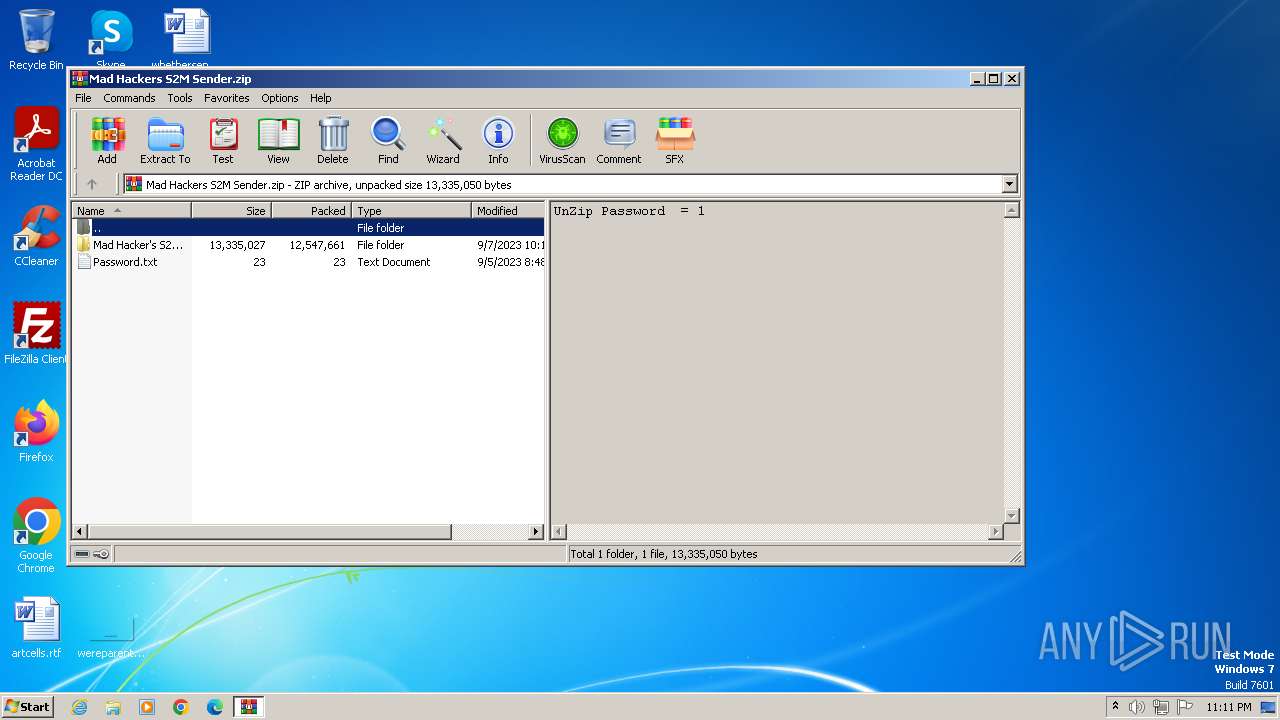
| File name: | Mad Hackers S2M Sender.zip |
| Full analysis: | https://app.any.run/tasks/e93bfe78-b6c6-4014-9cc2-1f6963335c28 |
| Verdict: | Malicious activity |
| Analysis date: | October 31, 2023, 23:10:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 105194348E1959541E1869706A061F77 |
| SHA1: | 1CA6B9A0977BC0B058C23537120F396FEB236D32 |
| SHA256: | 999BE5F2D390251B0BEBCFDE7D6381B100912953914B5BAC07B575E1551D9D61 |
| SSDEEP: | 98304:6qQCVJiiig2At7LjryQWMbMz0hVvCrLuI1kfPcPg+RZ9Y6yCLipj2IGY+7fm69KC:nXk+aKawPuNgurxPqnF4 |
MALICIOUS
Drops the executable file immediately after the start
- send.exe (PID: 3736)
- Setup.exe (PID: 3776)
- svchost.exe (PID: 1840)
SUSPICIOUS
Process drops legitimate windows executable
- send.exe (PID: 3736)
- Setup.exe (PID: 3776)
- svchost.exe (PID: 1840)
Reads the Internet Settings
- send.exe (PID: 3736)
- svchost.exe (PID: 1840)
- Setup.exe (PID: 3776)
Creates executable files that already exist in Windows
- Setup.exe (PID: 3776)
- svchost.exe (PID: 1840)
The process creates files with name similar to system file names
- Setup.exe (PID: 3776)
- svchost.exe (PID: 1840)
Reads settings of System Certificates
- svchost.exe (PID: 1840)
INFO
Manual execution by a user
- send.exe (PID: 3736)
- notepad++.exe (PID: 240)
Reads the computer name
- send.exe (PID: 3736)
- Setup.exe (PID: 2976)
- Setup.exe (PID: 3776)
- svchost.exe (PID: 1840)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2564)
Checks supported languages
- send.exe (PID: 3736)
- Setup.exe (PID: 2976)
- Setup.exe (PID: 3776)
- svchost.exe (PID: 1840)
Create files in a temporary directory
- send.exe (PID: 3736)
Reads the machine GUID from the registry
- Setup.exe (PID: 2976)
- Setup.exe (PID: 3776)
- send.exe (PID: 3736)
- svchost.exe (PID: 1840)
Creates files or folders in the user directory
- Setup.exe (PID: 3776)
- svchost.exe (PID: 1840)
Reads Environment values
- svchost.exe (PID: 1840)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2023:09:07 02:19:08 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Mad Hacker's S2M Sender/ |
Total processes
44
Monitored processes
6
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
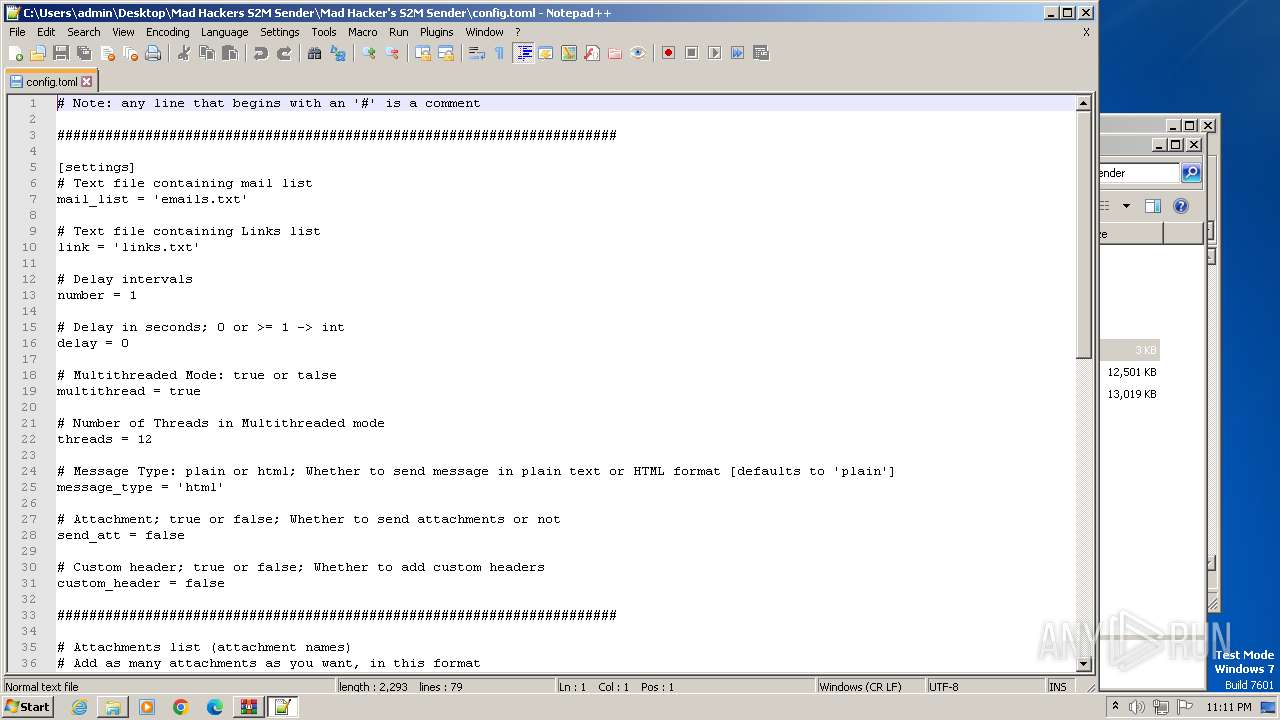
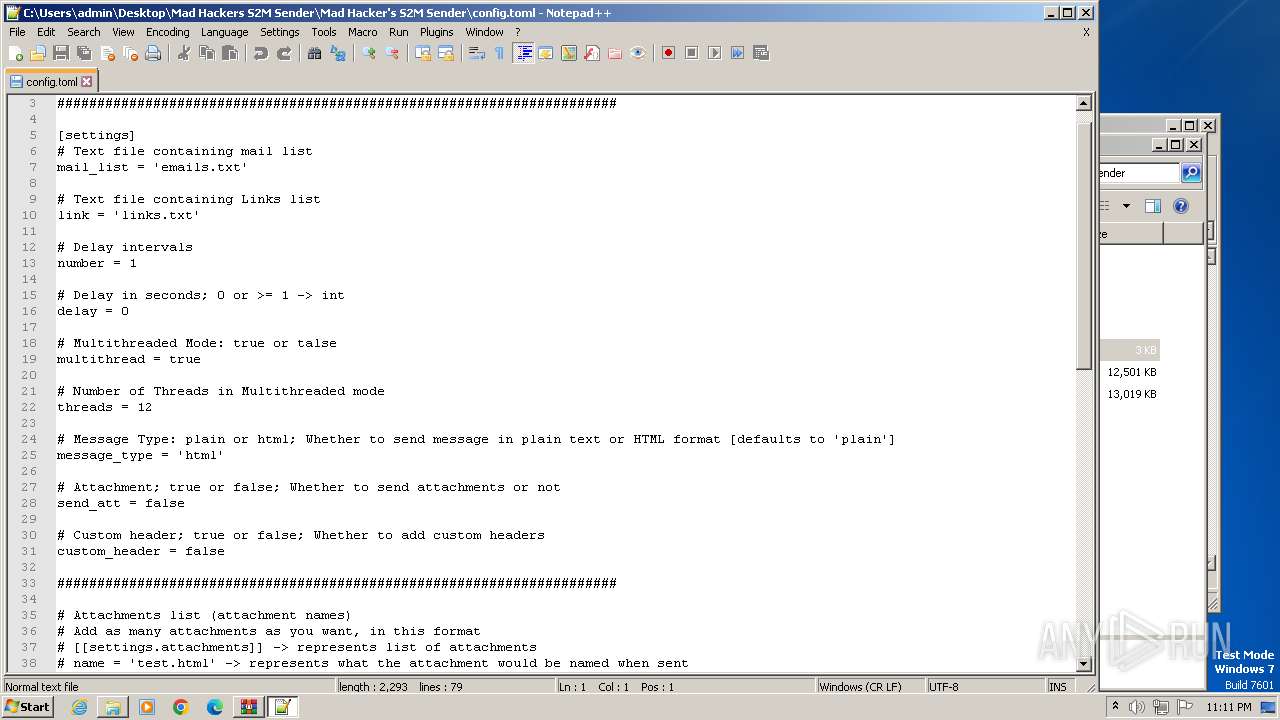
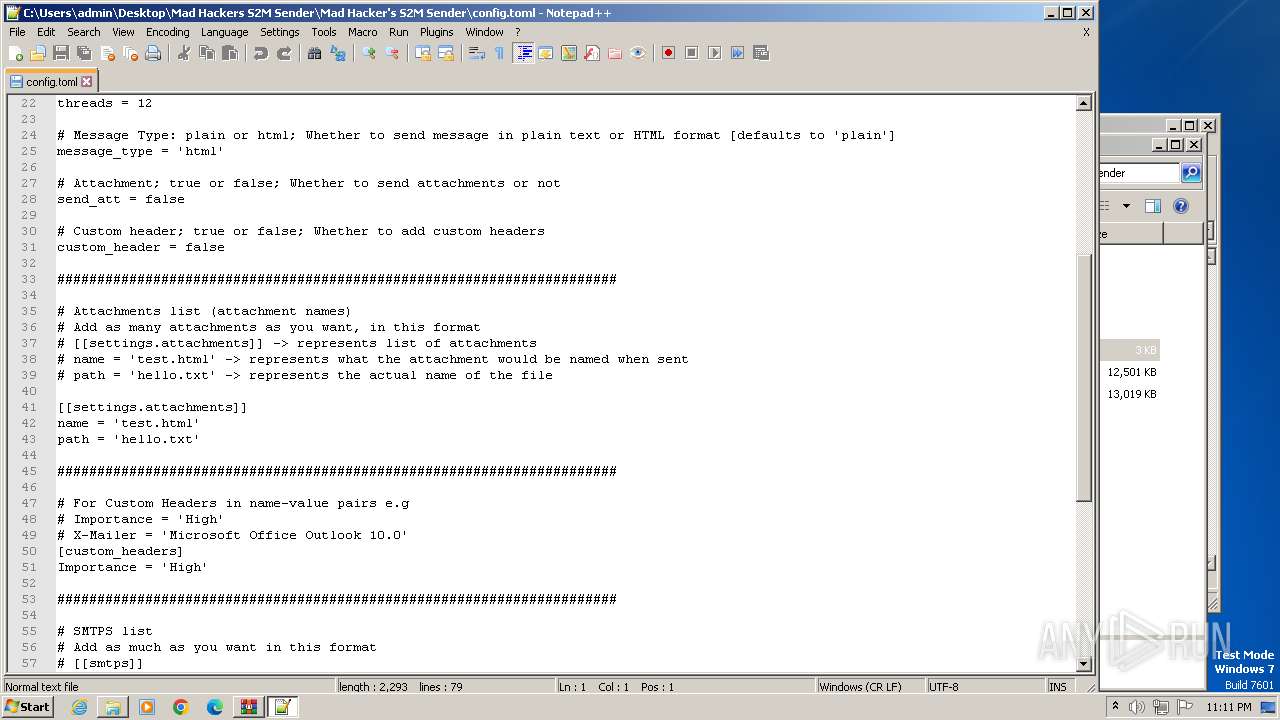
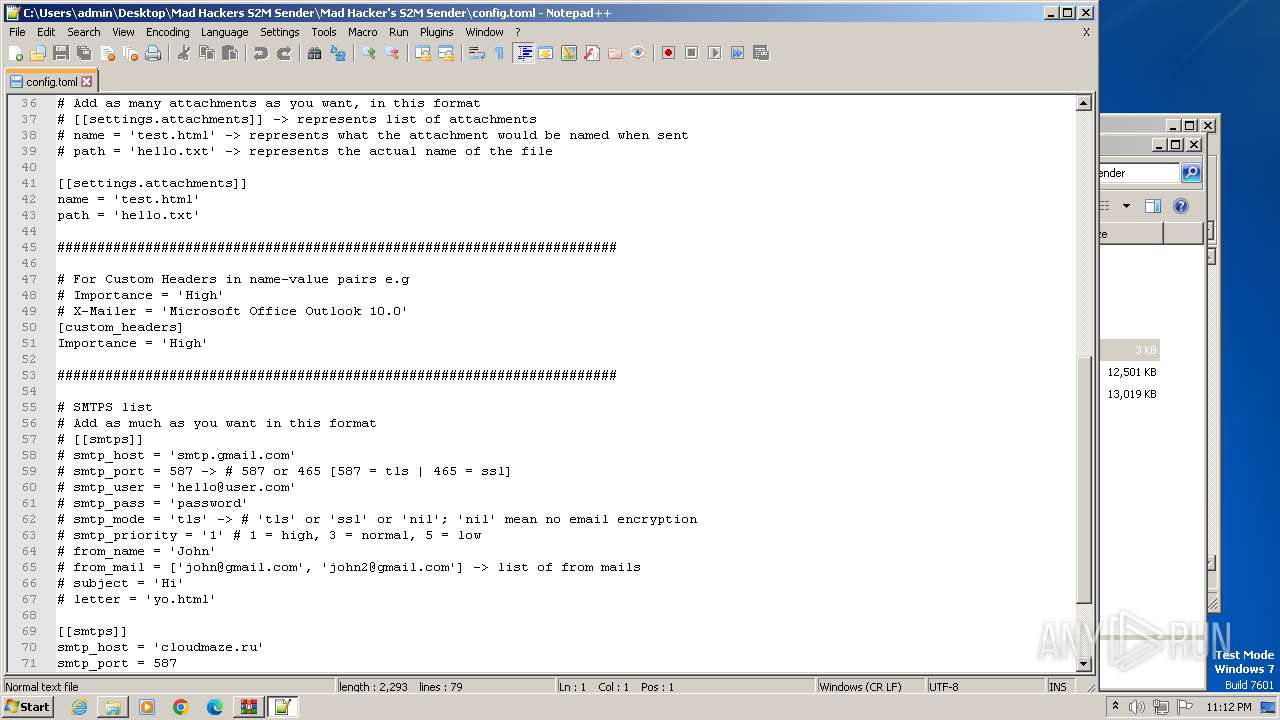
| 240 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\Mad Hackers S2M Sender\Mad Hacker's S2M Sender\config.toml" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
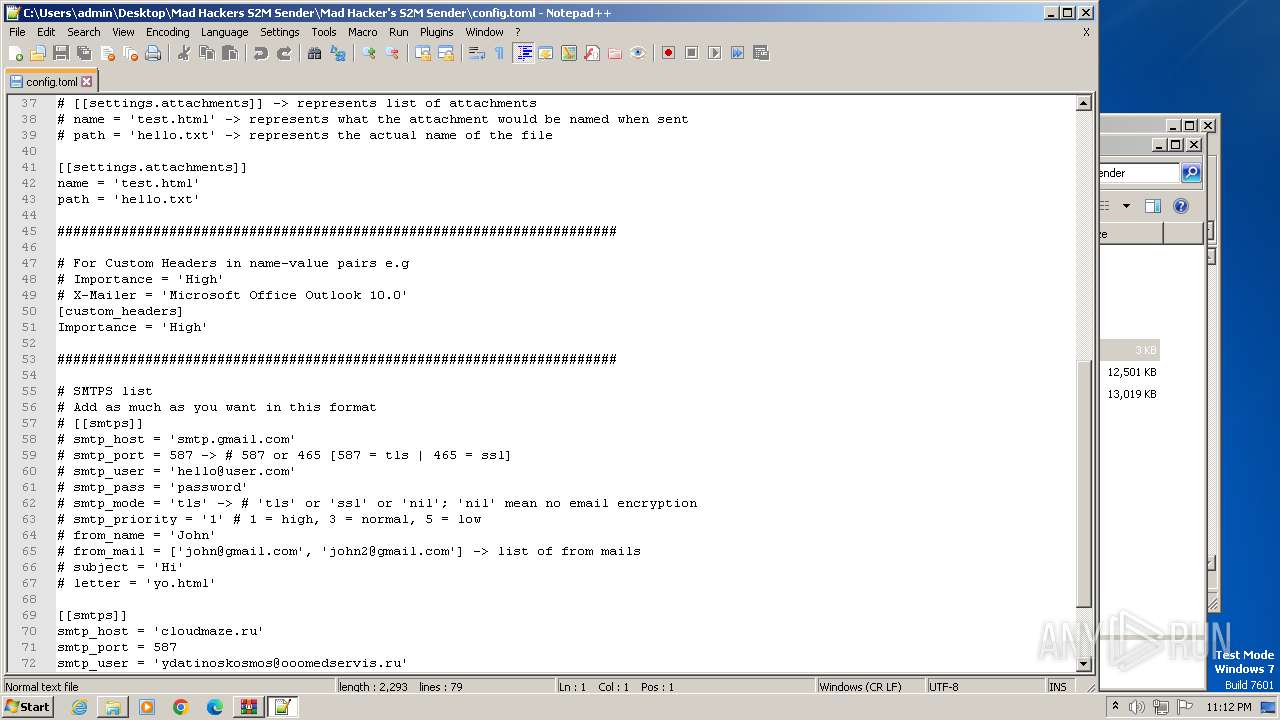
| 1840 | "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\svchost.exe" | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\svchost.exe | Setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 8.1.1.7900 Modules
| |||||||||||||||
| 2564 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Mad Hackers S2M Sender.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2976 | "C:\Users\admin\AppData\Local\Temp\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Setup.exe | — | send.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 8.1.1.7900 Modules
| |||||||||||||||
| 3736 | "C:\Users\admin\Desktop\Mad Hackers S2M Sender\Mad Hacker's S2M Sender\send.exe" | C:\Users\admin\Desktop\Mad Hackers S2M Sender\Mad Hacker's S2M Sender\send.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 3776 | "C:\Users\admin\AppData\Local\Temp\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Setup.exe | — | send.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 8.1.1.7900 Modules
| |||||||||||||||
Total events
5 854
Read events
5 794
Write events
60
Delete events
0
Modification events
| (PID) Process: | (2564) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
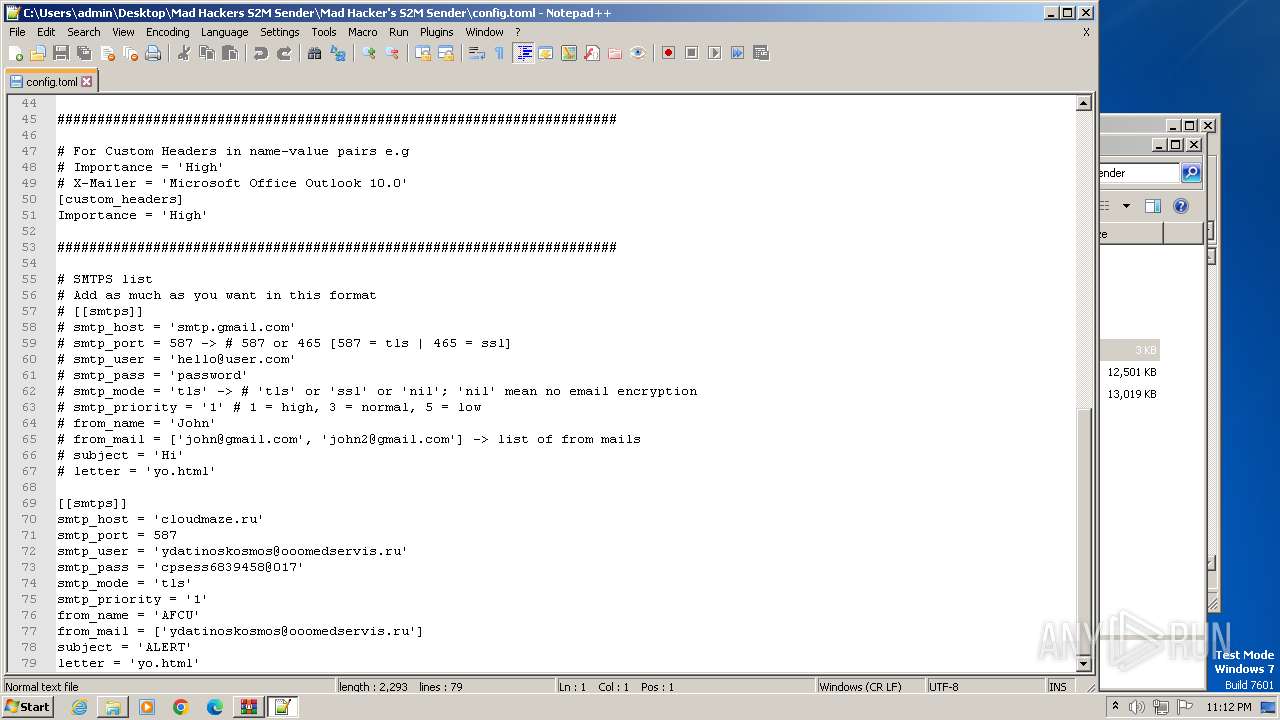
| (PID) Process: | (3736) send.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3736) send.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
5
Suspicious files
2
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
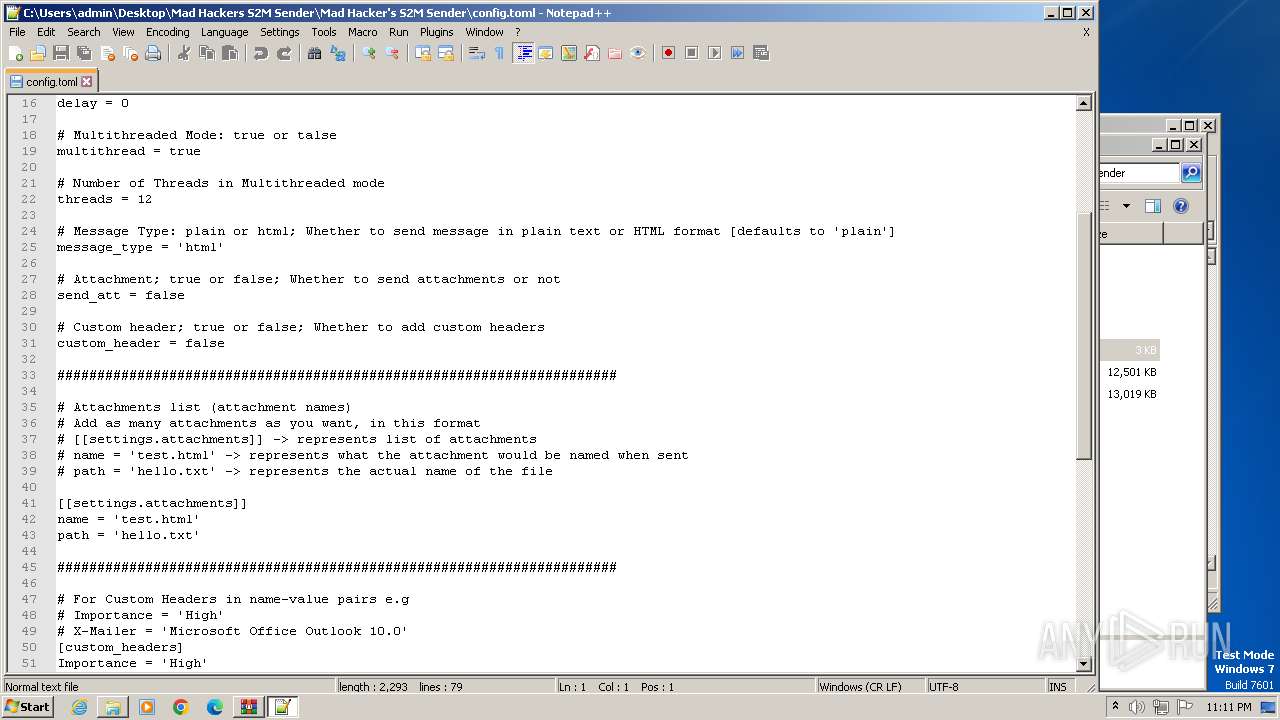
| 2564 | WinRAR.exe | C:\Users\admin\Desktop\Mad Hackers S2M Sender\Mad Hacker's S2M Sender\attachments\hello.txt | text | |
MD5:75A70A9352B587BB0CE9AB521FDC961A | SHA256:3A830B8237CD4935021BE29150590C687F68A3311DD2805290325B15D81E46A0 | |||
| 1840 | svchost.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\explorer.zip | compressed | |
MD5:7ECA085E07E2426A3E07B977EAF19CEC | SHA256:865BE5E48FB179C6A76AF2774A528EF97F257E10622A836A5D6FA86557BC3B15 | |||
| 2564 | WinRAR.exe | C:\Users\admin\Desktop\Mad Hackers S2M Sender\Mad Hacker's S2M Sender\file\links\links.txt | text | |
MD5:759E3F11A2BB6517FE44DB56396E98FF | SHA256:FA0E5107F7EAEF442DBDDA0A805CA5EDE8A2E6457A0D2AF44F34E42324373870 | |||
| 2564 | WinRAR.exe | C:\Users\admin\Desktop\Mad Hackers S2M Sender\Mad Hacker's S2M Sender\doc\requirements.txt | text | |
MD5:DF7561B725E50E527ABED0E3E57D4E33 | SHA256:B89FE52C982E70403EF979BD637D2CFE3439846A02B11B435FE745499B8F2D94 | |||
| 2564 | WinRAR.exe | C:\Users\admin\Desktop\Mad Hackers S2M Sender\Mad Hacker's S2M Sender\file\maillist\emails.txt | text | |
MD5:477A7AE36092B382C403700378A9E46F | SHA256:705AD709FAE223F1596B5BDC67A26A7E0B540917C7B47CCF4951106C2999B6B5 | |||
| 2564 | WinRAR.exe | C:\Users\admin\Desktop\Mad Hackers S2M Sender\Mad Hacker's S2M Sender\letter\yo.html | text | |
MD5:CE3736721907235A6BCE8E34C8EF07F6 | SHA256:6A50FE340DB0EF44CB26BA6887B20C0F28C2CF37F36E7E83AC6C8500D7CED031 | |||
| 3736 | send.exe | C:\Users\admin\Desktop\Mad Hackers S2M Sender\Mad Hacker's S2M Sender\send .exe | executable | |
MD5:2C28CA07E62827BC442F313B3F822BB7 | SHA256:2F74A55FA9703D822B7D387CE01E80679D557E972DB3862A571A78BC24CE5917 | |||
| 2564 | WinRAR.exe | C:\Users\admin\Desktop\Mad Hackers S2M Sender\Mad Hacker's S2M Sender\send.exe | executable | |
MD5:E24D6B7F4BCD7A0BBBB5E2731790B146 | SHA256:A2E452150746A5345C2BB5FD1CD4B795904484D8EE8089F4F64BE132BAED9604 | |||
| 3736 | send.exe | C:\Users\admin\AppData\Local\Temp\Setup.exe | executable | |
MD5:6D5AD2ADCE366350200958C37F08A994 | SHA256:C0B6C7B060BA8B898777CE72E4A2D0B0A9DF4591DDDD10037762DA40E6887FC2 | |||
| 3776 | Setup.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\svchost.exe | executable | |
MD5:5E24E97BBC8354E13EE3AB70DA2F3AF6 | SHA256:69D3CF6C83D6B21ABBE13EA46F6FA0462C564712DDAD17B9151AC36DB85486FE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
6
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1840 | svchost.exe | HEAD | 200 | 107.180.41.239:80 | http://amazonhost.thedreamsop.com/2023/explorer.txt | unknown | — | — | unknown |
1840 | svchost.exe | HEAD | 200 | 107.180.41.239:80 | http://amazonhost.thedreamsop.com/2023/explorer.txt | unknown | — | — | unknown |
1840 | svchost.exe | HEAD | 200 | 107.180.41.239:80 | http://amazonhost.thedreamsop.com/2023/explorer.txt | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2656 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1840 | svchost.exe | 142.250.185.97:443 | proxy-cheap.blogspot.com | GOOGLE | US | whitelisted |
1840 | svchost.exe | 107.180.41.239:80 | amazonhost.thedreamsop.com | AS-26496-GO-DADDY-COM-LLC | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
proxy-cheap.blogspot.com |
| unknown |
amazonhost.thedreamsop.com |
| unknown |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|