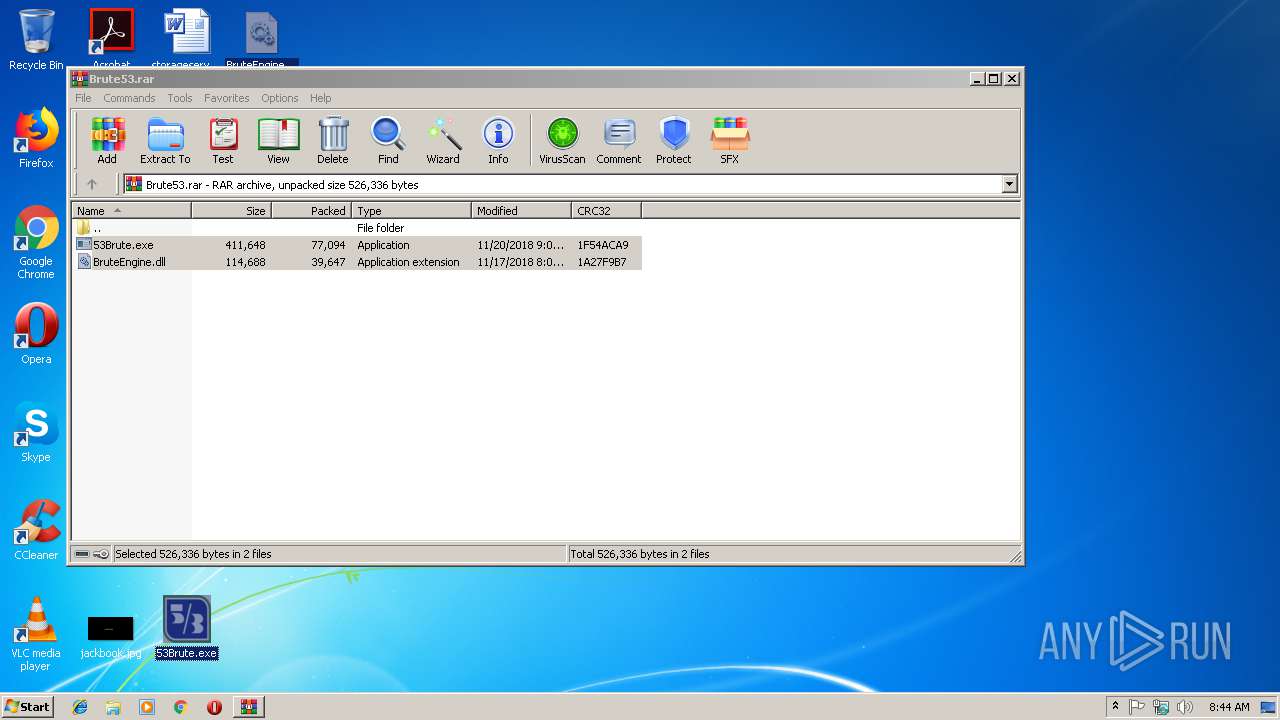
| File name: | Brute53.rar |
| Full analysis: | https://app.any.run/tasks/b6257330-90d1-427a-b74b-c7782dc5592d |
| Verdict: | Malicious activity |
| Analysis date: | December 06, 2018, 08:43:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 2255555BF63FB6A34668EE4D759E9DCD |
| SHA1: | F94D347B5EC4DBB68D9816DE0E7384C878057E30 |
| SHA256: | 995C9C17C515B96081B4404D874922173AC305742807437F8913BB3215D0DAB5 |
| SSDEEP: | 3072:GG39hxHOWdwsc2h/El89SApGn3Sx0JdmjBJ115:b9eivc2zInixe8 |
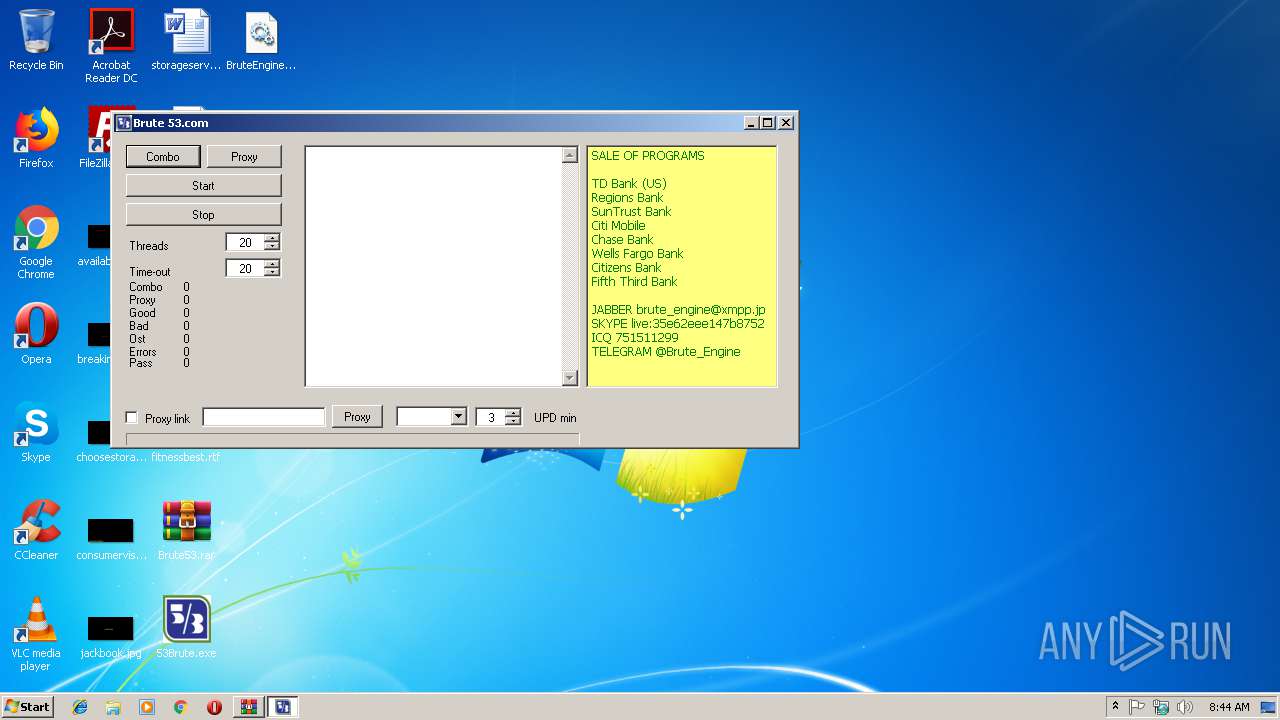
MALICIOUS
Application was dropped or rewritten from another process
- 53Brute.exe (PID: 3488)
Changes the autorun value in the registry
- reg.exe (PID: 2664)
SUSPICIOUS
Creates files in the user directory
- 53Brute.exe (PID: 3488)
- Skype.exe (PID: 3416)
- Skype.exe (PID: 2332)
- Skype.exe (PID: 2100)
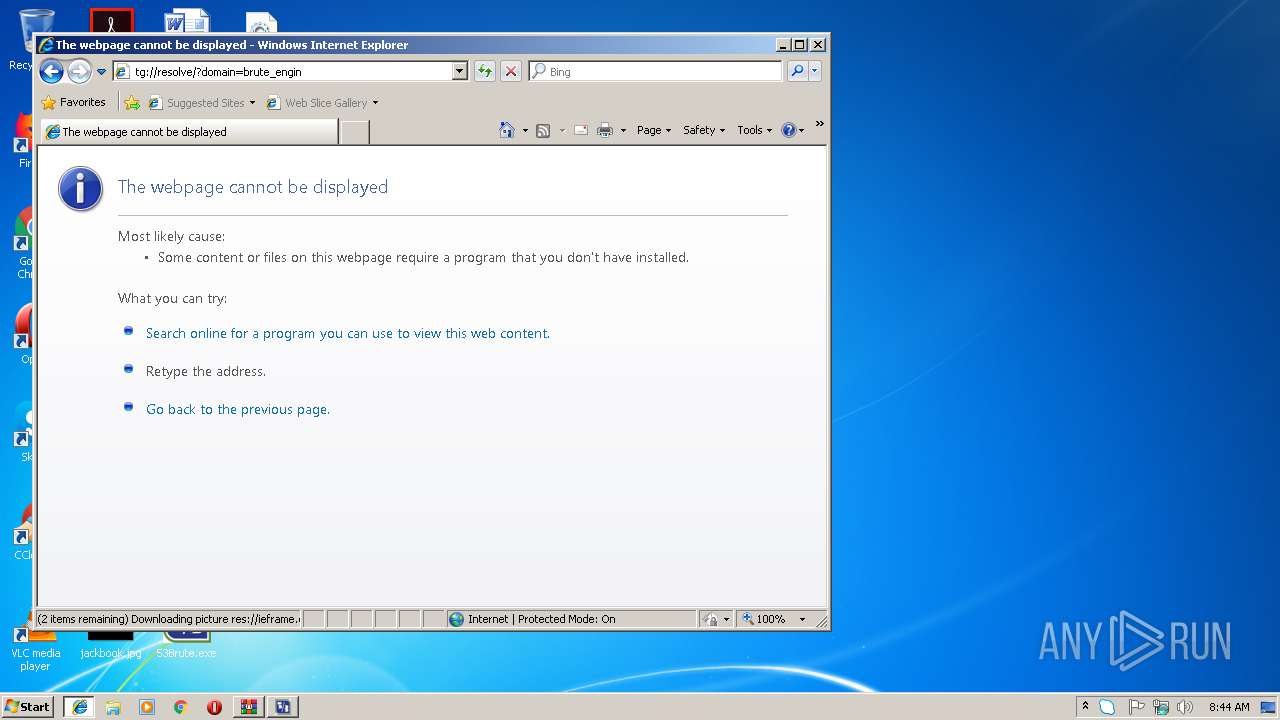
Starts Internet Explorer
- 53Brute.exe (PID: 3488)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3588)
Uses REG.EXE to modify Windows registry
- Skype.exe (PID: 3416)
Reads CPU info
- Skype.exe (PID: 3416)
Modifies the open verb of a shell class
- Skype.exe (PID: 3416)
Application launched itself
- Skype.exe (PID: 2100)
- Skype.exe (PID: 2332)
- Skype.exe (PID: 3416)
INFO
Changes internet zones settings
- iexplore.exe (PID: 3720)
Reads internet explorer settings
- iexplore.exe (PID: 2212)
Reads settings of System Certificates
- Skype.exe (PID: 3416)
Dropped object may contain Bitcoin addresses
- Skype.exe (PID: 3416)
Creates files in the user directory
- iexplore.exe (PID: 2212)
Reads Internet Cache Settings
- iexplore.exe (PID: 2212)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
46
Monitored processes
12
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2100 | "C:\Program Files\Microsoft\Skype for Desktop\Skype.exe" --type=renderer --ms-disable-indexeddb-transaction-timeout --no-sandbox --service-pipe-token=BF97EED422B53FE7A97ECF7E1781CEEA --lang=en-US --app-user-model-id=Microsoft.Skype.SkypeDesktop --app-path="C:\Program Files\Microsoft\Skype for Desktop\resources\app.asar" --node-integration=false --webview-tag=true --no-sandbox --preload="C:\Program Files\Microsoft\Skype for Desktop\resources\app.asar\Preload.js" --context-id=1 --enable-pinch --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --content-image-texture-target=0,0,3553;0,1,3553;0,2,3553;0,3,3553;0,4,3553;0,5,3553;0,6,3553;0,7,3553;0,8,3553;0,9,3553;0,10,3553;0,11,3553;0,12,3553;0,13,3553;0,14,3553;0,15,3553;0,16,3553;0,17,3553;1,0,3553;1,1,3553;1,2,3553;1,3,3553;1,4,3553;1,5,3553;1,6,3553;1,7,3553;1,8,3553;1,9,3553;1,10,3553;1,11,3553;1,12,3553;1,13,3553;1,14,3553;1,15,3553;1,16,3553;1,17,3553;2,0,3553;2,1,3553;2,2,3553;2,3,3553;2,4,3553;2,5,3553;2,6,3553;2,7,3553;2,8,3553;2,9,3553;2,10,3553;2,11,3553;2,12,3553;2,13,3553;2,14,3553;2,15,3553;2,16,3553;2,17,3553;3,0,3553;3,1,3553;3,2,3553;3,3,3553;3,4,3553;3,5,3553;3,6,3553;3,7,3553;3,8,3553;3,9,3553;3,10,3553;3,11,3553;3,12,3553;3,13,3553;3,14,3553;3,15,3553;3,16,3553;3,17,3553;4,0,3553;4,1,3553;4,2,3553;4,3,3553;4,4,3553;4,5,3553;4,6,3553;4,7,3553;4,8,3553;4,9,3553;4,10,3553;4,11,3553;4,12,3553;4,13,3553;4,14,3553;4,15,3553;4,16,3553;4,17,3553 --disable-accelerated-video-decode --disable-gpu-compositing --enable-gpu-async-worker-context --service-request-channel-token=BF97EED422B53FE7A97ECF7E1781CEEA --renderer-client-id=4 --mojo-platform-channel-handle=2640 /prefetch:1 | C:\Program Files\Microsoft\Skype for Desktop\Skype.exe | — | Skype.exe | |||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: MEDIUM Description: Skype Exit code: 0 Version: 8.29.0.50 Modules
| |||||||||||||||
| 2212 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3720 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2332 | "C:\Program Files\Microsoft\Skype for Desktop\Skype.exe" --type=renderer --ms-disable-indexeddb-transaction-timeout --no-sandbox --service-pipe-token=CE58E52EB02A37A9671D123AFE651EA3 --lang=en-US --app-user-model-id=Microsoft.Skype.SkypeDesktop --app-path="C:\Program Files\Microsoft\Skype for Desktop\resources\app.asar" --node-integration=false --webview-tag=true --no-sandbox --preload="C:\Program Files\Microsoft\Skype for Desktop\resources\app.asar\Preload.js" --context-id=2 --enable-pinch --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --content-image-texture-target=0,0,3553;0,1,3553;0,2,3553;0,3,3553;0,4,3553;0,5,3553;0,6,3553;0,7,3553;0,8,3553;0,9,3553;0,10,3553;0,11,3553;0,12,3553;0,13,3553;0,14,3553;0,15,3553;0,16,3553;0,17,3553;1,0,3553;1,1,3553;1,2,3553;1,3,3553;1,4,3553;1,5,3553;1,6,3553;1,7,3553;1,8,3553;1,9,3553;1,10,3553;1,11,3553;1,12,3553;1,13,3553;1,14,3553;1,15,3553;1,16,3553;1,17,3553;2,0,3553;2,1,3553;2,2,3553;2,3,3553;2,4,3553;2,5,3553;2,6,3553;2,7,3553;2,8,3553;2,9,3553;2,10,3553;2,11,3553;2,12,3553;2,13,3553;2,14,3553;2,15,3553;2,16,3553;2,17,3553;3,0,3553;3,1,3553;3,2,3553;3,3,3553;3,4,3553;3,5,3553;3,6,3553;3,7,3553;3,8,3553;3,9,3553;3,10,3553;3,11,3553;3,12,3553;3,13,3553;3,14,3553;3,15,3553;3,16,3553;3,17,3553;4,0,3553;4,1,3553;4,2,3553;4,3,3553;4,4,3553;4,5,3553;4,6,3553;4,7,3553;4,8,3553;4,9,3553;4,10,3553;4,11,3553;4,12,3553;4,13,3553;4,14,3553;4,15,3553;4,16,3553;4,17,3553 --disable-accelerated-video-decode --disable-gpu-compositing --enable-gpu-async-worker-context --service-request-channel-token=CE58E52EB02A37A9671D123AFE651EA3 --renderer-client-id=3 --mojo-platform-channel-handle=1544 /prefetch:1 | C:\Program Files\Microsoft\Skype for Desktop\Skype.exe | — | Skype.exe | |||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: MEDIUM Description: Skype Exit code: 0 Version: 8.29.0.50 Modules
| |||||||||||||||
| 2588 | C:\Windows\system32\reg.exe QUERY HKCU\Software\Microsoft\Skype /v RestartForUpdate | C:\Windows\system32\reg.exe | — | Skype.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2640 | "C:\Program Files\Microsoft\Skype for Desktop\Skype.exe" --reporter-url=https://rink.hockeyapp.net/api/2/apps/a741743329d94bc08826af367733939d/crashes/upload --application-name=skype-preview "--crashes-directory=C:\Users\admin\AppData\Local\Temp\skype-preview Crashes" --v=1 | C:\Program Files\Microsoft\Skype for Desktop\Skype.exe | Skype.exe | ||||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: MEDIUM Description: Skype Exit code: 0 Version: 8.29.0.50 Modules
| |||||||||||||||
| 2664 | C:\Windows\system32\reg.exe ADD HKCU\Software\Microsoft\Windows\CurrentVersion\Run /v "Skype for Desktop" /t REG_SZ /d "C:\Program Files\Microsoft\Skype for Desktop\Skype.exe" /f | C:\Windows\system32\reg.exe | Skype.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2736 | "C:\Program Files\Microsoft\Skype for Desktop\Skype.exe" --reporter-url=https://rink.hockeyapp.net/api/2/apps/a741743329d94bc08826af367733939d/crashes/upload --application-name=skype-preview "--crashes-directory=C:\Users\admin\AppData\Local\Temp\skype-preview Crashes" --v=1 | C:\Program Files\Microsoft\Skype for Desktop\Skype.exe | Skype.exe | ||||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: MEDIUM Description: Skype Exit code: 2 Version: 8.29.0.50 Modules
| |||||||||||||||
| 3272 | "C:\Program Files\Microsoft\Skype for Desktop\Skype.exe" --reporter-url=https://rink.hockeyapp.net/api/2/apps/a741743329d94bc08826af367733939d/crashes/upload --application-name=skype-preview "--crashes-directory=C:\Users\admin\AppData\Local\Temp\skype-preview Crashes" --v=1 | C:\Program Files\Microsoft\Skype for Desktop\Skype.exe | Skype.exe | ||||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: MEDIUM Description: Skype Exit code: 2 Version: 8.29.0.50 Modules
| |||||||||||||||
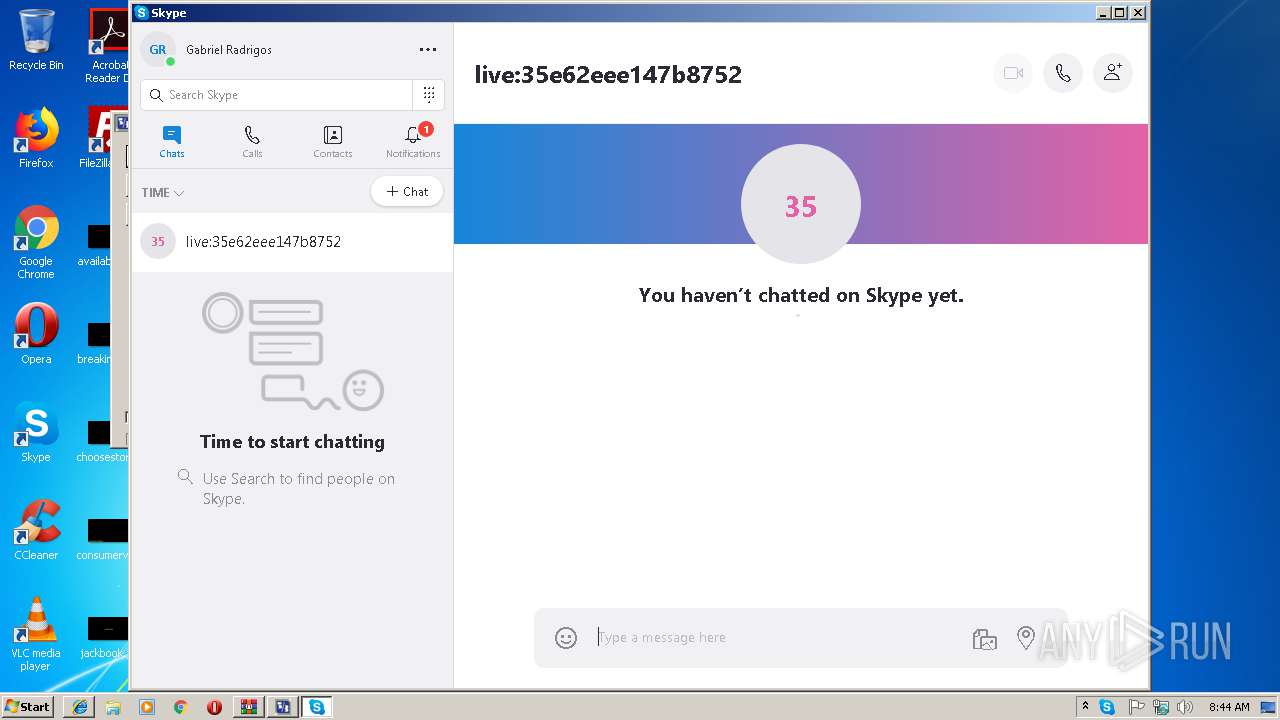
| 3416 | "C:\Program Files\Microsoft\Skype for Desktop\Skype.exe" -- "skype:live:35e62eee147b8752?chat" | C:\Program Files\Microsoft\Skype for Desktop\Skype.exe | 53Brute.exe | ||||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: MEDIUM Description: Skype Exit code: 0 Version: 8.29.0.50 Modules
| |||||||||||||||
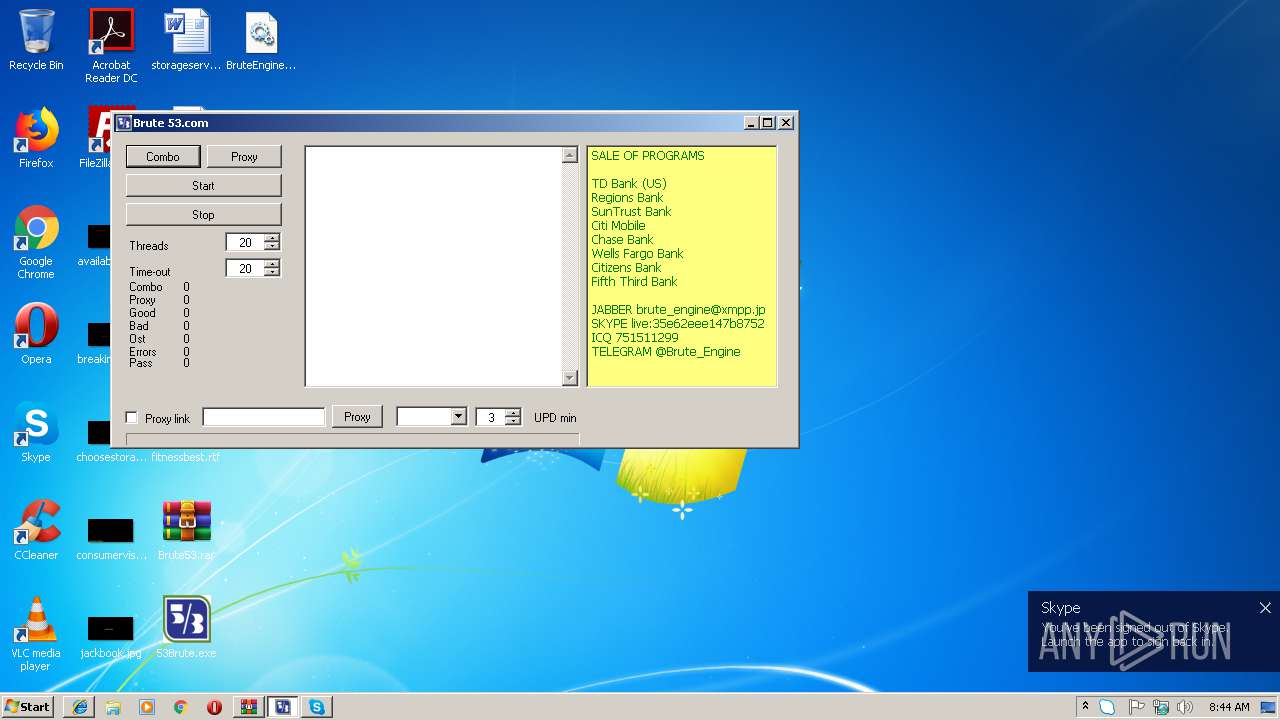
| 3488 | "C:\Users\admin\Desktop\53Brute.exe" | C:\Users\admin\Desktop\53Brute.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: 53.com Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
862
Read events
798
Write events
64
Delete events
0
Modification events
| (PID) Process: | (3588) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3588) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3588) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3588) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Brute53.rar | |||
| (PID) Process: | (3588) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3588) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3588) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3588) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3720) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3720) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
2
Suspicious files
6
Text files
27
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3720 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3720 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2212 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\brute_engin[1].txt | — | |
MD5:— | SHA256:— | |||
| 3416 | Skype.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\SGZBWIGLQMZGMXZRT4HY.temp | — | |
MD5:— | SHA256:— | |||
| 3588 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3588.35293\53Brute.exe | executable | |
MD5:— | SHA256:— | |||
| 3588 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3588.35293\BruteEngine.dll | executable | |
MD5:— | SHA256:— | |||
| 2212 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@t[1].txt | text | |
MD5:— | SHA256:— | |||
| 3416 | Skype.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\b916037c1e115fe0.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 2212 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\brute_engin[1].htm | html | |
MD5:— | SHA256:— | |||
| 3416 | Skype.exe | C:\Users\admin\AppData\Local\Temp\98bb7db7-25d7-4a59-afd1-69697ef158e1.tmp.ico | image | |
MD5:75A3D7765F2F4F8712775B10E1D18003 | SHA256:28854F198091126B6E3A57FE312A3B77C1074CD0B111AED6F7604A2467F52166 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
16
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3720 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3720 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2212 | iexplore.exe | 172.217.168.42:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3416 | Skype.exe | 13.90.95.57:443 | get.skype.com | Microsoft Corporation | US | whitelisted |
3416 | Skype.exe | 23.101.156.198:443 | a.config.skype.com | Microsoft Corporation | US | whitelisted |
2212 | iexplore.exe | 172.217.168.14:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
3416 | Skype.exe | 152.199.19.160:443 | endpoint920510.azureedge.net | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3416 | Skype.exe | 157.55.135.132:443 | login.live.com | Microsoft Corporation | US | whitelisted |
3416 | Skype.exe | 216.58.215.234:443 | www.googleapis.com | Google Inc. | US | whitelisted |
3416 | Skype.exe | 40.79.33.178:443 | avatar.skype.com | Microsoft Corporation | US | whitelisted |
3416 | Skype.exe | 13.107.3.128:443 | config.edge.skype.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
t.me |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
telegram.org |
| whitelisted |
get.skype.com |
| whitelisted |
a.config.skype.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
endpoint920510.azureedge.net |
| whitelisted |
login.live.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Skype.exe | [2640:2628:1206/084418.674:VERBOSE1:crash_service_main.cc(78)] Session start. cmdline is [--reporter-url=https://rink.hockeyapp.net/api/2/apps/a741743329d94bc08826af367733939d/crashes/upload --application-name=skype-preview "--crashes-directory=C:\Users\admin\AppData\Local\Temp\skype-preview Crashes" --v=1]
|
Skype.exe | [2640:2628:1206/084418.674:VERBOSE1:crash_service.cc(145)] window handle is 0001024A
|
Skype.exe | [2640:2628:1206/084418.674:VERBOSE1:crash_service.cc(300)] pipe name is \\.\pipe\skype-preview Crash Service
dumps at C:\Users\admin\AppData\Local\Temp\skype-preview Crashes
|
Skype.exe | [2640:2628:1206/084418.674:VERBOSE1:crash_service.cc(304)] checkpoint is C:\Users\admin\AppData\Local\Temp\skype-preview Crashes\crash_checkpoint.txt
server is https://rink.hockeyapp.net/api/2/apps/a741743329d94bc08826af367733939d/crashes/upload
maximum 128 reports/day
reporter is electron-crash-service
|
Skype.exe | [2640:2628:1206/084418.674:VERBOSE1:crash_service_main.cc(94)] Ready to process crash requests
|
Skype.exe | [2640:2632:1206/084418.674:VERBOSE1:crash_service.cc(333)] client start. pid = 3416
|
Skype.exe | [2640:2632:1206/084420.986:VERBOSE1:crash_service.cc(333)] client start. pid = 2332
|
Skype.exe | [2736:2824:1206/084421.174:VERBOSE1:crash_service_main.cc(78)] Session start. cmdline is [--reporter-url=https://rink.hockeyapp.net/api/2/apps/a741743329d94bc08826af367733939d/crashes/upload --application-name=skype-preview "--crashes-directory=C:\Users\admin\AppData\Local\Temp\skype-preview Crashes" --v=1]
|
Skype.exe | [2736:2824:1206/084421.174:VERBOSE1:crash_service.cc(145)] window handle is 00040278
|
Skype.exe | [2736:2824:1206/084421.174:VERBOSE1:crash_service.cc(300)] pipe name is \\.\pipe\skype-preview Crash Service
dumps at C:\Users\admin\AppData\Local\Temp\skype-preview Crashes
|