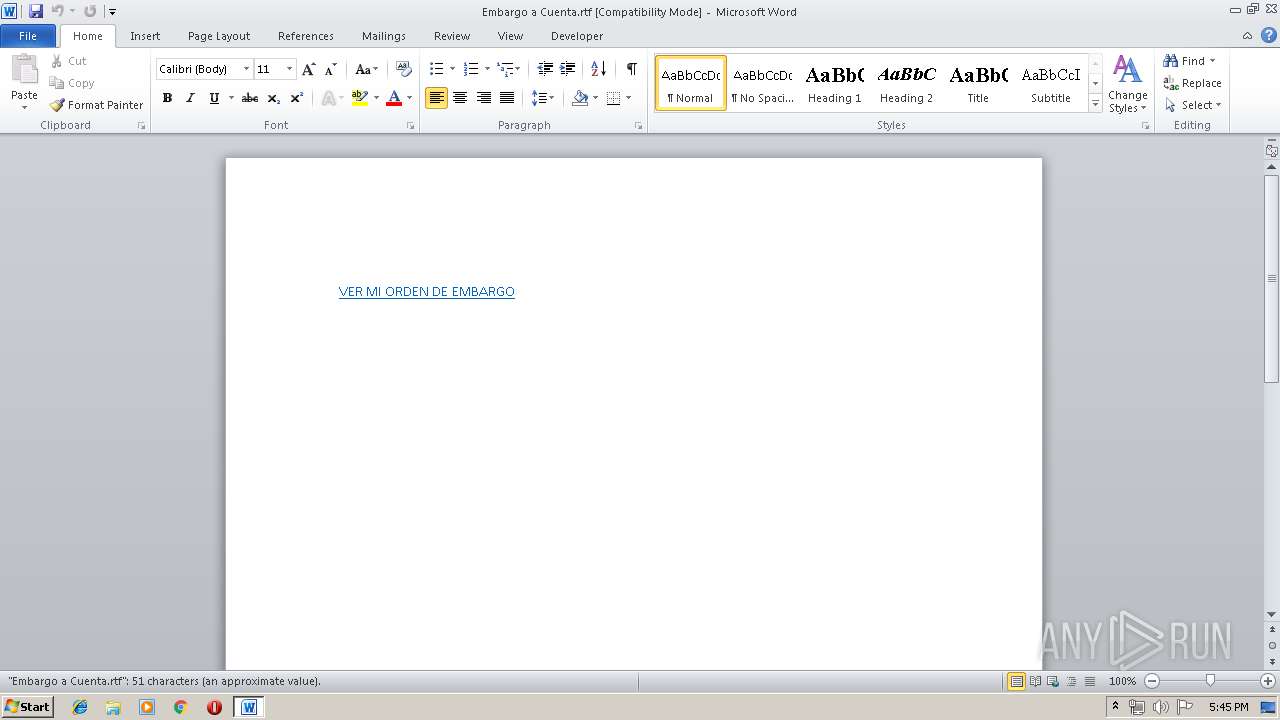
| File name: | Embargo a Cuenta.rtf |
| Full analysis: | https://app.any.run/tasks/348b8e33-9a02-42c9-951f-b9593cc09df6 |
| Verdict: | Malicious activity |
| Analysis date: | June 19, 2019, 16:45:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/rtf |
| File info: | Rich Text Format data, version 1, unknown character set |
| MD5: | D5CB6D49C3F7F4C02D6CCFFF5BCE685D |
| SHA1: | 58275E42F3BBFC03A62BF3124468184A98F50329 |
| SHA256: | 9959968A7CDFA1AC21D5AD45F341E9F25C6EC931A786C3231E851ABE4D5FA138 |
| SSDEEP: | 384:lugKf+2OrN7vQtV6nEFPmi6rGsqWqtZccVF3V7Ly4nMNLoJ0y:lugKfYItbtZVWNLoJ0y |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Internet Cache Settings
- WINWORD.EXE (PID: 2948)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 2948)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2948)
Reads settings of System Certificates
- WINWORD.EXE (PID: 2948)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rtf | | | Rich Text Format (100) |
|---|
EXIF
RTF
| LastModifiedBy: | Centro de Servicios Judiciales |
|---|---|
| CreateDate: | 2019:05:28 22:57:00 |
| ModifyDate: | 2019:06:18 19:44:00 |
| RevisionNumber: | 17 |
| TotalEditTime: | 14 minutes |
| Pages: | 1 |
| Words: | 9 |
| Characters: | 53 |
| CharactersWithSpaces: | 61 |
| InternalVersionNumber: | 105 |
Total processes
33
Monitored processes
1
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2948 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Embargo a Cuenta.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
1 395
Read events
772
Write events
618
Delete events
5
Modification events
| (PID) Process: | (2948) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | q'= |
Value: 71273D00840B0000010000000000000000000000 | |||
| (PID) Process: | (2948) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2948) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2948) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1322450974 | |||
| (PID) Process: | (2948) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1322451088 | |||
| (PID) Process: | (2948) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1322451089 | |||
| (PID) Process: | (2948) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 840B000050975E76BE26D50100000000 | |||
| (PID) Process: | (2948) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | k(= |
Value: 6B283D00840B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2948) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | k(= |
Value: 6B283D00840B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2948) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
0
Suspicious files
0
Text files
1
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2948 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR1351.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2948 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\admin@mediafire[1].txt | — | |
MD5:— | SHA256:— | |||
| 2948 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$bargo a Cuenta.rtf | pgc | |
MD5:— | SHA256:— | |||
| 2948 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2948 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\admin@mediafire[2].txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
3
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2948 | WINWORD.EXE | GET | 301 | 91.216.63.240:80 | http://cort.as/-JtpO | ES | html | 280 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2948 | WINWORD.EXE | 91.216.63.240:80 | cort.as | Ediciones El Pais, S.L. | ES | unknown |
2948 | WINWORD.EXE | 104.19.194.29:443 | www.mediafire.com | Cloudflare Inc | US | shared |
2948 | WINWORD.EXE | 205.196.122.218:443 | download1277.mediafire.com | MediaFire, LLC | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cort.as |
| unknown |
www.mediafire.com |
| shared |
download1277.mediafire.com |
| malicious |