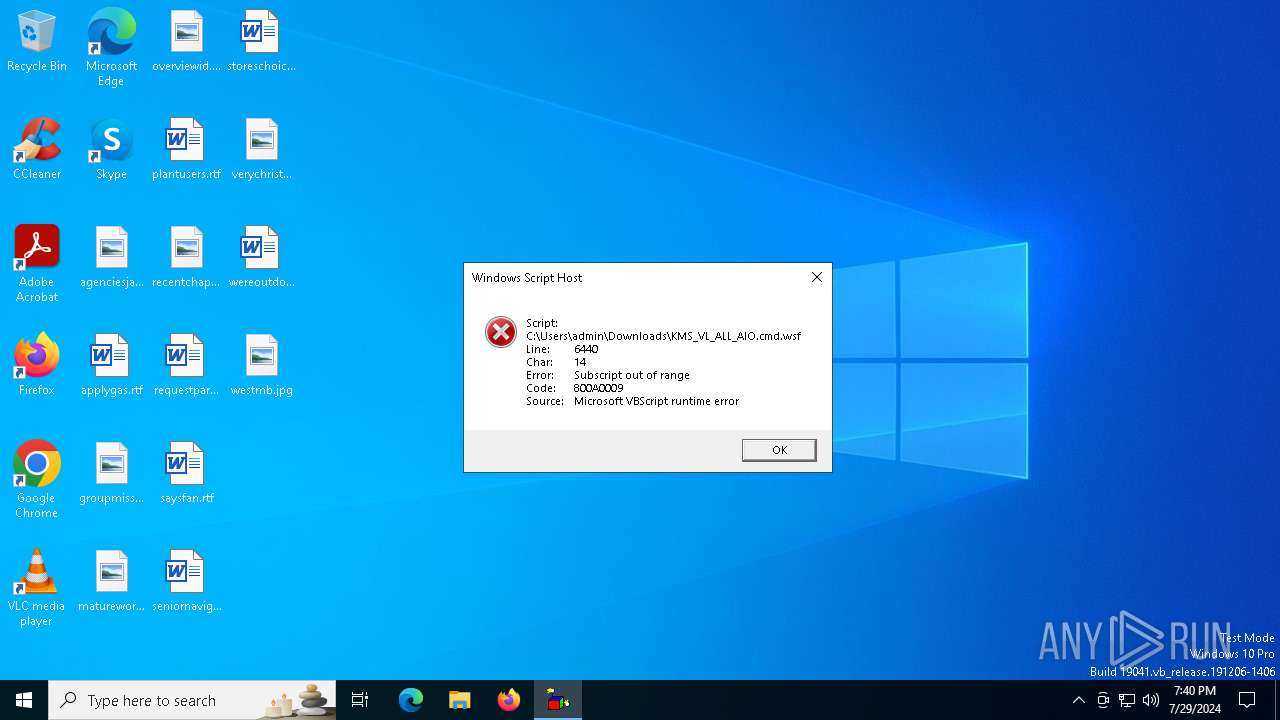
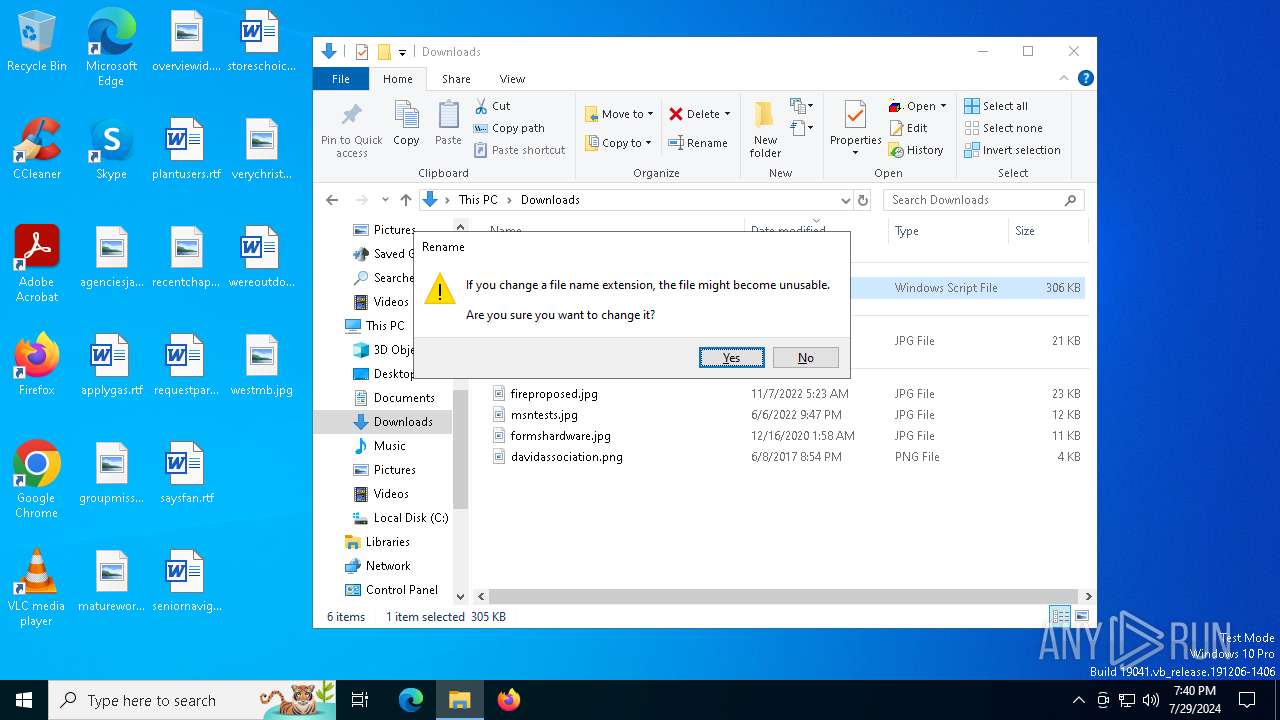
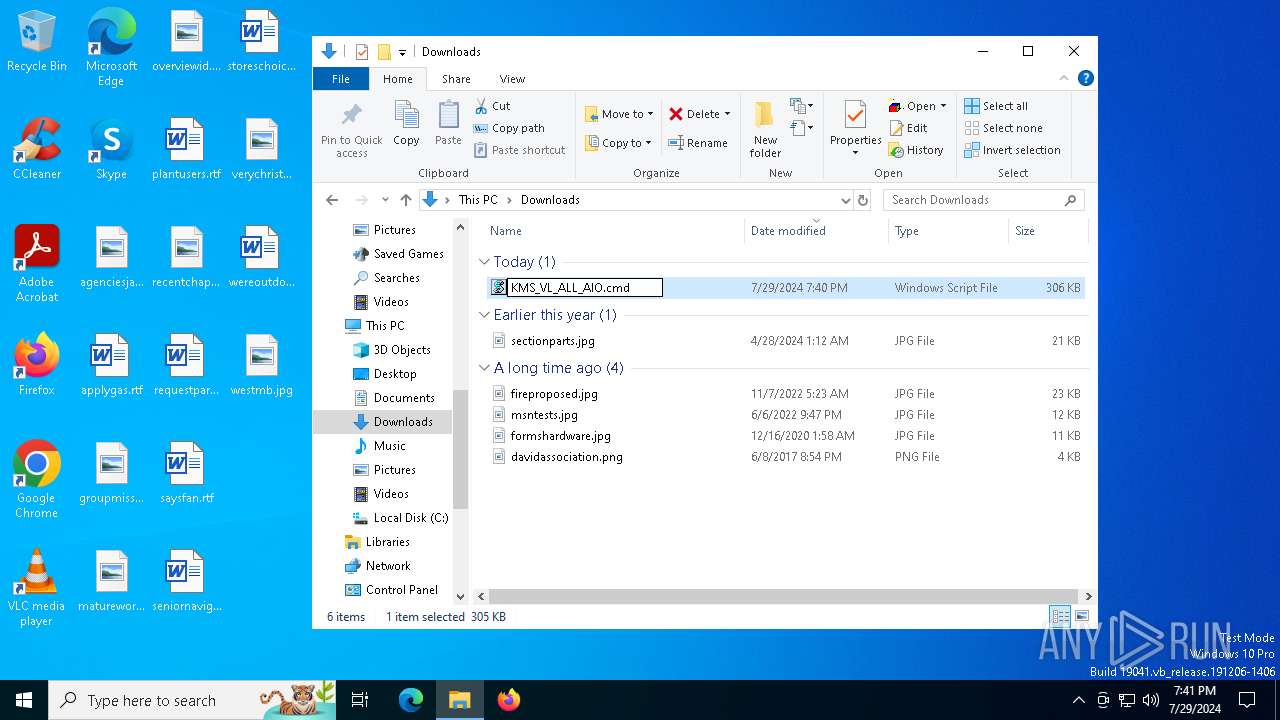
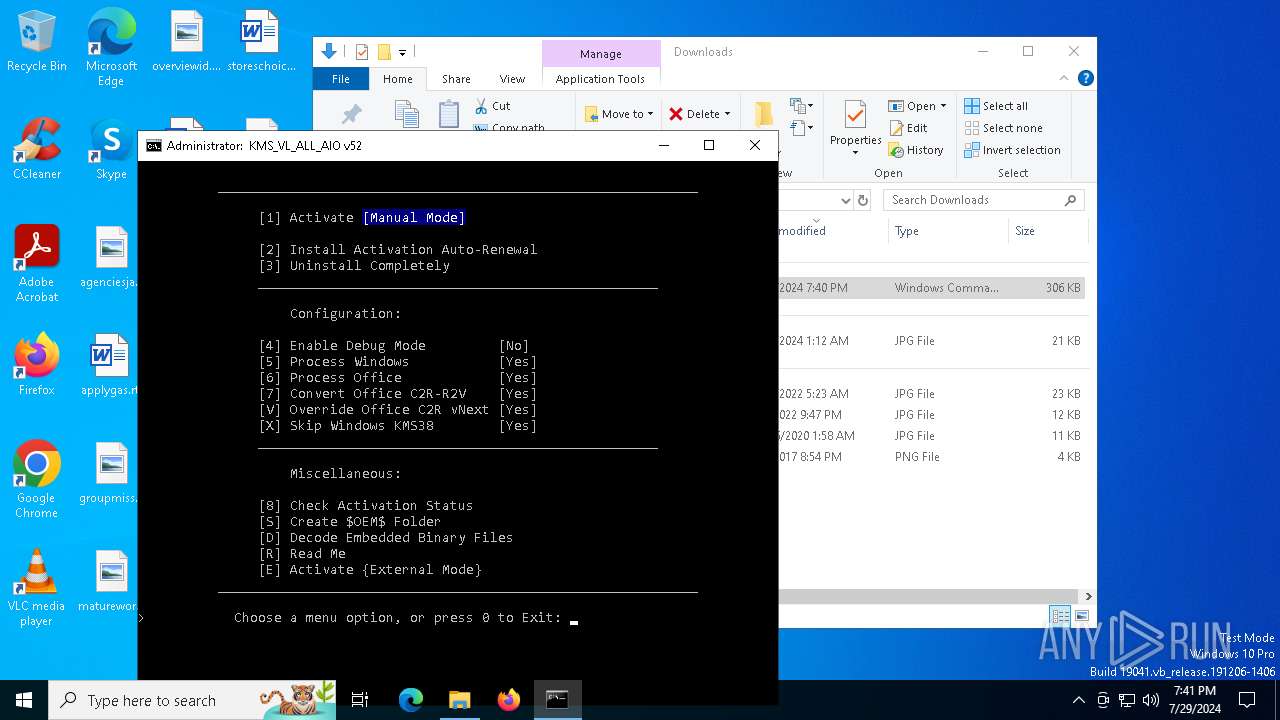
| File name: | KMS_VL_ALL_AIO.cmd |
| Full analysis: | https://app.any.run/tasks/2844faa7-6093-4c70-ab3c-19f7932abb2f |
| Verdict: | Malicious activity |
| Analysis date: | July 29, 2024, 19:40:30 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | exported SGML document, ASCII text, with CRLF line terminators |
| MD5: | 33F59B72AAA2D7257384F15E5FD9A536 |
| SHA1: | F2B980813FC36E39BFA45E14BF87EC18368A3CF4 |
| SHA256: | 9A1CEB9BF93C1A7C920105B55755EA8D773F24989A0A0179D5D9F5A891E9D37A |
| SSDEEP: | 6144:YTJ9JzFmdIc8dGT6SLCc6Ekr6gIeQ6TsHjcqBD+N8H5:yJ9JzoIcfN6EkrzISTsHAqN26 |
MALICIOUS
Starts NET.EXE for service management
- cmd.exe (PID: 6064)
- net.exe (PID: 5040)
- net.exe (PID: 5192)
Uses WMIC.EXE to add exclusions to the Windows Defender
- cmd.exe (PID: 6064)
Drops the executable file immediately after the start
- powershell.exe (PID: 2508)
- csc.exe (PID: 3944)
SUSPICIOUS
Application launched itself
- cmd.exe (PID: 4052)
- cmd.exe (PID: 6064)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6064)
- cmd.exe (PID: 4052)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 6064)
- cmd.exe (PID: 4052)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 4052)
- cmd.exe (PID: 6064)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 4052)
- cmd.exe (PID: 6064)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 4052)
- cscript.exe (PID: 6648)
- cmd.exe (PID: 6064)
Runs shell command (SCRIPT)
- cscript.exe (PID: 6648)
Uses RUNDLL32.EXE to load library
- cscript.exe (PID: 6648)
Executing commands from ".cmd" file
- cscript.exe (PID: 6648)
Hides command output
- cmd.exe (PID: 4376)
- cmd.exe (PID: 6364)
- cmd.exe (PID: 4068)
- cmd.exe (PID: 2300)
- cmd.exe (PID: 6164)
- cmd.exe (PID: 3360)
- cmd.exe (PID: 7008)
- cmd.exe (PID: 6632)
- cmd.exe (PID: 1476)
- cmd.exe (PID: 3188)
- cmd.exe (PID: 4376)
- cmd.exe (PID: 5268)
- cmd.exe (PID: 208)
- cmd.exe (PID: 1800)
- cmd.exe (PID: 1084)
- cmd.exe (PID: 6888)
- cmd.exe (PID: 7052)
- cmd.exe (PID: 204)
- cmd.exe (PID: 396)
- cmd.exe (PID: 2520)
- cmd.exe (PID: 488)
- cmd.exe (PID: 6224)
- cmd.exe (PID: 788)
Starts SC.EXE for service management
- cmd.exe (PID: 6064)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6064)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 6064)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 2508)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 6064)
Gets content of a file (POWERSHELL)
- powershell.exe (PID: 2508)
Executable content was dropped or overwritten
- csc.exe (PID: 3944)
- powershell.exe (PID: 2508)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 2508)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 2300)
- cmd.exe (PID: 6064)
- cmd.exe (PID: 5192)
- cmd.exe (PID: 528)
Uses WMIC.EXE to obtain service application data
- cmd.exe (PID: 3384)
- cmd.exe (PID: 6064)
- cmd.exe (PID: 6316)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 624)
The process executes VB scripts
- cmd.exe (PID: 6064)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 624)
INFO
Manual execution by a user
- cmd.exe (PID: 4052)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 3568)
- cscript.exe (PID: 6648)
- WMIC.exe (PID: 3140)
- WMIC.exe (PID: 4808)
- WMIC.exe (PID: 4544)
- WMIC.exe (PID: 1340)
- WMIC.exe (PID: 456)
- WMIC.exe (PID: 2632)
- WMIC.exe (PID: 6440)
- WMIC.exe (PID: 5592)
- WMIC.exe (PID: 2508)
- WMIC.exe (PID: 6164)
- WMIC.exe (PID: 4808)
- WMIC.exe (PID: 7040)
- WMIC.exe (PID: 1992)
- WMIC.exe (PID: 1176)
- WMIC.exe (PID: 1620)
- WMIC.exe (PID: 5396)
- WMIC.exe (PID: 6224)
- cscript.exe (PID: 624)
- WMIC.exe (PID: 2976)
- WMIC.exe (PID: 4076)
- WMIC.exe (PID: 5632)
- WMIC.exe (PID: 2508)
- WMIC.exe (PID: 6584)
- WMIC.exe (PID: 6812)
- WMIC.exe (PID: 788)
Checks operating system version
- cmd.exe (PID: 6064)
Reads Microsoft Office registry keys
- reg.exe (PID: 6688)
- reg.exe (PID: 5268)
- reg.exe (PID: 1084)
- reg.exe (PID: 6652)
- reg.exe (PID: 6076)
- reg.exe (PID: 4388)
- reg.exe (PID: 6872)
- reg.exe (PID: 2928)
- reg.exe (PID: 2100)
- reg.exe (PID: 5624)
- reg.exe (PID: 3484)
- reg.exe (PID: 2100)
- reg.exe (PID: 2200)
- reg.exe (PID: 3392)
- reg.exe (PID: 4868)
- reg.exe (PID: 6432)
- reg.exe (PID: 208)
- reg.exe (PID: 892)
- reg.exe (PID: 4608)
- reg.exe (PID: 892)
- reg.exe (PID: 6736)
- reg.exe (PID: 4316)
- reg.exe (PID: 1712)
- reg.exe (PID: 6676)
- reg.exe (PID: 7148)
- reg.exe (PID: 2816)
- reg.exe (PID: 6676)
- reg.exe (PID: 6164)
- reg.exe (PID: 1328)
Checks supported languages
- mode.com (PID: 7036)
- csc.exe (PID: 3944)
- cvtres.exe (PID: 2300)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 2508)
Gets a random number, or selects objects randomly from a collection (POWERSHELL)
- powershell.exe (PID: 2508)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 2508)
Reads the machine GUID from the registry
- csc.exe (PID: 3944)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .wsf | | | Windows Script File (72.7) |
|---|---|---|
| .html | | | HyperText Markup Language (27.2) |
Total processes
638
Monitored processes
494
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | C:\WINDOWS\system32\cmd.exe /c ECHO Microsoft-Windows-ProfessionalEdition~31bf3856ad364e35~amd64~~10.0.19041.4046 | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 204 | C:\WINDOWS\system32\cmd.exe /c "reg query HKLM\SOFTWARE\WOW6432Node\Microsoft\Office\ClickToRun /v InstallPath" 2>nul | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 204 | findstr /I /C:"ProPlus2019Volume" "C:\WINDOWS\Temp\crvProductIds.txt" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 204 | findstr /I /C:"HomeBusiness2021Retail" "C:\WINDOWS\Temp\crvProductIds.txt" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 204 | find /i "Office16Professional2019VL_MAK" "C:\WINDOWS\Temp\crvRetail.txt" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 204 | findstr /I /C:"ProjectStd2019Retail" "C:\WINDOWS\Temp\crvProductIds.txt" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 204 | findstr /I /C:"OneNoteRetail" "C:\WINDOWS\Temp\crvProductIds.txt" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 208 | C:\WINDOWS\system32\cmd.exe /c "prompt #$H#$E# & echo on & for %B in (1) do rem" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 208 | FIND /I "0x70" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 208 | C:\WINDOWS\system32\cmd.exe /c "reg query HKLM\SOFTWARE\WOW6432Node\Microsoft\Office\16.0\Common\InstallRoot /v Path" 2>nul | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
36 595
Read events
36 570
Write events
25
Delete events
0
Modification events
| (PID) Process: | (6648) cscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6648) cscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6648) cscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6648) cscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3940) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\CurrentVersion\Software Protection Platform |
| Operation: | write | Name: | NoGenTicket |
Value: 1 | |||
| (PID) Process: | (6688) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SppExtComObj.exe |
| Operation: | write | Name: | VerifierDlls |
Value: SppExtComObjHook.dll | |||
| (PID) Process: | (5124) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SppExtComObj.exe |
| Operation: | write | Name: | VerifierDebug |
Value: 0 | |||
| (PID) Process: | (6340) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SppExtComObj.exe |
| Operation: | write | Name: | VerifierFlags |
Value: | |||
| (PID) Process: | (3524) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SppExtComObj.exe |
| Operation: | write | Name: | GlobalFlag |
Value: 256 | |||
| (PID) Process: | (1328) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SppExtComObj.exe |
| Operation: | write | Name: | KMS_Emulation |
Value: 1 | |||
Executable files
2
Suspicious files
3
Text files
17
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2748 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_knzrcw54.jwk.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1176 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_3qsfbtry.12j.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2748 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ubk5guib.gkr.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2508 | powershell.exe | C:\Windows\Temp\__PSScriptPolicyTest_t4c0znrz.iuy.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2508 | powershell.exe | C:\Windows\Temp\__PSScriptPolicyTest_rwx1oiie.gnb.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5124 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_vjqidovf.lq5.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2508 | powershell.exe | C:\Windows\Temp\1fxsj4ep\1fxsj4ep.0.cs | text | |
MD5:EAFBB318108FC62A15B458EBBA405940 | SHA256:45EE3DD57AA47FCF92C09A44276DE5EF1688BB0563E09206D8E882528E6DE9D2 | |||
| 2748 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:09DA3CC9F1FB537FCE1870351DF9DB2E | SHA256:DD6C70B8C193D2E0D3BE7630F1FB959B3B6451B7808CC4E3022F746592929666 | |||
| 2508 | powershell.exe | C:\Windows\System32\SppExtComObjHook.dll | executable | |
MD5:5EE1DD6608439D755F7161BB83C62216 | SHA256:5420B32332112564AB739D2305BBA45F0C6559A708C360BF76BECF8EF0CFBA7A | |||
| 3944 | csc.exe | C:\Windows\Temp\1fxsj4ep\1fxsj4ep.dll | executable | |
MD5:040E054F2F040646879FFA618E8150D1 | SHA256:25E2A17BC239F1E23C042EC3EB79BB937362A153356D96078A9E331448D30BD0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
41
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4424 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
6828 | backgroundTaskHost.exe | GET | — | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3676 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6828 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://crl3.digicert.com/DigiCertGlobalRootG2.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
996 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6012 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5368 | SearchApp.exe | 131.253.33.254:443 | a-ring-fallback.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
5368 | SearchApp.exe | 95.100.146.19:443 | www.bing.com | Akamai International B.V. | CZ | unknown |
6412 | slui.exe | 40.91.76.224:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4560 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1620 | slui.exe | 40.91.76.224:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
a-ring-fallback.msedge.net |
| unknown |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
fp-afd-nocache-ccp.azureedge.net |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
th.bing.com |
| whitelisted |