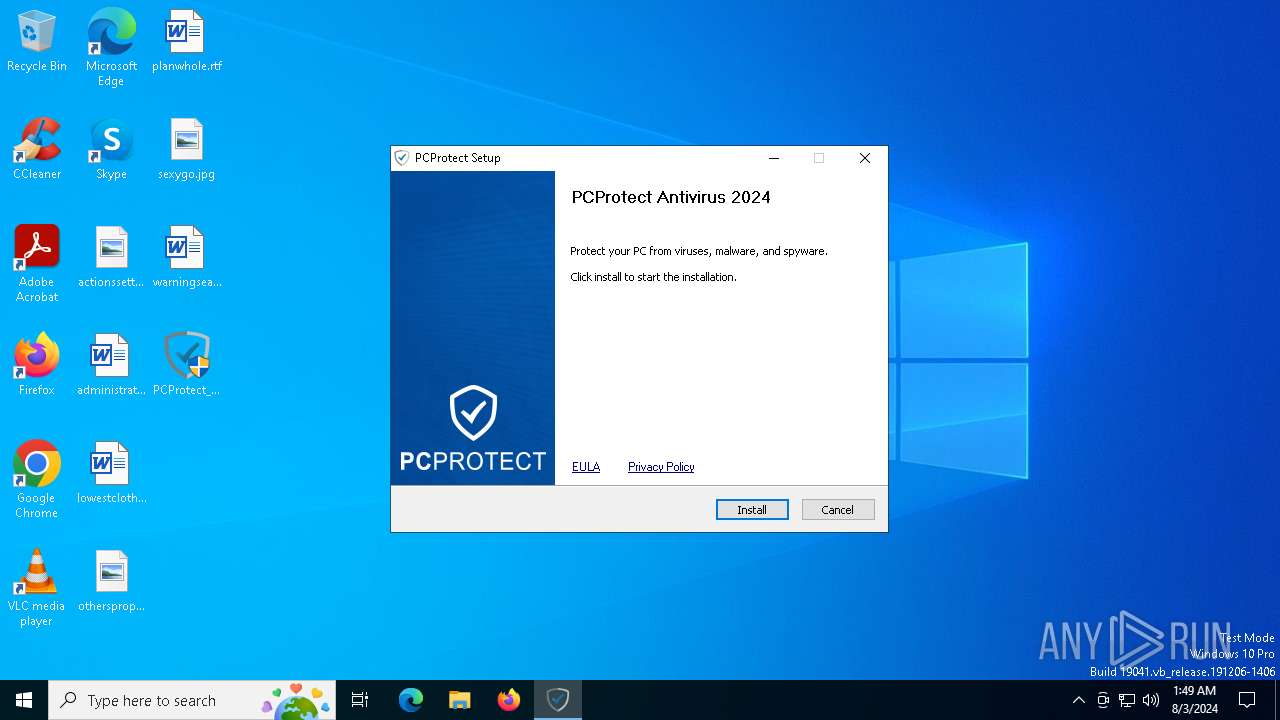
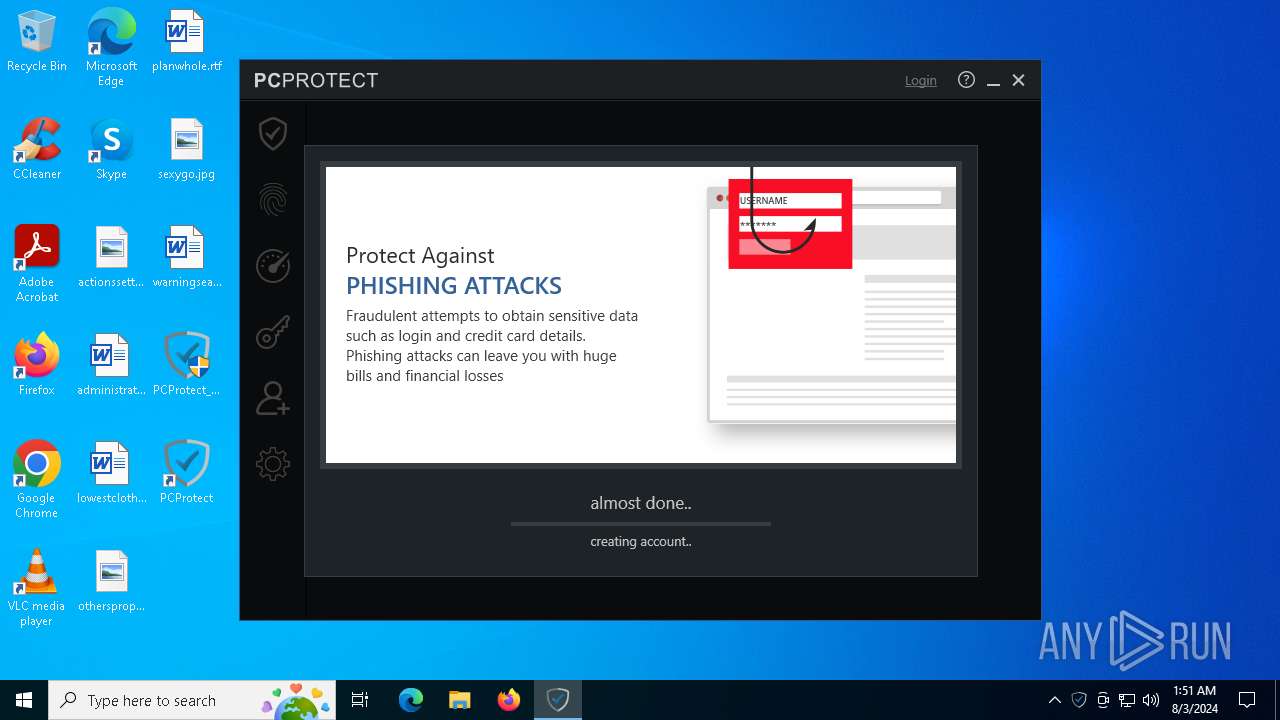
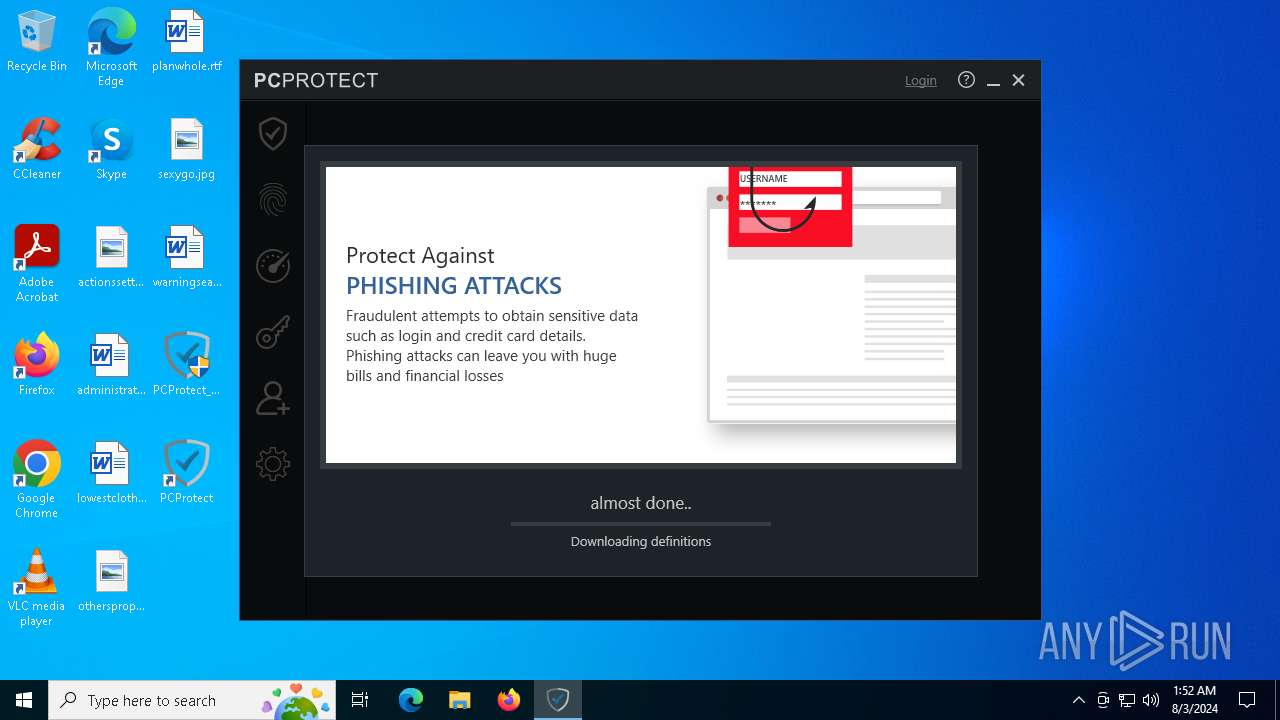
| File name: | PCProtect_Setup.exe |
| Full analysis: | https://app.any.run/tasks/7a5d88cd-ae85-425b-bbc4-f23236031095 |
| Verdict: | Malicious activity |
| Threats: | Stealers are a group of malicious software that are intended for gaining unauthorized access to users’ information and transferring it to the attacker. The stealer malware category includes various types of programs that focus on their particular kind of data, including files, passwords, and cryptocurrency. Stealers are capable of spying on their targets by recording their keystrokes and taking screenshots. This type of malware is primarily distributed as part of phishing campaigns. |
| Analysis date: | August 03, 2024, 01:49:27 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 87CB9284AAC0AA4112C153A5BCD89E99 |
| SHA1: | 3B724CE214652B93D1A5FB5FD5DE29C24F69C3DF |
| SHA256: | 99C2474F5BEA6E3955D1002AA98678C32E9C0E9F2FB6D0C35D3A428EC279D103 |
| SSDEEP: | 786432:sSHEaiqBJ7V7lO70LeOBmFFIi0gJZdnhit:sSHGKzJs0LeOBmFFIi0gJZlwt |
MALICIOUS
Deletes shadow copies
- PCProtect_Setup.exe (PID: 6920)
Drops the executable file immediately after the start
- SecurityService.exe (PID: 6736)
- PCProtect_Setup.exe (PID: 6920)
Steals credentials from Web Browsers
- PCProtect.exe (PID: 4060)
- SecurityService.exe (PID: 2136)
Actions looks like stealing of personal data
- PCProtect.exe (PID: 4060)
- SecurityService.exe (PID: 2136)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- PCProtect_Setup.exe (PID: 6920)
Uses WMIC.EXE
- PCProtect_Setup.exe (PID: 6920)
Uses TASKKILL.EXE to kill process
- PCProtect_Setup.exe (PID: 6920)
Process drops legitimate windows executable
- PCProtect_Setup.exe (PID: 6920)
Searches for installed software
- dllhost.exe (PID: 6164)
Executes as Windows Service
- VSSVC.exe (PID: 3812)
- SecurityService.exe (PID: 5484)
The process drops C-runtime libraries
- PCProtect_Setup.exe (PID: 6920)
Drops a system driver (possible attempt to evade defenses)
- PCProtect_Setup.exe (PID: 6920)
- SecurityService.exe (PID: 6736)
Creates a software uninstall entry
- PCProtect_Setup.exe (PID: 6920)
Creates files in the driver directory
- SecurityService.exe (PID: 6736)
Reads the date of Windows installation
- PCProtect_Setup.exe (PID: 6920)
Executable content was dropped or overwritten
- SecurityService.exe (PID: 6736)
- PCProtect_Setup.exe (PID: 6920)
Starts SC.EXE for service management
- SecurityService.exe (PID: 6736)
- SecurityService.exe (PID: 2136)
Reads security settings of Internet Explorer
- PCProtect_Setup.exe (PID: 6920)
- PCProtect.exe (PID: 4060)
Get information on the list of running processes
- PCProtect_Setup.exe (PID: 6920)
The process creates files with name similar to system file names
- PCProtect_Setup.exe (PID: 6920)
Application launched itself
- SecurityService.exe (PID: 5484)
INFO
Create files in a temporary directory
- PCProtect_Setup.exe (PID: 6920)
- PCProtect.exe (PID: 4060)
Checks supported languages
- PCProtect_Setup.exe (PID: 6920)
- SecurityService.exe (PID: 6736)
- subinacl.exe (PID: 6280)
- PCProtect.exe (PID: 4060)
- SecurityService.exe (PID: 5484)
- SecurityService.exe (PID: 2136)
Reads the computer name
- PCProtect_Setup.exe (PID: 6920)
- SecurityService.exe (PID: 6736)
- subinacl.exe (PID: 6280)
- PCProtect.exe (PID: 4060)
- SecurityService.exe (PID: 5484)
- SecurityService.exe (PID: 2136)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 7000)
Creates files in the program directory
- SecurityService.exe (PID: 6736)
- PCProtect.exe (PID: 4060)
- SecurityService.exe (PID: 5484)
- PCProtect_Setup.exe (PID: 6920)
- SecurityService.exe (PID: 2136)
Process checks computer location settings
- PCProtect_Setup.exe (PID: 6920)
Creates files or folders in the user directory
- PCProtect.exe (PID: 4060)
Disables trace logs
- PCProtect.exe (PID: 4060)
Reads Environment values
- PCProtect.exe (PID: 4060)
- SecurityService.exe (PID: 5484)
- SecurityService.exe (PID: 2136)
Reads the software policy settings
- PCProtect.exe (PID: 4060)
- SecurityService.exe (PID: 2136)
- SecurityService.exe (PID: 5484)
Checks proxy server information
- PCProtect.exe (PID: 4060)
Reads the machine GUID from the registry
- SecurityService.exe (PID: 2136)
- SecurityService.exe (PID: 5484)
- PCProtect.exe (PID: 4060)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:08:01 02:43:48+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 25600 |
| InitializedDataSize: | 118784 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x3461 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.24.38.0 |
| ProductVersionNumber: | 5.24.38.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| FileDescription: | PCProtect Ultimate Antivirus Installer |
| FileVersion: | 5.24.38.0 |
| LegalCopyright: | (C) Protected Antivirus Limited |
| OriginalFileName: | PCProtect.exe |
| ProductName: | PCProtect |
| ProductVersion: | 5.24.38.0 |
Total processes
145
Monitored processes
29
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1360 | "sc" create ProtectedELAM binpath= "C:\WINDOWS\system32\drivers\protected_elam.sys" type= kernel start= boot error= critical group= Early-Launch | C:\Windows\System32\sc.exe | — | SecurityService.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Exit code: 1073 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2136 | "C:\Program Files (x86)\PCProtect\SecurityService.exe" --run-service --run-service-id=5484 | C:\Program Files (x86)\PCProtect\SecurityService.exe | SecurityService.exe | ||||||||||||
User: SYSTEM Company: PCProtect Integrity Level: SYSTEM Description: PCProtect Ultimate Antivirus Service Version: 5.24.38.0 Modules
| |||||||||||||||
| 2728 | "sc" create SecurityService start= auto binpath= "\"C:\Program Files (x86)\PCProtect\SecurityService.exe\"" displayname= "PC Security Management Service" obj= LocalSystem password= "" | C:\Windows\SysWOW64\sc.exe | — | SecurityService.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3812 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3992 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SecurityService.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4016 | C:\WINDOWS\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4060 | "C:\Program Files (x86)\PCProtect\PCProtect.exe" --installed --installer="C:\Users\admin\Desktop\PCProtect_Setup.exe" | C:\Program Files (x86)\PCProtect\PCProtect.exe | PCProtect_Setup.exe | ||||||||||||
User: admin Company: PCProtect Integrity Level: HIGH Description: PCProtect Ultimate Antivirus User Interface Version: 5.24.38.0 Modules
| |||||||||||||||
| 5244 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5484 | "C:\Program Files (x86)\PCProtect\SecurityService.exe" | C:\Program Files (x86)\PCProtect\SecurityService.exe | services.exe | ||||||||||||
User: SYSTEM Company: PCProtect Integrity Level: SYSTEM Description: PCProtect Ultimate Antivirus Service Version: 5.24.38.0 Modules
| |||||||||||||||
| 6164 | C:\WINDOWS\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
27 627
Read events
27 356
Write events
251
Delete events
20
Modification events
| (PID) Process: | (6920) PCProtect_Setup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 40000000000000003D4CB97A47E5DA01081B0000541B0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6164) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 48000000000000003CB0BB7A47E5DA011418000068040000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6164) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000DA64FE7A47E5DA011418000068040000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6164) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000DA64FE7A47E5DA011418000068040000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6164) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 480000000000000014CA007B47E5DA011418000068040000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6164) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 48000000000000007692057B47E5DA011418000068040000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6164) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (6164) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000ED6A7A7B47E5DA011418000068040000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6164) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 480000000000000060CE7C7B47E5DA011418000068010000E80300000100000000000000000000002ADEDEC59A21784797A79C68490ECFF500000000000000000000000000000000 | |||
| (PID) Process: | (3812) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 480000000000000044AC887B47E5DA01E40E00009C180000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
499
Suspicious files
137
Text files
54
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6164 | dllhost.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 6920 | PCProtect_Setup.exe | C:\Users\admin\AppData\Local\Temp\nsj923B.tmp\nsRandom.dll | executable | |
MD5:AB467B8DFAA660A0F0E5B26E28AF5735 | SHA256:DB267D9920395B4BADC48DE04DF99DFD21D579480D103CAE0F48E6578197FF73 | |||
| 6920 | PCProtect_Setup.exe | C:\Users\admin\AppData\Local\Temp\nsj923B.tmp\modern-wizard.bmp | image | |
MD5:3EB2FF327FB3FC2495C7B4333D4BEDE2 | SHA256:B2C7196BC66D0BA39812AF671542664C2C8216B3334D1CBBD57241BF11653B0A | |||
| 6920 | PCProtect_Setup.exe | C:\Users\admin\AppData\Local\Temp\nsj923B.tmp\SysRestore.dll | executable | |
MD5:DA046184A8D7269A0E138B0B0B9B2EB5 | SHA256:C5E335BD19FA798F120287FE3ED920296F899223942FD6B987585A765F0ADEC2 | |||
| 6920 | PCProtect_Setup.exe | C:\Program Files (x86)\PCProtect\AviraLib.dll | executable | |
MD5:FB8D7D2F2D25346E8CE9A70B5DF5DB55 | SHA256:A02884ADF7C6CEA2DE69D260034930EBF9A0BBB51E7CEEB12B7FDD6D38941F80 | |||
| 6164 | dllhost.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:EBB7810A64FDECD9B69E85E5AB24090C | SHA256:31A8BEAD162409C7D5DCA17BBB0AAF6FB3CF99EFBB0B1C1CD56A4B349F18E268 | |||
| 6920 | PCProtect_Setup.exe | C:\Program Files (x86)\PCProtect\Branding.Desktop.dll | executable | |
MD5:83DF60E9FA070F73FC478F3E2FA33118 | SHA256:ED3D49A91F5B88D425D5CEDA3E120638C5A16116CF719E899A3395092DBD2FD6 | |||
| 6920 | PCProtect_Setup.exe | C:\Program Files (x86)\PCProtect\installer.log | text | |
MD5:46B80930C603A18ED7E611839E3CBD34 | SHA256:39B0CD2C015C3CE3D166C4303B20824C5695C8CE08DA811B9A51866B48D8C901 | |||
| 6920 | PCProtect_Setup.exe | C:\Program Files (x86)\PCProtect\D3DCompiler_47_cor3.dll | executable | |
MD5:5E717C95808BCB5F654BB312D289B837 | SHA256:E745872DB4DD114A65EE1504F401EA26D879EDB6614E369A07A80CE7AD1950CA | |||
| 6920 | PCProtect_Setup.exe | C:\Program Files (x86)\PCProtect\Accessibility.dll | executable | |
MD5:1B4CC6782E295675217CD17DF70057F3 | SHA256:F08BDBF797DFDBBDE37000FB29141CAEC4BEB4DC0F552AB2CFE0887E1E6C5F60 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
38
TCP/UDP connections
48
DNS requests
10
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | HEAD | 200 | 185.172.148.128:443 | https://definition.protected.net/vdf.zip | unknown | — | — | unknown |
— | — | GET | — | 185.172.148.128:443 | https://definition.protected.net/vdf.zip | unknown | — | — | unknown |
— | — | GET | — | 34.128.164.30:443 | https://api.pcprotect.com/v1/experian | unknown | — | — | unknown |
— | — | GET | — | 34.128.164.30:443 | https://api.pcprotect.com/v1/addon | unknown | — | — | unknown |
— | — | GET | — | 34.128.164.30:443 | https://api.pcprotect.com/v1/user/sso | unknown | — | — | unknown |
— | — | GET | — | 34.128.164.30:443 | https://api.pcprotect.com/v1/user/mobile-download/pcprotect?fresh=0 | unknown | — | — | unknown |
— | — | GET | — | 34.128.164.30:443 | https://api.pcprotect.com/v1/variable | unknown | — | — | unknown |
— | — | POST | 200 | 20.57.103.21:443 | https://in.appcenter.ms/logs?api-version=1.0.0 | unknown | binary | 129 b | unknown |
— | — | POST | 200 | 20.57.103.21:443 | https://in.appcenter.ms/logs?api-version=1.0.0 | unknown | binary | 138 b | unknown |
— | — | POST | 200 | 34.128.164.30:443 | https://api.pcprotect.com/v1/user | unknown | binary | 1.94 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
4060 | PCProtect.exe | 34.128.164.30:443 | api.pcprotect.com | GOOGLE | US | unknown |
4060 | PCProtect.exe | 4.152.45.219:443 | in.appcenter.ms | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2136 | SecurityService.exe | 185.172.148.128:443 | definition.protected.net | proinity GmbH | CH | unknown |
5484 | SecurityService.exe | 20.57.103.21:443 | in.appcenter.ms | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2136 | SecurityService.exe | 20.57.103.21:443 | in.appcenter.ms | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
5336 | SearchApp.exe | 2.23.209.187:443 | www.bing.com | Akamai International B.V. | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
api.pcprotect.com |
| unknown |
in.appcenter.ms |
| unknown |
definition.protected.net |
| unknown |
www.bing.com |
| whitelisted |
api.phantom.avira-vpn.com |
| unknown |
Threats
Process | Message |
|---|---|
SecurityService.exe | SQLite error (1): duplicate column name: key in "ALTER TABLE sf_notify ADD COLUMN key TEXT PRIMARY KEY"
|
SecurityService.exe | SQLite error (1): duplicate column name: value in "ALTER TABLE sf_notify ADD COLUMN value TEXT"
|
SecurityService.exe | SQLite error (1): duplicate column name: key in "ALTER TABLE wwwcache ADD COLUMN key TEXT PRIMARY KEY"
|
SecurityService.exe | SQLite error (1): duplicate column name: value in "ALTER TABLE wwwcache ADD COLUMN value TEXT"
|