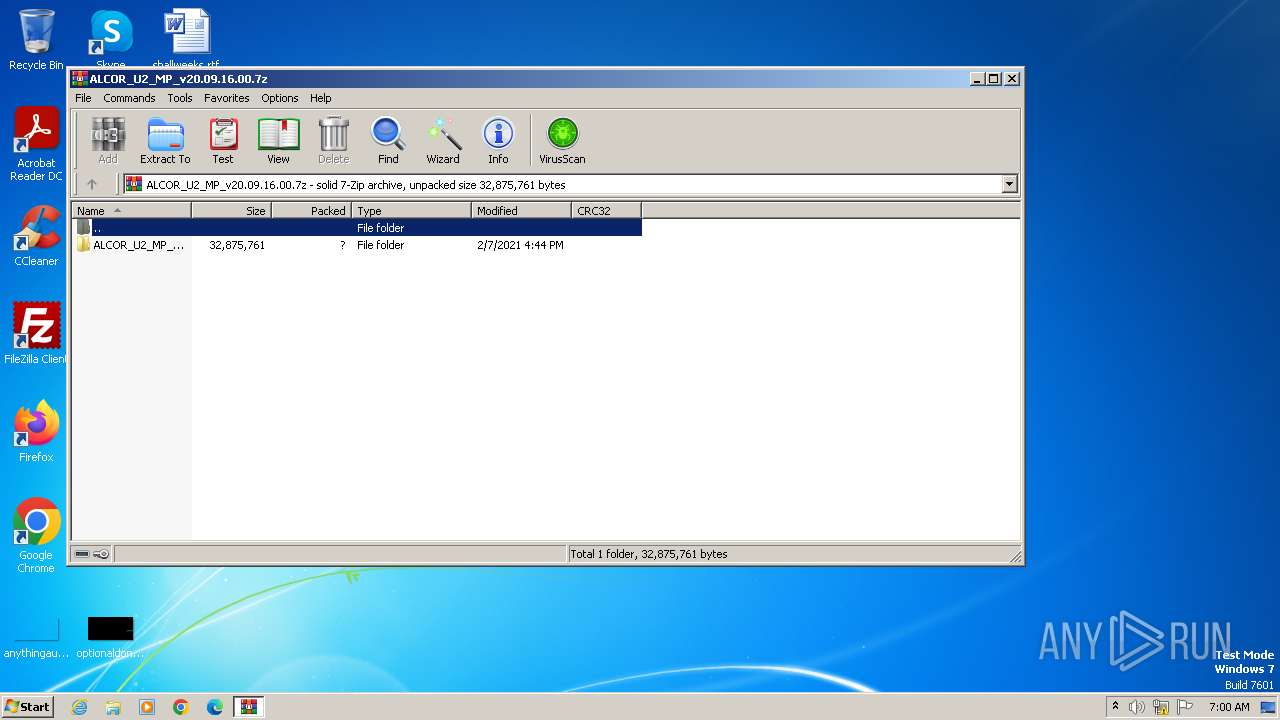
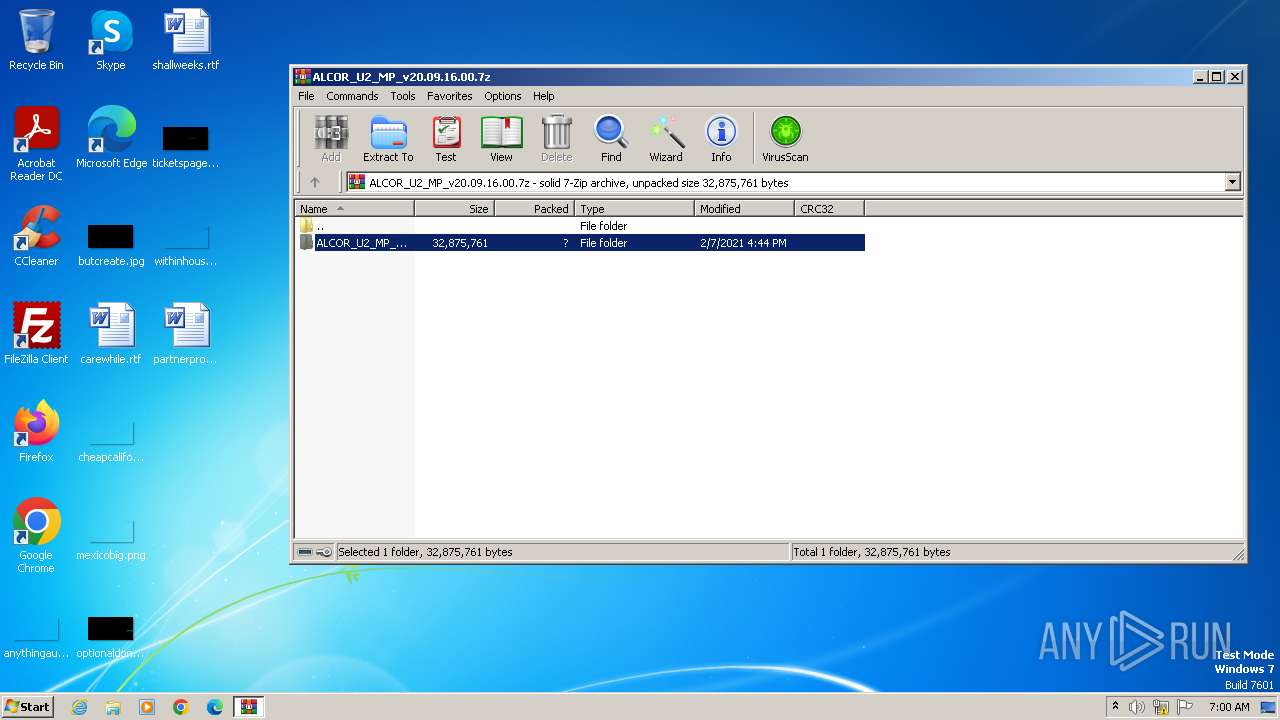
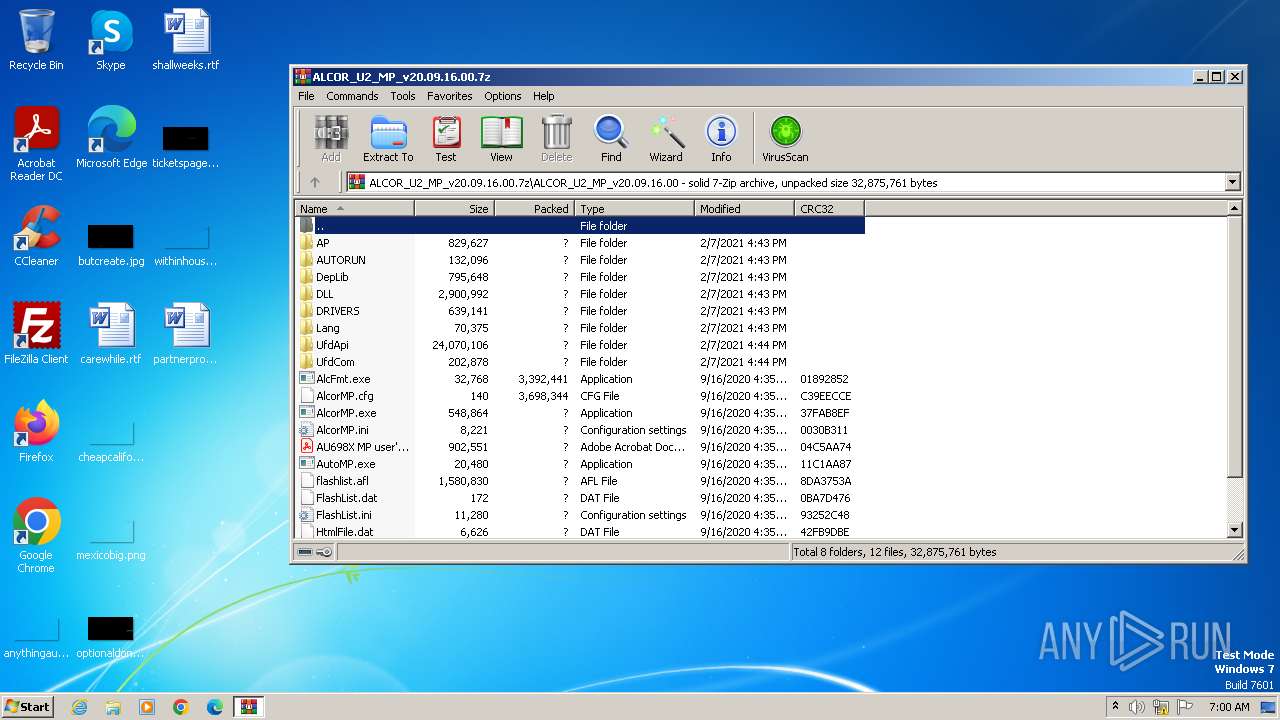
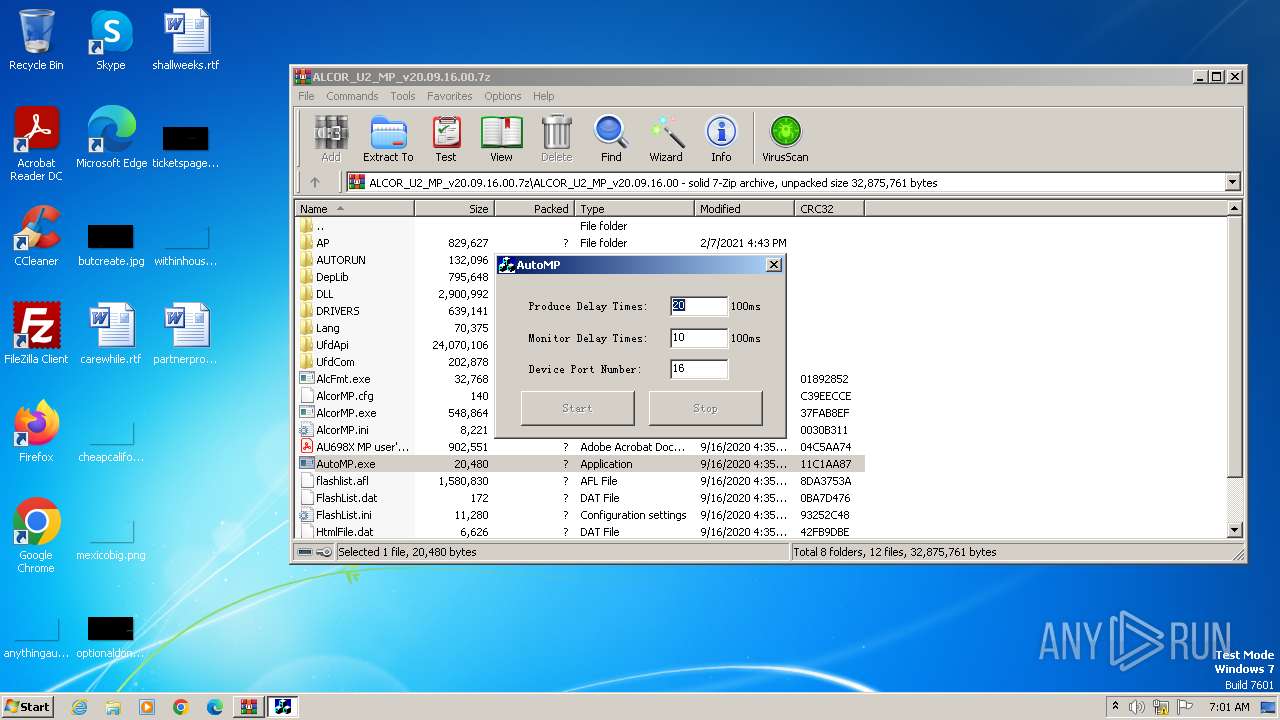
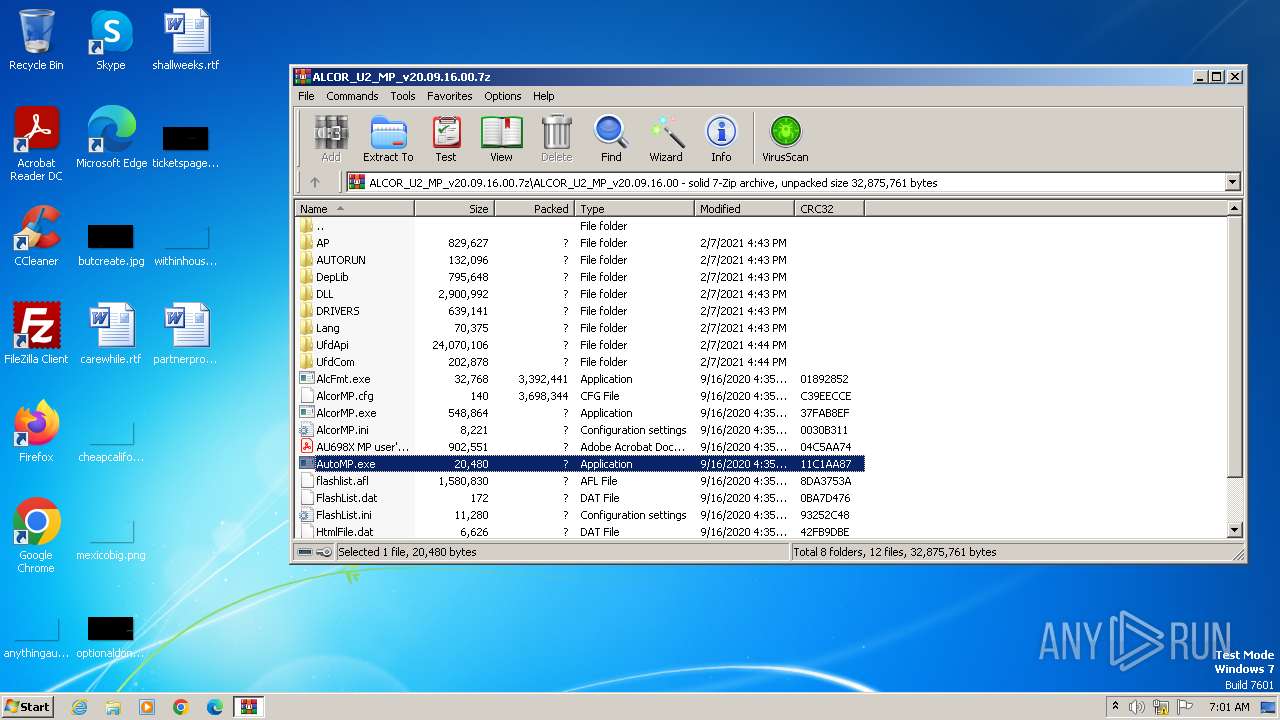
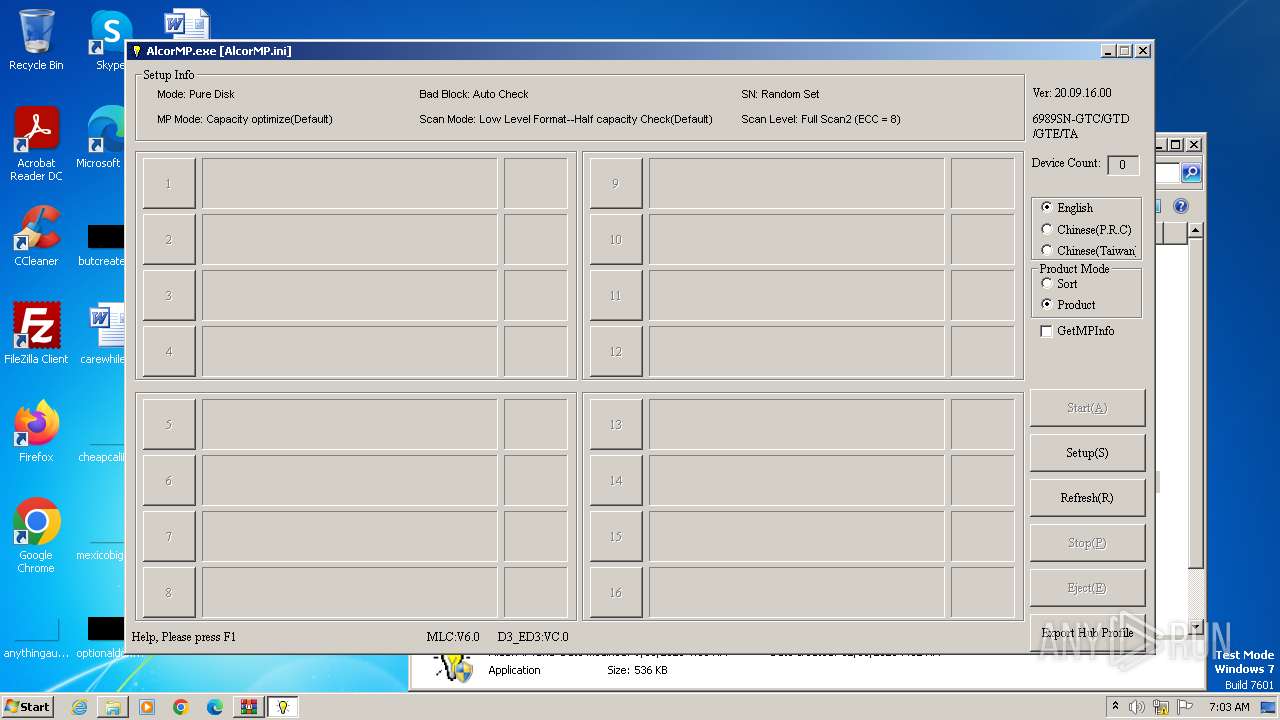
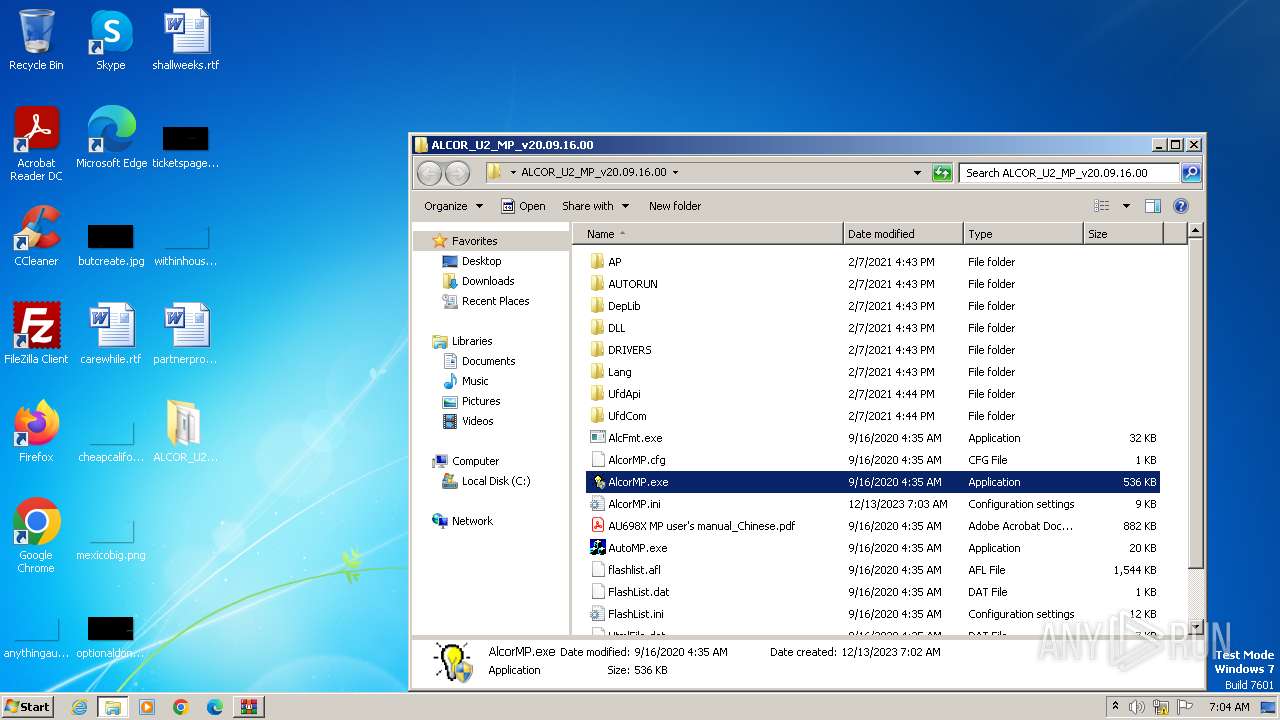
| File name: | ALCOR_U2_MP_v20.09.16.00.7z |
| Full analysis: | https://app.any.run/tasks/d60b5aa5-fc78-43fb-872c-54c60846fc88 |
| Verdict: | Malicious activity |
| Analysis date: | December 13, 2023, 07:00:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 9FBC9D40C2451418FA85082FDA5E36C0 |
| SHA1: | 5E679B8AA57BF5177FE25E611D6F7F7C8DE9F40D |
| SHA256: | 9A2E57E380D5CBEE33D6C3B00A521337D97C0F11FF712F2D516BCE1540AA10EA |
| SSDEEP: | 98304:6MOt0flQfkn2mDExSMQvhzlgjA47CMkkxgDk6SKawPXW3psZ0k1R/AdXPI7oMhGl:mexgUgqQOWXenhu |
MALICIOUS
Creates a writable file in the system directory
- LoadDrv.exe (PID: 1888)
Drops the executable file immediately after the start
- LoadDrv.exe (PID: 1888)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 2524)
- LoadDrv.exe (PID: 1888)
Creates files in the driver directory
- LoadDrv.exe (PID: 1888)
Connects to unusual port
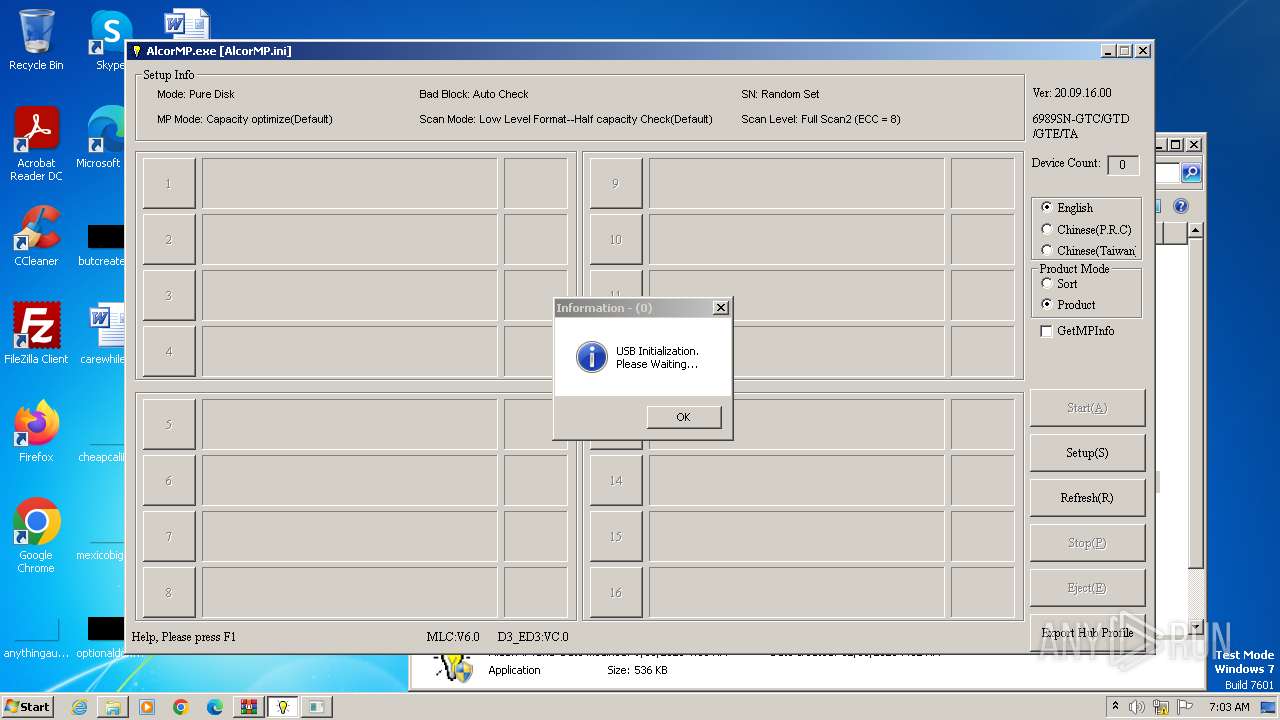
- AlcorMP.exe (PID: 3716)
INFO
Checks supported languages
- wmpnscfg.exe (PID: 2920)
- AutoMP.exe (PID: 3932)
- AutoMP.exe (PID: 944)
- AlcorMP.exe (PID: 3716)
- KillBaboon.exe (PID: 3460)
- LoadDrv.exe (PID: 968)
- LoadDrv.exe (PID: 1888)
- DrvCovEx.exe (PID: 984)
- VerifyCat.exe (PID: 3524)
- LoadDrv.exe (PID: 2916)
- KillBaboon.exe (PID: 2056)
- LoadDrv.exe (PID: 2940)
Reads the computer name
- wmpnscfg.exe (PID: 2920)
- AlcorMP.exe (PID: 3716)
- KillBaboon.exe (PID: 3460)
- LoadDrv.exe (PID: 1888)
- DrvCovEx.exe (PID: 984)
Manual execution by a user
- wmpnscfg.exe (PID: 2920)
- AutoMP.exe (PID: 944)
- AlcorMP.exe (PID: 3876)
- AlcorMP.exe (PID: 3716)
Application launched itself
- AcroRd32.exe (PID: 1116)
- RdrCEF.exe (PID: 3940)
Drops the executable file immediately after the start
- RdrCEF.exe (PID: 3940)
- WinRAR.exe (PID: 2524)
Create files in a temporary directory
- VerifyCat.exe (PID: 3524)
Reads the machine GUID from the registry
- VerifyCat.exe (PID: 3524)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
72
Monitored processes
24
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
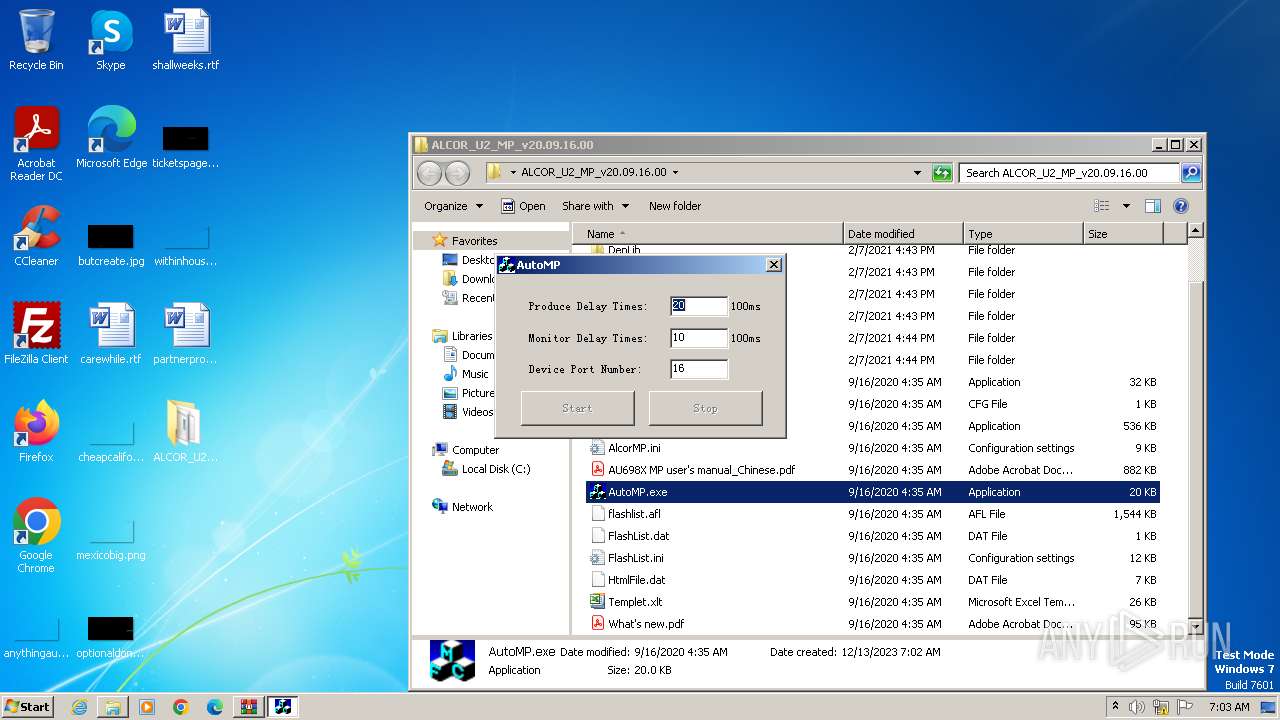
| 944 | "C:\Users\admin\Desktop\ALCOR_U2_MP_v20.09.16.00\AutoMP.exe" | C:\Users\admin\Desktop\ALCOR_U2_MP_v20.09.16.00\AutoMP.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: AutoMP Microsoft 基础类应用程序 Exit code: 2 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 968 | C:\Users\admin\Desktop\ALCOR_U2_MP_v20.09.16.00\drivers\LoadDrv.exe SetIgnoreHwID 058f6387 | C:\Users\admin\Desktop\ALCOR_U2_MP_v20.09.16.00\DRIVERS\LoadDrv.exe | — | AlcorMP.exe | |||||||||||
User: admin Company: ALCOR Integrity Level: HIGH Description: LoadDrv Exit code: 0 Version: 1, 2, 0, 0 Modules
| |||||||||||||||
| 984 | C:\Windows\system32\DrvCovEx.exe RegisterOnly DrvCovEx | C:\Windows\System32\DrvCovEx.exe | — | LoadDrv.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 1016 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --touch-events=enabled --field-trial-handle=1164,8243647319095041121,10362609712404587434,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-gpu-compositing --lang=en-US --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=12328738564227501697 --renderer-client-id=2 --mojo-platform-channel-handle=1172 --allow-no-sandbox-job /prefetch:1 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1116 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa2524.35889\AU698X MP user's manual_Chinese.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1352 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer "C:\Users\admin\AppData\Local\Temp\Rar$DIa2524.35889\AU698X MP user's manual_Chinese.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1888 | C:\Users\admin\Desktop\ALCOR_U2_MP_v20.09.16.00\drivers\LoadDrv.exe InstByIni | C:\Users\admin\Desktop\ALCOR_U2_MP_v20.09.16.00\DRIVERS\LoadDrv.exe | — | AlcorMP.exe | |||||||||||
User: admin Company: ALCOR Integrity Level: HIGH Description: LoadDrv Exit code: 0 Version: 1, 2, 0, 0 Modules
| |||||||||||||||
| 2028 | C:\Windows\System32\rundll32.exe shell32.dll,SHCreateLocalServerRunDll {995C996E-D918-4a8c-A302-45719A6F4EA7} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2056 | C:\Users\admin\Desktop\ALCOR_U2_MP_v20.09.16.00\drivers\KillBaboon.exe Once | C:\Users\admin\Desktop\ALCOR_U2_MP_v20.09.16.00\DRIVERS\KillBaboon.exe | — | LoadDrv.exe | |||||||||||
User: admin Integrity Level: HIGH Description: KillBaboon Exit code: 0 Version: 1, 2, 0, 0 Modules
| |||||||||||||||
| 2524 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\ALCOR_U2_MP_v20.09.16.00.7z" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
8 588
Read events
8 444
Write events
139
Delete events
5
Modification events
| (PID) Process: | (2524) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1352) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 1 | |||
| (PID) Process: | (1352) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral |
| Operation: | write | Name: | uLastAppLaunchTimeStamp |
Value: 738908672 | |||
Executable files
51
Suspicious files
264
Text files
531
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2524 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2524.35889\AU698X MP user's manual_Chinese.pdf | ||
MD5:57FC8257D01A08CB974FF5A44F19B5E8 | SHA256:1BCE74E048ACDF8D6878D7613E59CCC97A3B5BE0C7E5E0059E3D5631F7CEB1D7 | |||
| 1352 | AcroRd32.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Reader\Files\TESTING | binary | |
MD5:DC84B0D741E5BEAE8070013ADDCC8C28 | SHA256:81FF65EFC4487853BDB4625559E69AB44F19E0F5EFBD6D5B2AF5E3AB267C8E06 | |||
| 1352 | AcroRd32.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\Security\ES_session_storei | binary | |
MD5:C73BEC68085E957B08D29BED1AC299C3 | SHA256:135C01B699D9F78A13CA1590AB59CD01F2A508EFA799573827D8D6F1B7EC7349 | |||
| 1352 | AcroRd32.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Reader\SOPHIA.json | binary | |
MD5:01F233C92A89C705229A0D63D09F846A | SHA256:62137C4381ACC2DE8BCA158AD9D9CE730BD7A96A39A2FB64CE7CFA5C861CF7B4 | |||
| 3940 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\983b7a3da8f39a46_0 | binary | |
MD5:42D7074974A53832BC5B55EDB8D6F508 | SHA256:2F7D2813AA6F43B4D8199D261328152DBE1BA70B572CDE3DD1BA998560625EC5 | |||
| 3940 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\8c84d92a9dbce3e0_0 | binary | |
MD5:4C9F97A4250546989F75DCAFACFBC740 | SHA256:8536ECB7099994E5744EFB02B275D0D54C23D58E388006CFEF4485758533AEAD | |||
| 3940 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\8e417e79df3bf0e9_0 | binary | |
MD5:F79205D589E80D98DE390765C8C16F43 | SHA256:C45580524542136EC41703FC5176F48917C13974A03BF73D65ACE0EE9E783358 | |||
| 3940 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\92c56fa2a6c4d5ba_0 | binary | |
MD5:CCE1DBE3A34C6F61CEF4B2511CC6CCCE | SHA256:7825F024CA5ADAD265AECDEECAFAFD70D854C44F423D5FC410C2191F63F9D3E0 | |||
| 3940 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\560e9c8bff5008d8_0 | binary | |
MD5:E5E9309C8C08396ED429117839252629 | SHA256:DD95500D2F8D6FED5935D9EC05ED4C81658C8ADEF74608DD2A40BE6081ED484F | |||
| 3940 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\86b8040b7132b608_0 | binary | |
MD5:A76DC438CF2F9A6DA178A9C2CA254F42 | SHA256:3EC8F550160132A991FF5F1FED1475D3FA1BB528C1348C9C83AC06B02C1CA712 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
16
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
— | — | 192.168.100.162:49211 | — | — | — | unknown |
3716 | AlcorMP.exe | 10.5.100.215:34835 | — | — | — | unknown |
3716 | AlcorMP.exe | 16.1.64.254:34835 | — | — | US | unknown |
— | — | 192.168.100.162:49215 | — | — | — | unknown |
— | — | 192.168.100.162:49219 | — | — | — | unknown |