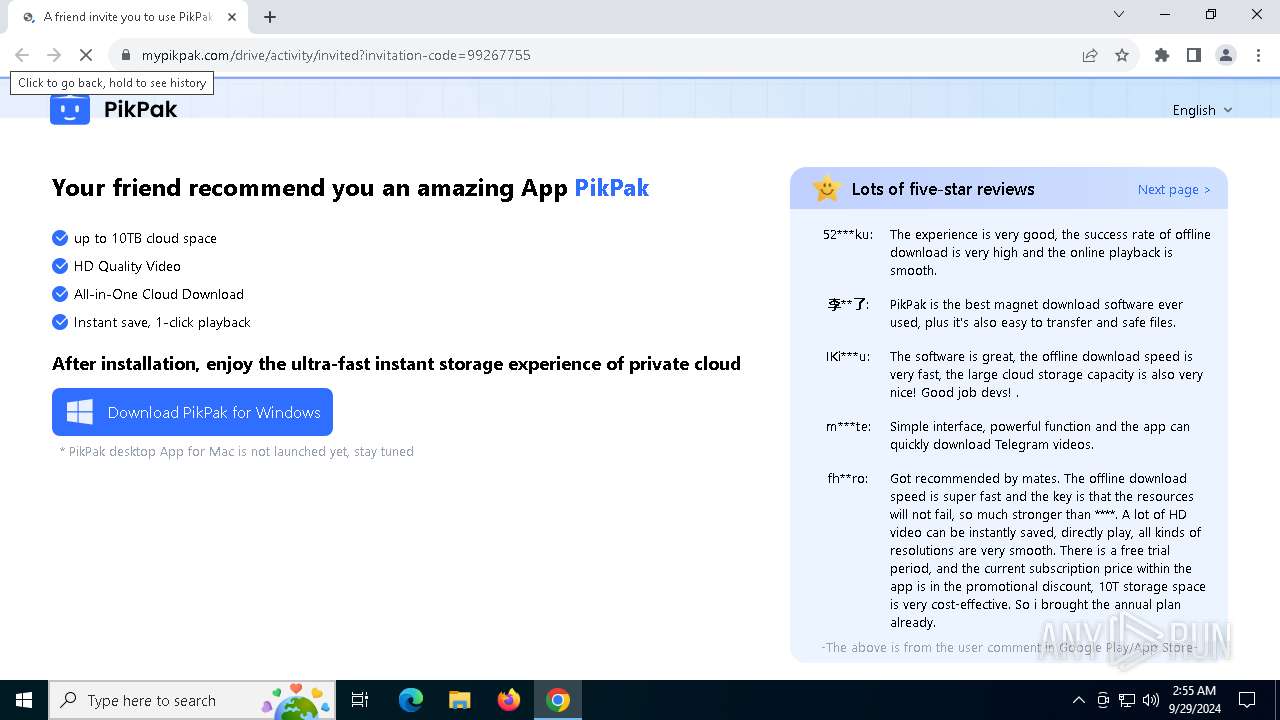
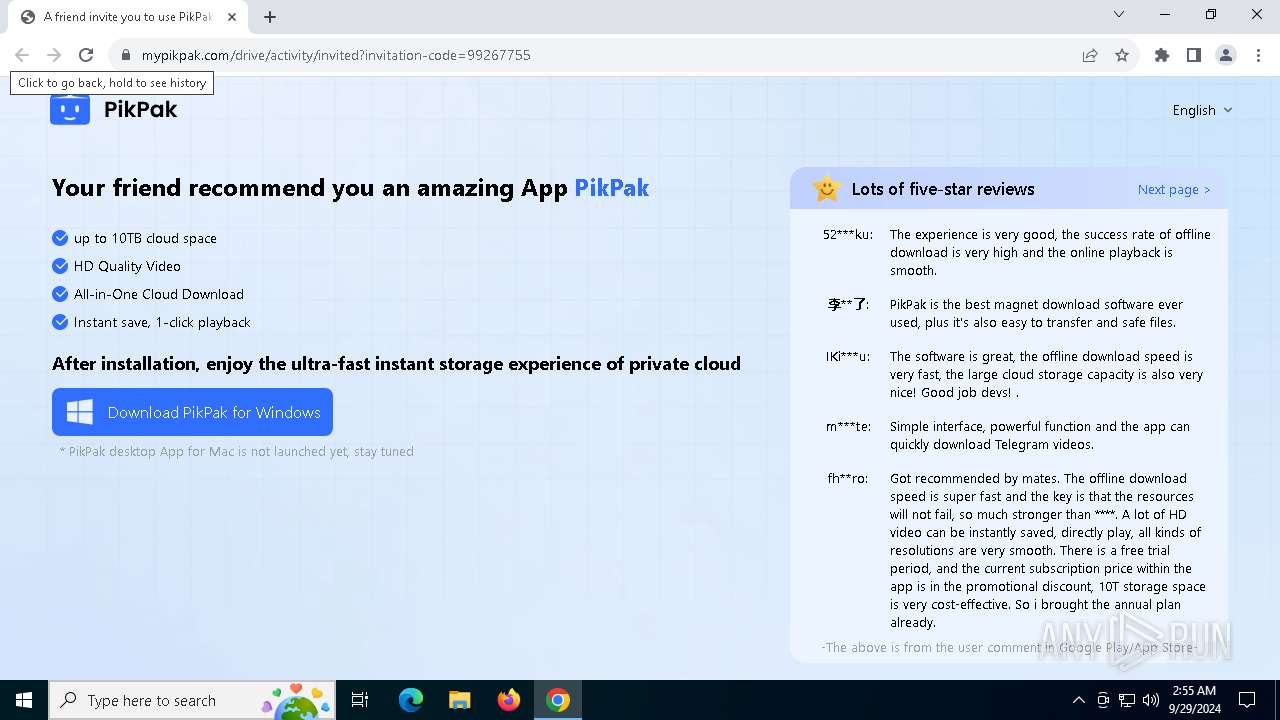
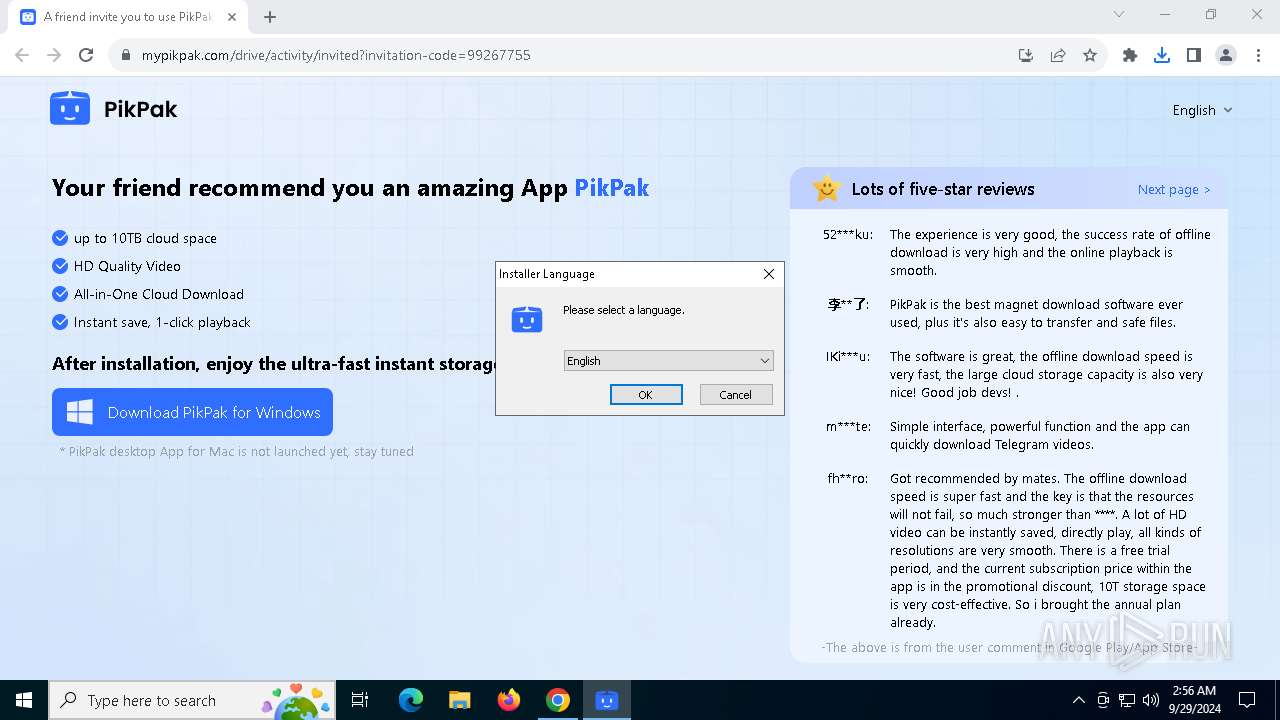
| URL: | https://mypikpak.com/drive/activity/invited?invitation-code=99267755 |
| Full analysis: | https://app.any.run/tasks/cfc270ac-3436-41e6-b183-208ceba67ab7 |
| Verdict: | Malicious activity |
| Analysis date: | September 29, 2024, 02:55:34 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MD5: | A27A10EDAC075F58BF102A2AF5F5B13C |
| SHA1: | DA4FF2E42B96BD34573E1853713D2326CDB4B613 |
| SHA256: | 98BF0D951859FD27EB95FF2BF58256F3E0DD72B99FF957E0BA864C903E66B605 |
| SSDEEP: | 3:N884qSJAkaMLTQERADAYckhF:28uJ+KkD+2F |
MALICIOUS
No malicious indicators.SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
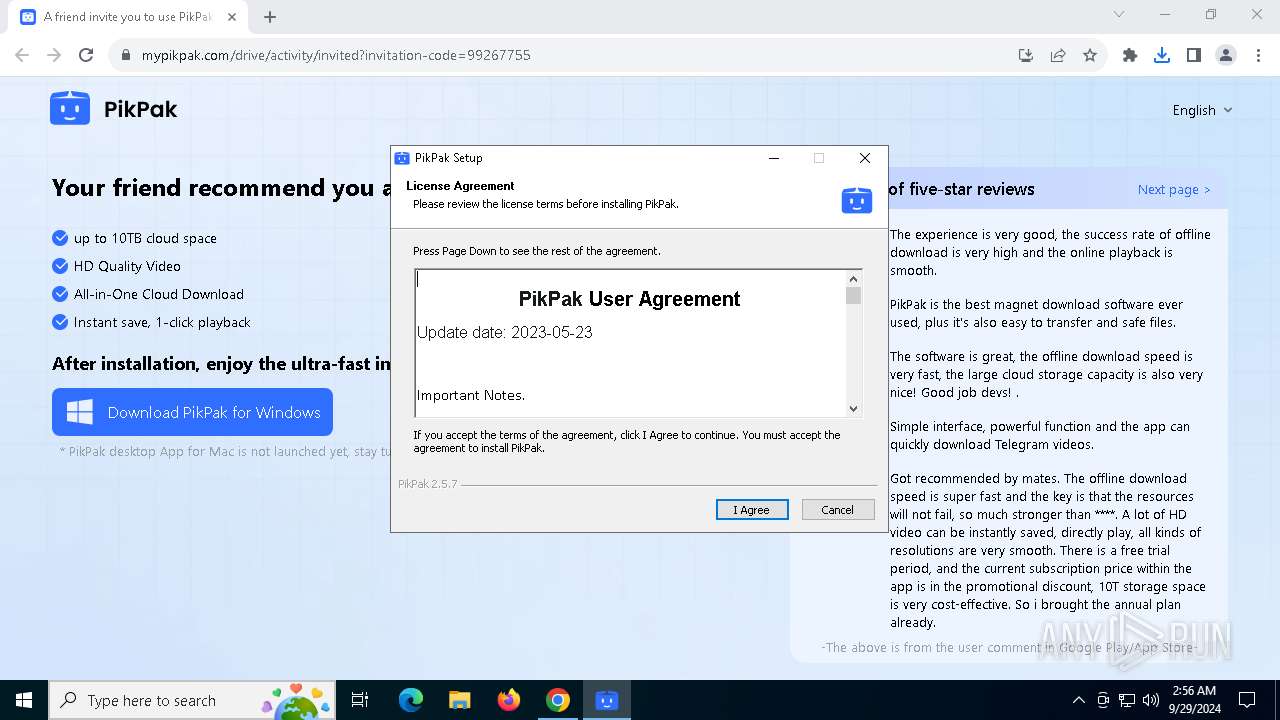
- PikPak-V2.5.7-99267755.exe (PID: 6100)
The process drops C-runtime libraries
- PikPak-V2.5.7-99267755.exe (PID: 6100)
Process drops legitimate windows executable
- PikPak-V2.5.7-99267755.exe (PID: 6100)
Uses NETSH.EXE to add a firewall rule or allowed programs
- PikPak-V2.5.7-99267755.exe (PID: 6100)
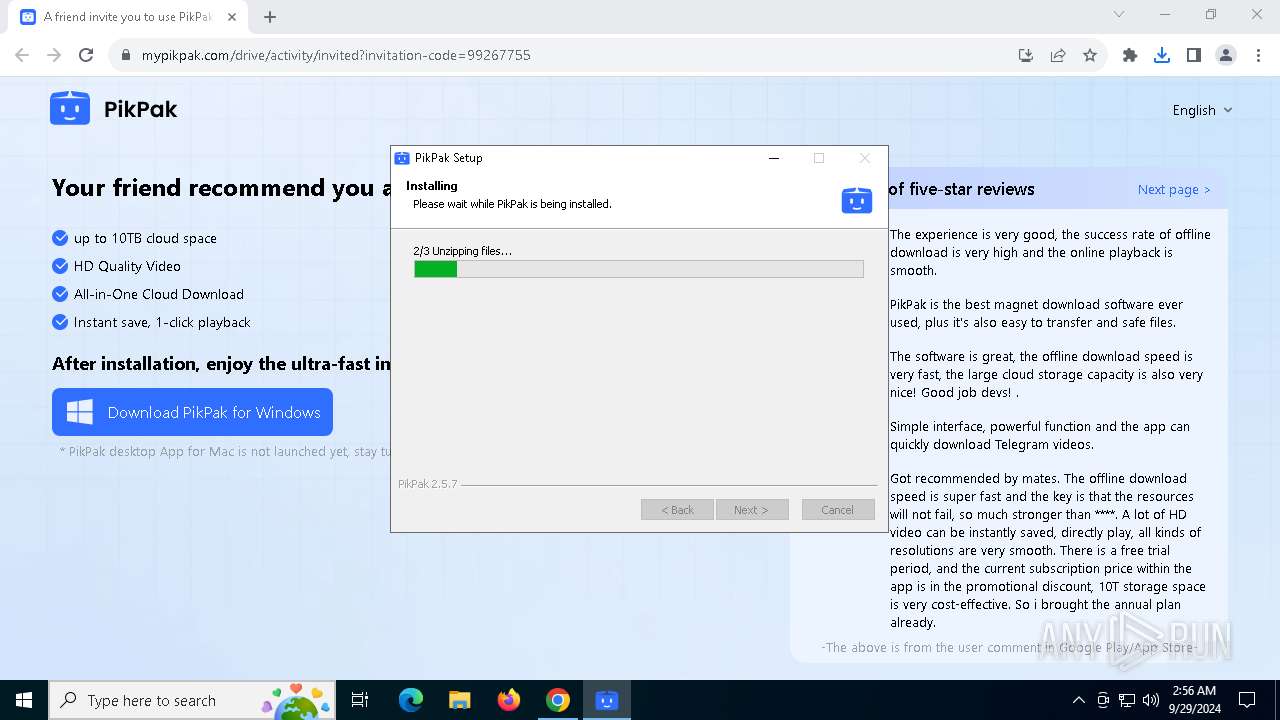
Drops 7-zip archiver for unpacking
- PikPak-V2.5.7-99267755.exe (PID: 6100)
Executable content was dropped or overwritten
- PikPak-V2.5.7-99267755.exe (PID: 6100)
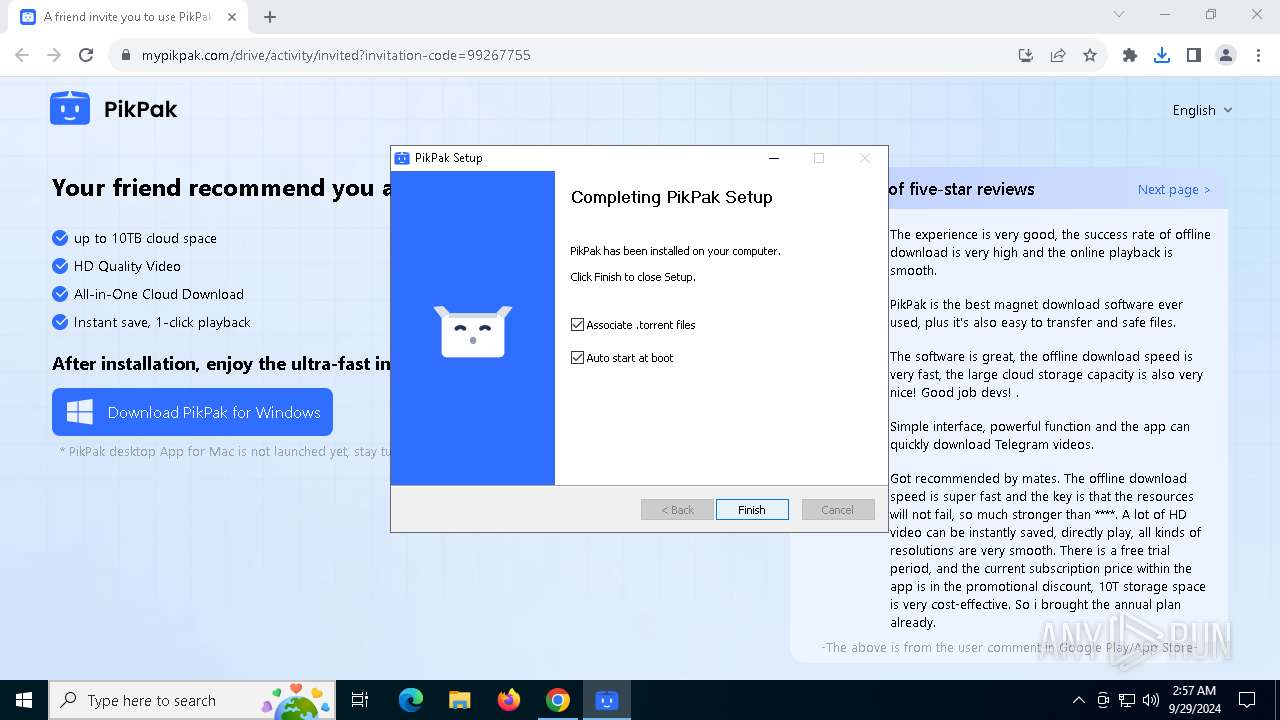
Application launched itself
- PikPak.exe (PID: 6228)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- PikPak-V2.5.7-99267755.exe (PID: 6100)
INFO
Application launched itself
- chrome.exe (PID: 5940)
Executable content was dropped or overwritten
- chrome.exe (PID: 5940)
- chrome.exe (PID: 7524)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
181
Monitored processes
41
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 492 | netsh.exe advfirewall firewall add rule name="DownloadServer for PikPak" dir=in action=allow program="C:\Program Files (x86)\PikPak\resources\bin\sdk\downloadserver.exe" enable=yes | C:\Windows\SysWOW64\netsh.exe | — | PikPak-V2.5.7-99267755.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1920 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=9 --mojo-platform-channel-handle=4456 --field-trial-handle=1876,i,18159609089606828871,13533641631570409302,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2448 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5576 --field-trial-handle=1876,i,18159609089606828871,13533641631570409302,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2872 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=2100 --field-trial-handle=1876,i,18159609089606828871,13533641631570409302,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:3 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 3440 | C:\WINDOWS\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3528 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3580 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --lang=en-US --service-sandbox-type=icon_reader --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5204 --field-trial-handle=1876,i,18159609089606828871,13533641631570409302,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 4036 | "C:\Windows\System32\explorer.exe" /e,PikPak.exe | C:\Windows\SysWOW64\explorer.exe | — | PikPak-V2.5.7-99267755.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4248 | "C:\Users\admin\Downloads\PikPak-V2.5.7-99267755.exe" | C:\Users\admin\Downloads\PikPak-V2.5.7-99267755.exe | — | chrome.exe | |||||||||||
User: admin Company: PIKCLOUD PTE.LTD. Integrity Level: MEDIUM Description: PikPak Exit code: 3221226540 Version: 2.5.7.4835 Modules
| |||||||||||||||
| 4668 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4632 --field-trial-handle=1876,i,18159609089606828871,13533641631570409302,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
18 857
Read events
18 790
Write events
42
Delete events
25
Modification events
| (PID) Process: | (5940) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (5940) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (5940) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (5940) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (5940) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (2448) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 010000000000000026893F321B12DB01 | |||
| (PID) Process: | (5940) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C1I |
Value: 1 | |||
| (PID) Process: | (5940) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C2I |
Value: 1 | |||
| (PID) Process: | (5940) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C7I |
Value: 1 | |||
| (PID) Process: | (5940) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C1S |
Value: 1 | |||
Executable files
258
Suspicious files
300
Text files
511
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5940 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF3f4ff2.TMP | — | |
MD5:— | SHA256:— | |||
| 5940 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5940 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF3f5011.TMP | — | |
MD5:— | SHA256:— | |||
| 5940 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF3f5011.TMP | — | |
MD5:— | SHA256:— | |||
| 5940 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5940 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5940 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF3f5011.TMP | — | |
MD5:— | SHA256:— | |||
| 5940 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF3f5011.TMP | — | |
MD5:— | SHA256:— | |||
| 5940 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5940 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
34
TCP/UDP connections
95
DNS requests
82
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
8 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6852 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2064 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1076 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adan7kcukgedhjqx7qv26ki2oerq_2024.9.25.2/kiabhabjdbkjdpjbpigfodbdjmbglcoo_2024.09.25.02_all_actdncfqjoiiwhxqc27jt6lspq3a.crx3 | unknown | — | — | whitelisted |
1076 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adan7kcukgedhjqx7qv26ki2oerq_2024.9.25.2/kiabhabjdbkjdpjbpigfodbdjmbglcoo_2024.09.25.02_all_actdncfqjoiiwhxqc27jt6lspq3a.crx3 | unknown | — | — | whitelisted |
2064 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1076 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adan7kcukgedhjqx7qv26ki2oerq_2024.9.25.2/kiabhabjdbkjdpjbpigfodbdjmbglcoo_2024.09.25.02_all_actdncfqjoiiwhxqc27jt6lspq3a.crx3 | unknown | — | — | whitelisted |
1076 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adan7kcukgedhjqx7qv26ki2oerq_2024.9.25.2/kiabhabjdbkjdpjbpigfodbdjmbglcoo_2024.09.25.02_all_actdncfqjoiiwhxqc27jt6lspq3a.crx3 | unknown | — | — | whitelisted |
1076 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjhkYWYwZDctOTExOS00MGQ5LTgyNjAtN2FlY2ZjMDg0NmNj/1.0.0.17_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | whitelisted |
1076 | svchost.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/AMpg5-cnrANo_2018.8.8.0/2018.8.8.0_win64_win_third_party_module_list.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
8 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6852 | svchost.exe | 40.126.32.136:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6852 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5940 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2872 | chrome.exe | 64.233.166.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
2872 | chrome.exe | 170.33.96.94:443 | mypikpak.com | Alibaba.com Singapore E-Commerce Private Limited | SG | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
mypikpak.com |
| unknown |
accounts.google.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
res-etl-ssl.mypikpak.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2872 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] An application monitoring request to sentry .io |
2872 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] An application monitoring request to sentry .io |
2872 | chrome.exe | Misc activity | ET INFO DNS Query to Alibaba Cloud CDN Domain (aliyuncs .com) |
2872 | chrome.exe | Misc activity | ET INFO DNS Query to Alibaba Cloud CDN Domain (aliyuncs .com) |
2872 | chrome.exe | Misc activity | ET INFO Observed Alibaba Cloud CDN Domain (aliyuncs .com in TLS SNI) |
2872 | chrome.exe | Misc activity | ET INFO Observed Alibaba Cloud CDN Domain (aliyuncs .com in TLS SNI) |
2872 | chrome.exe | Misc activity | ET INFO Observed Alibaba Cloud CDN Domain (aliyuncs .com in TLS SNI) |