| File name: | multiloginx-amd64 (7).exe |
| Full analysis: | https://app.any.run/tasks/af90a3bd-9206-410b-a8a0-8f2ea3670f27 |
| Verdict: | Malicious activity |
| Analysis date: | August 26, 2024, 13:54:50 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 6ED54996ECCD717A5F0DB930D835E54C |
| SHA1: | FF339B31D1088B5DE4BE230CAECF1E235E294CC7 |
| SHA256: | 99C506D2026E2947D9470F5CD8F1EDB5A28F1FED5B647E1E794763BF6AB389A9 |
| SSDEEP: | 98304:6rq3BdwRZAiSJ0+j0gnlQ7ehEiSvWUPz28/uhlxD5qrUme5uPJiWXQaI7dbL7PD5:P9JXKS3uArL |
MALICIOUS
Changes powershell execution policy (Bypass)
- multiloginx-amd64 (7).tmp (PID: 6292)
- agent.exe (PID: 4820)
Bypass execution policy to execute commands
- powershell.exe (PID: 5388)
- powershell.exe (PID: 7104)
- powershell.exe (PID: 5244)
- powershell.exe (PID: 6996)
- powershell.exe (PID: 1448)
Modifies hosts file to block updates
- powershell.exe (PID: 5388)
Adds path to the Windows Defender exclusion list
- multiloginx-amd64 (7).tmp (PID: 6292)
SUSPICIOUS
Drops the executable file immediately after the start
- multiloginx-amd64 (7).exe (PID: 1184)
- multiloginx-amd64 (7).exe (PID: 532)
- multiloginx-amd64 (7).tmp (PID: 6292)
- agent.exe (PID: 4820)
Executable content was dropped or overwritten
- multiloginx-amd64 (7).exe (PID: 1184)
- multiloginx-amd64 (7).exe (PID: 532)
- multiloginx-amd64 (7).tmp (PID: 6292)
- agent.exe (PID: 4820)
Reads security settings of Internet Explorer
- multiloginx-amd64 (7).tmp (PID: 6496)
Reads the date of Windows installation
- multiloginx-amd64 (7).tmp (PID: 6496)
Starts POWERSHELL.EXE for commands execution
- multiloginx-amd64 (7).tmp (PID: 6292)
- agent.exe (PID: 4820)
Reads the Windows owner or organization settings
- multiloginx-amd64 (7).tmp (PID: 6292)
The process executes Powershell scripts
- multiloginx-amd64 (7).tmp (PID: 6292)
- agent.exe (PID: 4820)
Checks a user's role membership (POWERSHELL)
- powershell.exe (PID: 5388)
Creates files in the driver directory
- powershell.exe (PID: 5388)
Script adds exclusion path to Windows Defender
- multiloginx-amd64 (7).tmp (PID: 6292)
The process bypasses the loading of PowerShell profile settings
- agent.exe (PID: 4820)
INFO
Reads Environment values
- multiloginx-amd64 (7).exe (PID: 1184)
- multiloginx-amd64 (7).tmp (PID: 6496)
- multiloginx-amd64 (7).exe (PID: 532)
- multiloginx-amd64 (7).tmp (PID: 6292)
Checks supported languages
- multiloginx-amd64 (7).tmp (PID: 6496)
- multiloginx-amd64 (7).exe (PID: 1184)
- multiloginx-amd64 (7).exe (PID: 532)
- multiloginx-amd64 (7).tmp (PID: 6292)
- agent.exe (PID: 4820)
- launcher-windows_amd64.exe (PID: 6260)
Create files in a temporary directory
- multiloginx-amd64 (7).exe (PID: 1184)
- multiloginx-amd64 (7).exe (PID: 532)
- multiloginx-amd64 (7).tmp (PID: 6292)
- agent.exe (PID: 4820)
Reads the computer name
- multiloginx-amd64 (7).tmp (PID: 6496)
- multiloginx-amd64 (7).exe (PID: 532)
- multiloginx-amd64 (7).tmp (PID: 6292)
- agent.exe (PID: 4820)
Process checks computer location settings
- multiloginx-amd64 (7).tmp (PID: 6496)
Creates files or folders in the user directory
- multiloginx-amd64 (7).tmp (PID: 6292)
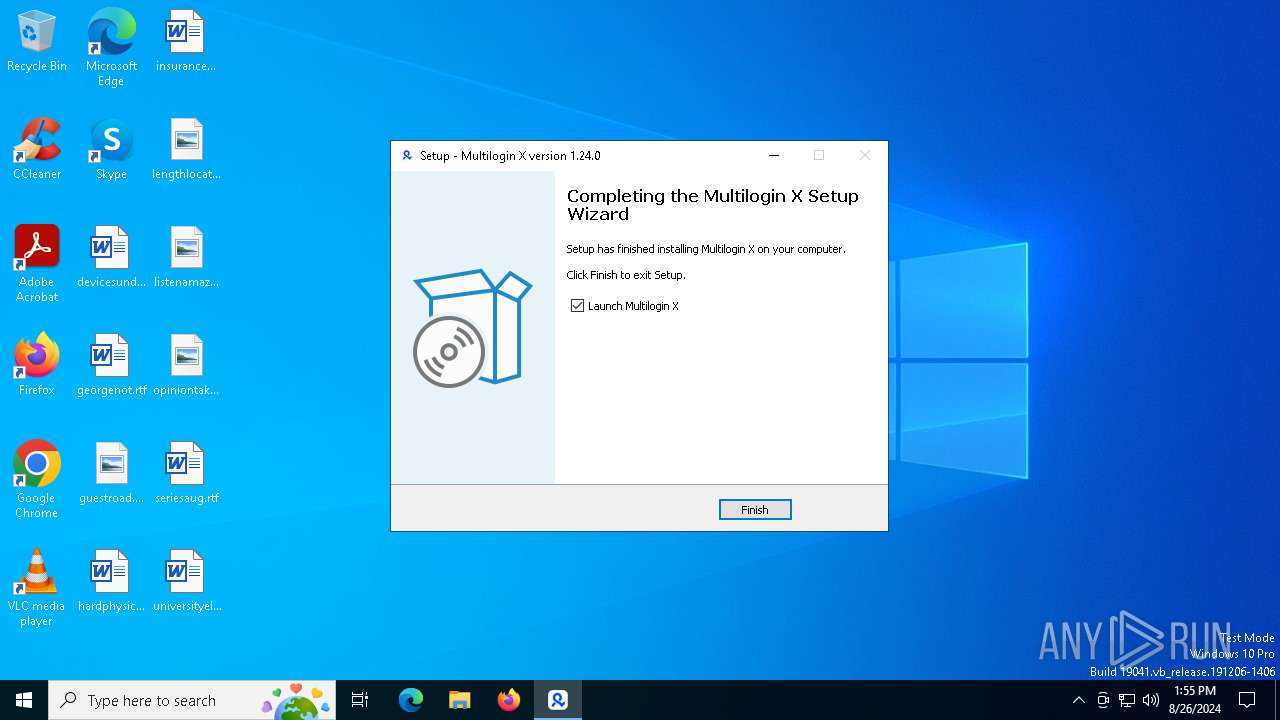
Creates a software uninstall entry
- multiloginx-amd64 (7).tmp (PID: 6292)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7104)
- powershell.exe (PID: 6996)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7104)
Reads the software policy settings
- agent.exe (PID: 4820)
Reads the machine GUID from the registry
- agent.exe (PID: 4820)
- launcher-windows_amd64.exe (PID: 6260)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (67.7) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (25.6) |
| .exe | | | Win32 Executable (generic) (2.7) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
| .exe | | | Generic Win/DOS Executable (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:06:09 05:41:36+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 685056 |
| InitializedDataSize: | 140800 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa83bc |
| OSVersion: | 6.1 |
| ImageVersion: | - |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
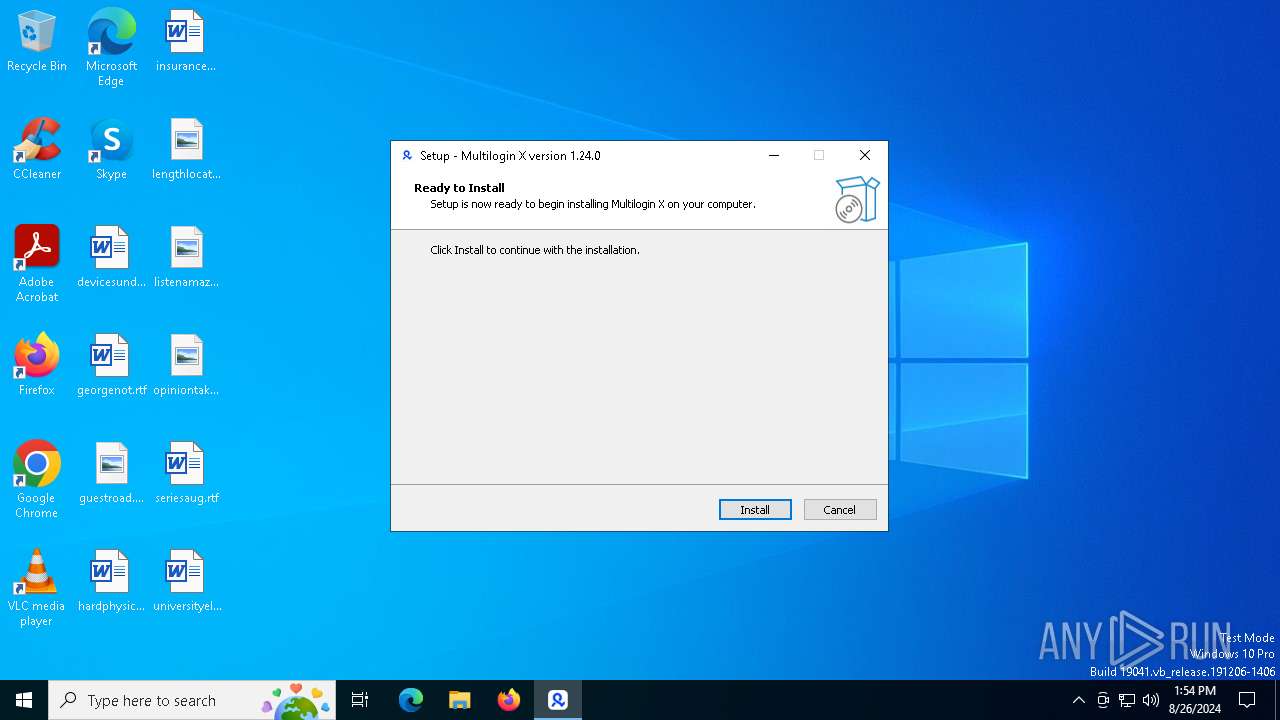
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | multilogin.com |
| FileDescription: | Multilogin X Setup |
| FileVersion: | |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | Multilogin X |
| ProductVersion: | 1.24.0 |
Total processes
146
Monitored processes
19
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 532 | "C:\Users\admin\AppData\Local\Temp\multiloginx-amd64 (7).exe" /SPAWNWND=$A02A2 /NOTIFYWND=$F035E | C:\Users\admin\AppData\Local\Temp\multiloginx-amd64 (7).exe | multiloginx-amd64 (7).tmp | ||||||||||||
User: admin Company: multilogin.com Integrity Level: HIGH Description: Multilogin X Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 1184 | "C:\Users\admin\AppData\Local\Temp\multiloginx-amd64 (7).exe" | C:\Users\admin\AppData\Local\Temp\multiloginx-amd64 (7).exe | explorer.exe | ||||||||||||
User: admin Company: multilogin.com Integrity Level: MEDIUM Description: Multilogin X Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 1448 | PowerShell -ExecutionPolicy Bypass -File C:\Users\admin\AppData\Local\Temp\03da5fb4-511c-413f-6d8c-61c083e8dfd1.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | agent.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2660 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | launcher-windows_amd64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2816 | powershell -NoProfile Get-StartApps | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | agent.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4820 | "C:\Users\admin\AppData\Local\Multilogin X\agent.exe" | C:\Users\admin\AppData\Local\Multilogin X\agent.exe | multiloginx-amd64 (7).tmp | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 4920 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5244 | PowerShell -ExecutionPolicy Bypass -File C:\Users\admin\AppData\Local\Temp\18e2030d-ebdf-470a-6668-6ec0ef7f5dde.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | agent.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5388 | "powershell.exe" -ExecutionPolicy Bypass -File "C:\Users\admin\AppData\Local\Temp\is-DD67T.tmp\set_host.ps1" -agent "MLX" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | multiloginx-amd64 (7).tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5516 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
49 173
Read events
48 877
Write events
290
Delete events
6
Modification events
| (PID) Process: | (6292) multiloginx-amd64 (7).tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 941800005B65FD89BFF7DA01 | |||
| (PID) Process: | (6292) multiloginx-amd64 (7).tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 426CE6536A24731CA26CC3FEEC09FF304422CEF23984BDE63E1E0C286786B2D8 | |||
| (PID) Process: | (6292) multiloginx-amd64 (7).tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (6292) multiloginx-amd64 (7).tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Users\admin\AppData\Local\Multilogin X\agent.exe | |||
| (PID) Process: | (6292) multiloginx-amd64 (7).tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: 1A7BE3D75C961EEE611EA9FA79E89F5AAC2F4857C9E1D3614F39E64A99F068D1 | |||
| (PID) Process: | (6292) multiloginx-amd64 (7).tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\mlx |
| Operation: | write | Name: | URL Protocol |
Value: | |||
| (PID) Process: | (6292) multiloginx-amd64 (7).tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{2f1be220-a5fc-4fc5-8375-3573cf225fec}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.3.0 | |||
| (PID) Process: | (6292) multiloginx-amd64 (7).tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{2f1be220-a5fc-4fc5-8375-3573cf225fec}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Users\admin\AppData\Local\Multilogin X | |||
| (PID) Process: | (6292) multiloginx-amd64 (7).tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{2f1be220-a5fc-4fc5-8375-3573cf225fec}_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Users\admin\AppData\Local\Multilogin X\ | |||
| (PID) Process: | (6292) multiloginx-amd64 (7).tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{2f1be220-a5fc-4fc5-8375-3573cf225fec}_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: Multilogin X | |||
Executable files
9
Suspicious files
2
Text files
32
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 532 | multiloginx-amd64 (7).exe | C:\Users\admin\AppData\Local\Temp\is-EEFRG.tmp\multiloginx-amd64 (7).tmp | executable | |
MD5:86B7CA354FC74604F0C230B247B47F23 | SHA256:9097A82D4282AA5F0D0CB94620B2FFCE774FE7D6CD22E7C802722668F643E274 | |||
| 6292 | multiloginx-amd64 (7).tmp | C:\Users\admin\AppData\Local\Multilogin X\unins000.exe | executable | |
MD5:941362BA6CB18F9669AFE8F388974B1E | SHA256:E90E10FA05AA9B43086A78018ACDC853FD49D16D445A8D43E54B7642D8D90D28 | |||
| 6292 | multiloginx-amd64 (7).tmp | C:\Users\admin\AppData\Local\Multilogin X\is-CI76O.tmp | executable | |
MD5:941362BA6CB18F9669AFE8F388974B1E | SHA256:E90E10FA05AA9B43086A78018ACDC853FD49D16D445A8D43E54B7642D8D90D28 | |||
| 6292 | multiloginx-amd64 (7).tmp | C:\Users\admin\AppData\Local\Multilogin X\is-AJO67.tmp | executable | |
MD5:1339FCA8579859D4A31F0D89066AB880 | SHA256:026978405E9B4945CE575C7BE782511D2CAC81345F1F1441E046C74E8D8E1C52 | |||
| 6292 | multiloginx-amd64 (7).tmp | C:\Users\admin\AppData\Local\Temp\is-DD67T.tmp\is-B2IMK.tmp | text | |
MD5:EFD10786E9F3E2861A5F1812C4EAB046 | SHA256:4EBCA76A670C2D935FC8FE0BA87ED74A3B91233E23EA8DFAED79FB1E075426E5 | |||
| 1184 | multiloginx-amd64 (7).exe | C:\Users\admin\AppData\Local\Temp\is-CREM6.tmp\multiloginx-amd64 (7).tmp | executable | |
MD5:86B7CA354FC74604F0C230B247B47F23 | SHA256:9097A82D4282AA5F0D0CB94620B2FFCE774FE7D6CD22E7C802722668F643E274 | |||
| 6292 | multiloginx-amd64 (7).tmp | C:\Users\admin\AppData\Local\Temp\is-DD67T.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 6292 | multiloginx-amd64 (7).tmp | C:\Users\admin\AppData\Local\Multilogin X\unins000.dat | dat | |
MD5:672F952DB4067E8E26C2F9675742C1A8 | SHA256:8F8201EDC527DA16F27559668AA1074BC0259A9E251BB26722F6B8EF497A8855 | |||
| 6292 | multiloginx-amd64 (7).tmp | C:\Users\admin\AppData\Local\Temp\is-DD67T.tmp\add_firewall_rules.ps1 | text | |
MD5:E9A81546BEC2BAF0F3264E4A8F6DCF7F | SHA256:0EFD8622E645418832E975BC1BFF6C619863DC7794E5BF1355C30D18A8315744 | |||
| 7104 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_w02e0ify.ifv.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
21
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2144 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6480 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6480 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6208 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6164 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6164 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2144 | svchost.exe | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2144 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6480 | SIHClient.exe | 40.68.123.157:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
mlxdists.s3.eu-west-3.amazonaws.com |
| shared |