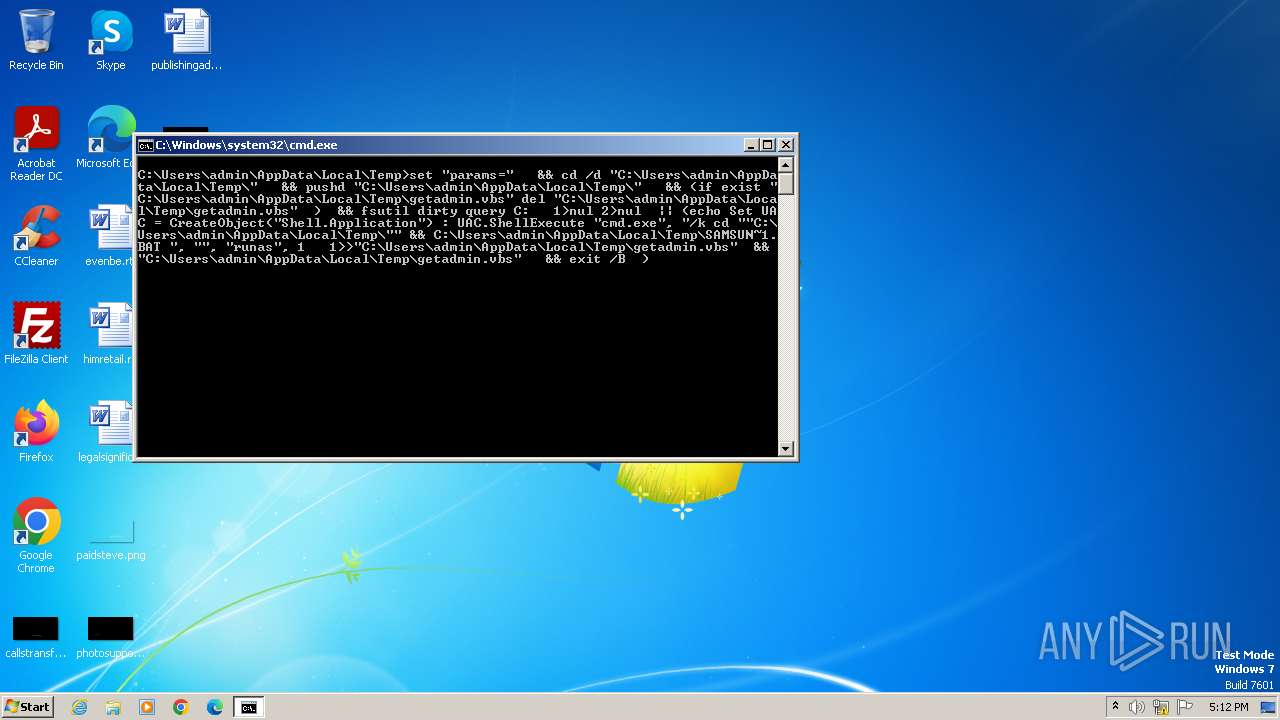
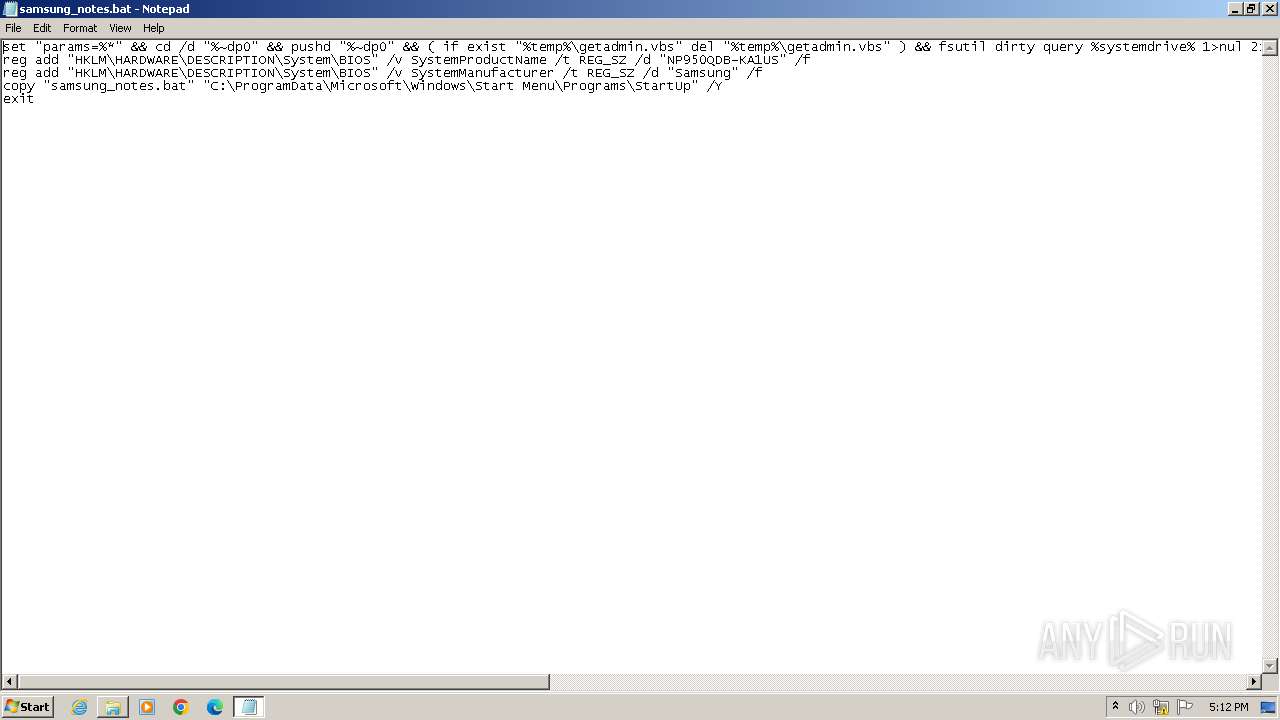
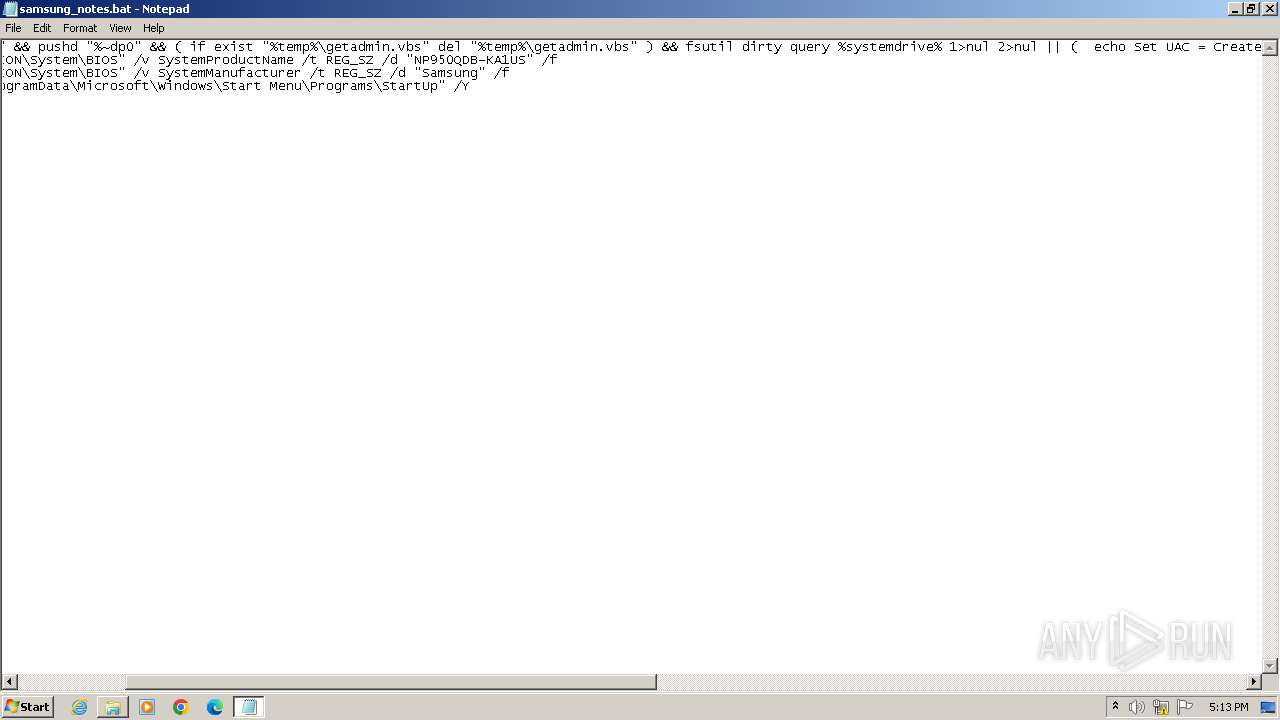
| File name: | samsung_notes.bat |
| Full analysis: | https://app.any.run/tasks/1472ef2a-dfae-415a-af76-571ec69dbae7 |
| Verdict: | Malicious activity |
| Analysis date: | May 18, 2024, 16:12:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines (363), with CRLF line terminators |
| MD5: | 86F37D90024D178FBCD1609F8383B33D |
| SHA1: | 11A37D0D5F951E9341C3216CC4F16C1A42760CFF |
| SHA256: | 993B08E24FFCA38478CEFE91B10CE9D7CD13CA64A74211CF8F4FF9BFB61C0195 |
| SSDEEP: | 12:btIdk5jtnrC0yyGyDHx9sM3d2K+89udqQghlaVM1tWtJj:b+otrlyRgx9so2e98UaVM8F |
MALICIOUS
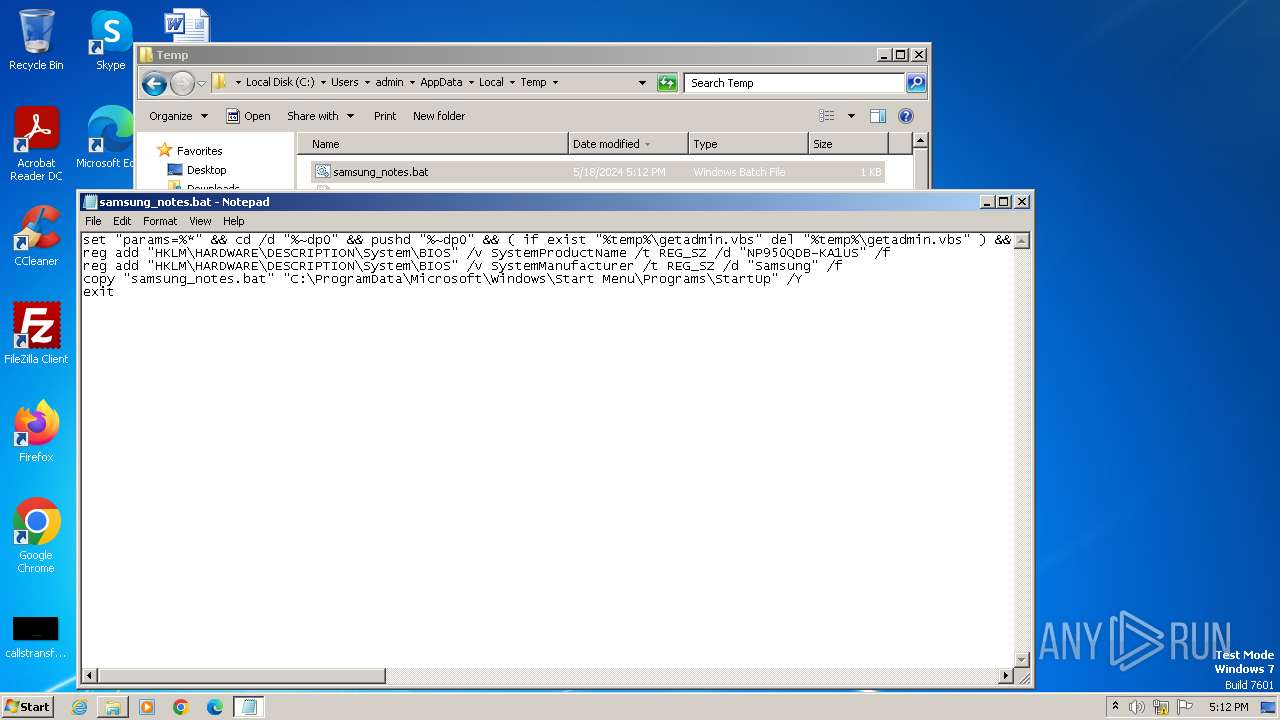
Create files in the Startup directory
- cmd.exe (PID: 2044)
SUSPICIOUS
Reads the Internet Settings
- wscript.exe (PID: 4036)
- cmd.exe (PID: 3976)
- cmd.exe (PID: 1980)
- wscript.exe (PID: 2456)
Runs shell command (SCRIPT)
- wscript.exe (PID: 4036)
- wscript.exe (PID: 2456)
Executing commands from a ".bat" file
- wscript.exe (PID: 4036)
- wscript.exe (PID: 2456)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2044)
- cmd.exe (PID: 2324)
The process executes VB scripts
- cmd.exe (PID: 1980)
- cmd.exe (PID: 3976)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 2456)
- wscript.exe (PID: 4036)
INFO
Manual execution by a user
- explorer.exe (PID: 1768)
- cmd.exe (PID: 1980)
- notepad.exe (PID: 2372)
Creates files in the program directory
- cmd.exe (PID: 2044)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
59
Monitored processes
16
Malicious processes
2
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1292 | reg add "HKLM\HARDWARE\DESCRIPTION\System\BIOS" /v SystemProductName /t REG_SZ /d "NP950QDB-KA1US" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1432 | fsutil dirty query C: | C:\Windows\System32\fsutil.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: fsutil.exe Exit code: 0 Version: 6.1.7601.17577 (win7sp1_gdr.110310-1504) Modules
| |||||||||||||||
| 1768 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1980 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\samsung_notes.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2044 | "C:\Windows\System32\cmd.exe" /k cd "C:\Users\admin\AppData\Local\Temp\" && C:\Users\admin\AppData\Local\Temp\SAMSUN~1.BAT | C:\Windows\System32\cmd.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2180 | reg add "HKLM\HARDWARE\DESCRIPTION\System\BIOS" /v SystemManufacturer /t REG_SZ /d "Samsung" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2324 | "C:\Windows\System32\cmd.exe" /k cd "C:\Users\admin\AppData\Local\Temp\" && C:\Users\admin\AppData\Local\Temp\SAMSUN~1.BAT | C:\Windows\System32\cmd.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2340 | fsutil dirty query C: | C:\Windows\System32\fsutil.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: fsutil.exe Exit code: 1 Version: 6.1.7601.17577 (win7sp1_gdr.110310-1504) Modules
| |||||||||||||||
| 2372 | "C:\Windows\System32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\samsung_notes.bat | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2456 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\getadmin.vbs" | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
Total events
7 090
Read events
7 054
Write events
36
Delete events
0
Modification events
| (PID) Process: | (3976) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3976) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3976) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3976) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (4036) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4036) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4036) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (4036) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1292) reg.exe | Key: | HKEY_LOCAL_MACHINE\HARDWARE\DESCRIPTION\System\BIOS |
| Operation: | write | Name: | SystemProductName |
Value: NP950QDB-KA1US | |||
| (PID) Process: | (2180) reg.exe | Key: | HKEY_LOCAL_MACHINE\HARDWARE\DESCRIPTION\System\BIOS |
| Operation: | write | Name: | SystemManufacturer |
Value: Samsung | |||
Executable files
0
Suspicious files
0
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2044 | cmd.exe | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\StartUp\samsung_notes.bat | text | |
MD5:86F37D90024D178FBCD1609F8383B33D | SHA256:993B08E24FFCA38478CEFE91B10CE9D7CD13CA64A74211CF8F4FF9BFB61C0195 | |||
| 1980 | cmd.exe | C:\Users\admin\AppData\Local\Temp\getadmin.vbs | text | |
MD5:C3F9FE9125C2F98CAAEFF017055088CA | SHA256:A7645AB349B137C711D2033625E93FECF55B9215A7DE01C94D09738E66B6ACA6 | |||
| 3976 | cmd.exe | C:\Users\admin\AppData\Local\Temp\getadmin.vbs | text | |
MD5:C3F9FE9125C2F98CAAEFF017055088CA | SHA256:A7645AB349B137C711D2033625E93FECF55B9215A7DE01C94D09738E66B6ACA6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |