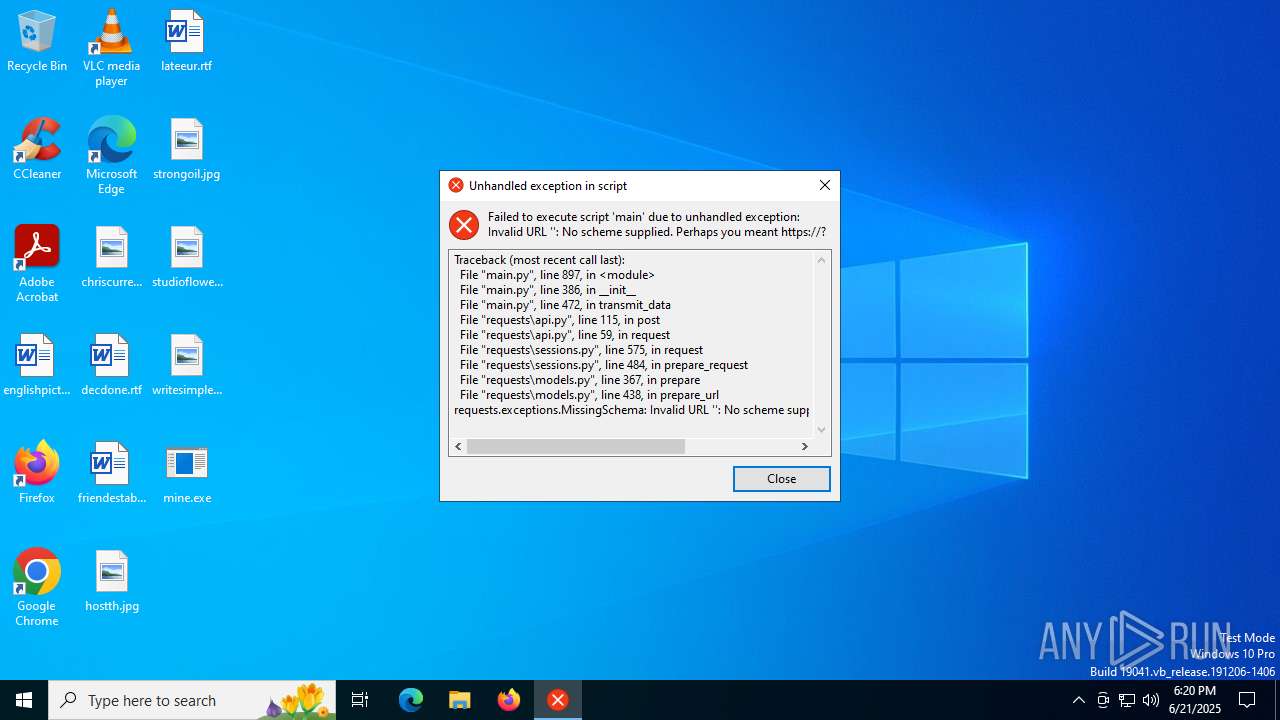
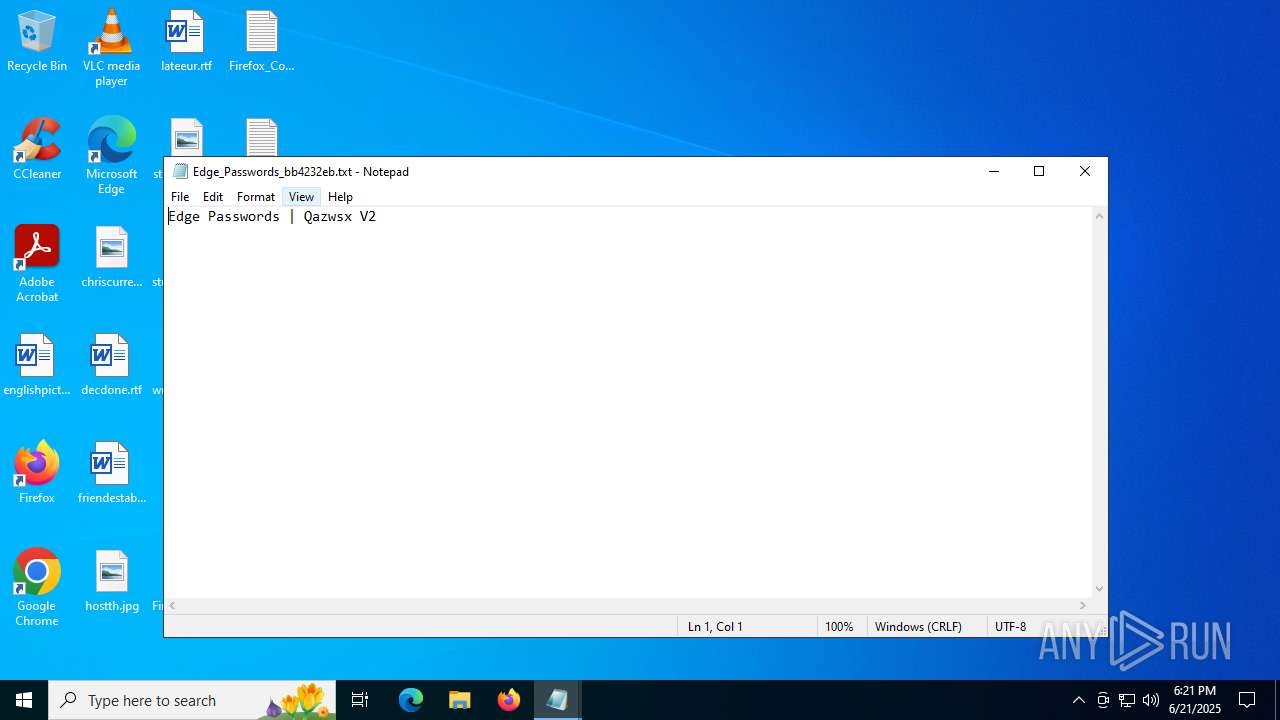
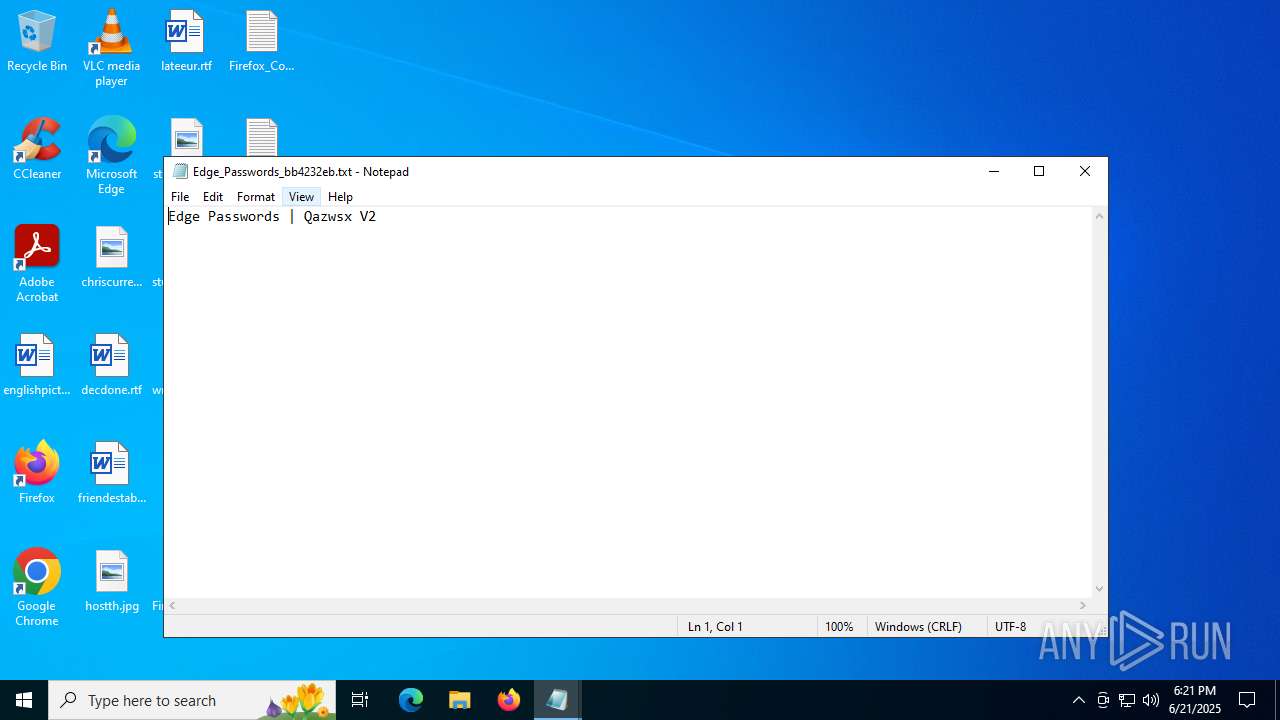
| File name: | mine.exe |
| Full analysis: | https://app.any.run/tasks/a0da54d4-affd-418b-9707-5dc8a7332aeb |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 18:20:11 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| MD5: | F51870B7E811AC63B7571259D8DE6649 |
| SHA1: | C01CE9FF46D664FDBAD623358CE0226E4D21D8B0 |
| SHA256: | 9A4D3E35A4EC43ACB41F81E38EEF9B6C42D95476D90ED629F601E68F5204348C |
| SSDEEP: | 196608:I4GpJhBiCWMG+A7q/Tevfk7E4wAwOd881mwo/kiPNAnB9CkvxUnVAK:IBvWJzq/Kvfk7YANd6wo/jlA7COxumK |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- mine.exe (PID: 5340)
Process drops python dynamic module
- mine.exe (PID: 5340)
Process drops legitimate windows executable
- mine.exe (PID: 5340)
Application launched itself
- mine.exe (PID: 5340)
The process drops C-runtime libraries
- mine.exe (PID: 5340)
Loads Python modules
- mine.exe (PID: 3588)
Potential Corporate Privacy Violation
- mine.exe (PID: 3588)
Checks for external IP
- mine.exe (PID: 3588)
- svchost.exe (PID: 2200)
INFO
Reads the computer name
- mine.exe (PID: 5340)
- mine.exe (PID: 3588)
Checks supported languages
- mine.exe (PID: 5340)
- mine.exe (PID: 3588)
Create files in a temporary directory
- mine.exe (PID: 5340)
- mine.exe (PID: 3588)
The sample compiled with english language support
- mine.exe (PID: 5340)
Checks proxy server information
- mine.exe (PID: 3588)
- slui.exe (PID: 2404)
Creates files or folders in the user directory
- mine.exe (PID: 3588)
Reads security settings of Internet Explorer
- notepad.exe (PID: 1728)
- notepad.exe (PID: 2632)
- notepad.exe (PID: 1604)
- notepad.exe (PID: 2116)
Manual execution by a user
- notepad.exe (PID: 1728)
- notepad.exe (PID: 2116)
- notepad.exe (PID: 1604)
- notepad.exe (PID: 2632)
Reads the software policy settings
- slui.exe (PID: 2404)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (57.6) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.9) |
| .exe | | | Generic Win/DOS Executable (2.6) |
| .exe | | | DOS Executable Generic (2.6) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:06:21 17:55:41+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.43 |
| CodeSize: | 173568 |
| InitializedDataSize: | 94208 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xce30 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
137
Monitored processes
8
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1604 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Edge_Cookies_bb4232eb.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
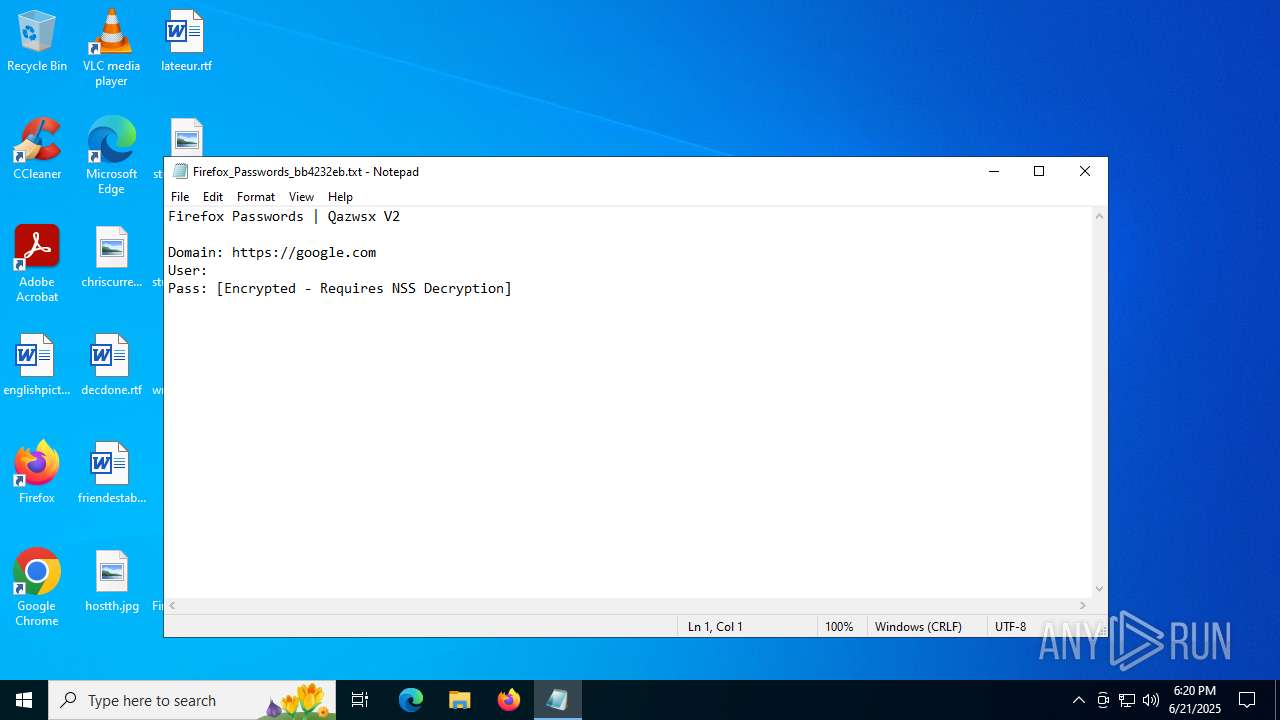
| 1728 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Firefox_Passwords_bb4232eb.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2116 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Edge_Passwords_bb4232eb.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2404 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2632 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Firefox_Cookies_bb4232eb.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3588 | "C:\Users\admin\Desktop\mine.exe" | C:\Users\admin\Desktop\mine.exe | mine.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 5340 | "C:\Users\admin\Desktop\mine.exe" | C:\Users\admin\Desktop\mine.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
Total events
4 517
Read events
4 517
Write events
0
Delete events
0
Modification events
Executable files
80
Suspicious files
7
Text files
29
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5340 | mine.exe | C:\Users\admin\AppData\Local\Temp\_MEI53402\Crypto\Cipher\_raw_blowfish.pyd | executable | |
MD5:CCE591EEEA855E374307B20400B828D0 | SHA256:614BCA7E1DDACDD1F13C523218EF0E948828CB250BB56C057821AB8AEB0684A6 | |||
| 5340 | mine.exe | C:\Users\admin\AppData\Local\Temp\_MEI53402\Crypto\Cipher\_raw_ctr.pyd | executable | |
MD5:8F385DBACD6C787926AB370C59D8BBA2 | SHA256:DDF0B165C1C4EFF98C4AC11E08C7BEADCDD8CC76F495980A21DF85BA4368762A | |||
| 5340 | mine.exe | C:\Users\admin\AppData\Local\Temp\_MEI53402\Crypto\Cipher\_pkcs1_decode.pyd | executable | |
MD5:ADDD92647204366DF68667E42182A934 | SHA256:F54CEBED8650C5274E81A4569708A0346DE560B89F1862DAD0E2CCB0D4D12043 | |||
| 5340 | mine.exe | C:\Users\admin\AppData\Local\Temp\_MEI53402\Crypto\Cipher\_raw_aes.pyd | executable | |
MD5:E59AE32AF366ED8A93B875517AEE9AFC | SHA256:67DD4F1547145355726E07769BC30BDC5CD7A559F80E3B35CC095E462D2124E3 | |||
| 5340 | mine.exe | C:\Users\admin\AppData\Local\Temp\_MEI53402\Crypto\Cipher\_raw_aesni.pyd | executable | |
MD5:74754F8EFA859912E8BF19C4DFA205B3 | SHA256:1FE62525DE39118C28C06C5DEE73340B451B1BF5EF989067FEBDAD86F0C20238 | |||
| 5340 | mine.exe | C:\Users\admin\AppData\Local\Temp\_MEI53402\Crypto\Cipher\_chacha20.pyd | executable | |
MD5:3816FAEFB26DCBC3E351DB6AFBD0B774 | SHA256:1E20F6D84838619AF92DE88355E9E76996E7346152E9179098AE7A5E72425141 | |||
| 5340 | mine.exe | C:\Users\admin\AppData\Local\Temp\_MEI53402\Crypto\Cipher\_raw_cast.pyd | executable | |
MD5:5055A838161FED842054259A61D53E5E | SHA256:C07032D21BACCA699F79F0C8338163F6748FA9AF03FE0212F862AC81AF18CEAF | |||
| 5340 | mine.exe | C:\Users\admin\AppData\Local\Temp\_MEI53402\Crypto\Cipher\_Salsa20.pyd | executable | |
MD5:20B7C6271603BC7C2087B2E589B51EF3 | SHA256:433310A5FDC3DF5F19F905237751156001C69D7805789D6178C6ACBB31E90105 | |||
| 5340 | mine.exe | C:\Users\admin\AppData\Local\Temp\_MEI53402\Crypto\Cipher\_ARC4.pyd | executable | |
MD5:211277A44CAC7C71FA844E9D156B9F6D | SHA256:4347B2AB52AF042670BD9DC2AC2F15B2487980E92E523DA0641B8287D8816CE6 | |||
| 5340 | mine.exe | C:\Users\admin\AppData\Local\Temp\_MEI53402\Crypto\Cipher\_raw_des3.pyd | executable | |
MD5:02DA7BD57BDBE809295E77115A4DE3F0 | SHA256:C9CE943634D2F0F88EFD33C57E1FB99756CC8D543ADE1A35ADB954EA5F882C89 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
43
DNS requests
20
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.55.104.190:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.55.104.190:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.55.104.190:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 40.126.31.129:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
3588 | mine.exe | GET | 200 | 34.117.59.81:80 | http://ipinfo.io/json | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.190.159.131:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 16.7 Kb | whitelisted |
— | — | POST | 200 | 40.126.31.73:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.55.104.190:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
1268 | svchost.exe | 23.55.104.190:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
— | — | 23.55.104.190:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
5944 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
1268 | svchost.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
pastebin.com |
| whitelisted |
ipinfo.io |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |
2200 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ipinfo .io) |
3588 | mine.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Python Suspicious User Agent |
3588 | mine.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ipinfo.io |