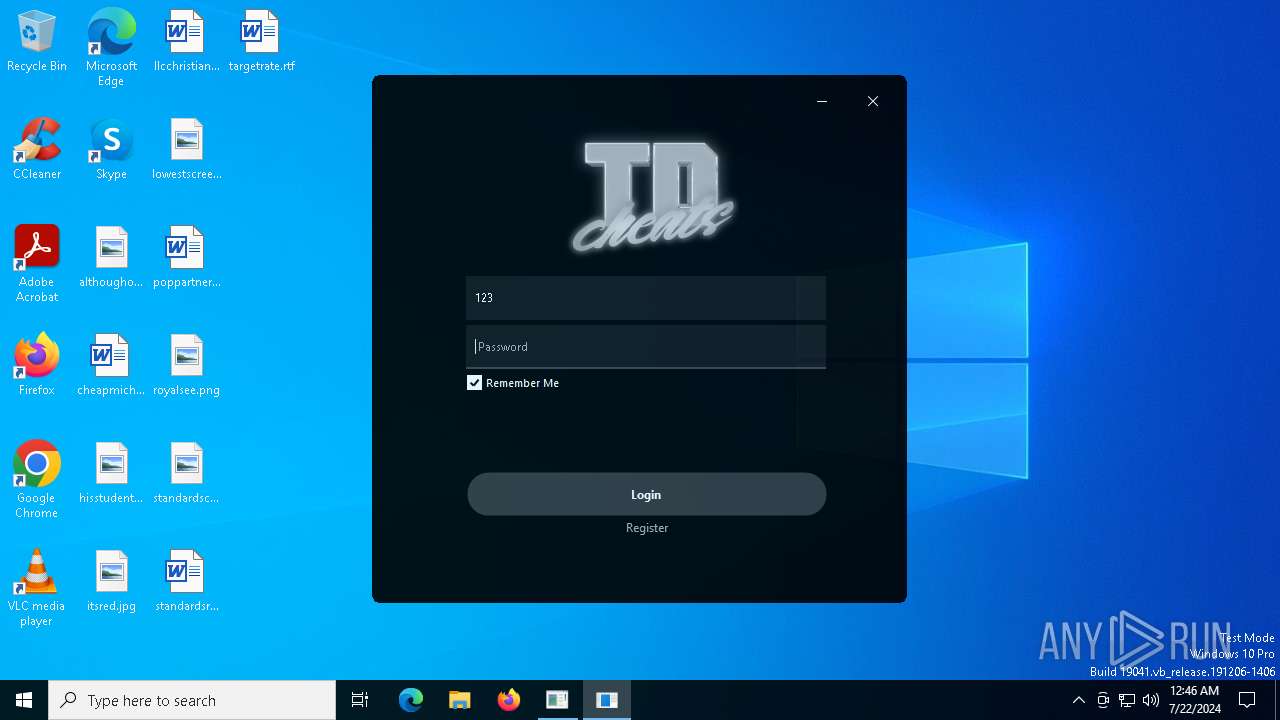
| File name: | discord.exe |
| Full analysis: | https://app.any.run/tasks/4524966f-d1f2-4d14-b2a5-48a0e6009337 |
| Verdict: | Malicious activity |
| Analysis date: | July 22, 2024, 00:45:45 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (console) x86-64, for MS Windows |
| MD5: | C86B001CC5E65B7F214740C5776DE1C9 |
| SHA1: | AA6C8C4AD02EB05B0B060AEC9EE82C4E2C575940 |
| SHA256: | 9A2513A43268DE41B3BEBEEEE9E48A5B2B626FD6402551830CBD91C5C6B533CC |
| SSDEEP: | 768:mSFfMY+jS2fPK4kJnyVDLpRWuhjgeFHP:jFfMY+jS2fPK4kALZJge |
MALICIOUS
Actions looks like stealing of personal data
- discord.exe (PID: 5768)
- conhost.exe (PID: 7088)
Drops the executable file immediately after the start
- discord.exe (PID: 5768)
Scans artifacts that could help determine the target
- discord.exe (PID: 5768)
SUSPICIOUS
Checks Windows Trust Settings
- discord.exe (PID: 5768)
The process creates files with name similar to system file names
- discord.exe (PID: 5768)
Executable content was dropped or overwritten
- discord.exe (PID: 5768)
Reads security settings of Internet Explorer
- discord.exe (PID: 5768)
There is functionality for taking screenshot (YARA)
- fontdrvhost.exe (PID: 4164)
INFO
Reads the computer name
- discord.exe (PID: 5768)
- fontdrvhost.exe (PID: 4164)
Reads the software policy settings
- discord.exe (PID: 5768)
- fontdrvhost.exe (PID: 4164)
Reads the machine GUID from the registry
- discord.exe (PID: 5768)
- fontdrvhost.exe (PID: 4164)
Checks proxy server information
- discord.exe (PID: 5768)
- fontdrvhost.exe (PID: 4164)
Creates files or folders in the user directory
- discord.exe (PID: 5768)
Checks supported languages
- discord.exe (PID: 5768)
- fontdrvhost.exe (PID: 4164)
Reads Environment values
- fontdrvhost.exe (PID: 4164)
Disables trace logs
- fontdrvhost.exe (PID: 4164)
Creates files in the program directory
- fontdrvhost.exe (PID: 4164)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:06:15 03:29:18+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.38 |
| CodeSize: | 17408 |
| InitializedDataSize: | 14336 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x4510 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
142
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4164 | C:\Windows\Temp\fontdrvhost.exe | C:\Windows\Temp\fontdrvhost.exe | discord.exe | ||||||||||||
User: admin Integrity Level: HIGH Version: 1.0 Modules
| |||||||||||||||
| 5768 | "C:\Users\admin\AppData\Local\Temp\discord.exe" | C:\Users\admin\AppData\Local\Temp\discord.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 6240 | "C:\Users\admin\AppData\Local\Temp\discord.exe" | C:\Users\admin\AppData\Local\Temp\discord.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 7088 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | discord.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 127
Read events
3 101
Write events
26
Delete events
0
Modification events
| (PID) Process: | (5768) discord.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (5768) discord.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (5768) discord.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (5768) discord.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (5768) discord.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5768) discord.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5768) discord.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4164) fontdrvhost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (4164) fontdrvhost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\fontdrvhost_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4164) fontdrvhost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\fontdrvhost_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
Executable files
4
Suspicious files
5
Text files
1
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4164 | fontdrvhost.exe | C:\ProgramData\KeyAuth\debug\fontdrvhost\Jul_22_2024_logs.txt | text | |
MD5:53DEC63CD45F1A699835AB76BA7EC8C6 | SHA256:4BC05B7EFC64AB995901DB0C8919A410B09A36FDB7B931F1C6F4189DCC8243AA | |||
| 5768 | discord.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\Guna.UI2[1].dll | executable | |
MD5:846A7E5993282E220B26B82E7A39A40A | SHA256:5613682635617CD43720807448F69B10090932E8571A358B92361D2A2C7A4597 | |||
| 5768 | discord.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_89854CA6A0F0936A4D2ECA78845CEA25 | binary | |
MD5:22ECE3A7F5B641967C177127A524FE7B | SHA256:6FF1FFB48CAC72BF9FC14A7959C9C5D1505D4A1B0E3EE5BADBAF6DE56FEB2545 | |||
| 5768 | discord.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_89854CA6A0F0936A4D2ECA78845CEA25 | der | |
MD5:77AFFE72D09834E6F82179985A7FE9CD | SHA256:CB77DA2B4FB45016A9A1B1D373D83A29D3325E775E91E5B6593C94044936FEA0 | |||
| 5768 | discord.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\A66A8DB907BADC9D16AD67B2FBFFDD5C | binary | |
MD5:FAECAFBC21BEE25CB92F72E8146206E3 | SHA256:D09CF6A5ED59C19355944753834FCC883D5EFA0D7BACAFD3A2C0885E45A70930 | |||
| 5768 | discord.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\D0E1C4B6144E7ECAB3F020E4A19EFC29_B5F77004C894173A10E3A199871D2D90 | binary | |
MD5:41645328E478BCD42E5DC810DE0D97E1 | SHA256:C7D2509F23FA0227A1503FC8681FABDA6FD7F9716EEC9747819DA850655073FF | |||
| 5768 | discord.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\D0E1C4B6144E7ECAB3F020E4A19EFC29_B5F77004C894173A10E3A199871D2D90 | der | |
MD5:2E391C412274D1668C846B871A31FC8E | SHA256:C6C49F6D207C73C2793CC00932F61F6F05A0DC5F79968A7B5E93A2F73FEDA411 | |||
| 5768 | discord.exe | C:\Windows\Temp\fontdrvhost.exe | executable | |
MD5:1AFA452A07A592A4281302E5217D922A | SHA256:42F3966319BCCB5D3C438A235DA324894493DC37D51E677210A1CA2FDCB2D739 | |||
| 5768 | discord.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\E4DJRUXW\fontdrvhost[1].exe | executable | |
MD5:1AFA452A07A592A4281302E5217D922A | SHA256:42F3966319BCCB5D3C438A235DA324894493DC37D51E677210A1CA2FDCB2D739 | |||
| 5768 | discord.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_49536AB5156BDD74EFF881D01C36A419 | der | |
MD5:7CFF46B0A3A19ADB658286DDF09AE6B6 | SHA256:FE9B634AFE36C0D40C79E1C1DC1A4FC7AF0505E14491FBF1980B4EAC0D365391 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
43
DNS requests
18
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5768 | discord.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEFZnHQTqT5lMbxCBR1nSdZQ%3D | unknown | — | — | whitelisted |
5768 | discord.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBSr83eyJy3njhjVpn5bEpfc6MXawQQUOuEJhtTPGcKWdnRJdtzgNcZjY5oCEQDzZE5rbgBQI34JRr174fUd | unknown | — | — | whitelisted |
5768 | discord.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPlNxcMEqnlIVyH5VuZ4lawhZX3QQU9oUKOxGG4QR9DqoLLNLuzGR7e64CEE4o94a2bBo7lCzSxA63QqU%3D | unknown | — | — | whitelisted |
5768 | discord.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAz1vQYrVgL0erhQLCPM8GY%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4716 | svchost.exe | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5620 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.209.32.198:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5768 | discord.exe | 140.82.121.3:443 | github.com | GITHUB | US | unknown |
5768 | discord.exe | 104.18.38.233:80 | ocsp.comodoca.com | CLOUDFLARENET | — | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
github.com |
| shared |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
raw.githubusercontent.com |
| shared |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2168 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
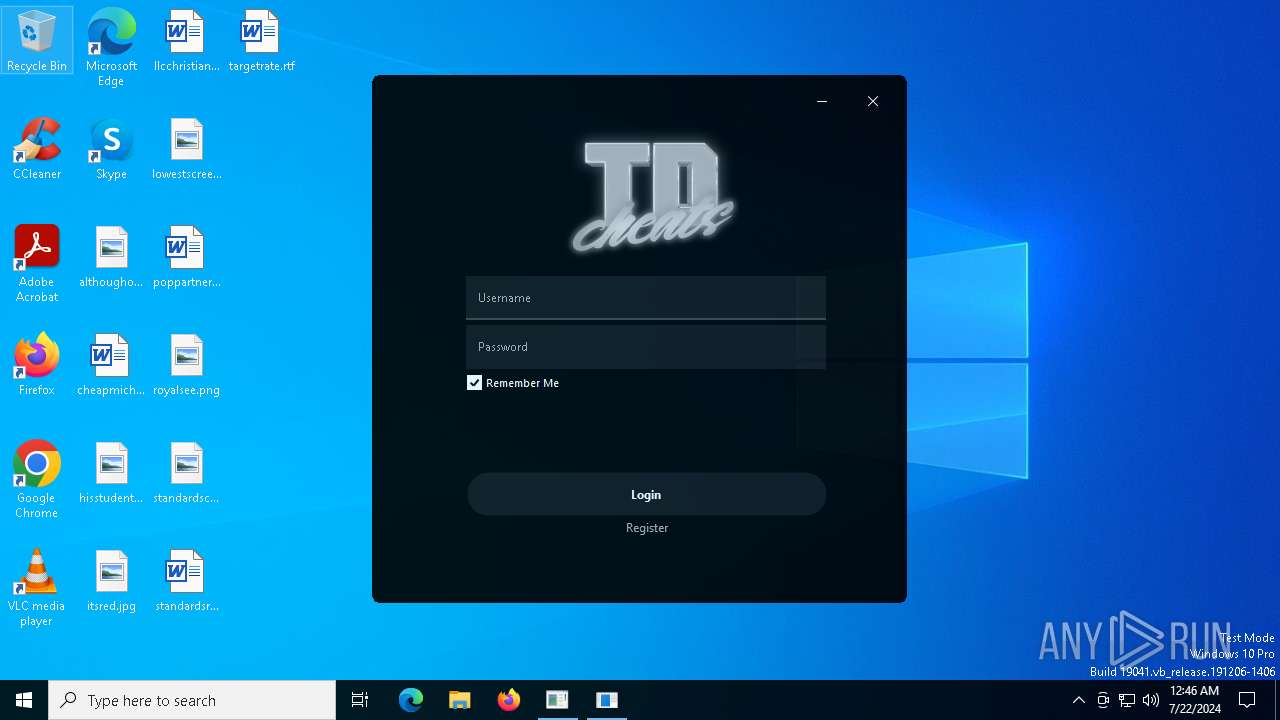
2168 | svchost.exe | Potentially Bad Traffic | ET INFO Fake Game Cheat Related Domain in DNS Lookup (keyauth .win) |
4164 | fontdrvhost.exe | Potentially Bad Traffic | ET INFO Fake Game Cheat Related Domain (keyauth .win) in TLS SNI |