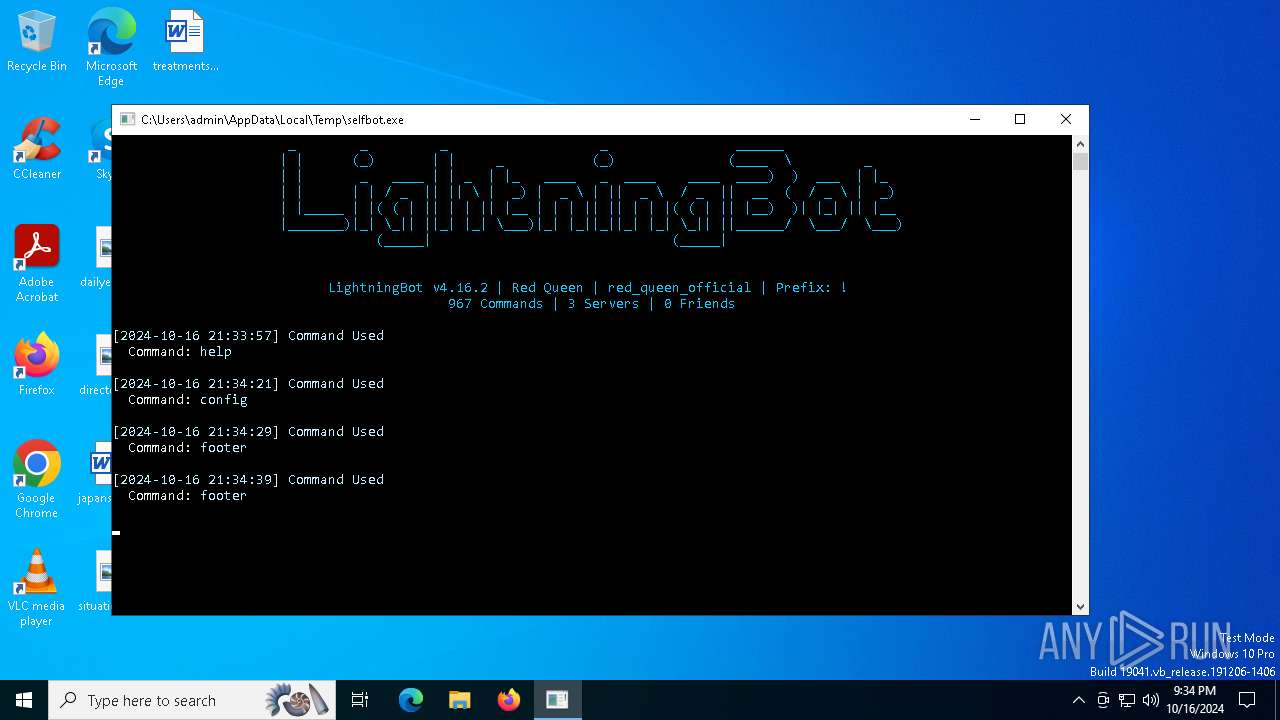
| File name: | selfbot.exe |
| Full analysis: | https://app.any.run/tasks/7d4093fb-9731-4954-ad6c-03eeafa310aa |
| Verdict: | Malicious activity |
| Analysis date: | October 16, 2024, 21:29:39 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (console) x86-64, for MS Windows |
| MD5: | 8F51259600ABF7AD700D70848F36216B |
| SHA1: | 0645EA6CDD98DBC77E376DC2C58DCFB93F83B0E1 |
| SHA256: | 996853D821D6C52826B7C0C57808A8A4DF548196A7FC404A17B726439DB929FD |
| SSDEEP: | 98304:iCT2pccIWBqm58abX4GGhzBAZHBMsqM0sIWOzUaUoSJPU74sKFcbnhwkXMsFXOQT:MukcADtVl8+CJcY9uz4FU |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 6488)
- powershell.exe (PID: 3696)
- powershell.exe (PID: 2196)
- powershell.exe (PID: 3648)
- powershell.exe (PID: 6248)
- powershell.exe (PID: 6516)
Changes powershell execution policy (Bypass)
- selfbot.exe (PID: 4548)
SUSPICIOUS
The process bypasses the loading of PowerShell profile settings
- selfbot.exe (PID: 4548)
Starts POWERSHELL.EXE for commands execution
- selfbot.exe (PID: 4548)
The process executes Powershell scripts
- selfbot.exe (PID: 4548)
INFO
Checks supported languages
- selfbot.exe (PID: 4548)
UPX packer has been detected
- selfbot.exe (PID: 4548)
Reads the software policy settings
- selfbot.exe (PID: 4548)
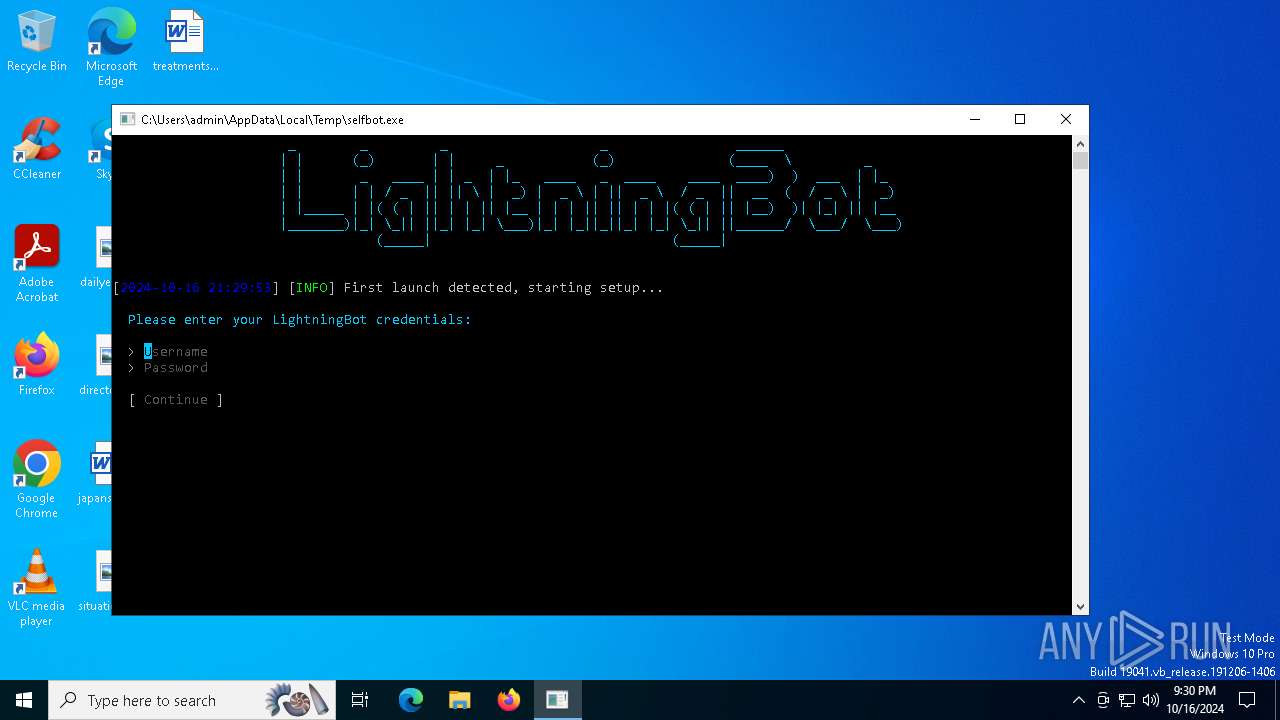
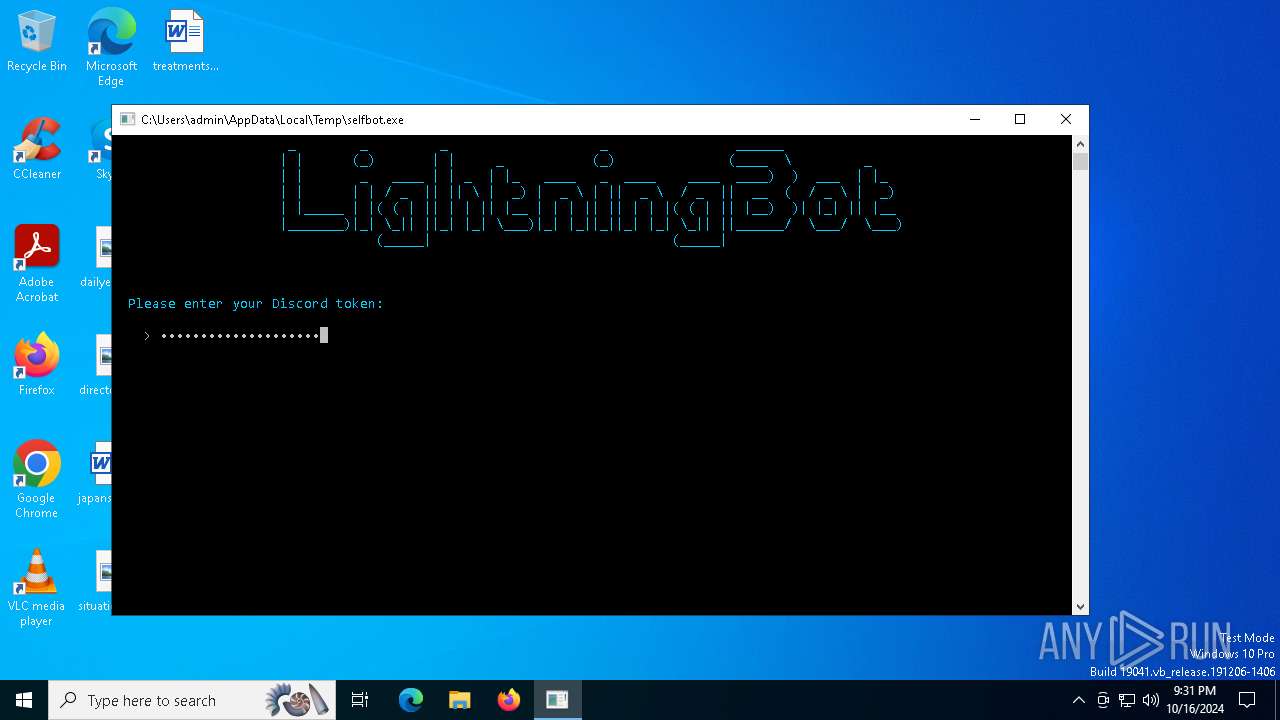
Attempting to use instant messaging service
- selfbot.exe (PID: 4548)
Creates files or folders in the user directory
- selfbot.exe (PID: 4548)
Drops encrypted JS script (Microsoft Script Encoder)
- selfbot.exe (PID: 4548)
Create files in a temporary directory
- selfbot.exe (PID: 4548)
Reads the computer name
- selfbot.exe (PID: 4548)
Reads the machine GUID from the registry
- selfbot.exe (PID: 4548)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (87.1) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.4) |
| .exe | | | DOS Executable Generic (6.4) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 0000:00:00 00:00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 3 |
| CodeSize: | 11407360 |
| InitializedDataSize: | 4096 |
| UninitializedDataSize: | 29446144 |
| EntryPoint: | 0x26f6280 |
| OSVersion: | 6.1 |
| ImageVersion: | 1 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows command line |
Total processes
140
Monitored processes
9
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2196 | PowerShell -ExecutionPolicy Bypass -File C:\Users\admin\AppData\Local\Temp\ddcc9e20-6f09-41dd-5a03-fca7e13c1e5d.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | selfbot.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3648 | PowerShell -ExecutionPolicy Bypass -File C:\Users\admin\AppData\Local\Temp\f15ff8ad-011e-4d41-63bb-d139ce165da1.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | selfbot.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3696 | PowerShell -ExecutionPolicy Bypass -File C:\Users\admin\AppData\Local\Temp\c78632be-9152-487c-4eac-2d0397cca99a.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | selfbot.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4548 | "C:\Users\admin\AppData\Local\Temp\selfbot.exe" | C:\Users\admin\AppData\Local\Temp\selfbot.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6248 | PowerShell -ExecutionPolicy Bypass -File C:\Users\admin\AppData\Local\Temp\7e6fa6b6-c3a9-4e40-7cd9-d0457fa960ce.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | selfbot.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6284 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | selfbot.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6488 | PowerShell -ExecutionPolicy Bypass -File C:\Users\admin\AppData\Local\Temp\9cc2445c-a0ed-48f2-4e6c-0eb568c9e3e6.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | selfbot.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6516 | PowerShell -ExecutionPolicy Bypass -File C:\Users\admin\AppData\Local\Temp\c10731c2-0136-4549-4a61-b6e011d6182e.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | selfbot.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6704 | powershell -NoProfile Get-StartApps | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | selfbot.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
35 698
Read events
35 698
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
2
Text files
23
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6704 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_va020sam.st3.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6704 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_4nfupk4k.5j3.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4548 | selfbot.exe | C:\Users\admin\AppData\Roaming\LightningBot\Logo.png | image | |
MD5:83BF0E353373ECC8D638DA44DE4F5602 | SHA256:B5664B33E6B81468DB063C8FC0632C6AA7CCC0562F870B3F07CFE72E2CF6DE79 | |||
| 4548 | selfbot.exe | C:\Users\admin\AppData\Roaming\LightningBot\Config\config.json | binary | |
MD5:70C0083019F3EDCFAA1B1FC3847C5B0C | SHA256:BCC70CD955D0B687294C084A7EC4CC7166701E5C30A08257C10AAD4CCF09B559 | |||
| 4548 | selfbot.exe | C:\Users\admin\AppData\Local\Temp\9cc2445c-a0ed-48f2-4e6c-0eb568c9e3e6.ps1 | text | |
MD5:E43873CFD725C6A6217B9E335A56DD8E | SHA256:AADFE70CFAAD84166778F639F712774FE642A7933E2EB4825F550F4C4BAC07AE | |||
| 6704 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:65179433C0FBDAA2A5C6ADEEAE95584D | SHA256:1F08E803F8DF8882FCA020D862C8684AA26787A8D03E9B1E51720CCC73324A3E | |||
| 6516 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_tobzt4aw.sni.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4548 | selfbot.exe | C:\Users\admin\AppData\Local\Temp\f15ff8ad-011e-4d41-63bb-d139ce165da1.ps1 | text | |
MD5:BBF52B9D08AEED797DB2B70BF87FEBB2 | SHA256:606D2D04EC04A3AD4EE9574C6D3361220635CABA6E1B134FBC8F76F602867D1F | |||
| 4548 | selfbot.exe | C:\Users\admin\AppData\Local\Temp\7e6fa6b6-c3a9-4e40-7cd9-d0457fa960ce.ps1 | text | |
MD5:B052F411EC369BCD26E5BE529E277B20 | SHA256:FD023DCF2E7E5ACA71C8598EB1D682A98D8F8B9EB2915E882B37CF4B8623E60D | |||
| 6248 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_nsov4cb3.vhs.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
67
DNS requests
30
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6944 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2776 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6136 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6136 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3608 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1584 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6944 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6944 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4548 | selfbot.exe | 172.67.180.228:443 | api.lightning-bot.com | CLOUDFLARENET | US | unknown |
4360 | SearchApp.exe | 104.126.37.147:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
api.lightning-bot.com |
| unknown |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2172 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
4548 | selfbot.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
2172 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
4548 | selfbot.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |