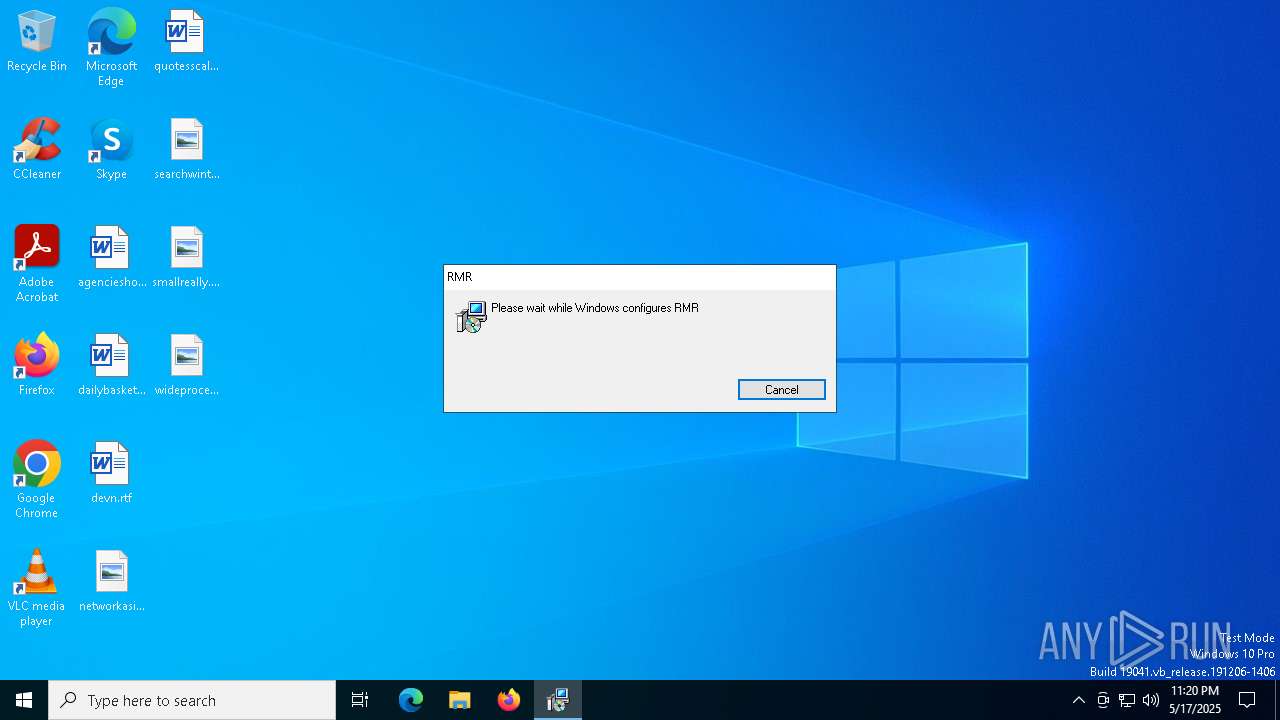
| File name: | s.msi |
| Full analysis: | https://app.any.run/tasks/b2ba5ddc-7a02-4b51-9f84-503bc375e52c |
| Verdict: | Malicious activity |
| Analysis date: | May 17, 2025, 23:20:19 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Security: 0, Code page: 1252, Revision Number: {10BFDD7E-7DBA-4183-8B3D-EEBBCDB51ABC}, Number of Words: 10, Subject: RMR, Author: R$A, Name of Creating Application: RMR, Template: ;1033, Title: Installation Database, Keywords: Installer, MSI, Database, Create Time/Date: Sun May 4 22:50:43 2025, Last Saved Time/Date: Sun May 4 22:50:43 2025, Last Printed: Sun May 4 22:50:43 2025, Number of Pages: 450 |
| MD5: | BD34FD1919B87A56C83C911AD5272A85 |
| SHA1: | F8D5D6ACEE8D2C9EEFE5D6CBE98A52D57AEE42DA |
| SHA256: | 9A64F7B8160C37F9D54BD20A263AE8265FF4D6F6E810C5C0BC7A3CFA8BF0DAA6 |
| SSDEEP: | 49152:f9IuHEo0RMWm9TABSYTJU4JVpDpWi4bxYjmcTFWnPZDdz9xH:f9Iho6MWm98sYTJU4ryh91 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 6044)
Detects AdvancedInstaller (YARA)
- msiexec.exe (PID: 1532)
- msiexec.exe (PID: 1760)
INFO
An automatically generated document
- msiexec.exe (PID: 1532)
Reads the computer name
- msiexec.exe (PID: 1760)
Checks supported languages
- msiexec.exe (PID: 1760)
Manages system restore points
- SrTasks.exe (PID: 6576)
The sample compiled with english language support
- msiexec.exe (PID: 1760)
Executable content was dropped or overwritten
- msiexec.exe (PID: 1760)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (81.9) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (9.2) |
| .msp | | | Windows Installer Patch (7.6) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| Security: | None |
|---|---|
| CodePage: | Windows Latin 1 (Western European) |
| RevisionNumber: | {10BFDD7E-7DBA-4183-8B3D-EEBBCDB51ABC} |
| Words: | 10 |
| Subject: | RMR |
| Author: | R$A |
| LastModifiedBy: | - |
| Software: | RMR |
| Template: | ;1033 |
| Comments: | - |
| Title: | Installation Database |
| Keywords: | Installer, MSI, Database |
| CreateDate: | 2025:05:04 22:50:43 |
| ModifyDate: | 2025:05:04 22:50:43 |
| LastPrinted: | 2025:05:04 22:50:43 |
| Pages: | 450 |
Total processes
145
Monitored processes
10
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1532 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\s.msi | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1760 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3008 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4200 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4488 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5360 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5728 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6044 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6068 | C:\Windows\syswow64\MsiExec.exe -Embedding D58F30132FD171335E9D00811BD6285D | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6576 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 620
Read events
3 421
Write events
181
Delete events
18
Modification events
| (PID) Process: | (1760) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000CC790F4582C7DB01E00600008C170000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1760) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 480000000000000062DE114582C7DB01E00600008C170000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1760) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 480000000000000080275E4582C7DB01E00600008C170000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1760) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 480000000000000080275E4582C7DB01E00600008C170000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1760) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 48000000000000003BF0624582C7DB01E00600008C170000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1760) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 48000000000000000E55654582C7DB01E00600008C170000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1760) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (1760) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 48000000000000003C57E14582C7DB01E00600008C170000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1760) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 480000000000000022A8E34582C7DB01E0060000F0100000E8030000010000000000000000000000BD469824C6F1BC448D432D95A616D7F700000000000000000000000000000000 | |||
| (PID) Process: | (6044) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000E936ED4582C7DB019C170000EC080000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
8
Suspicious files
18
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1760 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 1760 | msiexec.exe | C:\Windows\Installer\MSI7B1.tmp | executable | |
MD5:379F76E2FA6EEF4C2116C2A3AE6896BE | SHA256:C54F8A0CC280A9A0C934B8B23BBD530BA739E79AD686121CC8B659882CEB60FD | |||
| 1760 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:8C7A9D92231DBD48D83BDB50F170D5BB | SHA256:4751385CD8B169ACC6A94B062636084C638E0CF5DDF82C28B31E8A67A8E1BC60 | |||
| 1760 | msiexec.exe | C:\Windows\Installer\1104cf.msi | executable | |
MD5:BD34FD1919B87A56C83C911AD5272A85 | SHA256:9A64F7B8160C37F9D54BD20A263AE8265FF4D6F6E810C5C0BC7A3CFA8BF0DAA6 | |||
| 1760 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{249846bd-f1c6-44bc-8d43-2d95a616d7f7}_OnDiskSnapshotProp | binary | |
MD5:8C7A9D92231DBD48D83BDB50F170D5BB | SHA256:4751385CD8B169ACC6A94B062636084C638E0CF5DDF82C28B31E8A67A8E1BC60 | |||
| 1760 | msiexec.exe | C:\Windows\Installer\MSI762.tmp | executable | |
MD5:379F76E2FA6EEF4C2116C2A3AE6896BE | SHA256:C54F8A0CC280A9A0C934B8B23BBD530BA739E79AD686121CC8B659882CEB60FD | |||
| 1760 | msiexec.exe | C:\Windows\Temp\~DFAB7A520173CC0CA3.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 1760 | msiexec.exe | C:\Windows\Temp\~DF7A9DBBBC7B02247F.TMP | binary | |
MD5:C9F7CE5780302055AACFDC1DE9852CA3 | SHA256:E7AB45318CB0AA29ECF9A52E19F56C53423E468A562496AEE603C551684B9D59 | |||
| 1760 | msiexec.exe | C:\Users\admin\AppData\Roaming\RS A\RMR\server.txt | text | |
MD5:61EED355DFB66580AA324ABA6B19B130 | SHA256:6F85BC19365E07BA2328500197710C335B1833F29E958AC1DA3E8D7F6048C808 | |||
| 1760 | msiexec.exe | C:\Windows\Temp\~DF4B64012D718C8A5A.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
33
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2320 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2320 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2112 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |