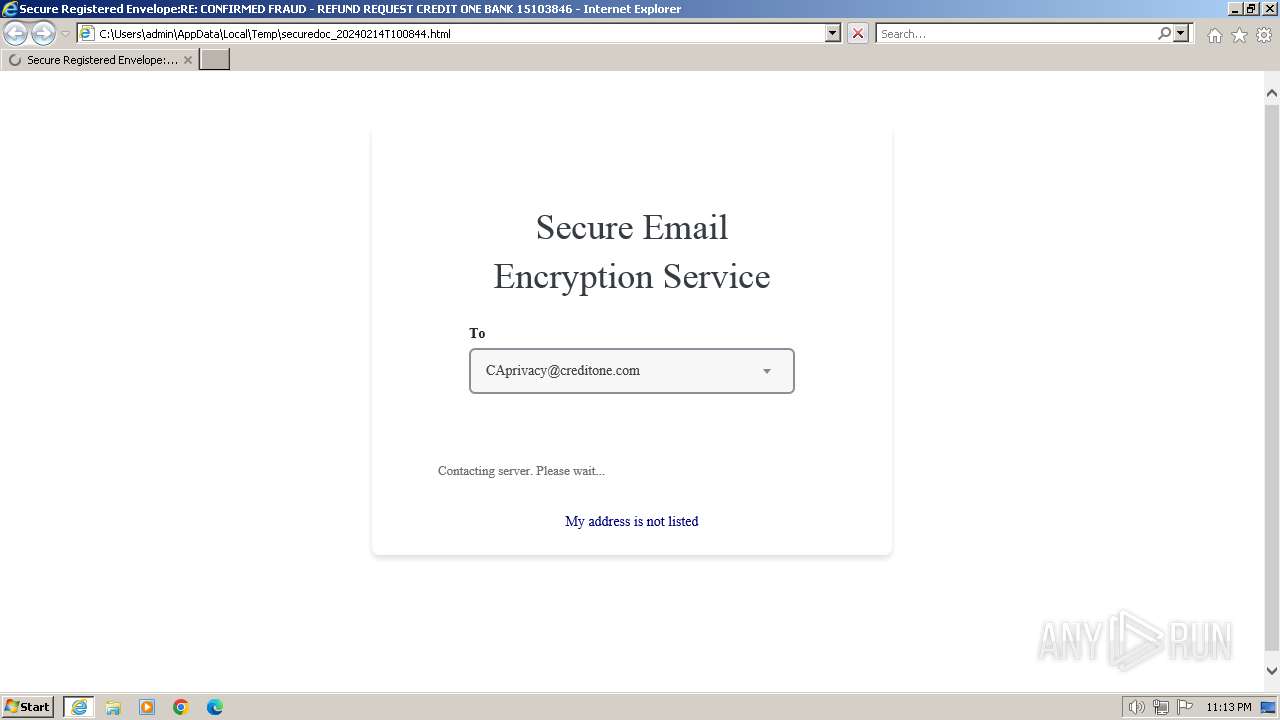
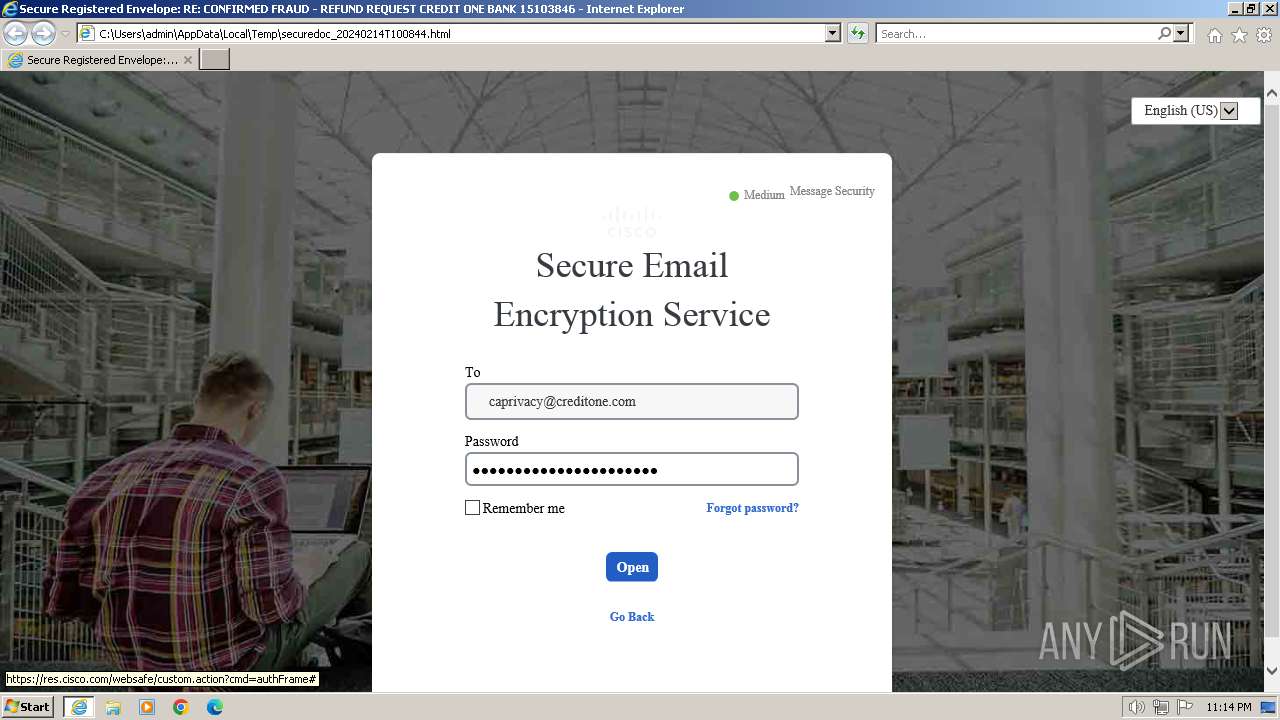
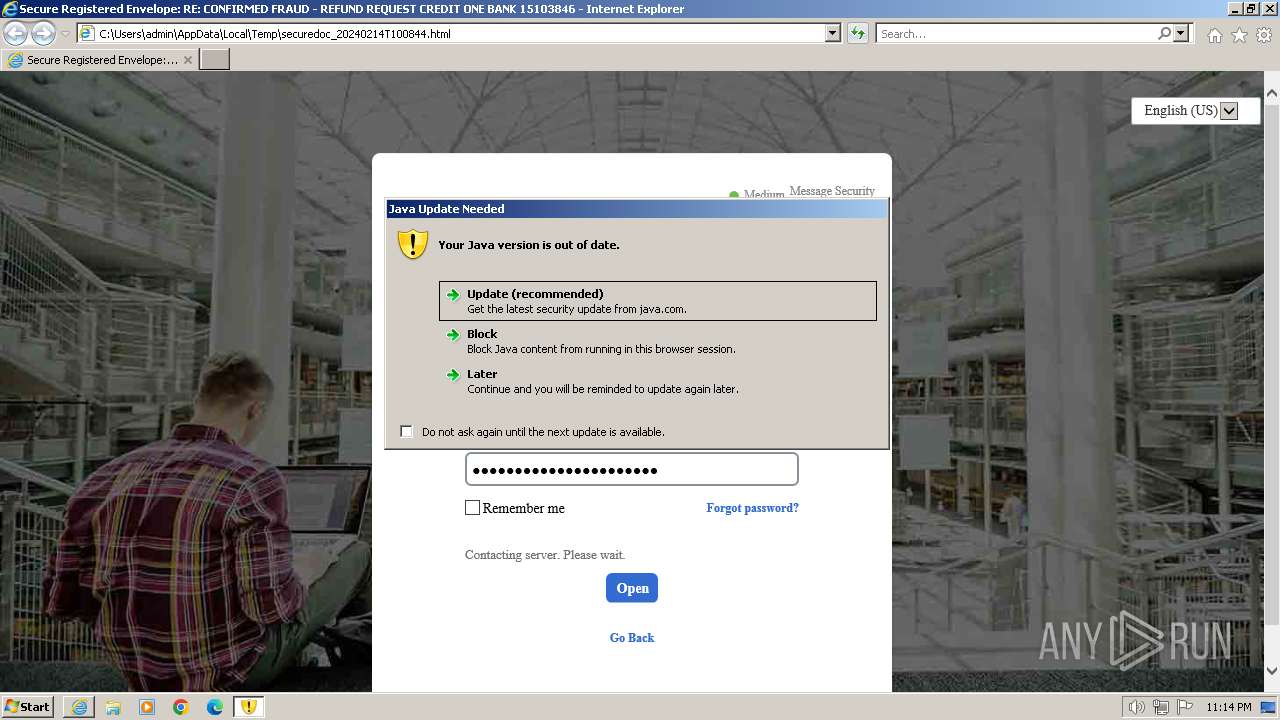
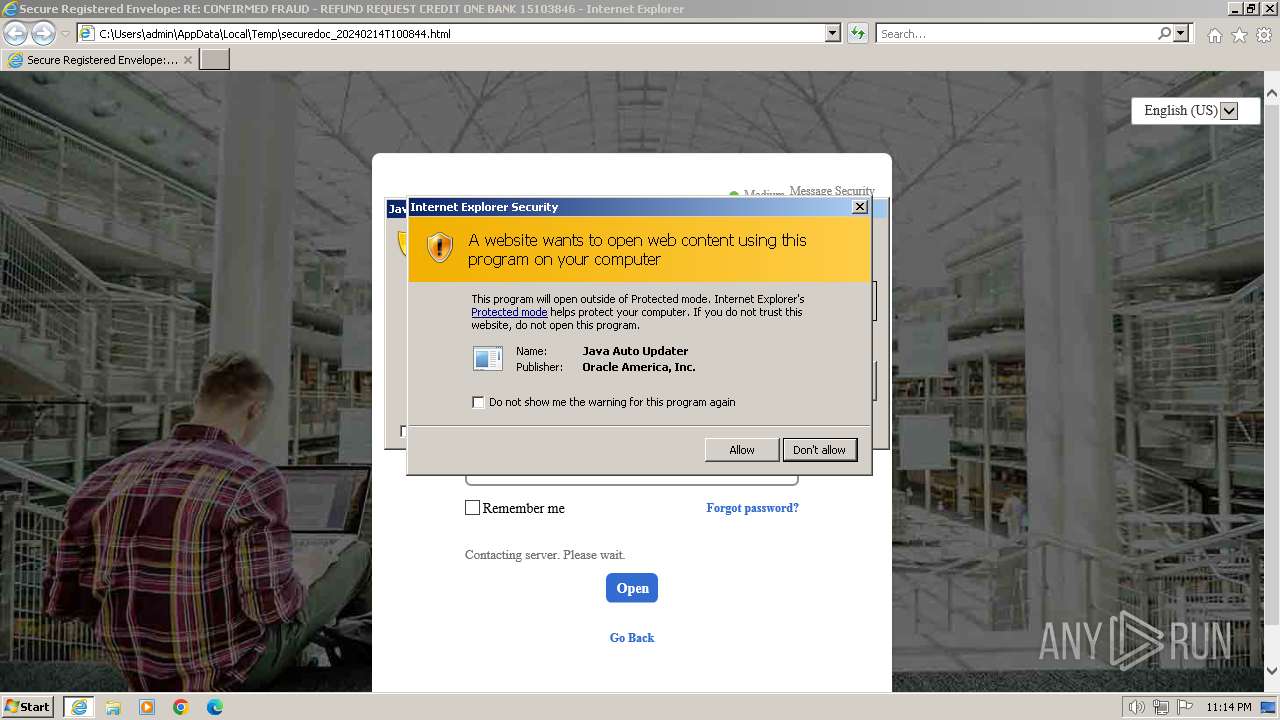
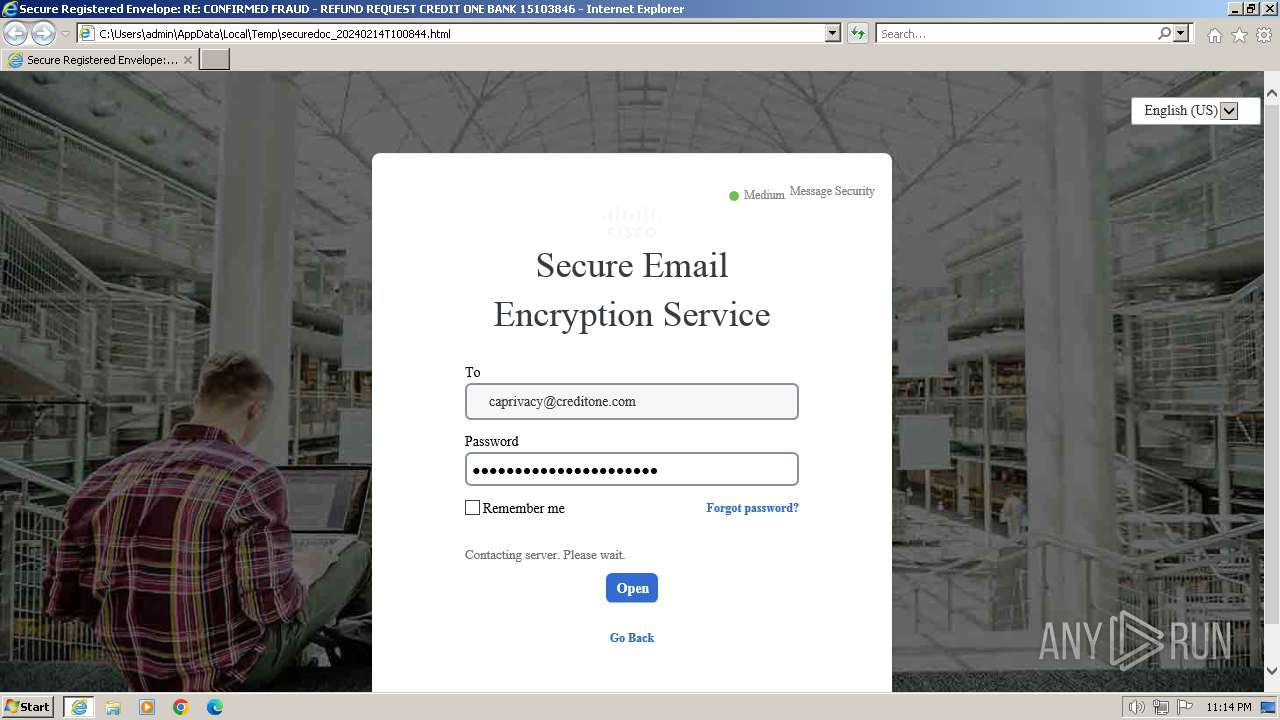
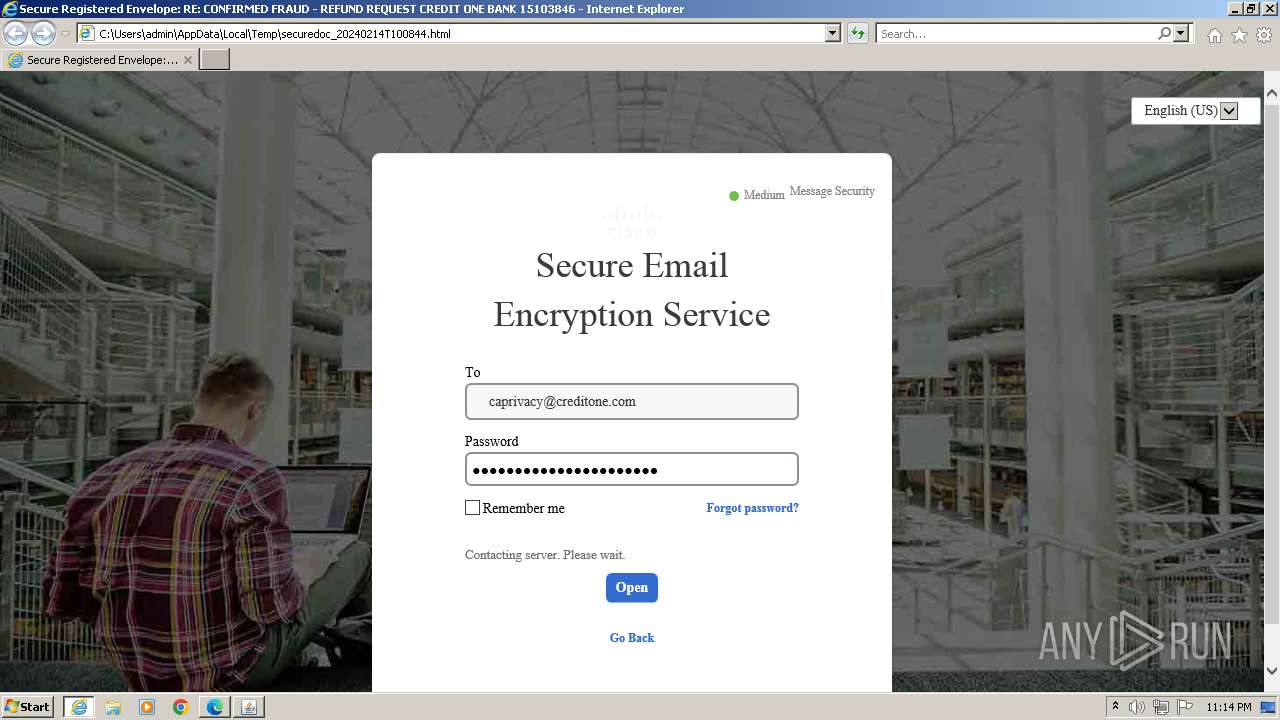
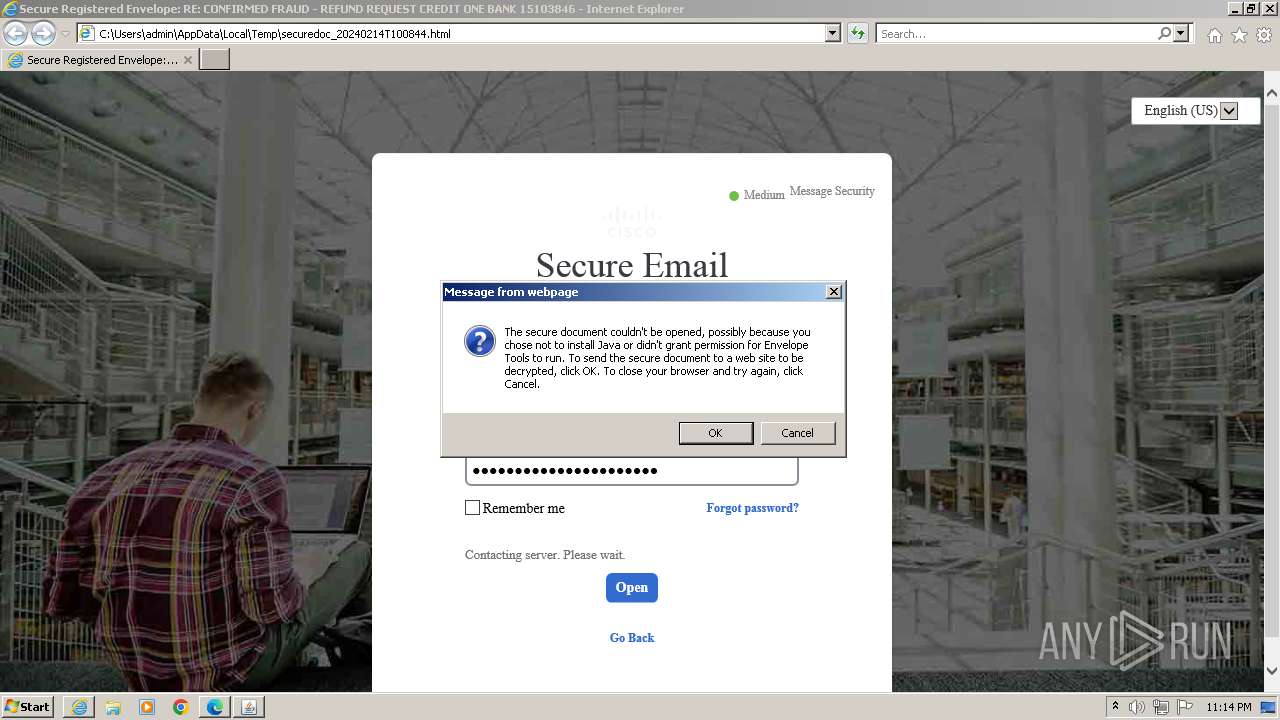
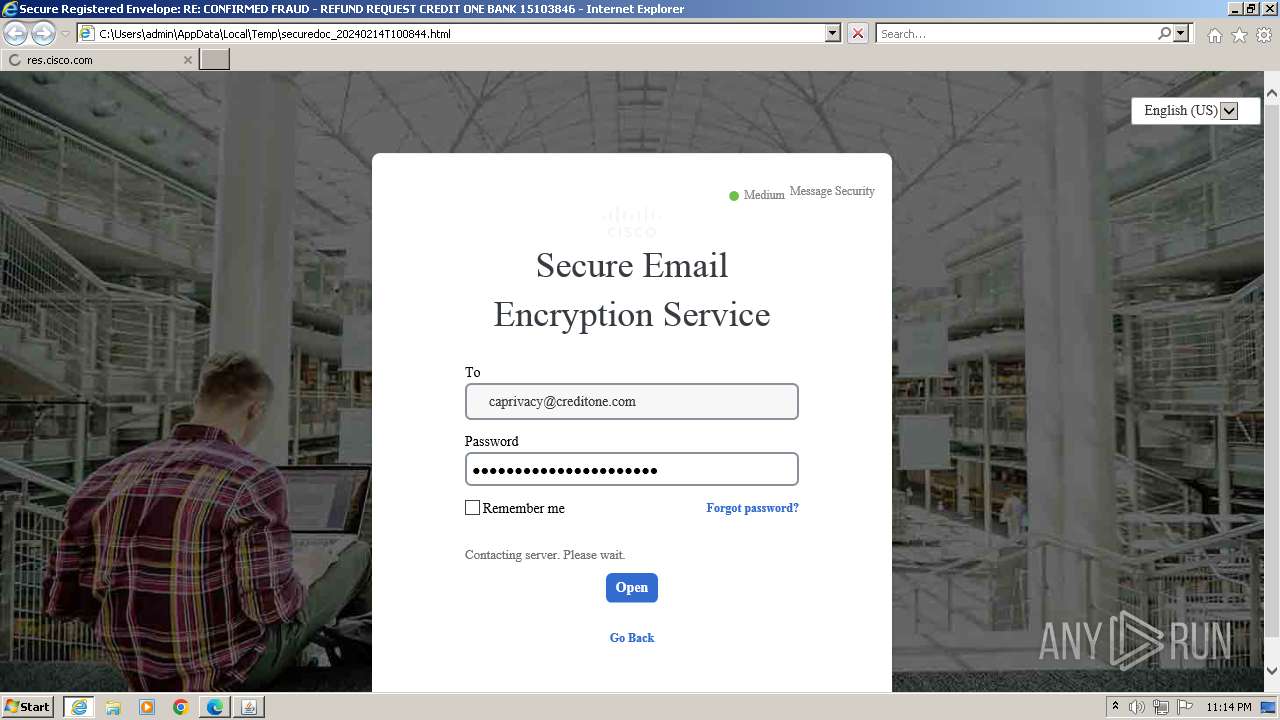
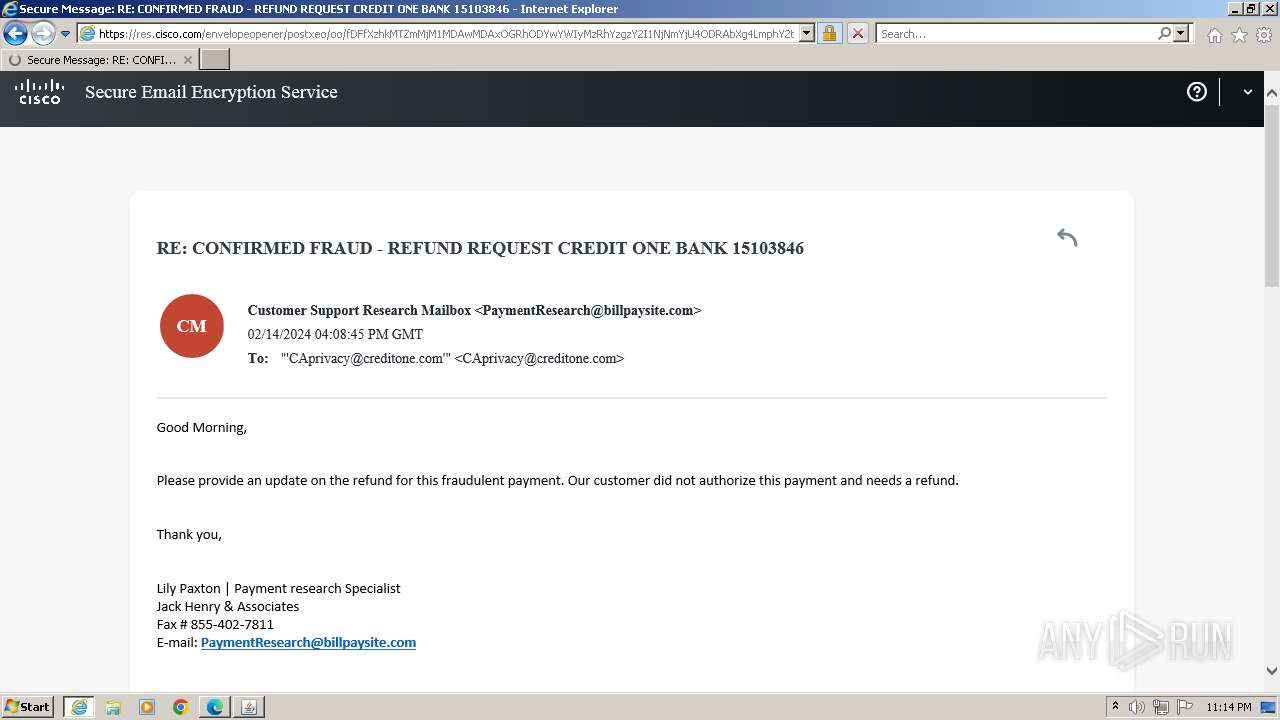
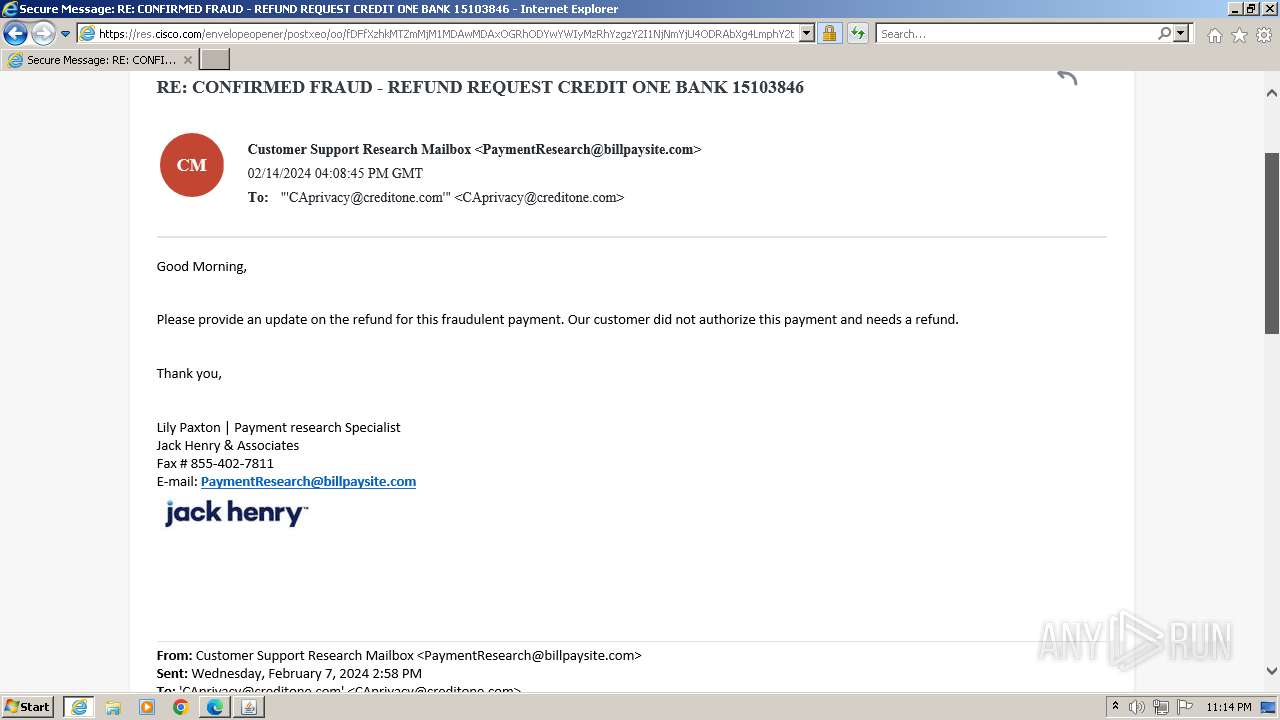
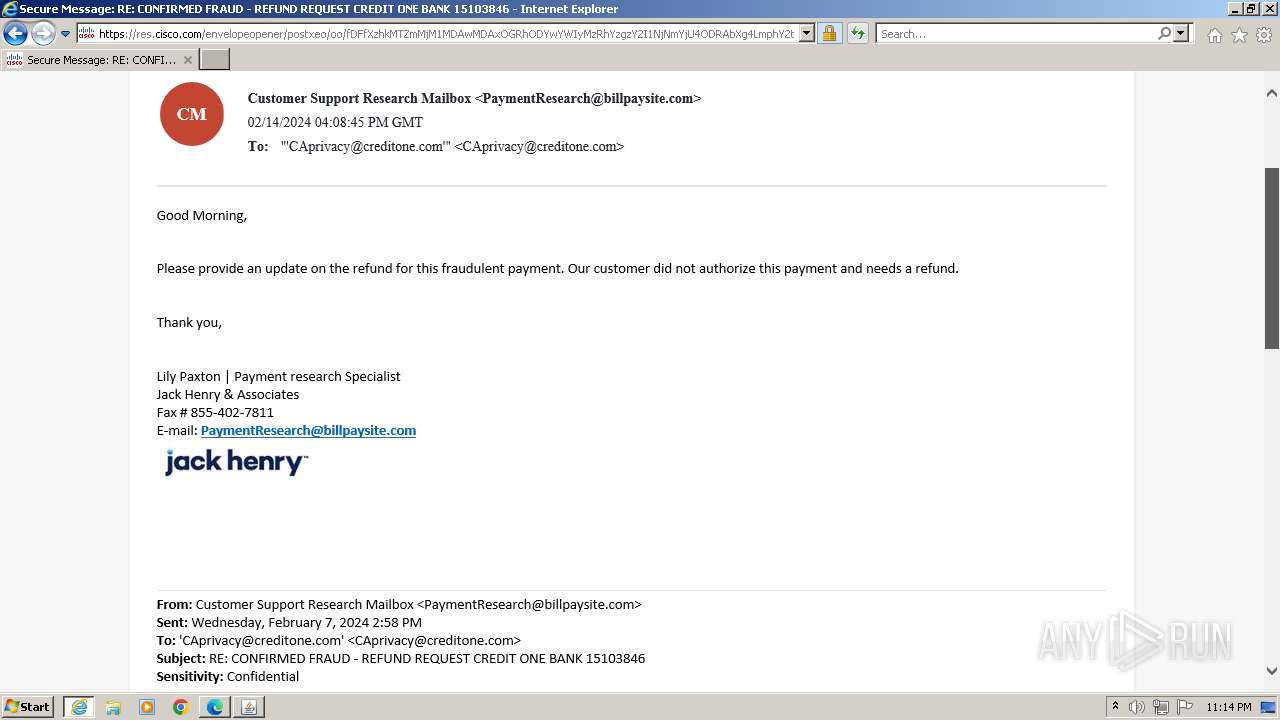
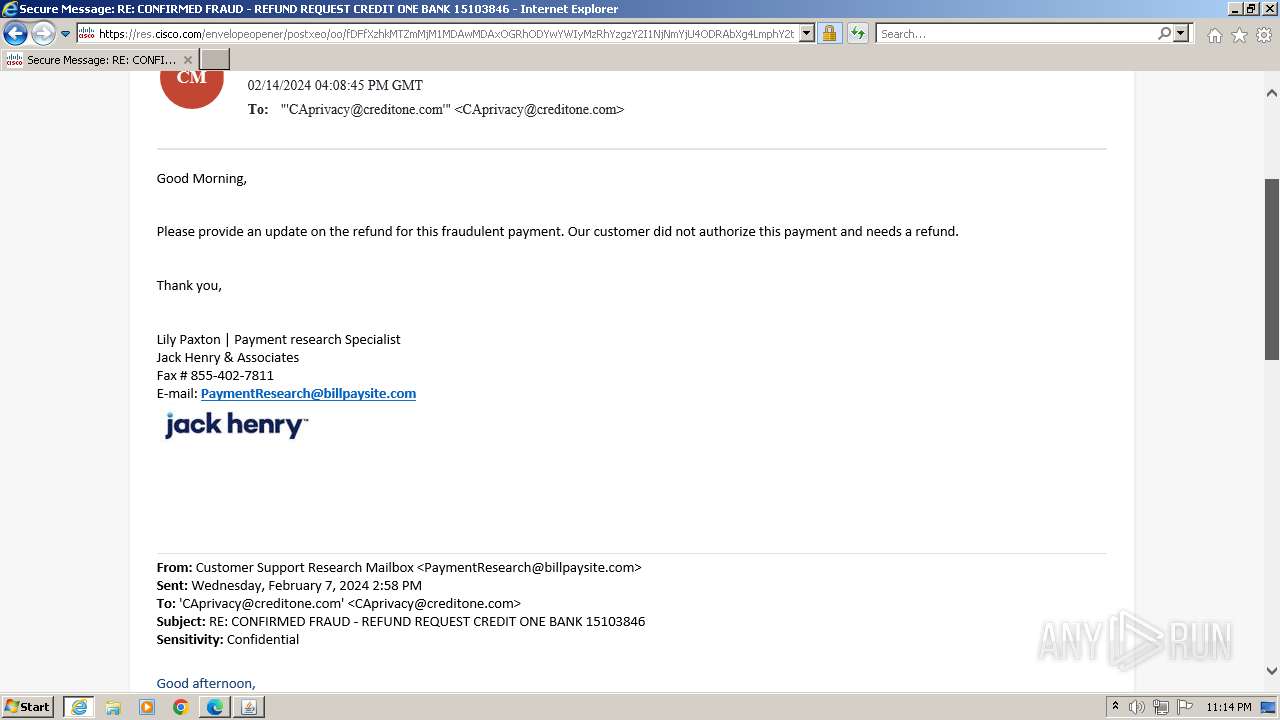
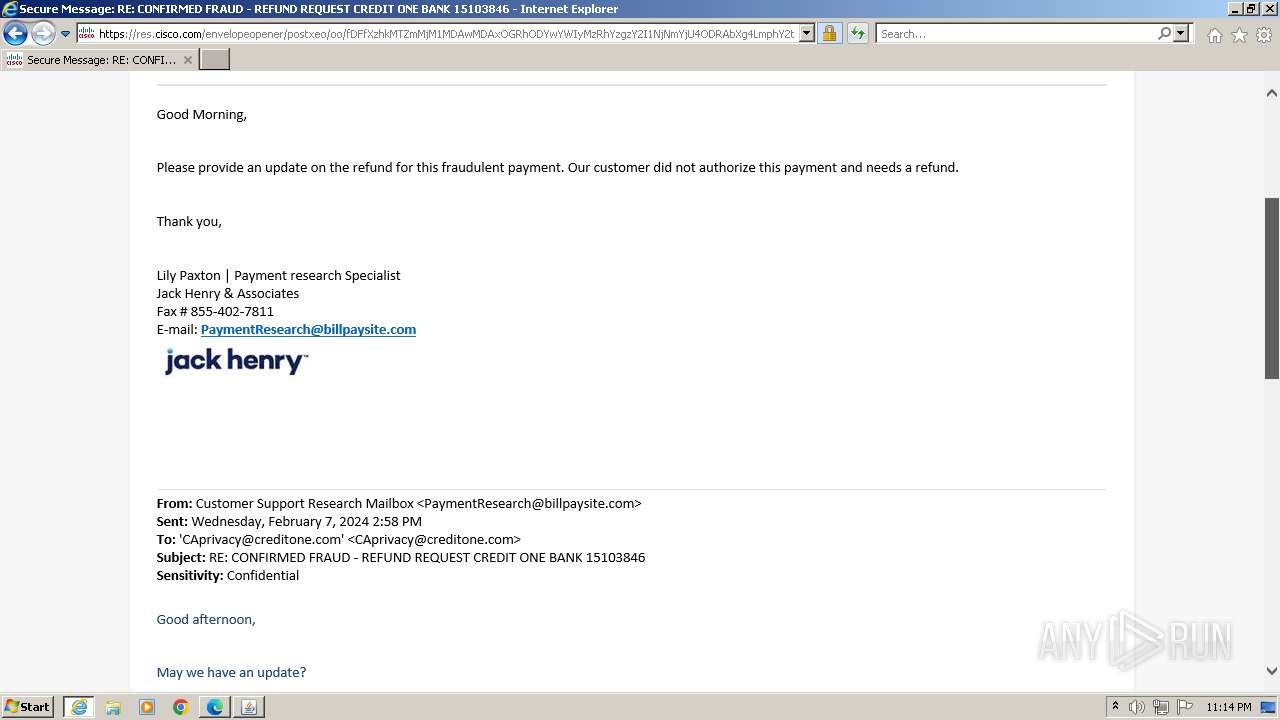
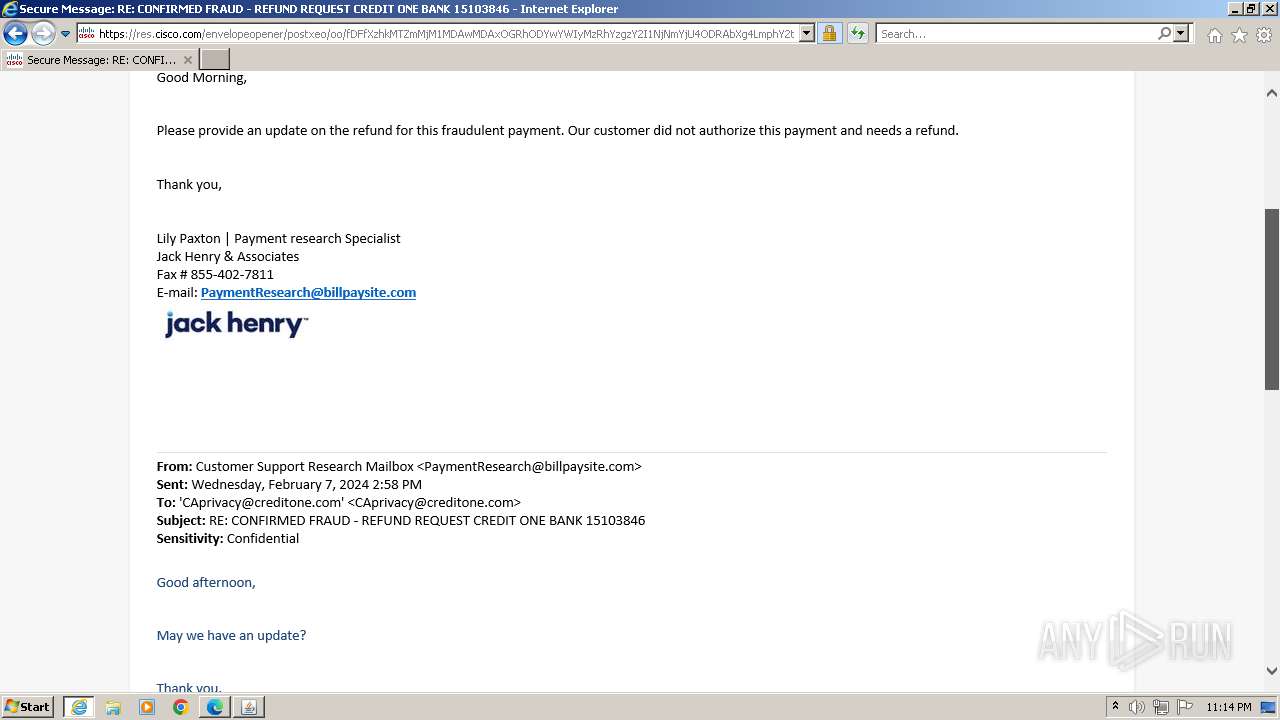
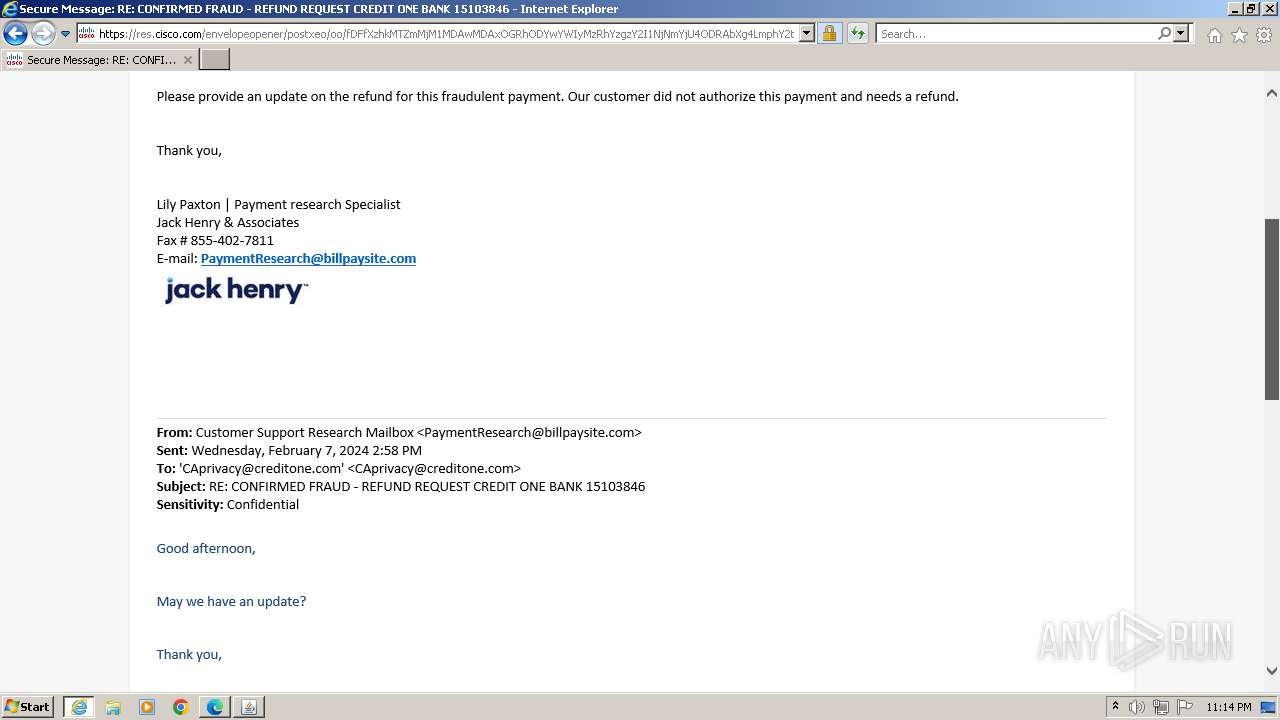
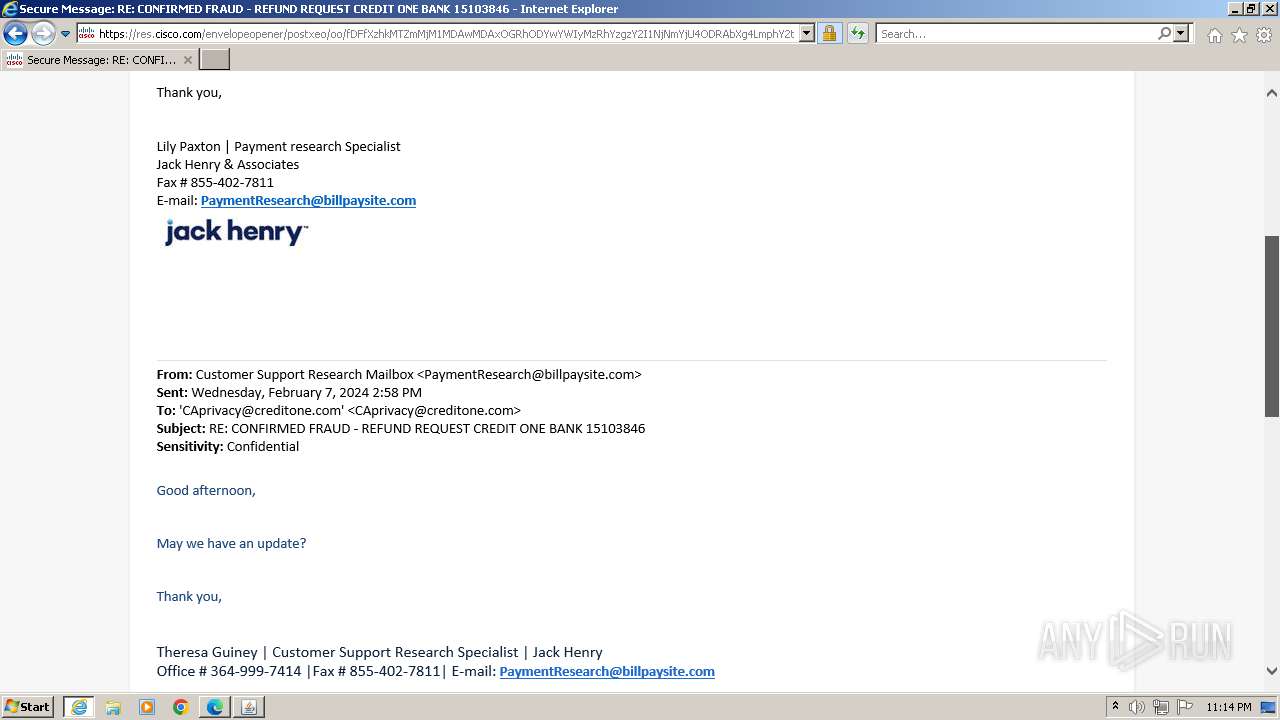
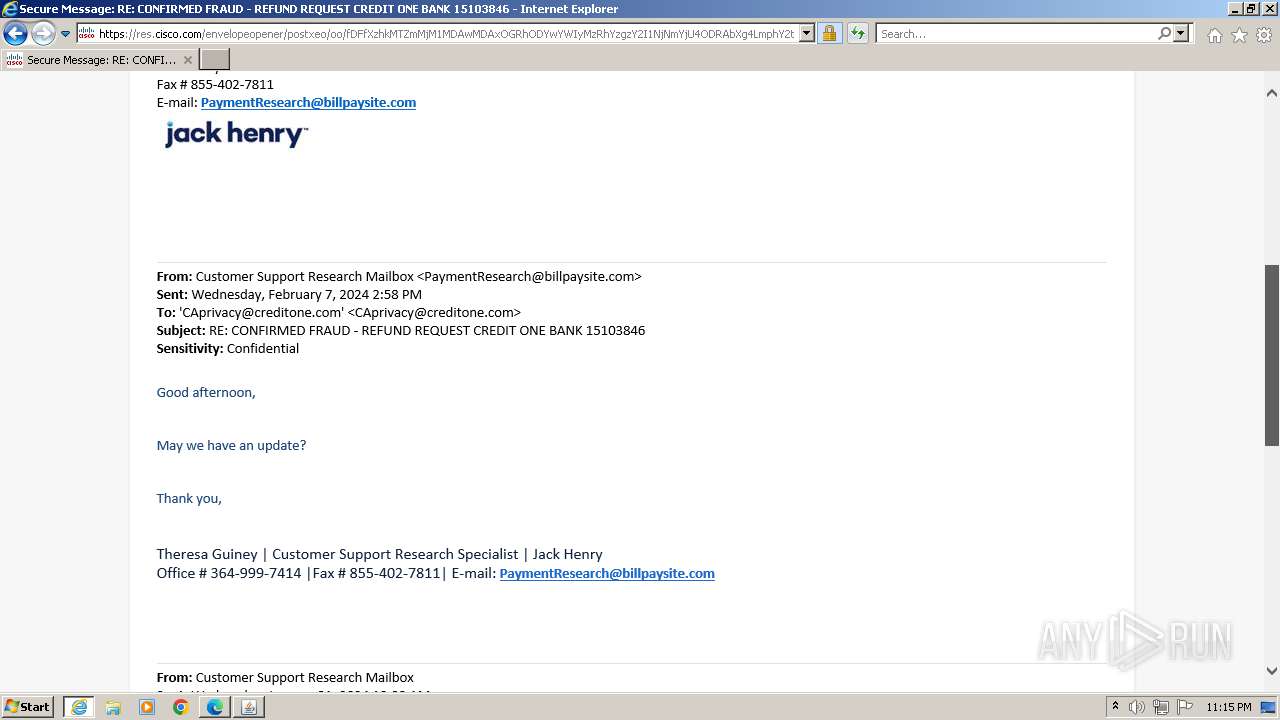
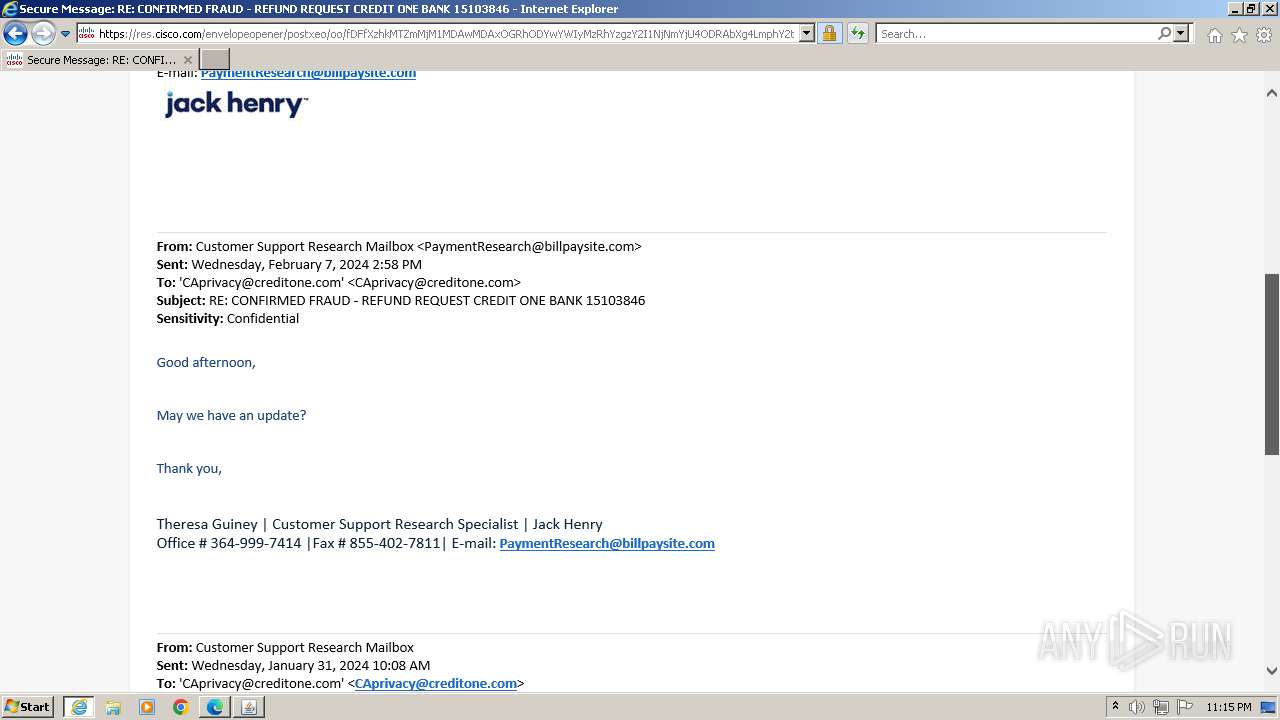
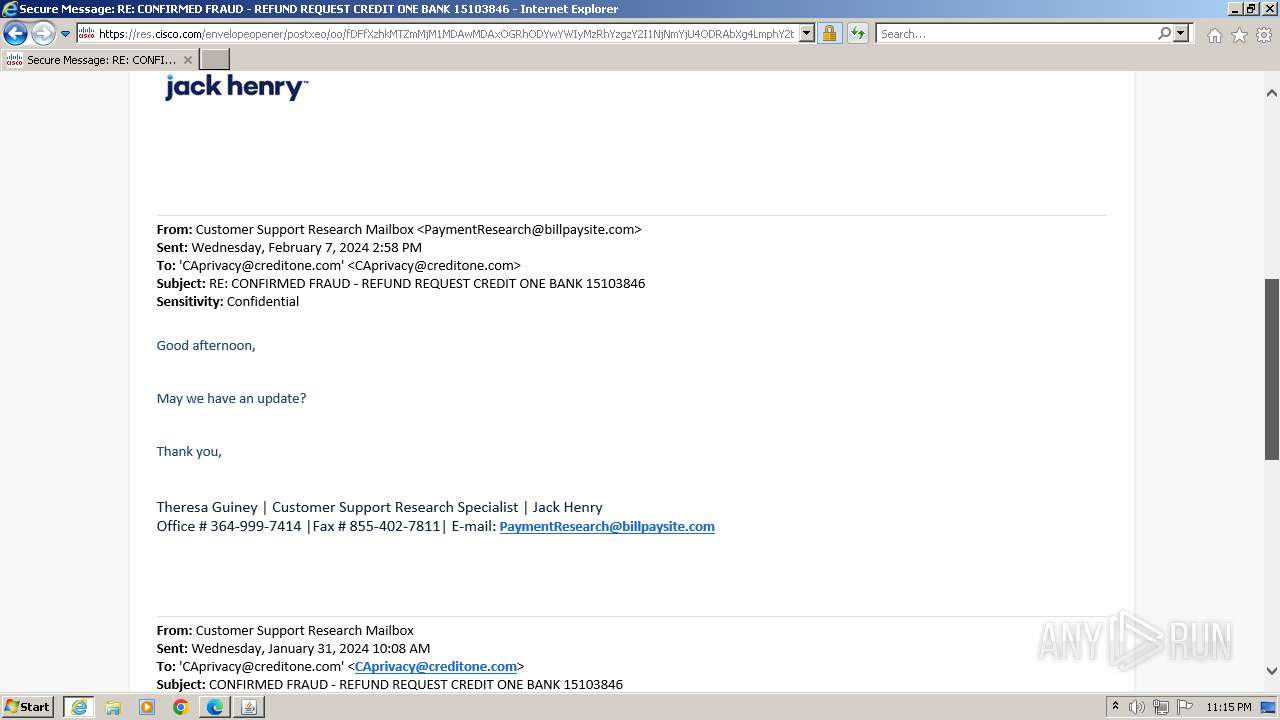
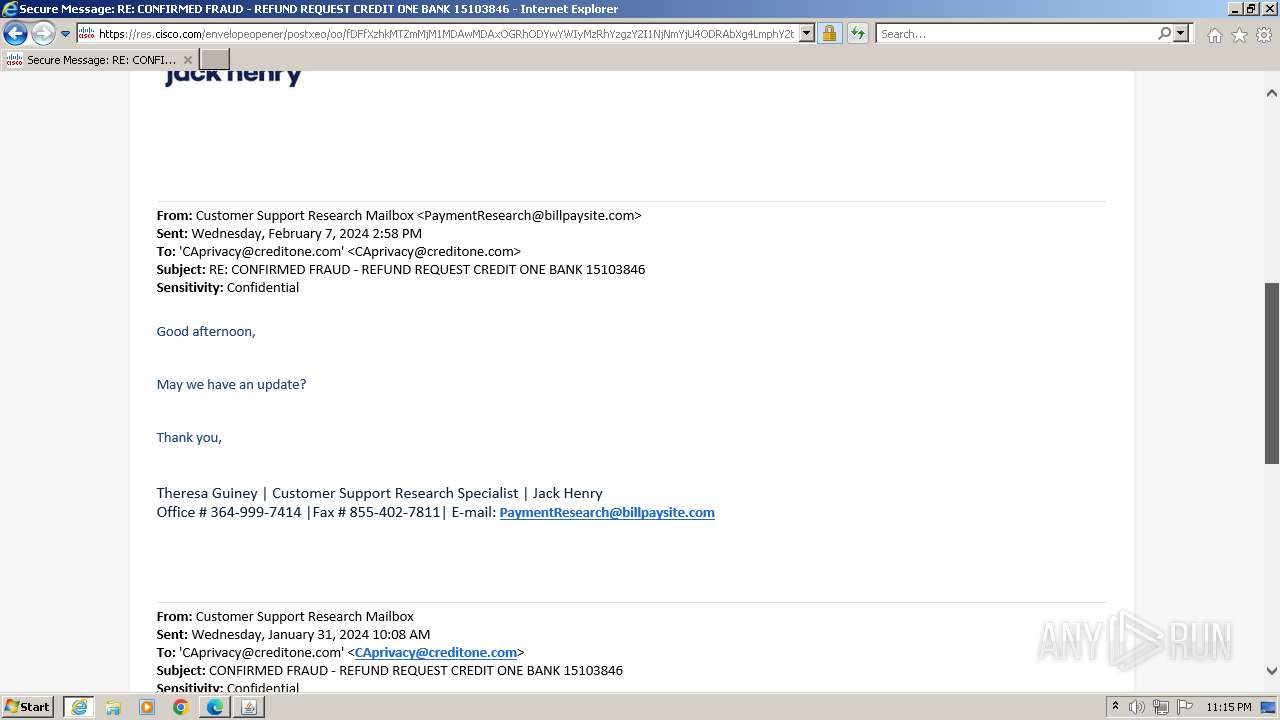
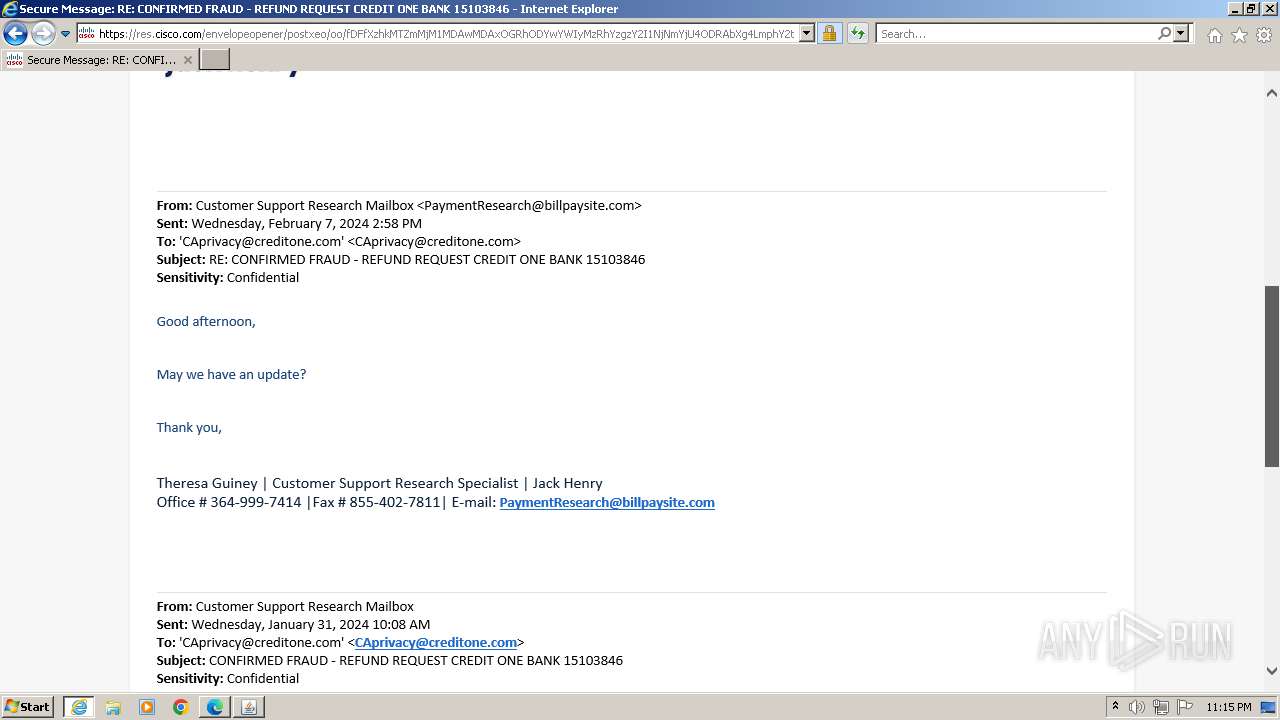
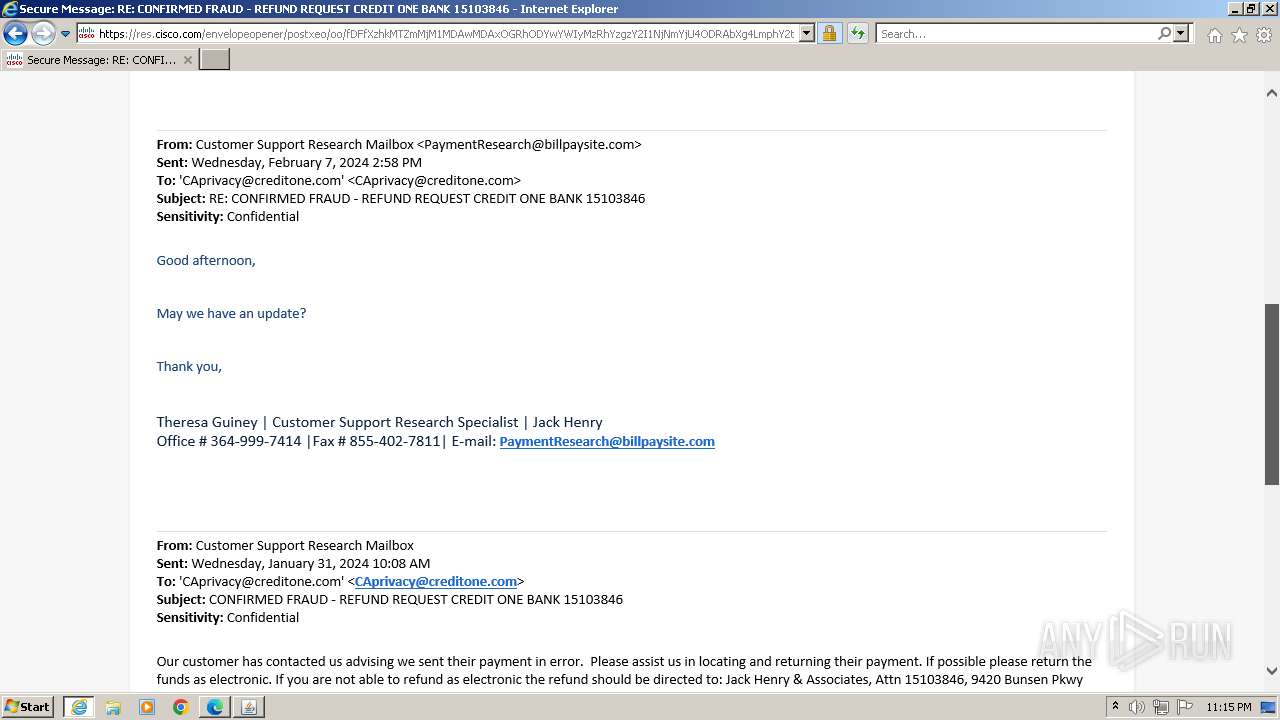
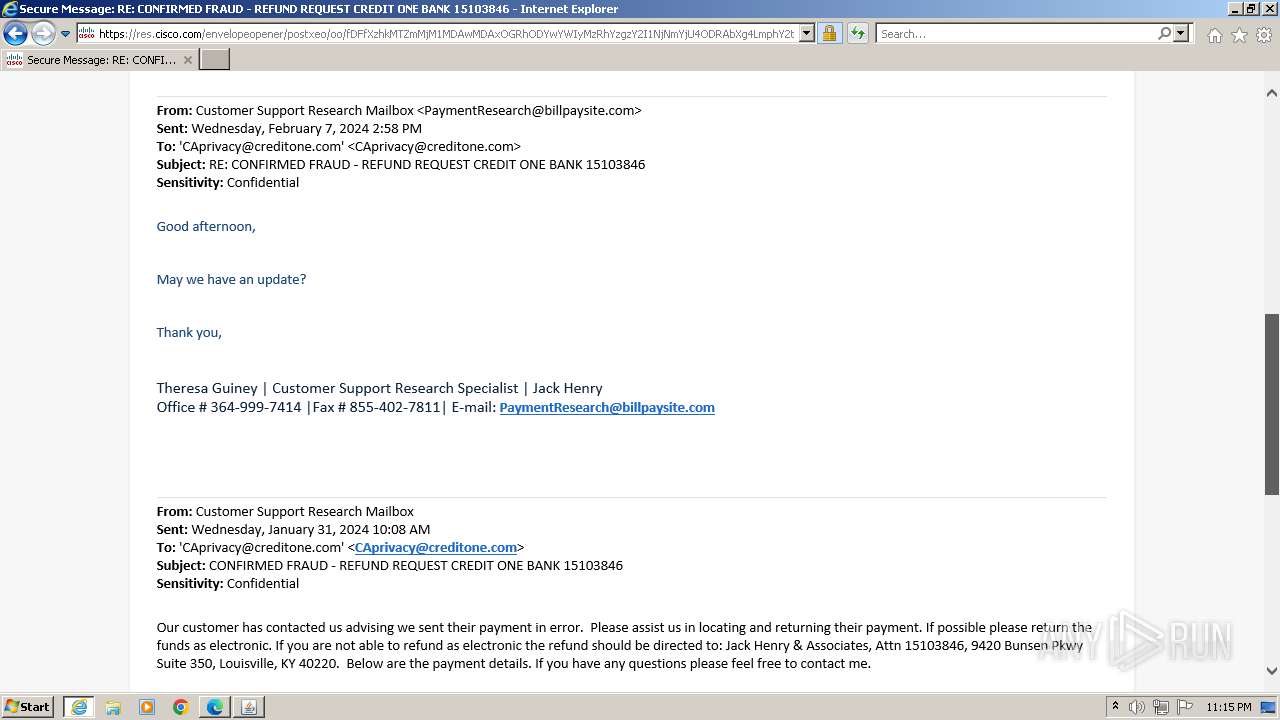
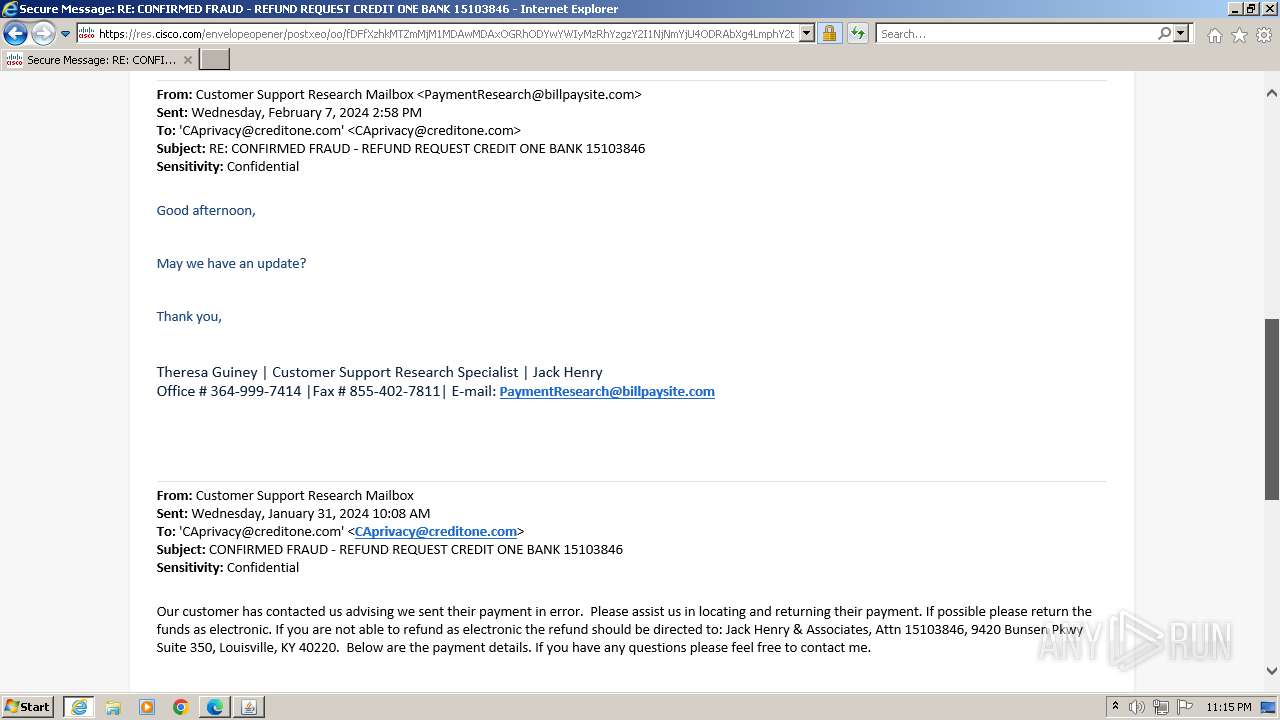
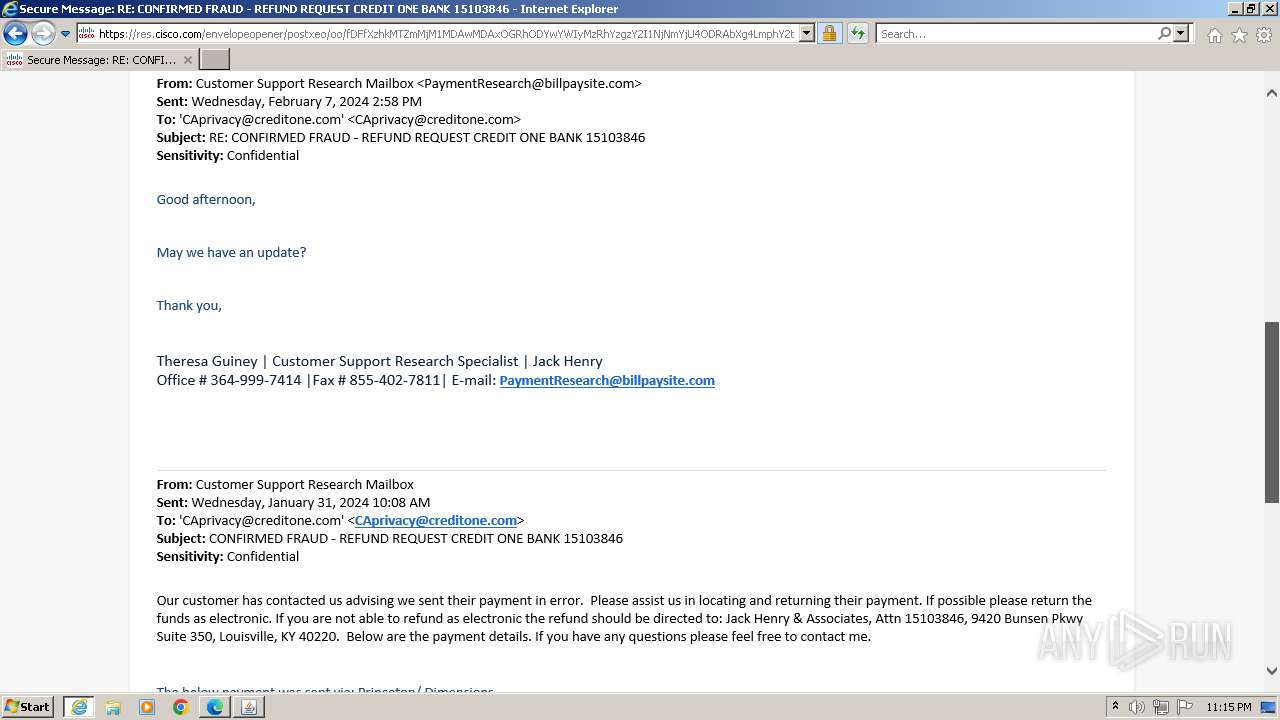
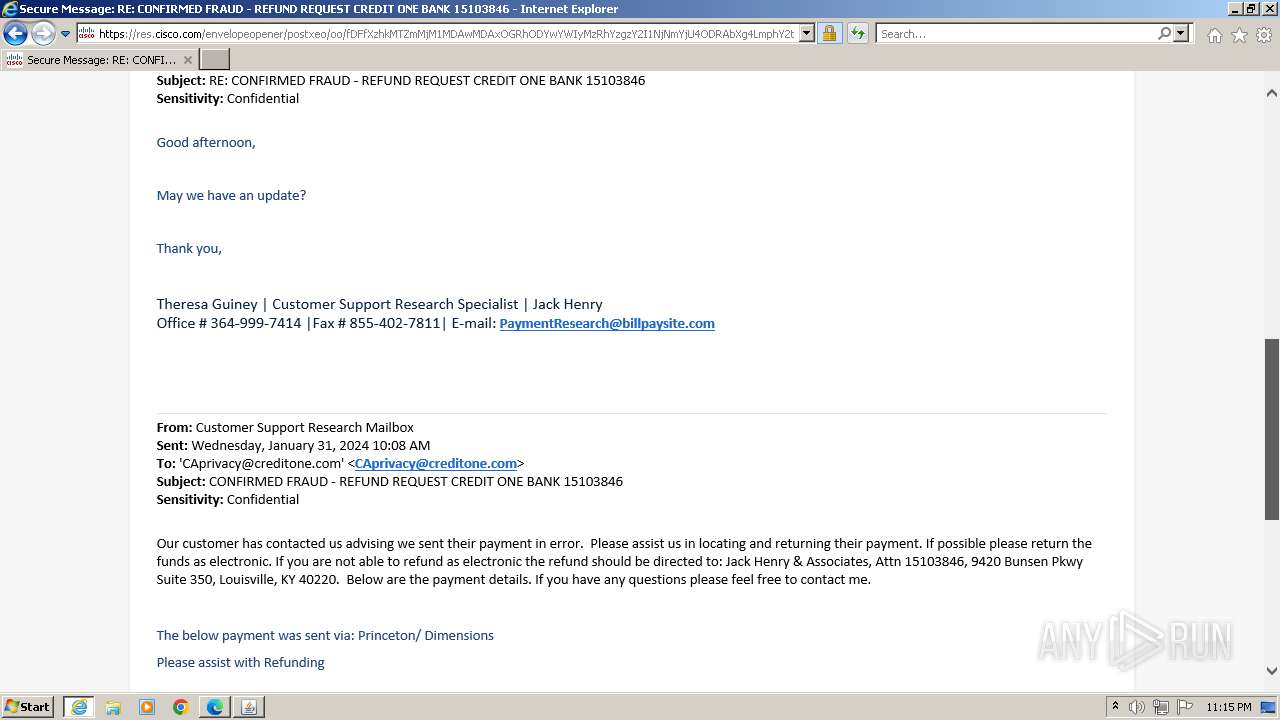
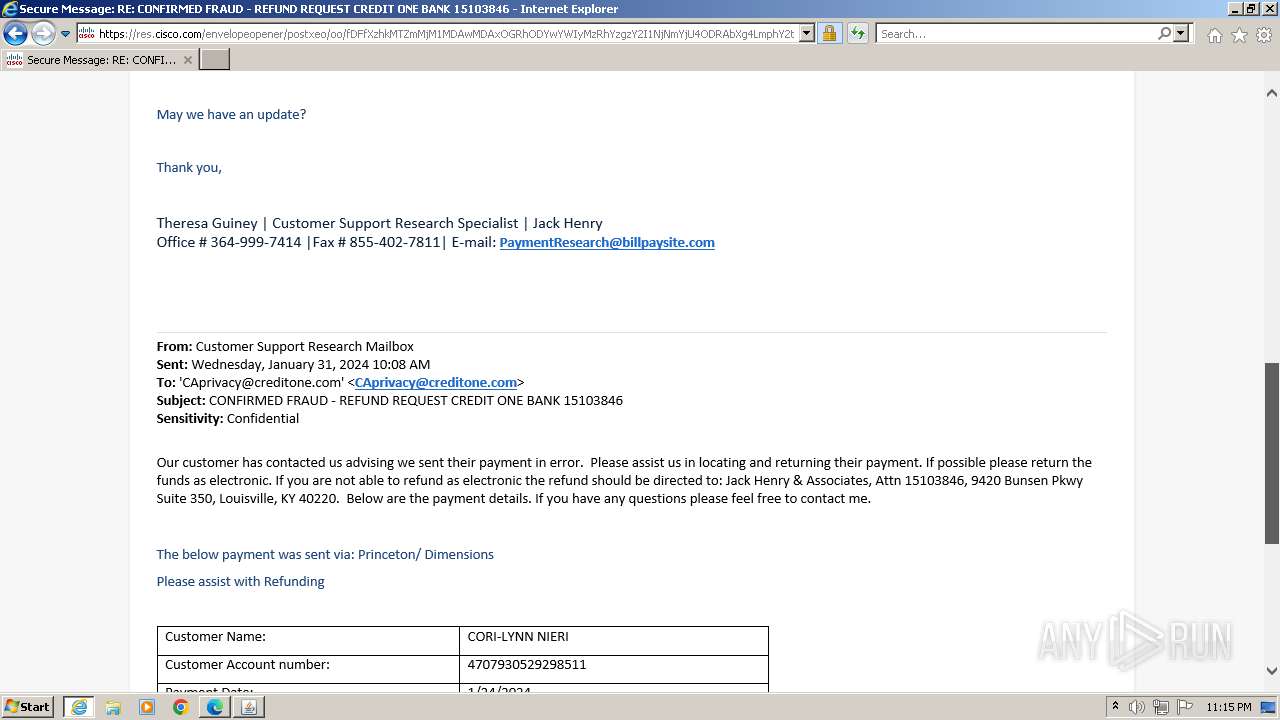
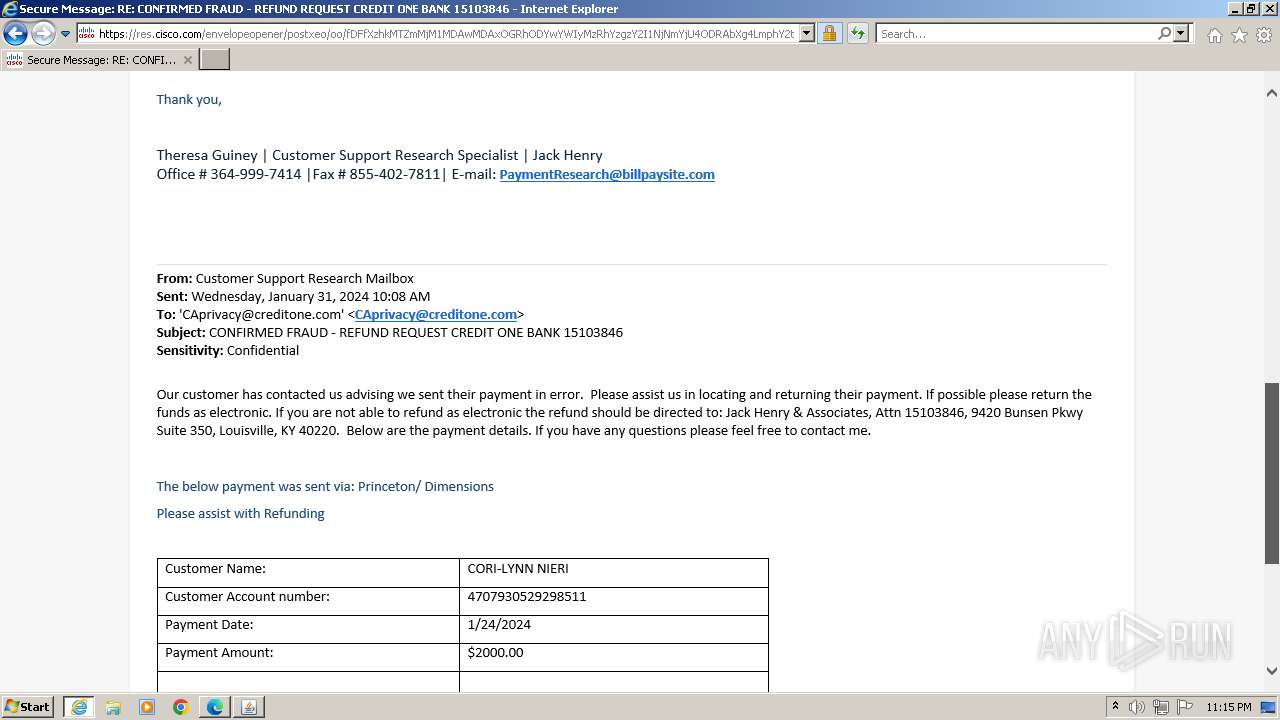
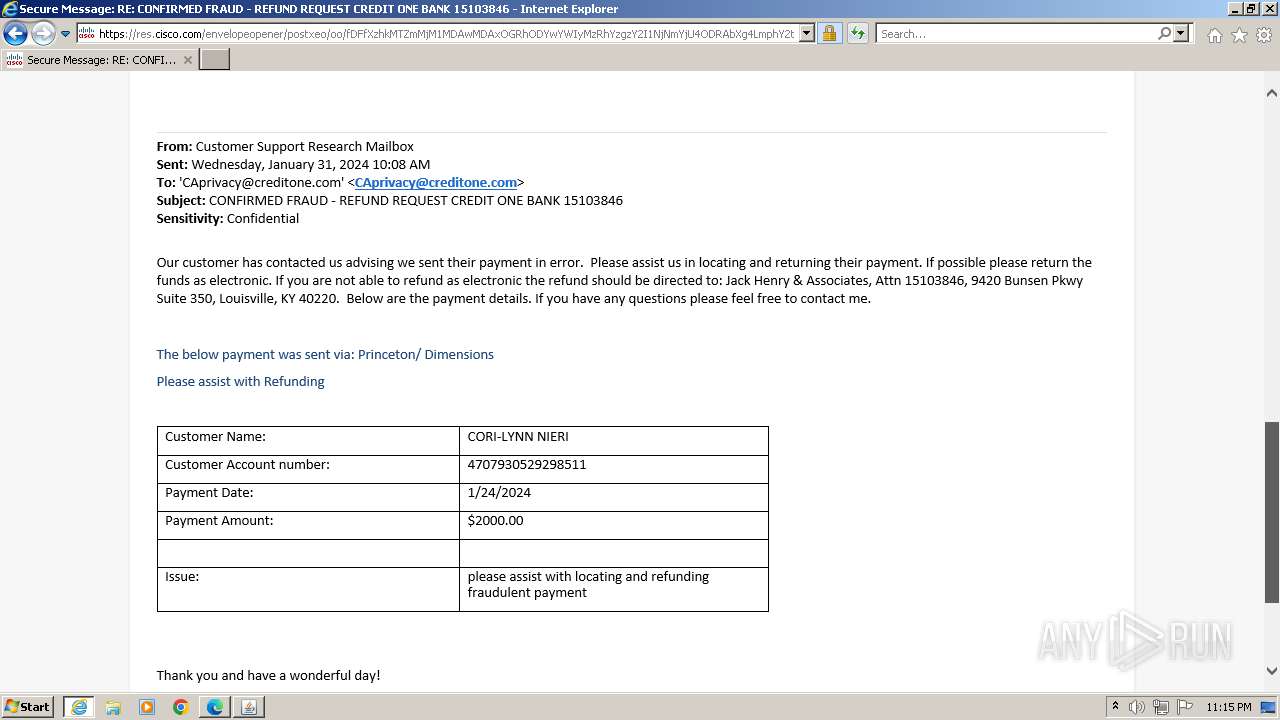
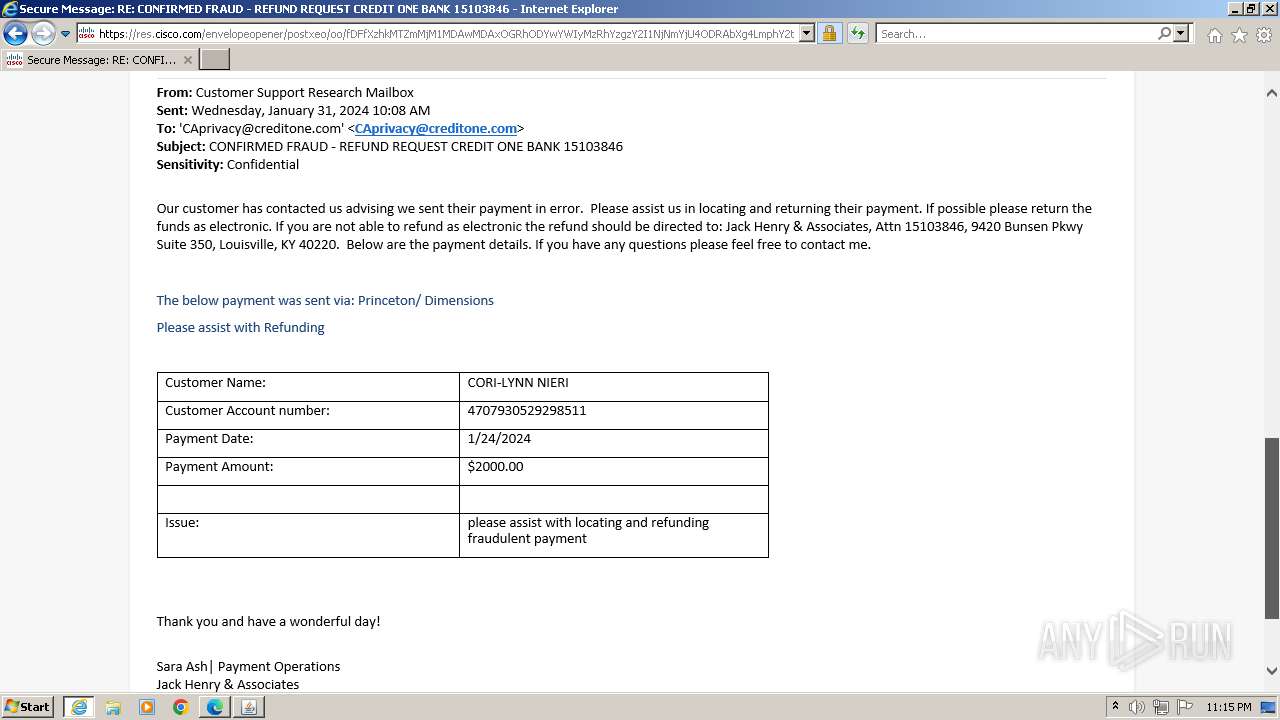
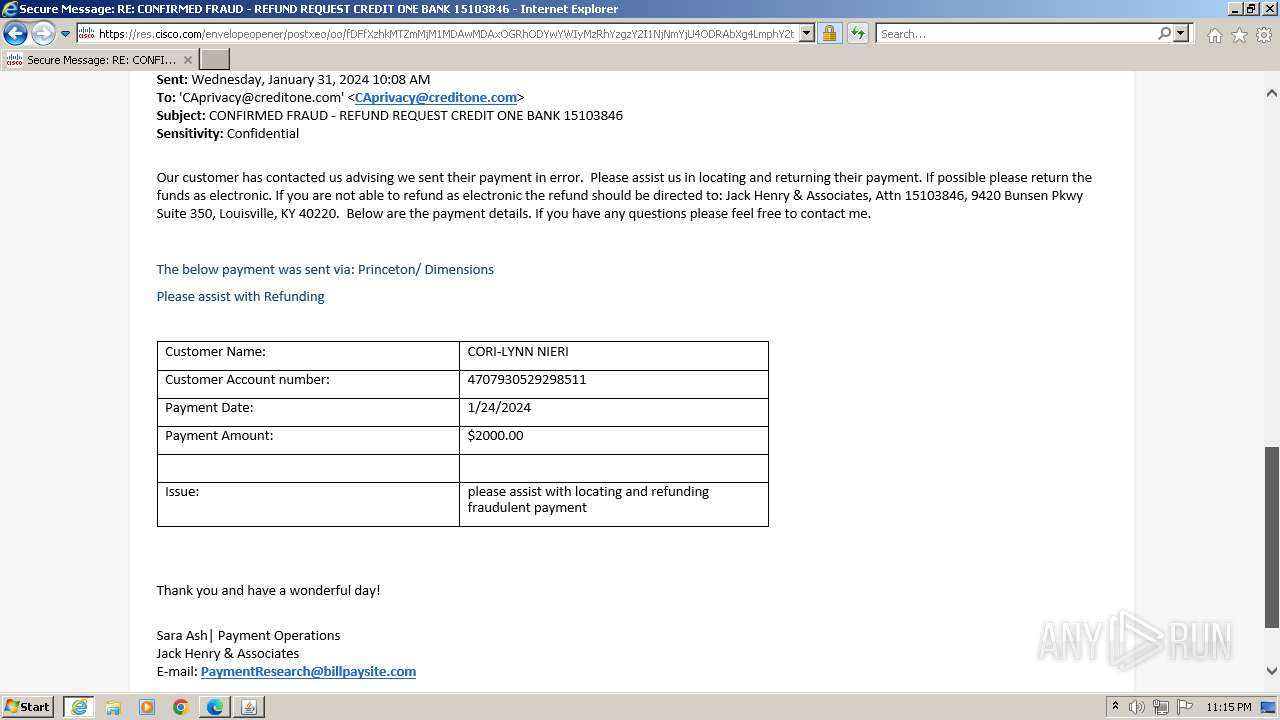
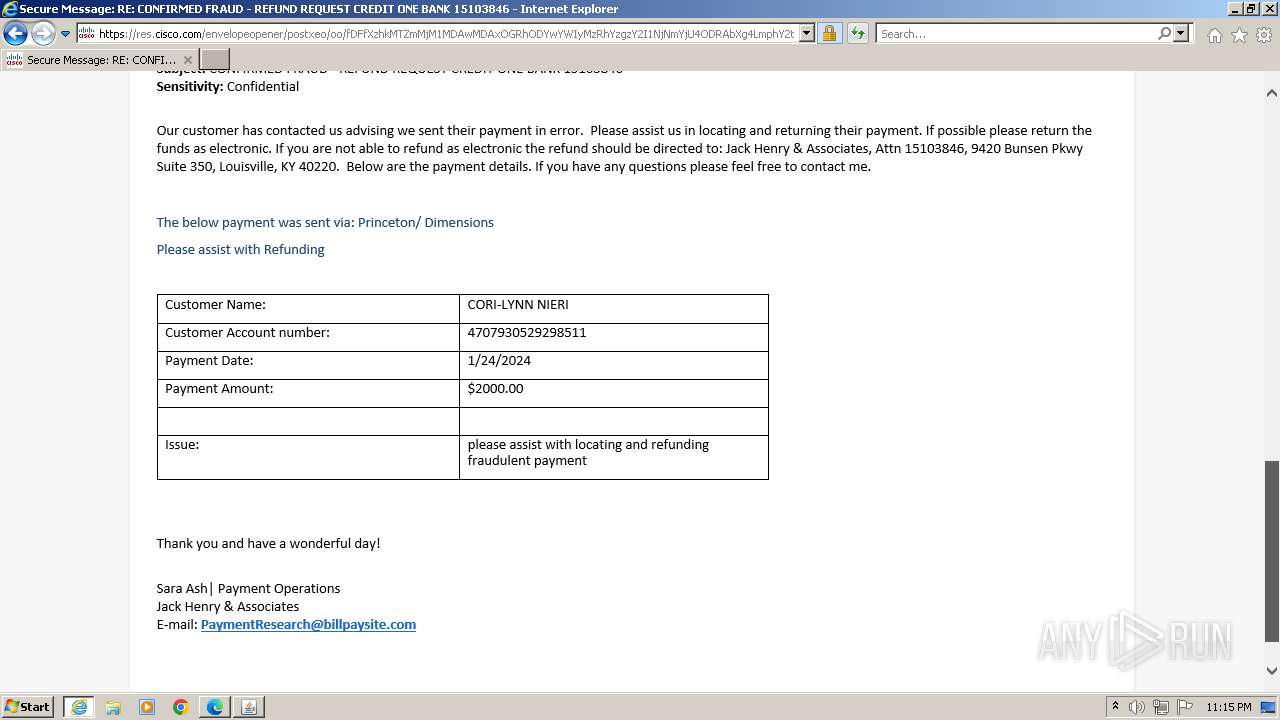
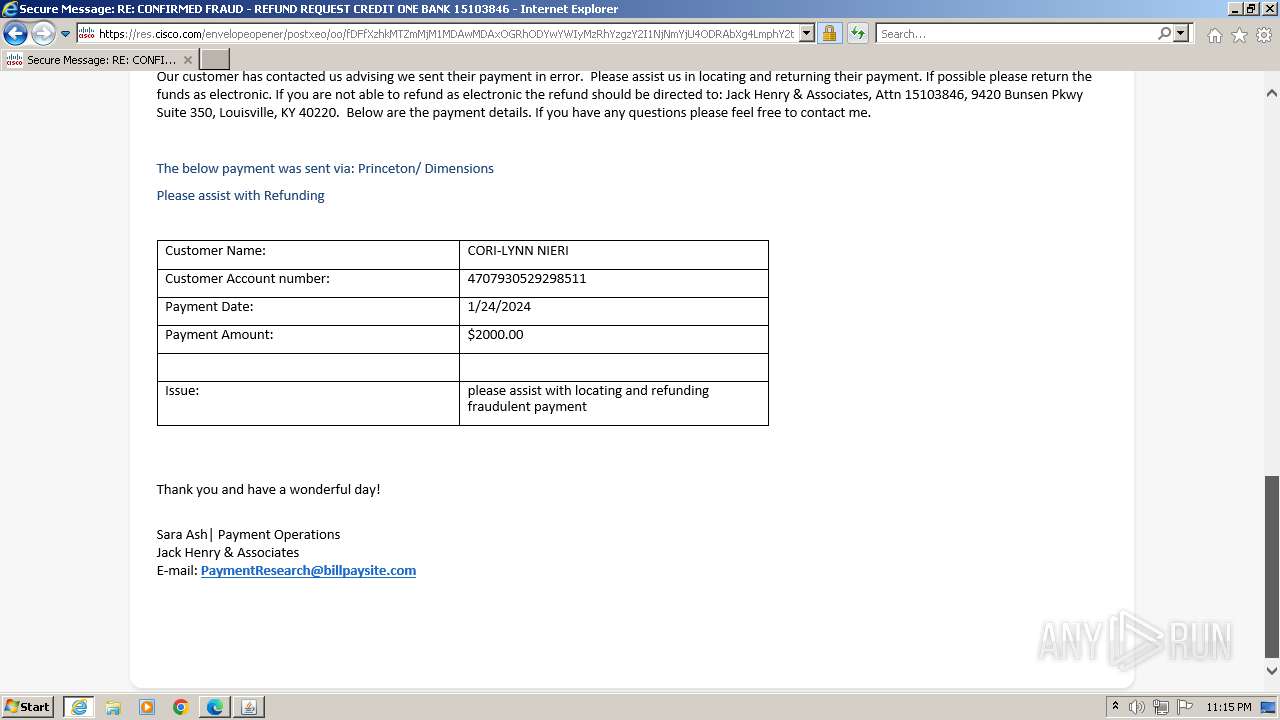
| File name: | securedoc_20240214T100844.html |
| Full analysis: | https://app.any.run/tasks/63017926-a2d2-459d-9a0c-d4b33b075169 |
| Verdict: | Malicious activity |
| Analysis date: | February 14, 2024, 23:13:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, Unicode text, UTF-8 text, with very long lines (474), with CRLF, LF line terminators |
| MD5: | CB6352CF9699AA0F7171FFE32EF87BB4 |
| SHA1: | 37FBE9BAA52E12B77BB13E281C61826BB8D29A4A |
| SHA256: | 99B32A5AA4996A2EBD6A464E6ED37CC4A31D515A10250F71A5F9A2EF4FAA0DE0 |
| SSDEEP: | 3072:8tl/LQISQGjA4RPe8IjIHYONivQpgxmUqA:m/LQIGZIjIHYONivQpg75 |
MALICIOUS
No malicious indicators.SUSPICIOUS
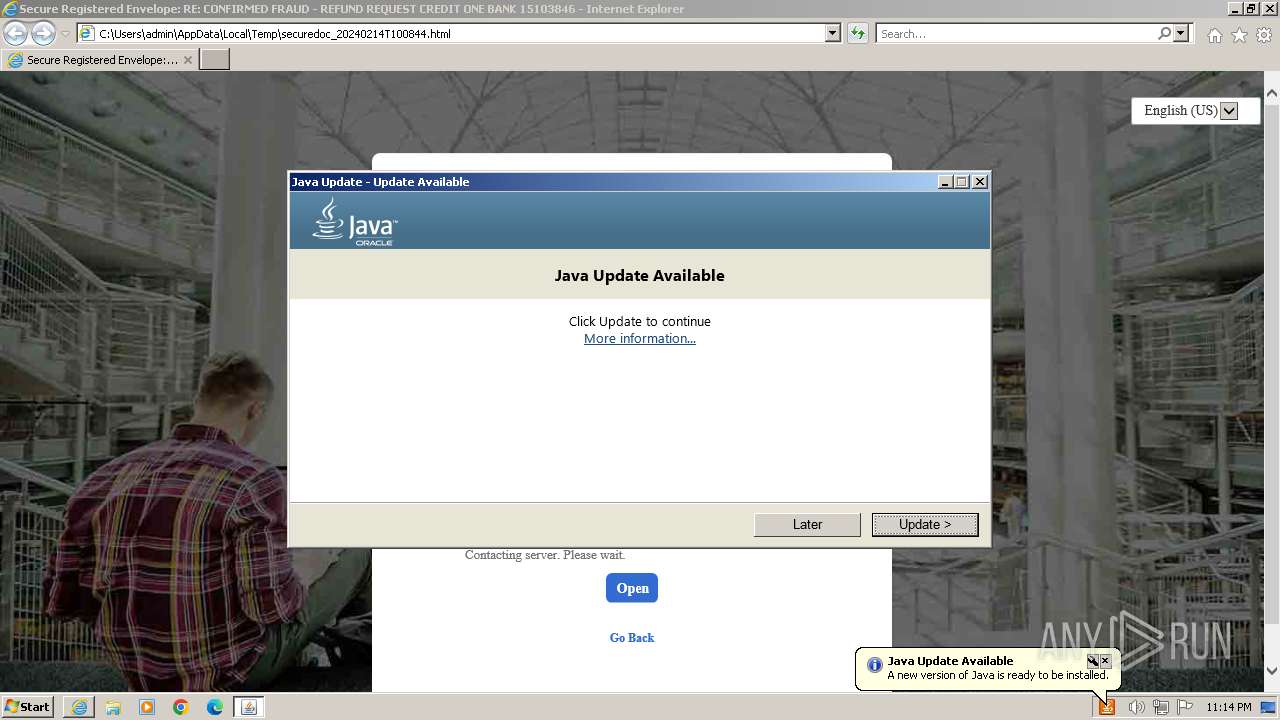
Checks for Java to be installed
- jp2launcher.exe (PID: 2372)
- javaw.exe (PID: 2156)
- javaw.exe (PID: 1112)
- javaw.exe (PID: 2488)
- jucheck.exe (PID: 2804)
- jp2launcher.exe (PID: 3404)
- jp2launcher.exe (PID: 2760)
Reads the Internet Settings
- jucheck.exe (PID: 2804)
- jp2launcher.exe (PID: 2760)
- jp2launcher.exe (PID: 3404)
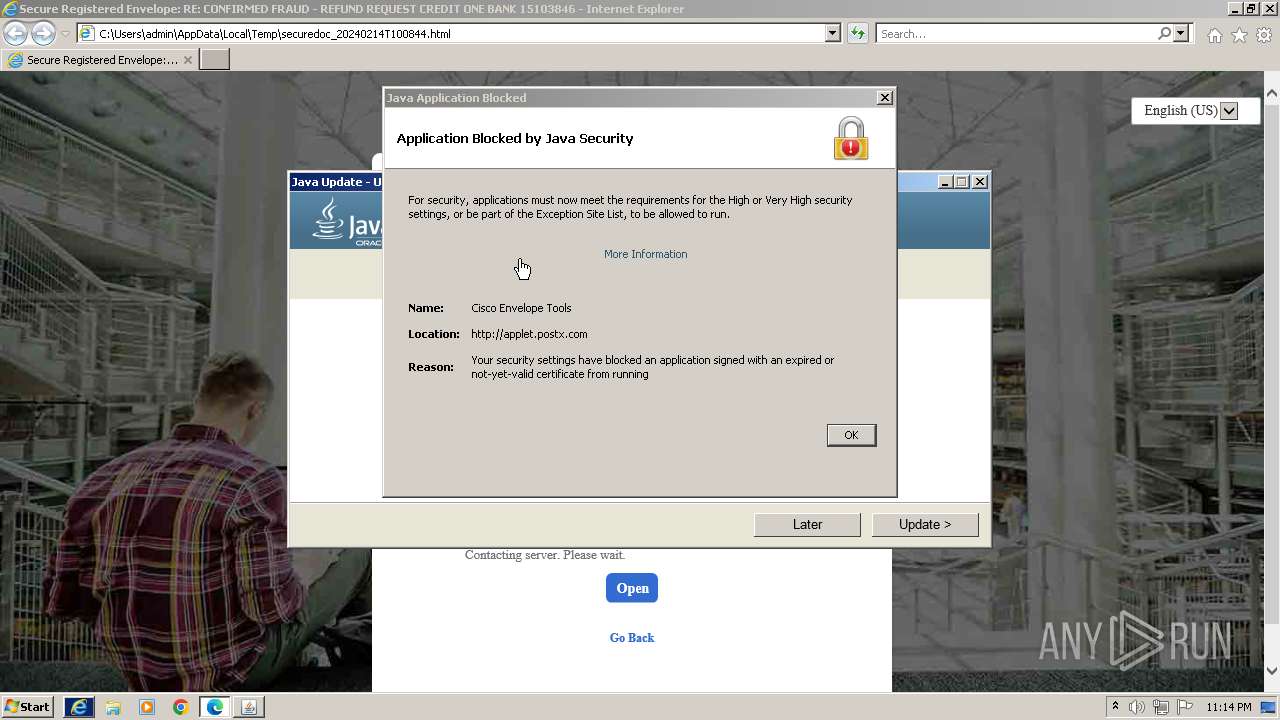
Checks Windows Trust Settings
- jucheck.exe (PID: 2804)
Reads security settings of Internet Explorer
- jucheck.exe (PID: 2804)
- jp2launcher.exe (PID: 3404)
Reads settings of System Certificates
- jucheck.exe (PID: 2804)
- jp2launcher.exe (PID: 3404)
- jp2launcher.exe (PID: 2760)
Reads Microsoft Outlook installation path
- jucheck.exe (PID: 2804)
Reads Internet Explorer settings
- jucheck.exe (PID: 2804)
INFO
Checks supported languages
- jp2launcher.exe (PID: 2372)
- javaw.exe (PID: 2156)
- javaw.exe (PID: 1112)
- javaw.exe (PID: 2488)
- jucheck.exe (PID: 2804)
- jp2launcher.exe (PID: 3404)
- jp2launcher.exe (PID: 2760)
- javaws.exe (PID: 680)
Reads the computer name
- javaw.exe (PID: 2156)
- javaw.exe (PID: 1112)
- javaw.exe (PID: 2488)
- jucheck.exe (PID: 2804)
- jp2launcher.exe (PID: 3404)
- jp2launcher.exe (PID: 2760)
Application launched itself
- iexplore.exe (PID: 3656)
- msedge.exe (PID: 1172)
Create files in a temporary directory
- javaw.exe (PID: 1112)
- javaw.exe (PID: 2156)
- javaw.exe (PID: 2488)
- jucheck.exe (PID: 2804)
- jp2launcher.exe (PID: 3404)
- jp2launcher.exe (PID: 2760)
Creates files in the program directory
- javaw.exe (PID: 2156)
- jucheck.exe (PID: 2804)
Reads the machine GUID from the registry
- jucheck.exe (PID: 2804)
- jp2launcher.exe (PID: 3404)
- jp2launcher.exe (PID: 2760)
Checks proxy server information
- jucheck.exe (PID: 2804)
- jp2launcher.exe (PID: 3404)
- jp2launcher.exe (PID: 2760)
Reads the software policy settings
- jucheck.exe (PID: 2804)
Creates files or folders in the user directory
- jucheck.exe (PID: 2804)
- jp2launcher.exe (PID: 3404)
- jp2launcher.exe (PID: 2760)
Reads security settings of Internet Explorer
- explorer.exe (PID: 3792)
Reads the Internet Settings
- explorer.exe (PID: 3792)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .html | | | HyperText Markup Language (100) |
|---|
Total processes
72
Monitored processes
34
Malicious processes
6
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 680 | "C:\Program Files\Java\jre1.8.0_271\bin\javaws.exe" -J-Djdk.disableLastUsageTracking=true -SSVBaselineUpdate | C:\Program Files\Java\jre1.8.0_271\bin\javaws.exe | — | jucheck.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Start Launcher Exit code: 0 Version: 11.271.2.09 Modules
| |||||||||||||||
| 784 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=entity_extraction_service.mojom.Extractor --lang=en-US --service-sandbox-type=entity_extraction --onnx-enabled-for-ee --mojo-platform-channel-handle=3784 --field-trial-handle=1356,i,9968255674561586391,11035756456116474702,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1044 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=4000 --field-trial-handle=1356,i,9968255674561586391,11035756456116474702,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1112 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -cp "C:\PROGRA~1\Java\JRE18~1.0_2\lib\deploy.jar" com.sun.deploy.panel.ControlPanel -userConfig "deployment.expiration.decision.timestamp.11.271.2" "1707952452" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | jp2launcher.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 1172 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" https://java.com/moreinfo8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1196 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1576 --field-trial-handle=1356,i,9968255674561586391,11035756456116474702,131072 /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1236 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3564 --field-trial-handle=1356,i,9968255674561586391,11035756456116474702,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1264 | "C:\Windows\explorer.exe" C:\ProgramData\Oracle\tmpinstall\javatmp.lnk | C:\Windows\explorer.exe | — | jucheck.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1316 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=109.0.5414.149 "--annotation=exe=C:\Program Files\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win32 "--annotation=prod=Microsoft Edge" --annotation=ver=109.0.1518.115 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0x108,0x699cf598,0x699cf5a8,0x699cf5b4 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1344 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --mojo-platform-channel-handle=3420 --field-trial-handle=1356,i,9968255674561586391,11035756456116474702,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
52 355
Read events
51 906
Write events
350
Delete events
99
Modification events
| (PID) Process: | (3656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31088539 | |||
| (PID) Process: | (3656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31088539 | |||
| (PID) Process: | (3656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
2
Suspicious files
51
Text files
88
Unknown types
64
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3892 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:D03FAA165164E23555706CAF87158DBB | SHA256:BB320419CF3F8E5627FB90E990EDE7AAB7D7ABA236B133173F2EA229A21370C1 | |||
| 3892 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | der | |
MD5:AC89A852C2AAA3D389B2D2DD312AD367 | SHA256:0B720E19270C672F9B6E0EC40B468AC49376807DE08A814573FE038779534F45 | |||
| 3892 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:96CBF30EAE2B5B28292E19B37E405CDB | SHA256:E4EC5C5DDE74232C0DFBC58FBF5CBDEE73C35B880E0B5474BE20896FF5501582 | |||
| 3892 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | der | |
MD5:68A60F4F0F4C8CA9986E2C97319505A7 | SHA256:802BDA88B95C7A685848CBB9A57E6EFF2864F2B62DF5090DC3687249268F6BA6 | |||
| 3892 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\263821BCA2CBC5EA0B25012F05788322_C1E82094EA58093A66BE56163A842E2D | binary | |
MD5:C775AA77AECC51792EECFFC511B24BA4 | SHA256:C5A1D6AB0F113F31B0DDD07D15DF442AE8102C91C8B6B7356FFBF9DB0C236A5F | |||
| 3892 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\select2.min[1].css | text | |
MD5:9F54E6414F87E0D14B9E966F19A174F9 | SHA256:15D6AD4DFDB43D0AFFAD683E70029F97A8F8FC8637A28845009EE0542DCCDF81 | |||
| 3656 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EAF8AA29A62AB29E614331747385D816_F9E4DC0B9D5C777357D7DB8DEF51118A | der | |
MD5:C25CE733F1C3C5FD74DE40DD831D1FEC | SHA256:404B959540AC14725B8B4CC0D69F8E8B783859397A14918CF529352370E83145 | |||
| 3892 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\263821BCA2CBC5EA0B25012F05788322_C1E82094EA58093A66BE56163A842E2D | binary | |
MD5:4A99CBF95BBB5FC9C617CCB6A47CB913 | SHA256:CAECD2FB7F086064F9D55637D92F490E410DD60F218C50DE6CD2D3BCCEF05297 | |||
| 3892 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6CFED4E1A8866BE87BE17622BFB4D726_FBADB8F7FD7B56EE191ACF24A8989D94 | binary | |
MD5:F1B2E5BA5B2DCB62F0833F91913FE2FF | SHA256:D82645E7F829BCFF42D3658463E0C4CC369B755CC11DEE2A2FD4A7304B1644CA | |||
| 3892 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\1QNN6R31.txt | text | |
MD5:4D1877CC5E58E219BEA4417C2A53A69C | SHA256:05C8C1CD4C97CD53D244AEC2D4D62A0CCA0EEAD9B58271D1096D0B80BA3ABECB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
30
TCP/UDP connections
107
DNS requests
68
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3892 | iexplore.exe | GET | 304 | 2.17.147.73:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?78efbe4abe9d690b | unknown | — | — | unknown |
3892 | iexplore.exe | GET | 304 | 2.17.147.73:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?75ec9f2a6caa82c8 | unknown | — | — | unknown |
3892 | iexplore.exe | GET | 304 | 2.17.147.73:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b5c2792402c26fa9 | unknown | — | — | unknown |
3892 | iexplore.exe | GET | 304 | 2.17.147.73:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?98316a4d970a5ec1 | unknown | — | — | unknown |
3892 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | unknown | binary | 1.47 Kb | unknown |
3892 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
3892 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
3892 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEAch2W18yjrFCctU7xjW0Yc%3D | unknown | binary | 471 b | unknown |
3892 | iexplore.exe | GET | 200 | 192.35.177.23:80 | http://commercial.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTQfEOioPd4%2FtCA3%2FhgDklRXB0FwgQU7UQZwNPwBovupHu%2BQucmVMiONnYCEEABbvsKIFz66%2BGPcdc6u3g%3D | unknown | binary | 1.63 Kb | unknown |
3892 | iexplore.exe | GET | 200 | 192.35.177.23:80 | http://commercial.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTULRG8NAnkG2vMiFulhUophWOf2gQUibibtp7t%2B7DGvQ3sZ048o5KdLfkCEEABi5YaEcOFzTolzL%2Frgf4%3D | unknown | binary | 1.46 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3892 | iexplore.exe | 142.250.185.234:443 | ajax.googleapis.com | GOOGLE | US | whitelisted |
3892 | iexplore.exe | 104.17.25.14:443 | cdnjs.cloudflare.com | CLOUDFLARENET | — | unknown |
3892 | iexplore.exe | 13.32.121.40:443 | static.cres-aws.com | AMAZON-02 | US | unknown |
3892 | iexplore.exe | 184.94.241.74:80 | res.cisco.com | IRONPORT-SYSTEMS-INC | US | unknown |
3892 | iexplore.exe | 2.17.147.73:80 | ctldl.windowsupdate.com | Akamai International B.V. | CZ | unknown |
3892 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3892 | iexplore.exe | 142.250.181.227:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
3892 | iexplore.exe | 184.94.241.74:443 | res.cisco.com | IRONPORT-SYSTEMS-INC | US | unknown |
3892 | iexplore.exe | 192.35.177.23:80 | commercial.ocsp.identrust.com | SLC-IDENT-AS | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
static.cres-aws.com |
| unknown |
cdnjs.cloudflare.com |
| whitelisted |
ajax.googleapis.com |
| whitelisted |
res.cisco.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
commercial.ocsp.identrust.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2760 | jp2launcher.exe | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |
3404 | jp2launcher.exe | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |
2760 | jp2launcher.exe | Misc activity | ET INFO JAVA - Java Archive Download By Vulnerable Client |