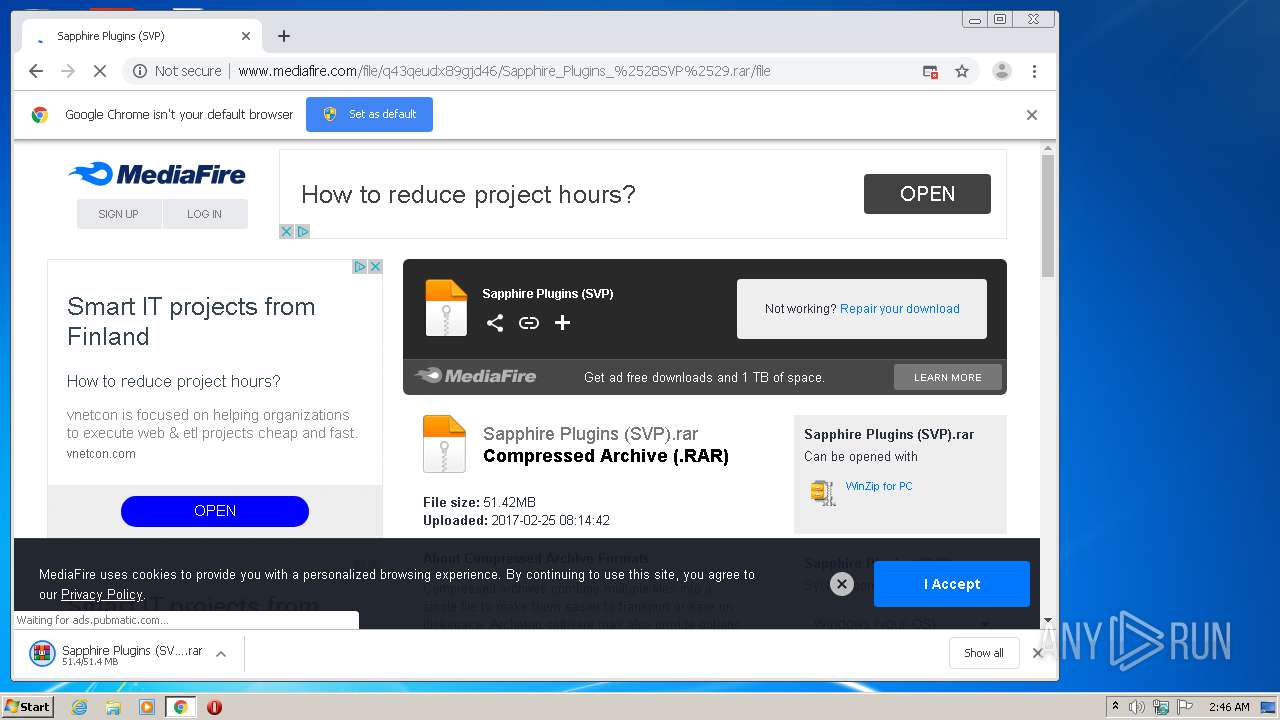
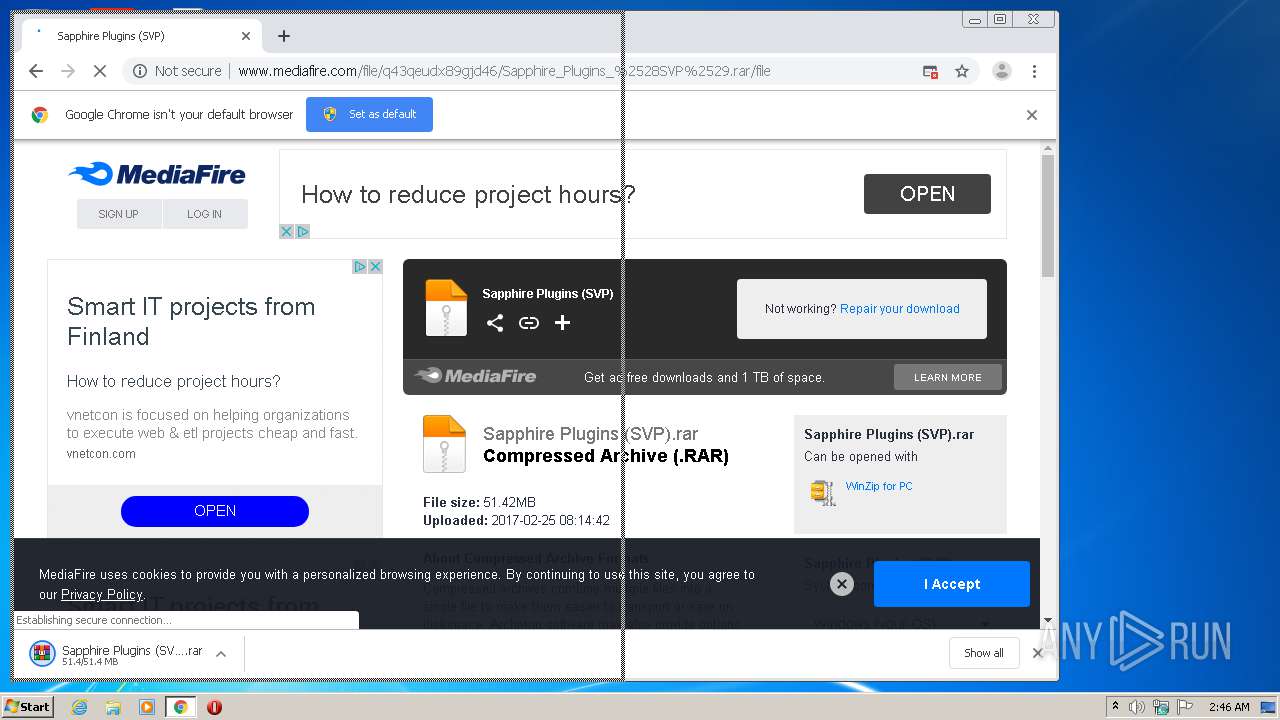
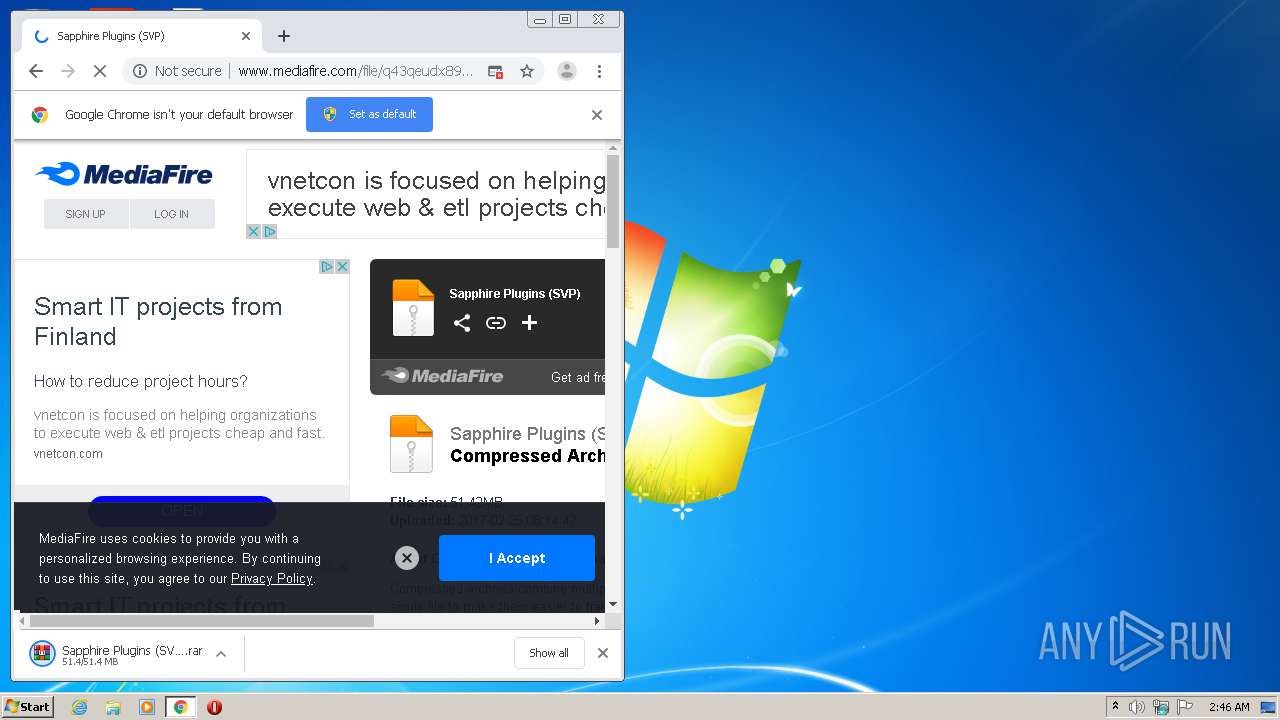
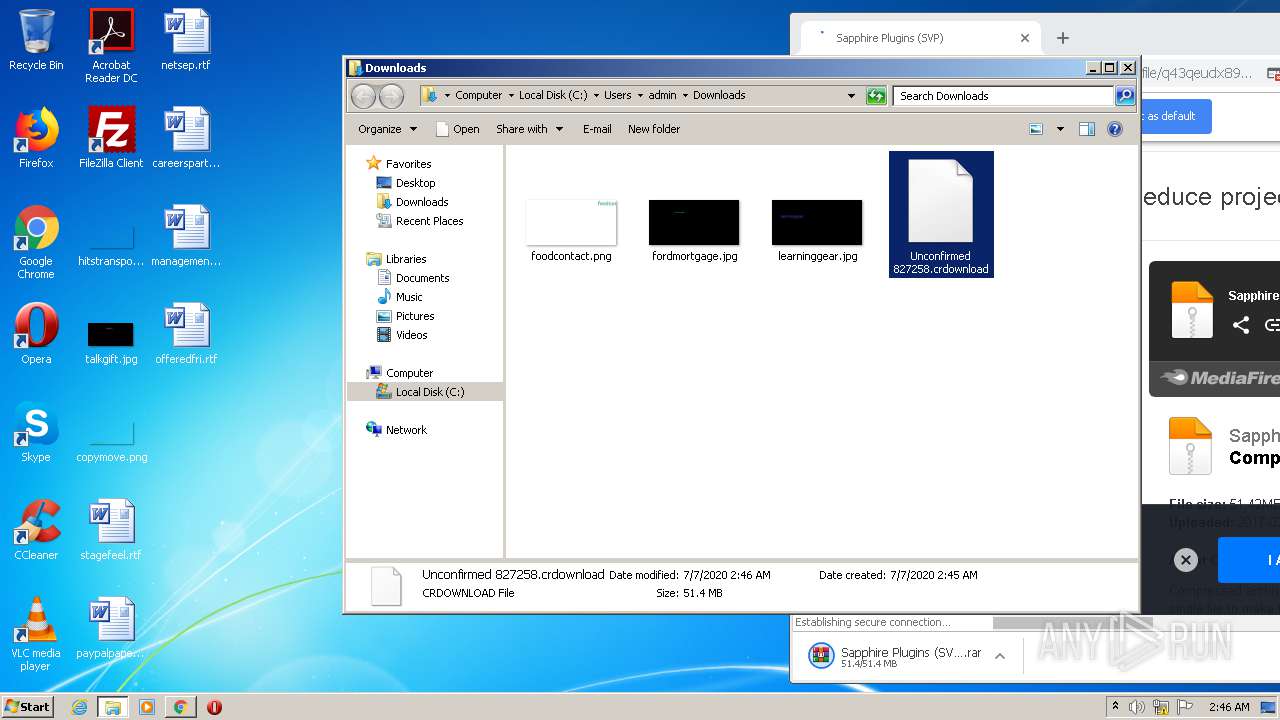
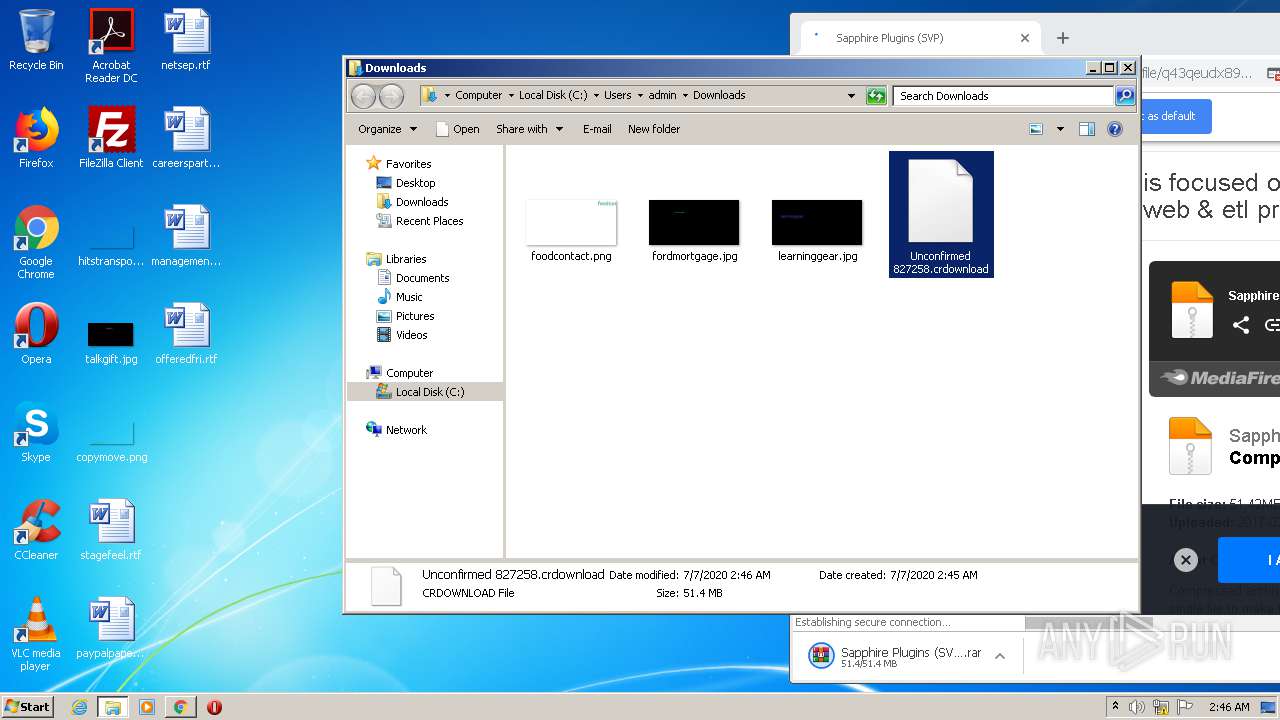
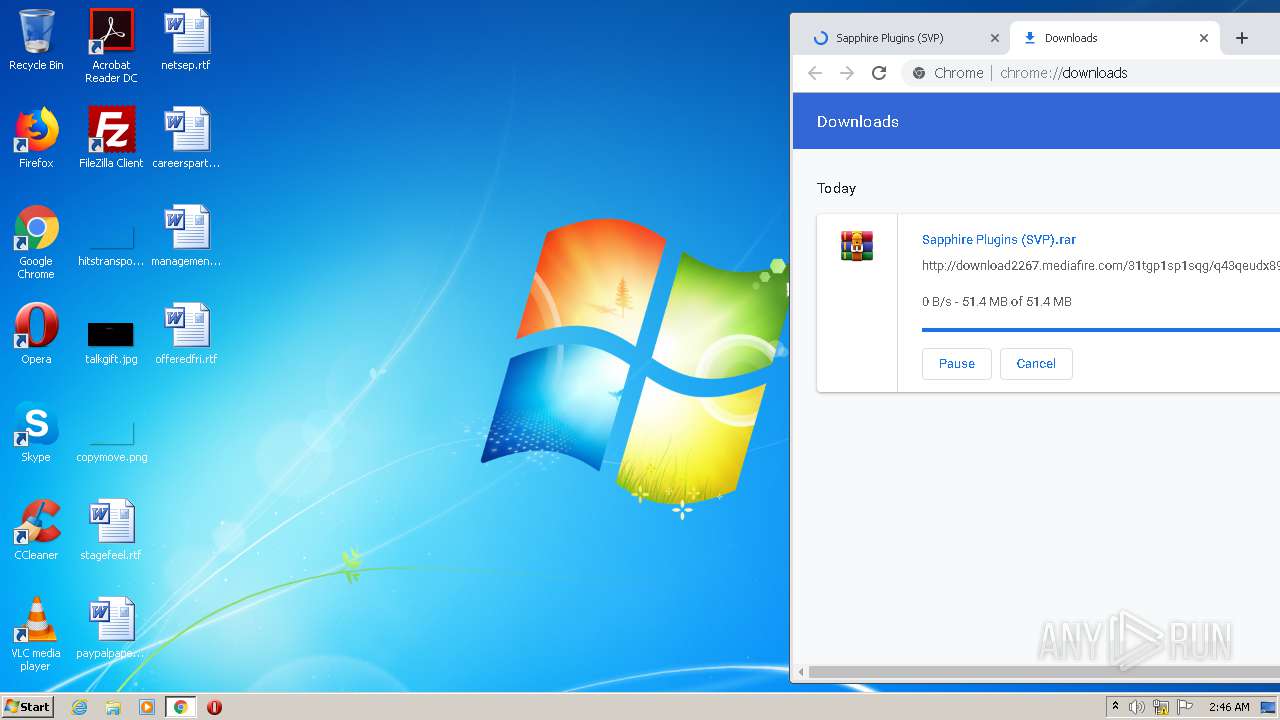
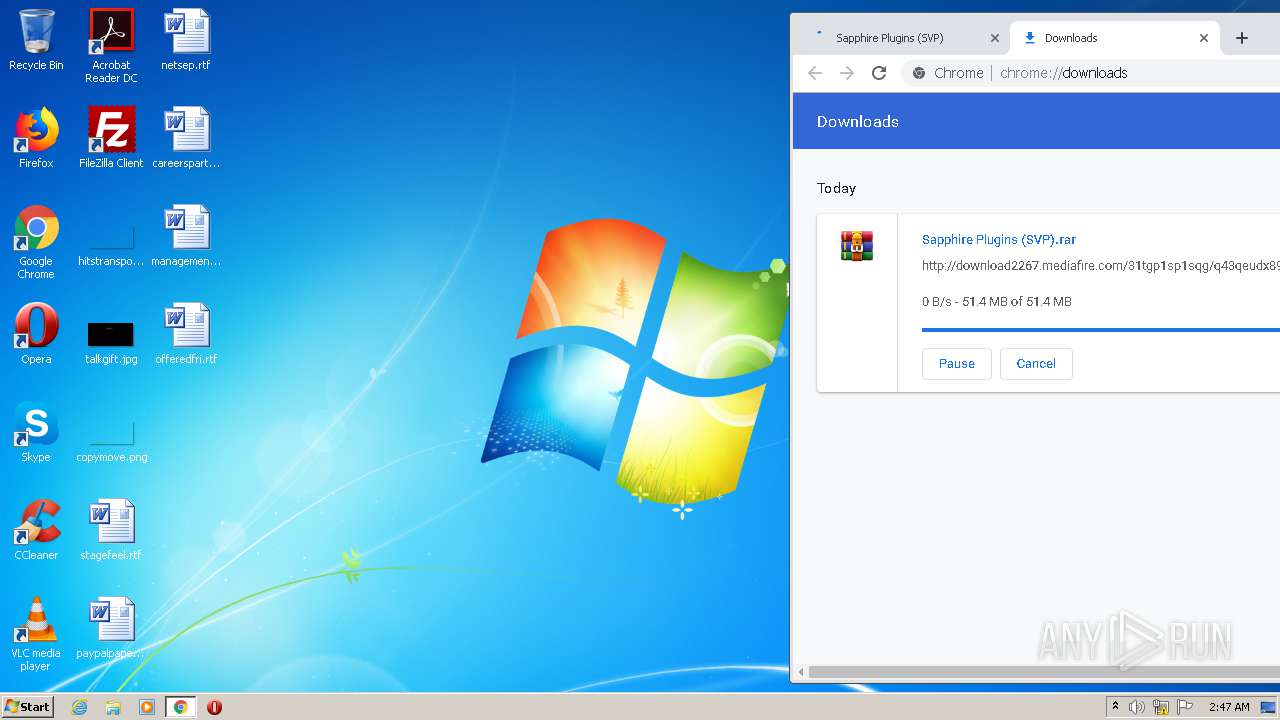
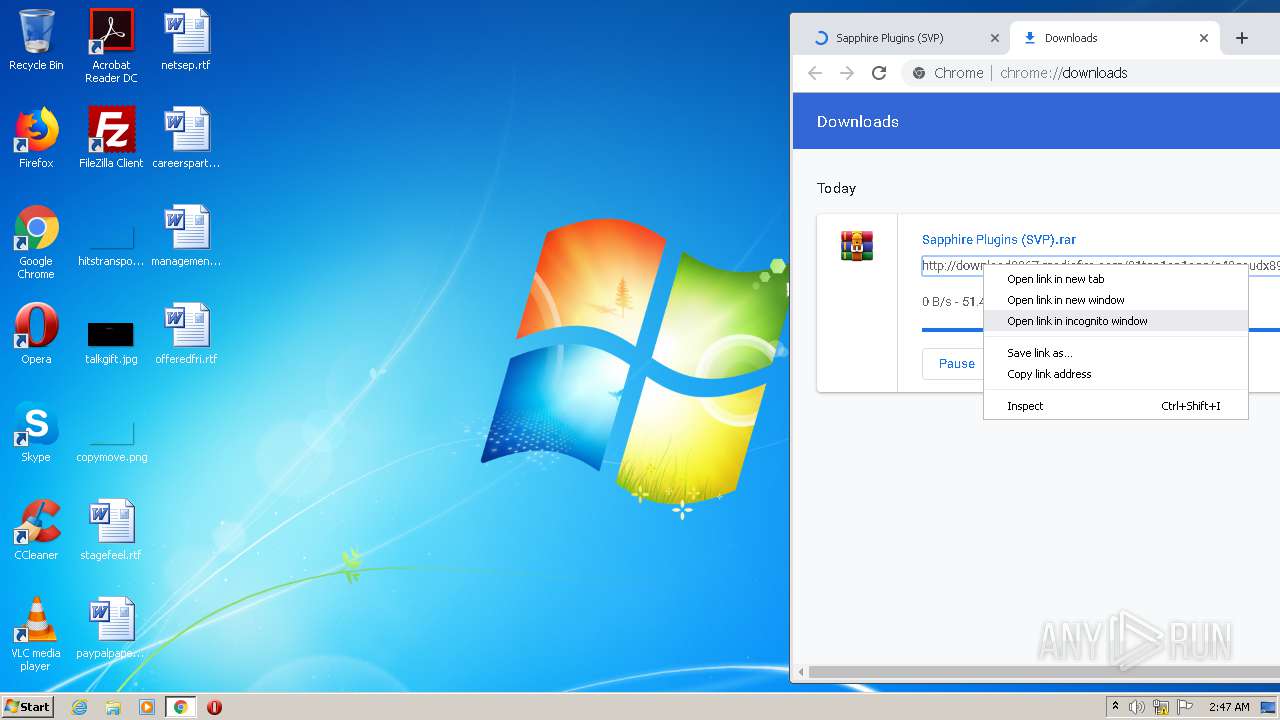
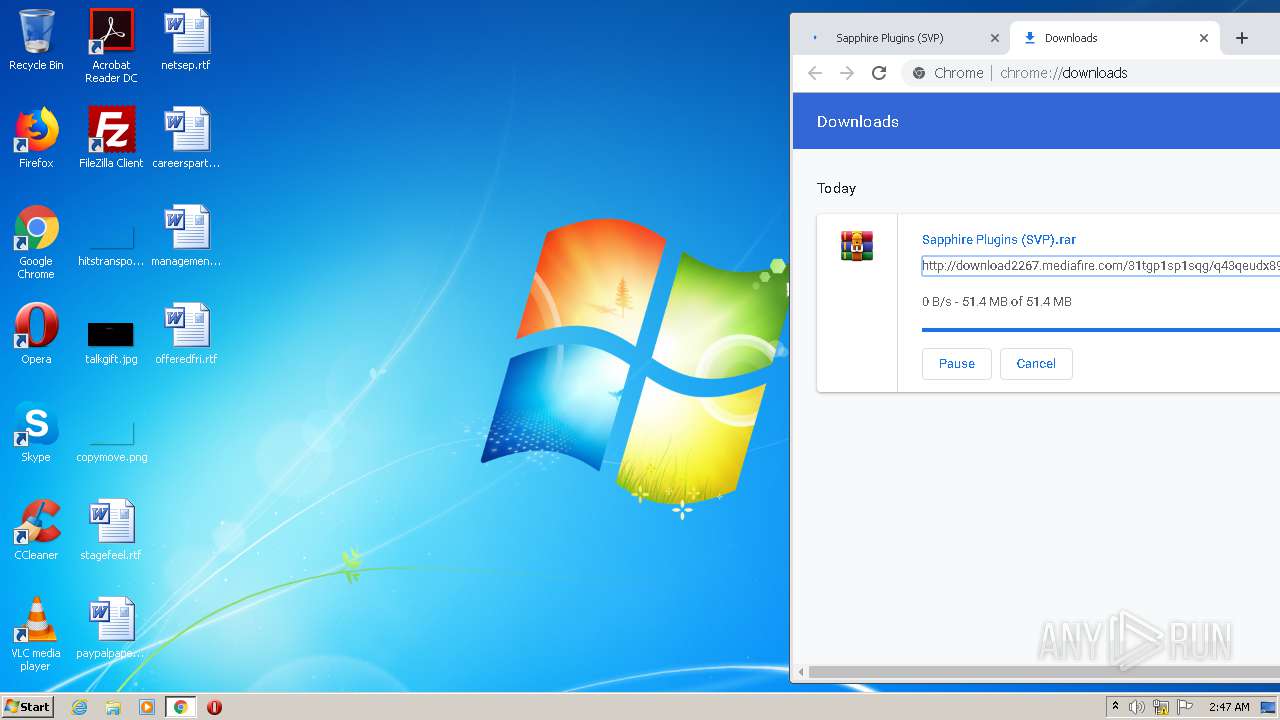
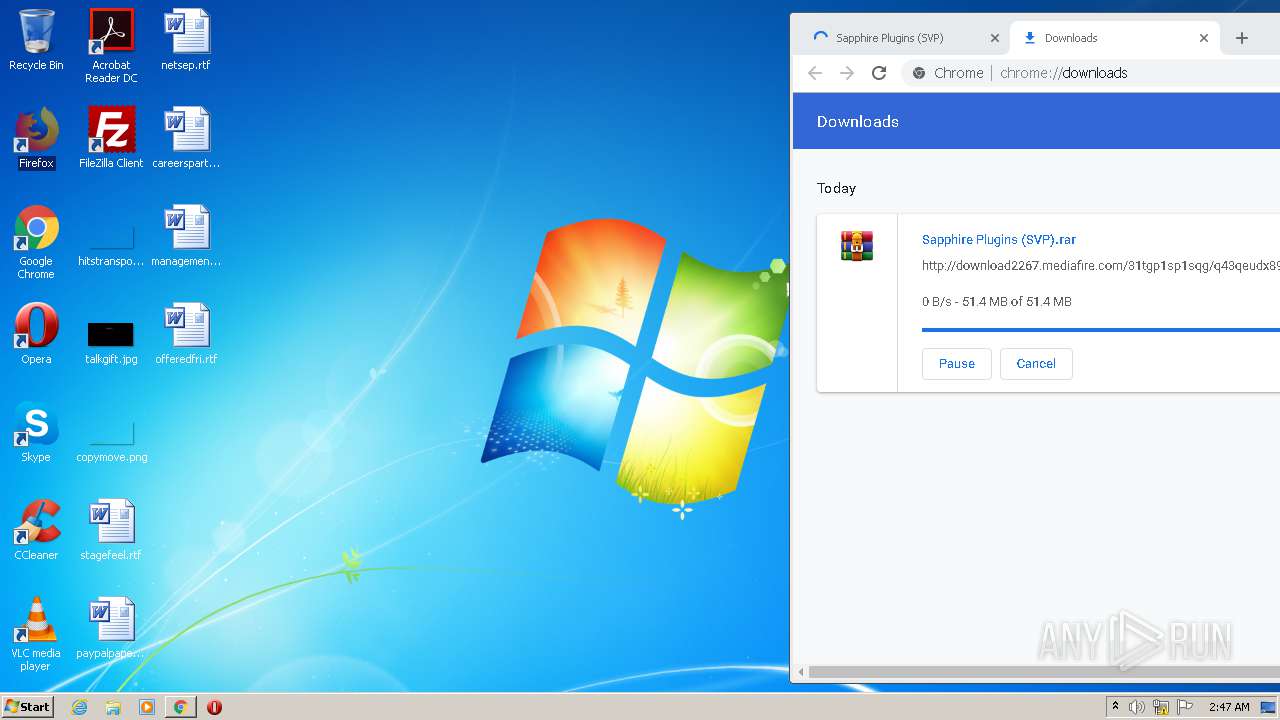
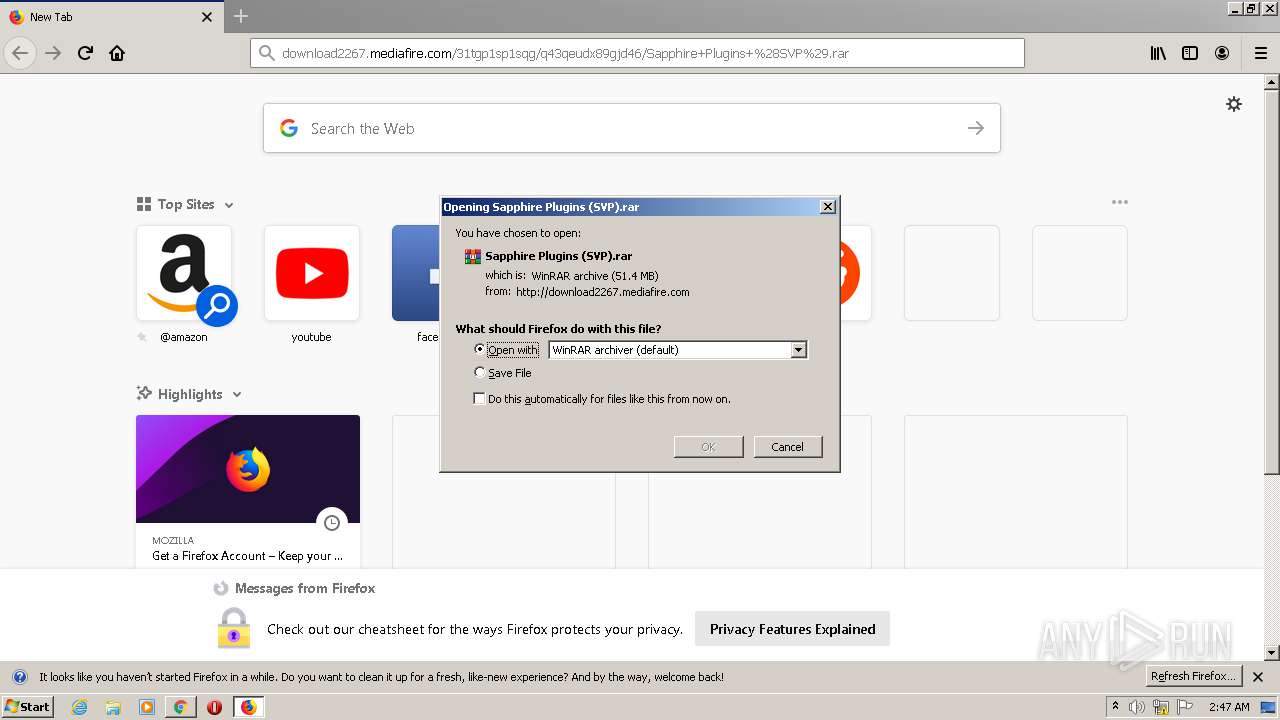
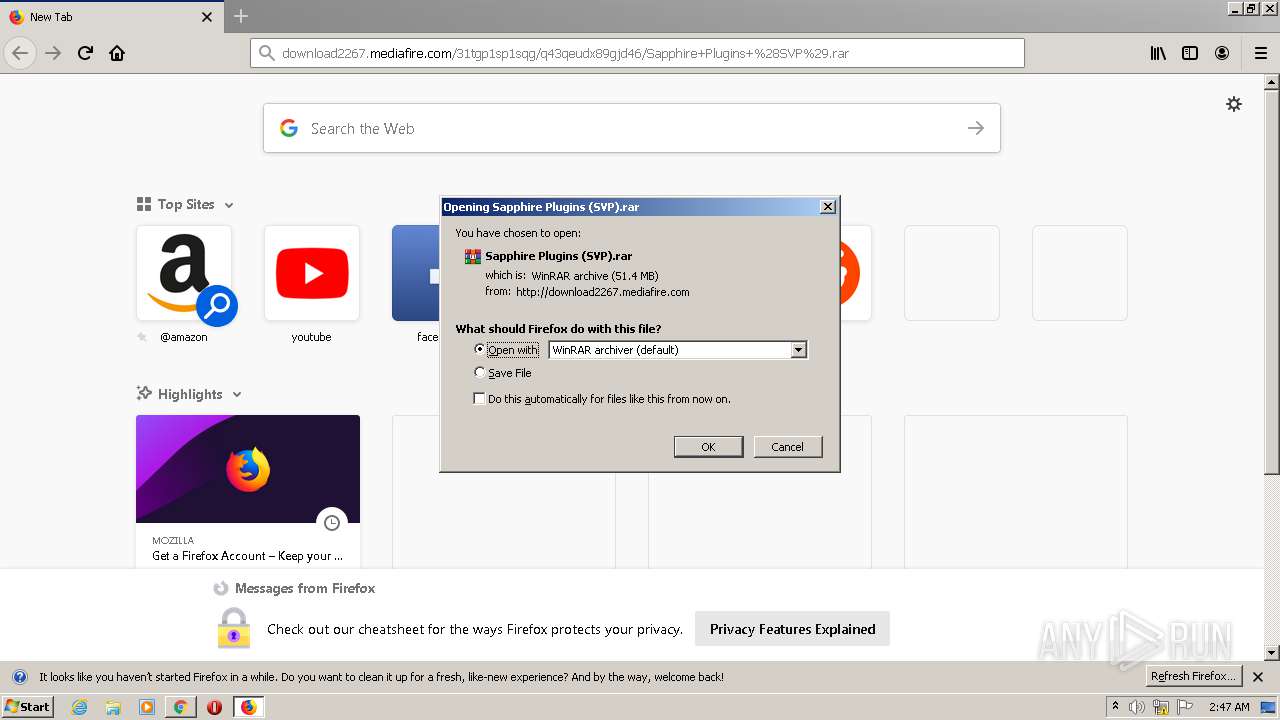
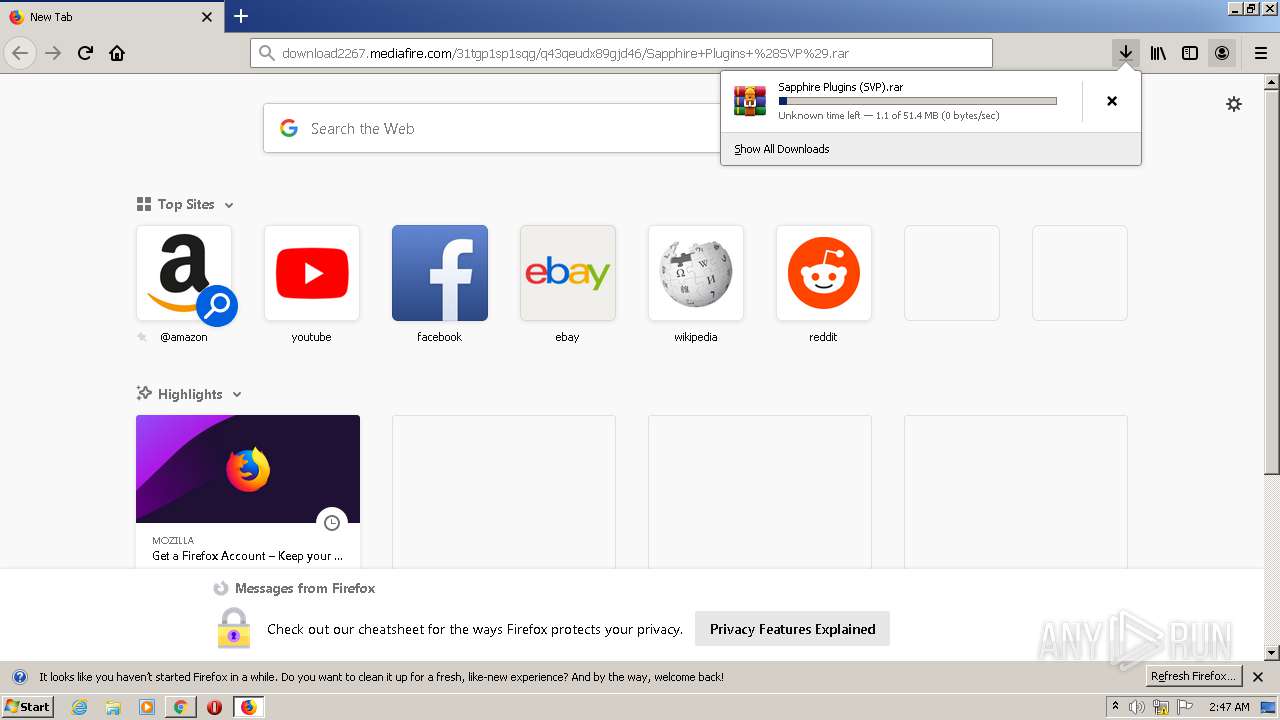
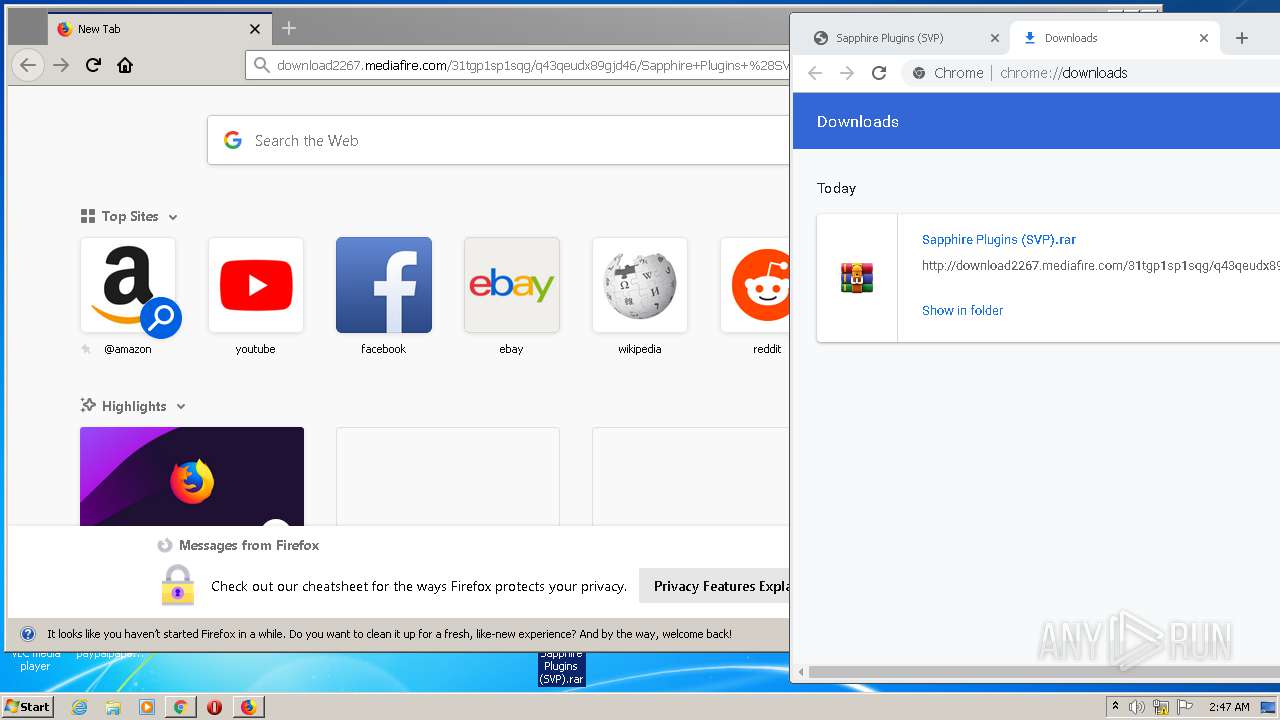
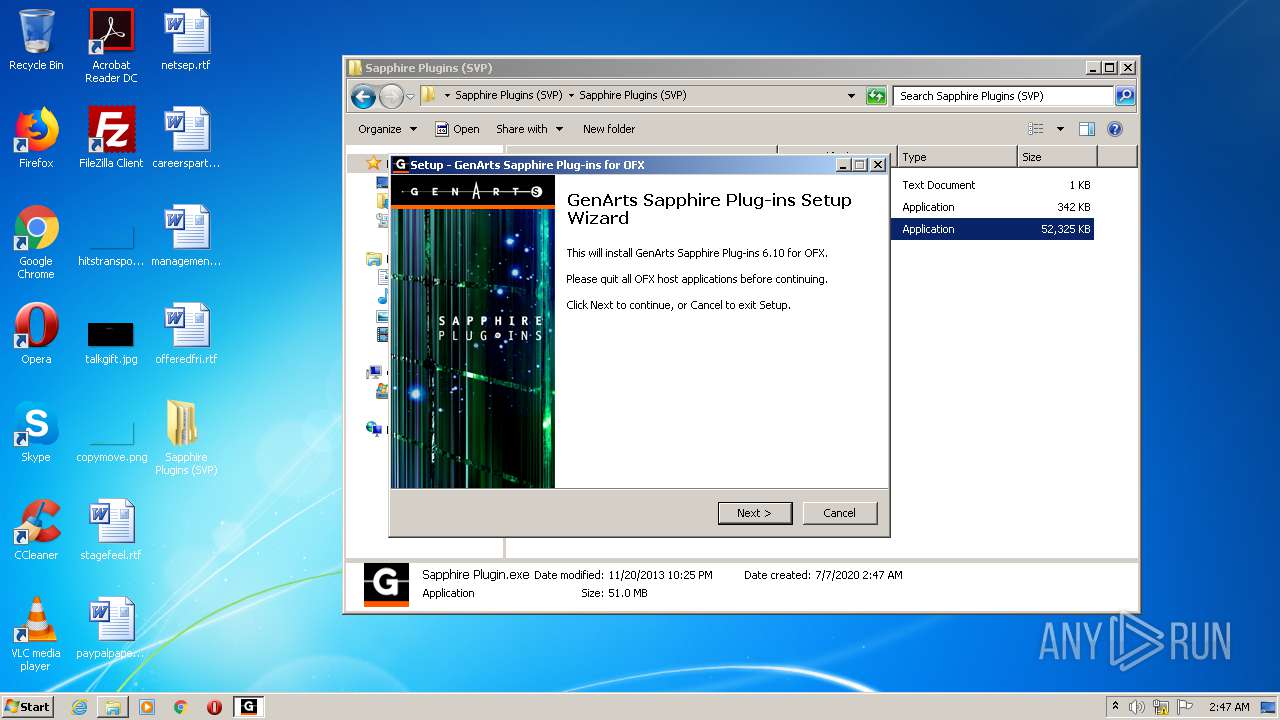
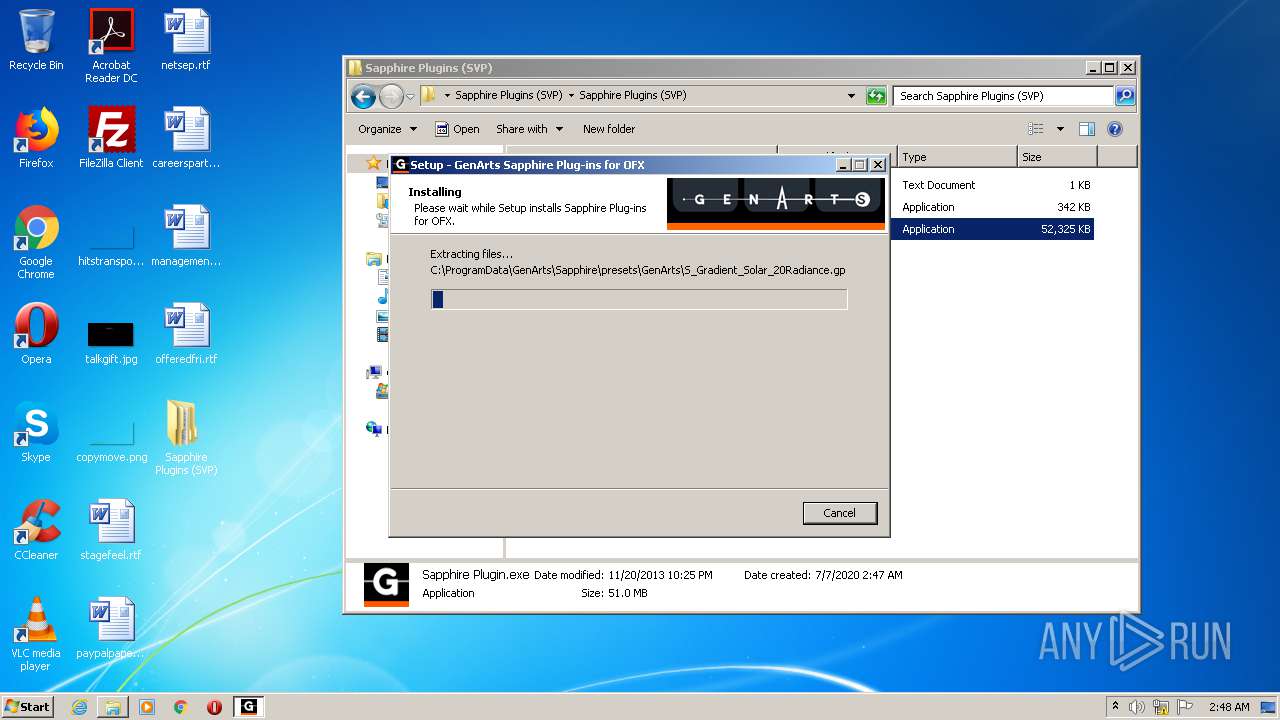
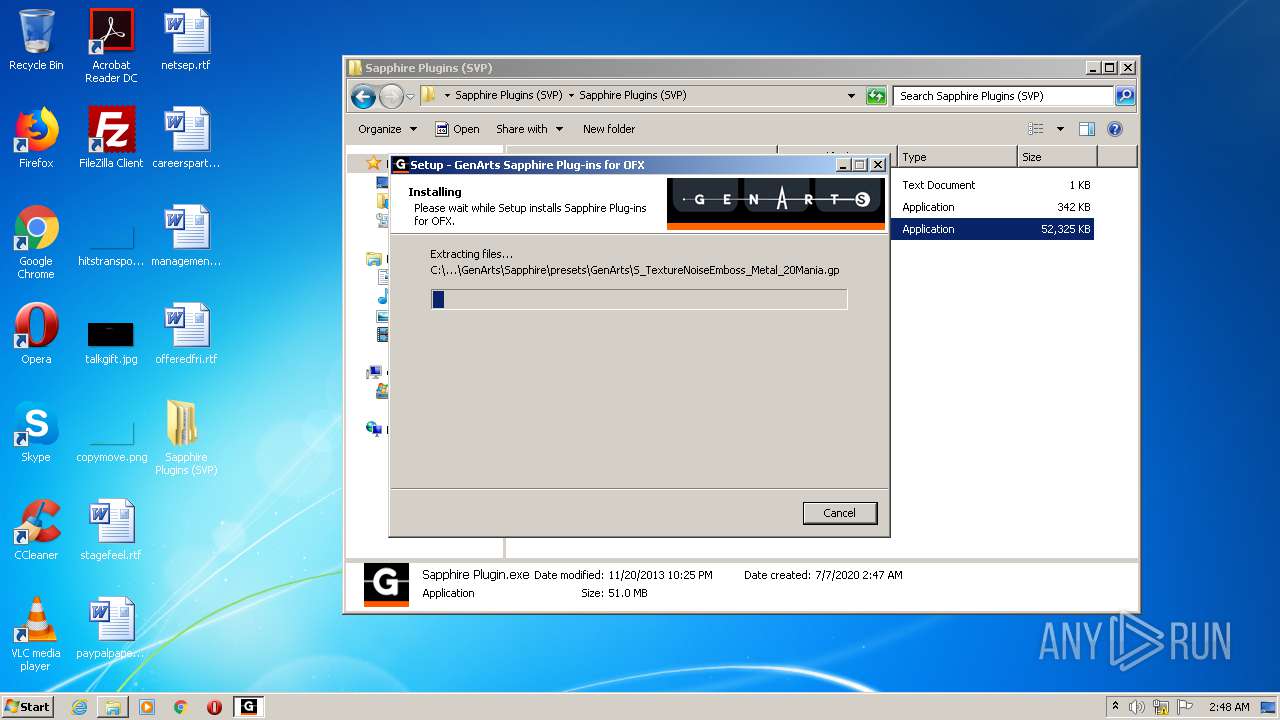
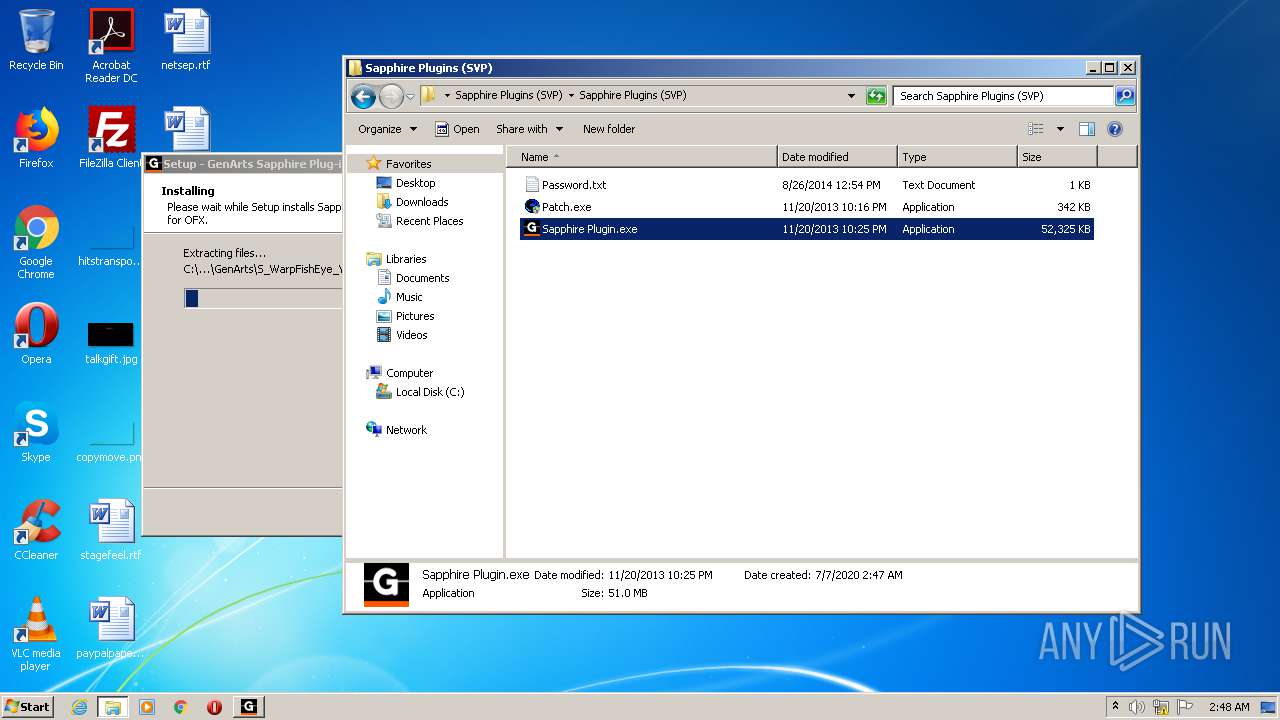
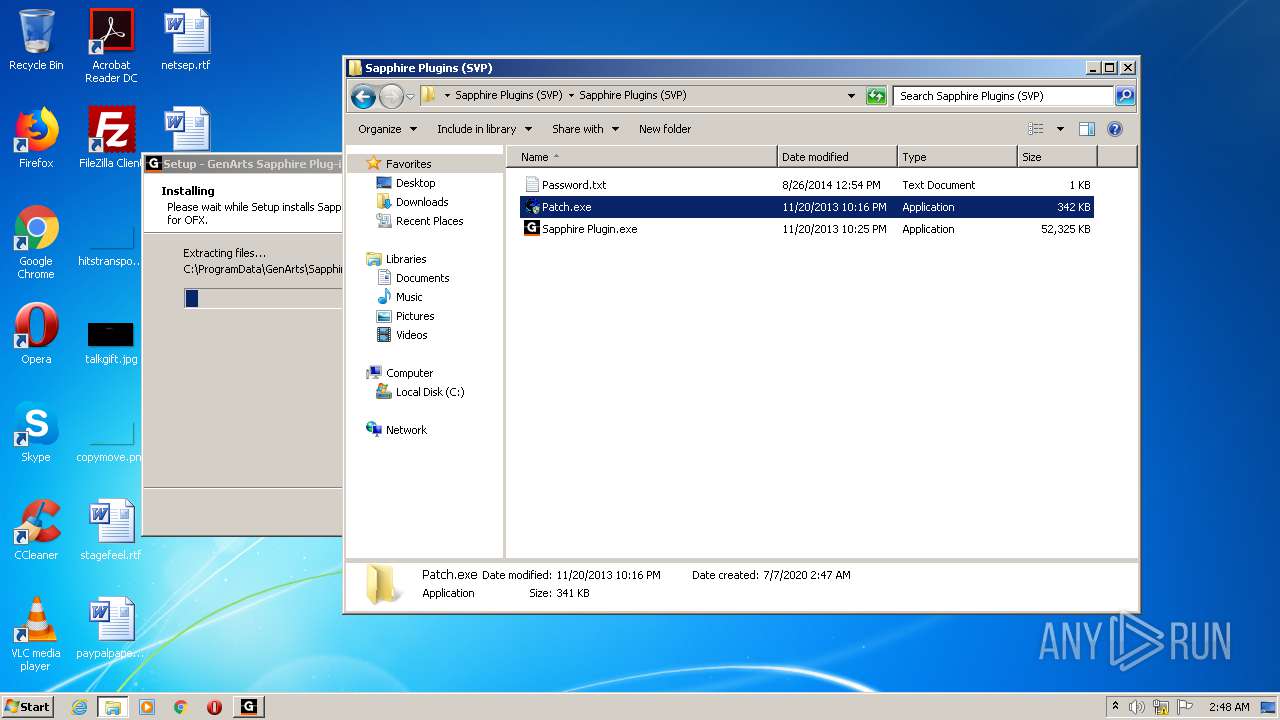
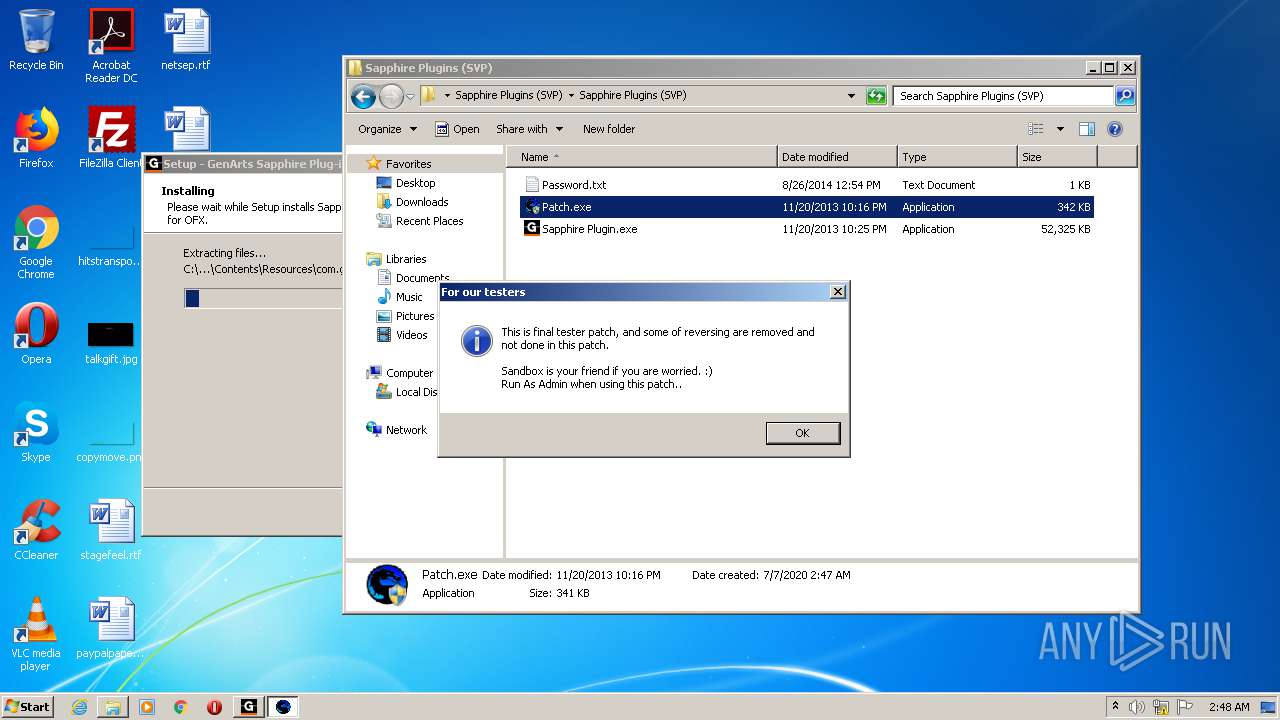
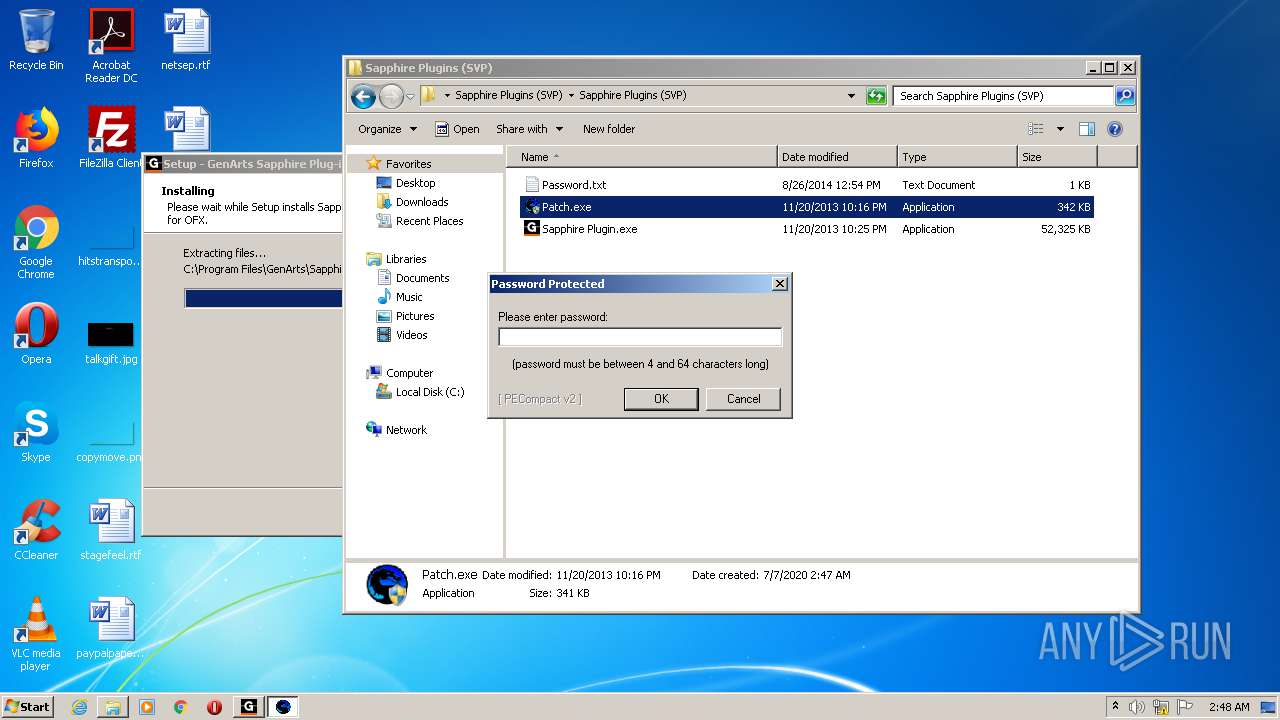
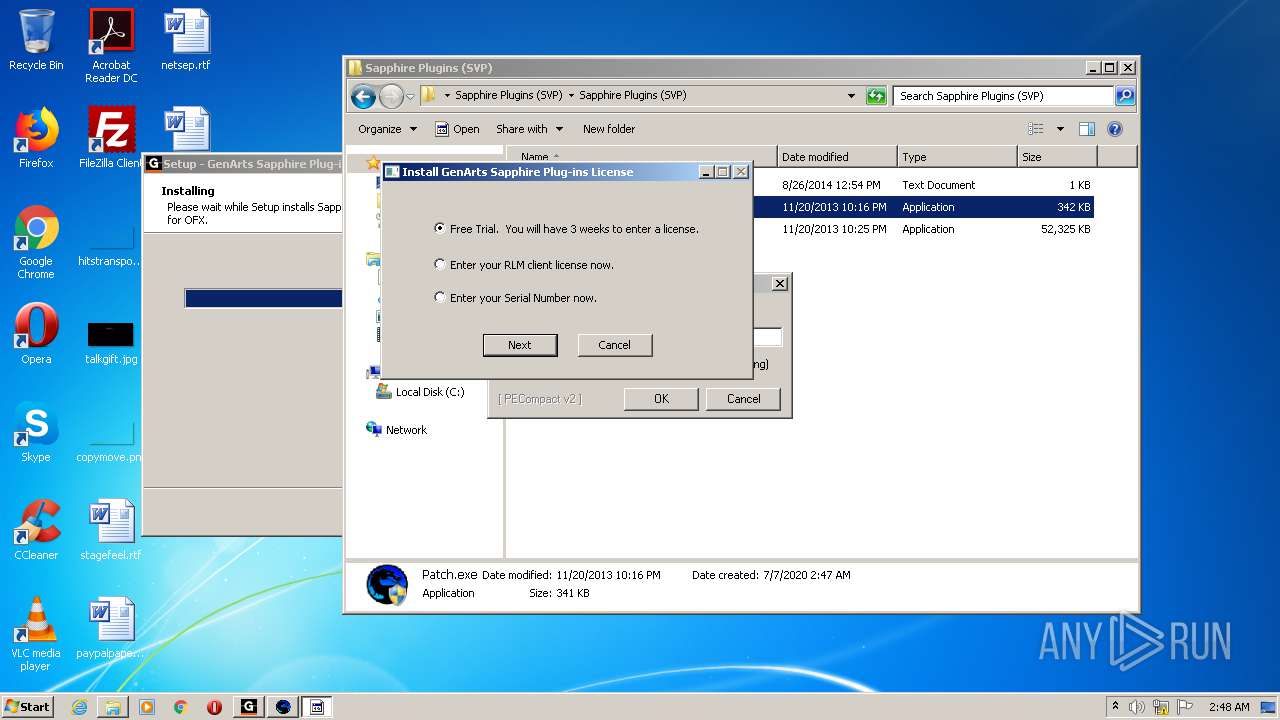
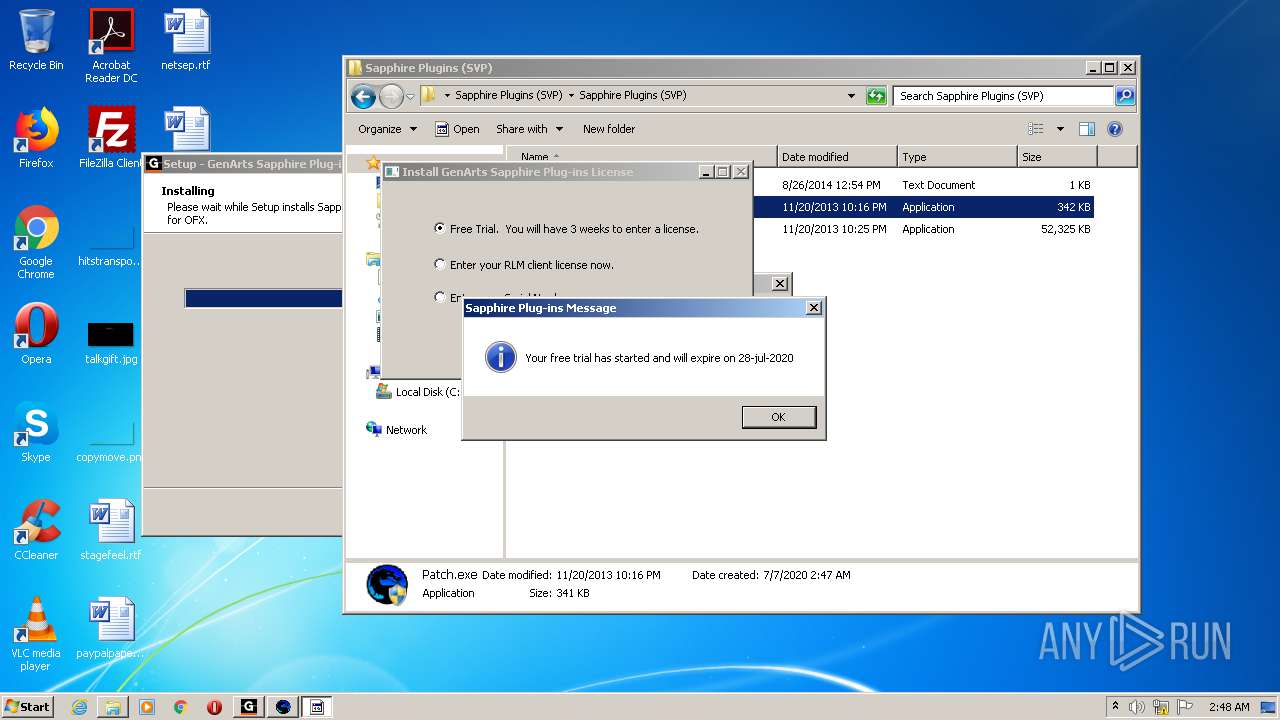
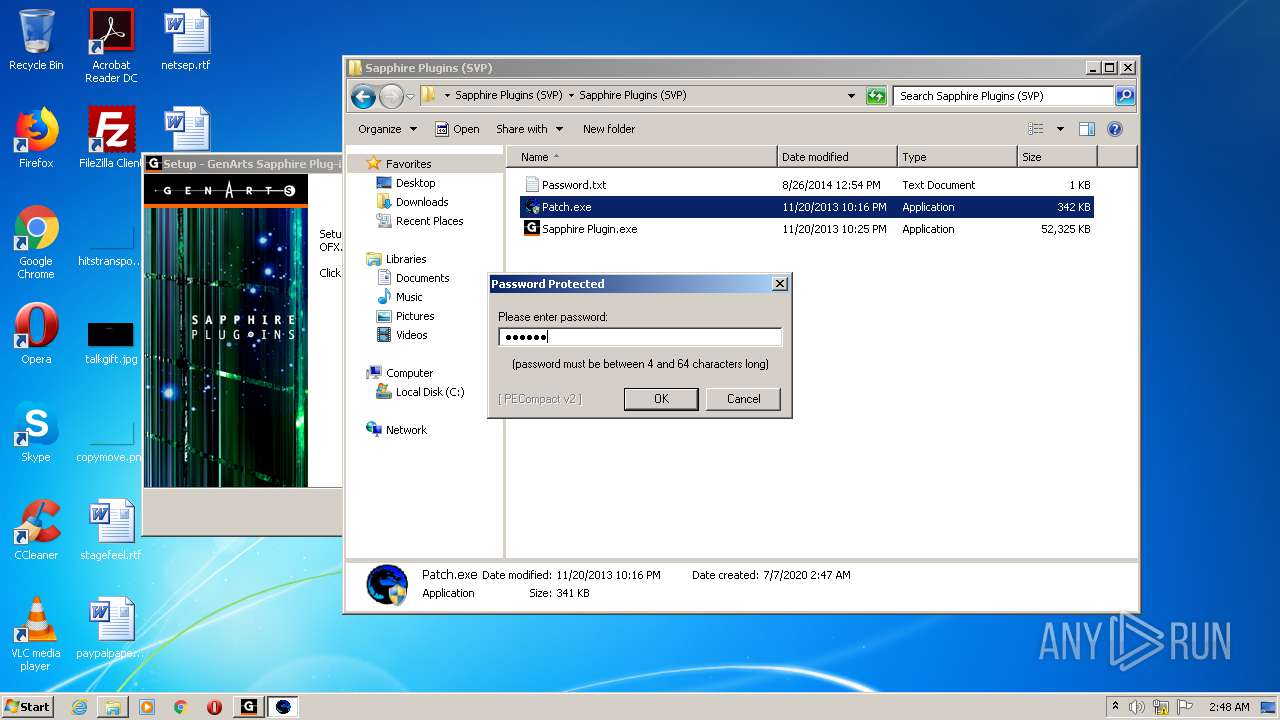
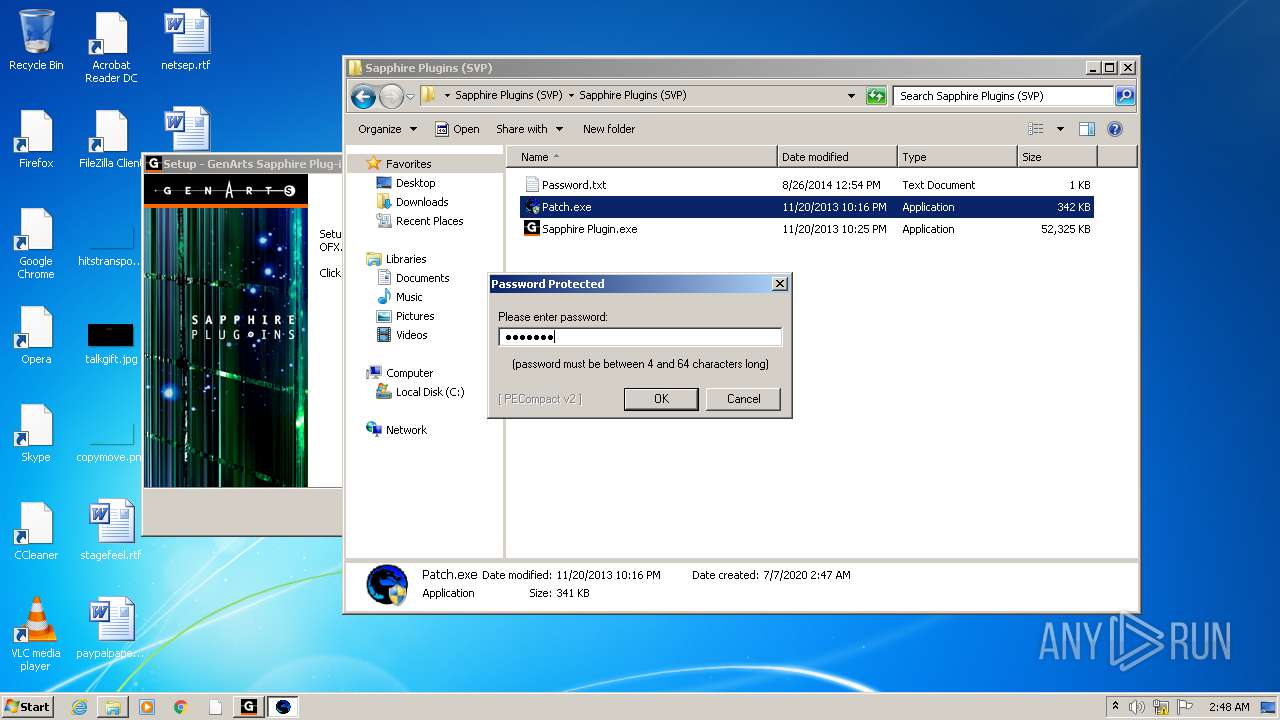
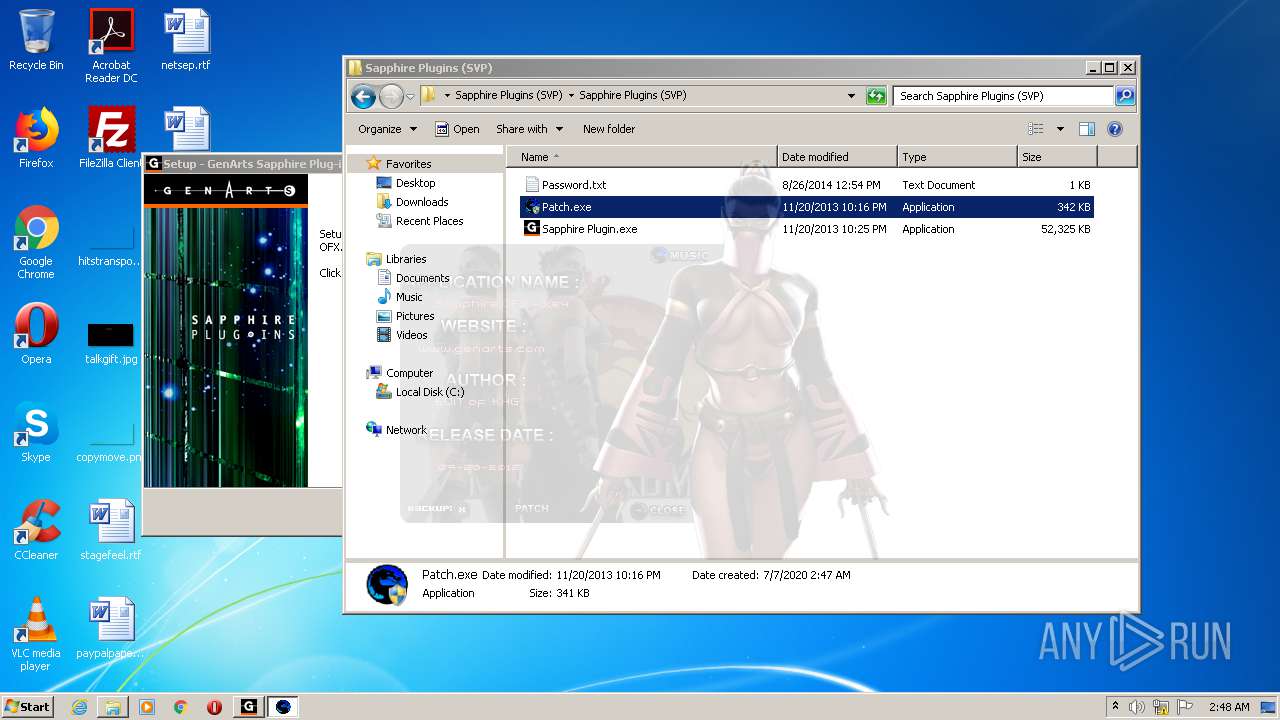
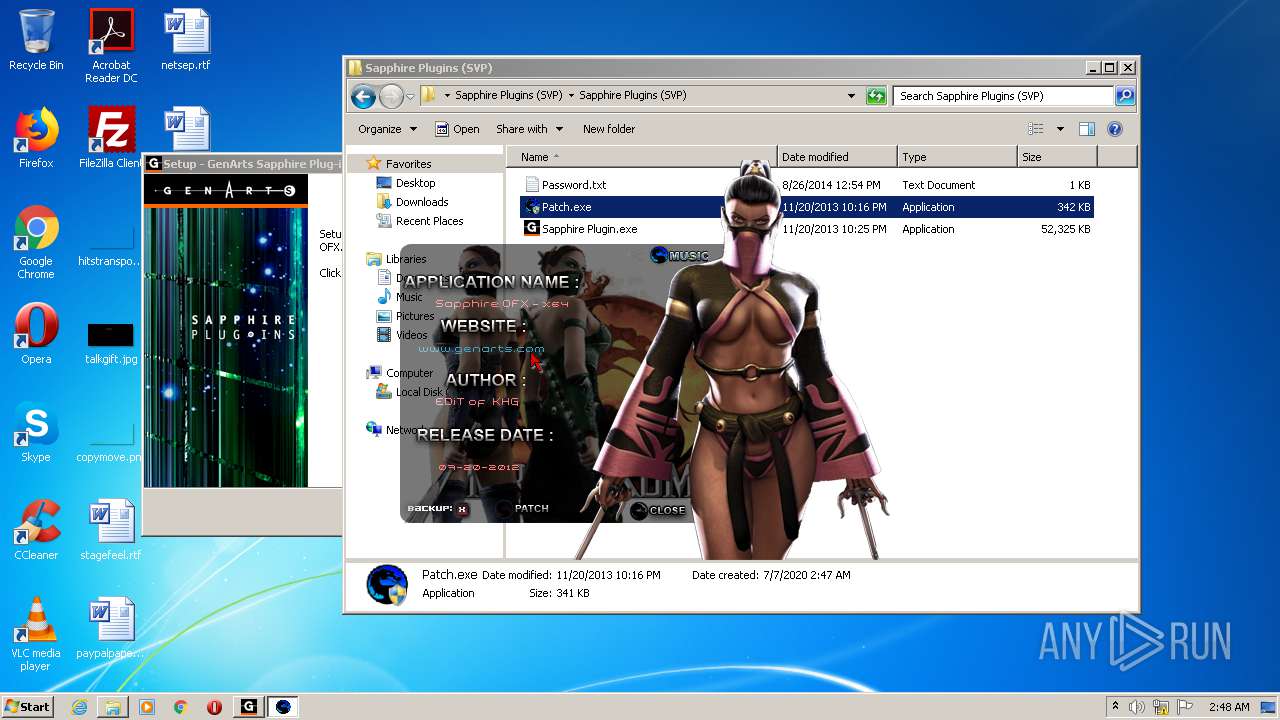
| URL: | http://www.mediafire.com/file/q43qeudx89gjd46/Sapphire_Plugins_%2528SVP%2529.rar/file |
| Full analysis: | https://app.any.run/tasks/54704a8d-eec5-43cb-853b-cf2daa8c7667 |
| Verdict: | Malicious activity |
| Analysis date: | July 07, 2020, 01:45:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | AE2DB56FD4929E1E9DE91324ED9D8372 |
| SHA1: | 6E751532EB5205BB673837A9DA84F337466D40D6 |
| SHA256: | 99CC7D2230528FF8CBCC48B017405CEC9050B24946B24F95ED62C0BE2BABABB7 |
| SSDEEP: | 3:N1KJS4w3eGUoIRBfcCr2V+J96yQXuyfLX+fA:Cc4w3eGk7rN7CuyfLOfA |
MALICIOUS
Application was dropped or rewritten from another process
- install.exe (PID: 4288)
- Patch.exe (PID: 4580)
- Patch.exe (PID: 5652)
- genarts-frontend.exe (PID: 4184)
Changes settings of System certificates
- msiexec.exe (PID: 860)
Loads dropped or rewritten executable
- install.exe (PID: 4288)
SUSPICIOUS
Creates files in the program directory
- firefox.exe (PID: 4016)
- genarts-frontend.exe (PID: 4184)
Modifies files in Chrome extension folder
- chrome.exe (PID: 440)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4308)
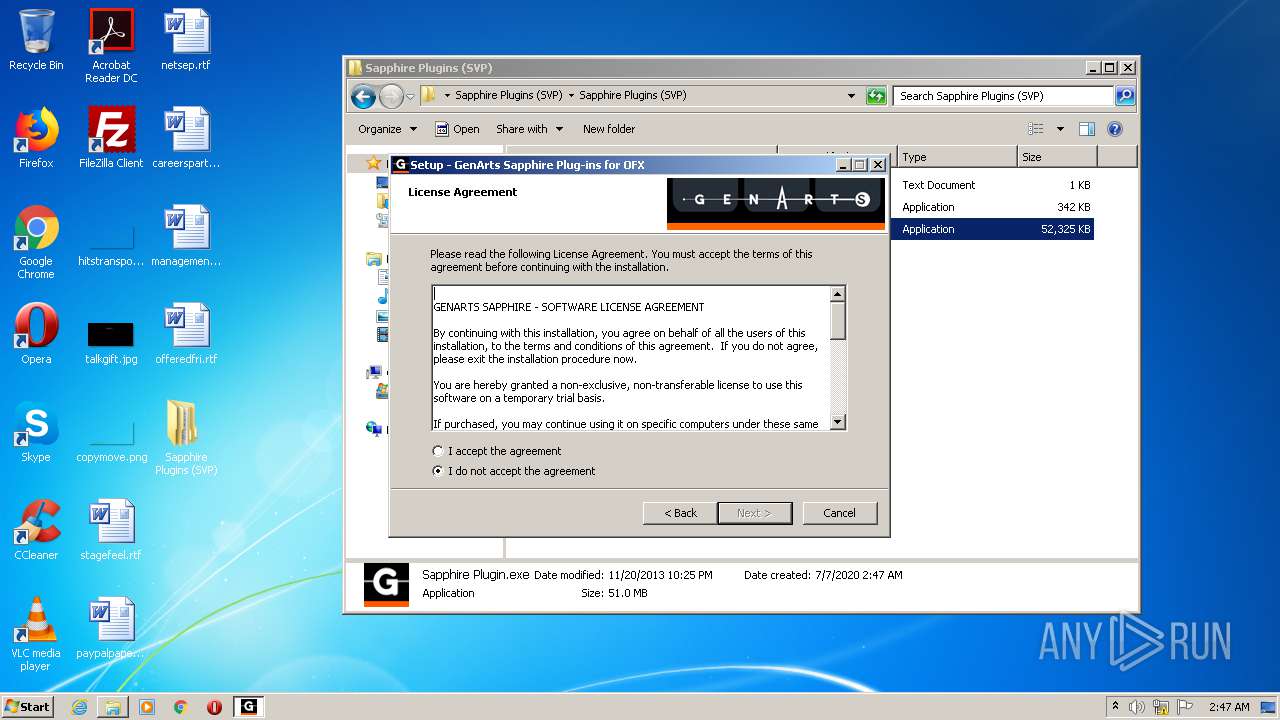
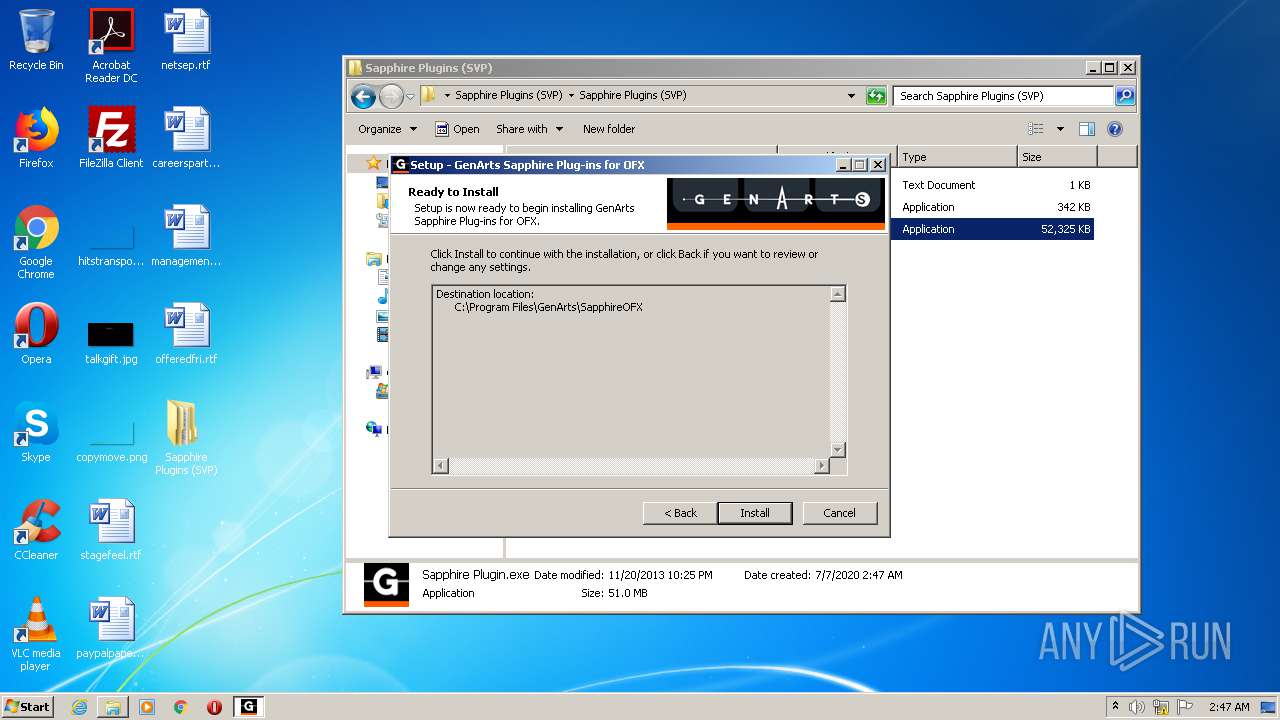
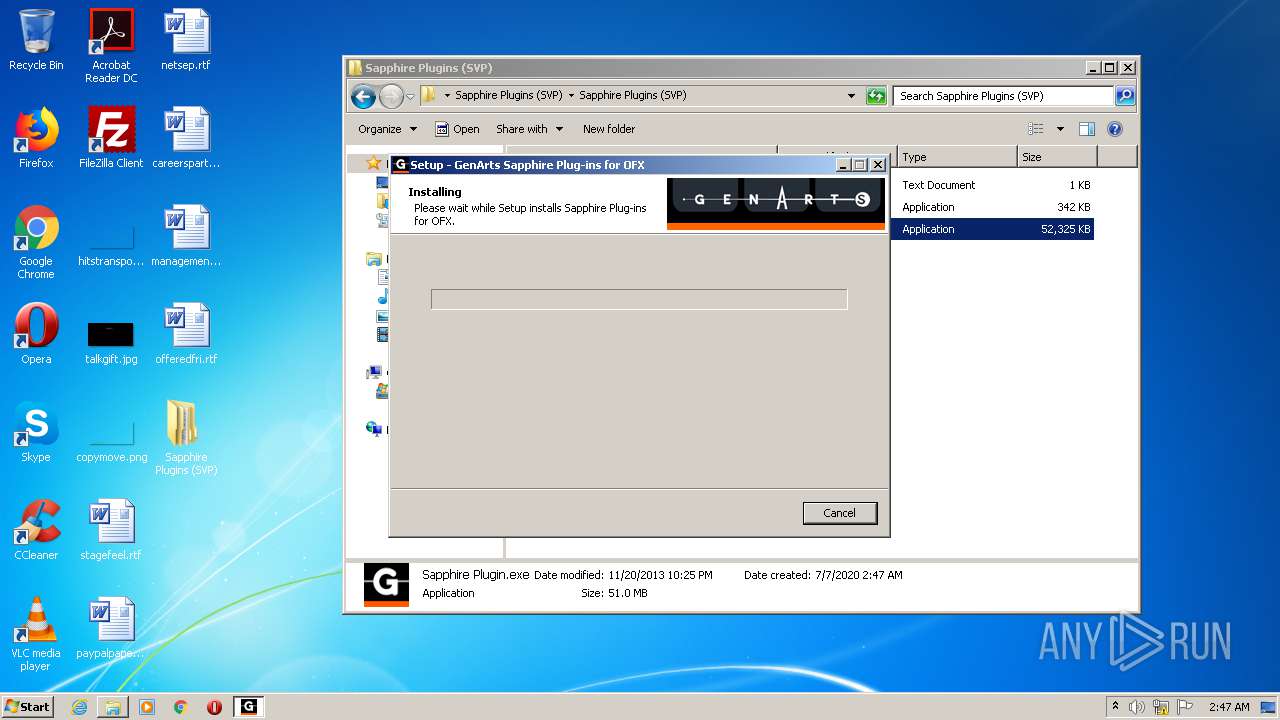
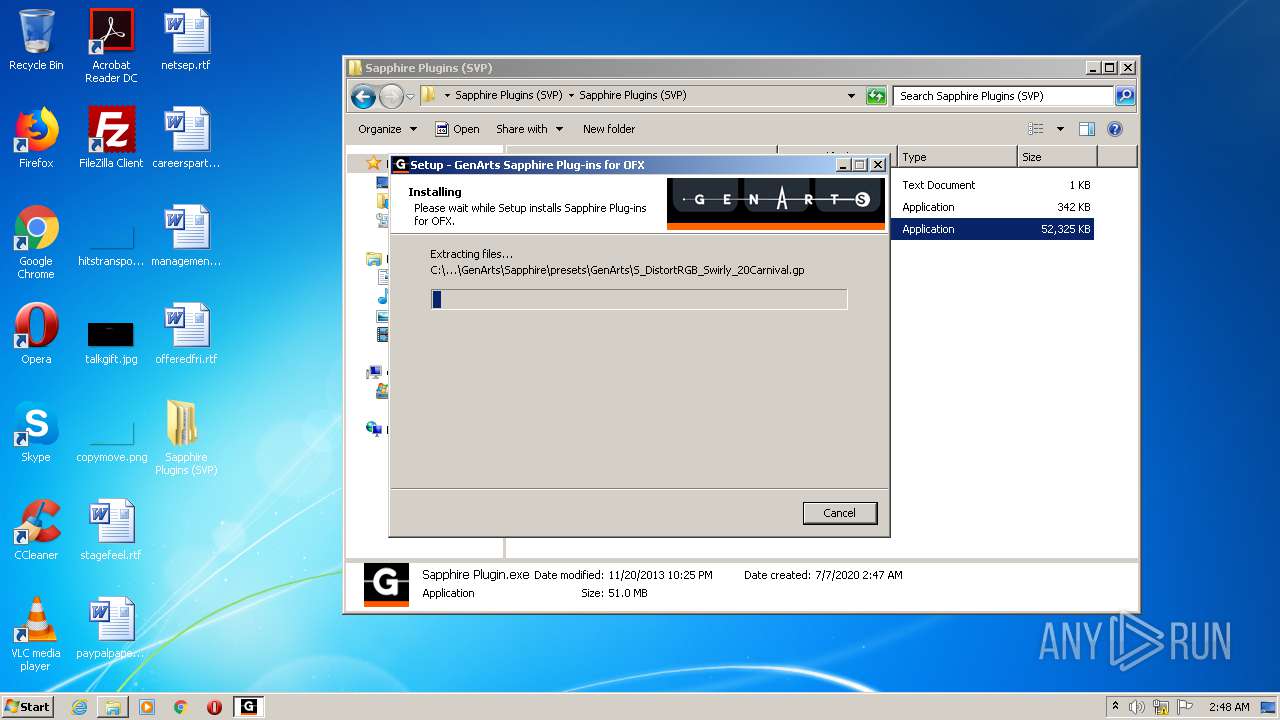
- Sapphire Plugin.exe (PID: 4708)
- Sapphire Plugin.exe (PID: 5204)
- Sapphire Plugin.tmp (PID: 2968)
- vcredist_x86.exe (PID: 900)
- msiexec.exe (PID: 860)
Creates files in the Windows directory
- msiexec.exe (PID: 860)
- license-install.exe (PID: 2940)
- Sapphire Plugin.tmp (PID: 2968)
Removes files from Windows directory
- msiexec.exe (PID: 860)
Adds / modifies Windows certificates
- msiexec.exe (PID: 860)
Modifies the open verb of a shell class
- Sapphire Plugin.tmp (PID: 2968)
INFO
Application launched itself
- chrome.exe (PID: 440)
- firefox.exe (PID: 4016)
Reads the hosts file
- chrome.exe (PID: 3972)
- chrome.exe (PID: 440)
Manual execution by user
- firefox.exe (PID: 3492)
- WinRAR.exe (PID: 4308)
- Sapphire Plugin.exe (PID: 4708)
- Patch.exe (PID: 5652)
- Patch.exe (PID: 4580)
Creates files in the user directory
- firefox.exe (PID: 4016)
Reads CPU info
- firefox.exe (PID: 4016)
Reads Internet Cache Settings
- pingsender.exe (PID: 6068)
- firefox.exe (PID: 4016)
- chrome.exe (PID: 440)
Dropped object may contain Bitcoin addresses
- chrome.exe (PID: 440)
- install.exe (PID: 4288)
- msiexec.exe (PID: 860)
- Sapphire Plugin.tmp (PID: 2968)
Adds / modifies Windows certificates
- pingsender.exe (PID: 6068)
Application was dropped or rewritten from another process
- Sapphire Plugin.tmp (PID: 4956)
- Sapphire Plugin.tmp (PID: 2968)
- license-install.exe (PID: 2940)
- vcredist_x86.exe (PID: 900)
Loads dropped or rewritten executable
- Sapphire Plugin.tmp (PID: 2968)
Creates a software uninstall entry
- msiexec.exe (PID: 860)
- Sapphire Plugin.tmp (PID: 2968)
Changes settings of System certificates
- pingsender.exe (PID: 6068)
Creates files in the program directory
- Sapphire Plugin.tmp (PID: 2968)
Reads settings of System Certificates
- chrome.exe (PID: 3972)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
129
Monitored processes
77
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 276 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=948,2265464923057055325,10575776886565743581,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=3057616682836972529 --renderer-client-id=27 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4408 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 440 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "http://www.mediafire.com/file/q43qeudx89gjd46/Sapphire_Plugins_%2528SVP%2529.rar/file" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 3221225547 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 620 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=948,2265464923057055325,10575776886565743581,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=662952052215371633 --renderer-client-id=18 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4476 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 860 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 900 | "C:\Users\admin\AppData\Local\Temp\is-F5Q0M.tmp\vcredist_x86" /q | C:\Users\admin\AppData\Local\Temp\is-F5Q0M.tmp\vcredist_x86.exe | Sapphire Plugin.tmp | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2008 Redistributable Setup Exit code: 0 Version: 9.0.21022.08 Modules
| |||||||||||||||
| 992 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=948,2265464923057055325,10575776886565743581,131072 --enable-features=PasswordImport --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=11104966320568467675 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2580 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1216 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=948,2265464923057055325,10575776886565743581,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=6057192916620724609 --renderer-client-id=26 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4172 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1264 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=948,2265464923057055325,10575776886565743581,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=2059950028833460947 --renderer-client-id=35 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4484 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1500 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=948,2265464923057055325,10575776886565743581,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=601229762456112130 --renderer-client-id=32 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3808 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1552 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=948,2265464923057055325,10575776886565743581,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=3958295372129887790 --renderer-client-id=16 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4632 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
5 727
Read events
4 220
Write events
1 468
Delete events
39
Modification events
| (PID) Process: | (440) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (440) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (440) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (440) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (440) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2184) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 440-13238559938993250 |
Value: 259 | |||
| (PID) Process: | (440) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (440) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (440) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3120-13213713943555664 |
Value: 0 | |||
| (PID) Process: | (440) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
144
Suspicious files
172
Text files
2 895
Unknown types
84
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 440 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-5F03D3C4-1B8.pma | — | |
MD5:— | SHA256:— | |||
| 440 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | — | |
MD5:— | SHA256:— | |||
| 440 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\23f88e38-6716-46fd-ab65-9a4b3c444f85.tmp | — | |
MD5:— | SHA256:— | |||
| 440 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000028.dbtmp | — | |
MD5:— | SHA256:— | |||
| 440 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Last Tabs | binary | |
MD5:— | SHA256:— | |||
| 440 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old~RF15d4ce.TMP | text | |
MD5:— | SHA256:— | |||
| 440 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 440 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF15d432.TMP | text | |
MD5:— | SHA256:— | |||
| 440 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 440 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RF15d645.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
45
TCP/UDP connections
173
DNS requests
171
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3972 | chrome.exe | GET | — | 199.91.155.8:80 | http://download2267.mediafire.com/31tgp1sp1sqg/q43qeudx89gjd46/Sapphire+Plugins+%28SVP%29.rar | US | — | — | suspicious |
3972 | chrome.exe | GET | 200 | 172.217.22.46:80 | http://translate.google.com/translate_a/element.js?cb=googFooterTranslate | US | text | 796 b | whitelisted |
3972 | chrome.exe | GET | 200 | 104.16.202.237:80 | http://www.mediafire.com/file/q43qeudx89gjd46/Sapphire_Plugins_%2528SVP%2529.rar/file | US | html | 83.7 Kb | shared |
3972 | chrome.exe | GET | 200 | 104.16.202.237:80 | http://www.mediafire.com/js/prebid2.44.1.js | US | text | 52.9 Kb | shared |
3972 | chrome.exe | GET | 200 | 104.16.202.237:80 | http://www.mediafire.com/images/icons/svg_light/icons_sprite.svg | US | image | 8.40 Kb | shared |
3972 | chrome.exe | GET | 200 | 104.16.203.237:80 | http://static.mediafire.com/images/backgrounds/download/apps_list_sprite-v4.png | US | image | 6.78 Kb | shared |
3972 | chrome.exe | POST | 200 | 185.33.221.13:80 | http://ib.adnxs.com/ut/v3/prebid | unknown | text | 242 b | whitelisted |
3972 | chrome.exe | GET | 200 | 205.185.216.10:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.0 Kb | whitelisted |
3972 | chrome.exe | GET | 200 | 205.185.216.10:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.0 Kb | whitelisted |
3972 | chrome.exe | GET | 200 | 104.16.203.237:80 | http://static.mediafire.com/images/backgrounds/header/mf_logo_full_color.svg | US | image | 1.51 Kb | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3972 | chrome.exe | 172.217.23.131:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3972 | chrome.exe | 104.16.202.237:80 | www.mediafire.com | Cloudflare Inc | US | unknown |
3972 | chrome.exe | 172.217.16.173:443 | accounts.google.com | Google Inc. | US | whitelisted |
3972 | chrome.exe | 172.217.22.46:80 | translate.google.com | Google Inc. | US | whitelisted |
3972 | chrome.exe | 216.58.206.8:443 | www.googletagmanager.com | Google Inc. | US | whitelisted |
3972 | chrome.exe | 23.0.43.79:443 | c.aaxads.com | Akamai Technologies, Inc. | NL | unknown |
3972 | chrome.exe | 172.217.21.226:443 | securepubads.g.doubleclick.net | Google Inc. | US | whitelisted |
3972 | chrome.exe | 172.217.16.206:443 | clients1.google.com | Google Inc. | US | whitelisted |
3972 | chrome.exe | 185.33.221.13:80 | ib.adnxs.com | AppNexus, Inc | — | unknown |
3972 | chrome.exe | 185.64.189.112:443 | hbopenbid.pubmatic.com | PubMatic, Inc. | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.mediafire.com |
| shared |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.googletagmanager.com |
| whitelisted |
translate.google.com |
| whitelisted |
securepubads.g.doubleclick.net |
| whitelisted |
c.aaxads.com |
| whitelisted |
static.mediafire.com |
| shared |
blog.mediafire.com |
| whitelisted |
download2267.mediafire.com |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3972 | chrome.exe | Misc Attack | ET DROP Dshield Block Listed Source group 1 |
1040 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |
1040 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |