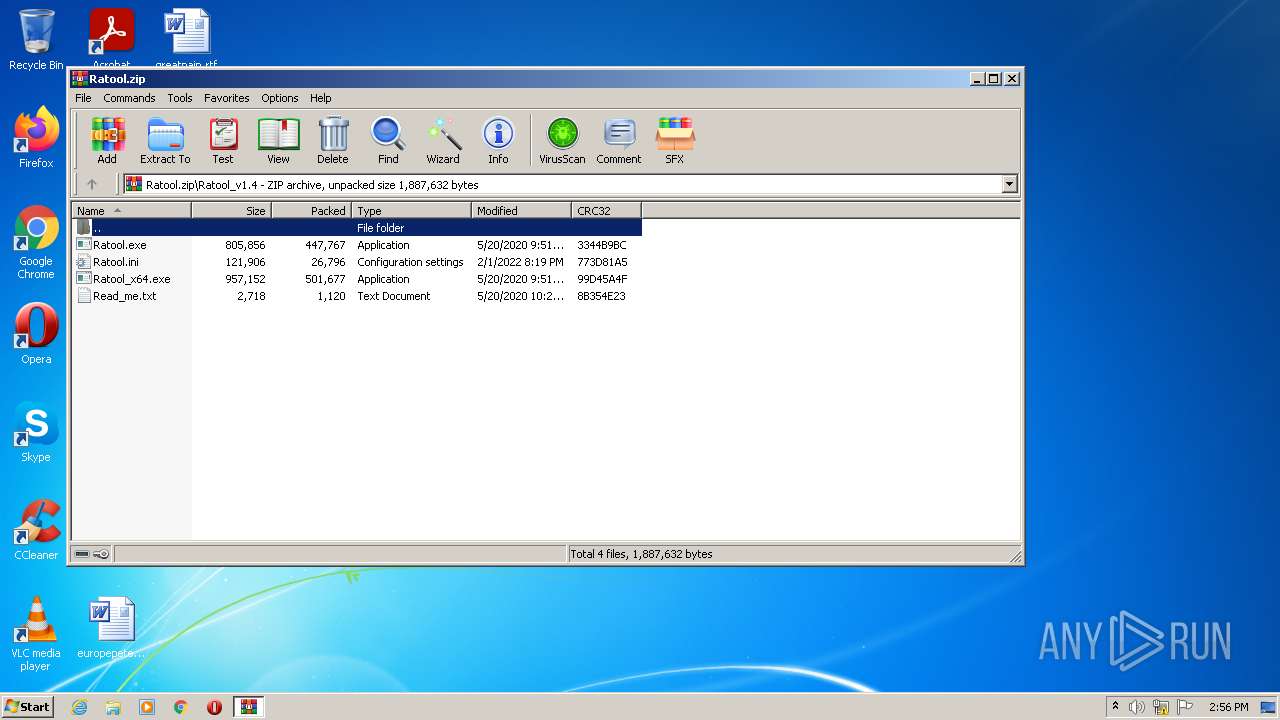
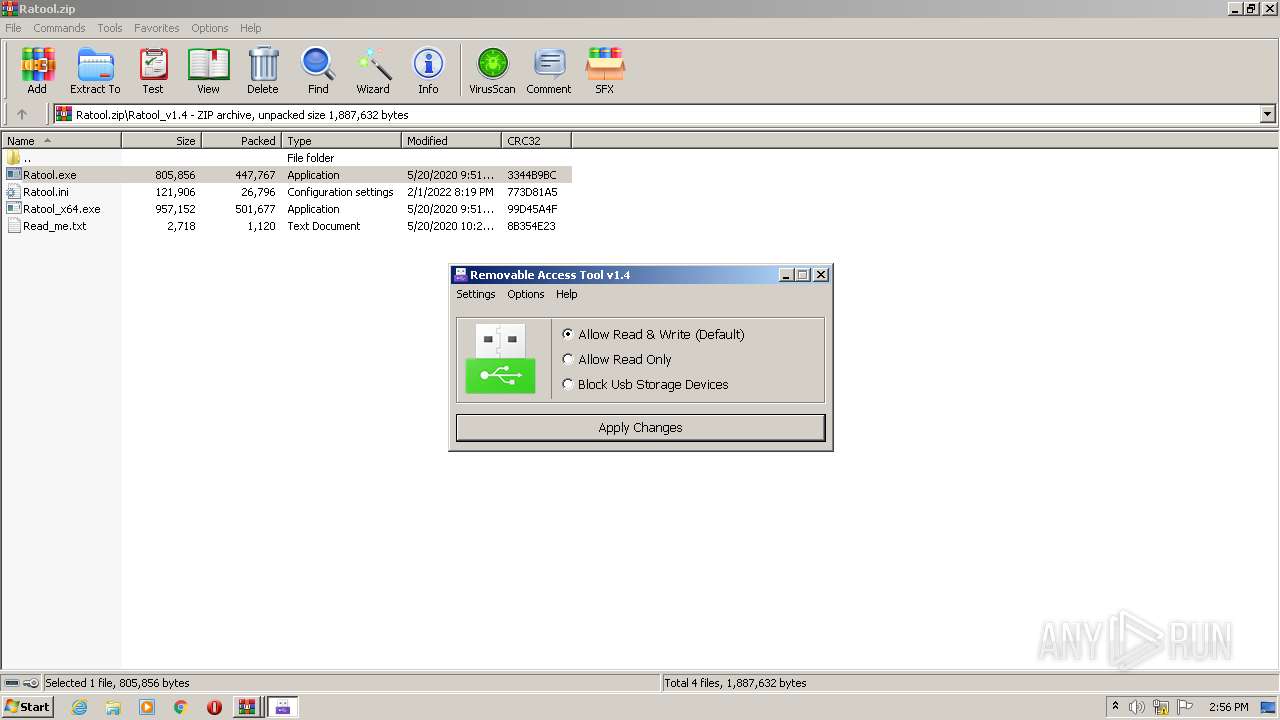
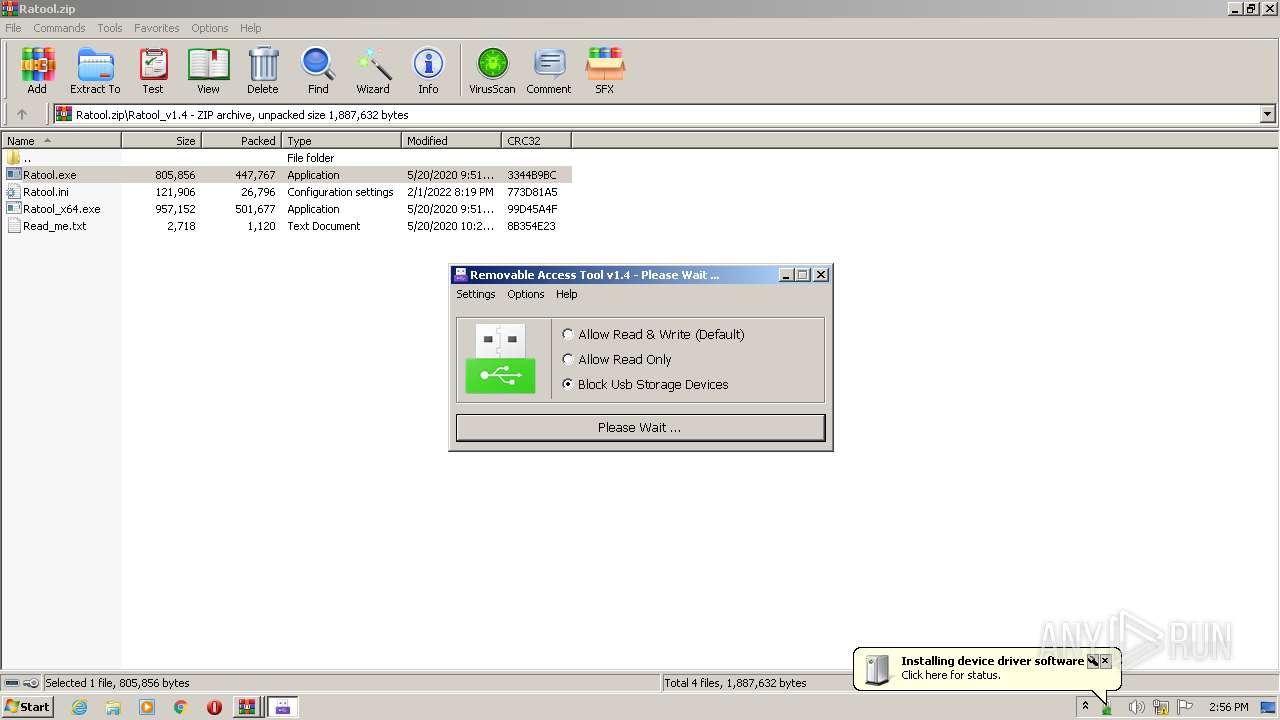
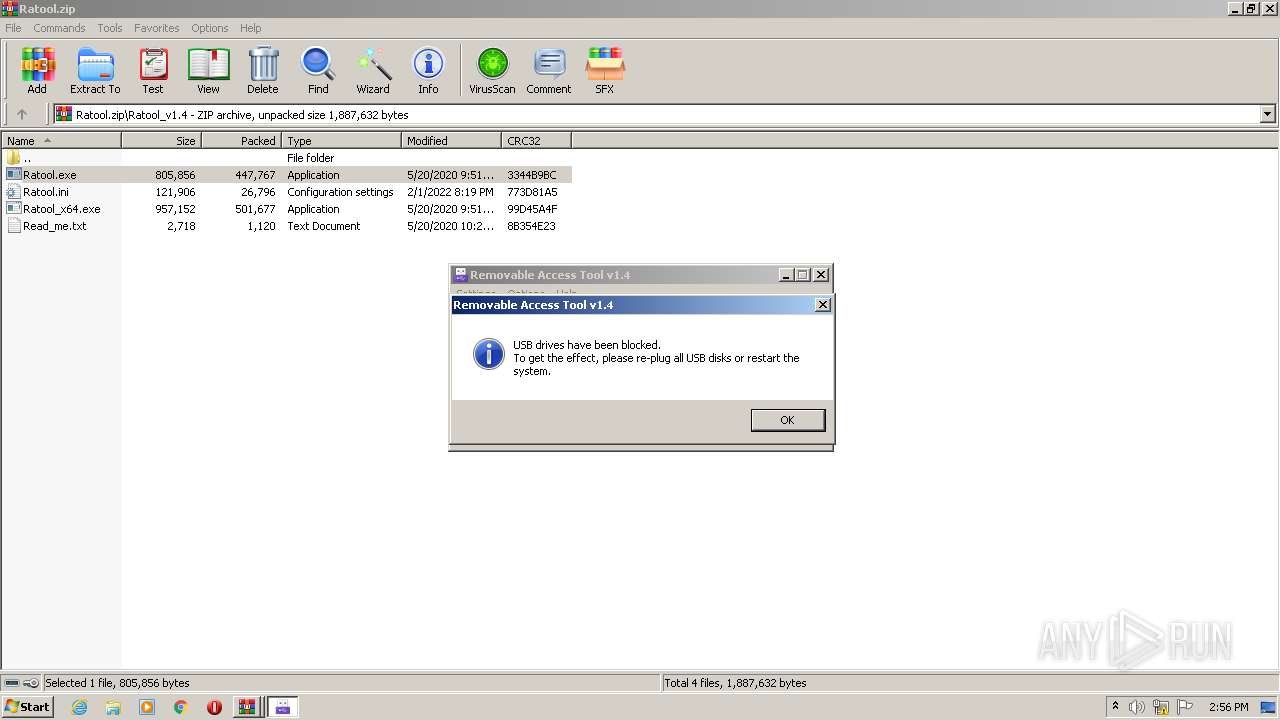
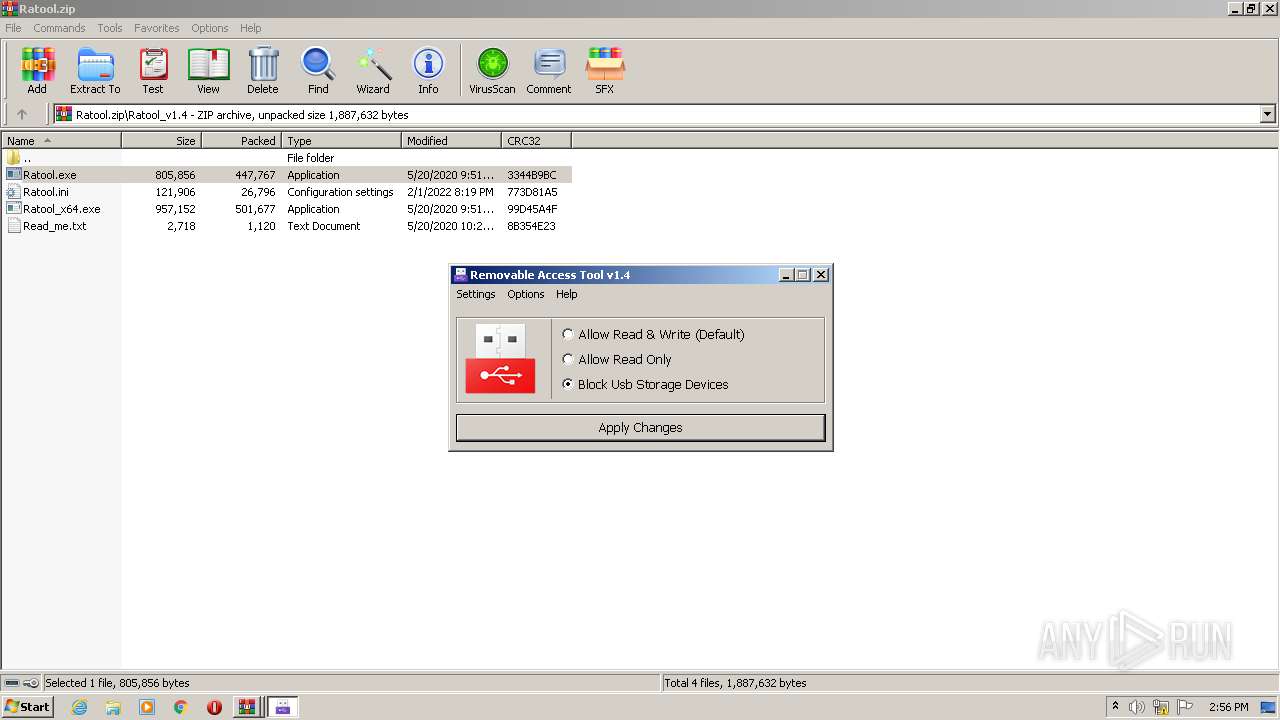
| File name: | Ratool.zip |
| Full analysis: | https://app.any.run/tasks/1dd91a8d-566d-4cba-8997-77a6ed6aeb90 |
| Verdict: | Malicious activity |
| Analysis date: | August 12, 2022, 13:56:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | CA2A75E392532DE2B6BBB3A586DB5ECB |
| SHA1: | B55F2428D6ACA42CDA42D13CB262D0B80A7352A2 |
| SHA256: | 99C3FE54A4F318FA495180D0EFD25376DCE6610EB9AFA44C46E113F555D1F977 |
| SSDEEP: | 24576:DiYtxjdQcY7dgAs3tvx/x4kf6jhXT/ddDA4zk4SygAS9ToAZ2CEJ:eY3dQV83tvx/byjhXTj84z1/gAooAAV |
MALICIOUS
Drops executable file immediately after starts
- WinRAR.exe (PID: 3448)
Application was dropped or rewritten from another process
- Ratool.exe (PID: 3876)
- Ratool.exe (PID: 416)
SUSPICIOUS
Executed via COM
- rundll32.exe (PID: 3944)
- DrvInst.exe (PID: 2324)
- rundll32.exe (PID: 1560)
- DrvInst.exe (PID: 3352)
- DrvInst.exe (PID: 2972)
Checks supported languages
- DrvInst.exe (PID: 2972)
- WinRAR.exe (PID: 3448)
- DrvInst.exe (PID: 2324)
- DrvInst.exe (PID: 3352)
- Ratool.exe (PID: 3876)
Reads the computer name
- DrvInst.exe (PID: 2972)
- WinRAR.exe (PID: 3448)
- DrvInst.exe (PID: 2324)
- DrvInst.exe (PID: 3352)
- Ratool.exe (PID: 3876)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3448)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3448)
Reads mouse settings
- Ratool.exe (PID: 3876)
Creates or modifies windows services
- Ratool.exe (PID: 3876)
INFO
Checks supported languages
- NOTEPAD.EXE (PID: 2396)
- dinotify.exe (PID: 3108)
- rundll32.exe (PID: 3944)
- rundll32.exe (PID: 1560)
Checks Windows Trust Settings
- DrvInst.exe (PID: 2972)
- DrvInst.exe (PID: 2324)
- DrvInst.exe (PID: 3352)
Reads the computer name
- rundll32.exe (PID: 3944)
- dinotify.exe (PID: 3108)
Reads settings of System Certificates
- DrvInst.exe (PID: 2972)
- DrvInst.exe (PID: 2324)
- DrvInst.exe (PID: 3352)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | Ratool_v1.4/ |
|---|---|
| ZipUncompressedSize: | - |
| ZipCompressedSize: | - |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 2020:05:20 11:51:12 |
| ZipCompression: | None |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
57
Monitored processes
10
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 416 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3448.24830\Ratool_v1.4\Ratool.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3448.24830\Ratool_v1.4\Ratool.exe | — | WinRAR.exe | |||||||||||
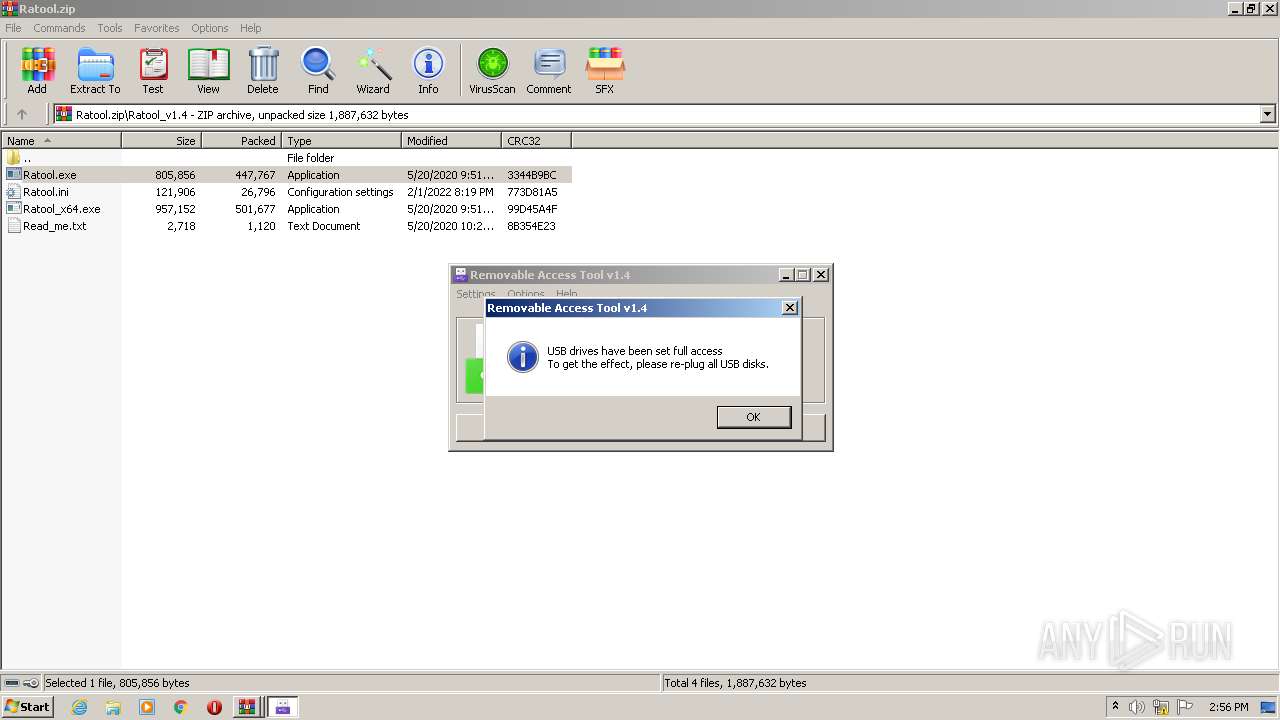
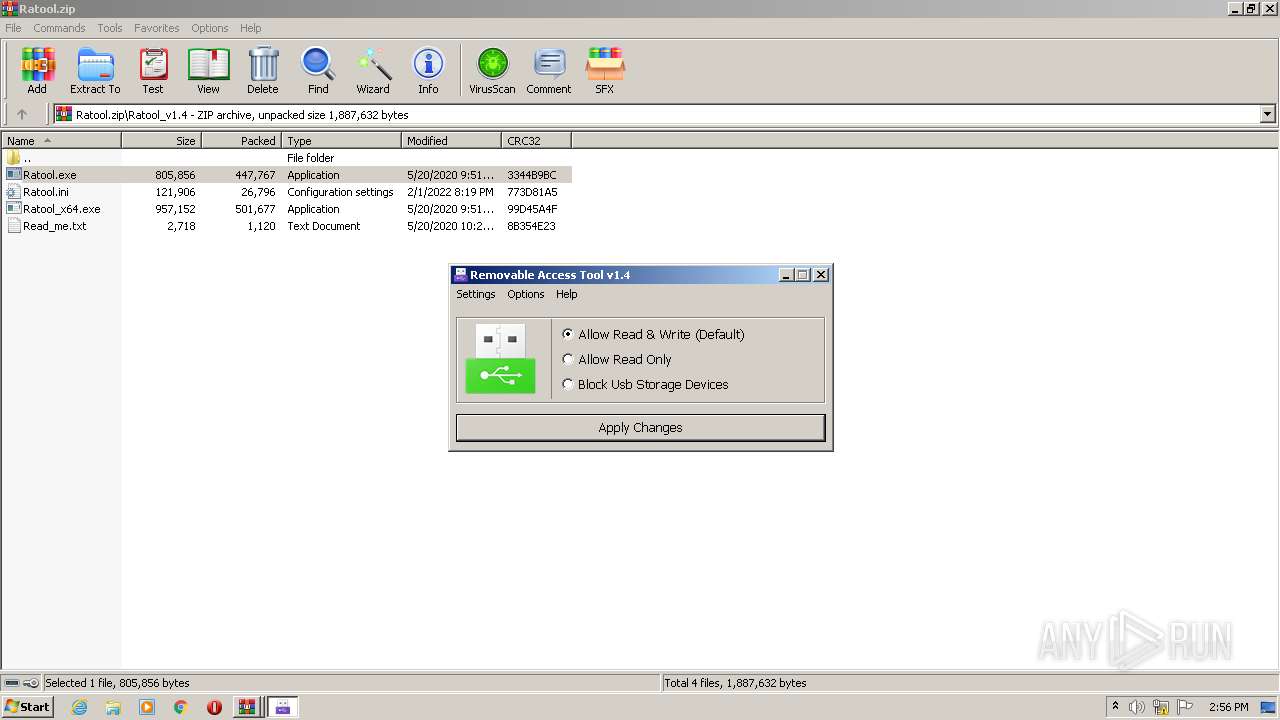
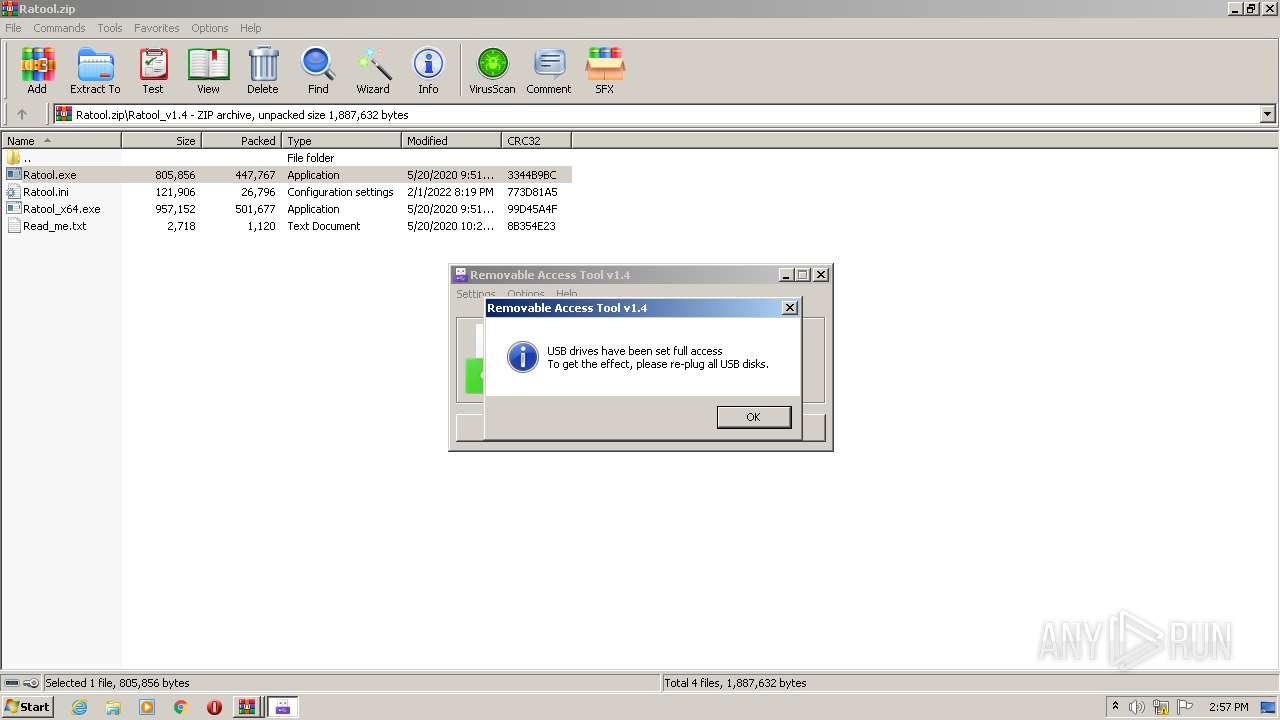
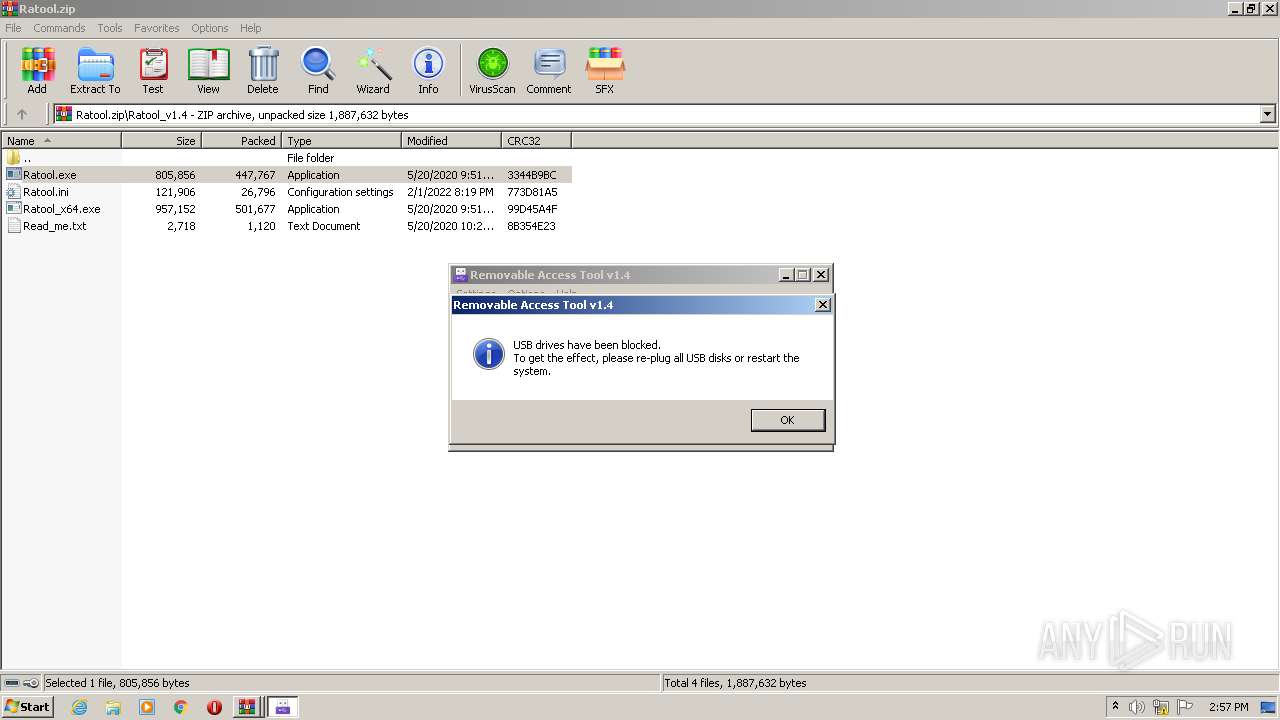
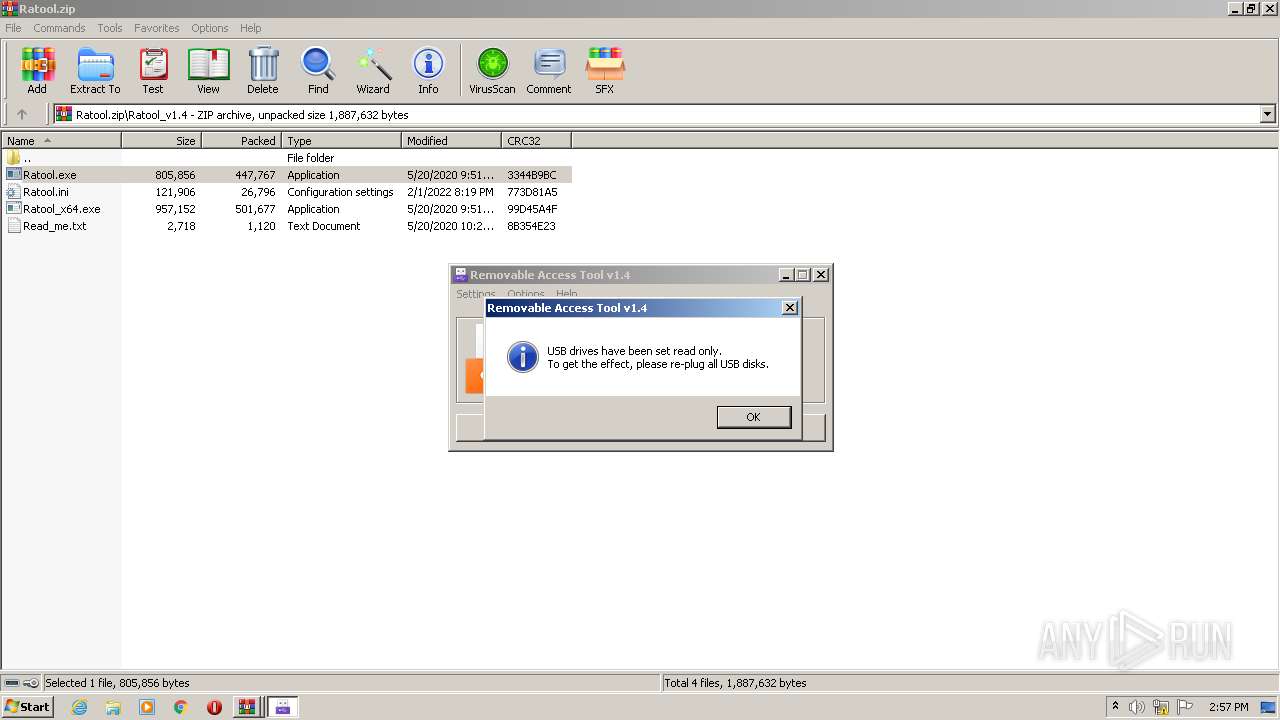
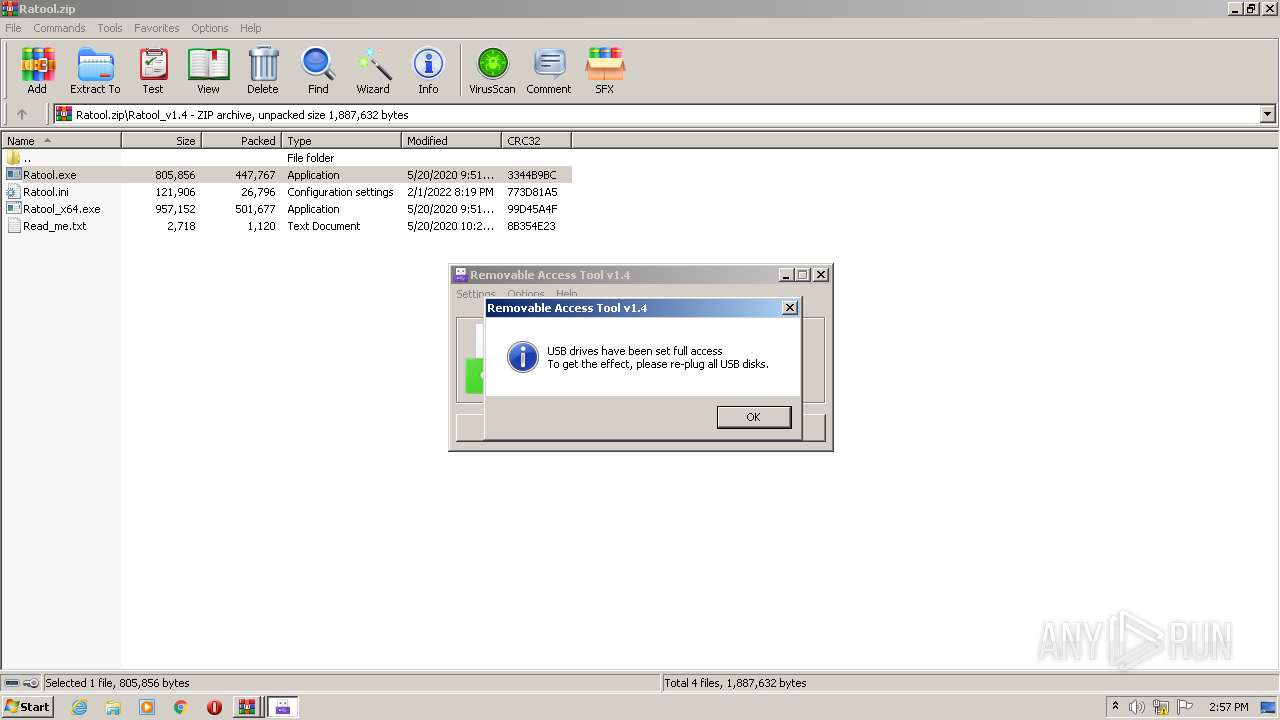
User: admin Company: www.sordum.org Integrity Level: MEDIUM Description: Removable Access Tool Exit code: 3221226540 Version: 1.4.0.0 Modules
| |||||||||||||||
| 1560 | C:\Windows\System32\rundll32.exe shell32.dll,SHCreateLocalServerRunDll {995C996E-D918-4a8c-A302-45719A6F4EA7} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2324 | DrvInst.exe "1" "200" "SCSI\Disk&Ven_Msft&Prod_Virtual_Disk\2&1f4adffe&0&000001" "" "" "69911eaf3" "00000000" "000005C8" "00000640" | C:\Windows\system32\DrvInst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2396 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa3448.23527\Ratool.ini | C:\Windows\system32\NOTEPAD.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2972 | DrvInst.exe "1" "200" "{8e7bd593-6e6c-4c52-86a6-77175494dd8e}\MsVhdHba\1&3030e83&0&01" "" "" "66583b687" "00000000" "0000039C" "00000404" | C:\Windows\system32\DrvInst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3108 | "C:\Windows\System32\dinotify.exe" pnpui.dll,SimplifiedDINotification | C:\Windows\System32\dinotify.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Device Installation Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3352 | DrvInst.exe "1" "200" "SCSI\Disk&Ven_Msft&Prod_Virtual_Disk\2&1f4adffe&0&000002" "" "" "6351683ab" "00000000" "0000063C" "00000630" | C:\Windows\system32\DrvInst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3448 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Ratool.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3876 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3448.24830\Ratool_v1.4\Ratool.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3448.24830\Ratool_v1.4\Ratool.exe | WinRAR.exe | ||||||||||||
User: admin Company: www.sordum.org Integrity Level: HIGH Description: Removable Access Tool Exit code: 0 Version: 1.4.0.0 Modules
| |||||||||||||||
| 3944 | rundll32.exe C:\Windows\system32\newdev.dll,pDiDeviceInstallNotification \\.\pipe\PNP_Device_Install_Pipe_1.{e3f4257d-e19b-4d4d-91d3-63b4f2c2bc34} "(null)" | C:\Windows\system32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
10 338
Read events
10 160
Write events
164
Delete events
14
Modification events
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Ratool.zip | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
4
Suspicious files
6
Text files
7
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3448.24050\Ratool_v1.4\Ratool.ini | text | |
MD5:— | SHA256:— | |||
| 3448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3448.23527\Ratool.ini | text | |
MD5:— | SHA256:— | |||
| 3448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3448.24830\Ratool_v1.4\Ratool.ini | text | |
MD5:— | SHA256:— | |||
| 3876 | Ratool.exe | C:\Windows\System32\GroupPolicy\Machine\Registry.pol | binary | |
MD5:— | SHA256:— | |||
| 3448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3448.24050\Ratool_v1.4\Read_me.txt | text | |
MD5:DD943471DB59DA2D0ED51C4C91B63F03 | SHA256:DF6C183F66D23E87B33E58ACA1313E6AAE8283D6C259EBA78313177CBCA10603 | |||
| 3448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3448.24050\Ratool_v1.4\Ratool_x64.exe | executable | |
MD5:696EE9B9E12B9657C75F5FA4B60C7D5E | SHA256:4A740E6001C7B0F5DEBEF0E28D4B6DB0BF07AD98F9037E04EF913C2CBCCC1E0D | |||
| 3448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3448.24830\Ratool_v1.4\Ratool_x64.exe | executable | |
MD5:696EE9B9E12B9657C75F5FA4B60C7D5E | SHA256:4A740E6001C7B0F5DEBEF0E28D4B6DB0BF07AD98F9037E04EF913C2CBCCC1E0D | |||
| 3448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3448.24830\Ratool_v1.4\Ratool.exe | executable | |
MD5:9C67C0C65B1E045662CBE9ADE83742E7 | SHA256:1E0E51061A67E15197B2BD1B47CA08C88809FC25F843D40503940713A142CC3F | |||
| 3876 | Ratool.exe | C:\Windows\System32\GroupPolicy\User\Registry.pol | binary | |
MD5:— | SHA256:— | |||
| 2972 | DrvInst.exe | C:\Windows\INF\setupapi.ev2 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report