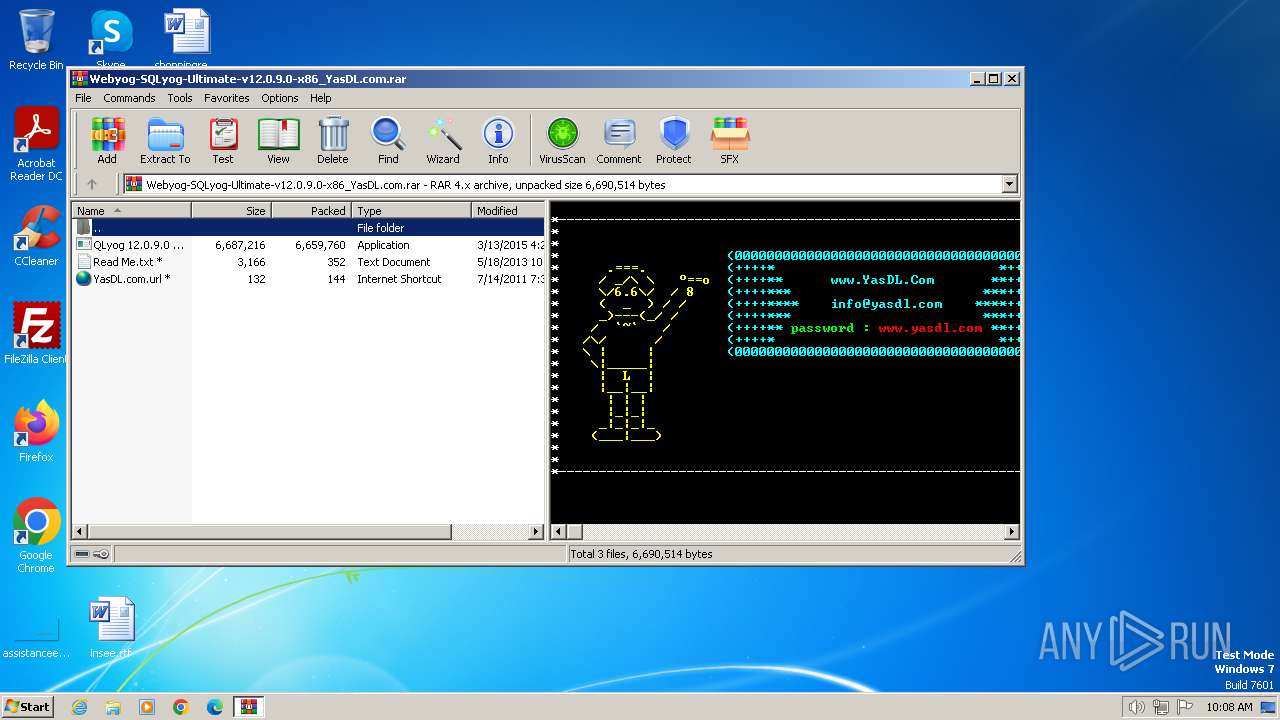
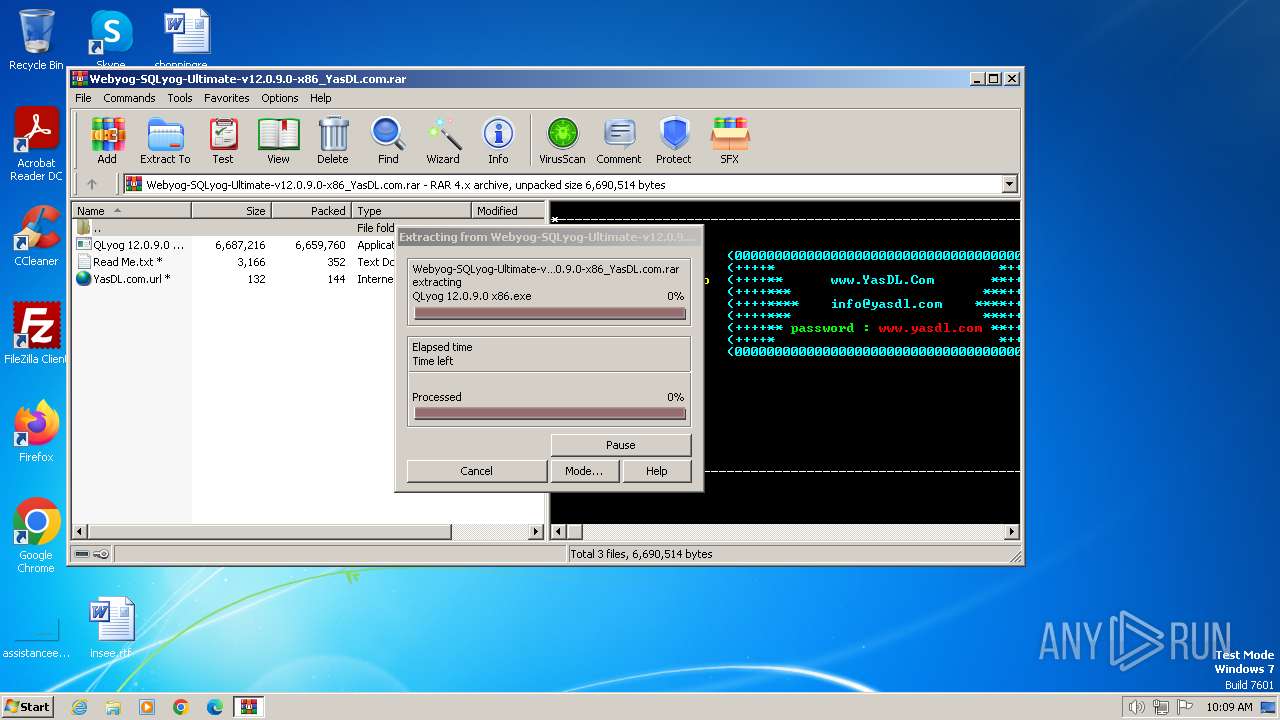
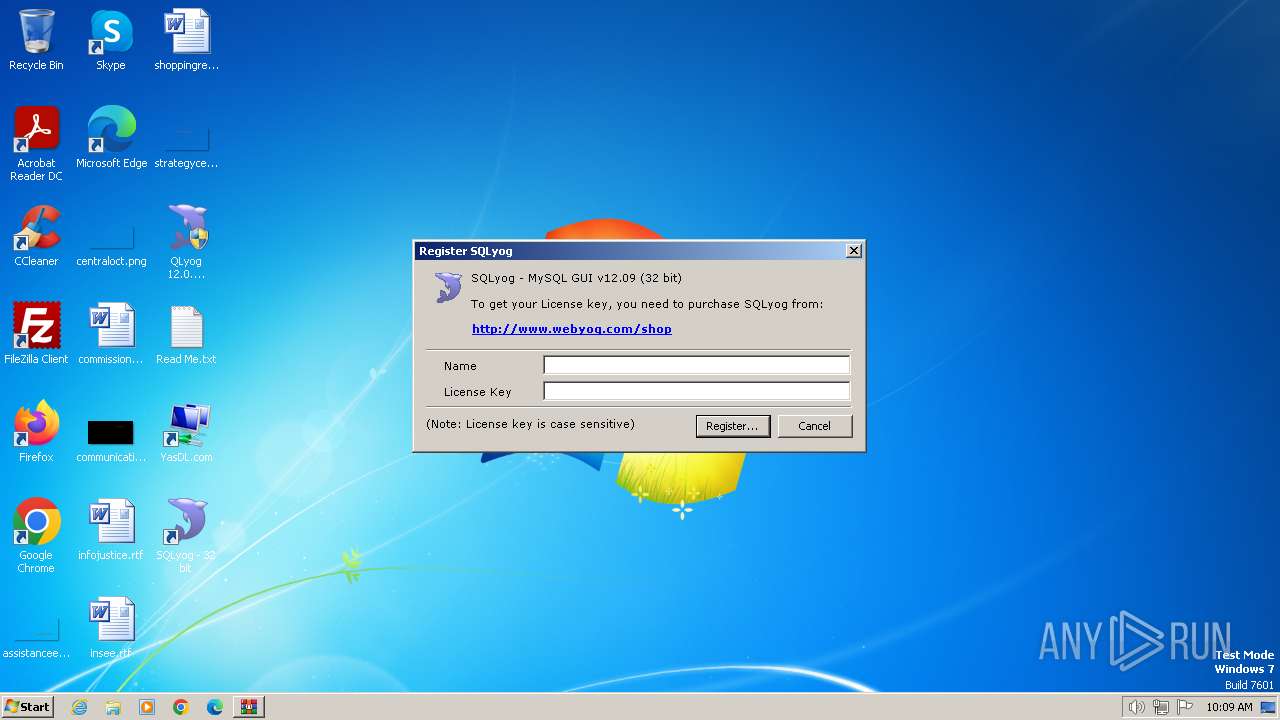
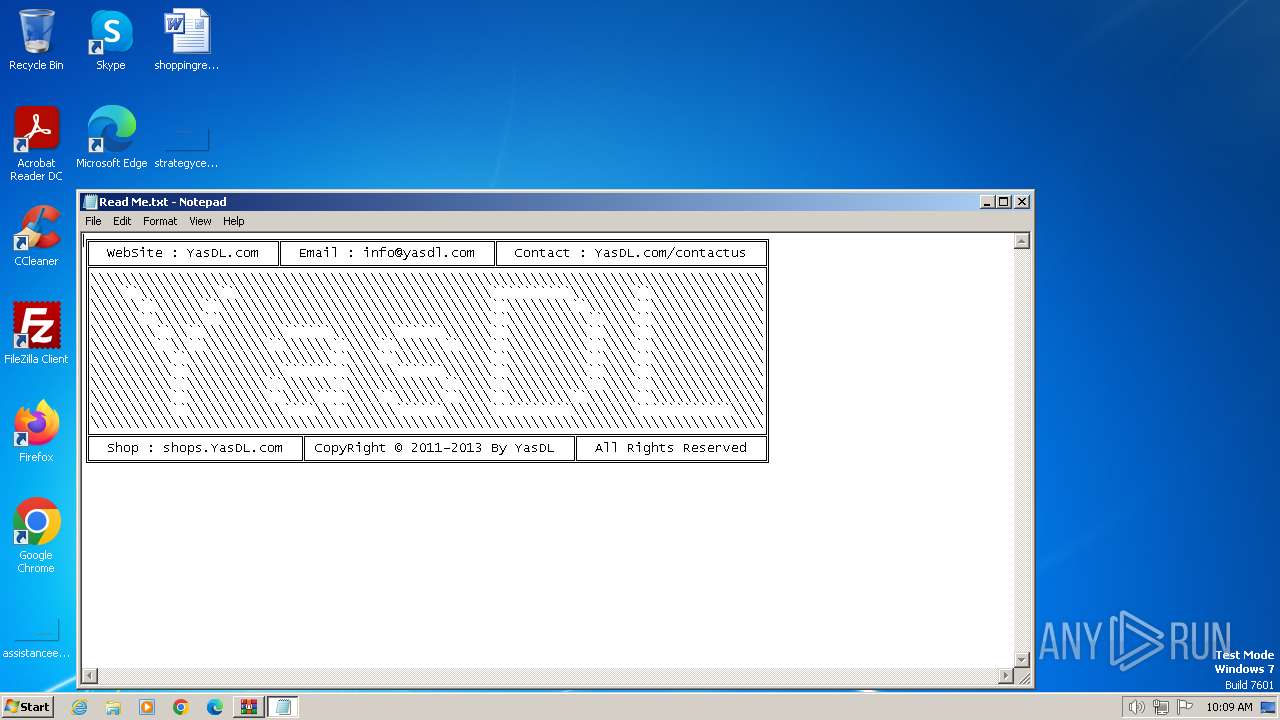
| File name: | Webyog-SQLyog-Ultimate-v12.0.9.0-x86_YasDL.com.rar |
| Full analysis: | https://app.any.run/tasks/6db21fd1-8702-41bb-867b-eda770ac74a7 |
| Verdict: | Malicious activity |
| Analysis date: | July 15, 2024, 09:08:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 6E69FC8606E9EF20F23AF04780BBFCE8 |
| SHA1: | 5E027663E23F767A7472480862634445B988B333 |
| SHA256: | 98CBC93CF37B27BDD130C3C04F3250072073E5006EC57E4A2CFB7982D95F38B3 |
| SSDEEP: | 98304:EZKviXlUCeszNVIA8noHjt+UfcQ12k1L2uzCYl1ZXJLEHxFGUxhtDzh0Sb0lpvpT:EPe80yS+MVgVJLn |
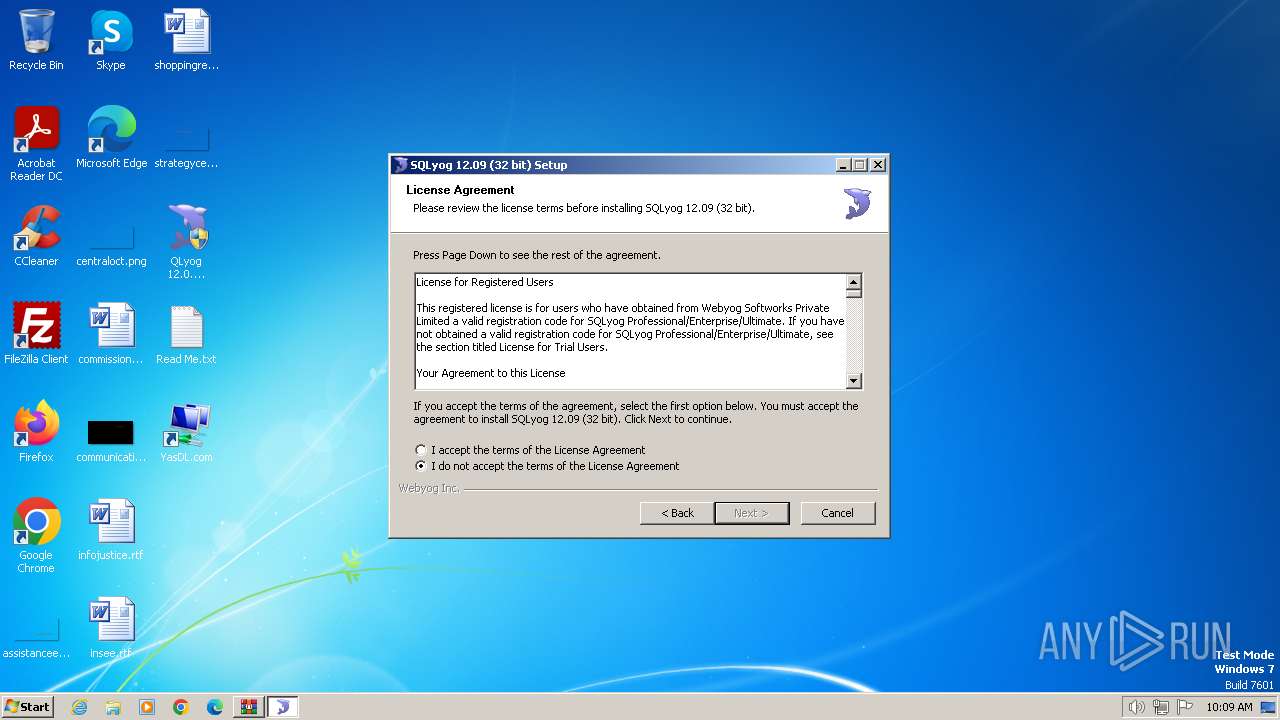
MALICIOUS
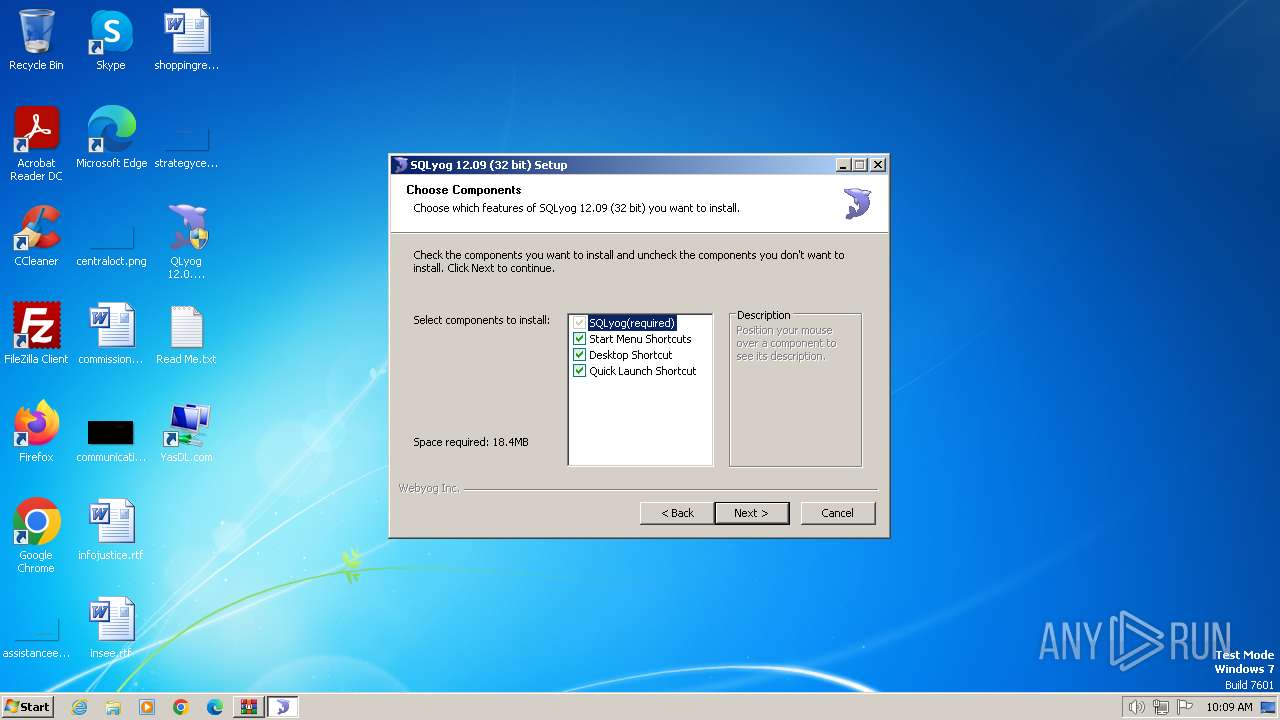
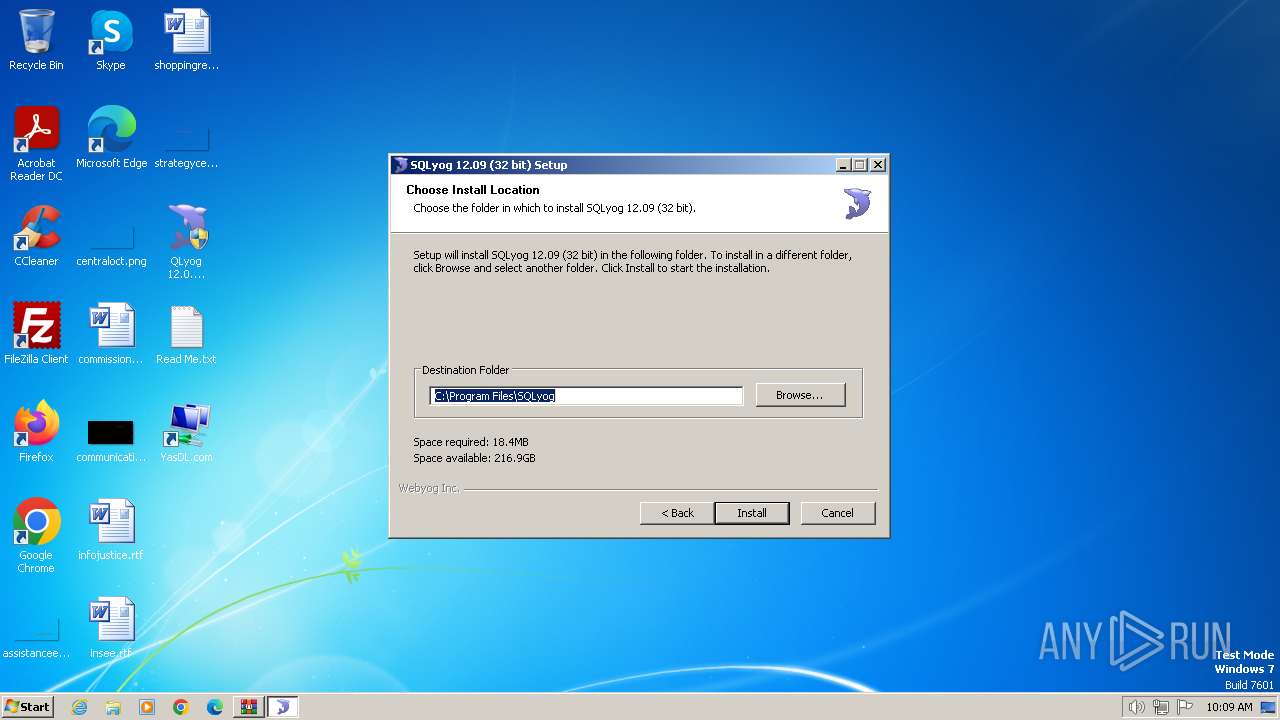
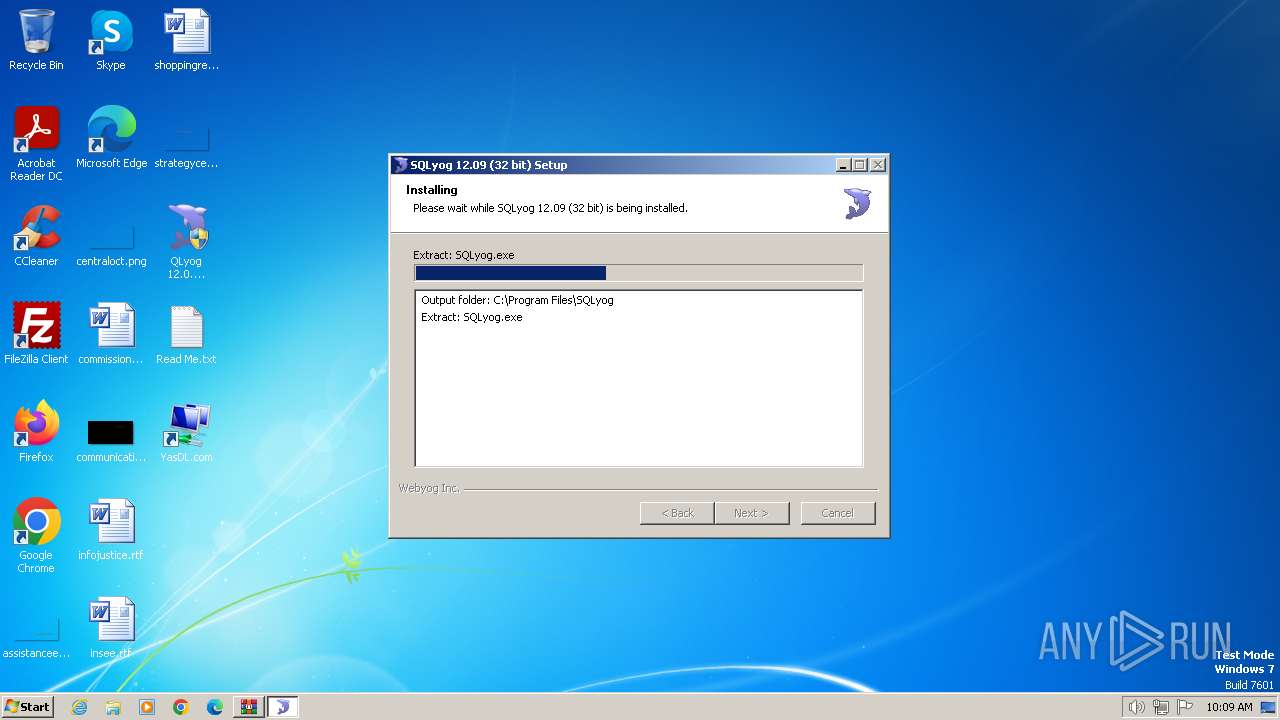
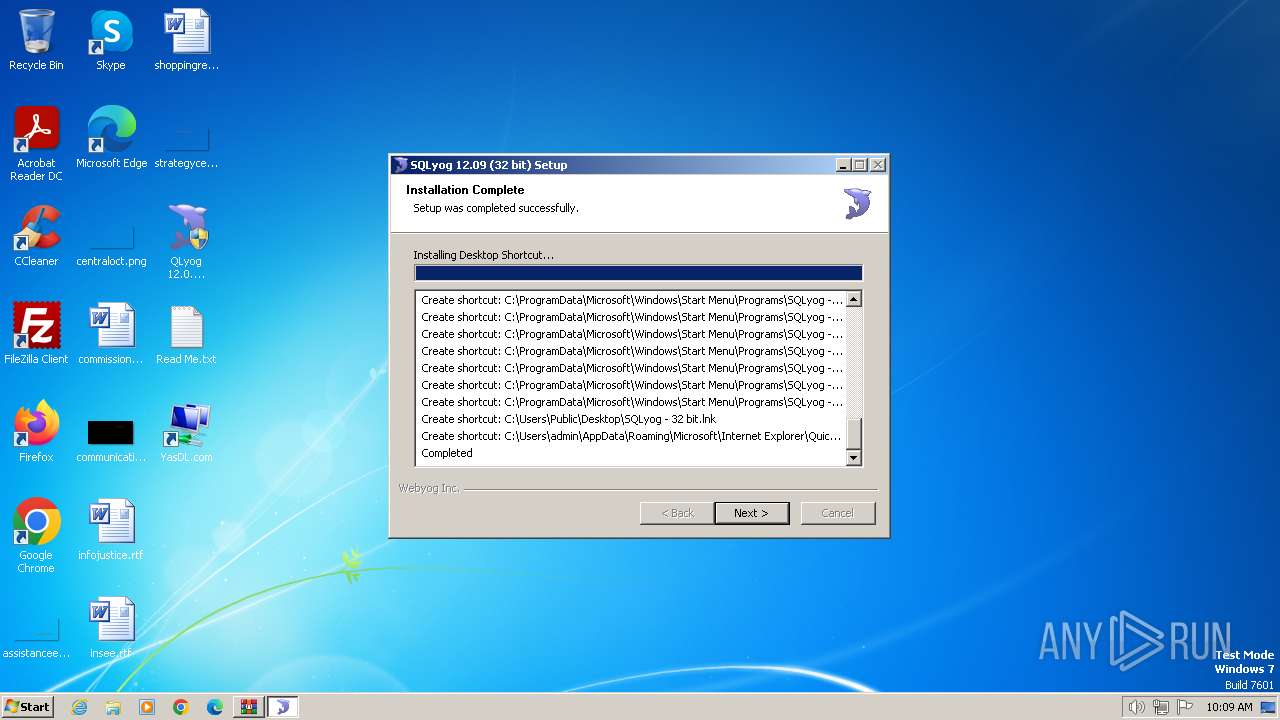
Drops the executable file immediately after the start
- QLyog 12.0.9.0 x86.exe (PID: 3160)
SUSPICIOUS
Executable content was dropped or overwritten
- QLyog 12.0.9.0 x86.exe (PID: 3160)
The process creates files with name similar to system file names
- QLyog 12.0.9.0 x86.exe (PID: 3160)
Malware-specific behavior (creating "System.dll" in Temp)
- QLyog 12.0.9.0 x86.exe (PID: 3160)
Creates a software uninstall entry
- QLyog 12.0.9.0 x86.exe (PID: 3160)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3384)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3384)
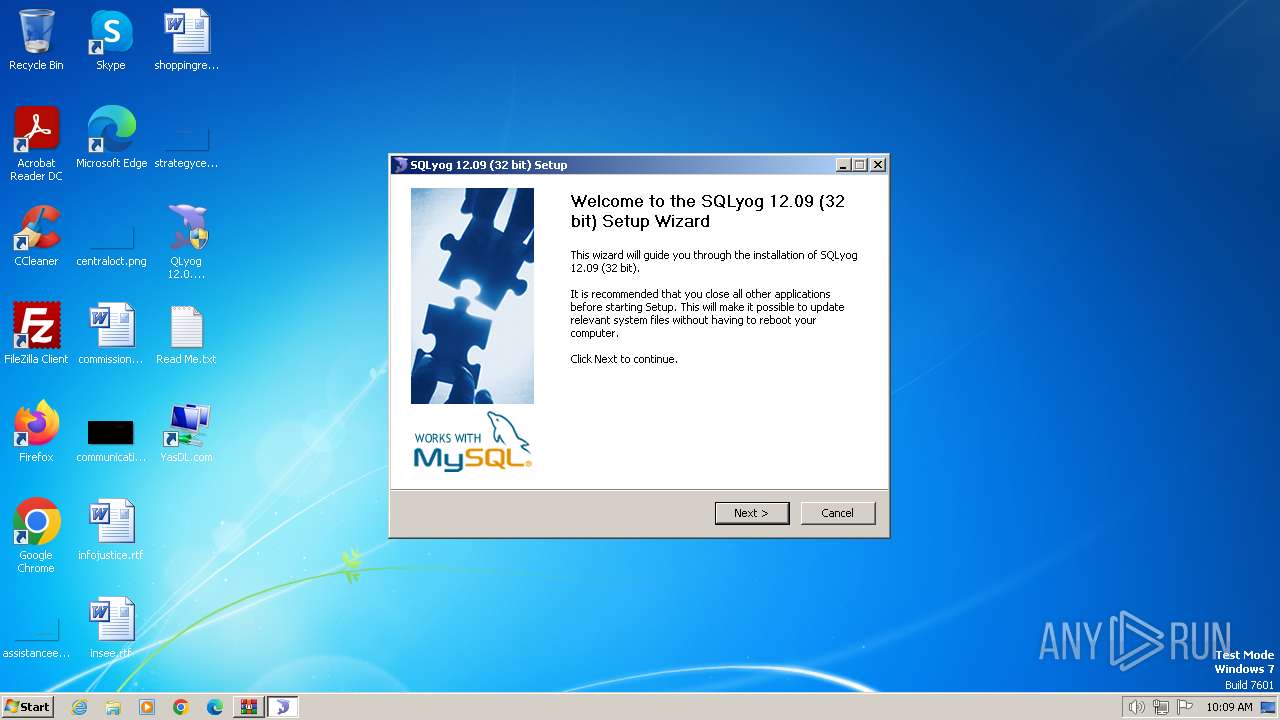
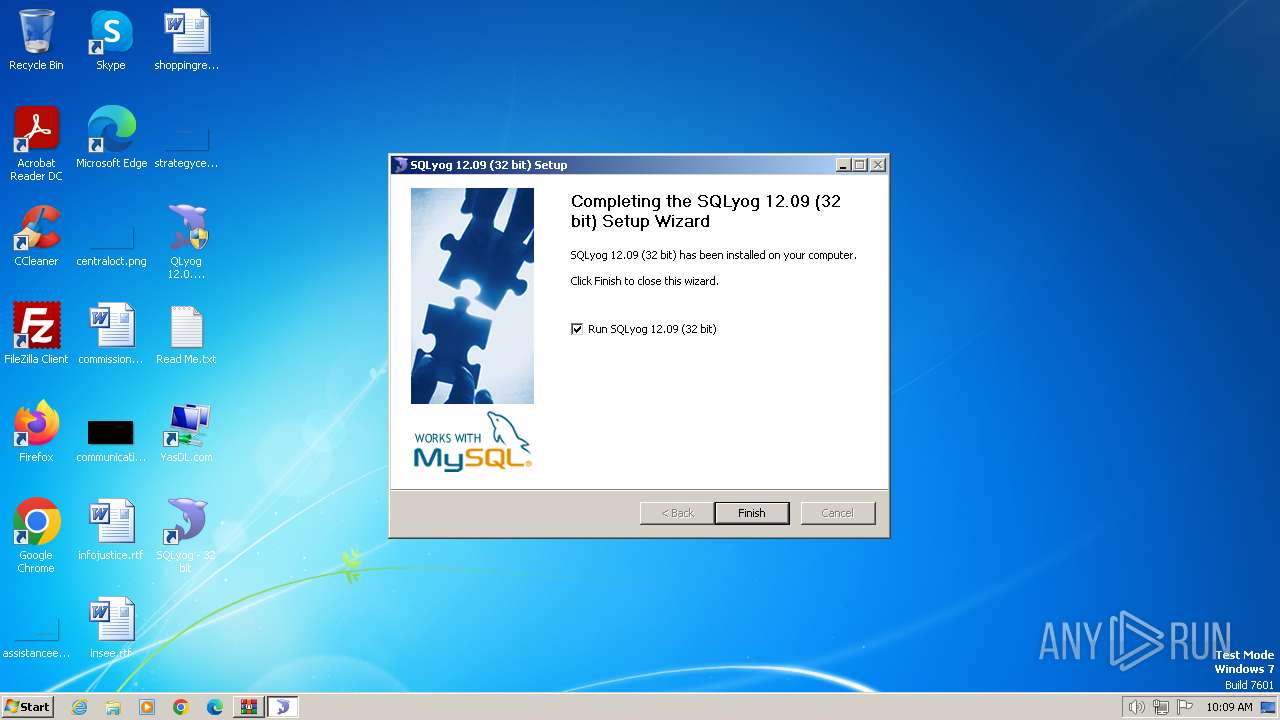
Manual execution by a user
- QLyog 12.0.9.0 x86.exe (PID: 3160)
- QLyog 12.0.9.0 x86.exe (PID: 3196)
- notepad.exe (PID: 3572)
Checks supported languages
- QLyog 12.0.9.0 x86.exe (PID: 3160)
- SQLyog.exe (PID: 2980)
Reads the computer name
- QLyog 12.0.9.0 x86.exe (PID: 3160)
- SQLyog.exe (PID: 2980)
Create files in a temporary directory
- QLyog 12.0.9.0 x86.exe (PID: 3160)
Creates files in the program directory
- QLyog 12.0.9.0 x86.exe (PID: 3160)
Creates files or folders in the user directory
- QLyog 12.0.9.0 x86.exe (PID: 3160)
- SQLyog.exe (PID: 2980)
UPX packer has been detected
- SQLyog.exe (PID: 2980)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 6659811 |
|---|---|
| UncompressedSize: | 6687216 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2015:03:13 04:25:44 |
| PackingMethod: | Normal |
| ArchivedFileName: | QLyog 12.0.9.0 x86.exe |
Total processes
47
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2980 | "C:\Program Files\SQLyog\SQLyog.exe" | C:\Program Files\SQLyog\SQLyog.exe | QLyog 12.0.9.0 x86.exe | ||||||||||||
User: admin Company: Webyog Inc. Integrity Level: HIGH Description: SQLyog - MySQL GUI Version: 12.0.9.0 Modules
| |||||||||||||||
| 3160 | "C:\Users\admin\Desktop\QLyog 12.0.9.0 x86.exe" | C:\Users\admin\Desktop\QLyog 12.0.9.0 x86.exe | explorer.exe | ||||||||||||
User: admin Company: Webyog Inc. Integrity Level: HIGH Description: SQLyog 12.09 (32 bit) Setup Exit code: 0 Version: 12.0.9.0 Modules
| |||||||||||||||
| 3196 | "C:\Users\admin\Desktop\QLyog 12.0.9.0 x86.exe" | C:\Users\admin\Desktop\QLyog 12.0.9.0 x86.exe | — | explorer.exe | |||||||||||
User: admin Company: Webyog Inc. Integrity Level: MEDIUM Description: SQLyog 12.09 (32 bit) Setup Exit code: 3221226540 Version: 12.0.9.0 Modules
| |||||||||||||||
| 3384 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Webyog-SQLyog-Ultimate-v12.0.9.0-x86_YasDL.com.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3572 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Read Me.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
5 039
Read events
4 999
Write events
40
Delete events
0
Modification events
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Webyog-SQLyog-Ultimate-v12.0.9.0-x86_YasDL.com.rar | |||
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
16
Suspicious files
17
Text files
17
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3384 | WinRAR.exe | C:\Users\admin\Desktop\QLyog 12.0.9.0 x86.exe | executable | |
MD5:1782FE3A97B53712AB8EF47641286A9B | SHA256:26CEE1B8AE70D17F1BBC797A572E8F367EFBCEC2FF53EFA393F00A2DAE00D764 | |||
| 3384 | WinRAR.exe | C:\Users\admin\Desktop\Read Me.txt | text | |
MD5:A6DD70C86877462DE9431034ED3D9B3F | SHA256:CFE269804CCC862D20CDDE034BE1DF16B5D6386A6075D12628880B401DC863AA | |||
| 3384 | WinRAR.exe | C:\Users\admin\Desktop\YasDL.com.url | url | |
MD5:1C815D5FC58800EDC61B341D36C7A293 | SHA256:499FFBD3E24ECA8F9D1E7E267EEAEF15890213865F94F529290837E4F57A4024 | |||
| 3160 | QLyog 12.0.9.0 x86.exe | C:\Program Files\SQLyog\htmlayout.dll | executable | |
MD5:4E852FE48E66CB7649E4D544DEA93619 | SHA256:25C1AF4385F02BEB8BA3B1F5355A68628A17E5301CE405268F4EEA04D4900AF4 | |||
| 3160 | QLyog 12.0.9.0 x86.exe | C:\Program Files\SQLyog\SQLyog.exe | executable | |
MD5:33897A98D200F36C5D53C65C7ABD4492 | SHA256:752026DC4EFED081482B1117EDDEA2A0B8CE0007F96835529A6F11E105BAEF0F | |||
| 3160 | QLyog 12.0.9.0 x86.exe | C:\Program Files\SQLyog\libeay32.dll | executable | |
MD5:B5691FD55C6DE498966F58566BB17918 | SHA256:E6CC31E6288411F05430976EBAEE9676756624757B73B2F0F4EBF12DFEC57B38 | |||
| 3160 | QLyog 12.0.9.0 x86.exe | C:\Program Files\SQLyog\plink.exe | executable | |
MD5:A0A9C26DD8F91A45650C2A508D4CEDE6 | SHA256:93D129C4A610E652DC3A8A2EE0BFC87C2D971BD00A0BA2C76F58802750BE2CED | |||
| 3160 | QLyog 12.0.9.0 x86.exe | C:\Program Files\SQLyog\SQLyog.dll | executable | |
MD5:893B647F99142021063F3267EF9104AC | SHA256:9E386D4CBD6329486990A42B3776CCD18F4DFF15344778D1CCE13DCAB3BC7515 | |||
| 3160 | QLyog 12.0.9.0 x86.exe | C:\Program Files\SQLyog\Keywords.db | binary | |
MD5:BFF32ED83F49911384E41655C738BEC6 | SHA256:512BB276B62141F909BC3DA072A0BEB329D864E2B45BD0878234F773001B1E2E | |||
| 3160 | QLyog 12.0.9.0 x86.exe | C:\Program Files\SQLyog\ssleay32.dll | executable | |
MD5:8BB897754D2A923AB5B08653ABB1617F | SHA256:0F0B76AC19A46A35ACF531BD43B8D7F8B2A38B75D440DD7A24F0ABDC6C84354C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
13
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 2.16.164.106:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1060 | svchost.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?6db8a07497701bb0 | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
1372 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 239.255.255.250:3702 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1372 | svchost.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
1372 | svchost.exe | 2.16.164.106:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
1372 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | unknown |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
1060 | svchost.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |