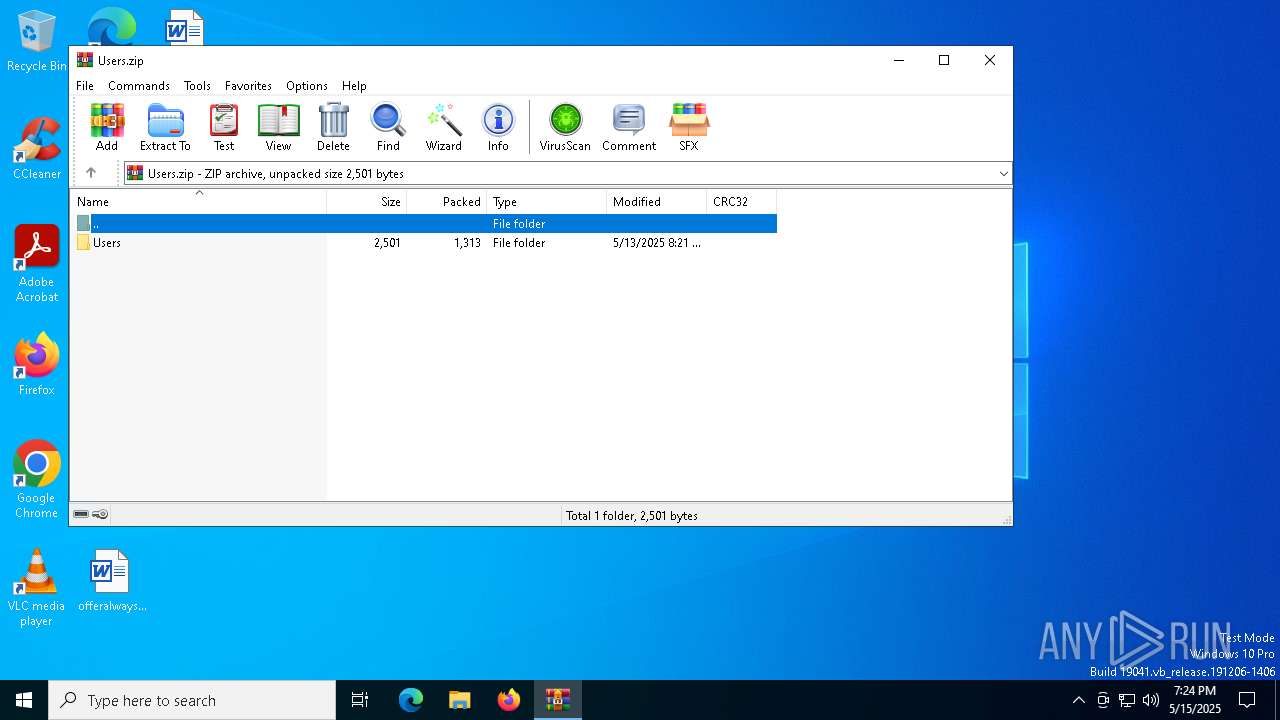
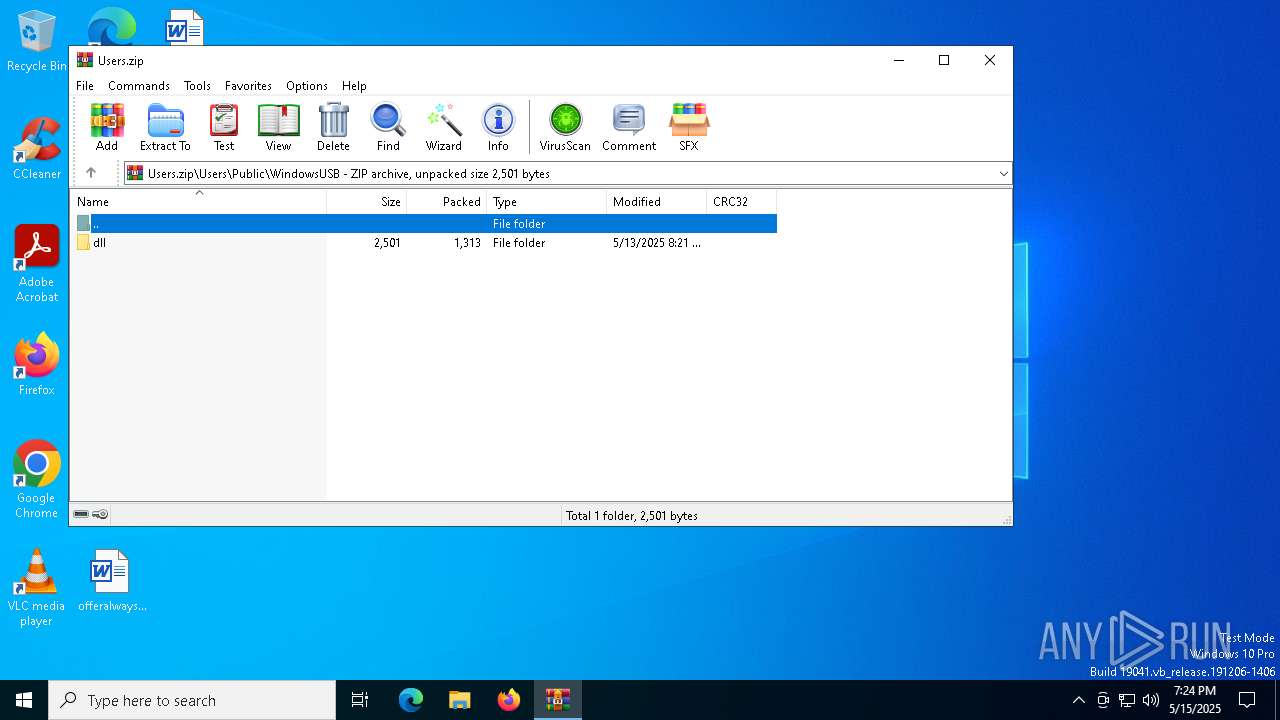
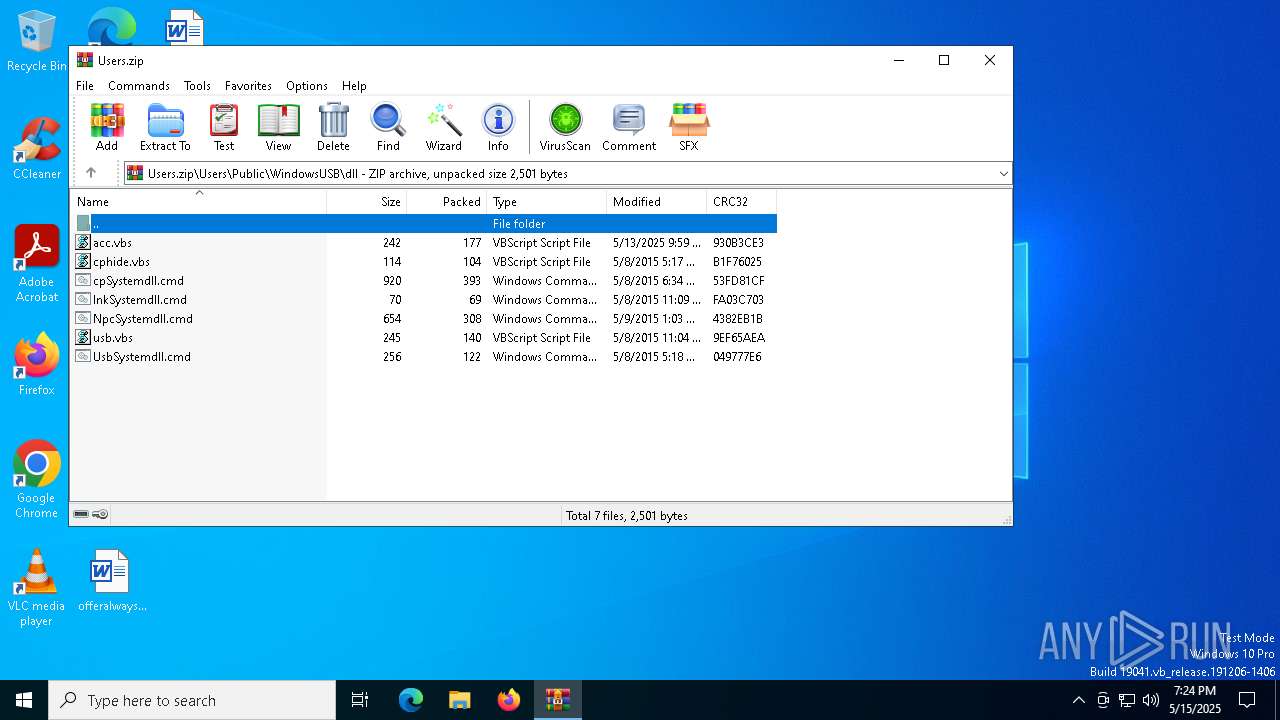
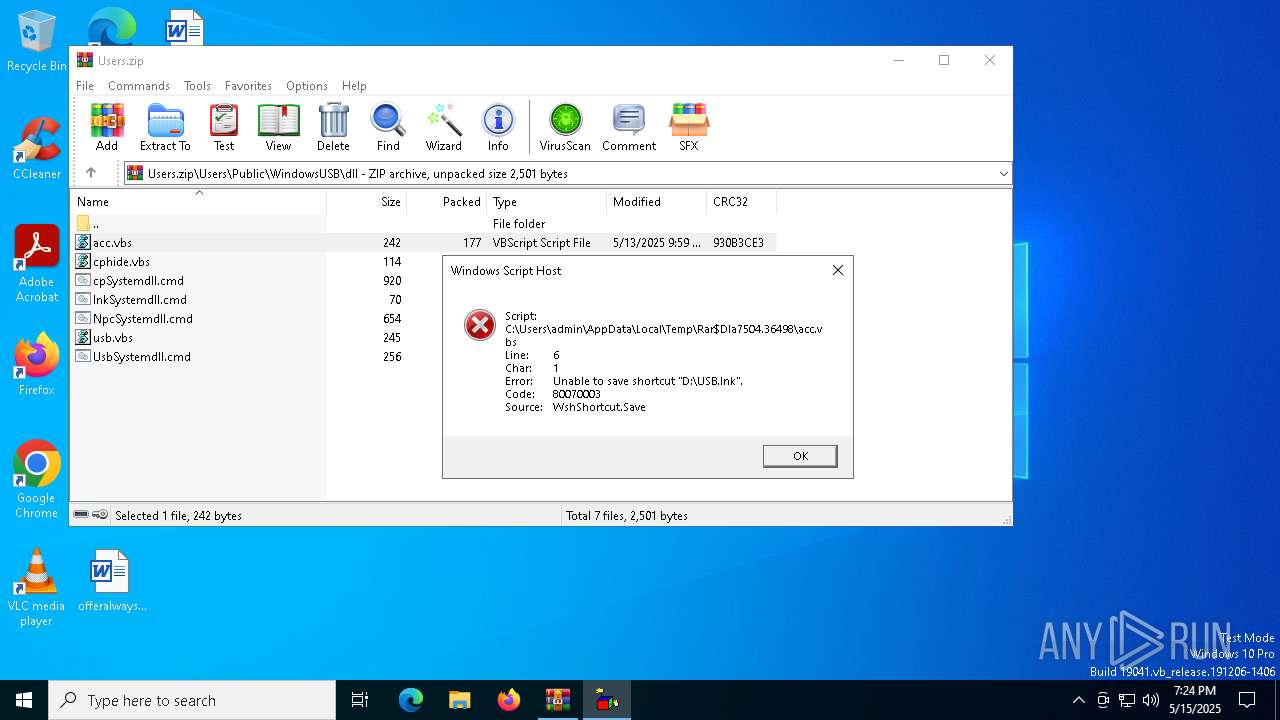
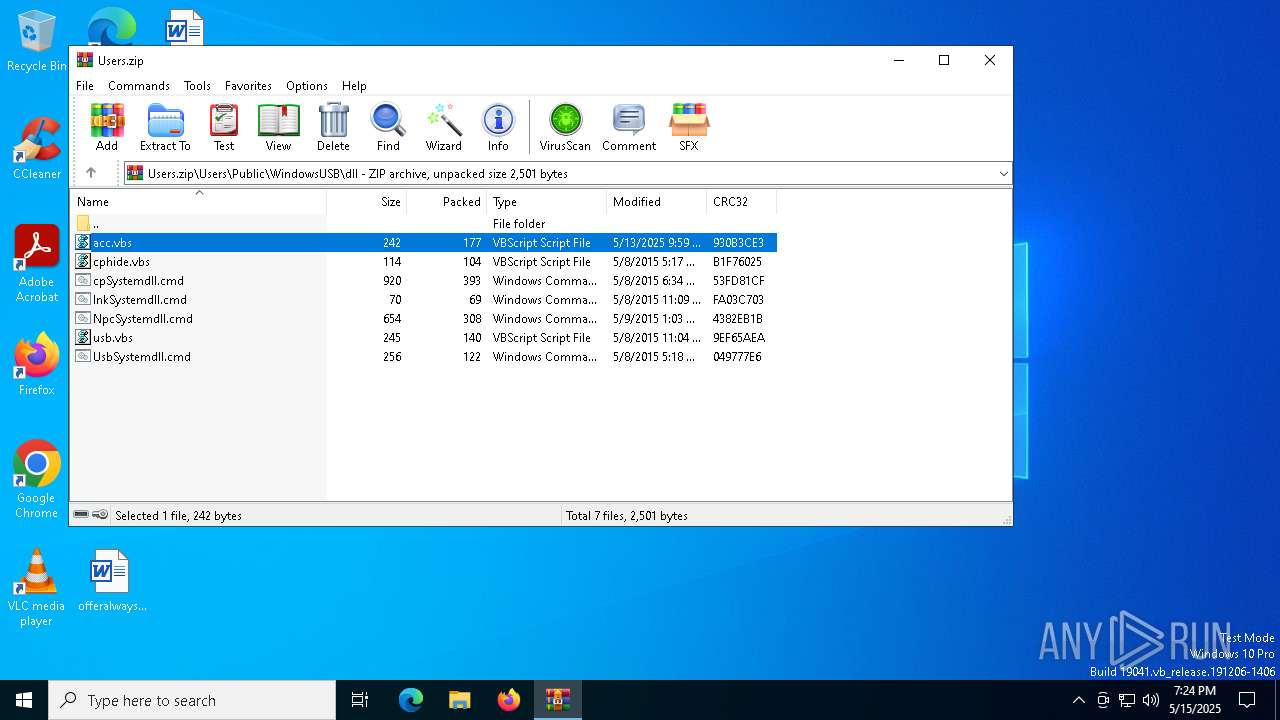
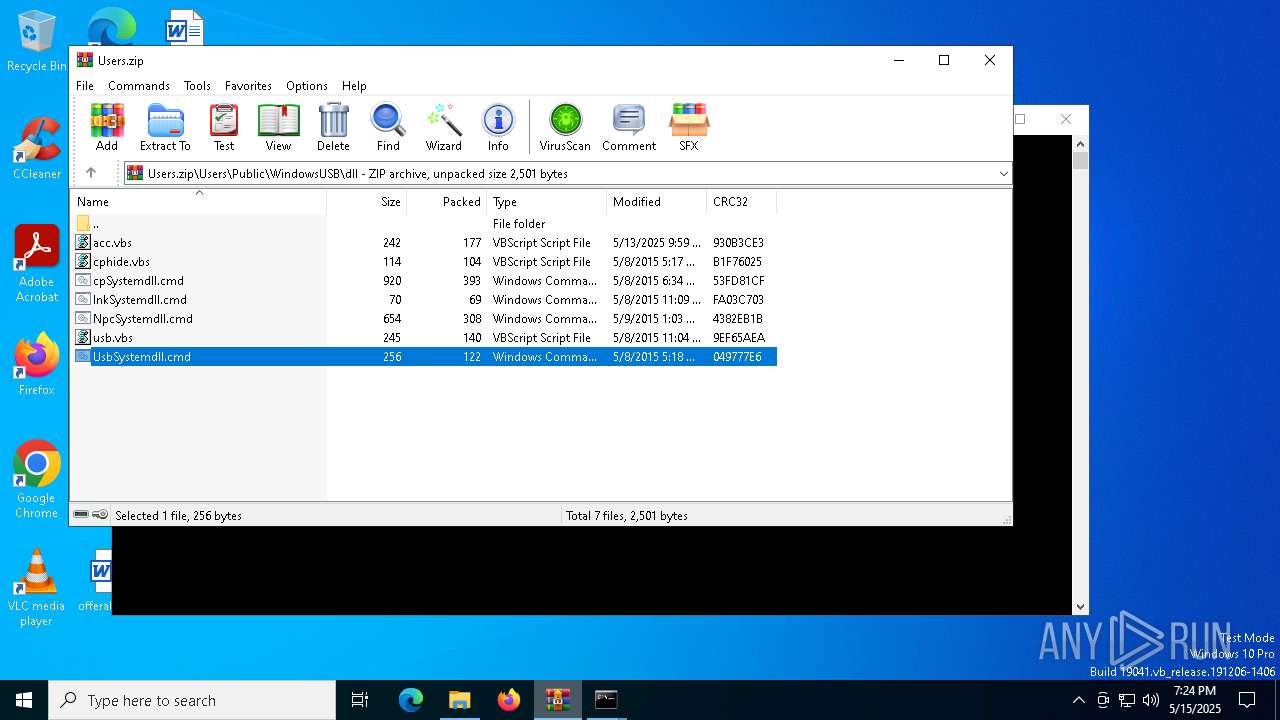
| File name: | Users.zip |
| Full analysis: | https://app.any.run/tasks/916a8174-b316-407a-ba49-05edc27fac22 |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2025, 19:23:58 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | DBB0A1E23D5FB6B087AAB2DFB5401F4A |
| SHA1: | 08661E6A555C7EEBCD9F1FBDEA9CC08F8405A839 |
| SHA256: | 9AA1761B216C12B5DA832AF6059CE481DE553F9E4396C85A8F587FD35414B9C5 |
| SSDEEP: | 96:2oz3e86TrRLKNFcw3vrNfh67DhnwXEvE3NAmrzfF9ocvhea69N44TBJjl1Ksuk:2U9erRLKNFd3367Dhk3NHrDF9xrAN44j |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7504)
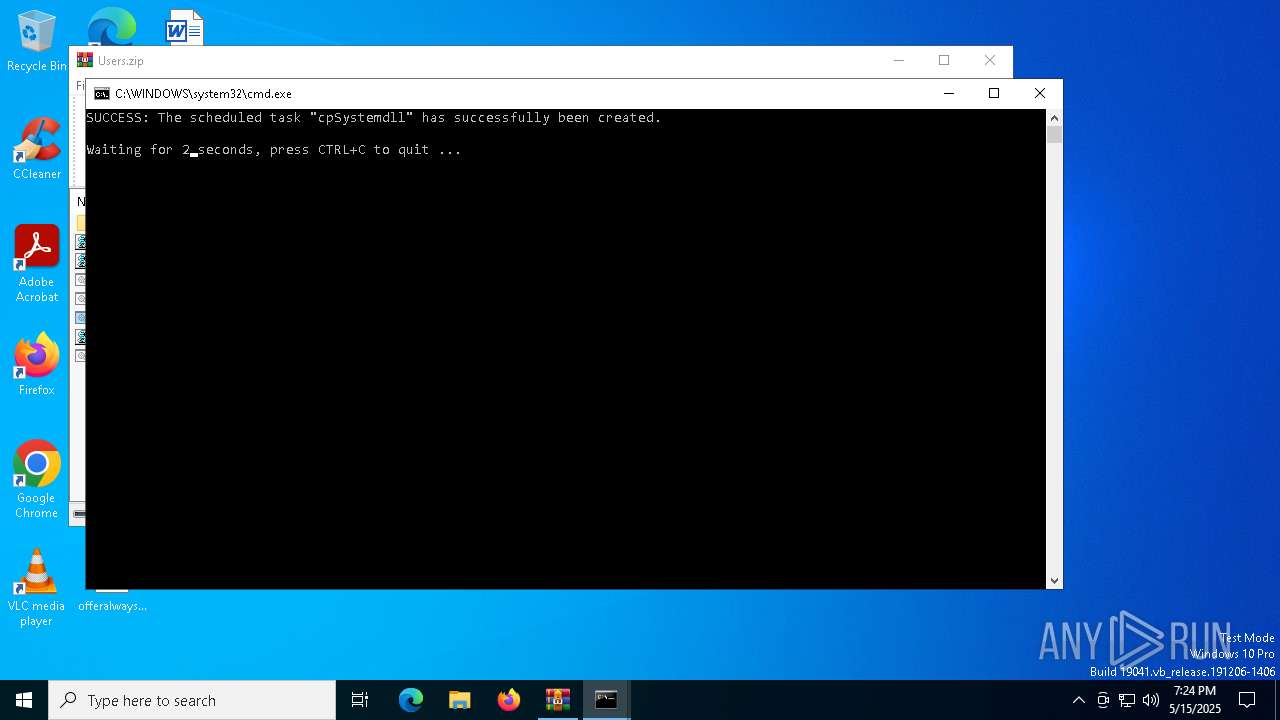
Uses Task Scheduler to run other applications
- cmd.exe (PID: 7148)
SUSPICIOUS
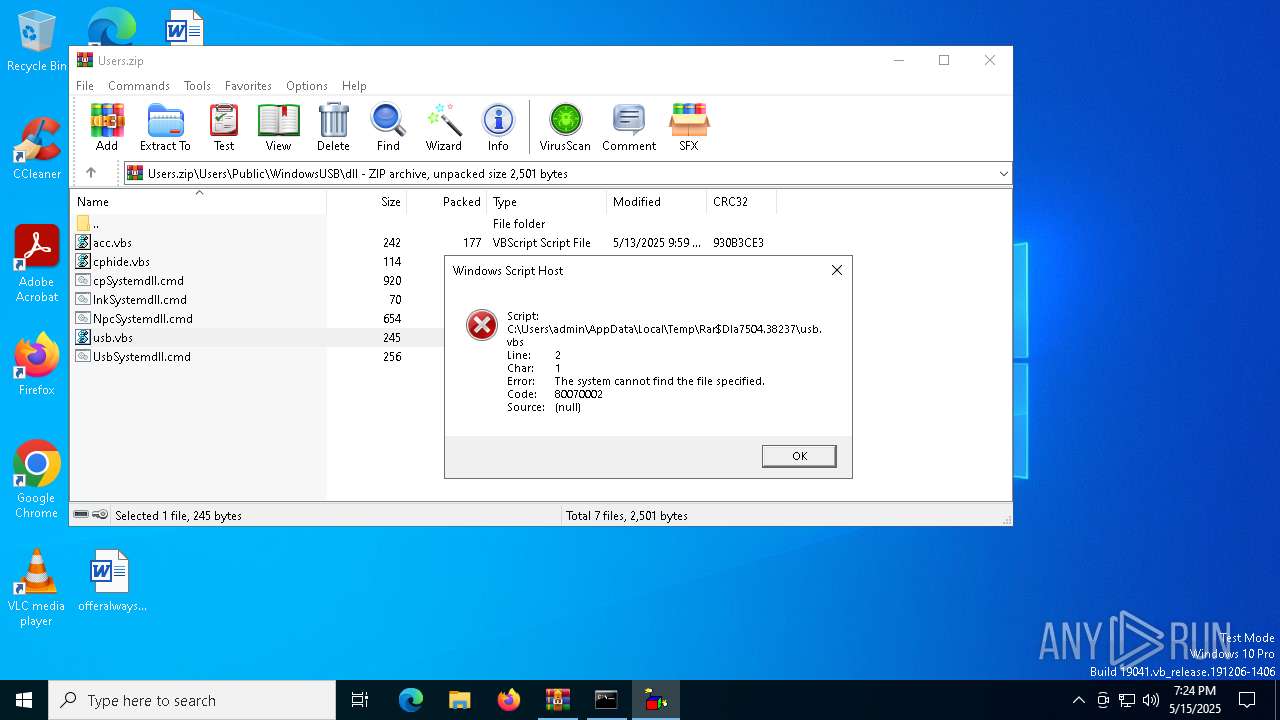
Runs shell command (SCRIPT)
- wscript.exe (PID: 8152)
- wscript.exe (PID: 8092)
- wscript.exe (PID: 3240)
- wscript.exe (PID: 7624)
The process executes VB scripts
- WinRAR.exe (PID: 7504)
- cmd.exe (PID: 7292)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7504)
Executing commands from ".cmd" file
- WinRAR.exe (PID: 7504)
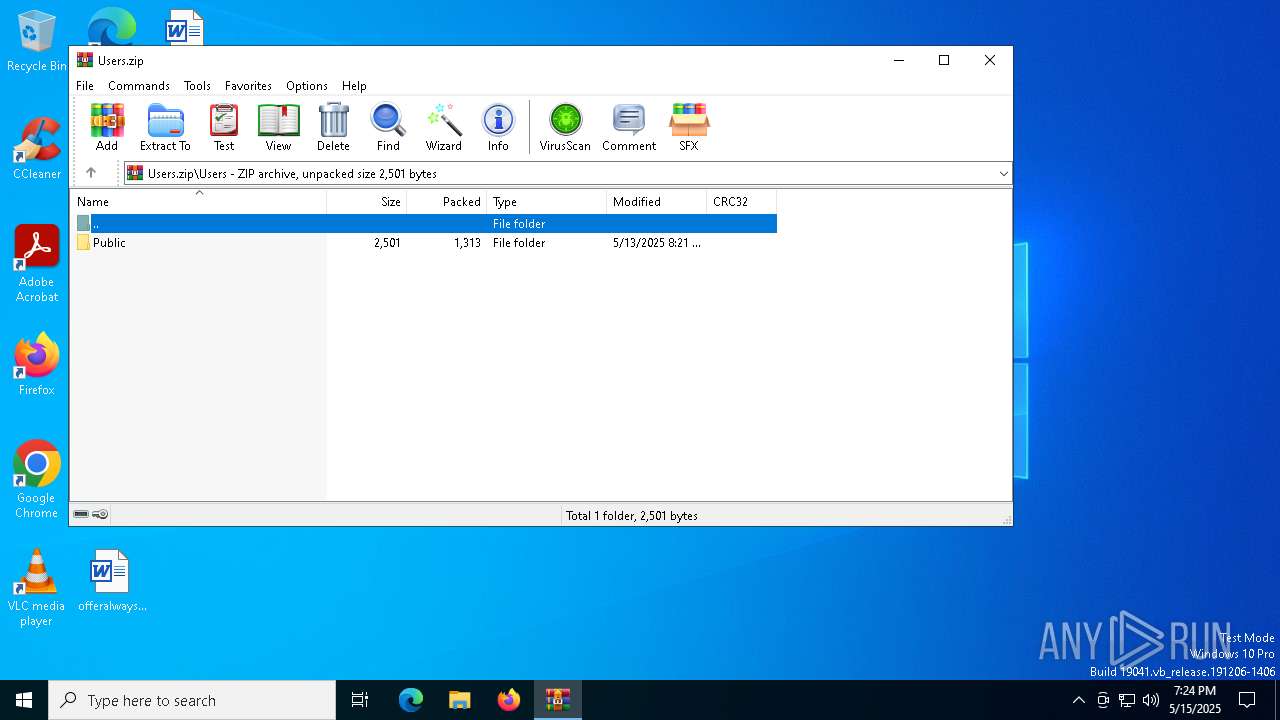
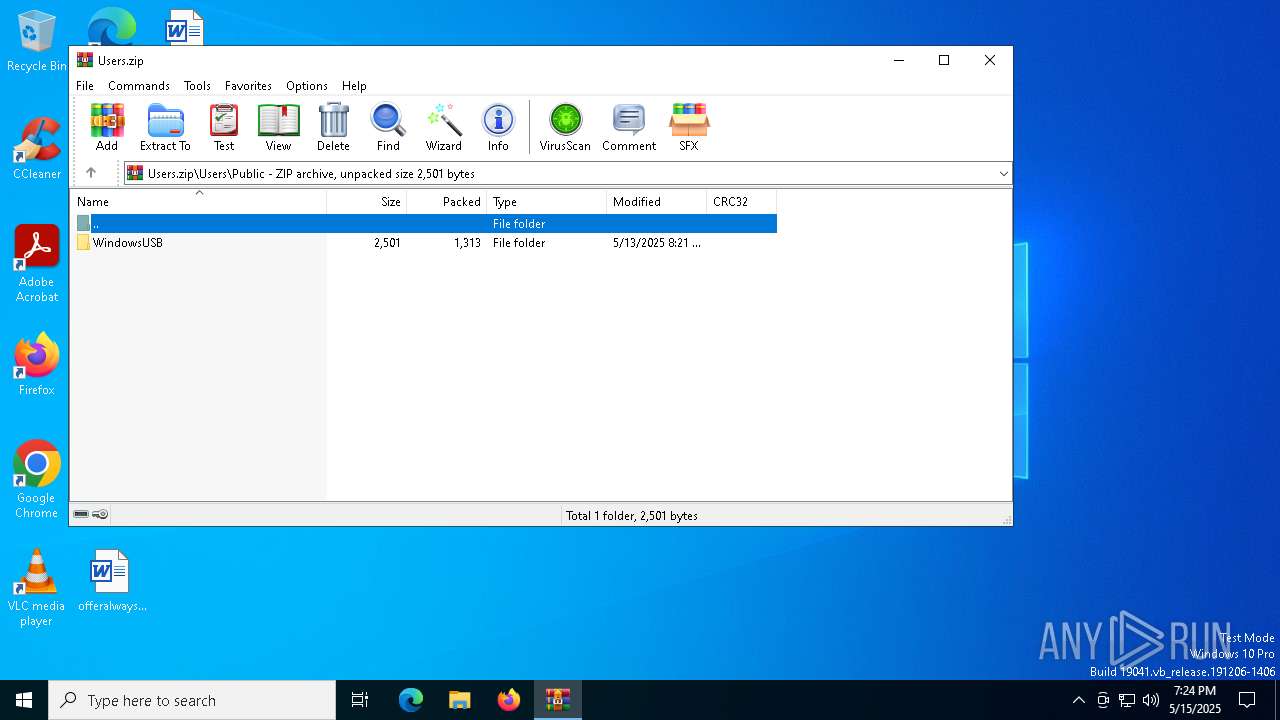
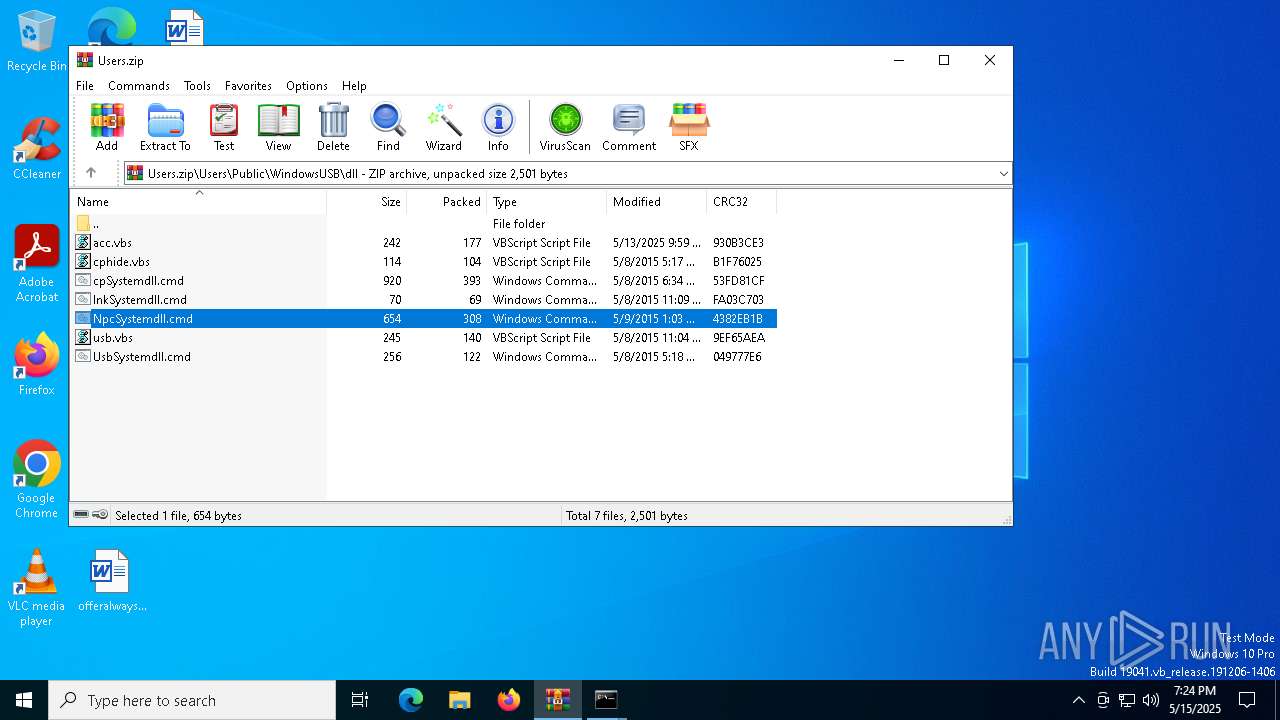
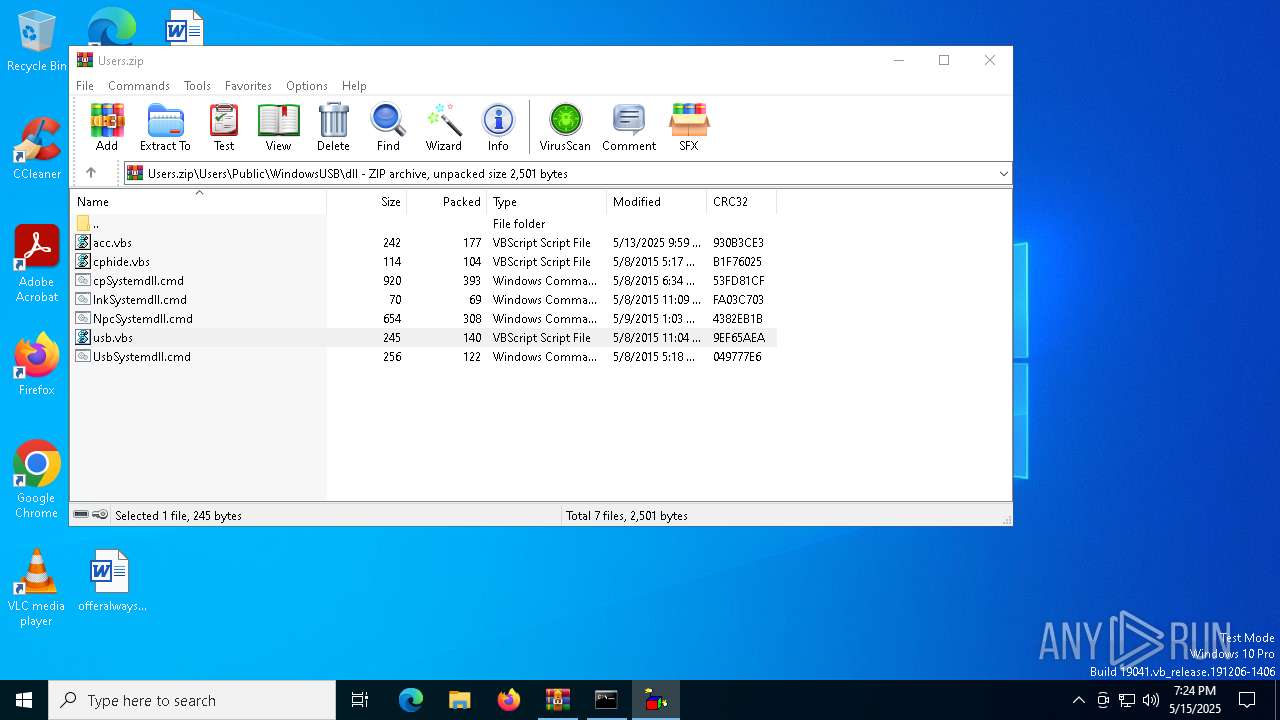
Likely accesses (executes) a file from the Public directory
- Robocopy.exe (PID: 7340)
- schtasks.exe (PID: 4268)
- schtasks.exe (PID: 6800)
- schtasks.exe (PID: 6112)
- Robocopy.exe (PID: 4740)
- wscript.exe (PID: 6132)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 7504)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 7292)
- cmd.exe (PID: 7148)
The process executes via Task Scheduler
- wscript.exe (PID: 6132)
INFO
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 7504)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:05:13 15:21:44 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Users/ |
Total processes
151
Monitored processes
24
Malicious processes
2
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2108 | timeout /nobreak 3 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3240 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa7504.38237\usb.vbs" | C:\Windows\System32\wscript.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 4268 | SCHTASKS.exe /Create /SC "MINUTE" /MO "1" /TN "cpSystemdll" /TR "\"C:\WINDOWS\System32\WScript.exe\" \"C:\Users\Public\WindowsUSB\dll\cphide.vbs\"" | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
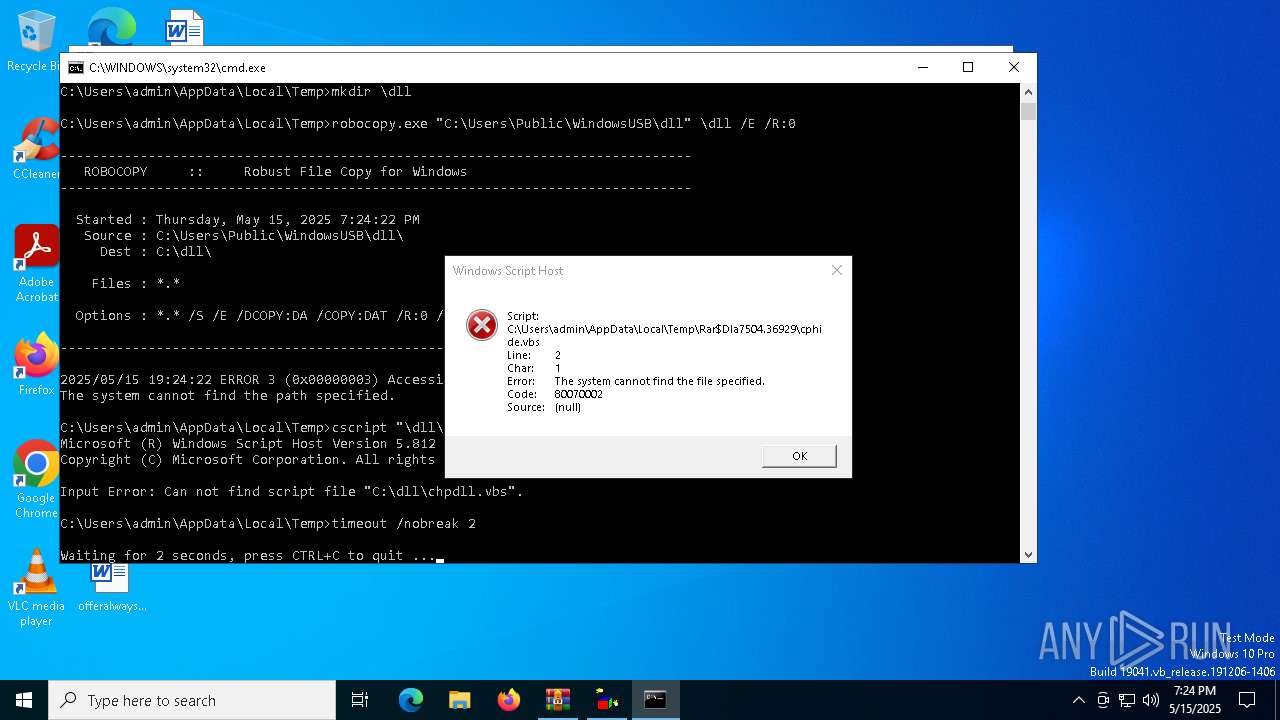
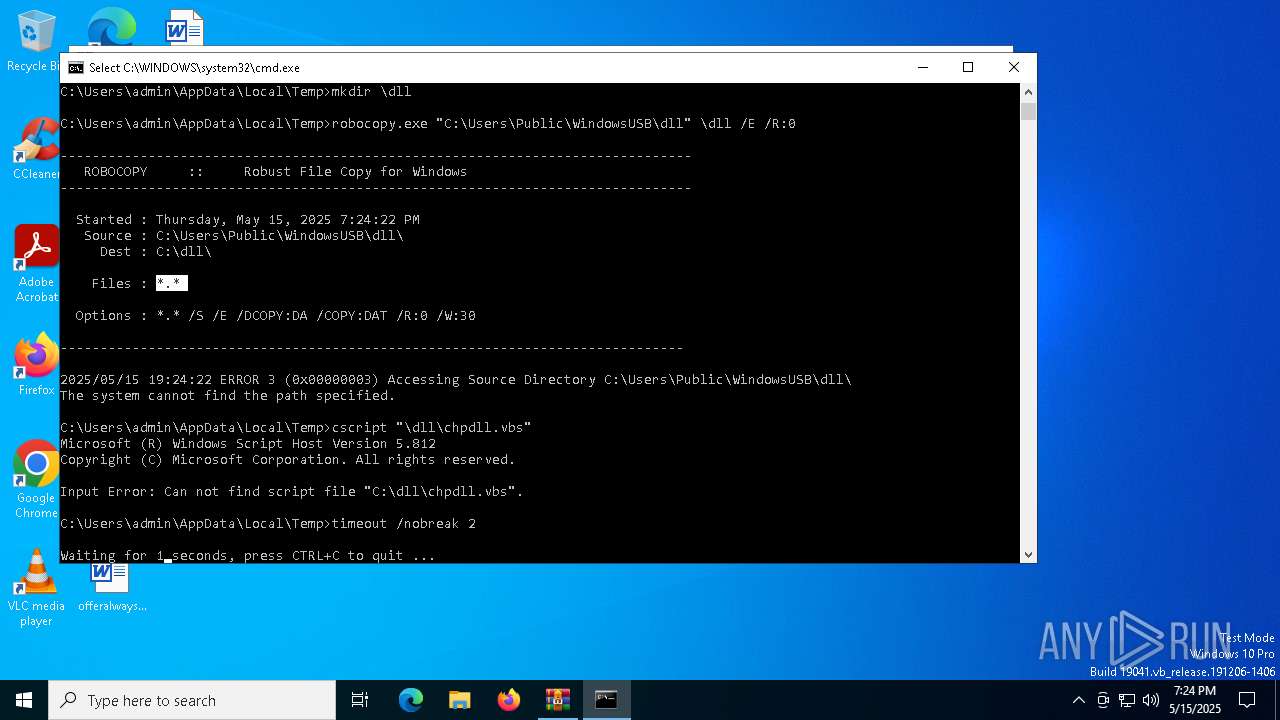
| 4448 | cscript "\dll\chpdll.vbs" | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 1 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 4740 | robocopy.exe /MIR \US12357SB\dll "C:\Users\Public\WindowsUSB\dll" | C:\Windows\System32\Robocopy.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Robocopy Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5256 | timeout /nobreak 2 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6112 | schtasks.exe /create /tn "linktest" /tr "\"C:\WINDOWS\System32\WScript.exe\" \"C:\Users\Public\WindowsUSB\dll\lnkhide.vbs\"" /sc "once" /sd Thu 05/15/2025 /st 19:29:00 | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 2147500037 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6132 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\Public\WindowsUSB\dll\cphide.vbs" | C:\Windows\System32\wscript.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 6800 | SCHTASKS.exe /Create /SC "HOURLY" /MO "8" /TN "lnkSystemdll" /TR "\"C:\WINDOWS\System32\WScript.exe\" \"C:\Users\Public\WindowsUSB\dll\lnkhide.vbs\"" | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 404
Read events
6 383
Write events
15
Delete events
6
Modification events
| (PID) Process: | (7504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Users.zip | |||
| (PID) Process: | (7504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbs\OpenWithProgids |
| Operation: | write | Name: | VBSFile |
Value: | |||
| (PID) Process: | (7340) Robocopy.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\ResKit\Robocopy |
| Operation: | delete value | Name: | WaitTime |
Value: | |||
Executable files
0
Suspicious files
0
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7504 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa7504.36498\acc.vbs | text | |
MD5:3F0E84503320DC347525FD945C9290D4 | SHA256:D18251F8328BA767CA119C4D2F66BF79C9560997FEF92E4333ADEA01B0B77B1B | |||
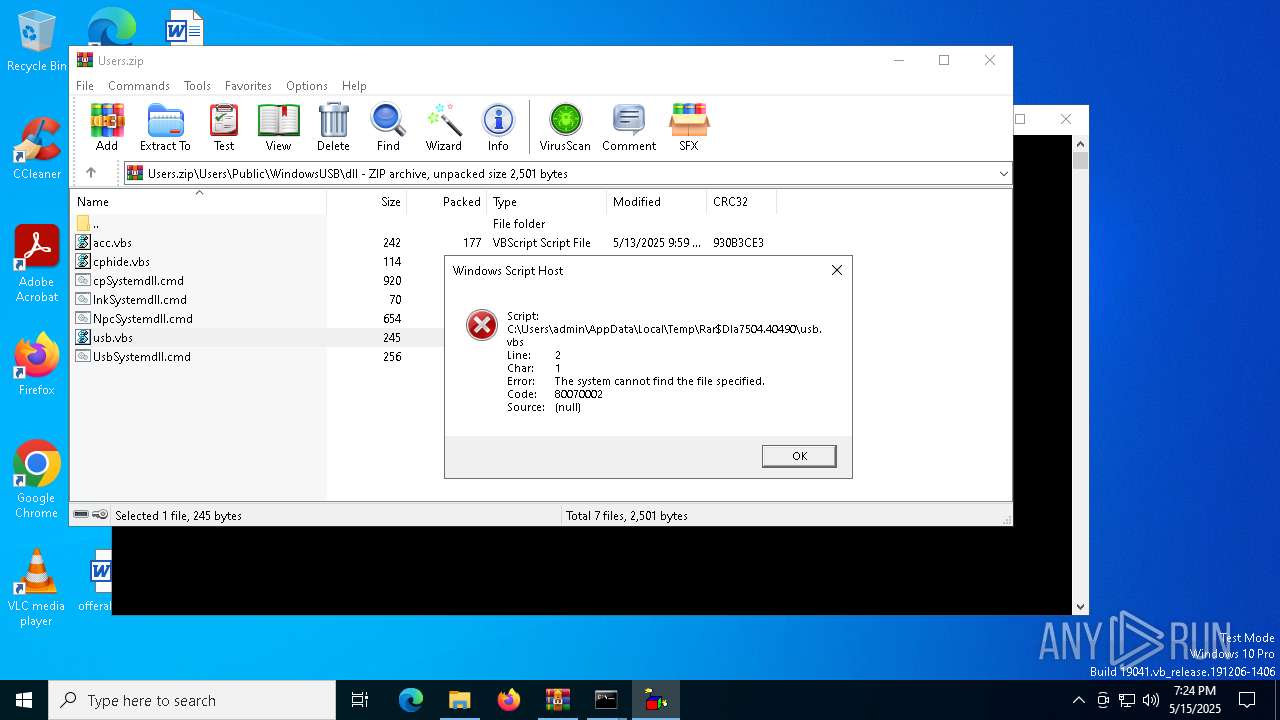
| 7504 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa7504.40490\usb.vbs | text | |
MD5:6CAD5AE385E066E5DDC51644D163411D | SHA256:745D0E84EDC8338B1BA17790F8F7EC6DBBF17708AF66294D1EFFD65FE034E8CE | |||
| 7504 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa7504.38237\usb.vbs | text | |
MD5:6CAD5AE385E066E5DDC51644D163411D | SHA256:745D0E84EDC8338B1BA17790F8F7EC6DBBF17708AF66294D1EFFD65FE034E8CE | |||
| 7504 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa7504.37688\NpcSystemdll.cmd | text | |
MD5:2D2DEB55CE1389D8ED0E4AC1067B1384 | SHA256:BE509F69D33E07470A56CF9406EE2617E33C04ADE64DBAC0409BD49C9C37C787 | |||
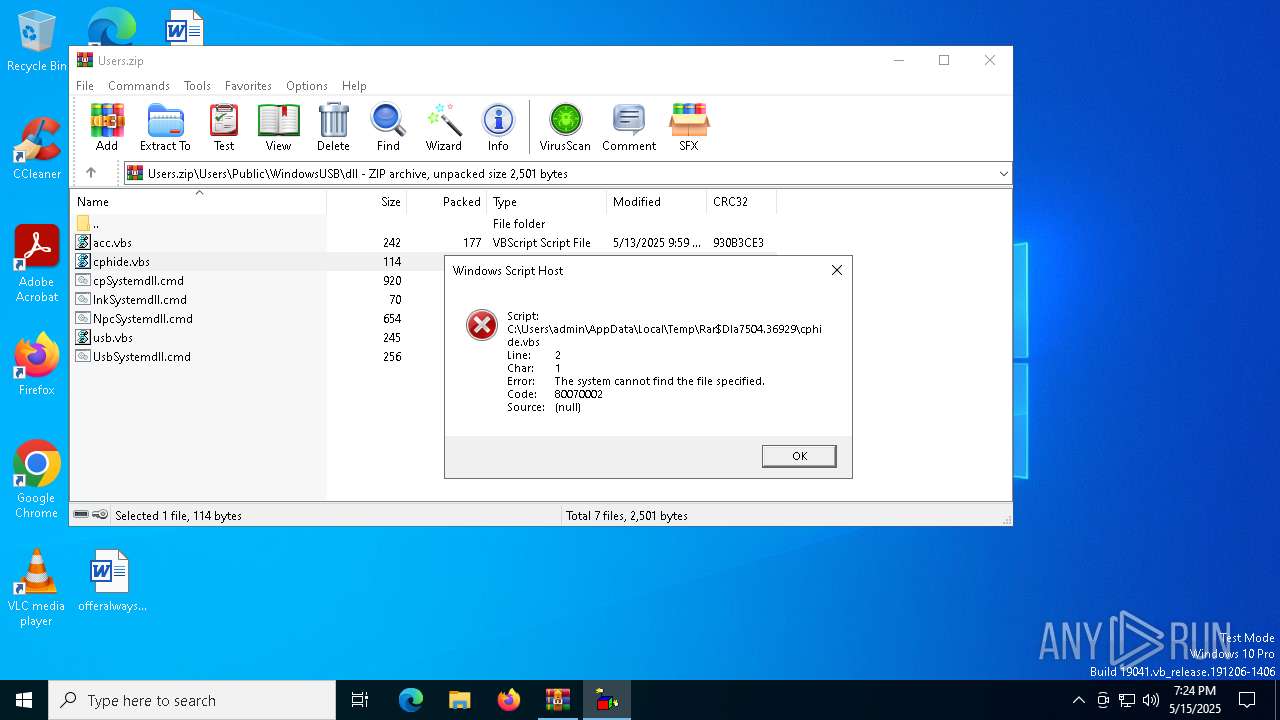
| 7504 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa7504.36929\cphide.vbs | text | |
MD5:1BF79D131DB604636B44CD98813B0BA6 | SHA256:47E3FDF5F28BB5AAB472C3D63FA8D13208AC838D60CCCFA7778703CF97A3D949 | |||
| 7504 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa7504.38548\UsbSystemdll.cmd | text | |
MD5:14E832C3EB2F4203896EA06D9B367027 | SHA256:7A00A7436055AC08527A4B91A74A19F49F9A7AEACF7E37F8E87C29255EC88E1B | |||
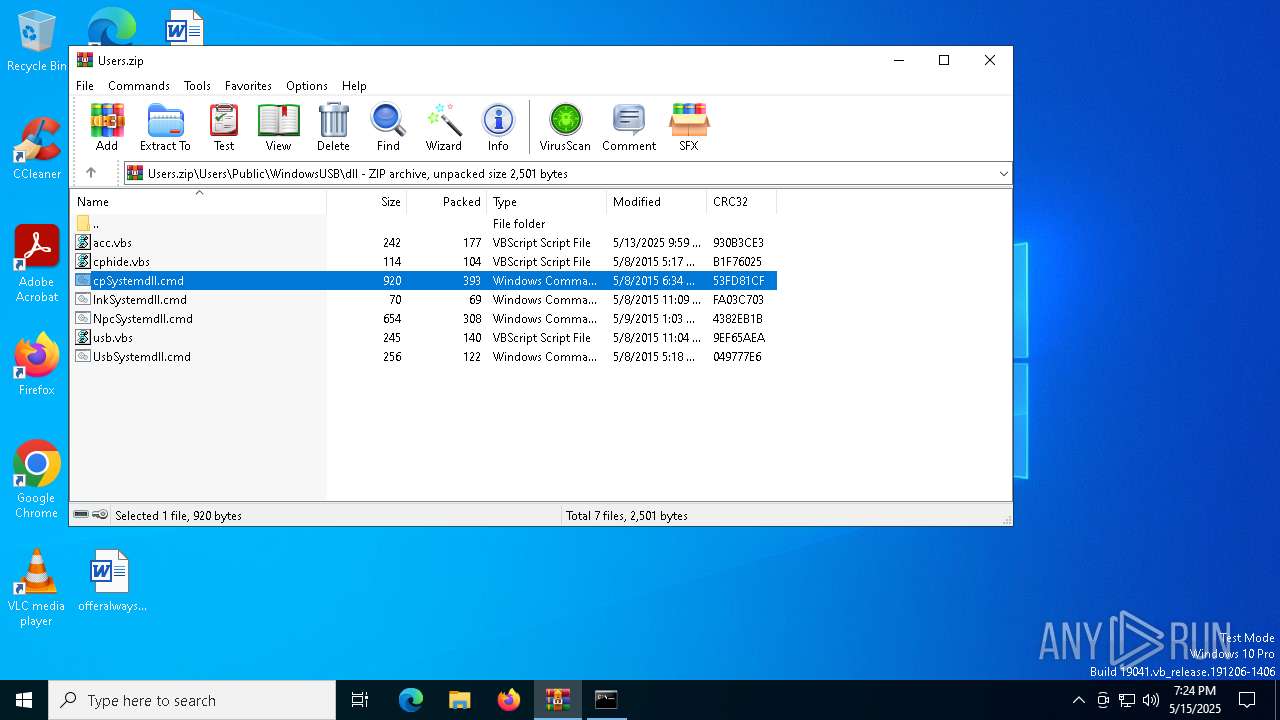
| 7504 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa7504.37118\cpSystemdll.cmd | text | |
MD5:E6881C942C8B5C832A2A01A131BF1833 | SHA256:01B7ABE294E7353E3E5420DFD32A9341B787DFC989297A9EA4E312FFABB08EA0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
19
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4488 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4488 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |