| File name: | storage.scr |
| Full analysis: | https://app.any.run/tasks/c20f958a-2230-4889-96b7-68bd1eb57c3b |
| Verdict: | Malicious activity |
| Analysis date: | July 11, 2019, 18:19:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 4A3D629A649B025576AA9F7D701BCD77 |
| SHA1: | 8DD19B4EA306EC0B3A0EC7C3249C1E36E49DBCBE |
| SHA256: | 995046C286B75FCF0D63610CFED339BF77015ABBAAB9B8C29F3B67860E6B832C |
| SSDEEP: | 6144:E1QMivgpQ25+yApTCg3cz6ufWeLuIrybTQg9o214QTB2I/51pftDKHpDbU69SWvG:0QMiG+2gef5x/xQTB2OfDKC7Wgca |
MALICIOUS
Changes the autorun value in the registry
- gegcazmfdfb.exe (PID: 2796)
- ccors.exe (PID: 2876)
- ccors.exe (PID: 1940)
UAC/LUA settings modification
- gegcazmfdfb.exe (PID: 2796)
- ccors.exe (PID: 2876)
- ccors.exe (PID: 1940)
Changes the login/logoff helper path in the registry
- gegcazmfdfb.exe (PID: 2796)
- ccors.exe (PID: 2876)
- ccors.exe (PID: 1940)
Application was dropped or rewritten from another process
- gegcazmfdfb.exe (PID: 2796)
- ccors.exe (PID: 2876)
- ccors.exe (PID: 1940)
Disables registry editing tools (regedit)
- gegcazmfdfb.exe (PID: 2796)
- ccors.exe (PID: 2876)
- ccors.exe (PID: 1940)
Changes appearance of the explorer extensions
- gegcazmfdfb.exe (PID: 2796)
- ccors.exe (PID: 2876)
- ccors.exe (PID: 1940)
SUSPICIOUS
Executable content was dropped or overwritten
- gegcazmfdfb.exe (PID: 2796)
- storage.scr (PID: 3712)
Creates files in the program directory
- ccors.exe (PID: 2876)
INFO
Dropped object may contain Bitcoin addresses
- gegcazmfdfb.exe (PID: 2796)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2008:12:07 08:53:27+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 7.1 |
| CodeSize: | 20480 |
| InitializedDataSize: | 446464 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2095 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 07-Dec-2008 07:53:27 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000F8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 07-Dec-2008 07:53:27 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00004C2E | 0x00005000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.43598 |
.rdata | 0x00006000 | 0x0000138A | 0x00002000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 3.35663 |
.data | 0x00008000 | 0x00064938 | 0x00065000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.02347 |
.rsrc | 0x0006D000 | 0x00005110 | 0x00006000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.31833 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 2.099 | 744 | Latin 1 / Western European | English - United States | RT_ICON |
2 | 4.27442 | 2216 | Latin 1 / Western European | English - United States | RT_ICON |
3 | 2.48765 | 296 | Latin 1 / Western European | English - United States | RT_ICON |
4 | 3.84177 | 1384 | Latin 1 / Western European | English - United States | RT_ICON |
5 | 2.76167 | 1640 | Latin 1 / Western European | English - United States | RT_ICON |
6 | 3.44345 | 1384 | Latin 1 / Western European | English - United States | RT_ICON |
7 | 3.47976 | 2216 | Latin 1 / Western European | English - United States | RT_ICON |
8 | 3.42089 | 3752 | Latin 1 / Western European | English - United States | RT_ICON |
9 | 2.41449 | 296 | Latin 1 / Western European | English - United States | RT_ICON |
10 | 2.64576 | 62 | Latin 1 / Western European | English - United States | RT_GROUP_ICON |
Imports
KERNEL32.dll |
SHELL32.dll |
Total processes
43
Monitored processes
6
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
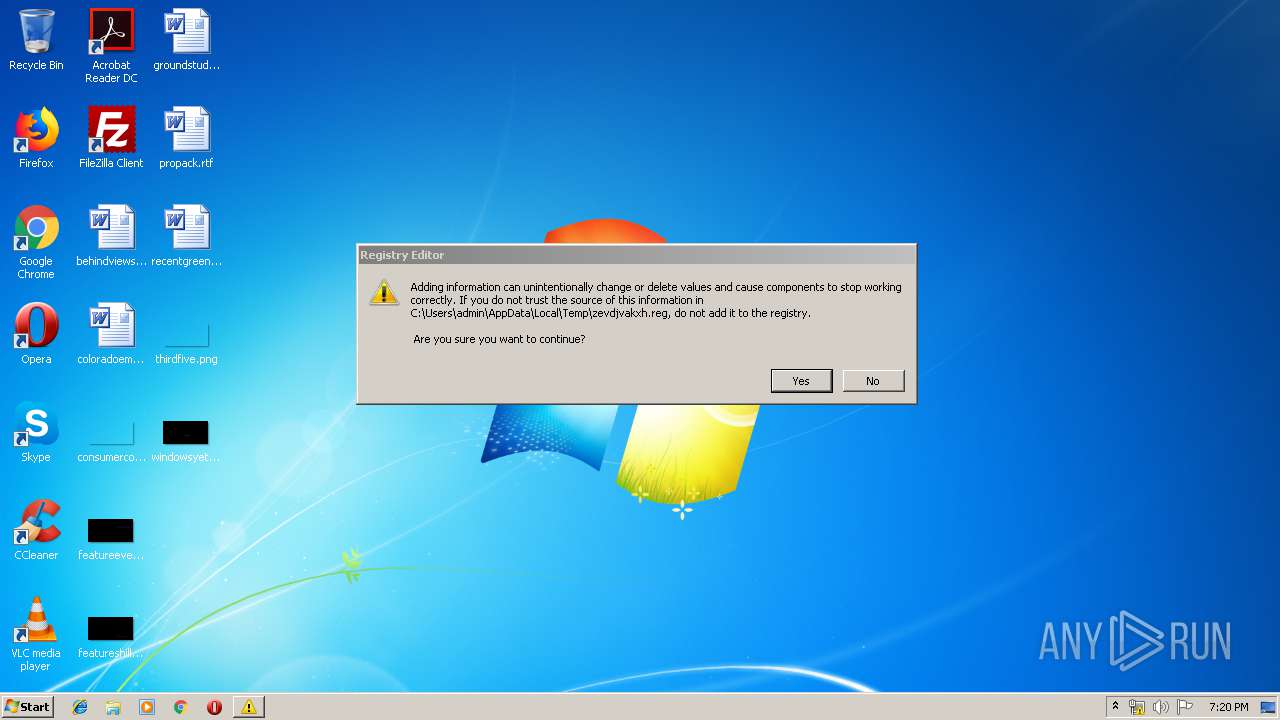
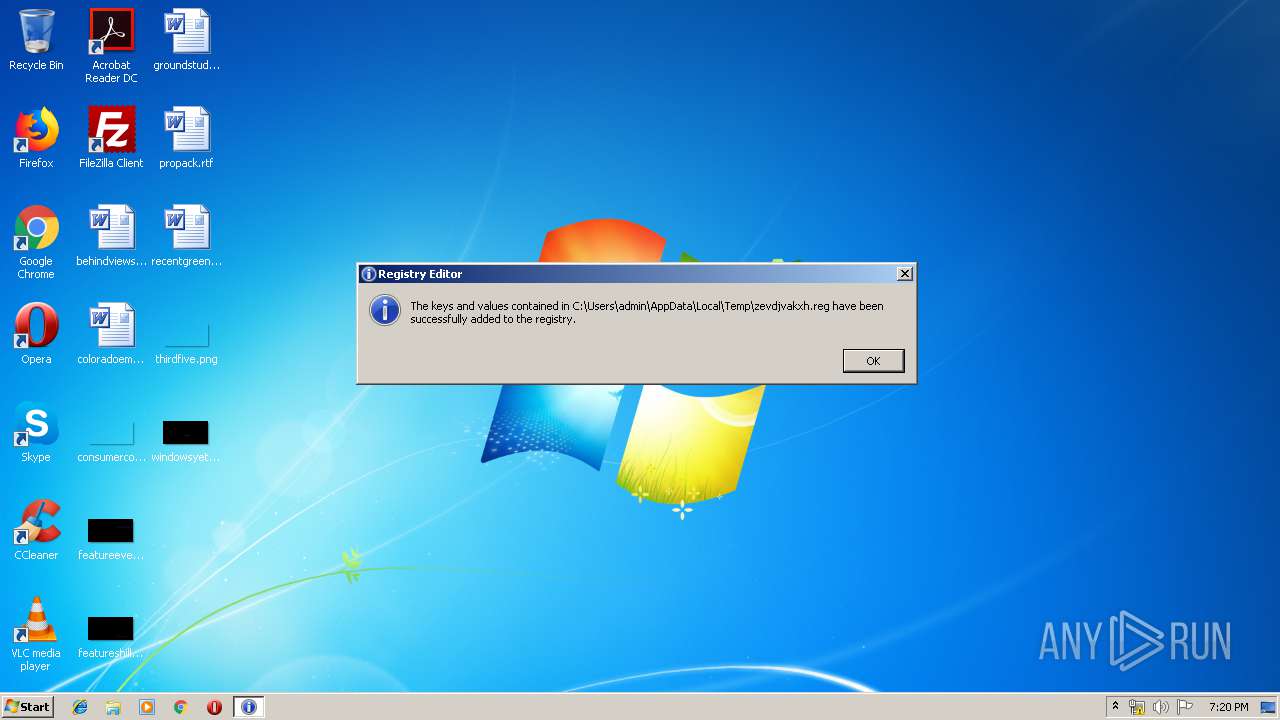
| 1916 | "regedit.exe" "C:\Users\admin\AppData\Local\Temp\zevdjvakxh.reg" | C:\Windows\regedit.exe | — | ccors.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Editor Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1940 | "C:\Users\admin\AppData\Local\Temp\ccors.exe" "-C:\Users\admin\AppData\Local\Temp\zkhvhzkatjpszadh.exe" | C:\Users\admin\AppData\Local\Temp\ccors.exe | gegcazmfdfb.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2796 | "C:\Users\admin\AppData\Local\Temp\gegcazmfdfb.exe" "c:\users\admin\appdata\local\temp\storage.scr*/S" | C:\Users\admin\AppData\Local\Temp\gegcazmfdfb.exe | storage.scr | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2876 | "C:\Users\admin\AppData\Local\Temp\ccors.exe" "-C:\Users\admin\AppData\Local\Temp\zkhvhzkatjpszadh.exe" | C:\Users\admin\AppData\Local\Temp\ccors.exe | gegcazmfdfb.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3036 | "regedit.exe" "C:\Users\admin\AppData\Local\Temp\zevdjvakxh.reg" | C:\Windows\regedit.exe | ccors.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Editor Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3712 | "C:\Users\admin\AppData\Local\Temp\storage.scr" /S | C:\Users\admin\AppData\Local\Temp\storage.scr | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
1 186
Read events
1 064
Write events
122
Delete events
0
Modification events
| (PID) Process: | (3712) storage.scr | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3712) storage.scr | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2796) gegcazmfdfb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | EnableLUA |
Value: 0 | |||
| (PID) Process: | (2796) gegcazmfdfb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon |
| Operation: | write | Name: | Shell |
Value: Explorer.exe | |||
| (PID) Process: | (2796) gegcazmfdfb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | acqvyhj |
Value: gsqfslxoizgksuydw.exe | |||
| (PID) Process: | (2796) gegcazmfdfb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | pshnrbem |
Value: ncdvlhwqnhryjovdzpef.exe . | |||
| (PID) Process: | (2796) gegcazmfdfb.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | zevdjvakxh |
Value: gsqfslxoizgksuydw.exe | |||
| (PID) Process: | (2796) gegcazmfdfb.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | uasbivbmalm |
Value: zkhvhzkatjpszadh.exe . | |||
| (PID) Process: | (2796) gegcazmfdfb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | qysdmbjwmzccg |
Value: C:\Users\admin\AppData\Local\Temp\csunebrmkfqykqyhevlng.exe | |||
| (PID) Process: | (2796) gegcazmfdfb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | ryrbjxeqfrts |
Value: C:\Users\admin\AppData\Local\Temp\aoofupdwsluakoubwlz.exe . | |||
Executable files
10
Suspicious files
6
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2796 | gegcazmfdfb.exe | C:\Users\admin\AppData\Local\Temp\gsqfslxoizgksuydw.exe | executable | |
MD5:— | SHA256:— | |||
| 2796 | gegcazmfdfb.exe | C:\Users\admin\AppData\Local\Temp\pcbrfzmezrzenqvbvj.exe | executable | |
MD5:— | SHA256:— | |||
| 2796 | gegcazmfdfb.exe | C:\Users\admin\AppData\Local\Temp\ncdvlhwqnhryjovdzpef.exe | executable | |
MD5:— | SHA256:— | |||
| 3712 | storage.scr | C:\Users\admin\AppData\Local\Temp\gegcazmfdfb.exe | executable | |
MD5:304415DF6AD55A90301AA8158E5E3582 | SHA256:34A5F9E2B494B086ABAD2721019BE271FA43350C9146F000E50FE554F170743D | |||
| 2796 | gegcazmfdfb.exe | C:\Users\admin\AppData\Local\Temp\aoofupdwsluakoubwlz.exe | executable | |
MD5:— | SHA256:— | |||
| 2876 | ccors.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\mkuvuzxagjcsmaqhmljtutywz.ibr | binary | |
MD5:— | SHA256:— | |||
| 2796 | gegcazmfdfb.exe | C:\Users\admin\AppData\Local\Temp\zkhvhzkatjpszadh.exe | executable | |
MD5:— | SHA256:— | |||
| 2796 | gegcazmfdfb.exe | C:\Users\admin\AppData\Local\Temp\tknhzxokjfranudnlduxrj.exe | executable | |
MD5:— | SHA256:— | |||
| 2796 | gegcazmfdfb.exe | C:\Users\admin\AppData\Local\Temp\csunebrmkfqykqyhevlng.exe | executable | |
MD5:— | SHA256:— | |||
| 2876 | ccors.exe | C:\Users\admin\AppData\Local\VirtualStore\Windows\System32\mkuvuzxagjcsmaqhmljtutywz.ibr | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report