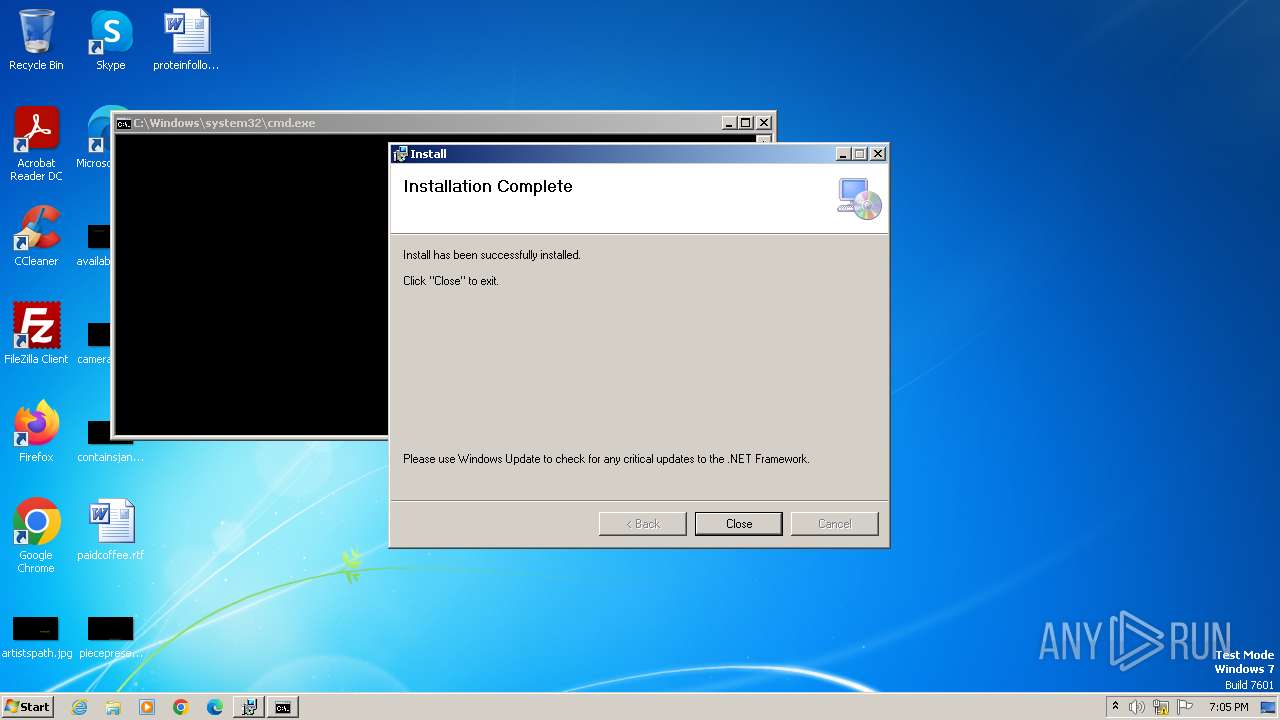
| File name: | Windows Pro Taskbar.msi |
| Full analysis: | https://app.any.run/tasks/bfcbceee-9ca7-47c7-b575-dd8204034332 |
| Verdict: | Malicious activity |
| Analysis date: | December 02, 2023, 19:03:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Create Time/Date: Mon Jun 21 08:00:00 1999, Name of Creating Application: Windows Installer, Security: 1, Code page: 1252, Template: Intel;1033, Number of Pages: 200, Revision Number: {35D3D526-D502-41C7-A590-D09206D3C13B}, Title: Install, Author: Install, Comments: Bringing the benefits of AI to everyone, Number of Words: 2, Last Saved Time/Date: Sat Dec 2 14:40:38 2023, Last Printed: Sat Dec 2 14:40:38 2023 |
| MD5: | 33DAC47110C5AA9BADA262A801996B1C |
| SHA1: | 75F86D2A240E66AC7740B06E8DD3DD3EE48E87D7 |
| SHA256: | 9A32A0335D8D7165BD043488A51BCAC1315DEB105841DD7588C32D19081F10BC |
| SSDEEP: | 24576:4uipiRvE4wThBDmmHFomQH/TMquzAN9X1ABV:4uipiRM4wThBDmmHFomc/TMquzk9XWj |
MALICIOUS
Drops the executable file immediately after the start
- msiexec.exe (PID: 3980)
Bypass execution policy to execute commands
- powershell.exe (PID: 3156)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 3600)
SUSPICIOUS
Process drops legitimate windows executable
- msiexec.exe (PID: 564)
- msiexec.exe (PID: 3980)
- chrome.exe (PID: 3972)
Executes as Windows Service
- VSSVC.exe (PID: 1560)
Starts CMD.EXE for commands execution
- msiexec.exe (PID: 3980)
The process executes Powershell scripts
- cmd.exe (PID: 3600)
Powershell version downgrade attack
- powershell.exe (PID: 3156)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 3600)
Reads the Internet Settings
- powershell.exe (PID: 3156)
- taskmgr.exe (PID: 2648)
- taskmgr.exe (PID: 3076)
Application launched itself
- taskmgr.exe (PID: 2648)
Executing commands from ".cmd" file
- msiexec.exe (PID: 3980)
INFO
Reads the computer name
- msiexec.exe (PID: 3980)
- msiexec.exe (PID: 3796)
- msiexec.exe (PID: 3588)
Checks supported languages
- msiexec.exe (PID: 3980)
- msiexec.exe (PID: 3796)
- msiexec.exe (PID: 3588)
Reads the machine GUID from the registry
- msiexec.exe (PID: 3980)
- msiexec.exe (PID: 3796)
- msiexec.exe (PID: 3588)
Create files in a temporary directory
- msiexec.exe (PID: 3796)
- msiexec.exe (PID: 3588)
- msiexec.exe (PID: 3980)
Application launched itself
- msiexec.exe (PID: 3980)
- chrome.exe (PID: 3972)
- msedge.exe (PID: 4016)
Drops the executable file immediately after the start
- msiexec.exe (PID: 564)
- chrome.exe (PID: 3972)
Creates files or folders in the user directory
- msiexec.exe (PID: 3980)
Manual execution by a user
- taskmgr.exe (PID: 2648)
Reads the time zone
- perfmon.exe (PID: 1420)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (90.2) |
|---|---|---|
| .msp | | | Windows Installer Patch (8.4) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CreateDate: | 1999:06:21 07:00:00 |
|---|---|
| Software: | Windows Installer |
| Security: | Password protected |
| CodePage: | Windows Latin 1 (Western European) |
| Template: | Intel;1033 |
| Pages: | 200 |
| RevisionNumber: | {35D3D526-D502-41C7-A590-D09206D3C13B} |
| Title: | Install |
| Subject: | - |
| Author: | Install |
| Keywords: | - |
| Comments: | Bringing the benefits of AI to everyone |
| Words: | 2 |
| ModifyDate: | 2023:12:02 14:40:38 |
| LastPrinted: | 2023:12:02 14:40:38 |
Total processes
80
Monitored processes
37
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 564 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\Windows Pro Taskbar.msi" | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1356 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=11 --mojo-platform-channel-handle=4040 --field-trial-handle=1160,i,78801202888492886,10381149692045693018,131072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1420 | "C:\Windows\System32\perfmon.exe" /res | C:\Windows\System32\perfmon.exe | — | taskmgr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Resource and Performance Monitor Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1560 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1672 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --mojo-platform-channel-handle=4248 --field-trial-handle=1348,i,14034409154449124852,6828535207008809068,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1876 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1296 --field-trial-handle=1348,i,14034409154449124852,6828535207008809068,131072 /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 2060 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=3408 --field-trial-handle=1348,i,14034409154449124852,6828535207008809068,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 2072 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=11 --mojo-platform-channel-handle=4068 --field-trial-handle=1348,i,14034409154449124852,6828535207008809068,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 2120 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --mojo-platform-channel-handle=3568 --field-trial-handle=1348,i,14034409154449124852,6828535207008809068,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 2128 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --first-renderer-process --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2044 --field-trial-handle=1160,i,78801202888492886,10381149692045693018,131072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
11 273
Read events
11 124
Write events
137
Delete events
12
Modification events
| (PID) Process: | (3980) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000F2B487BA16B0D901C80700002C0A0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3980) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4000000000000000F2B487BA16B0D901C80700002C0A0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3980) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 72 | |||
| (PID) Process: | (3980) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 40000000000000008C62D6BA16B0D901C80700002C0A0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3980) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Leave) |
Value: 400000000000000064514ABC16B0D901C80700002C0A0000D3070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3980) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppAddInterestingComponents (Enter) |
Value: 400000000000000064514ABC16B0D901C80700002C0A0000D4070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3980) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppAddInterestingComponents (Leave) |
Value: 400000000000000034645DBC16B0D901C80700002C0A0000D4070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3980) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Leave) |
Value: 4000000000000000781D5ABD16B0D901C80700002C0A0000D0070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3980) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Leave) |
Value: 4000000000000000781D5ABD16B0D901C80700002C0A0000D5070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3980) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRestore |
| Operation: | write | Name: | FirstRun |
Value: 0 | |||
Executable files
10
Suspicious files
92
Text files
60
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3980 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 3980 | msiexec.exe | C:\Program Files\Google\Install\System.Deployment.dll | executable | |
MD5:A3866C0523804E20005AB9CCDC1DC8B8 | SHA256:D1F155CBC36C0032382A39DEDAAB9D3CEB681ECE6DCFA988E34A3116B7CC5549 | |||
| 3980 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{85193b8e-b84c-4ba4-ba55-03a53f6ef26c}_OnDiskSnapshotProp | binary | |
MD5:4796766E8E103A271E55DC78B734499F | SHA256:52D03F34E8FB12A76D300E26CE43D382A2BCA2035C731FB87C1987E94BD1A11F | |||
| 3980 | msiexec.exe | C:\Program Files\Google\Install\Microsoft.VisualC.Dll | executable | |
MD5:8DF8C5146490DC4E469DDD31CED8A705 | SHA256:14F2E8D64BDB5B4FAD83B9D550FE1A39539CAEC3C66B8A6AB5A7995BBDA1A296 | |||
| 3980 | msiexec.exe | C:\Windows\Installer\MSI871C.tmp | executable | |
MD5:B77A2A2768B9CC78A71BBFFB9812B978 | SHA256:F74C97B1A53541B059D3BFAFE41A79005CE5065F8210D7DE9F1B600DC4E28AA0 | |||
| 3796 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\CFG68C0.tmp | xml | |
MD5:68675E0D405C8C76102802FA624EB895 | SHA256:B839CDD1C3F55651CD4D0E54A679BCE5AC60ED7618A7B74BFC8EF8CA311E53ED | |||
| 3980 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DF609B60733362818D.TMP | binary | |
MD5:A19C4CA3618320A12CB3F8135ECFFB17 | SHA256:FE3C8151CC3B5665C9F4C149797668BD463D7F4DBD24F8652E4B4E996F22EC44 | |||
| 3980 | msiexec.exe | C:\Program Files\Google\Install\nmmhkkegccagdldgiimedpic\background.js | text | |
MD5:260BE3713AF508AA4B27C21CB40F7832 | SHA256:A29A2A127981B15397EC0C8B2ECD15264CB6ACF59DAF8A8379132AA47437FE5B | |||
| 3588 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\CFG87A9.tmp | xml | |
MD5:68675E0D405C8C76102802FA624EB895 | SHA256:B839CDD1C3F55651CD4D0E54A679BCE5AC60ED7618A7B74BFC8EF8CA311E53ED | |||
| 3980 | msiexec.exe | C:\Program Files\Google\Install\nmmhkkegccagdldgiimedpic\manifest.json | binary | |
MD5:162CE37B0F293F4CFAD78AEFFA7028A5 | SHA256:F7AE9888BBFB60D6598FE9247FEF9EDEBC8928593F4E4032292D846E40B50254 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
107
DNS requests
42
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2900 | chrome.exe | 142.250.185.196:443 | www.google.com | GOOGLE | US | whitelisted |
3972 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2900 | chrome.exe | 142.250.186.138:443 | www.googleapis.com | GOOGLE | US | whitelisted |
2900 | chrome.exe | 64.233.166.84:443 | accounts.google.com | GOOGLE | US | unknown |
1876 | msedge.exe | 142.250.185.196:443 | www.google.com | GOOGLE | US | whitelisted |
4016 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
www.google.com |
| whitelisted |
www.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
edge-http.microsoft.com |
| whitelisted |