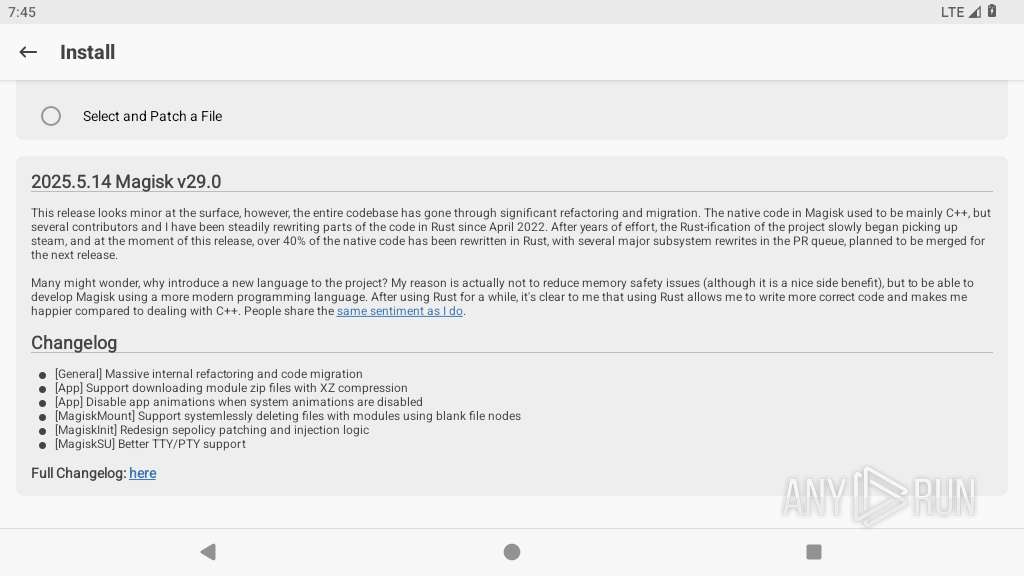
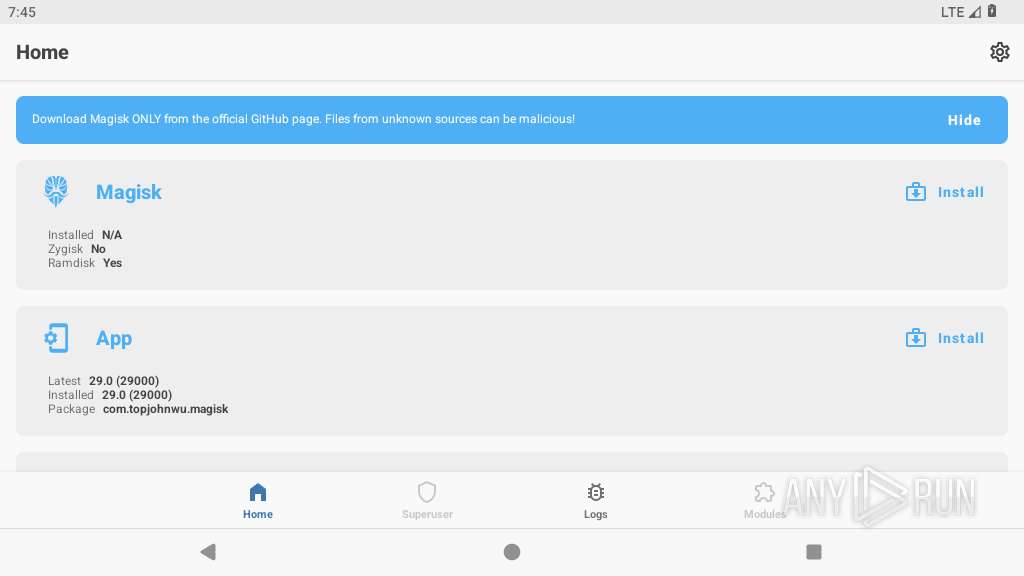
| File name: | magisk-manager-29-0.apk |
| Full analysis: | https://app.any.run/tasks/4ba5cc95-6d7b-478e-8644-cd5fba07415c |
| Verdict: | Malicious activity |
| Analysis date: | May 25, 2025, 19:44:15 |
| OS: | Android 14 |
| MIME: | application/vnd.android.package-archive |
| File info: | Android package (APK), with AndroidManifest.xml |
| MD5: | A8D62B58318A444B14A213EAC0643864 |
| SHA1: | E7AB8E900498409B4D4B123B0E556EED9E6FEBBB |
| SHA256: | 99D40DF1A68A05A5E78452A9CD4F2D753434D7622BAEEB44EA14AE8238C1A9CA |
| SSDEEP: | 98304:LmBG8g+ivawlCA+gtAzCIcuClKGw1F2H3hLNpOfy7Yka5VLAnGa2msvx/WzAOMIC:GVpNzkc4sp3HtKP9XcKQhlsm |
MALICIOUS
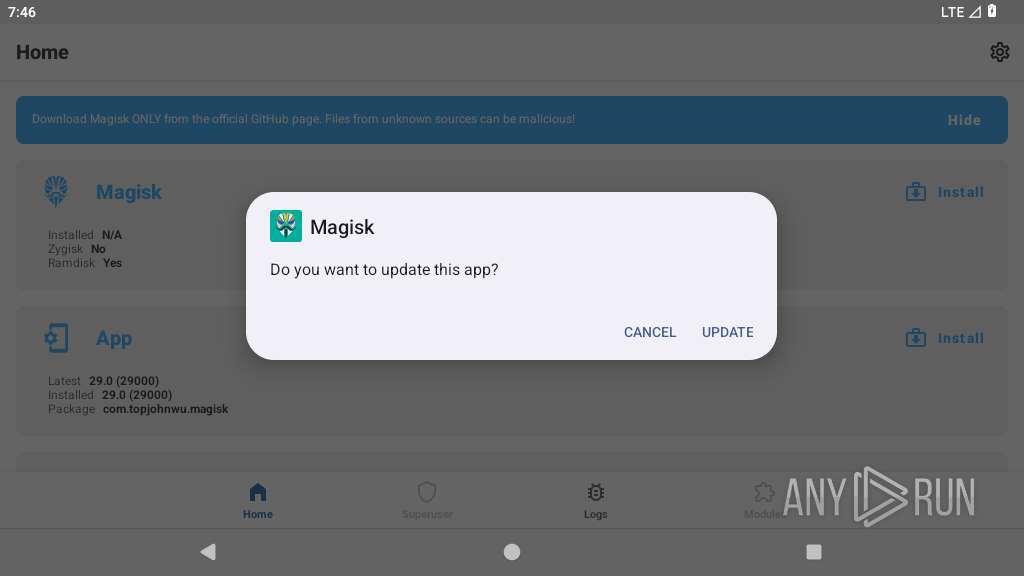
Initiates background APK installation
- app_process64 (PID: 2252)
- app_process64 (PID: 2559)
Executes system commands or scripts
- app_process64 (PID: 2559)
- app_process64 (PID: 2693)
SUSPICIOUS
Triggers notification to user
- app_process64 (PID: 2559)
- app_process64 (PID: 2693)
- app_process64 (PID: 2252)
Detects presence of QEMU emulator
- app_process64 (PID: 2693)
- app_process64 (PID: 2559)
- app_process64 (PID: 2768)
Accesses system-level resources
- app_process64 (PID: 2559)
- app_process64 (PID: 2693)
Collects data about the device's environment (JVM version)
- app_process64 (PID: 2693)
- app_process64 (PID: 2559)
INFO
Dynamically inspects or modifies classes, methods, and fields at runtime
- app_process64 (PID: 2252)
- app_process64 (PID: 2559)
- app_process64 (PID: 2768)
- app_process64 (PID: 2693)
Gets the display metrics associated with the device's screen
- app_process64 (PID: 2252)
- app_process64 (PID: 2559)
- app_process64 (PID: 2768)
Retrieves data from storage of application settings (SharedPreferences)
- app_process64 (PID: 2252)
- app_process64 (PID: 2559)
Dynamically loads a class in Java
- app_process64 (PID: 2559)
Dynamically registers broadcast event listeners
- app_process64 (PID: 2559)
- app_process64 (PID: 2252)
- app_process64 (PID: 2693)
Gets file name without full path
- app_process64 (PID: 2559)
Verifies whether the device is connected to the internet
- app_process64 (PID: 2559)
- app_process64 (PID: 2693)
- app_process64 (PID: 2252)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .apk | | | Android Package (62.8) |
|---|---|---|
| .jar | | | Java Archive (17.3) |
| .vym | | | VYM Mind Map (14.9) |
| .zip | | | ZIP compressed archive (4.7) |
EXIF
ZIP
| ZipRequiredVersion: | - |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0x52ba1090 |
| ZipCompressedSize: | 2139 |
| ZipUncompressedSize: | 8100 |
| ZipFileName: | AndroidManifest.xml |
Total processes
191
Monitored processes
67
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 2252 | com.topjohnwu.magisk | /system/bin/app_process64 | app_process64 | |
User: root Integrity Level: UNKNOWN Exit code: 9 | ||||
| 2280 | com.topjohnwu.magisk | /system/bin/app_process64 | — | app_process64 |
User: u0_a108 Integrity Level: UNKNOWN Exit code: 65280 | ||||
| 2286 | com.topjohnwu.magisk | /system/bin/app_process64 | — | app_process64 |
User: u0_a108 Integrity Level: UNKNOWN Exit code: 65280 | ||||
| 2287 | /data/app/~~yRMeJtHiVhObxDPIKj4j3g==/com.topjohnwu.magisk-p3jun-eFNixQKJLvNyBKTg==/lib/arm64/libbusybox.so sh | /data/app/~~yRMeJtHiVhObxDPIKj4j3g==/com.topjohnwu.magisk-p3jun-eFNixQKJLvNyBKTg==/lib/arm64/libbusybox.so | — | app_process64 |
User: u0_a108 Integrity Level: UNKNOWN Exit code: 9 | ||||
| 2299 | /data/app/~~yRMeJtHiVhObxDPIKj4j3g==/com.topjohnwu.magisk-p3jun-eFNixQKJLvNyBKTg==/lib/arm64/libbusybox.so sh | /data/app/~~yRMeJtHiVhObxDPIKj4j3g==/com.topjohnwu.magisk-p3jun-eFNixQKJLvNyBKTg==/lib/arm64/libbusybox.so | — | libbusybox.so |
User: u0_a108 Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2300 | getprop ro.build.ab_update | /system/bin/toolbox | — | libbusybox.so |
User: u0_a108 Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2301 | getprop ro.boot.slot_suffix | /system/bin/toolbox | — | libbusybox.so |
User: u0_a108 Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2302 | grep " / " /proc/mounts | /data/app/~~yRMeJtHiVhObxDPIKj4j3g==/com.topjohnwu.magisk-p3jun-eFNixQKJLvNyBKTg==/lib/arm64/libbusybox.so | — | libbusybox.so |
User: u0_a108 Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2303 | grep -qv rootfs | /data/app/~~yRMeJtHiVhObxDPIKj4j3g==/com.topjohnwu.magisk-p3jun-eFNixQKJLvNyBKTg==/lib/arm64/libbusybox.so | — | libbusybox.so |
User: u0_a108 Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2304 | grep " / " /proc/mounts | /data/app/~~yRMeJtHiVhObxDPIKj4j3g==/com.topjohnwu.magisk-p3jun-eFNixQKJLvNyBKTg==/lib/arm64/libbusybox.so | — | libbusybox.so |
User: u0_a108 Integrity Level: UNKNOWN Exit code: 0 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
22
Text files
14
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2252 | app_process64 | /data/data/com.topjohnwu.magisk/files/profileinstaller_profileWrittenFor_lastUpdateTime.dat | mpg | |
MD5:— | SHA256:— | |||
| 2252 | app_process64 | /data/data/com.topjohnwu.magisk/files/profileInstalled | binary | |
MD5:— | SHA256:— | |||
| 2252 | app_process64 | /data/data/com.topjohnwu.magisk/cache/okhttp/journal.tmp | text | |
MD5:— | SHA256:— | |||
| 2252 | app_process64 | /data/data/com.topjohnwu.magisk/cache/okhttp/b5e19eca1e184690a6d76eba4376f625.0.tmp | text | |
MD5:— | SHA256:— | |||
| 2252 | app_process64 | /data/data/com.topjohnwu.magisk/cache/okhttp/b5e19eca1e184690a6d76eba4376f625.1.tmp | compressed | |
MD5:— | SHA256:— | |||
| 2252 | app_process64 | /data/data/com.topjohnwu.magisk/cache/oat_primary/arm64/base.2252.tmp | binary | |
MD5:— | SHA256:— | |||
| 2252 | app_process64 | /data/data/com.topjohnwu.magisk/cache/okhttp/1f7735ac4a085a6351885ae554cf8296.0.tmp | text | |
MD5:— | SHA256:— | |||
| 2252 | app_process64 | /data/data/com.topjohnwu.magisk/cache/okhttp/1f7735ac4a085a6351885ae554cf8296.1.tmp | compressed | |
MD5:— | SHA256:— | |||
| 2252 | app_process64 | /data/data/com.topjohnwu.magisk/cache/29000.md | text | |
MD5:— | SHA256:— | |||
| 2252 | app_process64 | /data/data/com.topjohnwu.magisk/cache/okhttp/b5e19eca1e184690a6d76eba4376f625.0 | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
12
DNS requests
8
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 142.250.186.163:80 | http://connectivitycheck.gstatic.com/generate_204 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
449 | mdnsd | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 142.250.186.163:80 | connectivitycheck.gstatic.com | GOOGLE | US | whitelisted |
— | — | 142.250.185.100:443 | www.google.com | GOOGLE | US | whitelisted |
— | — | 216.239.35.0:123 | time.android.com | — | — | whitelisted |
— | — | 74.125.71.81:443 | staging-remoteprovisioning.sandbox.googleapis.com | GOOGLE | US | whitelisted |
2252 | app_process64 | 185.199.108.153:443 | topjohnwu.github.io | FASTLY | US | shared |
2252 | app_process64 | 140.82.121.4:443 | github.com | GITHUB | US | whitelisted |
2252 | app_process64 | 185.199.109.133:443 | objects.githubusercontent.com | FASTLY | US | whitelisted |
2559 | app_process64 | 140.82.121.4:443 | github.com | GITHUB | US | whitelisted |
2559 | app_process64 | 185.199.109.133:443 | objects.githubusercontent.com | FASTLY | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
connectivitycheck.gstatic.com |
| whitelisted |
www.google.com |
| whitelisted |
google.com |
| whitelisted |
time.android.com |
| whitelisted |
staging-remoteprovisioning.sandbox.googleapis.com |
| whitelisted |
topjohnwu.github.io |
| unknown |
github.com |
| whitelisted |
objects.githubusercontent.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Android Device Connectivity Check |