| File name: | DLCBoot.exe |
| Full analysis: | https://app.any.run/tasks/38012ed1-3713-45ee-a883-53768880c509 |
| Verdict: | Malicious activity |
| Analysis date: | March 09, 2024, 13:36:07 |
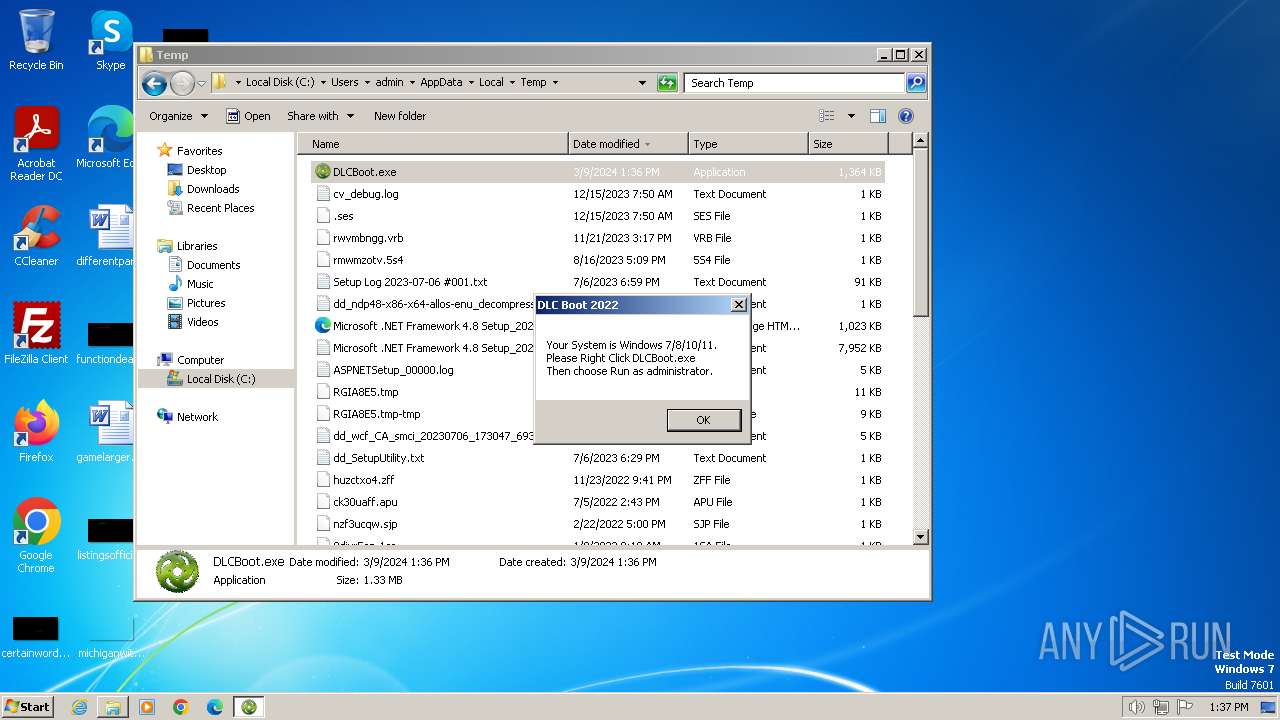
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 481B0102785D5B3EE4C9148963924A70 |
| SHA1: | C7DBA96869D0D7B74FB631FDC9356293A4FA63F9 |
| SHA256: | 9B0921C7EC2172A49E906C5302EAC7D207226ADF3FFCF9616466776CF86D9E1A |
| SSDEEP: | 49152:5DuZwb28dKYZYFGE9JlGMMrxkrkn2fuktkqMSbWaZnPLGejw2LqUGuUTHZHAqIfG:5DuZwNeoOUjDtARwmHnyeQxkuukuuou/ |
MALICIOUS
Drops the executable file immediately after the start
- rundll32.exe (PID: 3864)
- DLCBoot.exe (PID: 2772)
Creates a writable file in the system directory
- DLCBoot.exe (PID: 2772)
Registers / Runs the DLL via REGSVR32.EXE
- DLCBoot.exe (PID: 2772)
SUSPICIOUS
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 1544)
- regsvr32.exe (PID: 1792)
Process drops legitimate windows executable
- DLCBoot.exe (PID: 2772)
Executable content was dropped or overwritten
- DLCBoot.exe (PID: 2772)
Reads the Internet Settings
- DLCBoot.exe (PID: 2772)
INFO
Manual execution by a user
- DLCBoot.exe (PID: 2592)
- explorer.exe (PID: 3916)
- DLCBoot.exe (PID: 2772)
Reads the computer name
- DLCBoot.exe (PID: 2592)
- DLCBoot.exe (PID: 2772)
Checks supported languages
- DLCBoot.exe (PID: 2592)
- DLCBoot.exe (PID: 2772)
Reads the machine GUID from the registry
- DLCBoot.exe (PID: 2592)
- DLCBoot.exe (PID: 2772)
Create files in a temporary directory
- DLCBoot.exe (PID: 2772)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .ax | | | DirectShow filter (45.1) |
|---|---|---|
| .exe | | | Win32 Executable Microsoft Visual Basic 6 (18.3) |
| .exe | | | Win32 Executable MS Visual C++ (generic) (6.9) |
| .dll | | | Win32 Dynamic Link Library (generic) (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:06:28 01:20:56+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 1110016 |
| InitializedDataSize: | 294912 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2018 |
| OSVersion: | 4 |
| ImageVersion: | 4.1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.1.0.0 |
| ProductVersionNumber: | 4.1.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | Boot Any Where |
| CompanyName: | DLC Corporation |
| FileDescription: | DLC Boot 2022 |
| LegalCopyright: | Tran Duy Linh |
| ProductName: | DLC Boot 2022 |
| FileVersion: | 4.01 |
| ProductVersion: | 4.01 |
| InternalName: | DLCBoot |
| OriginalFileName: | DLCBoot.exe |
Total processes
47
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1544 | regsvr32 /s C:\Windows\System32\msinet.ocx | C:\Windows\System32\regsvr32.exe | — | DLCBoot.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1792 | regsvr32 /s C:\Windows\System32\comdlg32.ocx | C:\Windows\System32\regsvr32.exe | — | DLCBoot.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2592 | "C:\Users\admin\AppData\Local\Temp\DLCBoot.exe" | C:\Users\admin\AppData\Local\Temp\DLCBoot.exe | — | explorer.exe | |||||||||||
User: admin Company: DLC Corporation Integrity Level: MEDIUM Description: DLC Boot 2022 Exit code: 0 Version: 4.01 Modules
| |||||||||||||||
| 2772 | "C:\Users\admin\AppData\Local\Temp\DLCBoot.exe" | C:\Users\admin\AppData\Local\Temp\DLCBoot.exe | explorer.exe | ||||||||||||
User: admin Company: DLC Corporation Integrity Level: HIGH Description: DLC Boot 2022 Exit code: 0 Version: 4.01 Modules
| |||||||||||||||
| 3864 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL "C:\Users\admin\AppData\Local\Temp\DLCBoot.exe.ax" | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3916 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
562
Read events
540
Write events
6
Delete events
16
Modification events
| (PID) Process: | (1792) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{F9043C85-F6F2-101A-A3C9-08002B2F49FB} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1792) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{F9043C85-F6F2-101A-A3C9-08002B2F49FB}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (1792) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{7629CFA2-3FE5-101B-A3C9-08002B2F49FB} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1792) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{7629CFA2-3FE5-101B-A3C9-08002B2F49FB}\InprocServer32 |
| Operation: | delete value | Name: | ThreadingModel |
Value: | |||
| (PID) Process: | (1792) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{7629CFA4-3FE5-101B-A3C9-08002B2F49FB} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1792) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{7629CFA4-3FE5-101B-A3C9-08002B2F49FB}\InprocServer32 |
| Operation: | delete value | Name: | ThreadingModel |
Value: | |||
| (PID) Process: | (1792) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{3C4F3BE5-47EB-101B-A3C9-08002B2F49FB} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1792) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{3C4F3BE5-47EB-101B-A3C9-08002B2F49FB}\InprocServer32 |
| Operation: | delete value | Name: | ThreadingModel |
Value: | |||
| (PID) Process: | (1792) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{3C4F3BE3-47EB-101B-A3C9-08002B2F49FB} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1792) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{3C4F3BE3-47EB-101B-A3C9-08002B2F49FB}\InprocServer32 |
| Operation: | delete value | Name: | ThreadingModel |
Value: | |||
Executable files
2
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2772 | DLCBoot.exe | C:\Windows\System32\comdlg32.ocx | executable | |
MD5:AB412429F1E5FB9708A8CDEA07479099 | SHA256:E32D8BBE8E6985726742B496520FA47827F3B428648FA1BC34ECFFDD9BDAC240 | |||
| 2772 | DLCBoot.exe | C:\Windows\System32\msinet.ocx | executable | |
MD5:7BEC181A21753498B6BD001C42A42722 | SHA256:73DA54B69911BDD08EA8BBBD508F815EF7CFA59C4684D75C1C602252EC88EE31 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |