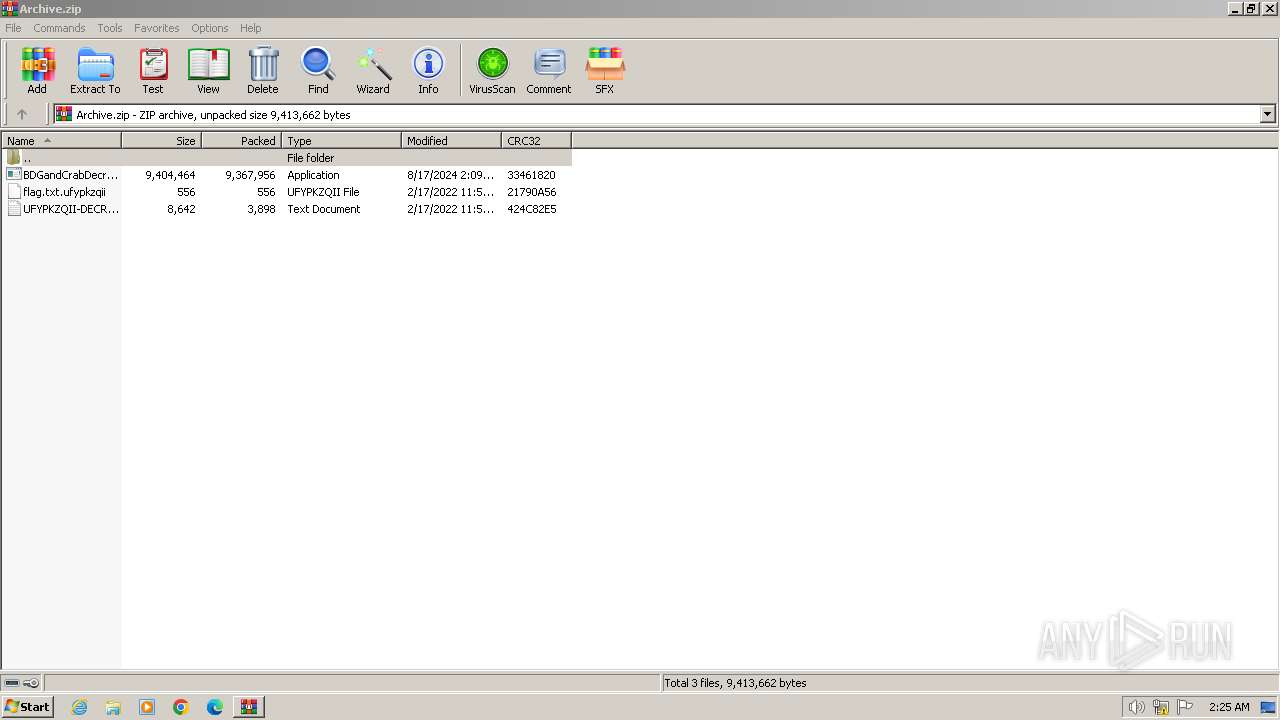
| File name: | Archive.zip |
| Full analysis: | https://app.any.run/tasks/fcea4971-a386-4cae-82b9-2632967c380c |
| Verdict: | Malicious activity |
| Threats: | GandCrab is probably one of the most famous Ransomware. A Ransomware is a malware that asks the victim to pay money in order to restore access to encrypted files. If the user does not cooperate the files are forever lost. |
| Analysis date: | August 17, 2024, 01:25:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
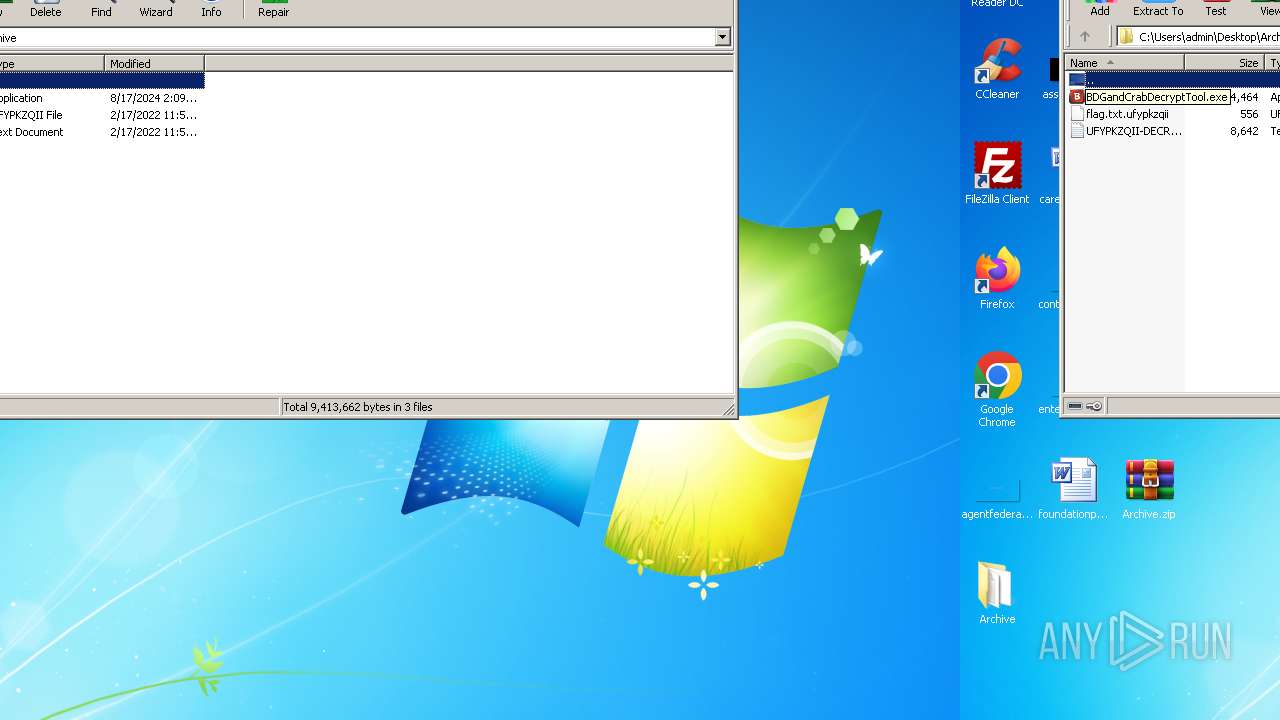
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 569FD4ED3BCC26490A7CAE8EAE0C2E19 |
| SHA1: | 3407538423DF95AEBDEA03C76C3F1EF4341F4AF1 |
| SHA256: | 9B0368B6333F33C733D99DC0C1A9AB8E8C6498F2F5501E8BF5D7616185B013CA |
| SSDEEP: | 98304:LYdUSVBo/a2ZF5oPbC0exXLKA0zgh7UV9q7S9UaodKG9Z0EGmFvLf6yzDoBSdpDg:fFU/8Yi586SB5Sw |
MALICIOUS
Gandcrab ransom note is found
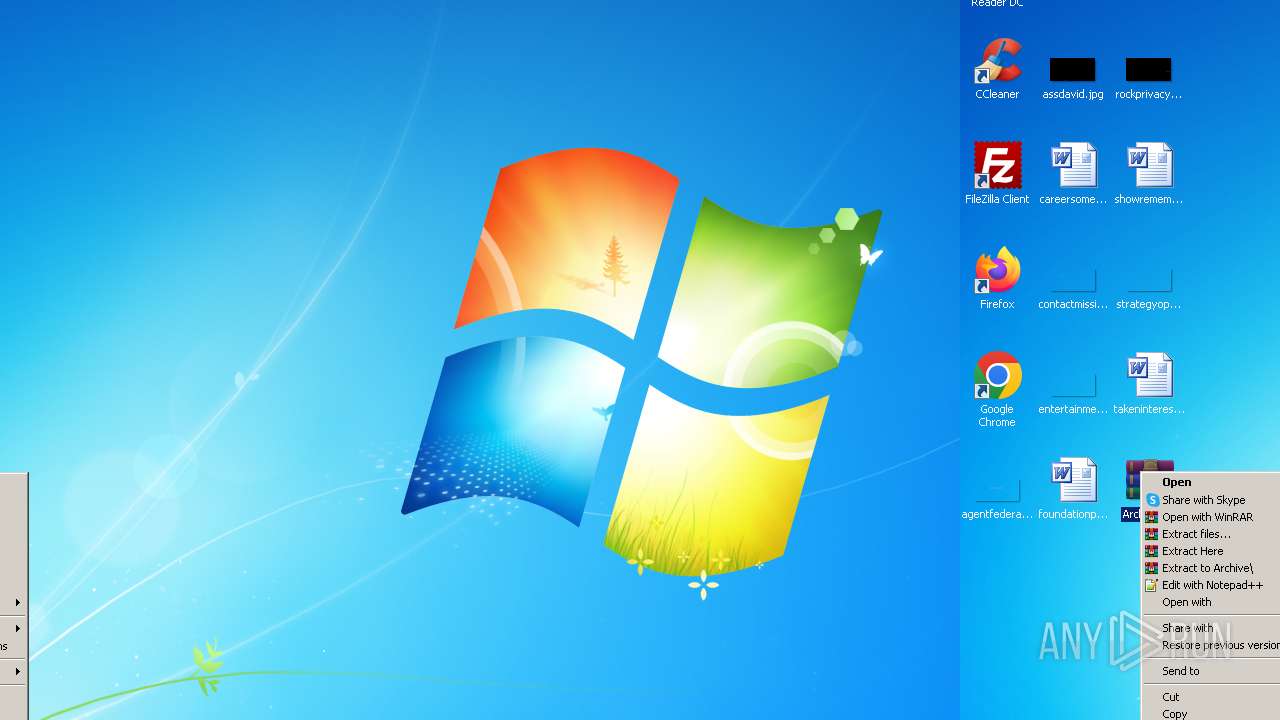
- WinRAR.exe (PID: 3352)
SUSPICIOUS
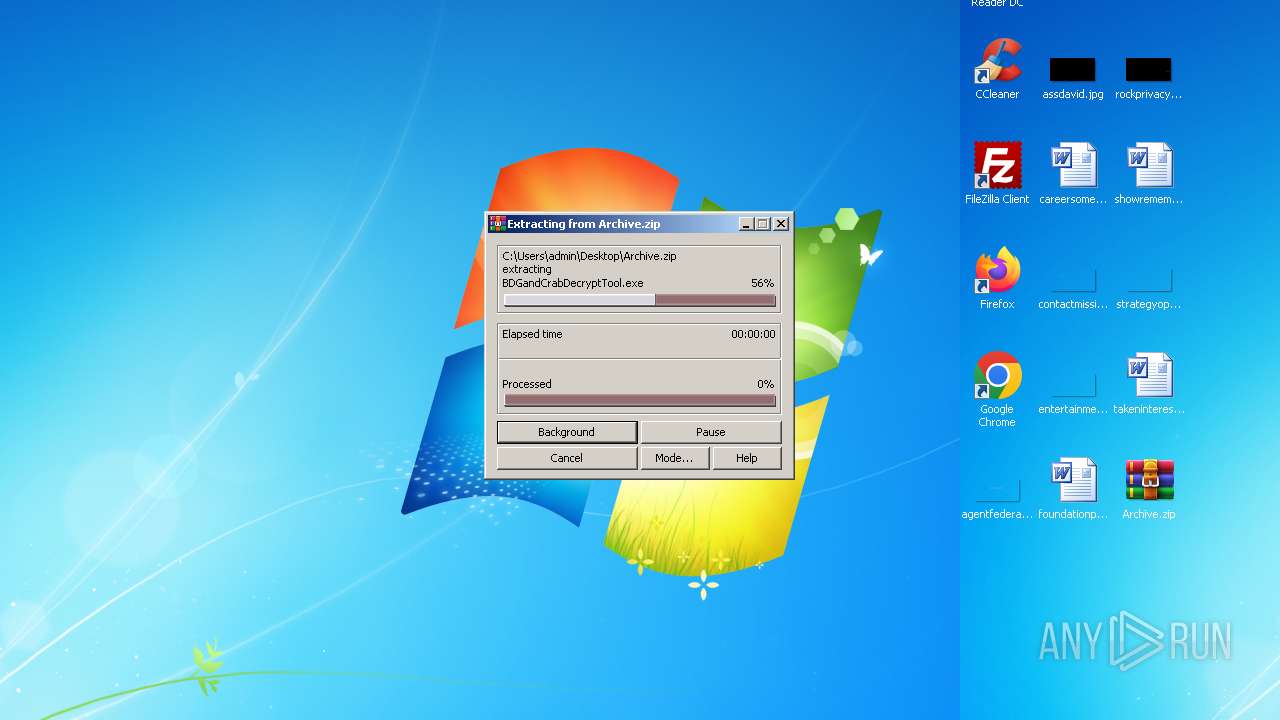
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2396)
- BDGandCrabDecryptTool.exe (PID: 3532)
Executable content was dropped or overwritten
- BDGandCrabDecryptTool.exe (PID: 3532)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3188)
INFO
Manual execution by a user
- WinRAR.exe (PID: 3352)
- wmpnscfg.exe (PID: 3356)
- WinRAR.exe (PID: 3188)
Checks supported languages
- wmpnscfg.exe (PID: 3356)
- BDGandCrabDecryptTool.exe (PID: 3532)
- RemovalToolGUI.exe (PID: 3252)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3352)
Reads the computer name
- wmpnscfg.exe (PID: 3356)
- RemovalToolGUI.exe (PID: 3252)
- BDGandCrabDecryptTool.exe (PID: 3532)
Dropped object may contain TOR URL's
- WinRAR.exe (PID: 3352)
Reads the machine GUID from the registry
- BDGandCrabDecryptTool.exe (PID: 3532)
Create files in a temporary directory
- BDGandCrabDecryptTool.exe (PID: 3532)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:08:17 03:09:48 |
| ZipCRC: | 0x33461820 |
| ZipCompressedSize: | 9367956 |
| ZipUncompressedSize: | 9404464 |
| ZipFileName: | BDGandCrabDecryptTool.exe |
Total processes
47
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2396 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Archive.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3188 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Archive.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3252 | C:\Users\admin\AppData\Local\Temp\BDRansomDecryptor\RemovalToolGUI.exe | C:\Users\admin\AppData\Local\Temp\BDRansomDecryptor\RemovalToolGUI.exe | — | BDGandCrabDecryptTool.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 3352 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\Archive.zip" "?\" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3356 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3532 | "C:\Users\admin\Desktop\Archive\BDGandCrabDecryptTool.exe" | C:\Users\admin\Desktop\Archive\BDGandCrabDecryptTool.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3764 | "C:\Users\admin\Desktop\Archive\BDGandCrabDecryptTool.exe" | C:\Users\admin\Desktop\Archive\BDGandCrabDecryptTool.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
Total events
7 566
Read events
7 512
Write events
54
Delete events
0
Modification events
| (PID) Process: | (2396) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2396) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2396) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2396) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2396) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2396) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2396) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Archive.zip | |||
| (PID) Process: | (2396) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2396) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2396) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
4
Suspicious files
1
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3352 | WinRAR.exe | C:\Users\admin\Desktop\Archive\UFYPKZQII-DECRYPT.txt | text | |
MD5:1FC06B03EDFB25E5FA4D0D0429D2E92F | SHA256:DAE0110C9C5980197E1FE1D7F62D52F76225A03A2AFCE332F54C9CADBA189C51 | |||
| 3532 | BDGandCrabDecryptTool.exe | C:\Users\admin\AppData\Local\Temp\BDRansomDecryptor\GandCrabDecryptLib.dll | executable | |
MD5:831FFA75ECA8D1DE37EBBA9B1F9D6112 | SHA256:91CF87A5A53B5E5C17E34A02ACE04BF9C94F8499F7DEDA7A1396EA9BA0704E5F | |||
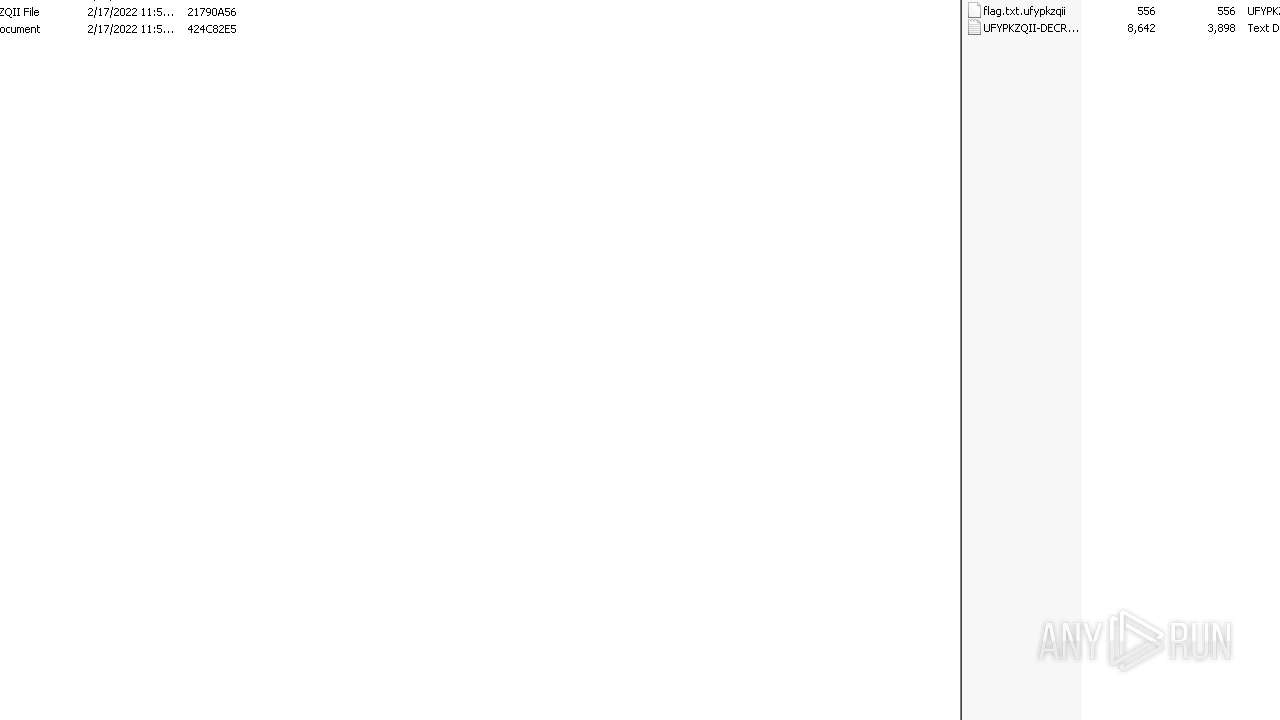
| 3352 | WinRAR.exe | C:\Users\admin\Desktop\Archive\flag.txt.ufypkzqii | binary | |
MD5:6FBBCC7A512D695CAF7EE0A9E030D0E6 | SHA256:DB4C41110970F0B129489F33FFB7F73D13397B8CAE40B97671CAEF6C07F9F347 | |||
| 3532 | BDGandCrabDecryptTool.exe | C:\Users\admin\AppData\Local\Temp\BDRansomDecryptor\sciter.dll | executable | |
MD5:B7DA140294AB3101DCFADEED4961D061 | SHA256:A600ACB45790BA6C5DCF1734149EE2FDA7967611F2E8B72148E29D7D33EEF13F | |||
| 3532 | BDGandCrabDecryptTool.exe | C:\Users\admin\AppData\Local\Temp\BDRansomDecryptor\RemovalToolGUI.exe | executable | |
MD5:CD55C5461755430369FF3526817727BB | SHA256:973441DCEC62D32945598766E696CC222398A67E2A208219886FD007FD799E88 | |||
| 3352 | WinRAR.exe | C:\Users\admin\Desktop\Archive\BDGandCrabDecryptTool.exe | executable | |
MD5:1FE7BE0B3F7A80291949935AD02BE376 | SHA256:616475AC8FBA91F8A3FA4D9F30CFB308759691954737C8DEA1F1DA843B2397B1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
12
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1060 | svchost.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?8f69642324cc87bd | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 239.255.255.250:3702 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1372 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
1372 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1372 | svchost.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
1372 | svchost.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |