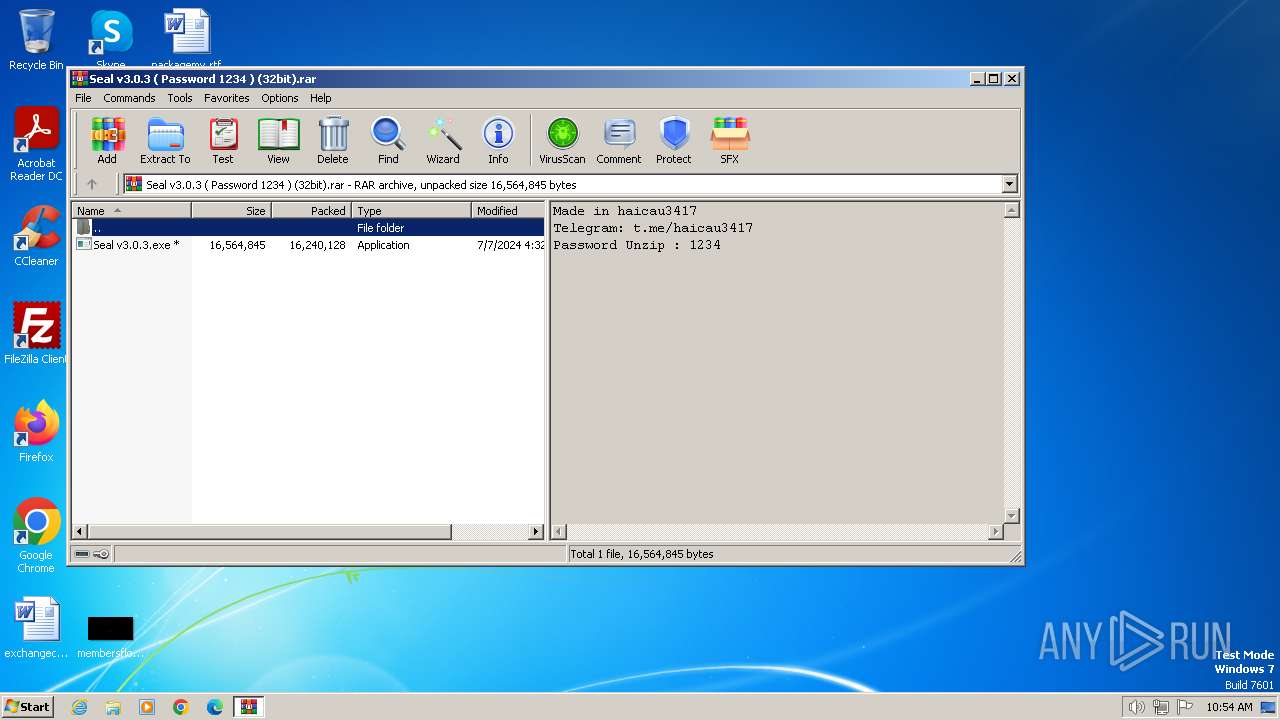
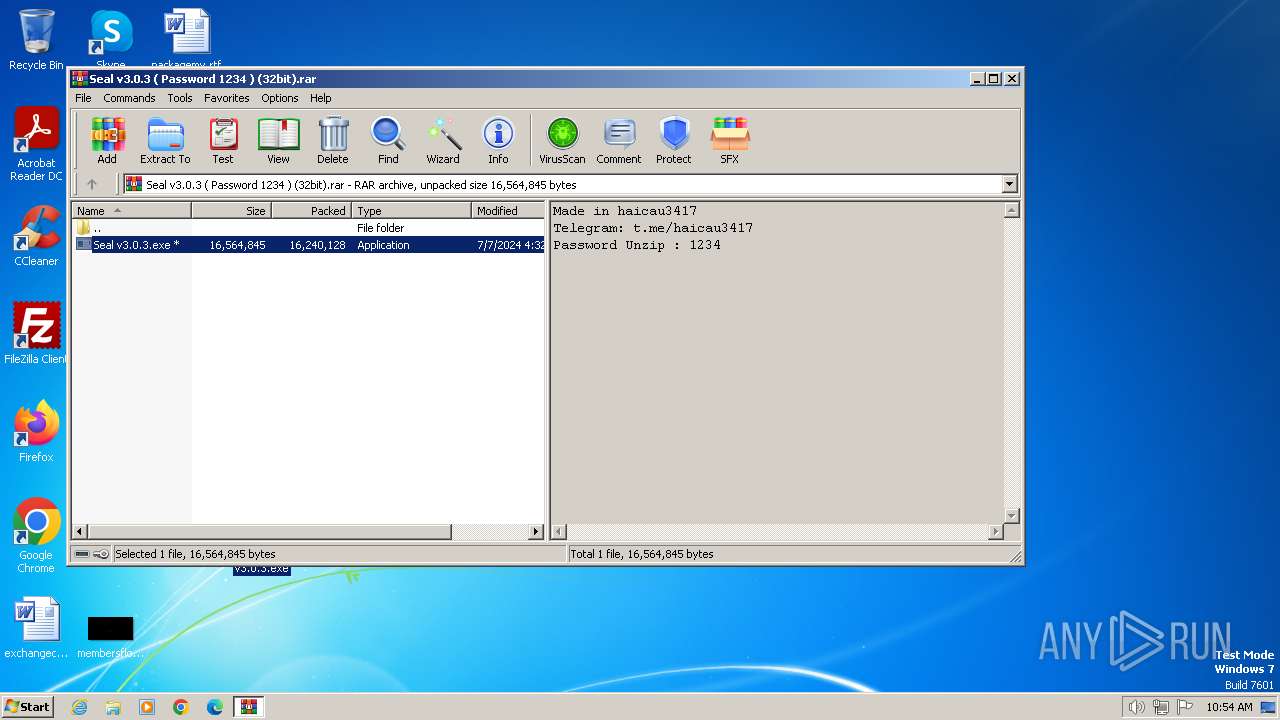
| File name: | Seal v3.0.3 ( Password 1234 ) (32bit).rar |
| Full analysis: | https://app.any.run/tasks/649755f9-de42-423f-a512-c03924d04222 |
| Verdict: | Malicious activity |
| Analysis date: | July 20, 2024, 09:54:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 03043182BA85E20AE8DAC16310F186FE |
| SHA1: | CD453E00AC98C6C4281C6EAC778CEB5900B80EAF |
| SHA256: | 9901E3AA56DA09EF4EFD8236995DF3C1BF33361981A25A70F969B79AA616E198 |
| SSDEEP: | 98304:BzjXYnev+LoJBbRB32I50mSc7Of7E6q2bN6Ait/tu9ehTRXengTWxqanRNFrVQ8n:JcIBOki7J6R0WwX1/C2IgfCAyqqc// |
MALICIOUS
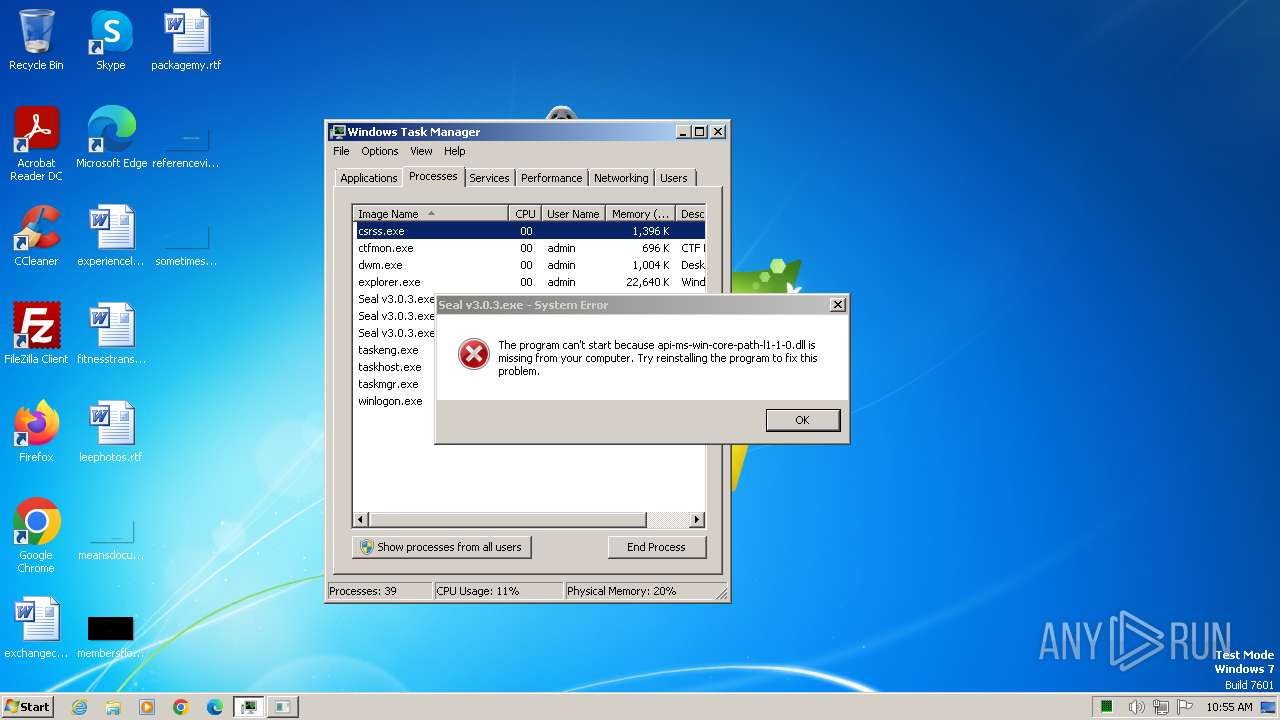
Drops the executable file immediately after the start
- Seal v3.0.3.exe (PID: 400)
- Seal v3.0.3.exe (PID: 2948)
SUSPICIOUS
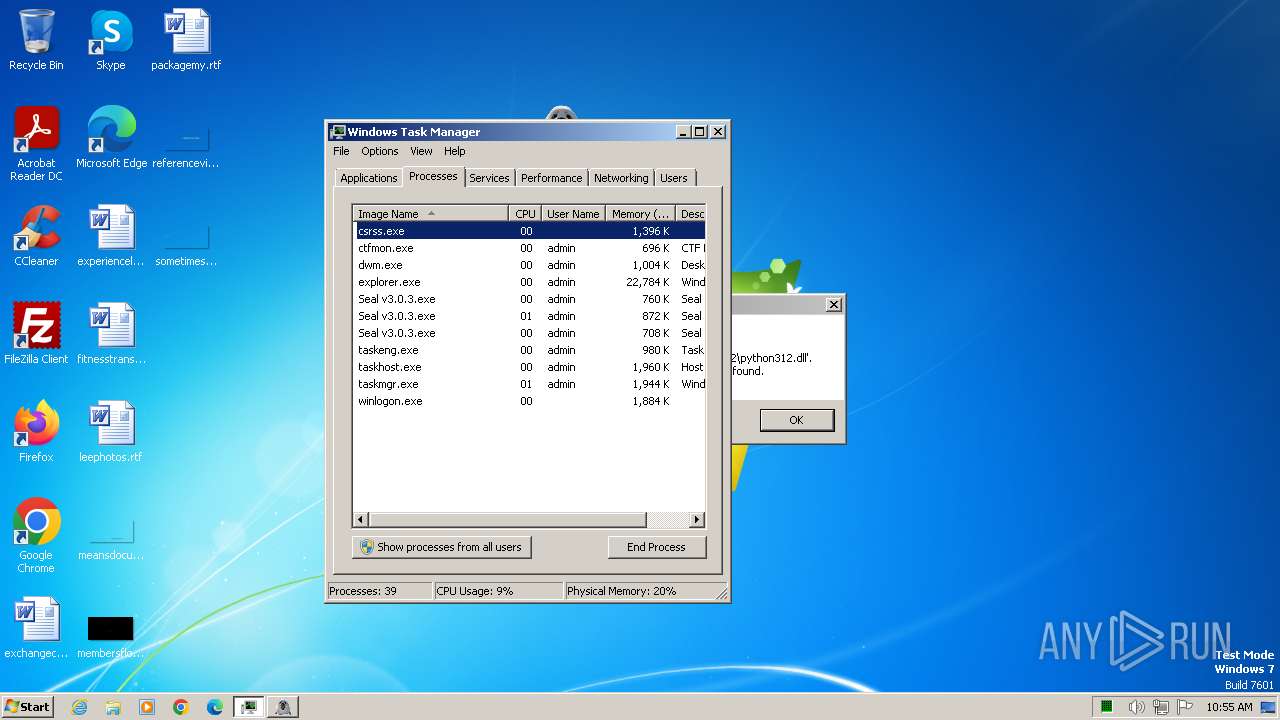
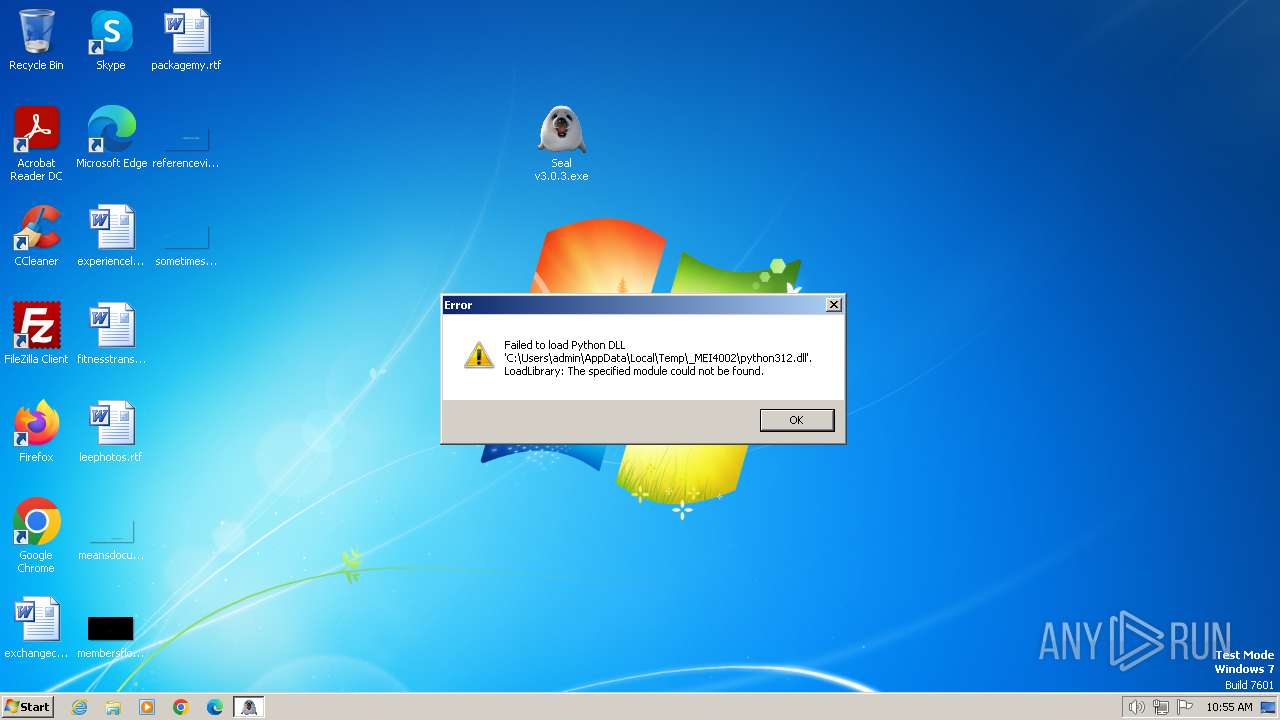
Process drops python dynamic module
- Seal v3.0.3.exe (PID: 400)
- Seal v3.0.3.exe (PID: 2948)
Executable content was dropped or overwritten
- Seal v3.0.3.exe (PID: 400)
- Seal v3.0.3.exe (PID: 2948)
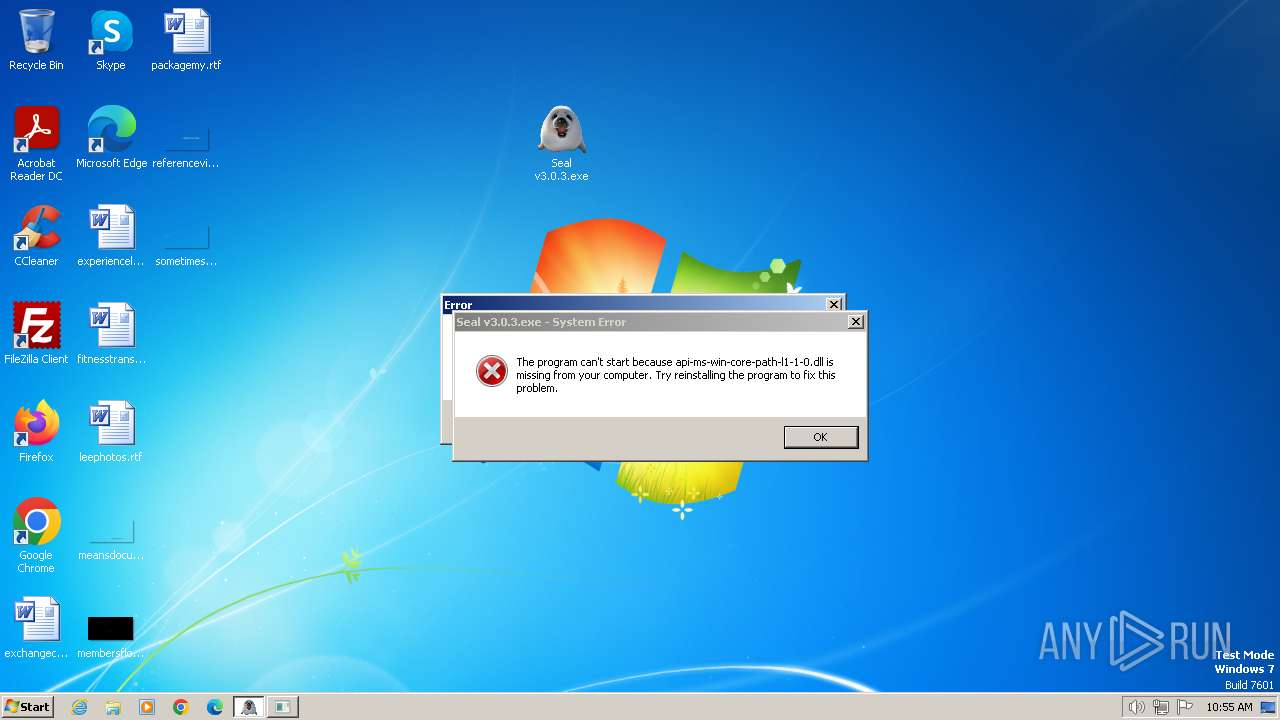
Process drops legitimate windows executable
- Seal v3.0.3.exe (PID: 400)
- Seal v3.0.3.exe (PID: 2948)
The process drops C-runtime libraries
- Seal v3.0.3.exe (PID: 400)
- Seal v3.0.3.exe (PID: 2948)
Application launched itself
- Seal v3.0.3.exe (PID: 2948)
- Seal v3.0.3.exe (PID: 400)
Loads Python modules
- Seal v3.0.3.exe (PID: 2432)
- Seal v3.0.3.exe (PID: 3652)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3520)
Checks supported languages
- Seal v3.0.3.exe (PID: 400)
- Seal v3.0.3.exe (PID: 2948)
- Seal v3.0.3.exe (PID: 2432)
- Seal v3.0.3.exe (PID: 3652)
Create files in a temporary directory
- Seal v3.0.3.exe (PID: 400)
- Seal v3.0.3.exe (PID: 2948)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3520)
Reads the computer name
- Seal v3.0.3.exe (PID: 400)
- Seal v3.0.3.exe (PID: 2948)
Manual execution by a user
- Seal v3.0.3.exe (PID: 400)
- Seal v3.0.3.exe (PID: 2948)
- taskmgr.exe (PID: 1980)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
43
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 400 | "C:\Users\admin\Desktop\Seal v3.0.3.exe" | C:\Users\admin\Desktop\Seal v3.0.3.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Modules
| |||||||||||||||
| 1980 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\System32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2432 | "C:\Users\admin\Desktop\Seal v3.0.3.exe" | C:\Users\admin\Desktop\Seal v3.0.3.exe | — | Seal v3.0.3.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Modules
| |||||||||||||||
| 2948 | "C:\Users\admin\Desktop\Seal v3.0.3.exe" | C:\Users\admin\Desktop\Seal v3.0.3.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Modules
| |||||||||||||||
| 3520 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Seal v3.0.3 ( Password 1234 ) (32bit).rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3652 | "C:\Users\admin\Desktop\Seal v3.0.3.exe" | C:\Users\admin\Desktop\Seal v3.0.3.exe | — | Seal v3.0.3.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Modules
| |||||||||||||||
Total events
3 865
Read events
3 839
Write events
26
Delete events
0
Modification events
| (PID) Process: | (3520) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3520) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3520) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3520) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3520) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3520) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3520) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Seal v3.0.3 ( Password 1234 ) (32bit).rar | |||
| (PID) Process: | (3520) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3520) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3520) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
149
Suspicious files
6
Text files
1 874
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3520 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3520.8091\Seal v3.0.3.exe | executable | |
MD5:0CFC1C84A3CFECF06616A008680159F6 | SHA256:D8342107A8647F970DDE83C9B6762958E7EDFA77BA6EE57CCCABE2D817D5DC88 | |||
| 400 | Seal v3.0.3.exe | C:\Users\admin\AppData\Local\Temp\_MEI4002\Crypto\Cipher\_raw_arc2.pyd | executable | |
MD5:A332271C53E041B9B892B60AD8DA8830 | SHA256:C1ADDB480CB90A9D8A2F5F73BC8EBCB3FD9D5BF8EE72D4F63D5DF759DE7733D5 | |||
| 400 | Seal v3.0.3.exe | C:\Users\admin\AppData\Local\Temp\_MEI4002\Crypto\Cipher\_chacha20.pyd | executable | |
MD5:54E6DE102DCBEF46AE7B5AC9F007E826 | SHA256:E7EF3EFE01606EBE564C1818EE5839A997CEB8B99846F6C4FBA86A09BCF9A507 | |||
| 400 | Seal v3.0.3.exe | C:\Users\admin\AppData\Local\Temp\_MEI4002\Crypto\Cipher\_raw_aes.pyd | executable | |
MD5:A37E15DDFA1524FE9C504A1D55C23559 | SHA256:627D3E576E266183380510BB3E2BED66BBA719A6F8DB6352E4A7888AE46C72CE | |||
| 400 | Seal v3.0.3.exe | C:\Users\admin\AppData\Local\Temp\_MEI4002\Crypto\Cipher\_raw_blowfish.pyd | executable | |
MD5:08A86CD45DA8764652261557F683BF2B | SHA256:37F946698ACCD3BBD777F791420765B079D634EE21749ED8239C963CE4857ED1 | |||
| 400 | Seal v3.0.3.exe | C:\Users\admin\AppData\Local\Temp\_MEI4002\Crypto\Cipher\_raw_cast.pyd | executable | |
MD5:47E50117EC9091C856FC542D03ED73B5 | SHA256:61B97957C93FC40AB9C7BDBEACA19FBD4D0EEA25ECE9A71447B6613663FC7037 | |||
| 400 | Seal v3.0.3.exe | C:\Users\admin\AppData\Local\Temp\_MEI4002\Crypto\Cipher\_Salsa20.pyd | executable | |
MD5:CB9E65D1D021CFB12C65C50BF80DAF5C | SHA256:8611AB59513020BB21528D604BD168B2BBBD4A87A093CE3502B8221D9E36ADFC | |||
| 400 | Seal v3.0.3.exe | C:\Users\admin\AppData\Local\Temp\_MEI4002\Crypto\Cipher\_pkcs1_decode.pyd | executable | |
MD5:B706A2C68D968D3DEBABB2032974A2D8 | SHA256:D23FC438498AFFB3C31BFE0E2BDA167D442D56F59D1AD86A52862E437B2E3B7A | |||
| 400 | Seal v3.0.3.exe | C:\Users\admin\AppData\Local\Temp\_MEI4002\Crypto\Cipher\_raw_cbc.pyd | executable | |
MD5:F2E41F7FA11EAD634DC262A6EDDD19E8 | SHA256:B6D80A0833306F7182F6D73059E7340BBF7879F5B515194EC4FF59D423557A7D | |||
| 400 | Seal v3.0.3.exe | C:\Users\admin\AppData\Local\Temp\_MEI4002\Crypto\Cipher\_raw_cfb.pyd | executable | |
MD5:40DA301B2DBB903A6D0F269E02B74C01 | SHA256:1D6A5CA1CFB202B6588FE34461A53AC07EF3DC1D3883A44F989F70E44A19B9B1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
13
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 304 | 23.50.131.216:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1060 | svchost.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a9f83325acc8ca75 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
— | — | 239.255.255.250:3702 | — | — | — | whitelisted |
1372 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
1372 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1372 | svchost.exe | 23.50.131.216:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |