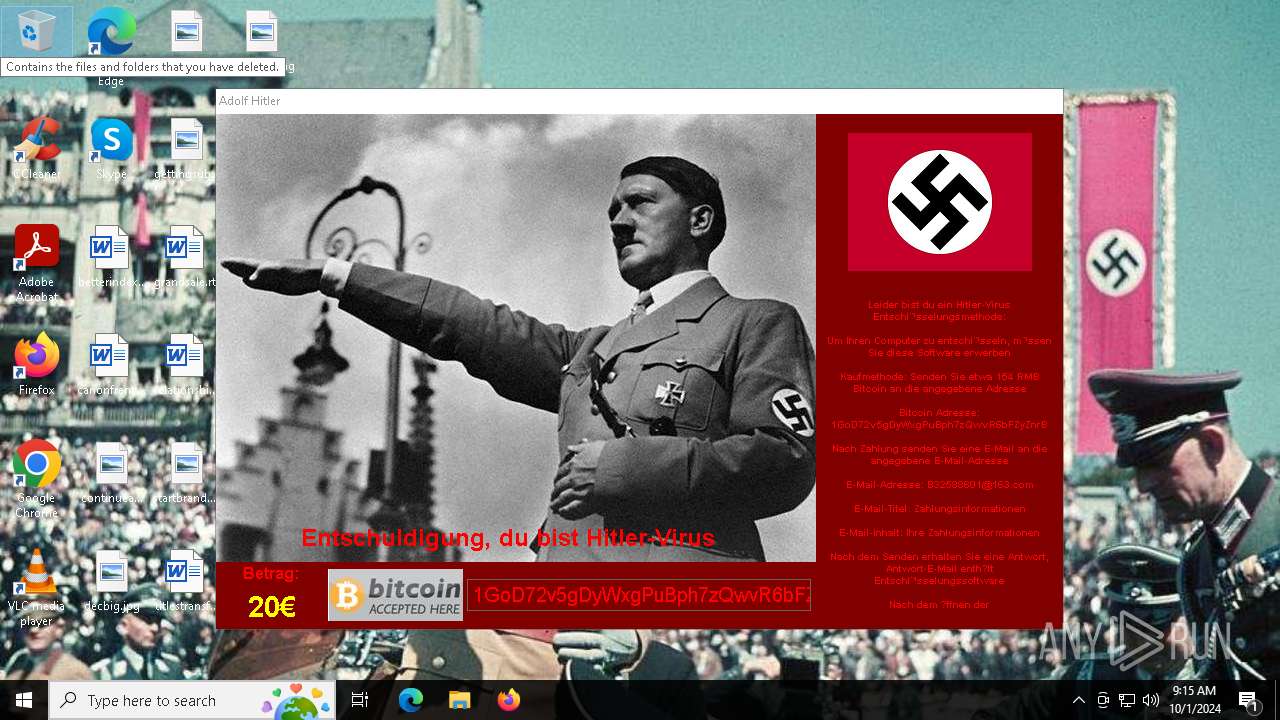
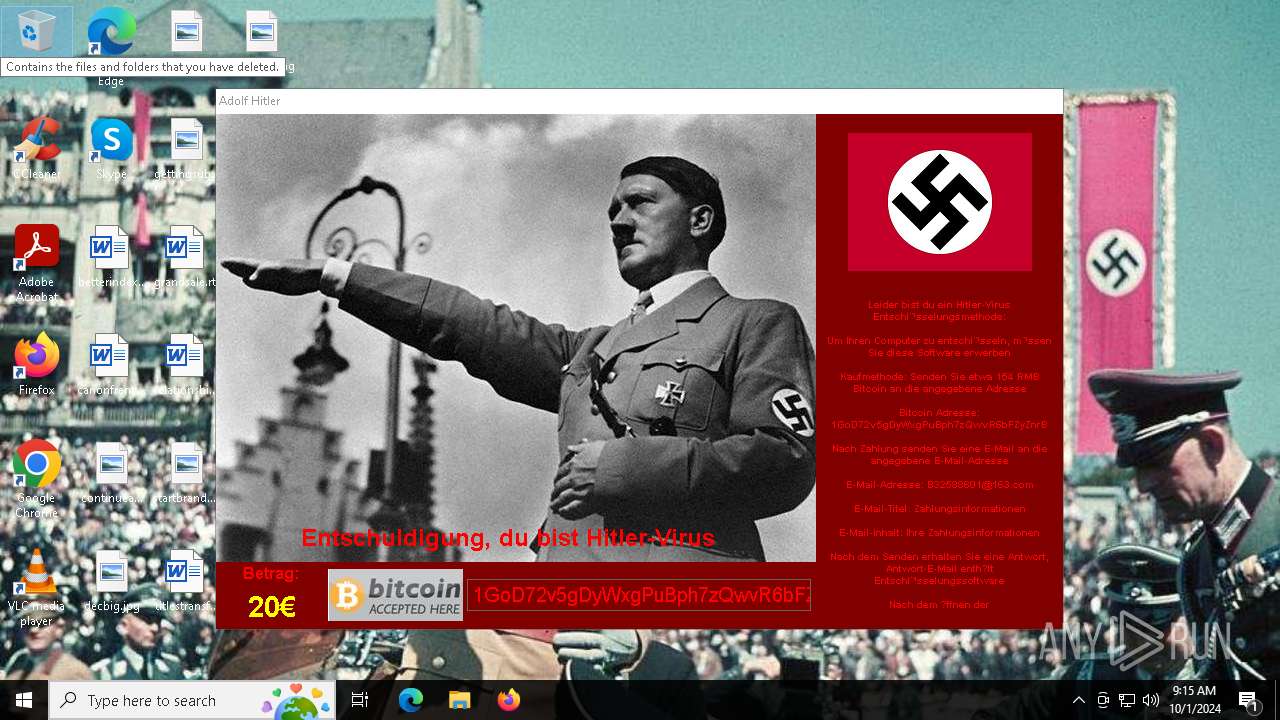
| File name: | Hitler.exe |
| Full analysis: | https://app.any.run/tasks/6764cd4d-5532-4db9-b628-d3fe68f92598 |
| Verdict: | Malicious activity |
| Analysis date: | October 01, 2024, 09:15:26 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | E64DBE09FC1805177D9058A40807E128 |
| SHA1: | FC15F43BE27987315C8BCF61FF392FF8AC3E394C |
| SHA256: | 9AE7D51B7C3E729D9FD0EB7B99811DE3270E7B37931FFF1F136EFEB50D276A4C |
| SSDEEP: | 98304:1KAeO3aJCht7w1vmAGkJLptIBdMLKRaIAx8aRDS8TwSsxQt1bzx4bO+L4dr0QTDh:k0 |
MALICIOUS
UAC/LUA settings modification
- Hitler.exe (PID: 2044)
Changes the autorun value in the registry
- Hitler.exe (PID: 2044)
Deletes shadow copies
- cmd.exe (PID: 3076)
SUSPICIOUS
Creates file in the systems drive root
- Hitler.exe (PID: 2044)
Uses ICACLS.EXE to modify access control lists
- Hitler.exe (PID: 2044)
Reads security settings of Internet Explorer
- Hitler.exe (PID: 2044)
Starts CMD.EXE for commands execution
- Hitler.exe (PID: 2044)
Executes as Windows Service
- VSSVC.exe (PID: 6100)
There is functionality for taking screenshot (YARA)
- Hitler.exe (PID: 2044)
There is functionality for capture public ip (YARA)
- Hitler.exe (PID: 2044)
Checks for external IP
- Hitler.exe (PID: 2044)
Connects to SMTP port
- Hitler.exe (PID: 2044)
INFO
Checks supported languages
- Hitler.exe (PID: 2044)
Create files in a temporary directory
- Hitler.exe (PID: 2044)
Reads the computer name
- Hitler.exe (PID: 2044)
Reads the machine GUID from the registry
- Hitler.exe (PID: 2044)
Checks proxy server information
- Hitler.exe (PID: 2044)
Creates files or folders in the user directory
- Hitler.exe (PID: 2044)
UPX packer has been detected
- Hitler.exe (PID: 2044)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (33.3) |
|---|---|---|
| .exe | | | UPX compressed Win32 Executable (32.6) |
| .scr | | | Windows screen saver (15.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (7.9) |
| .exe | | | Win32 Executable (generic) (5.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2017:11:05 04:11:25+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 3190784 |
| InitializedDataSize: | 335872 |
| UninitializedDataSize: | 1032192 |
| EntryPoint: | 0x407760 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
133
Monitored processes
9
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1884 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | icacls.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2008 | "C:\Users\admin\Desktop\Hitler.exe" | C:\Users\admin\Desktop\Hitler.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2044 | "C:\Users\admin\Desktop\Hitler.exe" | C:\Users\admin\Desktop\Hitler.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 2116 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2132 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2224 | wmic shadowcopy delete | C:\Windows\SysWOW64\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 2147749908 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3076 | cmd /c vssadmin delete shadow /all /quiet & wmic shadowcopy delete & bcdedit /set {default} boostatuspolicy ignoreallfailures & bcdedit /set {default} recoveryenabled no & wbadmin delete catalog -quiet | C:\Windows\SysWOW64\cmd.exe | — | Hitler.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5988 | icacls . /grant Everyone:F /T /C /Q | C:\Windows\SysWOW64\icacls.exe | — | Hitler.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6100 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
22 233
Read events
22 226
Write events
7
Delete events
0
Modification events
| (PID) Process: | (2044) Hitler.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | EnableLUA |
Value: 0 | |||
| (PID) Process: | (2044) Hitler.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Adolf Hitler |
Value: C:\Users\admin\Desktop\Hitler.exe | |||
| (PID) Process: | (2044) Hitler.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2044) Hitler.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2044) Hitler.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2132) ShellExperienceHost.exe | Key: | \REGISTRY\A\{876611b9-7607-26c7-3fbd-c5b19abd613e}\LocalState |
| Operation: | write | Name: | PeekBadges |
Value: 5B005D0000005E1B987CE213DB01 | |||
| (PID) Process: | (2132) ShellExperienceHost.exe | Key: | \REGISTRY\A\{876611b9-7607-26c7-3fbd-c5b19abd613e}\LocalState |
| Operation: | write | Name: | PeekBadges |
Value: 5B005D000000CB91987CE213DB01 | |||
Executable files
2
Suspicious files
2 754
Text files
11
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2044 | Hitler.exe | — | ||
MD5:— | SHA256:— | |||
| 2044 | Hitler.exe | C:\$WinREAgent\Backup\Winre.AdolfHitler | — | |
MD5:— | SHA256:— | |||
| 2044 | Hitler.exe | C:\$WinREAgent\Scratch\update.AdolfHitler | — | |
MD5:— | SHA256:— | |||
| 2044 | Hitler.exe | C:\_Adolf Hitler_.bmp | image | |
MD5:9EA2048780F96D11B4CE6EA76623B94D | SHA256:DEDF660BCC7C477A370F2C0899B7E01F9DC73D1EDF12BE0201F6D9C528B43D95 | |||
| 2044 | Hitler.exe | C:\$Recycle.Bin\S-1-5-18\desktop.AdolfHitler | text | |
MD5:A526B9E7C716B3489D8CC062FBCE4005 | SHA256:E1B9CE9B57957B1A0607A72A057D6B7A9B34EA60F3F8AA8F38A3AF979BD23066 | |||
| 2044 | Hitler.exe | C:\Users\admin\Desktop\_Adolf Hitler_.bmp | image | |
MD5:9EA2048780F96D11B4CE6EA76623B94D | SHA256:DEDF660BCC7C477A370F2C0899B7E01F9DC73D1EDF12BE0201F6D9C528B43D95 | |||
| 2044 | Hitler.exe | C:\Users\admin\Desktop\AdolfHitler | binary | |
MD5:D9364029A39FF14634FF132E2786CB47 | SHA256:C399AF25EAFAF9D89B33C5F0613D00B690BE5C11163DE45AA2F5D5739EFBB05F | |||
| 2044 | Hitler.exe | C:\found.000\file00000004.AdolfHitler | — | |
MD5:— | SHA256:— | |||
| 2044 | Hitler.exe | C:\$WinREAgent\RollbackInfo.AdolfHitler | binary | |
MD5:E3B64352FBB8F371F6F1DF904A8DD7CD | SHA256:7F815E46FE61D2DB386DF1E49994682FAAAF7845ADB69930B08F3DD1CDD741EE | |||
| 2044 | Hitler.exe | C:\$WinREAgent\Backup\location.txt | binary | |
MD5:2768599DB3B497D7E4D12D1CC16CD582 | SHA256:82EFD7CB1CD435C339D32CA677B911C2F29AF732B75B61D325727533C29A560E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
35
DNS requests
11
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7108 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2044 | Hitler.exe | GET | 200 | 103.235.46.96:80 | http://www.baidu.com/ | unknown | — | — | whitelisted |
2044 | Hitler.exe | GET | 200 | 174.35.118.62:80 | http://top.ip138.com/ | unknown | — | — | unknown |
2044 | Hitler.exe | GET | 301 | 138.113.149.152:80 | http://www.ip138.com/ | unknown | — | — | whitelisted |
— | — | GET | 302 | 174.35.118.62:443 | https://www.ip138.com/ | unknown | html | 138 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
7108 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.49.150.241:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
7108 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2044 | Hitler.exe | 103.235.46.96:80 | www.baidu.com | Beijing Baidu Netcom Science and Technology Co., Ltd. | HK | whitelisted |
7108 | svchost.exe | 20.49.150.241:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
2044 | Hitler.exe | 103.129.252.45:25 | smtp.163.com | NETEASE HONG KONG LIMITED | HK | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.baidu.com |
| whitelisted |
smtp.163.com |
| shared |
www.ip138.com |
| whitelisted |
top.ip138.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2044 | Hitler.exe | Generic Protocol Command Decode | SURICATA SMTP no server welcome message |
2 ETPRO signatures available at the full report