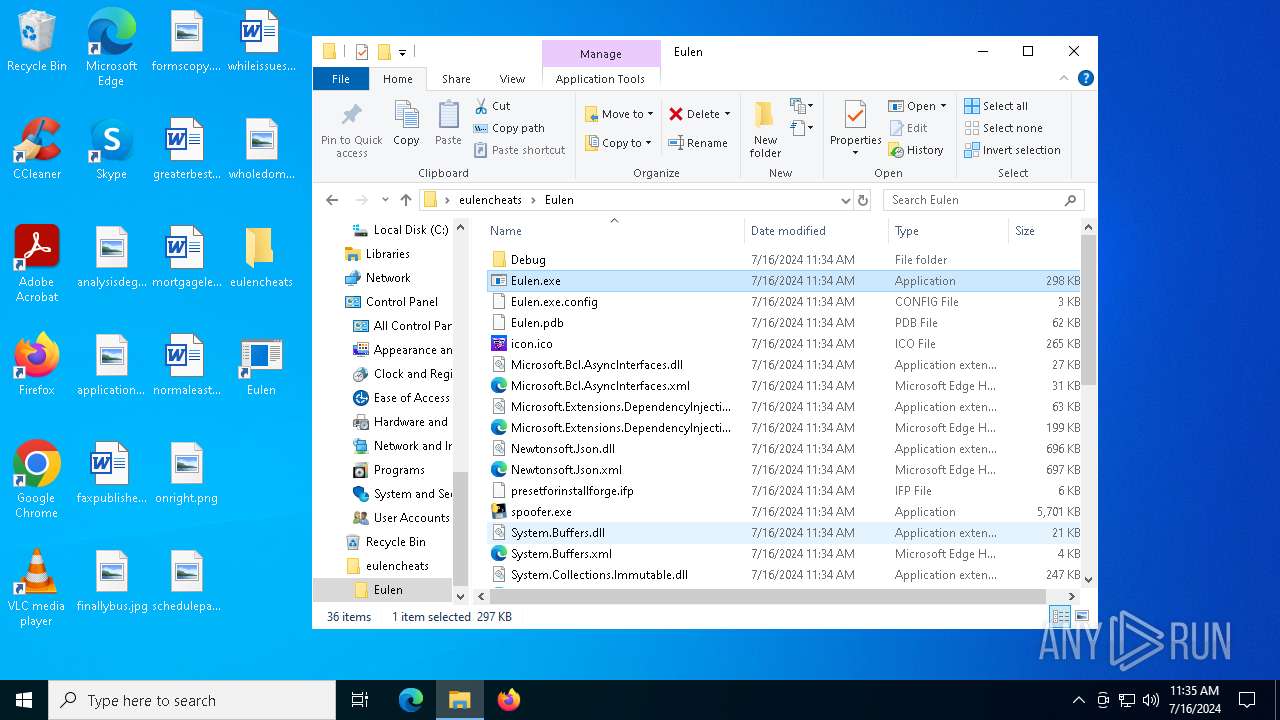
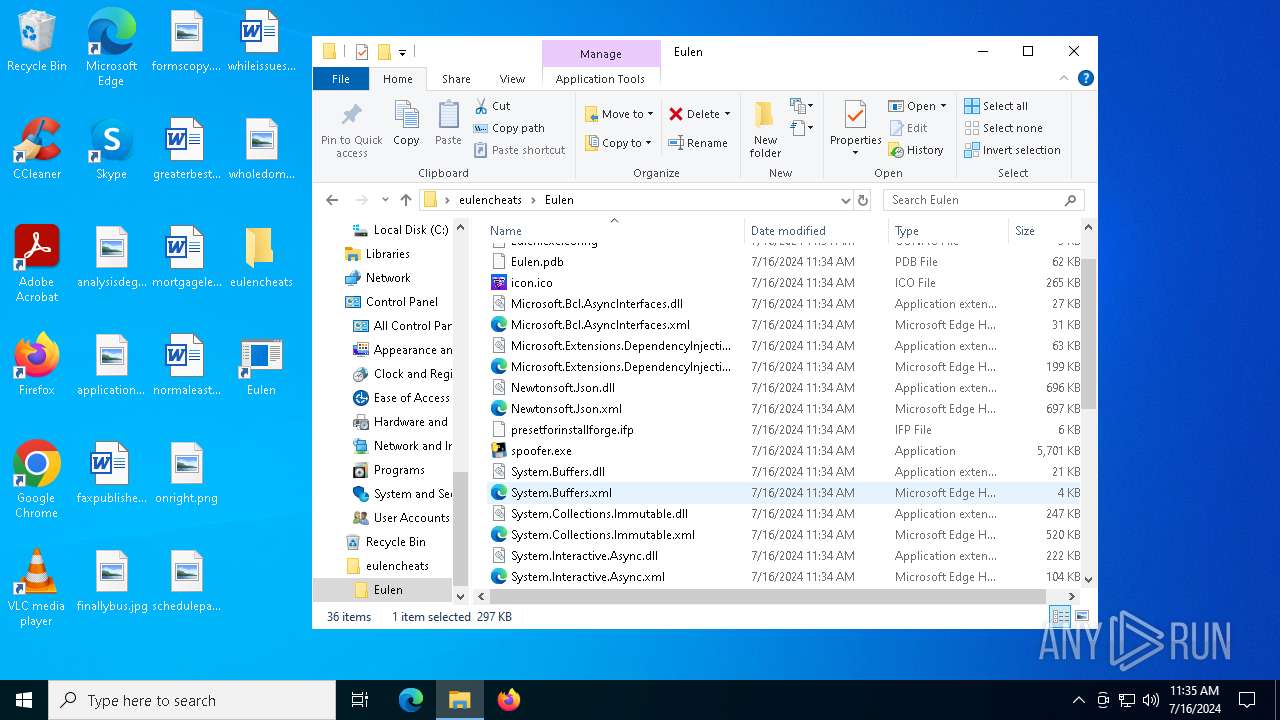
| File name: | Eulen.Installer.exe |
| Full analysis: | https://app.any.run/tasks/33e3e4d1-1a98-43a3-9bcc-48977b90e72e |
| Verdict: | Malicious activity |
| Analysis date: | July 16, 2024, 11:34:07 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows |
| MD5: | 19261726AFEEB62225EABD06682E47BC |
| SHA1: | 165C6ACA9D7CC12D166FCEE887FC3EF6CD7FF2BD |
| SHA256: | 9B0B8D0EB59B60B3A0B04E85091E49ADCC8A26DC3CE4F3DED129D5A1827509D3 |
| SSDEEP: | 98304:6VG6qMU5/XdPiF7H30PG49HCZ4WHDqKItKuS1KsgVtZLtlW9fL6hmaw3BXXJ3lj8:INY7Jwr9KOsOSnvbr465jCiV |
MALICIOUS
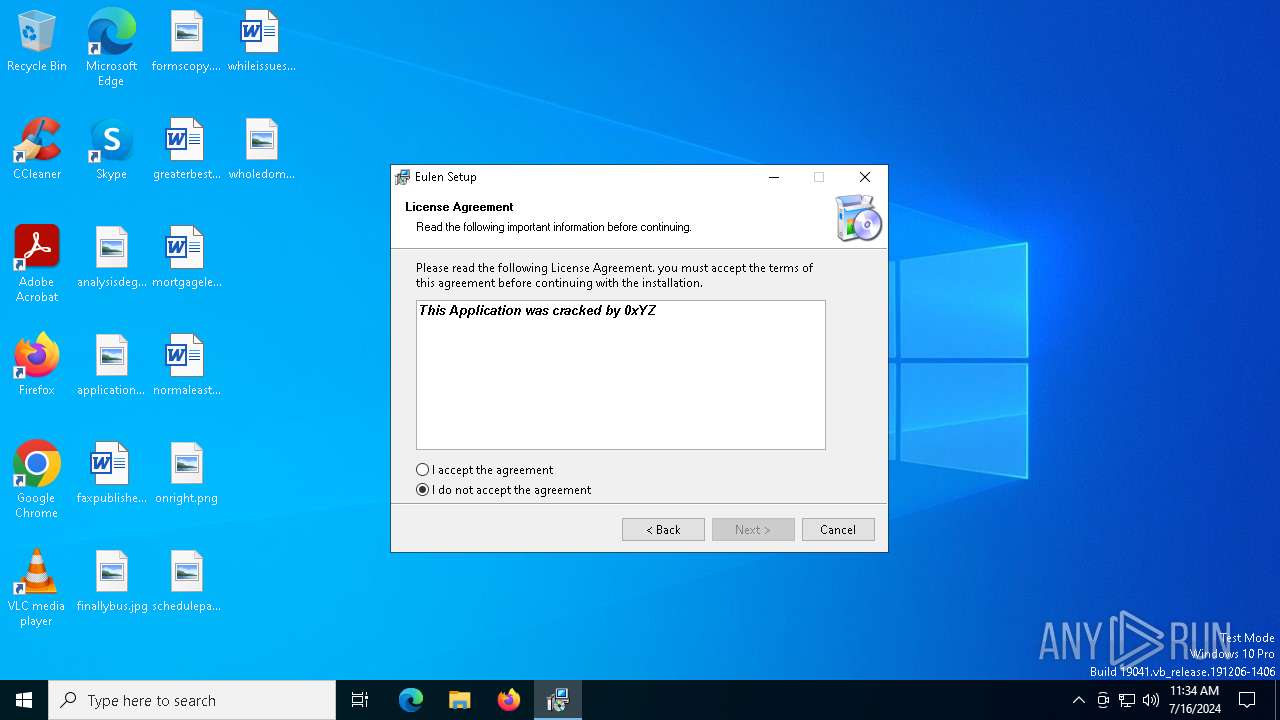
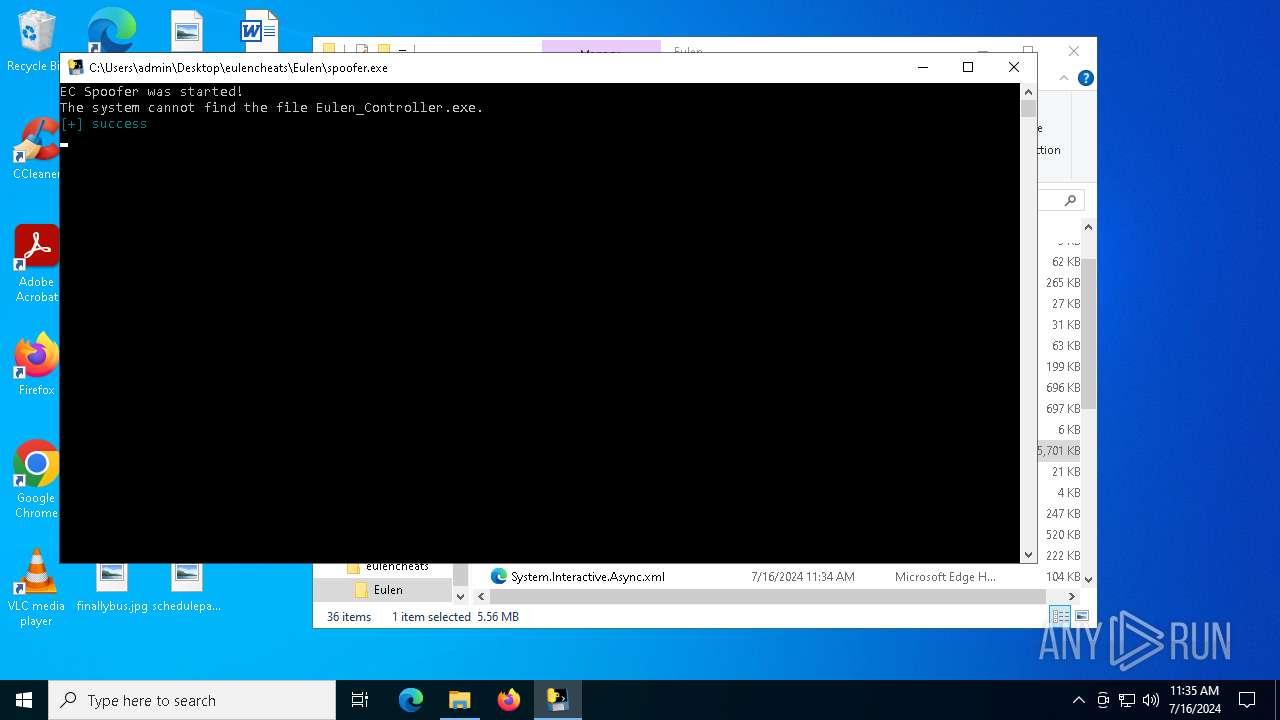
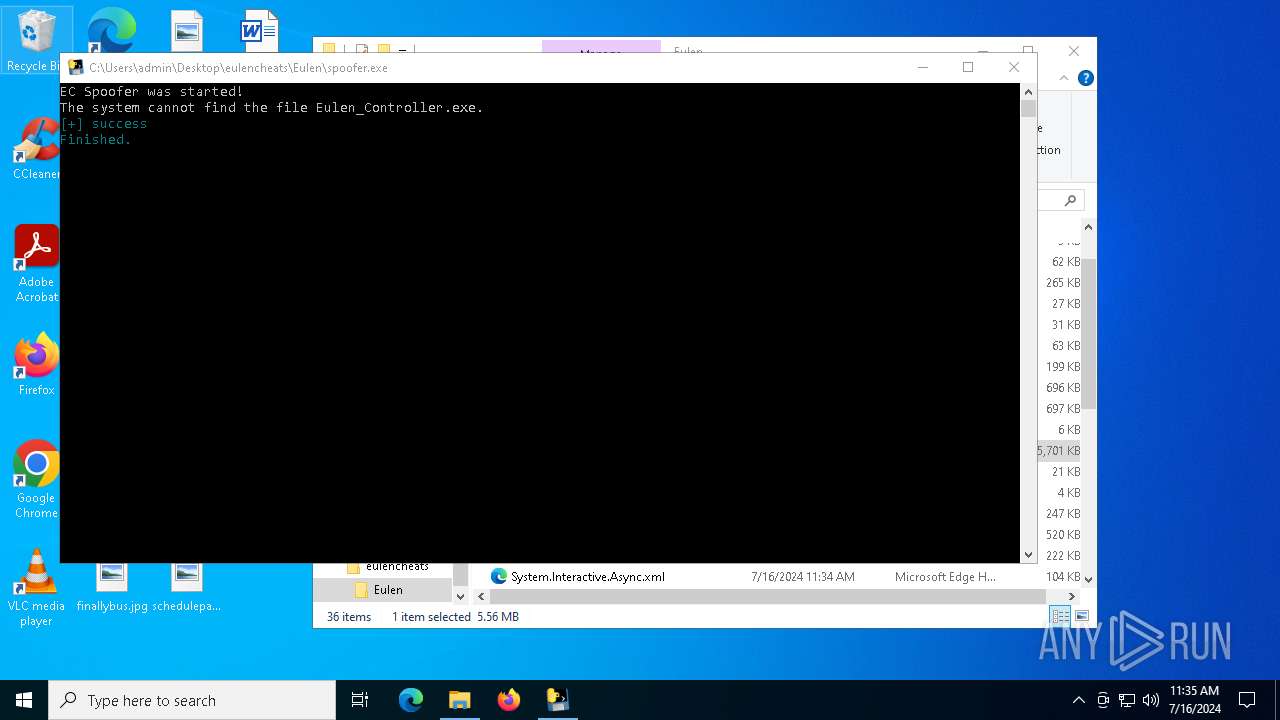
Drops the executable file immediately after the start
- Eulen.Installer.exe (PID: 6648)
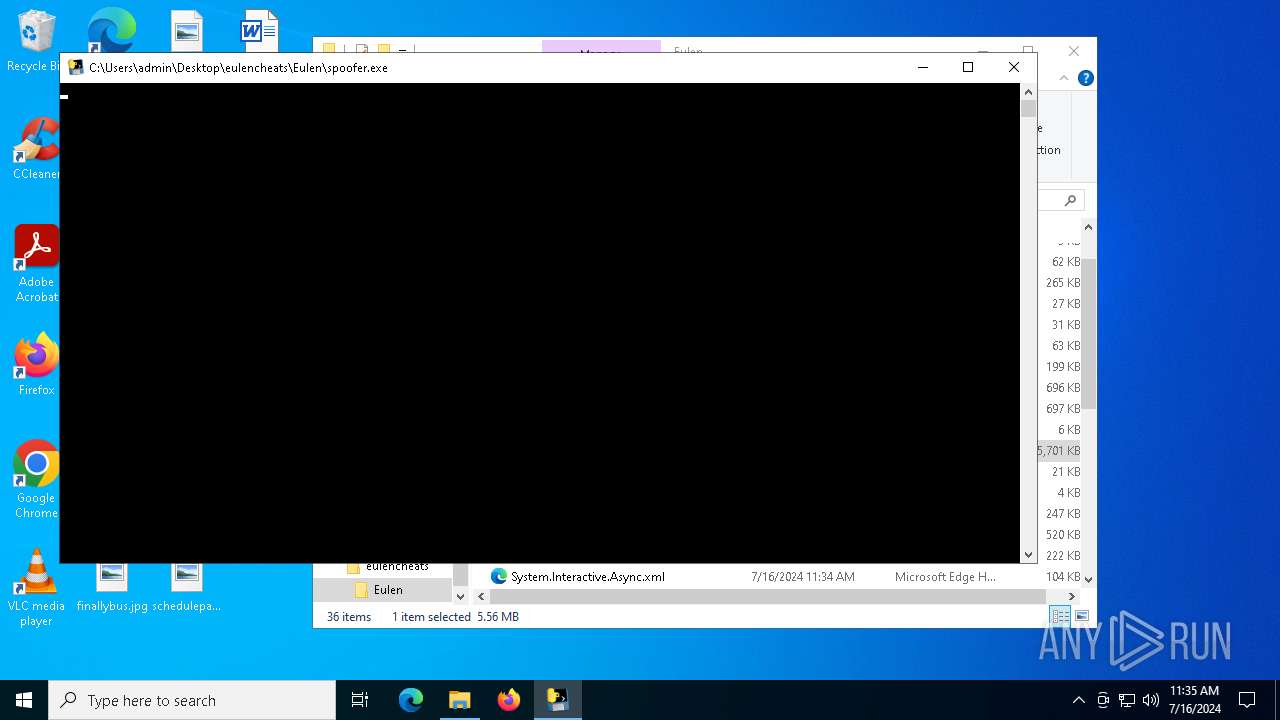
- spoofer.exe (PID: 6704)
Actions looks like stealing of personal data
- Eulen.Installer.exe (PID: 6648)
- Eulen.exe (PID: 4980)
- Eulen.exe (PID: 5604)
SUSPICIOUS
Creates file in the systems drive root
- Eulen.Installer.exe (PID: 6648)
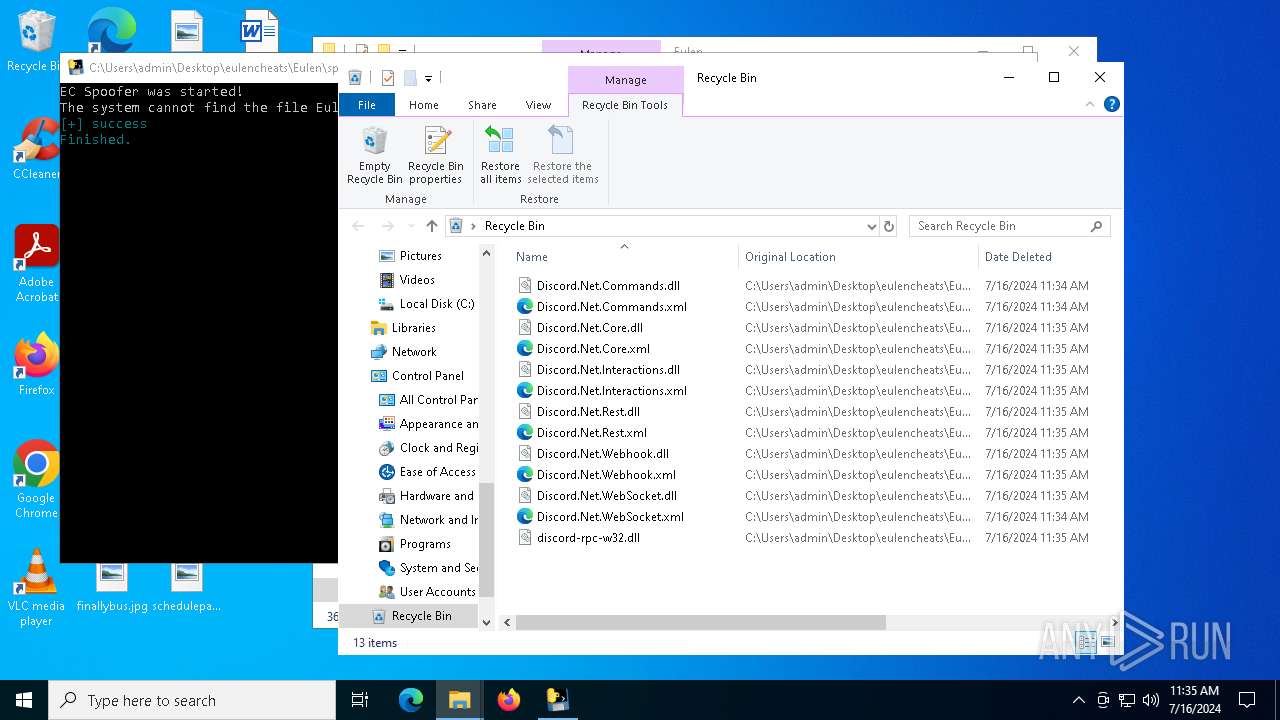
Process drops legitimate windows executable
- Eulen.Installer.exe (PID: 6648)
- spoofer.exe (PID: 6704)
Reads security settings of Internet Explorer
- Eulen.Installer.exe (PID: 6648)
- Eulen.exe (PID: 4980)
- Eulen.exe (PID: 5604)
Creates a software uninstall entry
- Eulen.Installer.exe (PID: 6648)
The process creates files with name similar to system file names
- Eulen.Installer.exe (PID: 6648)
Executable content was dropped or overwritten
- Eulen.Installer.exe (PID: 6648)
- spoofer.exe (PID: 6704)
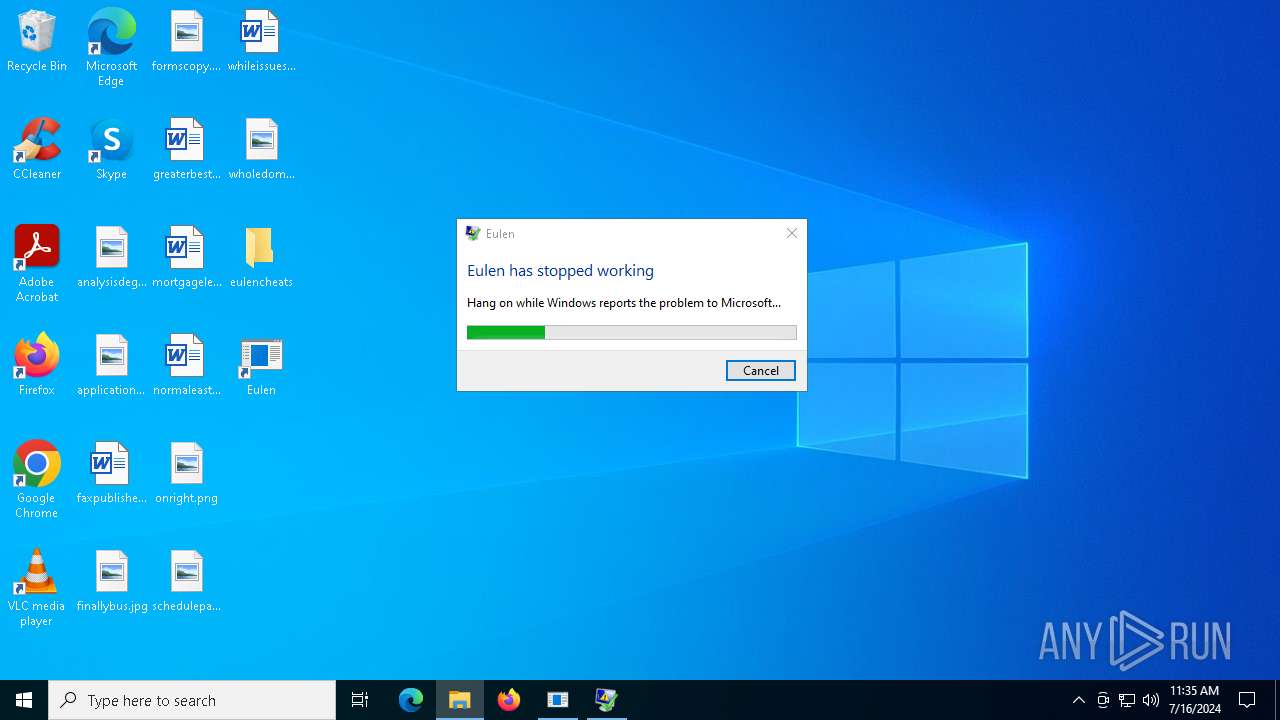
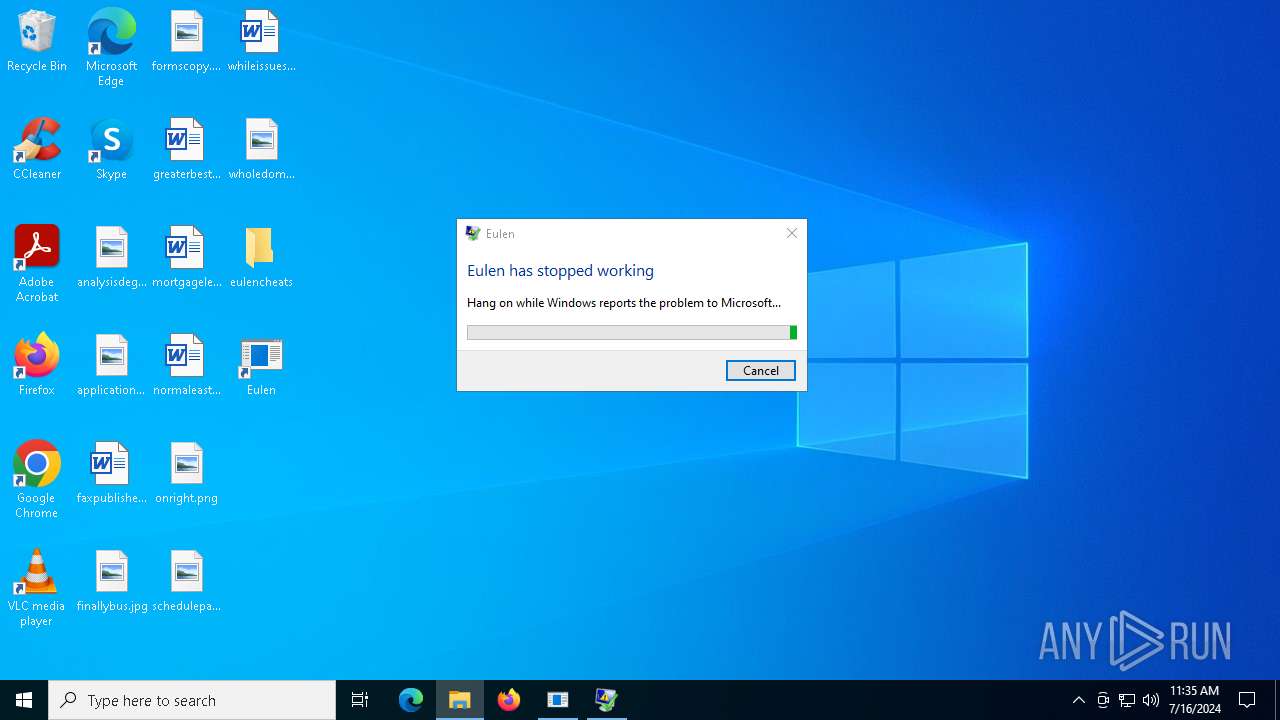
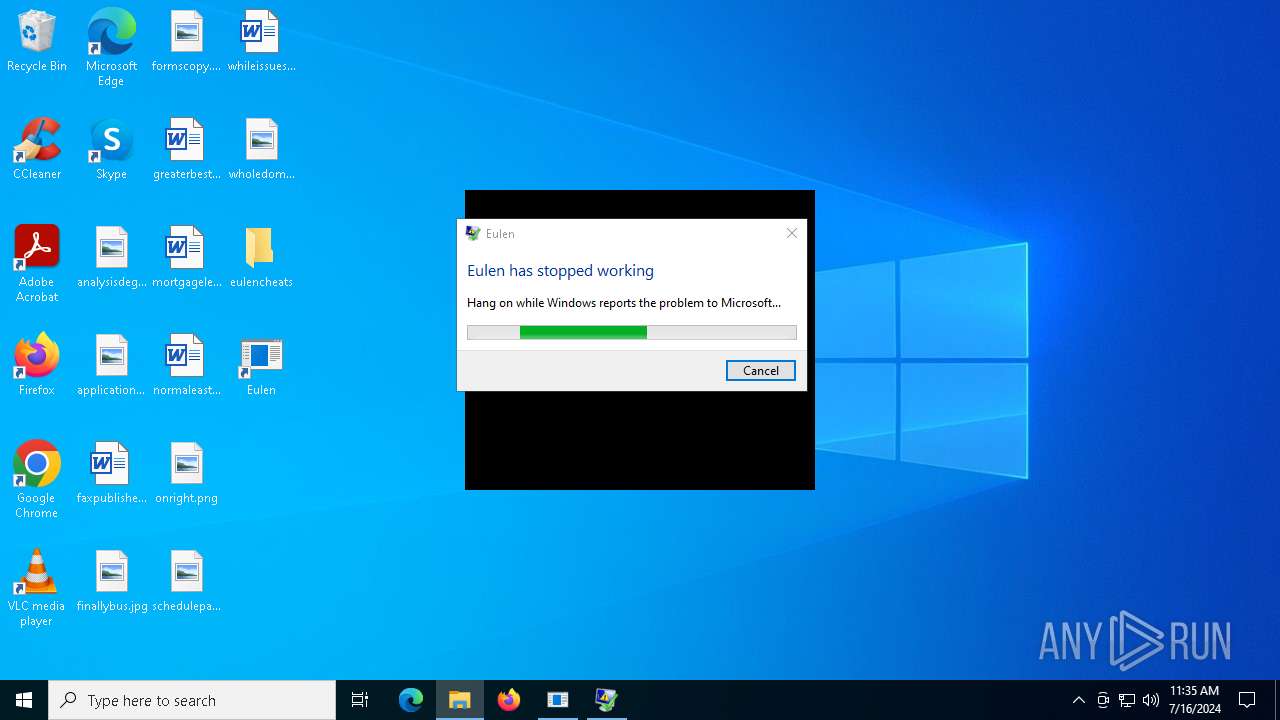
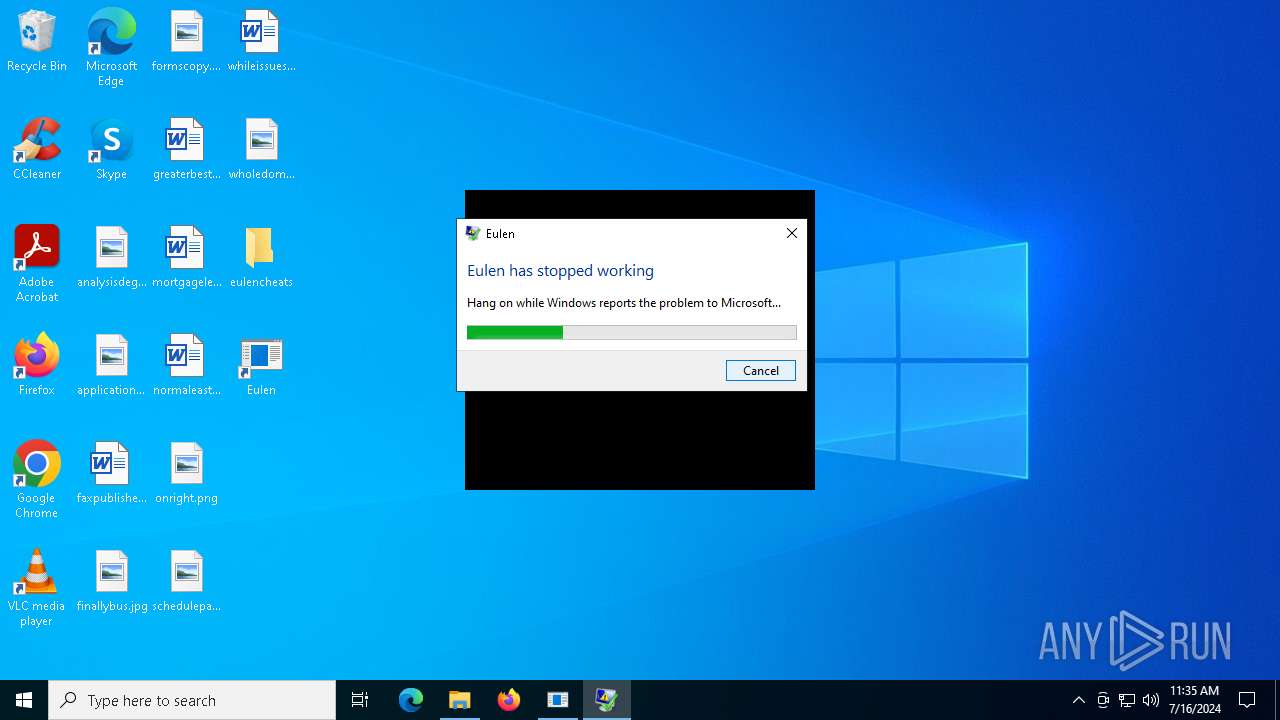
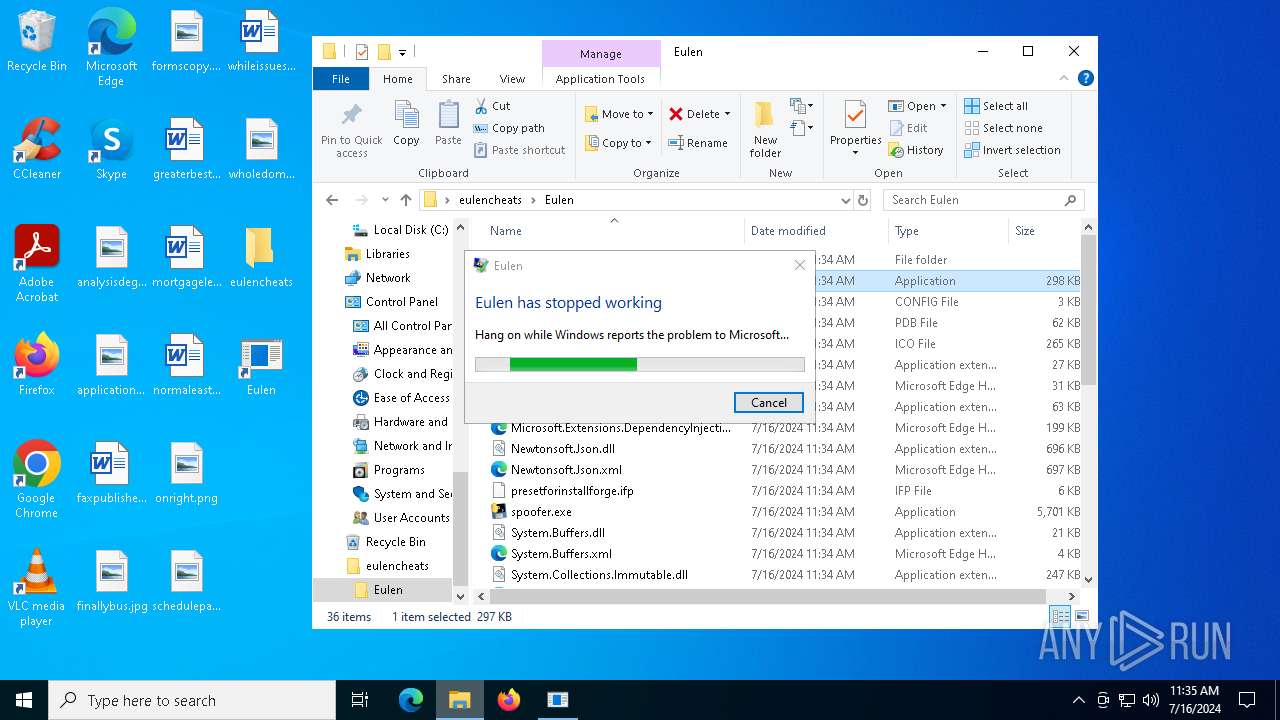
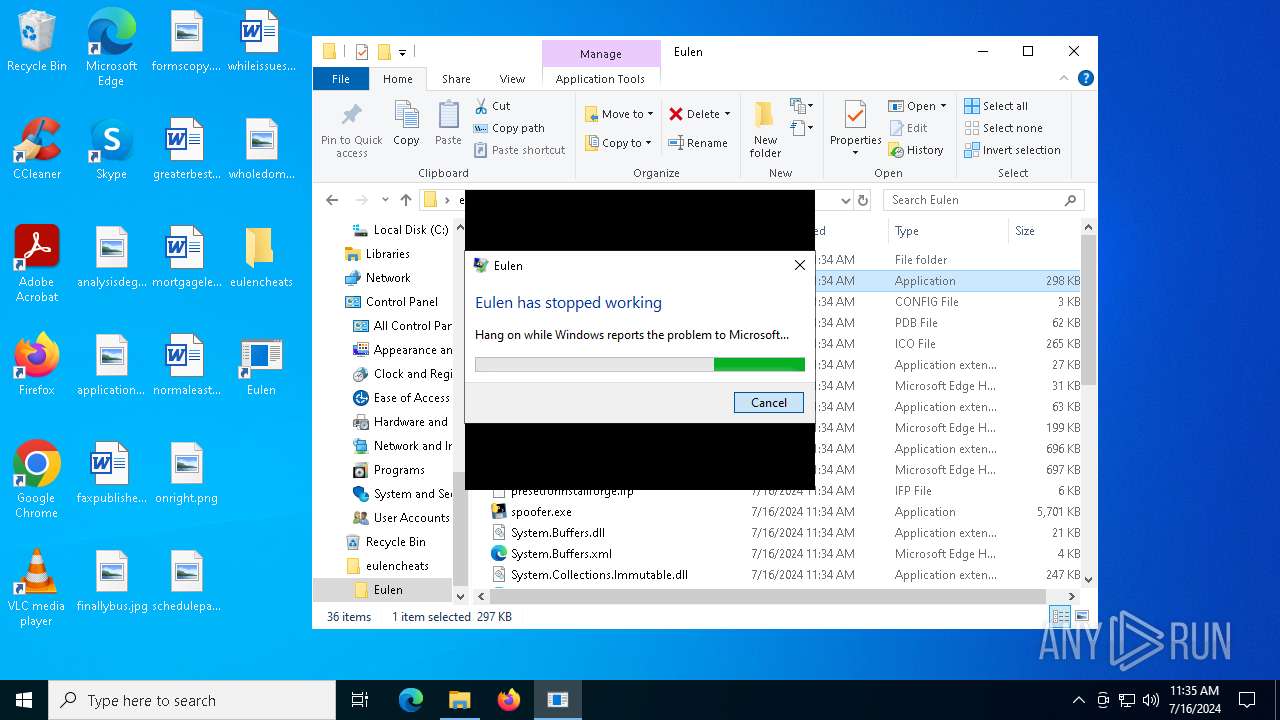
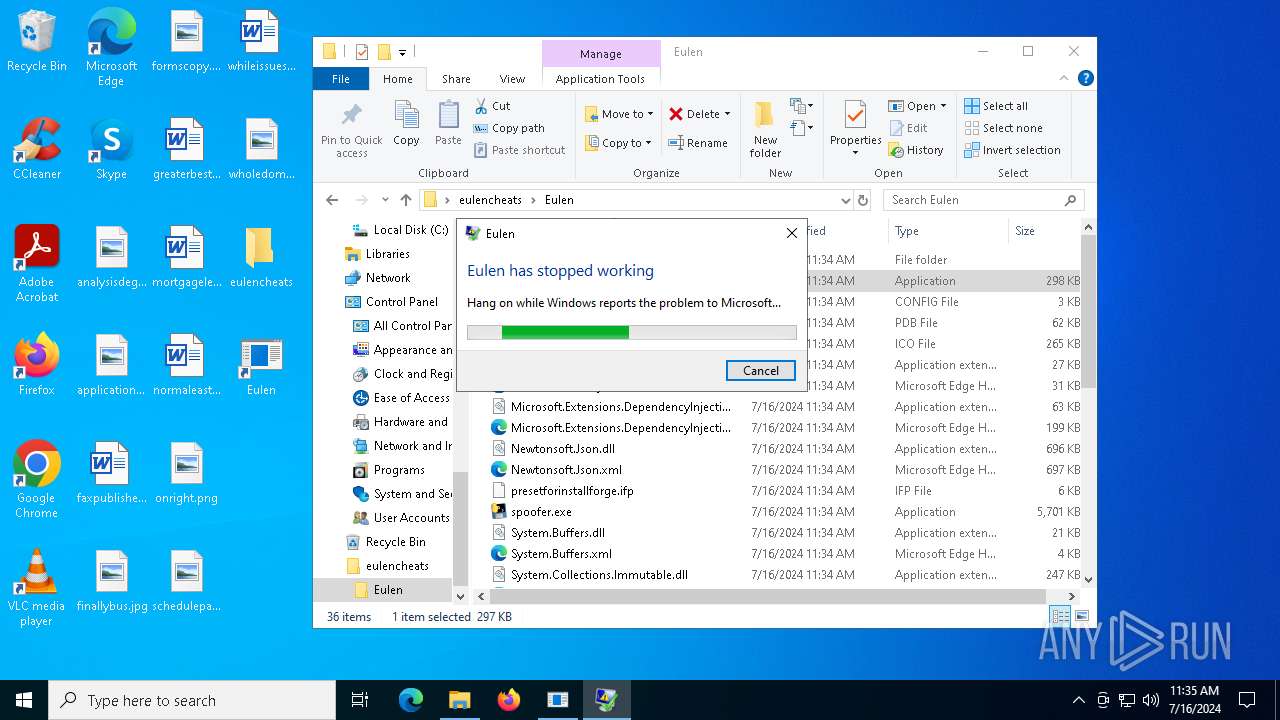
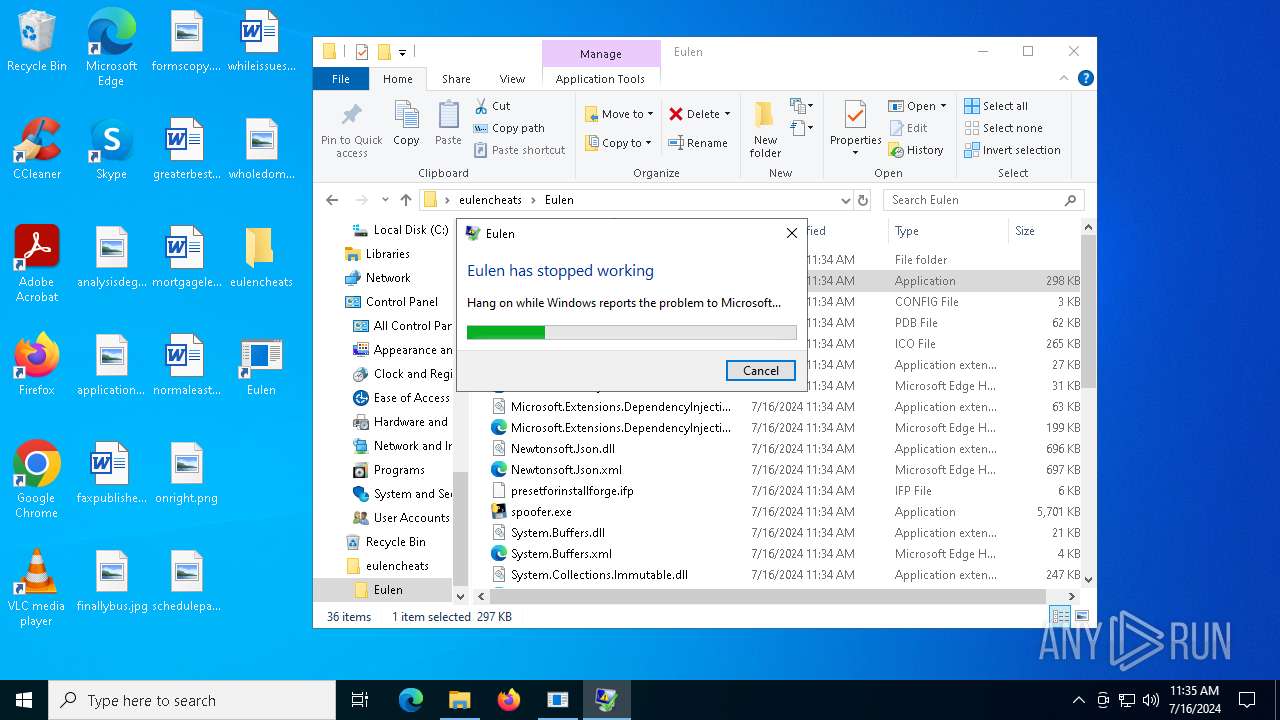
Executes application which crashes
- Eulen.exe (PID: 4980)
- Eulen.exe (PID: 5604)
The process drops C-runtime libraries
- spoofer.exe (PID: 6704)
Process drops python dynamic module
- spoofer.exe (PID: 6704)
Loads Python modules
- spoofer.exe (PID: 5960)
Application launched itself
- spoofer.exe (PID: 6704)
Starts CMD.EXE for commands execution
- spoofer.exe (PID: 5960)
INFO
Create files in a temporary directory
- Eulen.Installer.exe (PID: 6648)
- spoofer.exe (PID: 6704)
Checks supported languages
- Eulen.Installer.exe (PID: 6648)
- Eulen.exe (PID: 4980)
- spoofer.exe (PID: 6704)
- spoofer.exe (PID: 5960)
- Eulen.exe (PID: 5604)
Reads the computer name
- Eulen.Installer.exe (PID: 6648)
- Eulen.exe (PID: 4980)
- spoofer.exe (PID: 6704)
- Eulen.exe (PID: 5604)
Manual execution by a user
- Eulen.exe (PID: 4980)
- spoofer.exe (PID: 6704)
- Eulen.exe (PID: 5604)
Reads the machine GUID from the registry
- Eulen.exe (PID: 4980)
- spoofer.exe (PID: 5960)
- Eulen.exe (PID: 5604)
Checks proxy server information
- WerFault.exe (PID: 6688)
- WerFault.exe (PID: 1968)
- WerFault.exe (PID: 2020)
Reads the software policy settings
- WerFault.exe (PID: 6688)
- WerFault.exe (PID: 1968)
- WerFault.exe (PID: 2020)
Creates files or folders in the user directory
- WerFault.exe (PID: 6688)
- WerFault.exe (PID: 1968)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (47) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (34.1) |
| .dll | | | Win32 Dynamic Link Library (generic) (7.1) |
| .exe | | | Win32 Executable (generic) (4.9) |
| .exe | | | Win16/32 Executable Delphi generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:07:18 17:13:29+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit, No debug |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 795648 |
| InitializedDataSize: | 183296 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x16276 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 8.27.5.0 |
| ProductVersionNumber: | 8.27.5.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Unknown (0) |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
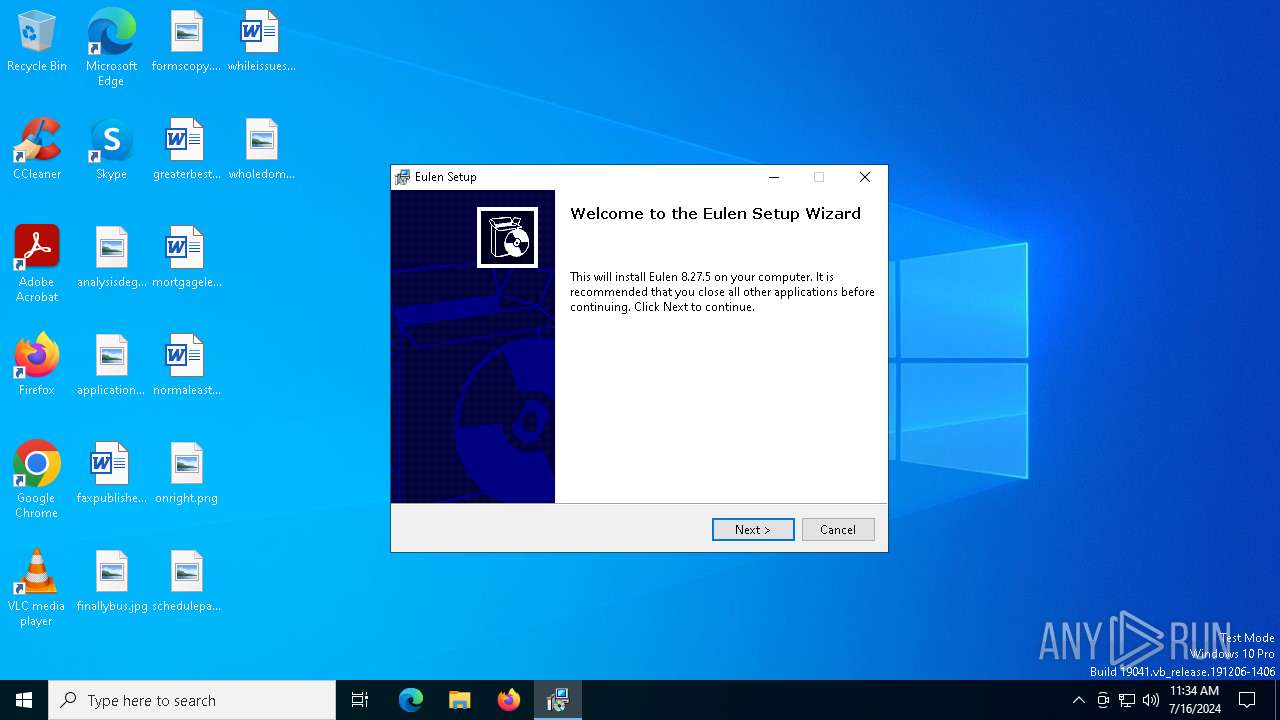
| ProductName: | Eulen Setup |
| InternalName: | Eulen Installer |
| OriginalFileName: | Eulen Installer.exe |
| ProductVersion: | 8.27.5 |
| FileVersion: | 8.27.5 |
| CompanyName: | eulencheats |
| Comments: | Created with InstallForge 1.4.4 |
Total processes
150
Monitored processes
12
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 836 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1220 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | spoofer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1968 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 4980 -s 1804 | C:\Windows\SysWOW64\WerFault.exe | Eulen.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2020 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 5604 -s 1752 | C:\Windows\SysWOW64\WerFault.exe | Eulen.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4980 | "C:\Users\admin\Desktop\eulencheats\Eulen\Eulen.exe" | C:\Users\admin\Desktop\eulencheats\Eulen\Eulen.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Eulen Exit code: 3221226525 Version: 1.0.0.0 Modules
| |||||||||||||||
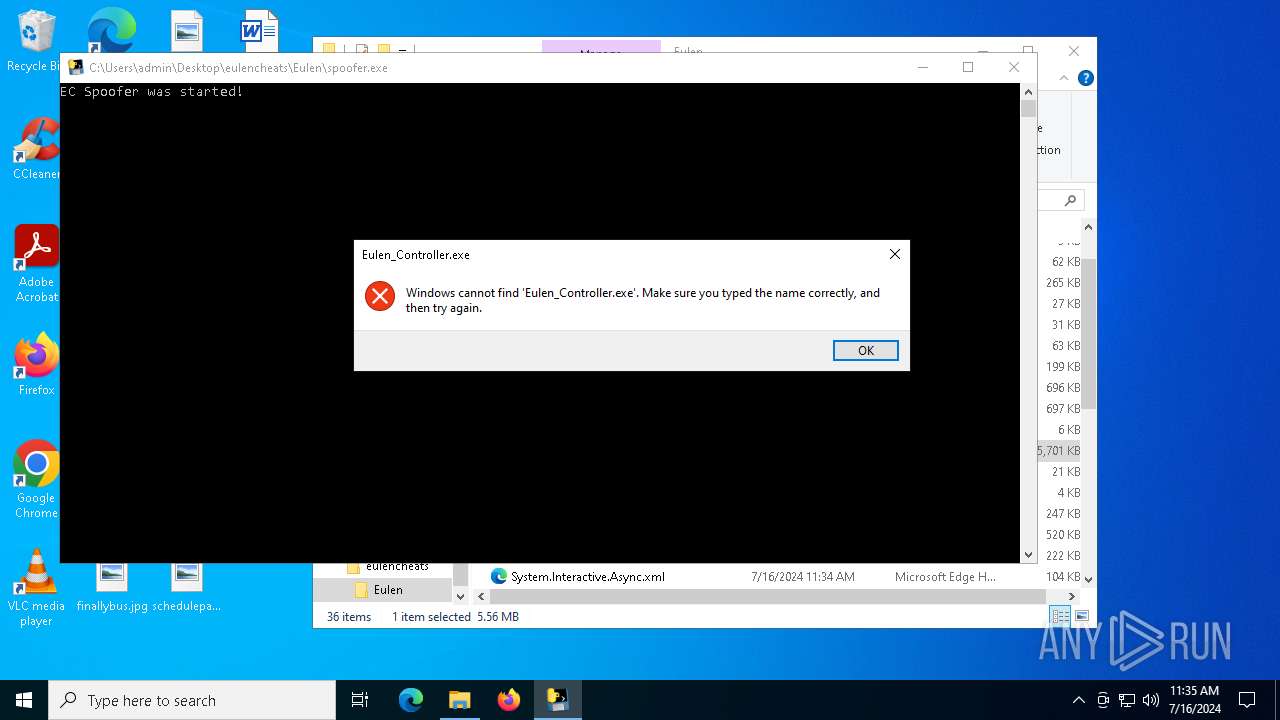
| 5532 | C:\WINDOWS\system32\cmd.exe /c start Eulen_Controller.exe | C:\Windows\System32\cmd.exe | — | spoofer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5604 | "C:\Users\admin\Desktop\eulencheats\Eulen\Eulen.exe" | C:\Users\admin\Desktop\eulencheats\Eulen\Eulen.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Eulen Version: 1.0.0.0 Modules
| |||||||||||||||
| 5960 | "C:\Users\admin\Desktop\eulencheats\Eulen\spoofer.exe" | C:\Users\admin\Desktop\eulencheats\Eulen\spoofer.exe | — | spoofer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6540 | "C:\Users\admin\AppData\Local\Temp\Eulen.Installer.exe" | C:\Users\admin\AppData\Local\Temp\Eulen.Installer.exe | — | explorer.exe | |||||||||||
User: admin Company: eulencheats Integrity Level: MEDIUM Exit code: 3221226540 Version: 8.27.5 Modules
| |||||||||||||||
| 6648 | "C:\Users\admin\AppData\Local\Temp\Eulen.Installer.exe" | C:\Users\admin\AppData\Local\Temp\Eulen.Installer.exe | explorer.exe | ||||||||||||
User: admin Company: eulencheats Integrity Level: HIGH Exit code: 0 Version: 8.27.5 Modules
| |||||||||||||||
Total events
20 494
Read events
20 478
Write events
16
Delete events
0
Modification events
| (PID) Process: | (6648) Eulen.Installer.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\MediaResources\DirectSound\Speaker Configuration |
| Operation: | write | Name: | Speaker Configuration |
Value: 4 | |||
| (PID) Process: | (6648) Eulen.Installer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | Browse For Folder Width |
Value: 318 | |||
| (PID) Process: | (6648) Eulen.Installer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | Browse For Folder Height |
Value: 288 | |||
| (PID) Process: | (6648) Eulen.Installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Eulen |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Users\admin\Desktop\eulencheats\Eulen\Uninstall.exe | |||
| (PID) Process: | (6648) Eulen.Installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Eulen |
| Operation: | write | Name: | UninstallString |
Value: C:\Users\admin\Desktop\eulencheats\Eulen\Uninstall.exe | |||
| (PID) Process: | (6648) Eulen.Installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Eulen |
| Operation: | write | Name: | InstallDate |
Value: 20240716 | |||
| (PID) Process: | (6648) Eulen.Installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Eulen |
| Operation: | write | Name: | InstallLocation |
Value: C:\Users\admin\Desktop\eulencheats\Eulen\ | |||
| (PID) Process: | (6648) Eulen.Installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Eulen |
| Operation: | write | Name: | EstimatedSize |
Value: 22076 | |||
| (PID) Process: | (6648) Eulen.Installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Eulen |
| Operation: | write | Name: | NoModify |
Value: 1 | |||
| (PID) Process: | (6648) Eulen.Installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Eulen |
| Operation: | write | Name: | NoRepair |
Value: 1 | |||
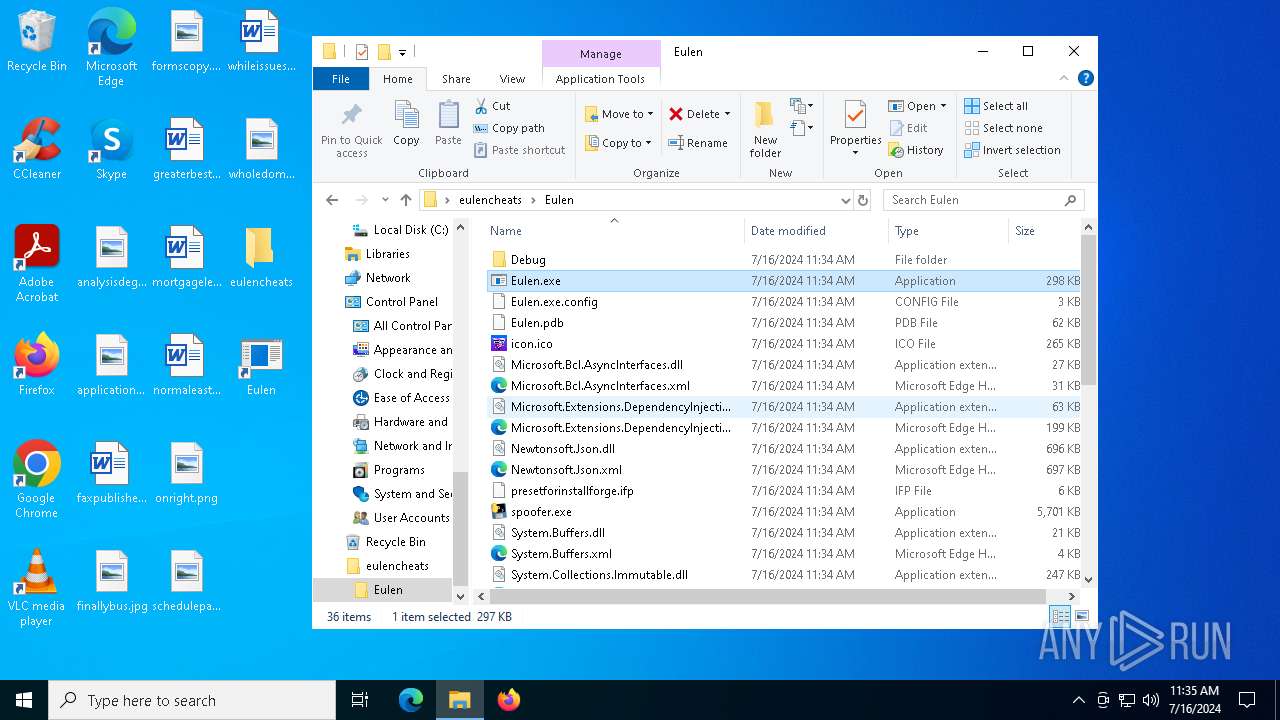
Executable files
36
Suspicious files
11
Text files
35
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6648 | Eulen.Installer.exe | C:\Users\admin\AppData\Local\Temp\IF{B38668DB-53C4-4CC7-9A7E-183B0B259544}\setupArchive.archive | — | |
MD5:— | SHA256:— | |||
| 6648 | Eulen.Installer.exe | C:\Users\admin\AppData\Local\Temp\IF{B38668DB-53C4-4CC7-9A7E-183B0B259544}\OS.dat | text | |
MD5:48D3C4D4CDC791B3C3E5B4432C3EA0BA | SHA256:38F778CBB7AA3D52F7FD5AB5CCF30B25962A6A5FECDFF6EFBB10501829459CA5 | |||
| 6648 | Eulen.Installer.exe | C:\Users\admin\AppData\Local\Temp\IF{B38668DB-53C4-4CC7-9A7E-183B0B259544}\setupConfiguration.archive | compressed | |
MD5:03F12A9620E961EDF92807014833B9D3 | SHA256:9D23817FF79860369312C135123DDC8407D54AC70FD641E7CE5E4A320C864D7E | |||
| 6648 | Eulen.Installer.exe | C:\Users\admin\Desktop\eulencheats\Eulen\Discord.Net.Rest.dll | executable | |
MD5:F886BA172A37911B022A10D54931509B | SHA256:AA82A19369498422CA40DE886C5B3A291269E44C78D101F2126C038E1E025315 | |||
| 6648 | Eulen.Installer.exe | C:\Users\admin\Desktop\eulencheats\Eulen\Discord.Net.Commands.dll | executable | |
MD5:D7B746736A3E3D7E4B746E2F6D99266C | SHA256:6FB5524D0F03158DBC113DC688CFC552F4E52F2CB858B74F2F173B32DFEB9FFD | |||
| 6648 | Eulen.Installer.exe | C:\Users\admin\Desktop\eulencheats\Eulen\Discord.Net.Interactions.xml | xml | |
MD5:4240B984D8072C2BAF50BCB51AE81A18 | SHA256:5E1585F002A7BAB3D97B6C2B72BBD7006F7A421C8F4819FC5D8BBEC5F1A2582D | |||
| 6648 | Eulen.Installer.exe | C:\Users\admin\Desktop\eulencheats\Eulen\Discord.Net.Webhook.dll | executable | |
MD5:9188D316763B975A9E3356A688C9607D | SHA256:ABD5A1E1DEBDBF33AE1281AAD9849A656A802438D54C413860C2D5103C7A362E | |||
| 6648 | Eulen.Installer.exe | C:\Users\admin\Desktop\eulencheats\Eulen\Uninstall.exe | executable | |
MD5:F553DFB018CECFFD6B8ABFDC3BA8A8DC | SHA256:57CC4023B38B9E512BF413C5D7299F367923235C0E19D20AB675F5B77C080CCA | |||
| 6648 | Eulen.Installer.exe | C:\Users\admin\Desktop\eulencheats\Eulen\Discord.Net.Rest.xml | xml | |
MD5:247C8AAB448604B436D8FF9B3D741E41 | SHA256:C7B71206A18E85B5C5903768248E6608337D6DBCE781A683CD5F8869944AB42B | |||
| 6648 | Eulen.Installer.exe | C:\Users\admin\Desktop\eulencheats\Eulen\Discord.Net.WebSocket.dll | executable | |
MD5:738A6E9D16277E5A66C57D57E1FC44E4 | SHA256:459337A2D00908B022ACF13E75F85EC48BEAB11BD697C155781F83407C157642 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
70
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2204 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2204 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3680 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6256 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6356 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5992 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6688 | WerFault.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6688 | WerFault.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5992 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1832 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.23.209.183:443 | www.bing.com | Akamai International B.V. | GB | unknown |
2124 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4656 | SearchApp.exe | 2.23.209.183:443 | www.bing.com | Akamai International B.V. | GB | unknown |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2204 | MoUsoCoreWorker.exe | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
2204 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
arc.msn.com |
| whitelisted |