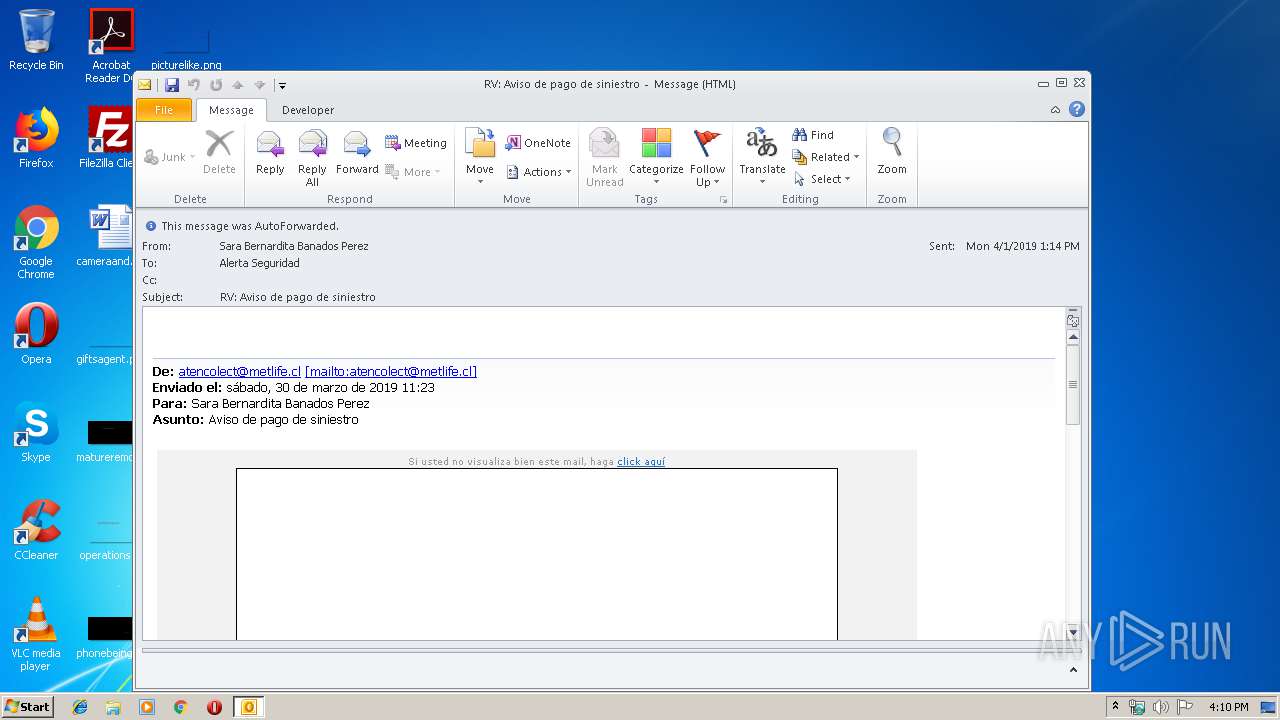
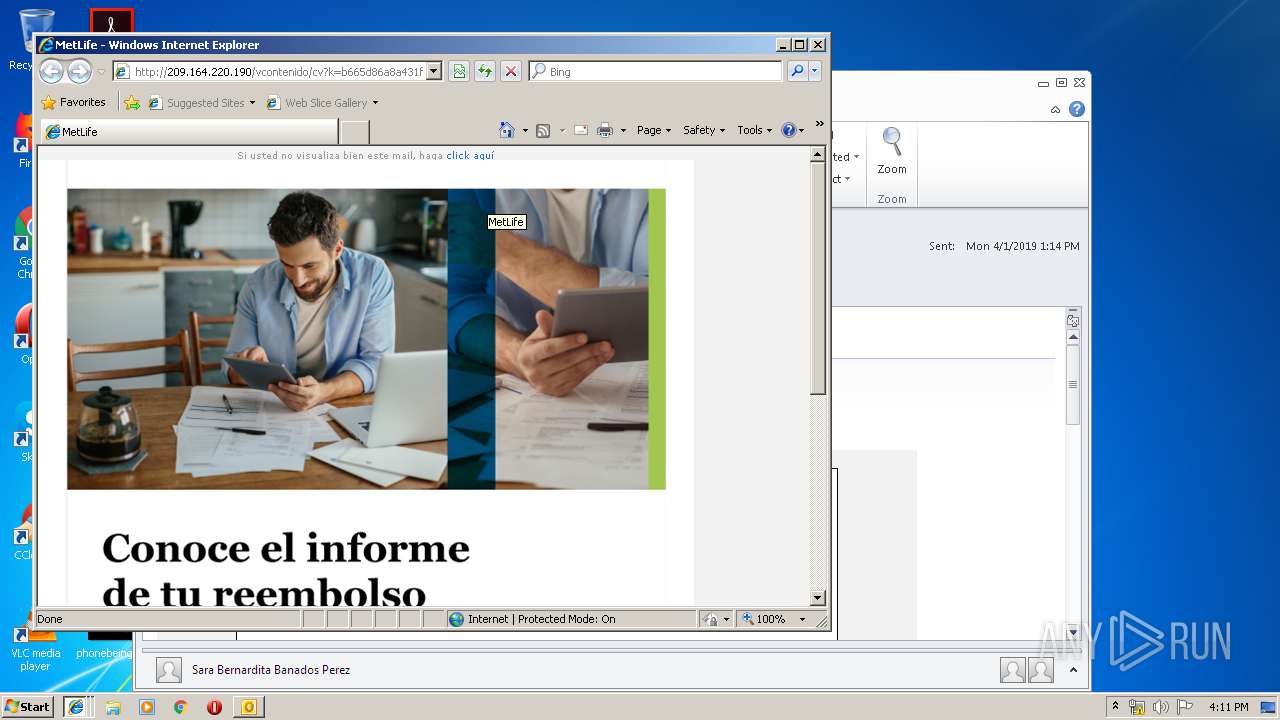
| File name: | RV Aviso de pago de siniestro.msg |
| Full analysis: | https://app.any.run/tasks/7e47fd59-2fa7-42ce-b878-a6d9b9b94824 |
| Verdict: | Malicious activity |
| Analysis date: | April 23, 2019, 15:09:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | 07AA161EE13F406510278B7CB9AADC41 |
| SHA1: | 94A5F92502D11E26DD8559E70F8D423273601765 |
| SHA256: | 9A3D364521AB0CEA62CC9A886D022625E5FA3DC78C213AB83034BD932F9AB263 |
| SSDEEP: | 768:1u2oejxzggTaFRbActUsKYsKewTuppk9VNv3lVzm+sKi7AN+:SejNrwGkuS3lVl |
MALICIOUS
Unusual execution from Microsoft Office
- OUTLOOK.EXE (PID: 3692)
SUSPICIOUS
Starts Internet Explorer
- OUTLOOK.EXE (PID: 3692)
Creates files in the user directory
- OUTLOOK.EXE (PID: 3692)
INFO
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 3692)
Changes internet zones settings
- iexplore.exe (PID: 2300)
Creates files in the user directory
- iexplore.exe (PID: 1812)
- iexplore.exe (PID: 2068)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 4064)
- iexplore.exe (PID: 2300)
Reads Internet Cache Settings
- iexplore.exe (PID: 1812)
- iexplore.exe (PID: 3244)
- iexplore.exe (PID: 2068)
Reads internet explorer settings
- iexplore.exe (PID: 2068)
- iexplore.exe (PID: 1812)
- iexplore.exe (PID: 3244)
Application launched itself
- iexplore.exe (PID: 2300)
Reads settings of System Certificates
- iexplore.exe (PID: 2300)
Changes settings of System certificates
- iexplore.exe (PID: 2300)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2300)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
42
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1812 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2300 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2068 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2300 CREDAT:203009 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
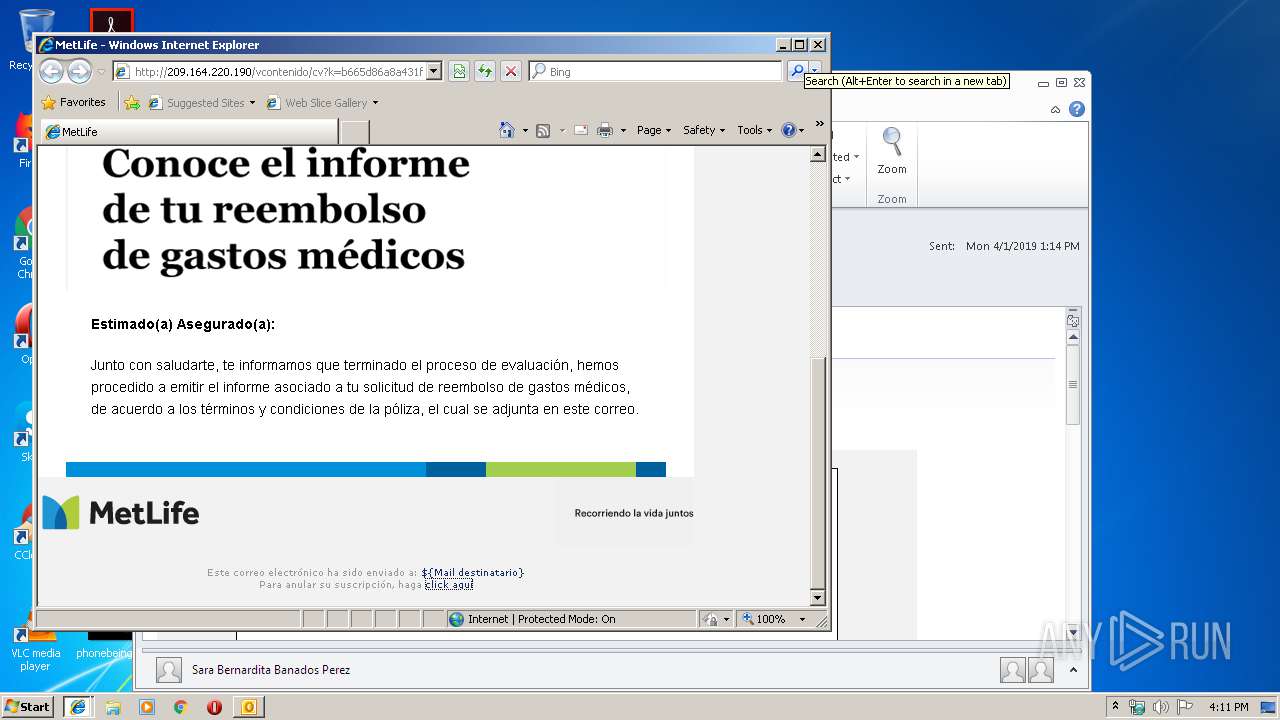
| 2300 | "C:\Program Files\Internet Explorer\iexplore.exe" http://209.164.220.190/vcontenido/cv?k=b665d86a8a431f3f9de664089d4f72c4 | C:\Program Files\Internet Explorer\iexplore.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3244 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2300 CREDAT:203010 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3692 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\RV Aviso de pago de siniestro.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 4064 | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe -Embedding | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 26.0 r0 Exit code: 0 Version: 26,0,0,131 Modules
| |||||||||||||||
Total events
2 071
Read events
1 518
Write events
530
Delete events
23
Modification events
| (PID) Process: | (3692) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3692) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3692) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\Resiliency\StartupItems |
| Operation: | write | Name: | p|6 |
Value: 707C36006C0E0000010000000000000000000000 | |||
| (PID) Process: | (3692) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook |
| Operation: | write | Name: | MTTT |
Value: 6C0E0000860975A8E6F9D40100000000 | |||
| (PID) Process: | (3692) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionNumber |
Value: 0 | |||
| (PID) Process: | (3692) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionDate |
Value: 220007520 | |||
| (PID) Process: | (3692) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\0a0d020000000000c000000000000046 |
| Operation: | write | Name: | 00030429 |
Value: 03000000 | |||
| (PID) Process: | (3692) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | {ED475418-B0D6-11D2-8C3B-00104B2A6676} |
Value: | |||
| (PID) Process: | (3692) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | LastChangeVer |
Value: 1200000000000000 | |||
| (PID) Process: | (3692) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109A10090400000000000F01FEC\Usage |
| Operation: | write | Name: | OutlookMAPI2Intl_1033 |
Value: 1318518805 | |||
Executable files
0
Suspicious files
0
Text files
66
Unknown types
30
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3692 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR5CE1.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3692 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\BDC1B5A.dat | image | |
MD5:— | SHA256:— | |||
| 3692 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:— | SHA256:— | |||
| 3692 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\F8DD3F93.dat | image | |
MD5:— | SHA256:— | |||
| 3692 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3692 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\5A7A37D.dat | image | |
MD5:— | SHA256:— | |||
| 3692 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\EB36E6C.dat | image | |
MD5:— | SHA256:— | |||
| 1812 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\1N70PVOU\cv[1].txt | — | |
MD5:— | SHA256:— | |||
| 3692 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\StructuredQuery.log | text | |
MD5:— | SHA256:— | |||
| 2300 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
23
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3692 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
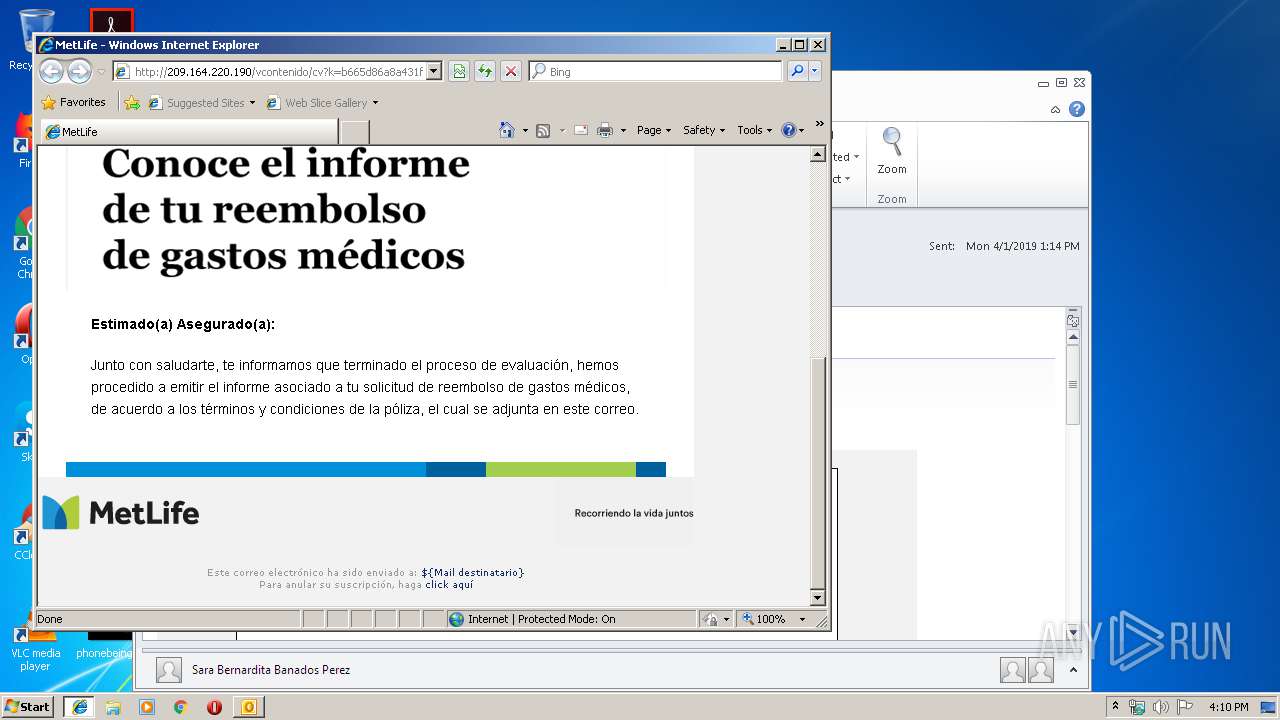
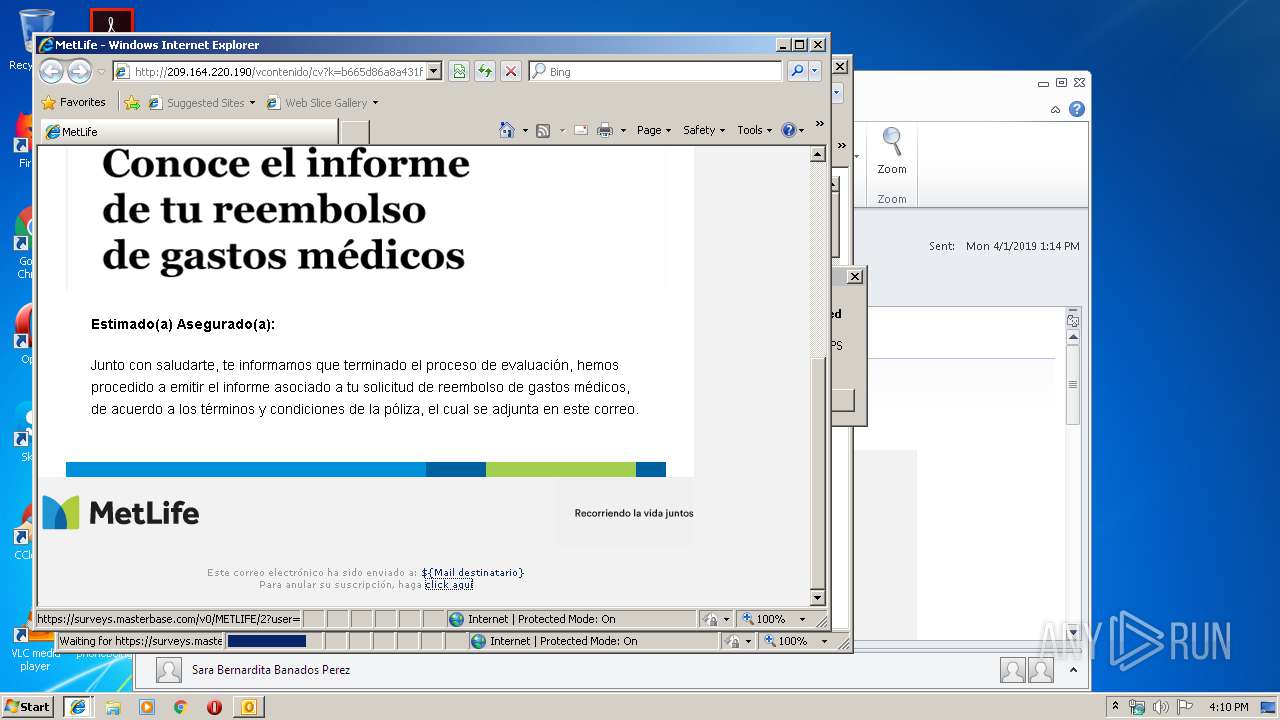
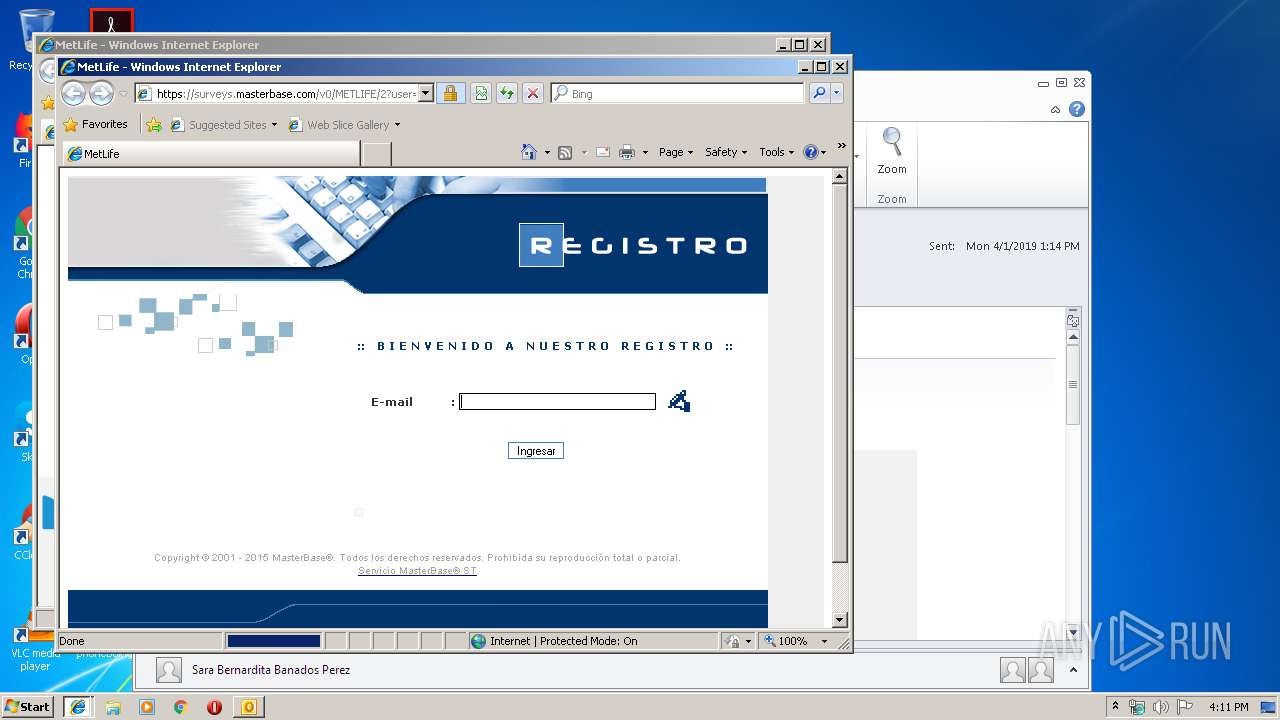
1812 | iexplore.exe | GET | 200 | 209.164.220.190:80 | http://209.164.220.190/vcontenido/cv?k=b665d86a8a431f3f9de664089d4f72c4&i=i.png | US | html | 12.7 Kb | unknown |
1812 | iexplore.exe | GET | 200 | 209.164.220.176:80 | http://www2.metlife.cl/campanas/2017/20170417-closing/images/closing-04.jpg | US | image | 5.30 Kb | unknown |
1812 | iexplore.exe | GET | 200 | 209.164.220.176:80 | http://www2.metlife.cl/campanas/2017/20170717-renovacion-poliza/images/Renovacion_Reembolso_03.jpg | US | image | 161 Kb | unknown |
1812 | iexplore.exe | GET | 200 | 209.164.220.190:80 | http://209.164.220.190/vcontenido/cv?k=b665d86a8a431f3f9de664089d4f72c4 | US | html | 12.7 Kb | unknown |
1812 | iexplore.exe | GET | 200 | 209.164.220.176:80 | http://www2.metlife.cl/campanas/2017/20170717-renovacion-poliza/images/Renovacion_Reembolso_07.jpg | US | image | 1.80 Kb | unknown |
3244 | iexplore.exe | GET | 301 | 209.164.220.174:80 | http://www.metlife.cl/ | US | html | 144 b | unknown |
1812 | iexplore.exe | GET | 200 | 209.164.220.190:80 | http://209.164.220.190/vcontenido/cv?k=b665d86a8a431f3f9de664089d4f72c4 | US | html | 12.7 Kb | unknown |
1812 | iexplore.exe | GET | 304 | 209.164.220.176:80 | http://www2.metlife.cl/campanas/2017/20170717-renovacion-poliza/images/Renovacion_Reembolso_07.jpg | US | — | — | unknown |
2300 | iexplore.exe | GET | 404 | 209.164.220.190:80 | http://209.164.220.190/favicon.ico | US | text | 130 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3692 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
2300 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2300 | iexplore.exe | 209.164.220.190:80 | — | MetLife | US | unknown |
2068 | iexplore.exe | 108.175.108.78:443 | surveys.masterbase.com | Master Base SA | US | unknown |
1812 | iexplore.exe | 209.164.220.176:80 | www2.metlife.cl | MetLife | US | unknown |
2300 | iexplore.exe | 108.175.108.78:443 | surveys.masterbase.com | Master Base SA | US | unknown |
2068 | iexplore.exe | 108.175.108.241:443 | imgsslscl.masterbase.com | Master Base SA | US | unknown |
— | — | 184.30.219.164:443 | w3.metlife.cl | Akamai International B.V. | NL | whitelisted |
3244 | iexplore.exe | 209.164.220.174:80 | www.metlife.cl | MetLife | US | unknown |
3244 | iexplore.exe | 184.30.219.164:443 | w3.metlife.cl | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
www2.metlife.cl |
| unknown |
www.bing.com |
| whitelisted |
surveys.masterbase.com |
| unknown |
imgsslscl.masterbase.com |
| unknown |
www.metlife.cl |
| unknown |
w3.metlife.cl |
| unknown |