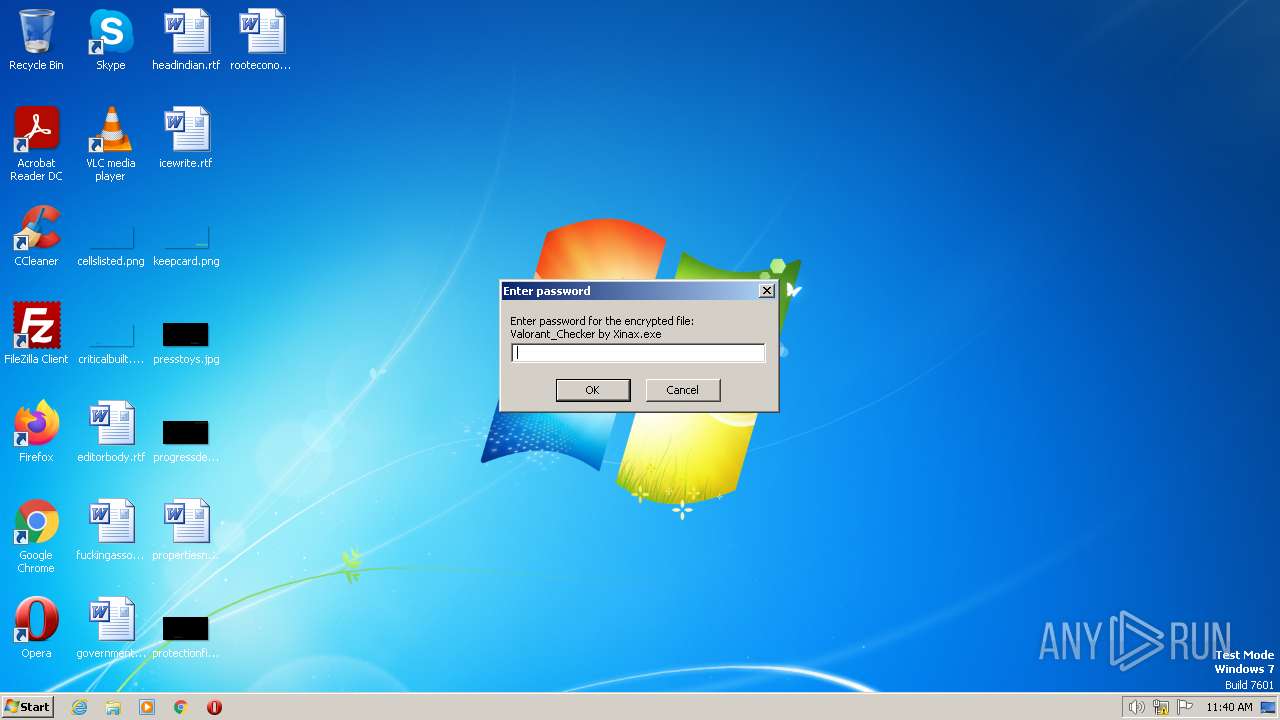
| File name: | Valorant Checker by Xinax.exe |
| Full analysis: | https://app.any.run/tasks/6aa18717-999d-47b1-b4d2-6ee731f487c6 |
| Verdict: | Malicious activity |
| Analysis date: | July 02, 2023, 10:40:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 737B4BEB0D2D9DF17F9CD77DD5DF149C |
| SHA1: | E54A157C6A7661AA3275213E5B35ABA21E79BBE8 |
| SHA256: | 9A1E210A7BF171FE6BCDEDDDAE899207D11F38122D4BEE14DFD4FE375A78DECF |
| SSDEEP: | 49152:IBJAfdK/QU9lR8V8gtCBrap0g5H6rZTvDS6zNwykkcak:yAdUB8uvBrap95Hmdvm6z2R |
MALICIOUS
Application was dropped or rewritten from another process
- Valorant Checker by Xinax.exe (PID: 3204)
- Valorant_Checker by Xinax.exe (PID: 1348)
Create files in the Startup directory
- Valorant_Checker by Xinax.exe (PID: 1348)
SUSPICIOUS
Reads the Internet Settings
- Valorant Checker by Xinax.exe (PID: 3416)
- Valorant Checker by Xinax.exe (PID: 3204)
Executable content was dropped or overwritten
- Valorant Checker by Xinax.exe (PID: 3416)
- Valorant_Checker by Xinax.exe (PID: 1348)
Checks for external IP
- Valorant Checker by Xinax.exe (PID: 3204)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 1852)
Executing commands from a ".bat" file
- Valorant Checker by Xinax.exe (PID: 3204)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 1852)
Starts application with an unusual extension
- cmd.exe (PID: 1852)
Reads settings of System Certificates
- Valorant Checker by Xinax.exe (PID: 3204)
Starts CMD.EXE for commands execution
- Valorant Checker by Xinax.exe (PID: 3204)
INFO
Checks supported languages
- Valorant Checker by Xinax.exe (PID: 3416)
- Valorant Checker by Xinax.exe (PID: 3204)
- chcp.com (PID: 1640)
- Valorant_Checker by Xinax.exe (PID: 1348)
Create files in a temporary directory
- Valorant Checker by Xinax.exe (PID: 3416)
- Valorant Checker by Xinax.exe (PID: 3204)
The process checks LSA protection
- Valorant Checker by Xinax.exe (PID: 3416)
- Valorant Checker by Xinax.exe (PID: 3204)
- taskkill.exe (PID: 2824)
- Valorant_Checker by Xinax.exe (PID: 1348)
Reads the computer name
- Valorant Checker by Xinax.exe (PID: 3416)
- Valorant Checker by Xinax.exe (PID: 3204)
- Valorant_Checker by Xinax.exe (PID: 1348)
Reads the machine GUID from the registry
- Valorant Checker by Xinax.exe (PID: 3204)
- Valorant_Checker by Xinax.exe (PID: 1348)
Creates files or folders in the user directory
- Valorant_Checker by Xinax.exe (PID: 1348)
Manual execution by a user
- opera.exe (PID: 2896)
Reads Environment values
- Valorant Checker by Xinax.exe (PID: 3204)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| Subsystem: | Windows GUI |
|---|---|
| SubsystemVersion: | 5.1 |
| ImageVersion: | - |
| OSVersion: | 5.1 |
| EntryPoint: | 0x1f530 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 261632 |
| CodeSize: | 203776 |
| LinkerVersion: | 14.3 |
| PEType: | PE32 |
| ImageFileCharacteristics: | Executable, 32-bit |
| TimeStamp: | 2022:03:03 13:15:57+00:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 03-Mar-2022 13:15:57 |
| Detected languages: |
|
| Debug artifacts: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000110 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 6 |
| Time date stamp: | 03-Mar-2022 13:15:57 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00031BDC | 0x00031C00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.71296 |
.rdata | 0x00033000 | 0x0000AEC0 | 0x0000B000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.26161 |
.data | 0x0003E000 | 0x00024720 | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.38746 |
.didat | 0x00063000 | 0x00000190 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.33273 |
.rsrc | 0x00064000 | 0x0000DFF8 | 0x0000E000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.63866 |
.reloc | 0x00072000 | 0x0000233C | 0x00002400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.62301 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.25329 | 1875 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 5.10026 | 2216 | UNKNOWN | English - United States | RT_ICON |
3 | 5.25868 | 3752 | UNKNOWN | English - United States | RT_ICON |
4 | 5.02609 | 1128 | UNKNOWN | English - United States | RT_ICON |
5 | 5.18109 | 4264 | UNKNOWN | English - United States | RT_ICON |
6 | 5.04307 | 9640 | UNKNOWN | English - United States | RT_ICON |
7 | 3.1586 | 482 | UNKNOWN | English - United States | RT_STRING |
8 | 3.11685 | 460 | UNKNOWN | English - United States | RT_STRING |
9 | 3.11236 | 440 | UNKNOWN | English - United States | RT_STRING |
10 | 2.99727 | 326 | UNKNOWN | English - United States | RT_STRING |
Imports
KERNEL32.dll |
OLEAUT32.dll |
USER32.dll (delay-loaded) |
gdiplus.dll |
Total processes
45
Monitored processes
8
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1348 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\Valorant_Checker by Xinax.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\Valorant_Checker by Xinax.exe | Valorant Checker by Xinax.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Google Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1640 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1852 | "C:\Windows\System32\cmd.exe" /C C:\Users\admin\AppData\Local\Temp\tmp25DF.tmp.bat | C:\Windows\System32\cmd.exe | — | Valorant Checker by Xinax.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2824 | TaskKill /F /IM 3204 | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2896 | "C:\Program Files\Opera\opera.exe" | C:\Program Files\Opera\opera.exe | explorer.exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: MEDIUM Description: Opera Internet Browser Exit code: 0 Version: 1748 Modules
| |||||||||||||||
| 3204 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\Valorant Checker by Xinax.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\Valorant Checker by Xinax.exe | Valorant Checker by Xinax.exe | ||||||||||||
User: admin Company: market.eu Integrity Level: MEDIUM Description: market.eu Exit code: 1 Version: 2.5.2.1 Modules
| |||||||||||||||
| 3224 | Timeout /T 2 /Nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3416 | "C:\Users\admin\AppData\Local\Temp\Valorant Checker by Xinax.exe" | C:\Users\admin\AppData\Local\Temp\Valorant Checker by Xinax.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
4 697
Read events
4 610
Write events
87
Delete events
0
Modification events
| (PID) Process: | (3416) Valorant Checker by Xinax.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3416) Valorant Checker by Xinax.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3416) Valorant Checker by Xinax.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3416) Valorant Checker by Xinax.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3204) Valorant Checker by Xinax.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3204) Valorant Checker by Xinax.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3204) Valorant Checker by Xinax.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3204) Valorant Checker by Xinax.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3204) Valorant Checker by Xinax.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2896) opera.exe | Key: | HKEY_CURRENT_USER\Software\Opera Software |
| Operation: | write | Name: | Last CommandLine v2 |
Value: C:\Program Files\Opera\opera.exe | |||
Executable files
3
Suspicious files
3
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2896 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opr365A.tmp | text | |
MD5:611E5199785121BF16E77FAA216E9A6F | SHA256:A37DD11486E6901DDCC0067545E69D768179CBEA8A44F3C791FA8E1D4BBDBD22 | |||
| 2896 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\AP02ZFYET1SQ50I4R7AM.temp | binary | |
MD5:FDBCDB294DED05EA01DCAA246B98C2C5 | SHA256:EAEC5A291DBC8E8760BAB0C1BB27CB801F671166CE85310FD173F54111357C4B | |||
| 2896 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\operaprefs.ini | text | |
MD5:611E5199785121BF16E77FAA216E9A6F | SHA256:A37DD11486E6901DDCC0067545E69D768179CBEA8A44F3C791FA8E1D4BBDBD22 | |||
| 2896 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opr36A9.tmp | xml | |
MD5:DFC2E670D6ADEBD80A7D54C5E1DA0A24 | SHA256:9EE4AC7A8F24FBF55D9B8C040DE5028AAB66BDAF0E099007C977E065A5A52967 | |||
| 3204 | Valorant Checker by Xinax.exe | C:\Users\admin\AppData\Local\Temp\tmp25DF.tmp.bat | text | |
MD5:4DA0B184BFA506C657E1704C3408742A | SHA256:12128AD2FD4AD204B4CCC5800649AA4C8FE0908F85A7F7607F3458808C9B69D6 | |||
| 2896 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\16ec093b8f51508f.customDestinations-ms~RF124176.TMP | binary | |
MD5:DBC8C3C79F0DFF4745A5E25E13611AEF | SHA256:70C54F2C53CF246603B8DE4755D95C5AA51BF4B232340BEA5879724A1F84F675 | |||
| 3416 | Valorant Checker by Xinax.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Valorant Checker by Xinax.exe | executable | |
MD5:5989BAA8CB04CA6BA45E71744937D96C | SHA256:FE9004DC4EAB9BB39F2D66DE153863EC5B097993DECBA65EEC005093CD839C62 | |||
| 3204 | Valorant Checker by Xinax.exe | C:\Users\admin\AppData\Local\Temp\Stealerium-Latest.log | text | |
MD5:1AC47A28CABC6B7B63A8C78C0DB4C1C3 | SHA256:4515D5487CE70CDA38DE9ADE119E29992BD27F362D5DC046B804A0BC2EB50032 | |||
| 2896 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\16ec093b8f51508f.customDestinations-ms | binary | |
MD5:FDBCDB294DED05EA01DCAA246B98C2C5 | SHA256:EAEC5A291DBC8E8760BAB0C1BB27CB801F671166CE85310FD173F54111357C4B | |||
| 3416 | Valorant Checker by Xinax.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Valorant_Checker by Xinax.exe | executable | |
MD5:9AC1D433D1648B9AC8D90A1B13A938FE | SHA256:24E15BCECDEF5DE18450AD9274701D119212FA6DB1F848F686950107EB524AD0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
12
DNS requests
4
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3204 | Valorant Checker by Xinax.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | text | 5 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2816 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1076 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3204 | Valorant Checker by Xinax.exe | 162.159.128.233:443 | discord.com | CLOUDFLARENET | — | malicious |
3204 | Valorant Checker by Xinax.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | malicious |
2896 | opera.exe | 185.26.182.93:443 | certs.opera.com | Opera Software AS | — | whitelisted |
2896 | opera.exe | 185.26.182.94:443 | certs.opera.com | Opera Software AS | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ip-api.com |
| malicious |
discord.com |
| whitelisted |
certs.opera.com |
| whitelisted |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3204 | Valorant Checker by Xinax.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
3204 | Valorant Checker by Xinax.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
3204 | Valorant Checker by Xinax.exe | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] External Hosting Lookup by ip-api |
1076 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
3204 | Valorant Checker by Xinax.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |