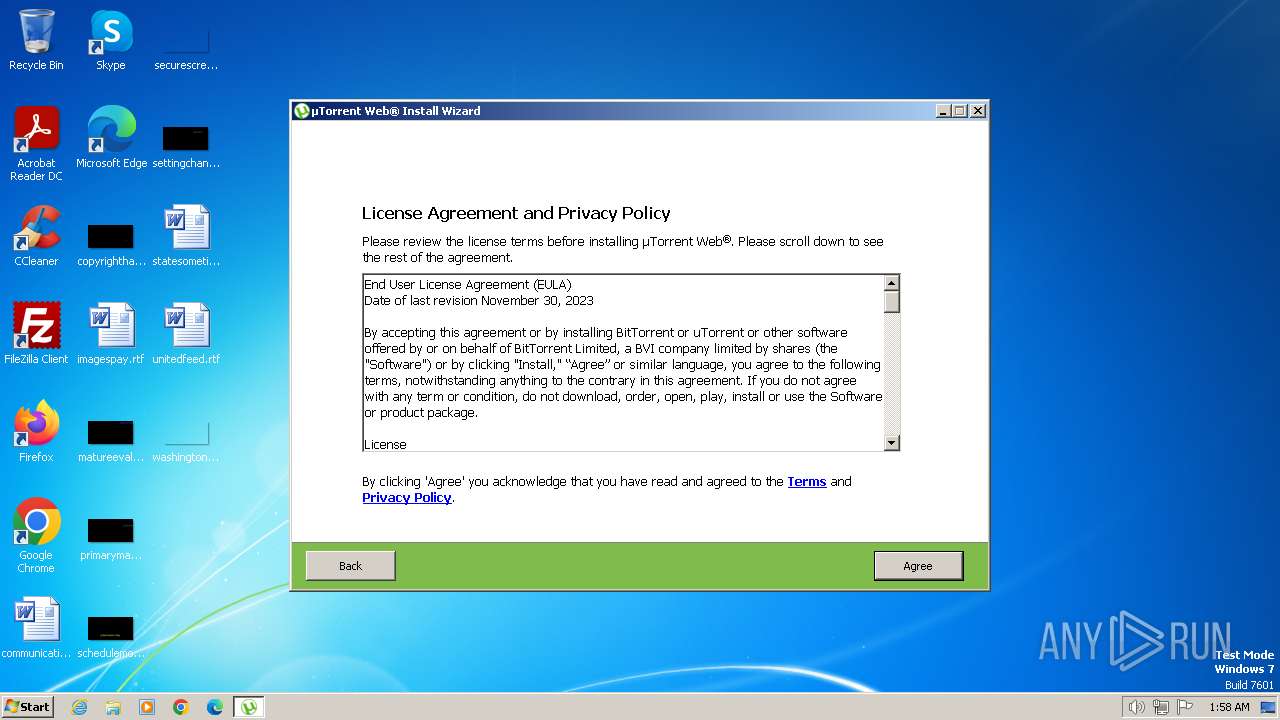
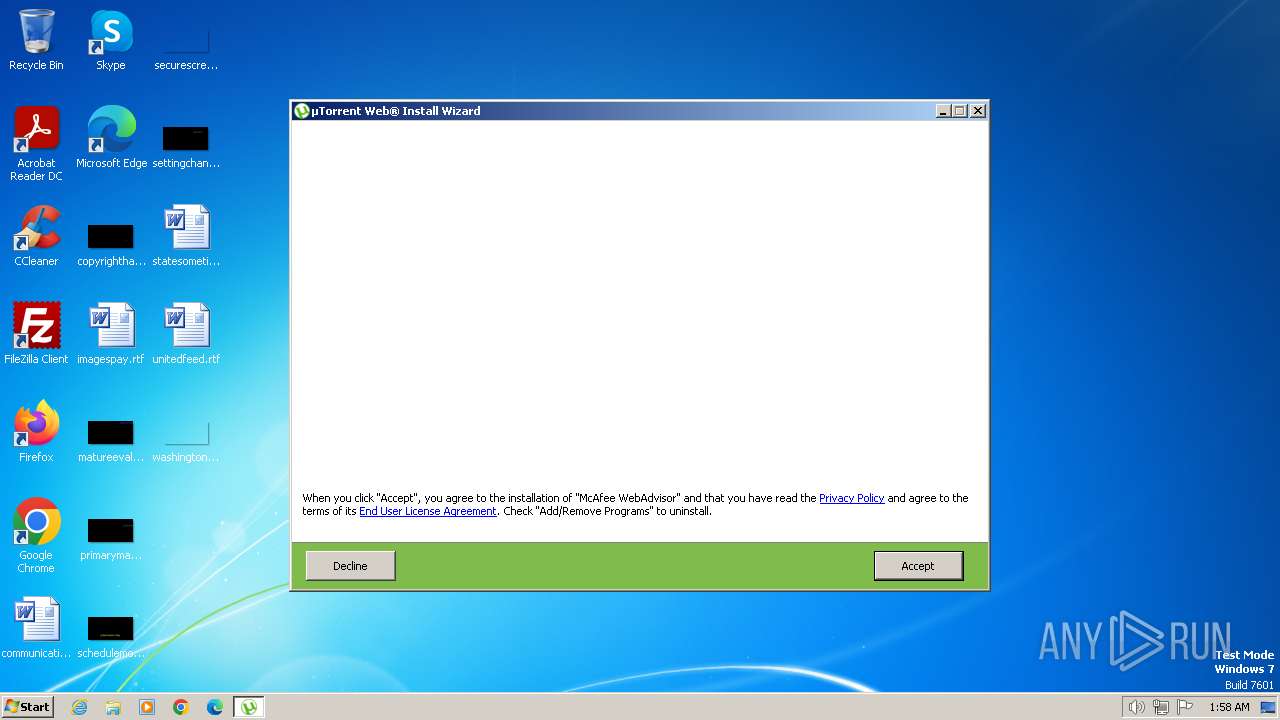
| File name: | utweb_installer.exe |
| Full analysis: | https://app.any.run/tasks/7c5e9a2a-6aa7-437d-9521-f5e9d4f5a382 |
| Verdict: | Malicious activity |
| Analysis date: | January 16, 2024, 01:57:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 5FE965E0F7AD4C851F49895C82380F2C |
| SHA1: | EA262BB1CC2AFF5D3D04DB9BB45CFE68A85CD2C8 |
| SHA256: | 99439443EE155CE812460C1026C67CF2B308A4154826428A36F007B1625B2CCB |
| SSDEEP: | 49152:77HecD4dnbibBlfYoJebw9FhFVt+LC4J65hP2fHIG+MZl3+aDM9+bwlE2RvtbW4J:H+cD4dnBJbw9FvN4wPPUrOaO+b0JRtW8 |
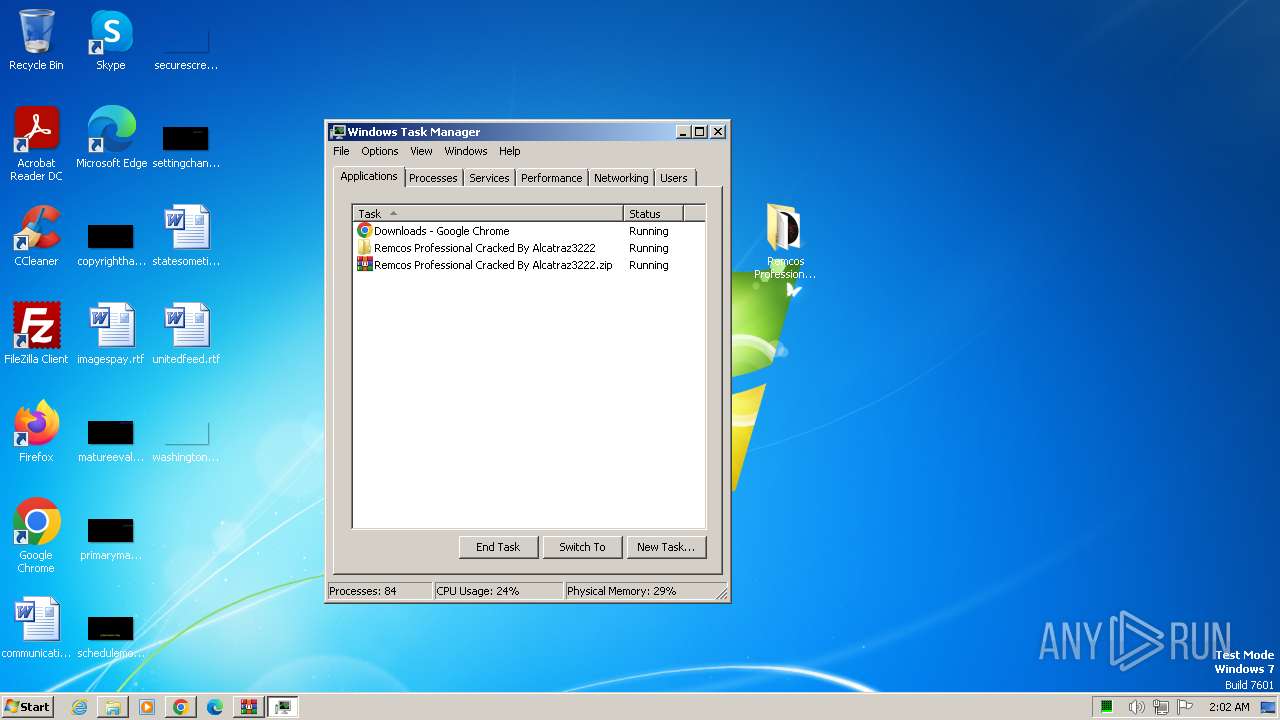
MALICIOUS
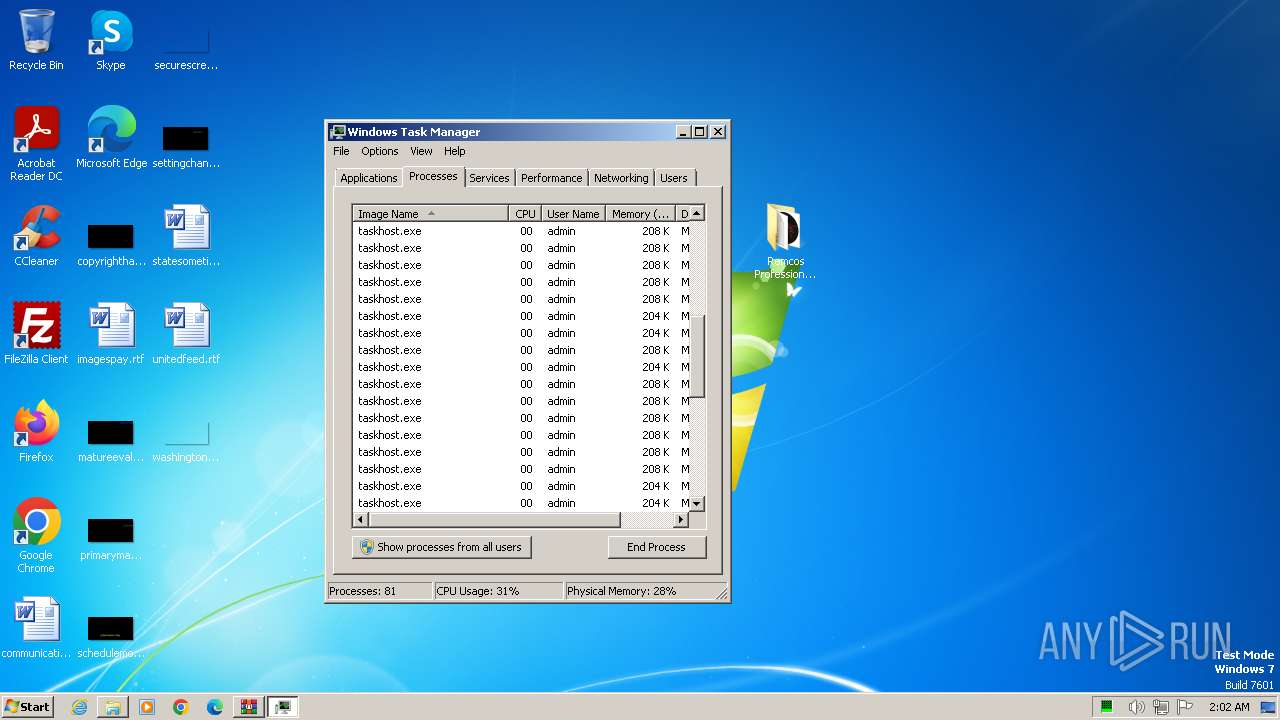
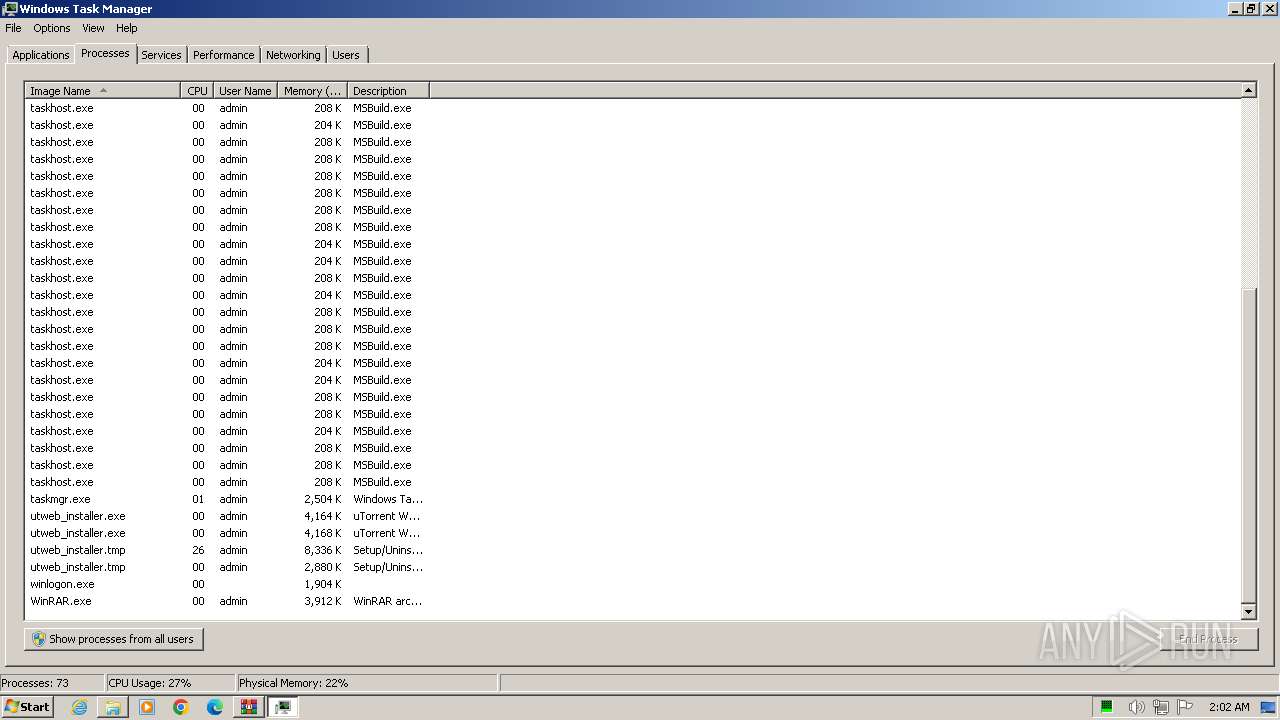
Drops the executable file immediately after the start
- utweb_installer.exe (PID: 128)
- utweb_installer.exe (PID: 492)
- utweb_installer.tmp (PID: 268)
- cmd.exe (PID: 3636)
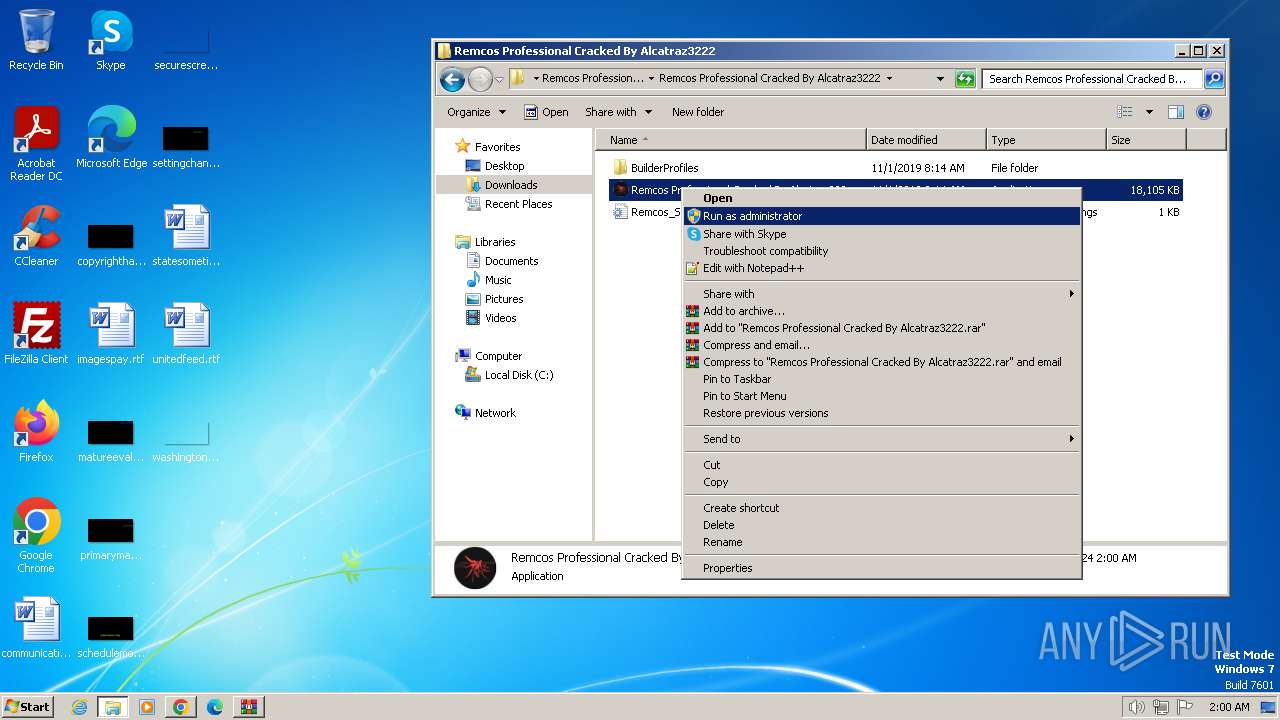
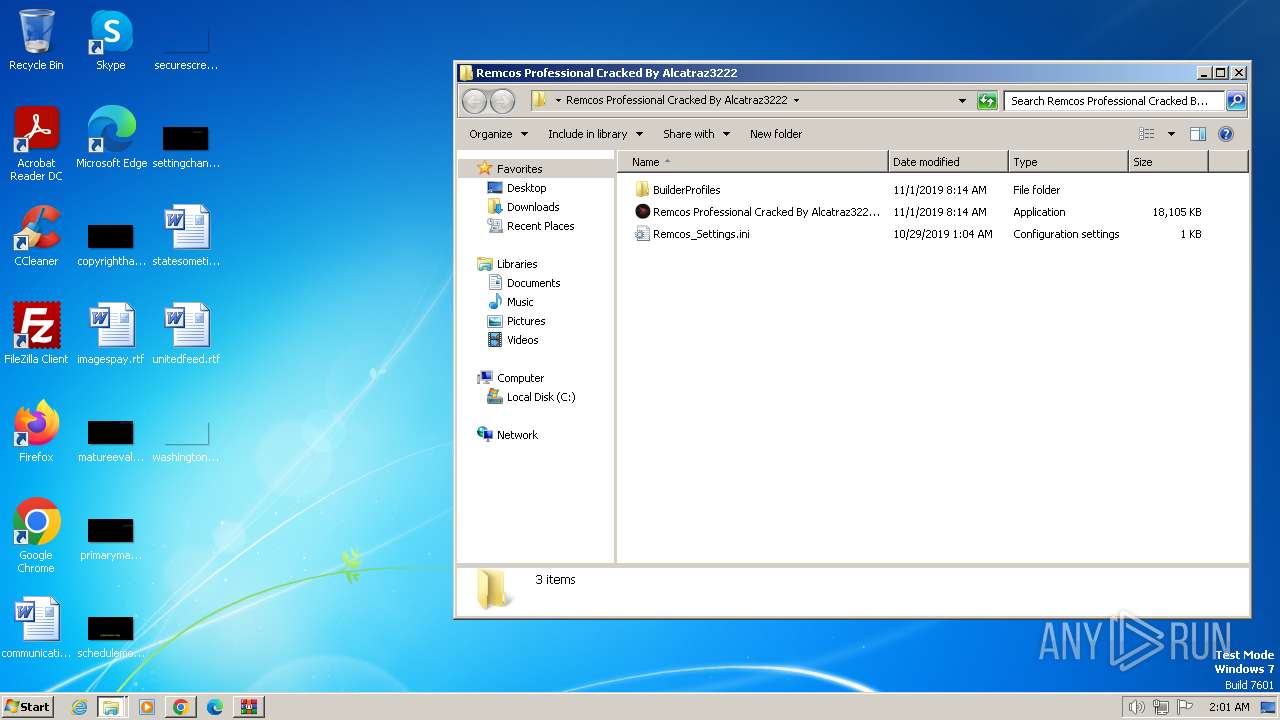
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 124)
SUSPICIOUS
Executable content was dropped or overwritten
- utweb_installer.exe (PID: 128)
- utweb_installer.exe (PID: 492)
- utweb_installer.tmp (PID: 268)
- cmd.exe (PID: 3636)
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 124)
Reads settings of System Certificates
- utweb_installer.tmp (PID: 268)
Reads the Windows owner or organization settings
- utweb_installer.tmp (PID: 268)
Reads the Internet Settings
- utweb_installer.tmp (PID: 268)
- saBSI.exe (PID: 3060)
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 124)
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 3956)
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 1548)
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 2356)
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 3644)
Checks Windows Trust Settings
- saBSI.exe (PID: 3060)
Reads security settings of Internet Explorer
- saBSI.exe (PID: 3060)
The process creates files with name similar to system file names
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 124)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 1652)
- cmd.exe (PID: 3444)
- cmd.exe (PID: 924)
- cmd.exe (PID: 3688)
- cmd.exe (PID: 2912)
Process drops legitimate windows executable
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 124)
Starts CMD.EXE for commands execution
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 3956)
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 1548)
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 2356)
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 3644)
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 124)
INFO
Checks supported languages
- utweb_installer.exe (PID: 128)
- utweb_installer.tmp (PID: 1776)
- utweb_installer.exe (PID: 492)
- utweb_installer.tmp (PID: 268)
- saBSI.exe (PID: 3060)
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 124)
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 3956)
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 1548)
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 2356)
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 3644)
Create files in a temporary directory
- utweb_installer.exe (PID: 128)
- utweb_installer.exe (PID: 492)
- utweb_installer.tmp (PID: 268)
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 124)
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 3956)
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 1548)
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 2356)
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 3644)
Reads the computer name
- utweb_installer.tmp (PID: 1776)
- utweb_installer.tmp (PID: 268)
- saBSI.exe (PID: 3060)
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 124)
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 3956)
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 1548)
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 2356)
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 3644)
Reads the machine GUID from the registry
- utweb_installer.tmp (PID: 268)
- saBSI.exe (PID: 3060)
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 124)
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 3956)
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 1548)
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 2356)
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 3644)
Creates files in the program directory
- saBSI.exe (PID: 3060)
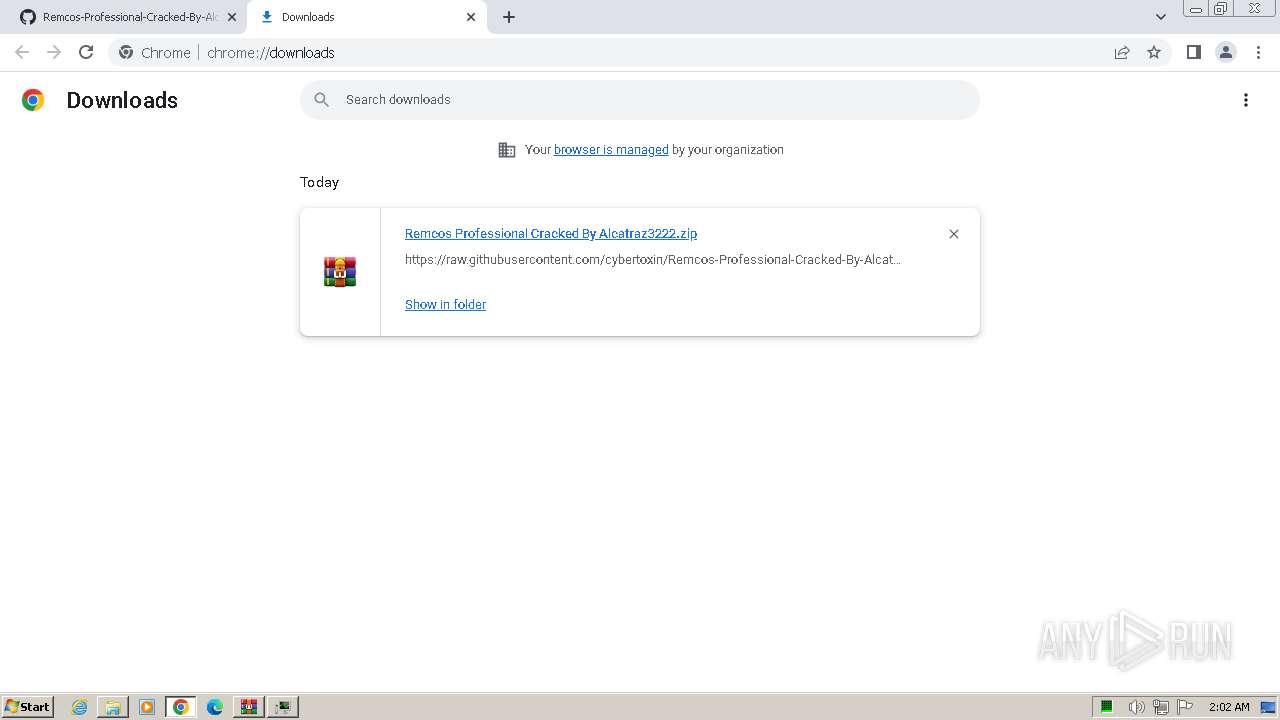
The process uses the downloaded file
- WinRAR.exe (PID: 3852)
- chrome.exe (PID: 3652)
- WinRAR.exe (PID: 2560)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3852)
- WinRAR.exe (PID: 2560)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3852)
- WinRAR.exe (PID: 2560)
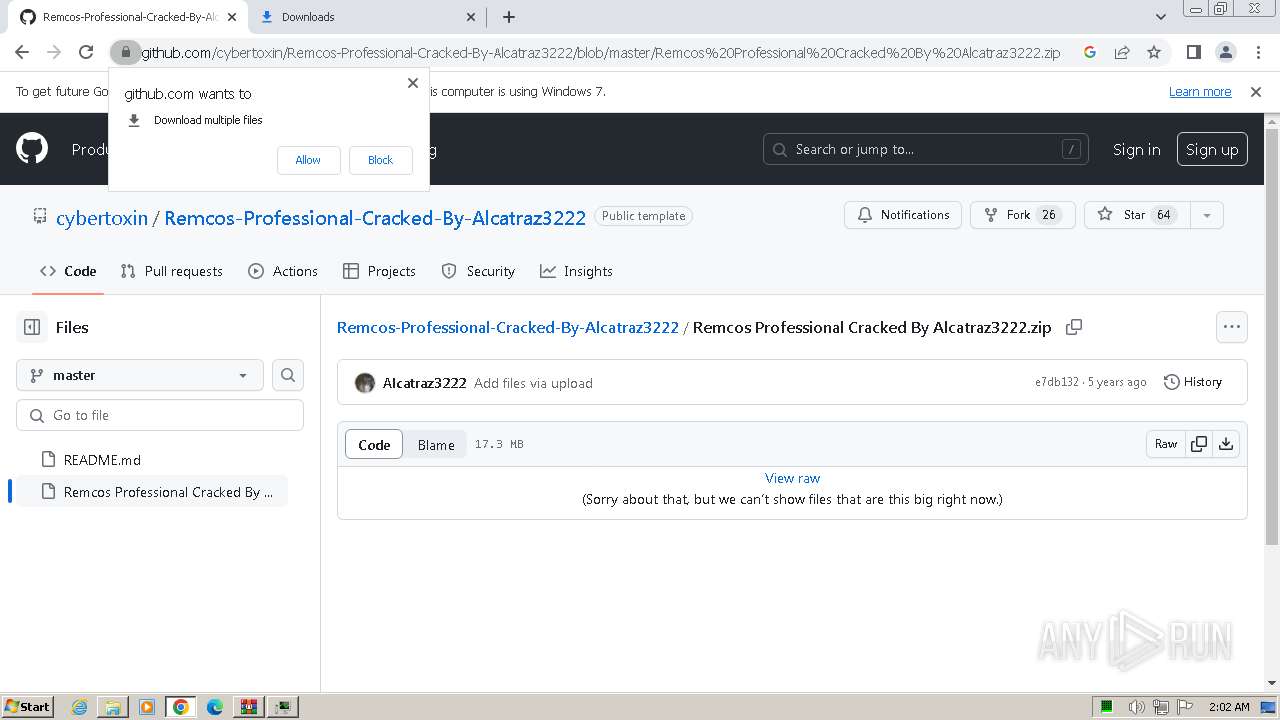
Manual execution by a user
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 124)
- chrome.exe (PID: 1588)
- WinRAR.exe (PID: 2560)
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 3956)
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 1548)
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 2356)
- Remcos Professional Cracked By Alcatraz3222.exe (PID: 3644)
- WINWORD.EXE (PID: 2856)
- taskmgr.exe (PID: 1428)
Application launched itself
- chrome.exe (PID: 1588)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (65.1) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (24.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (3.9) |
| .exe | | | Win32 Executable (generic) (2.6) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:04:14 18:10:23+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741888 |
| InitializedDataSize: | 77824 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.4.0.0 |
| ProductVersionNumber: | 1.4.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | |
| FileDescription: | uTorrеnt Web® |
| FileVersion: | 1.4 |
| LegalCopyright: | ©2022 RainBerry Inc. All Rights Reserved |
| OriginalFileName: | |
| ProductName: | uTorrеnt Web® |
| ProductVersion: | 1.4 |
Total processes
155
Monitored processes
89
Malicious processes
3
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Users\admin\Desktop\Remcos Professional Cracked By Alcatraz3222\Remcos Professional Cracked By Alcatraz3222.exe" | C:\Users\admin\Desktop\Remcos Professional Cracked By Alcatraz3222\Remcos Professional Cracked By Alcatraz3222.exe | explorer.exe | ||||||||||||
User: admin Company: Breaking-Security.net Integrity Level: MEDIUM Description: REMCOS Remote Control & Surveillance Exit code: 0 Version: 2.2.0.0 Modules
| |||||||||||||||
| 128 | "C:\Users\admin\AppData\Local\Temp\utweb_installer.exe" | C:\Users\admin\AppData\Local\Temp\utweb_installer.exe | explorer.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: uTorrеnt Web® Exit code: 0 Version: 1.4 Modules
| |||||||||||||||
| 268 | "C:\Users\admin\AppData\Local\Temp\is-IO45J.tmp\utweb_installer.tmp" /SL5="$501AC,866439,820736,C:\Users\admin\AppData\Local\Temp\utweb_installer.exe" /SPAWNWND=$401A6 /NOTIFYWND=$301AA | C:\Users\admin\AppData\Local\Temp\is-IO45J.tmp\utweb_installer.tmp | utweb_installer.exe | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 492 | "C:\Users\admin\AppData\Local\Temp\utweb_installer.exe" /SPAWNWND=$401A6 /NOTIFYWND=$301AA | C:\Users\admin\AppData\Local\Temp\utweb_installer.exe | utweb_installer.tmp | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: uTorrеnt Web® Exit code: 0 Version: 1.4 Modules
| |||||||||||||||
| 552 | "C:\Users\admin\AppData\Local\Temp\taskhost.exe" | C:\Users\admin\AppData\Local\Temp\taskhost.exe | — | Remcos Professional Cracked By Alcatraz3222.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 | |||||||||||||||
| 560 | "C:\Windows\System32\cmd.exe" /c echo [zoneTransfer]ZoneID = 2 > %temp%\Profile Remcos\Update_Lock_Remcos.exe:Zone.Identifier | C:\Windows\System32\cmd.exe | — | Remcos Professional Cracked By Alcatraz3222.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 712 | "C:\Users\admin\AppData\Local\Temp\taskhost.exe" | C:\Users\admin\AppData\Local\Temp\taskhost.exe | — | Remcos Professional Cracked By Alcatraz3222.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: MSBuild.exe Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 | |||||||||||||||
| 848 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=1336 --field-trial-handle=1176,i,2994741738809068738,6784409893746566,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 884 | "C:\Users\admin\AppData\Local\Temp\taskhost.exe" | C:\Users\admin\AppData\Local\Temp\taskhost.exe | — | Remcos Professional Cracked By Alcatraz3222.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 | |||||||||||||||
| 924 | "C:\Windows\System32\cmd.exe" /c reg add "HKCU\Software\Microsoft\Windows NT\CurrentVersion\Windows" /v Load /t REG_SZ /d "%temp%\Profile Remcos\Update_Lock_Remcos.exe.lnk" /f | C:\Windows\System32\cmd.exe | — | Remcos Professional Cracked By Alcatraz3222.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
16 439
Read events
16 103
Write events
192
Delete events
144
Modification events
| (PID) Process: | (268) utweb_installer.tmp | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1588) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1588) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1588) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (1588) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1588) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (1588) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 1 | |||
| (PID) Process: | (1588) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (1588) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (1588) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_installdate |
Value: 0 | |||
Executable files
11
Suspicious files
270
Text files
45
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1588 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RFe3729.TMP | — | |
MD5:— | SHA256:— | |||
| 1588 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 268 | utweb_installer.tmp | C:\Users\admin\AppData\Local\Temp\is-R9VMI.tmp\is-MHPR2.tmp | image | |
MD5:4CFFF8DC30D353CD3D215FD3A5DBAC24 | SHA256:0C430E56D69435D8AB31CBB5916A73A47D11EF65B37D289EE7D11130ADF25856 | |||
| 268 | utweb_installer.tmp | C:\Users\admin\AppData\Local\Temp\is-R9VMI.tmp\license.rtf | text | |
MD5:8A708BF775DE14E5FBB16F6077B454D5 | SHA256:ECA753676C5C71D7BE141451CD6D1426A08ED5C254078BC585D9BA91395A971A | |||
| 1588 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C016064A1F864C8140915D77CF3389A | SHA256:0E7265D4A8C16223538EDD8CD620B8820611C74538E420A88E333BE7F62AC787 | |||
| 268 | utweb_installer.tmp | C:\Users\admin\AppData\Local\Temp\is-R9VMI.tmp\WebAdvisor.png | image | |
MD5:4CFFF8DC30D353CD3D215FD3A5DBAC24 | SHA256:0C430E56D69435D8AB31CBB5916A73A47D11EF65B37D289EE7D11130ADF25856 | |||
| 492 | utweb_installer.exe | C:\Users\admin\AppData\Local\Temp\is-IO45J.tmp\utweb_installer.tmp | executable | |
MD5:0E033710D2433116341588B8F3A2E748 | SHA256:E0565DE2D030A8159BD3A518F367ACAA180F42A48B2233B4664459F4EC0587B3 | |||
| 1588 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:9F941EA08DBDCA2EB3CFA1DBBBA6F5DC | SHA256:127F71DF0D2AD895D4F293E62284D85971AE047CA15F90B87BF6335898B0B655 | |||
| 1588 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Variations | binary | |
MD5:961E3604F228B0D10541EBF921500C86 | SHA256:F7B24F2EB3D5EB0550527490395D2F61C3D2FE74BB9CB345197DAD81B58B5FED | |||
| 1588 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RFe3a17.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
73
DNS requests
74
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
856 | svchost.exe | GET | — | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | — | — | unknown |
856 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | — | — | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 6.05 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 10.9 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 10.9 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 10.3 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 21.2 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 43.3 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 87.1 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 173 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
268 | utweb_installer.tmp | 143.204.205.67:443 | d2sxdxjyuufits.cloudfront.net | AMAZON-02 | US | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
268 | utweb_installer.tmp | 67.215.238.66:443 | download-lb.utorrent.com | ASN-QUADRANET-GLOBAL | US | unknown |
848 | chrome.exe | 142.250.185.67:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
1588 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
848 | chrome.exe | 172.217.218.84:443 | accounts.google.com | GOOGLE | US | unknown |
848 | chrome.exe | 142.250.186.36:443 | www.google.com | GOOGLE | US | whitelisted |
848 | chrome.exe | 142.250.186.35:443 | www.gstatic.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
d2sxdxjyuufits.cloudfront.net |
| unknown |
download-lb.utorrent.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
analytics.apis.mcafee.com |
| unknown |
encrypted-tbn0.gstatic.com |
| whitelisted |
Threats
Process | Message |
|---|---|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in current directory
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in EXE directory
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in current directory
|
saBSI.exe | NotComDllGetInterface: C:\Users\admin\AppData\Local\Temp\is-R9VMI.tmp\component0_extract\saBSI.exe loading C:\Users\admin\AppData\Local\Temp\is-R9VMI.tmp\component0_extract\mfeaaca.dll, WinVerifyTrust failed with 80092003
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in current directory
|
saBSI.exe | NotComDllGetInterface: C:\Users\admin\AppData\Local\Temp\is-R9VMI.tmp\component0_extract\saBSI.exe loading C:\Users\admin\AppData\Local\Temp\is-R9VMI.tmp\component0_extract\mfeaaca.dll, WinVerifyTrust failed with 80092003
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in EXE directory
|
saBSI.exe | NotComDllGetInterface: C:\Users\admin\AppData\Local\Temp\is-R9VMI.tmp\component0_extract\saBSI.exe loading C:\Users\admin\AppData\Local\Temp\is-R9VMI.tmp\component0_extract\mfeaaca.dll, WinVerifyTrust failed with 80092003
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in EXE directory
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in EXE directory
|