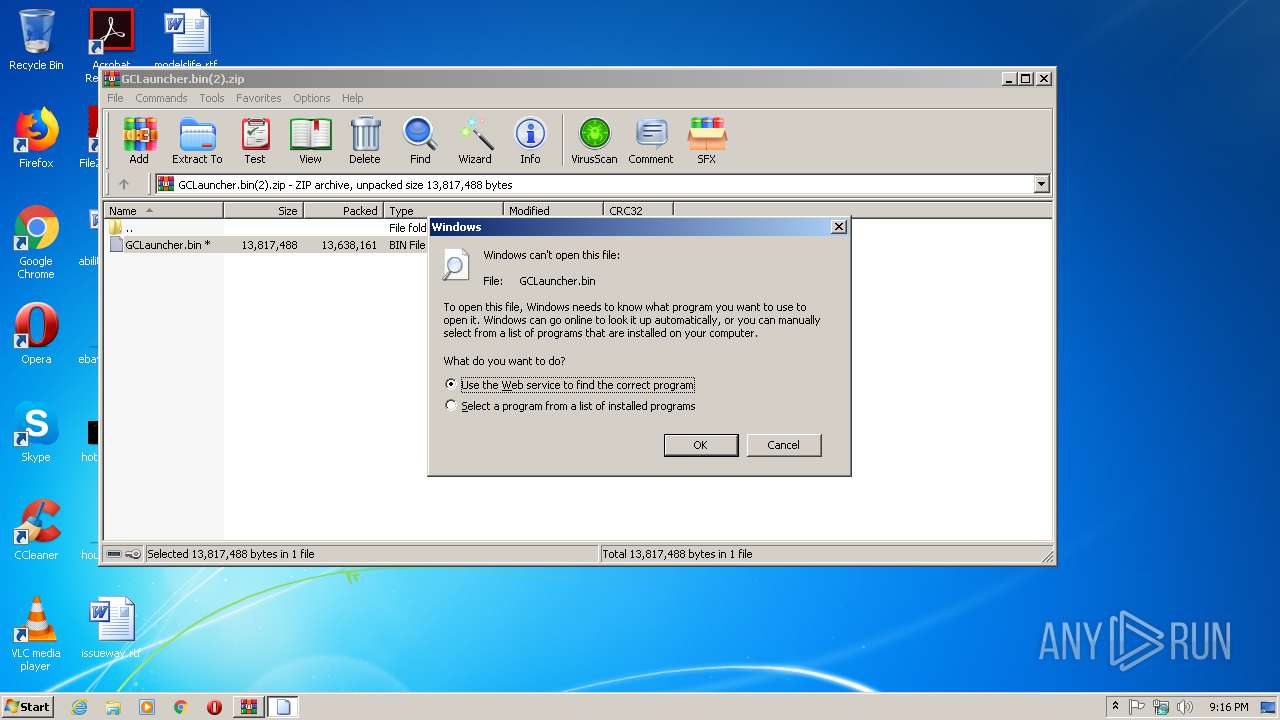
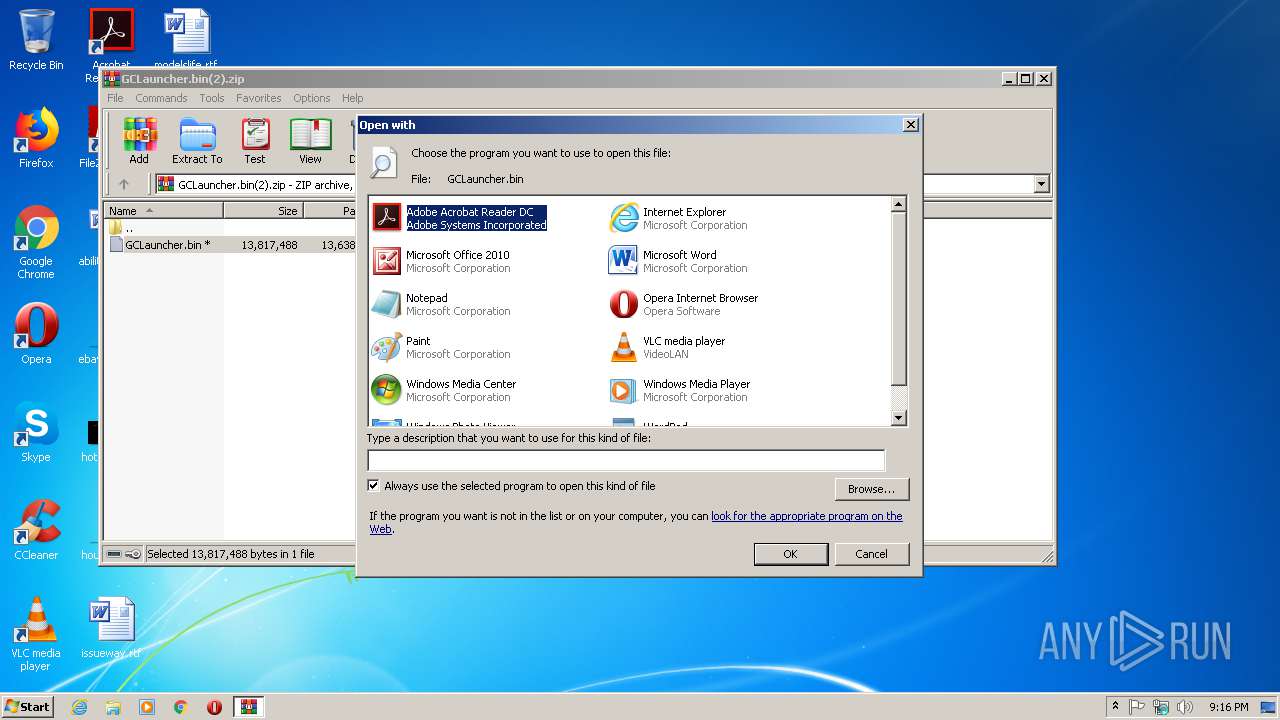
| File name: | GCLauncher.bin(2).zip |
| Full analysis: | https://app.any.run/tasks/09a2e32b-a2e3-4250-8230-c37a4fd5ddd9 |
| Verdict: | Malicious activity |
| Analysis date: | May 30, 2020, 20:15:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | FAEF3E871F9406E435C556ED2C62EF96 |
| SHA1: | 5A986403131E7EB0B6133DF6C70B8E08877839C1 |
| SHA256: | 9B0A954969819CC879450AEBD8D482233EC6CECA1421FE751E8EE754127D4DA3 |
| SSDEEP: | 196608:ZiLPDOdYL15HXMdh8gPaj746Re0e0bvrmkgvjWRGtjiyoXx+bKkl9Z4gB5WyLlkh:IrOdYL1ujete0mRvj0h1u4aWyLlkOCKe |
MALICIOUS
Changes the autorun value in the registry
- reg.exe (PID: 536)
SUSPICIOUS
Creates files in the user directory
- Skype.exe (PID: 2392)
- Skype.exe (PID: 3764)
- Skype.exe (PID: 2332)
Application launched itself
- Skype.exe (PID: 2392)
- Skype.exe (PID: 3764)
- Skype.exe (PID: 2332)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1492)
Uses RUNDLL32.EXE to load library
- WinRAR.exe (PID: 1492)
Reads CPU info
- Skype.exe (PID: 2392)
Modifies the open verb of a shell class
- Skype.exe (PID: 2392)
Changes IE settings (feature browser emulation)
- AcroRd32.exe (PID: 2424)
Uses REG.EXE to modify Windows registry
- Skype.exe (PID: 2392)
INFO
Manual execution by user
- Skype.exe (PID: 2392)
- opera.exe (PID: 2488)
Reads the hosts file
- Skype.exe (PID: 2392)
- RdrCEF.exe (PID: 3952)
Application launched itself
- AcroRd32.exe (PID: 2424)
- RdrCEF.exe (PID: 3952)
Creates files in the user directory
- opera.exe (PID: 2488)
Reads settings of System Certificates
- Skype.exe (PID: 2392)
Dropped object may contain Bitcoin addresses
- Skype.exe (PID: 2392)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 788 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:05:30 22:08:17 |
| ZipCRC: | 0x939d3000 |
| ZipCompressedSize: | 13638161 |
| ZipUncompressedSize: | 13817488 |
| ZipFileName: | GCLauncher.bin |
Total processes
50
Monitored processes
15
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 536 | C:\Windows\system32\reg.exe ADD HKCU\Software\Microsoft\Windows\CurrentVersion\Run /v "Skype for Desktop" /t REG_SZ /d "C:\Program Files\Microsoft\Skype for Desktop\Skype.exe" /f | C:\Windows\system32\reg.exe | Skype.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1360 | "C:\Program Files\Microsoft\Skype for Desktop\Skype.exe" --reporter-url=https://rink.hockeyapp.net/api/2/apps/a741743329d94bc08826af367733939d/crashes/upload --application-name=skype-preview "--crashes-directory=C:\Users\admin\AppData\Local\Temp\skype-preview Crashes" --v=1 | C:\Program Files\Microsoft\Skype for Desktop\Skype.exe | Skype.exe | ||||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: MEDIUM Description: Skype Exit code: 0 Version: 8.29.0.50 Modules
| |||||||||||||||
| 1492 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\GCLauncher.bin(2).zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1992 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="3952.0.1031253272\1879545664" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 2284 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\Rar$DIb1492.11287\GCLauncher.bin | C:\Windows\system32\rundll32.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2332 | "C:\Program Files\Microsoft\Skype for Desktop\Skype.exe" --type=renderer --ms-disable-indexeddb-transaction-timeout --no-sandbox --service-pipe-token=E49E4A6D855220AF01F29582343A585D --lang=en-US --app-user-model-id=Microsoft.Skype.SkypeDesktop --app-path="C:\Program Files\Microsoft\Skype for Desktop\resources\app.asar" --node-integration=false --webview-tag=true --no-sandbox --preload="C:\Program Files\Microsoft\Skype for Desktop\resources\app.asar\Preload.js" --context-id=1 --enable-pinch --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --content-image-texture-target=0,0,3553;0,1,3553;0,2,3553;0,3,3553;0,4,3553;0,5,3553;0,6,3553;0,7,3553;0,8,3553;0,9,3553;0,10,3553;0,11,3553;0,12,3553;0,13,3553;0,14,3553;0,15,3553;0,16,3553;0,17,3553;1,0,3553;1,1,3553;1,2,3553;1,3,3553;1,4,3553;1,5,3553;1,6,3553;1,7,3553;1,8,3553;1,9,3553;1,10,3553;1,11,3553;1,12,3553;1,13,3553;1,14,3553;1,15,3553;1,16,3553;1,17,3553;2,0,3553;2,1,3553;2,2,3553;2,3,3553;2,4,3553;2,5,3553;2,6,3553;2,7,3553;2,8,3553;2,9,3553;2,10,3553;2,11,3553;2,12,3553;2,13,3553;2,14,3553;2,15,3553;2,16,3553;2,17,3553;3,0,3553;3,1,3553;3,2,3553;3,3,3553;3,4,3553;3,5,3553;3,6,3553;3,7,3553;3,8,3553;3,9,3553;3,10,3553;3,11,3553;3,12,3553;3,13,3553;3,14,3553;3,15,3553;3,16,3553;3,17,3553;4,0,3553;4,1,3553;4,2,3553;4,3,3553;4,4,3553;4,5,3553;4,6,3553;4,7,3553;4,8,3553;4,9,3553;4,10,3553;4,11,3553;4,12,3553;4,13,3553;4,14,3553;4,15,3553;4,16,3553;4,17,3553 --disable-accelerated-video-decode --disable-gpu-compositing --enable-gpu-async-worker-context --service-request-channel-token=E49E4A6D855220AF01F29582343A585D --renderer-client-id=4 --mojo-platform-channel-handle=2672 /prefetch:1 | C:\Program Files\Microsoft\Skype for Desktop\Skype.exe | — | Skype.exe | |||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: MEDIUM Description: Skype Exit code: 0 Version: 8.29.0.50 Modules
| |||||||||||||||
| 2392 | "C:\Program Files\Microsoft\Skype for Desktop\Skype.exe" | C:\Program Files\Microsoft\Skype for Desktop\Skype.exe | explorer.exe | ||||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: MEDIUM Description: Skype Exit code: 0 Version: 8.29.0.50 Modules
| |||||||||||||||
| 2424 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIb1492.11287\GCLauncher.bin" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | rundll32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 0 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 2488 | "C:\Program Files\Opera\opera.exe" | C:\Program Files\Opera\opera.exe | explorer.exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: MEDIUM Description: Opera Internet Browser Exit code: 0 Version: 1748 Modules
| |||||||||||||||
| 2648 | C:\Windows\system32\reg.exe QUERY HKCU\Software\Microsoft\Skype /v RestartForUpdate | C:\Windows\system32\reg.exe | — | Skype.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 406
Read events
1 242
Write events
164
Delete events
0
Modification events
| (PID) Process: | (1492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1492) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1492) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (1492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\GCLauncher.bin(2).zip | |||
| (PID) Process: | (1492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
1
Suspicious files
29
Text files
16
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2392 | Skype.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\5OE3C9QU55NVGVZWS7YI.temp | — | |
MD5:— | SHA256:— | |||
| 2488 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opr1A77.tmp | — | |
MD5:— | SHA256:— | |||
| 2488 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opr1AC7.tmp | — | |
MD5:— | SHA256:— | |||
| 4028 | AcroRd32.exe | C:\Users\admin\AppData\LocalLow\Adobe\Acrobat\DC\ReaderMessages-journal | — | |
MD5:— | SHA256:— | |||
| 2392 | Skype.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\b916037c1e115fe0.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 2488 | opera.exe | C:\Users\admin\AppData\Local\Opera\Opera\cache\sesn\opr00001.tmp | — | |
MD5:— | SHA256:— | |||
| 2488 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opssl6.dat | binary | |
MD5:— | SHA256:— | |||
| 2488 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\HDVCT9ZV6ZSRPRUB9T5C.temp | — | |
MD5:— | SHA256:— | |||
| 2816 | Skype.exe | C:\Users\admin\AppData\Local\Temp\skype-preview Crashes\operation_log.txt | text | |
MD5:— | SHA256:— | |||
| 2488 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\operaprefs.ini | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
11
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2488 | opera.exe | GET | 200 | 93.184.220.29:80 | http://crl4.digicert.com/DigiCertHighAssuranceEVRootCA.crl | US | der | 564 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2392 | Skype.exe | 23.210.249.5:443 | download.skype.com | Akamai International B.V. | NL | whitelisted |
2488 | opera.exe | 185.26.182.93:443 | certs.opera.com | Opera Software AS | — | whitelisted |
2488 | opera.exe | 93.184.220.29:80 | crl4.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2392 | Skype.exe | 172.217.21.202:443 | www.googleapis.com | Google Inc. | US | whitelisted |
2392 | Skype.exe | 152.199.19.160:443 | bot-framework.azureedge.net | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2392 | Skype.exe | 52.174.193.75:443 | get.skype.com | Microsoft Corporation | NL | whitelisted |
2392 | Skype.exe | 13.107.42.23:443 | a.config.skype.com | Microsoft Corporation | US | suspicious |
2392 | Skype.exe | 52.233.180.130:443 | avatar.skype.com | Microsoft Corporation | NL | unknown |
— | — | 13.107.42.23:443 | a.config.skype.com | Microsoft Corporation | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
get.skype.com |
| whitelisted |
a.config.skype.com |
| whitelisted |
download.skype.com |
| whitelisted |
certs.opera.com |
| whitelisted |
crl4.digicert.com |
| whitelisted |
www.googleapis.com |
| whitelisted |
avatar.skype.com |
| whitelisted |
bot-framework.azureedge.net |
| whitelisted |
config.edge.skype.com |
| malicious |
Threats
Process | Message |
|---|---|
Skype.exe | [1360:1836:0530/211645.194:VERBOSE1:crash_service.cc(333)] client start. pid = 2392
|
Skype.exe | [1360:2160:0530/211645.194:VERBOSE1:crash_service.cc(145)] window handle is 0002015E
|
Skype.exe | [1360:2160:0530/211645.194:VERBOSE1:crash_service.cc(300)] pipe name is \\.\pipe\skype-preview Crash Service
dumps at C:\Users\admin\AppData\Local\Temp\skype-preview Crashes
|
Skype.exe | [1360:2160:0530/211645.194:VERBOSE1:crash_service.cc(304)] checkpoint is C:\Users\admin\AppData\Local\Temp\skype-preview Crashes\crash_checkpoint.txt
server is https://rink.hockeyapp.net/api/2/apps/a741743329d94bc08826af367733939d/crashes/upload
maximum 128 reports/day
reporter is electron-crash-service
|
Skype.exe | [1360:2160:0530/211645.194:VERBOSE1:crash_service_main.cc(78)] Session start. cmdline is [--reporter-url=https://rink.hockeyapp.net/api/2/apps/a741743329d94bc08826af367733939d/crashes/upload --application-name=skype-preview "--crashes-directory=C:\Users\admin\AppData\Local\Temp\skype-preview Crashes" --v=1]
|
Skype.exe | [1360:2160:0530/211645.194:VERBOSE1:crash_service_main.cc(94)] Ready to process crash requests
|
Skype.exe | [1360:1836:0530/211653.827:VERBOSE1:crash_service.cc(333)] client start. pid = 3764
|
Skype.exe | [2816:2696:0530/211654.155:ERROR:crash_service.cc(311)] could not start dumper
|
Skype.exe | [2816:2696:0530/211654.155:VERBOSE1:crash_service_main.cc(78)] Session start. cmdline is [--reporter-url=https://rink.hockeyapp.net/api/2/apps/a741743329d94bc08826af367733939d/crashes/upload --application-name=skype-preview "--crashes-directory=C:\Users\admin\AppData\Local\Temp\skype-preview Crashes" --v=1]
|
Skype.exe | [2816:2696:0530/211654.155:VERBOSE1:crash_service.cc(300)] pipe name is \\.\pipe\skype-preview Crash Service
dumps at C:\Users\admin\AppData\Local\Temp\skype-preview Crashes
|