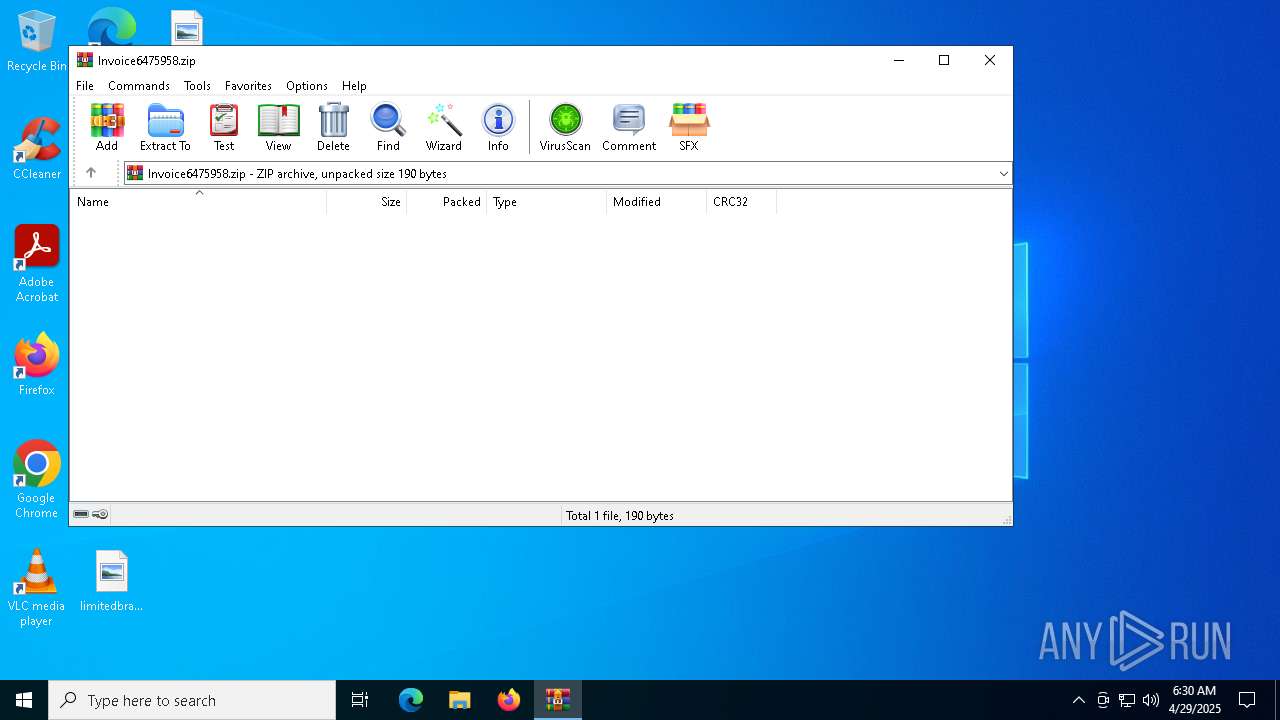
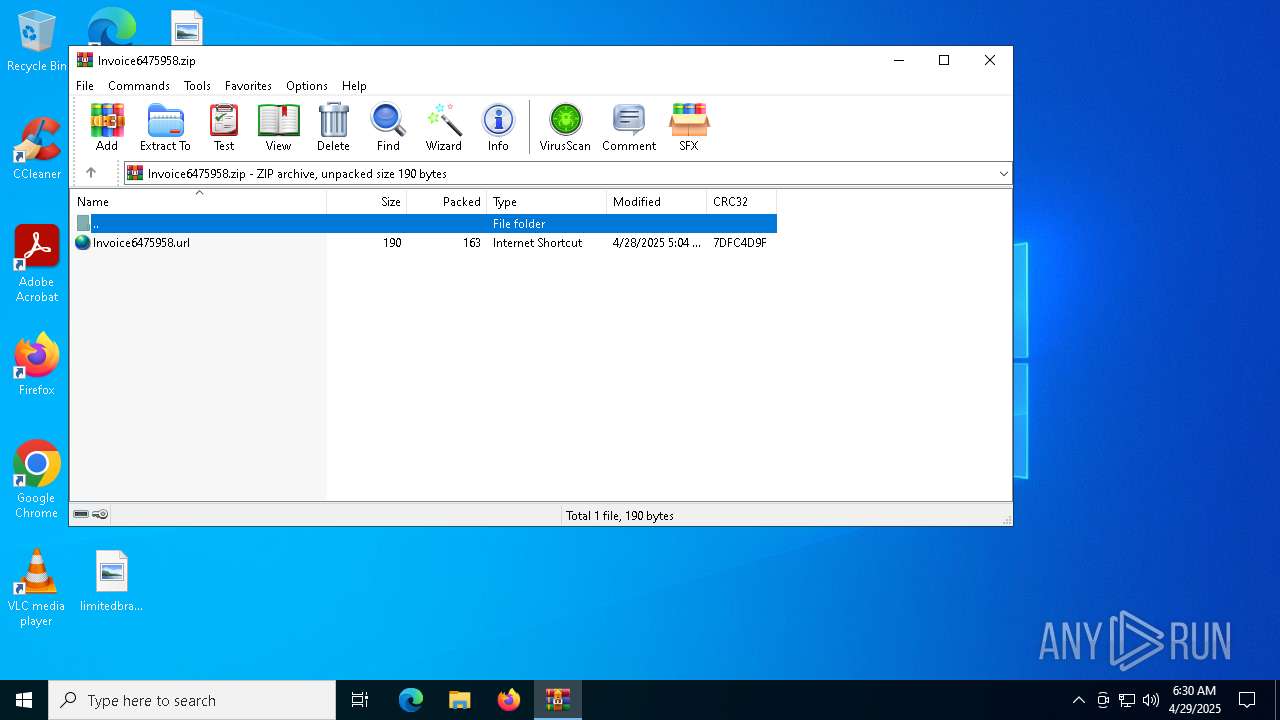
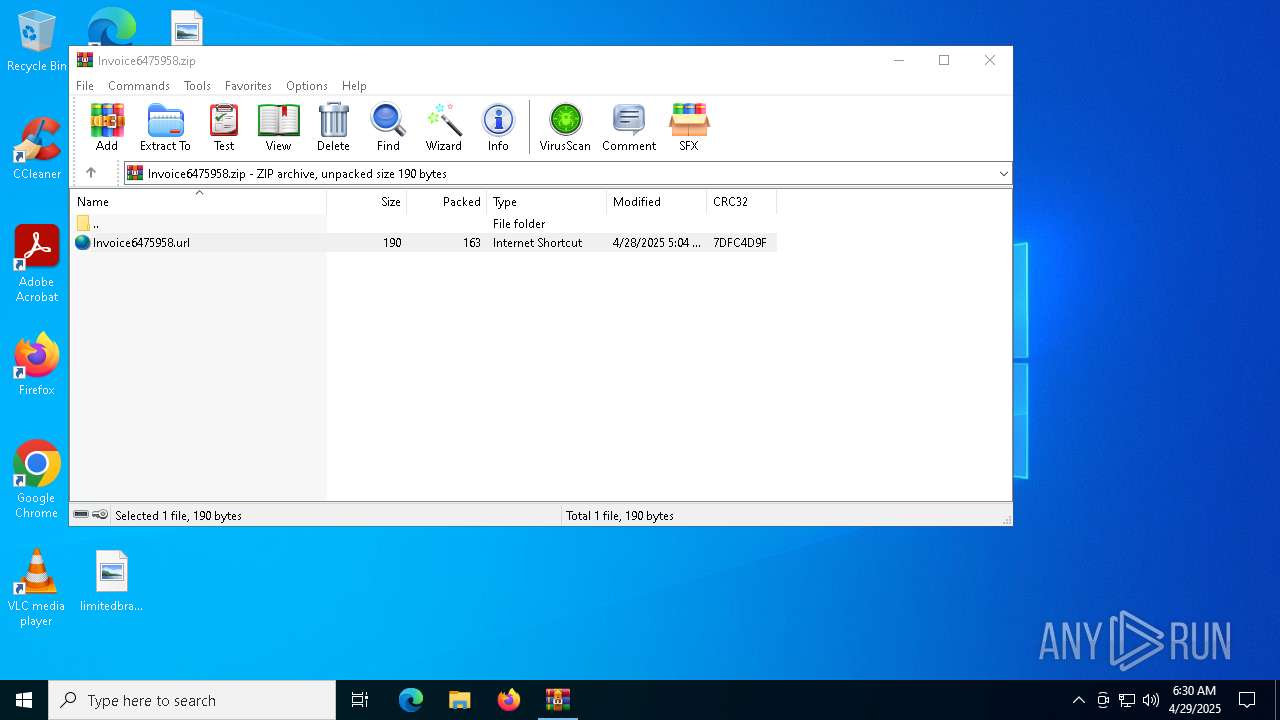
| File name: | Invoice6475958.zip |
| Full analysis: | https://app.any.run/tasks/8e0f8e37-2f4e-43a0-ad32-3ed53f0f9d0a |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 06:29:56 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | FFD6D2BBD411F9068B45249C79322FF6 |
| SHA1: | 1F4F38FB678E641960670A4AF4893F67454C2BD5 |
| SHA256: | 9AEFC80875B5D4A6FED6DEF9042F698BDDE2E0AE4606117AF182330091FF494E |
| SSDEEP: | 6:5j13iAm3dkRa3wWulT0nZRRolwjLItUaadK/TNTtouY+4mWuoiXcCW/5O1QiAm3C:5jljm5gaslKQJhouj7zMx/5vmHtal |
MALICIOUS
PHISHING has been detected (SURICATA)
- svchost.exe (PID: 2196)
SUSPICIOUS
Creates file in the systems drive root
- WinRAR.exe (PID: 5968)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 5968)
Abuses WebDav for code execution
- svchost.exe (PID: 5892)
Uses RUNDLL32.EXE to load library
- svchost.exe (PID: 5892)
SMB connection has been detected (probably for file transfer)
- explorer.exe (PID: 5492)
Uses pipe srvsvc via SMB (transferring data)
- explorer.exe (PID: 5492)
INFO
Local mutex for internet shortcut management
- WinRAR.exe (PID: 5968)
- explorer.exe (PID: 5492)
Checks proxy server information
- explorer.exe (PID: 5492)
- slui.exe (PID: 3888)
Reads the software policy settings
- explorer.exe (PID: 5492)
- slui.exe (PID: 3888)
Reads security settings of Internet Explorer
- explorer.exe (PID: 5492)
- notepad.exe (PID: 6564)
Creates files or folders in the user directory
- explorer.exe (PID: 5492)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:04:28 17:04:10 |
| ZipCRC: | 0x7dfc4d9f |
| ZipCompressedSize: | 163 |
| ZipUncompressedSize: | 190 |
| ZipFileName: | Invoice6475958.url |
Total processes
139
Monitored processes
7
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3888 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5492 | C:\WINDOWS\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5892 | C:\WINDOWS\system32\svchost.exe -k LocalService -p -s WebClient | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5968 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Invoice6475958.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6564 | "C:\WINDOWS\system32\notepad.exe" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7052 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
24 741
Read events
24 626
Write events
106
Delete events
9
Modification events
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconLayouts |
Value: 00000000000000000000000000000000030001000100010010000000000000002C000000000000003A003A007B00360034003500460046003000340030002D0035003000380031002D0031003000310042002D0039004600300038002D003000300041004100300030003200460039003500340045007D003E002000200000001000000000000000430043006C00650061006E00650072002E006C006E006B003E0020007C0000001500000000000000410064006F006200650020004100630072006F006200610074002E006C006E006B003E0020007C0000000F00000000000000460069007200650066006F0078002E006C006E006B003E0020007C000000150000000000000047006F006F0067006C00650020004300680072006F006D0065002E006C006E006B003E0020007C000000180000000000000056004C00430020006D006500640069006100200070006C0061007900650072002E006C006E006B003E0020007C00000016000000000000004D006900630072006F0073006F0066007400200045006400670065002E006C006E006B003E0020007C0000000D0000000000000053006B007900700065002E006C006E006B003E0020007C0000001200000000000000630061007200650065007200730074006F0070002E0070006E0067003E00200020000000160000000000000063006F006E00740069006E007500650062006F00730074006F006E002E007200740066003E002000200000000E000000000000006B00690074007300610074002E0070006E0067003E0020002000000015000000000000006C0069006D0069007400650064006200720061006E00640073002E0070006E0067003E0020002000000011000000000000006D00620077006100740063006800650073002E006A00700067003E0020002000000013000000000000006F007000740069006F006E0073006A006100760061002E007200740066003E00200020000000140000000000000077006900640065006300610072006F006C0069006E0061002E007200740066003E00200020000000160000000000000049006E0076006F0069006300650036003400370035003900350038002E007A00690070003E00200020000000010000000000000002000100000000000000000001000000000000000200010000000000000000001100000006000000010000001000000000000000000000000000000000000000803F0000004008000000803F0000404009000000803F000080400A000000803F0000A0400B0000000040000000000C00000000400000803F0D0000000040000000400E00000000000000803F0100000000000000004002000000000000004040030000000000000080400400000000000000A04005000000803F0000000006000000803F0000803F070000000040000040400F00 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconNameVersion |
Value: 1 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: EA71106800000000 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:00000000000402A2 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456BFA0DB55E4278845B426357D5B5F97B3 | |||
| (PID) Process: | (5968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Invoice6475958.zip | |||
| (PID) Process: | (5968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
0
Suspicious files
5
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5492 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
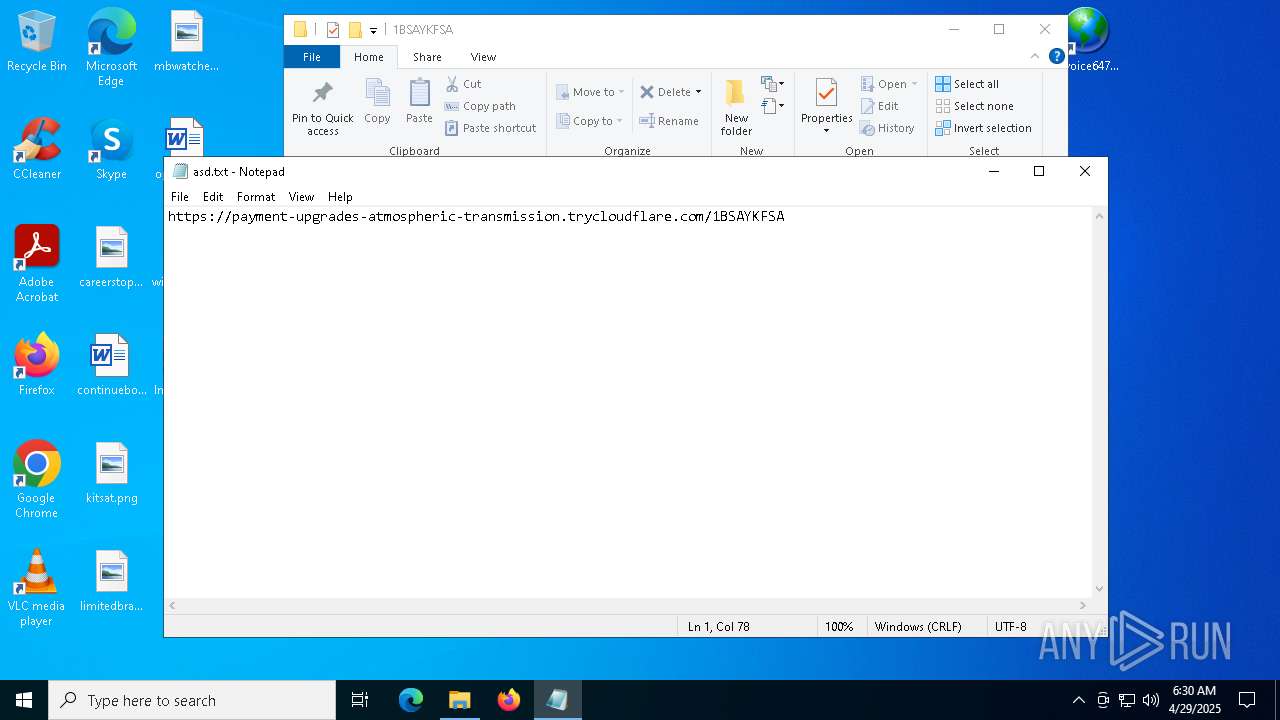
| 6564 | notepad.exe | C:\Users\admin\Documents\asd.txt | text | |
MD5:857D367D1747351FD3D4D589E4F815A0 | SHA256:82079D7E14C9C2F0041DC01DABB82C7D31002363E7863742D7E696629DAA3D06 | |||
| 5892 | svchost.exe | C:\Windows\ServiceProfiles\LocalService\AppData\Local\Temp\TfsStore\Tfs_DAV\{2AEED63A-0CC4-437E-B686-951D0924DC5E}.lnk | binary | |
MD5:200FC586A5BF718A3EDFA7F0AF0990BD | SHA256:8551C091AEB4D8615568ACBB32213C4E15AA1881718E4AC2EC39FBE5991F9673 | |||
| 5892 | svchost.exe | C:\Windows\ServiceProfiles\LocalService\AppData\Local\Temp\TfsStore\Tfs_DAV\{5EC261B4-9B12-4E47-BB10-5F7BCE20EB7E}.ini | text | |
MD5:06E8F7E6DDD666DBD323F7D9210F91AE | SHA256:8301E344371B0753D547B429C5FE513908B1C9813144F08549563AC7F4D7DA68 | |||
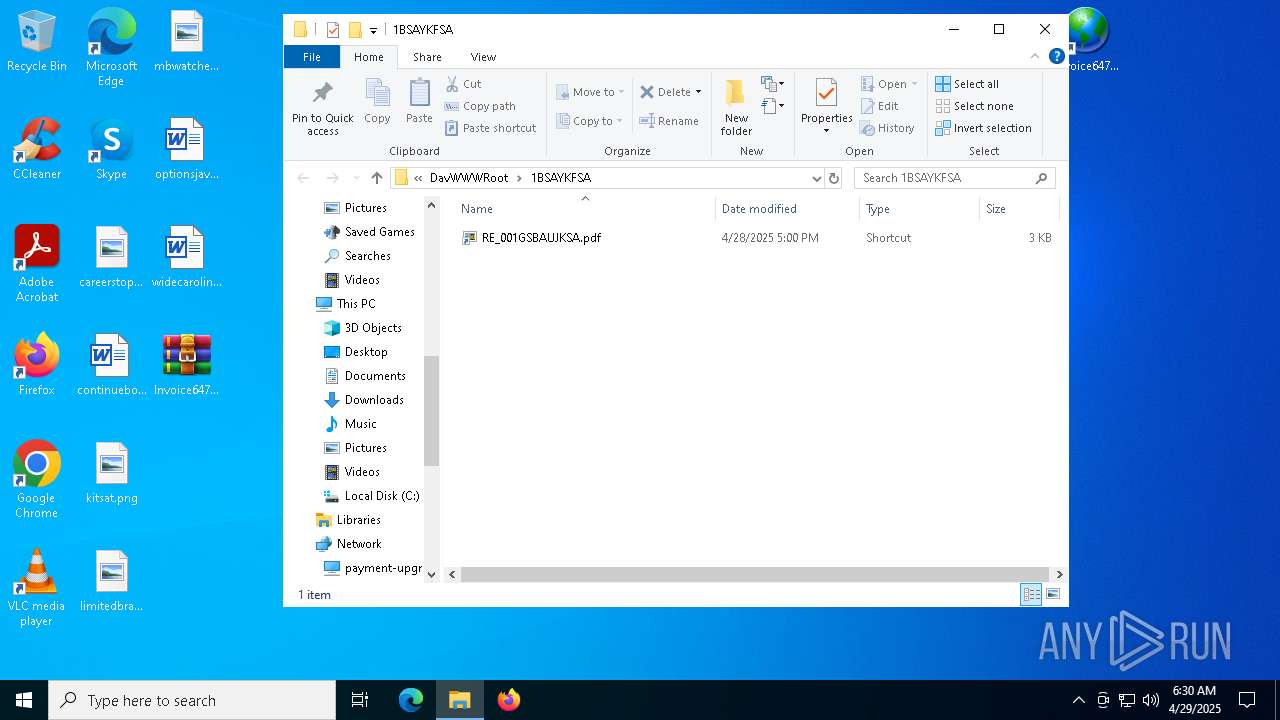
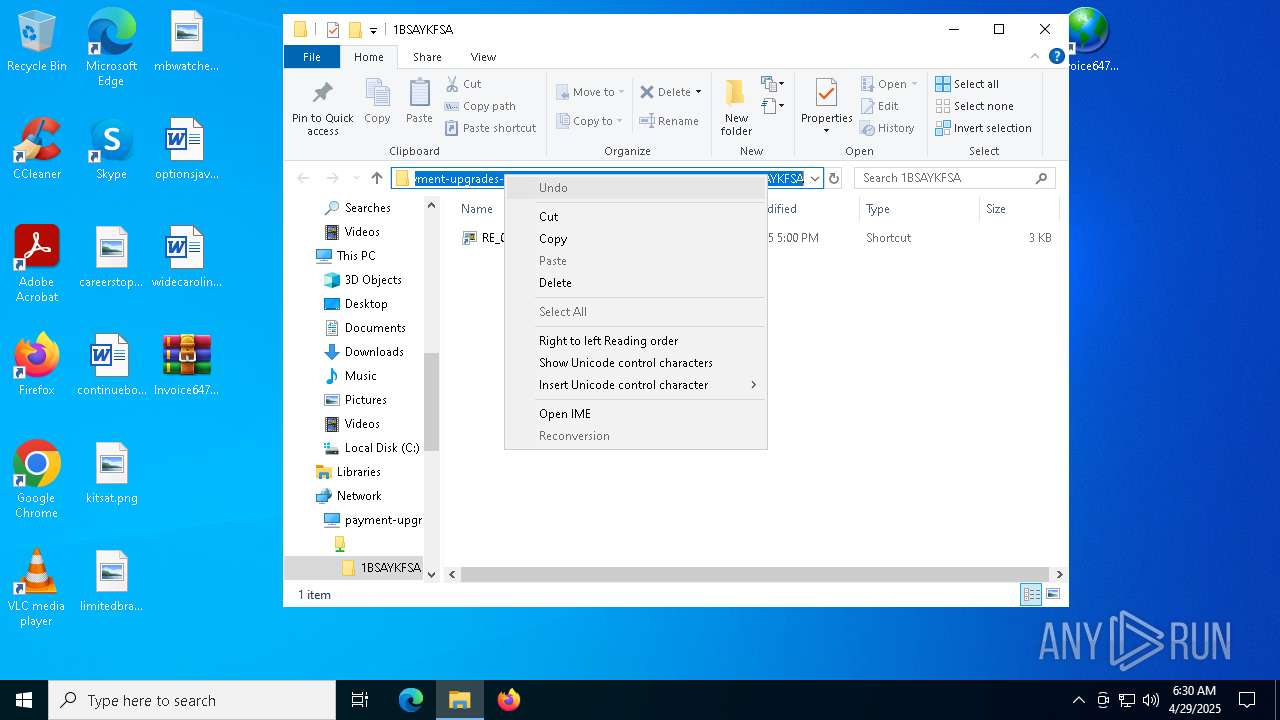
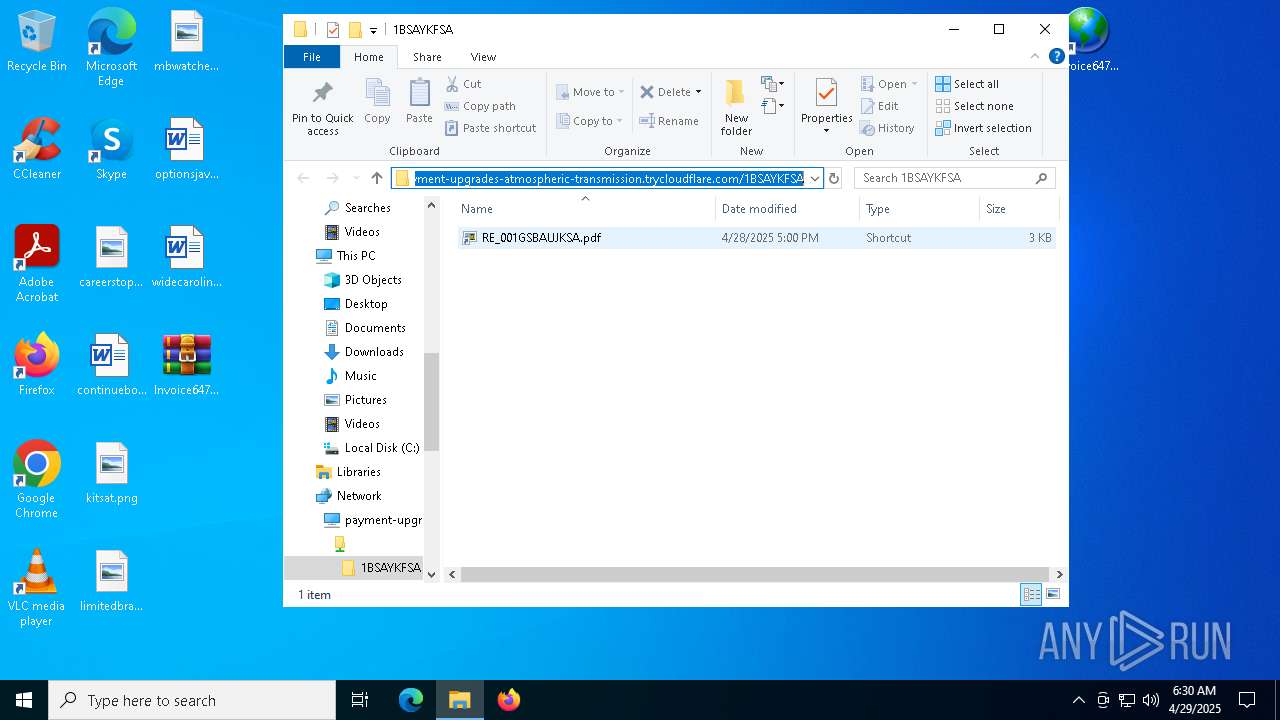
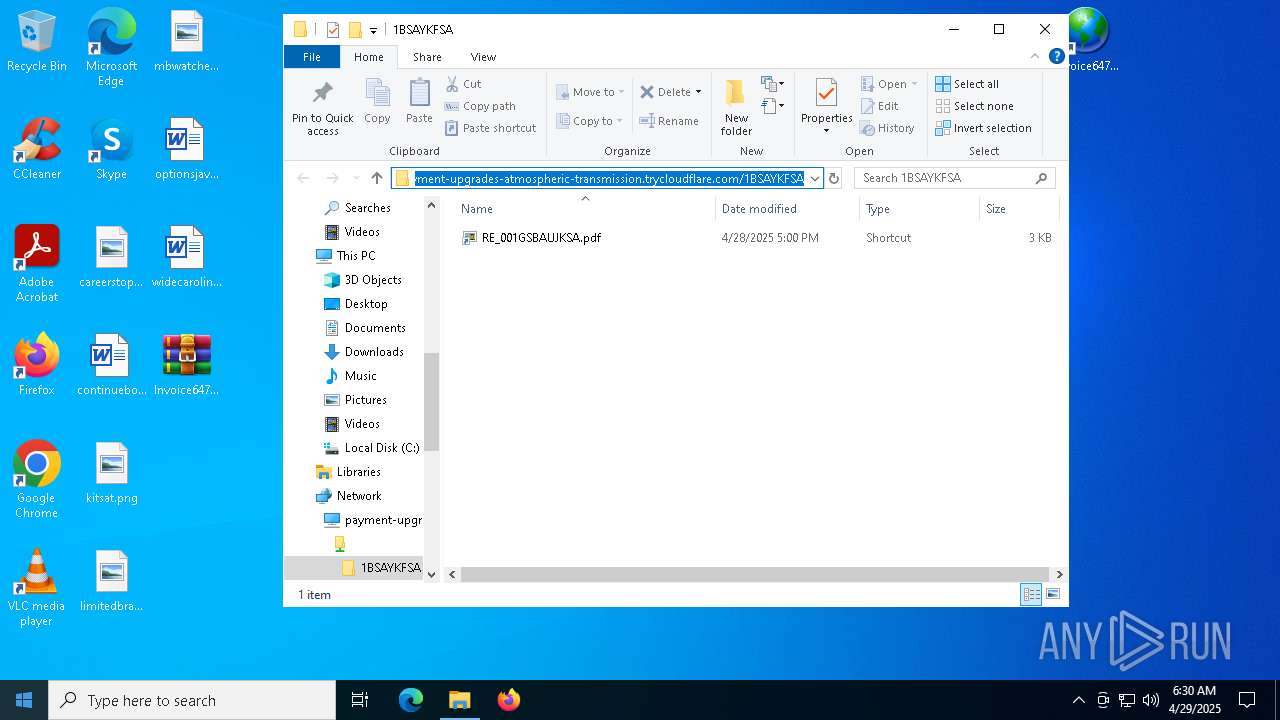
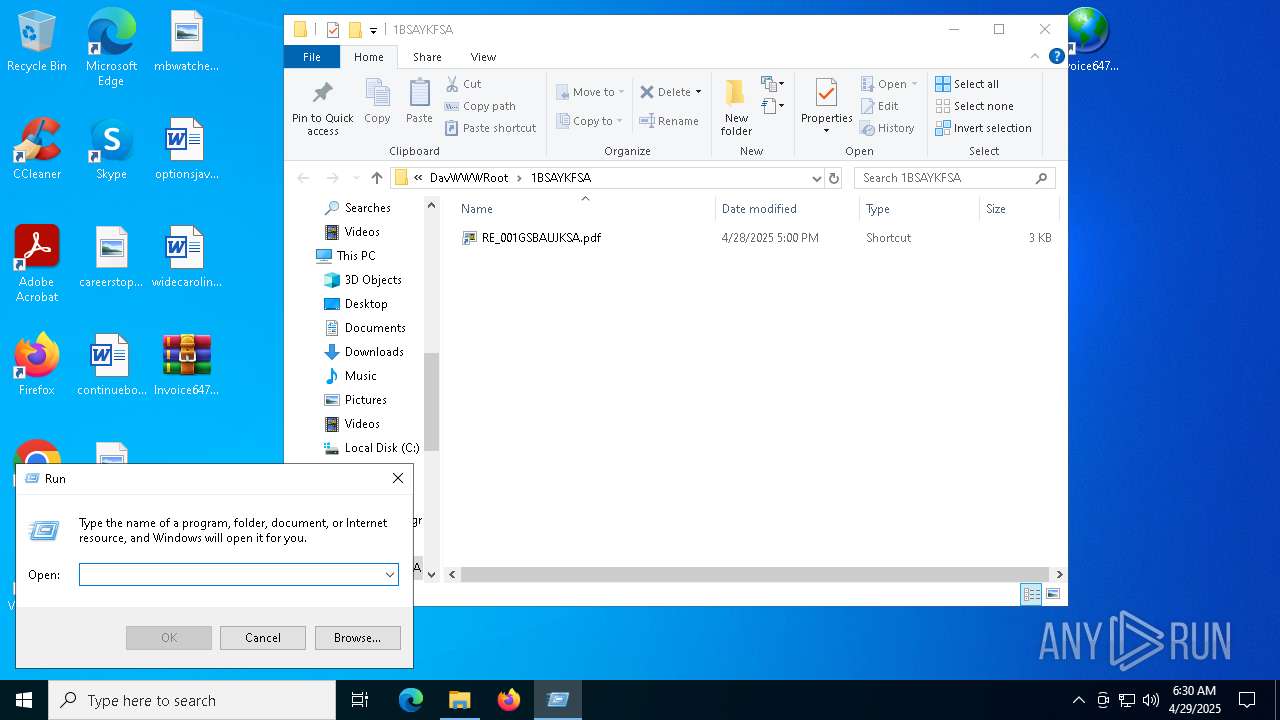
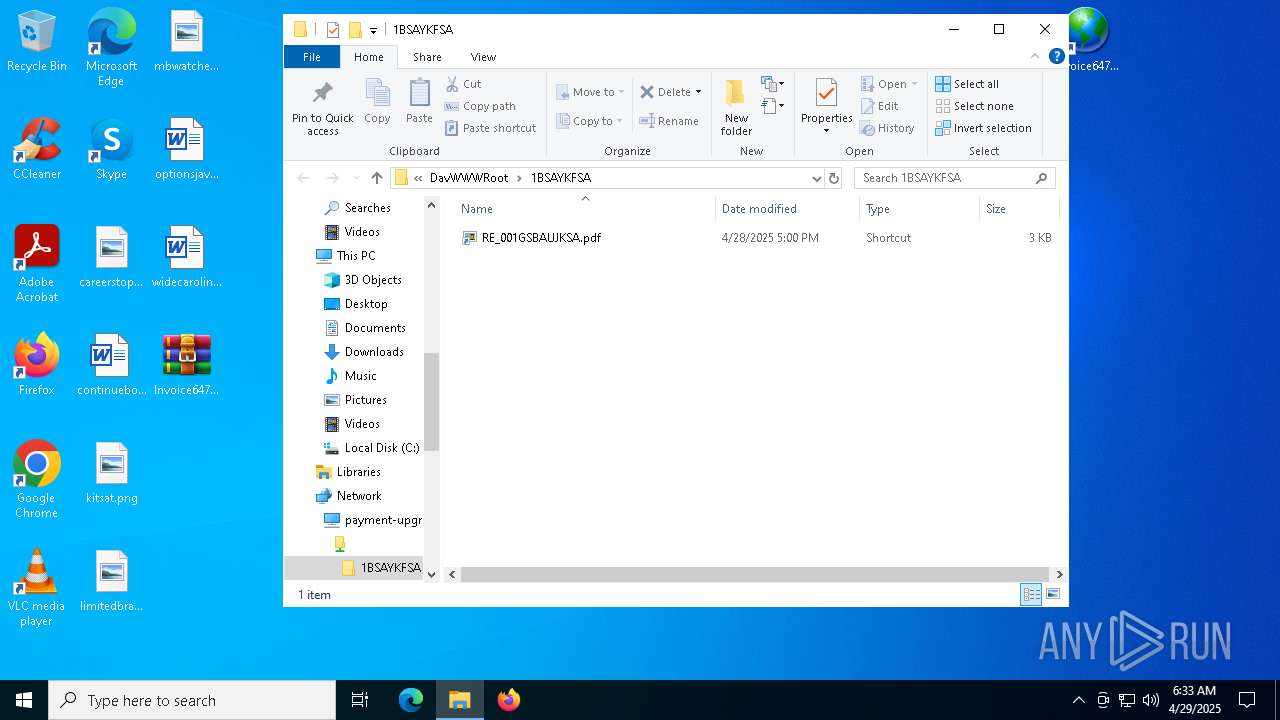
| 5492 | explorer.exe | C:\Users\admin\Desktop\Invoice6475958.url | binary | |
MD5:33E94AF5688A034E206EBA9BC4BF77F7 | SHA256:15C5BAE04F67B042E6694167B03C0285460C086584B5A5C5B9956358A3B3E451 | |||
| 5492 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\f01b4d95cf55d32a.automaticDestinations-ms | binary | |
MD5:2CFFF291F915950311A68067F73D80B4 | SHA256:32B5255E062D90AC9DBDAAF1D9DD815EBEC6CF42EDDF6222AFBFE597E3A33B28 | |||
| 5968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5968.3230\Invoice6475958.url | binary | |
MD5:33E94AF5688A034E206EBA9BC4BF77F7 | SHA256:15C5BAE04F67B042E6694167B03C0285460C086584B5A5C5B9956358A3B3E451 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
54
TCP/UDP connections
77
DNS requests
16
Threats
47
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
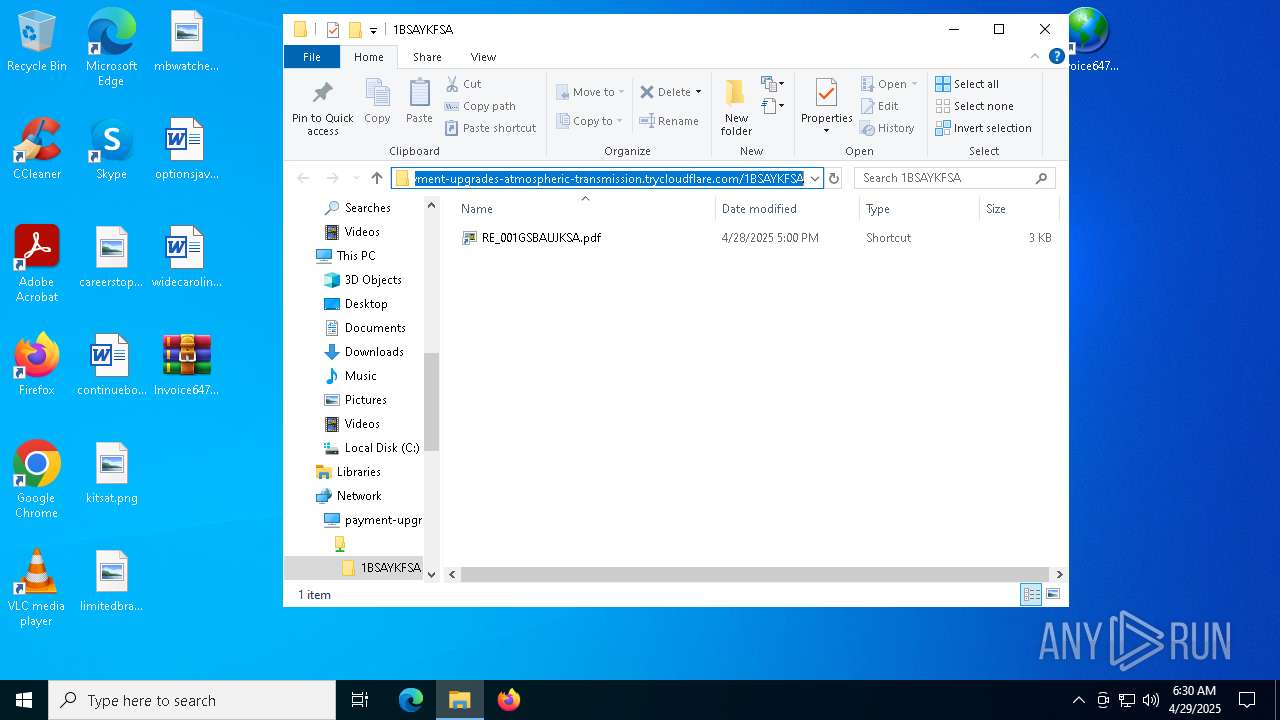
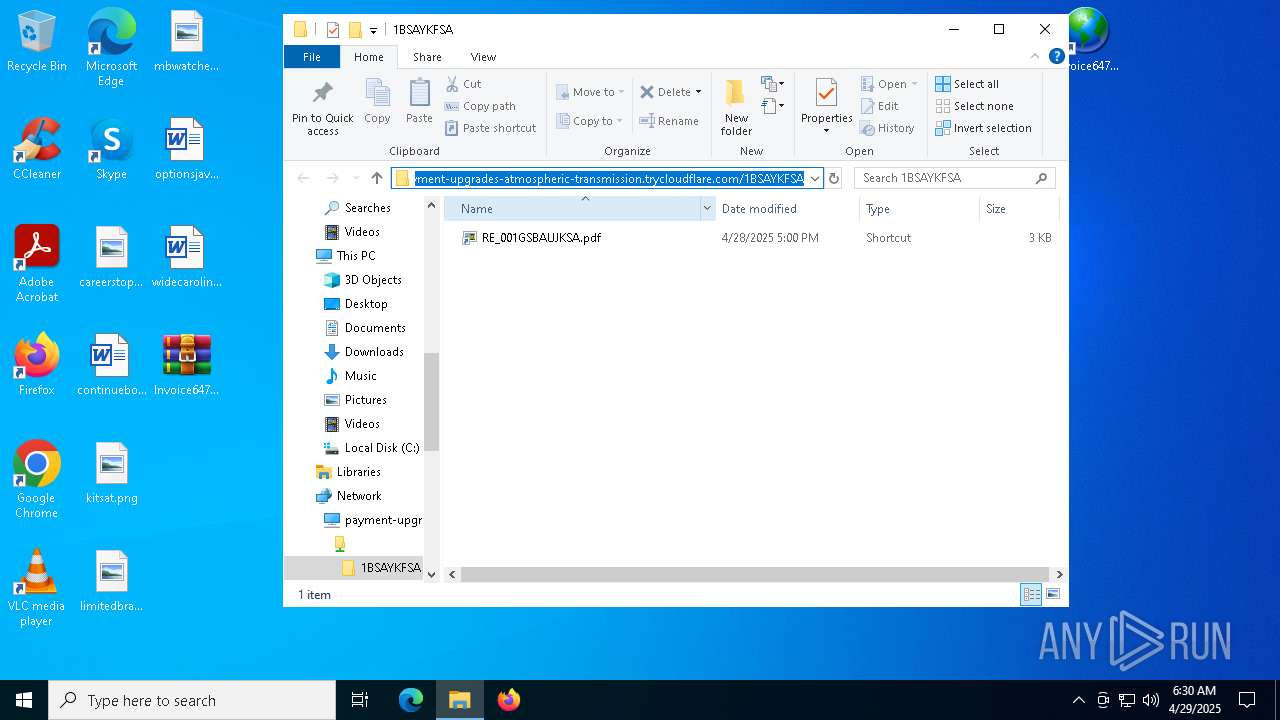
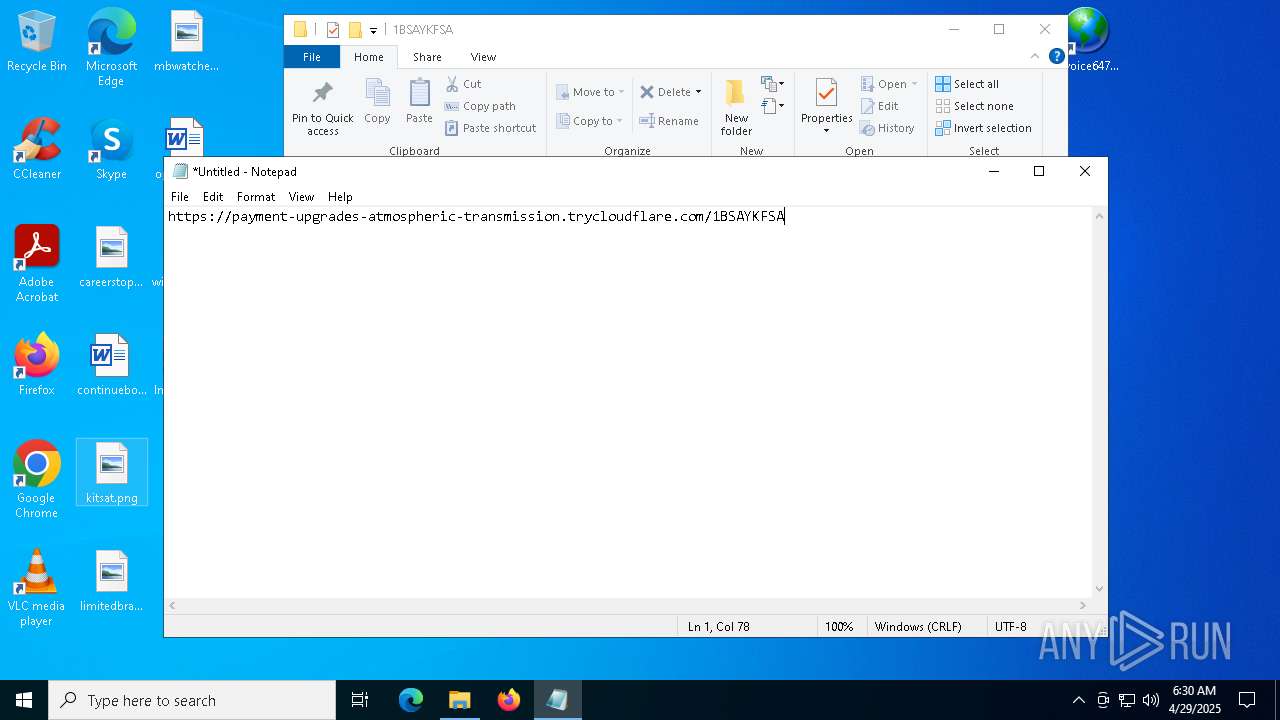
— | — | OPTIONS | 200 | 104.16.231.132:443 | https://payment-upgrades-atmospheric-transmission.trycloudflare.com/ | unknown | — | — | unknown |
— | — | OPTIONS | 200 | 104.16.231.132:443 | https://payment-upgrades-atmospheric-transmission.trycloudflare.com/ | unknown | — | — | unknown |
— | — | POST | 400 | 40.126.31.2:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 40.126.31.73:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 20.190.159.128:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | PROPFIND | 207 | 104.16.231.132:443 | https://payment-upgrades-atmospheric-transmission.trycloudflare.com/ | unknown | xml | 781 b | whitelisted |
— | — | PROPFIND | 207 | 104.16.231.132:443 | https://payment-upgrades-atmospheric-transmission.trycloudflare.com/1BSAYKFSA | unknown | xml | 1.55 Kb | whitelisted |
— | — | PROPFIND | 207 | 104.16.231.132:443 | https://payment-upgrades-atmospheric-transmission.trycloudflare.com/ | unknown | xml | 781 b | whitelisted |
— | — | PROPFIND | 207 | 104.16.231.132:443 | https://payment-upgrades-atmospheric-transmission.trycloudflare.com/desktop.ini | unknown | xml | 844 b | whitelisted |
— | — | POST | 400 | 40.126.31.2:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2112 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5492 | explorer.exe | 104.16.231.132:443 | payment-upgrades-atmospheric-transmission.trycloudflare.com | CLOUDFLARENET | — | whitelisted |
5892 | svchost.exe | 104.16.231.132:443 | payment-upgrades-atmospheric-transmission.trycloudflare.com | CLOUDFLARENET | — | whitelisted |
2240 | SIHClient.exe | 4.175.87.197:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
payment-upgrades-atmospheric-transmission.trycloudflare.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to Commonly Abused Cloudflare Domain (trycloudflare .com) |
2196 | svchost.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Cloudflare Tunnel (TryCloudflare) |
5492 | explorer.exe | Misc activity | ET INFO Observed trycloudflare .com Domain in TLS SNI |
5492 | explorer.exe | Misc activity | ET HUNTING TryCloudFlare Domain in TLS SNI |
2196 | svchost.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Domain was identified as Phishing (payment pattern) |
— | — | Potential Corporate Privacy Violation | POLICY [ANY.RUN] WebDav activity has been detected |
5892 | svchost.exe | Misc activity | ET HUNTING TryCloudFlare Domain in TLS SNI |
5892 | svchost.exe | Misc activity | ET INFO Observed trycloudflare .com Domain in TLS SNI |
5892 | svchost.exe | Misc activity | ET HUNTING TryCloudFlare Domain in TLS SNI |
5892 | svchost.exe | Misc activity | ET INFO Observed trycloudflare .com Domain in TLS SNI |