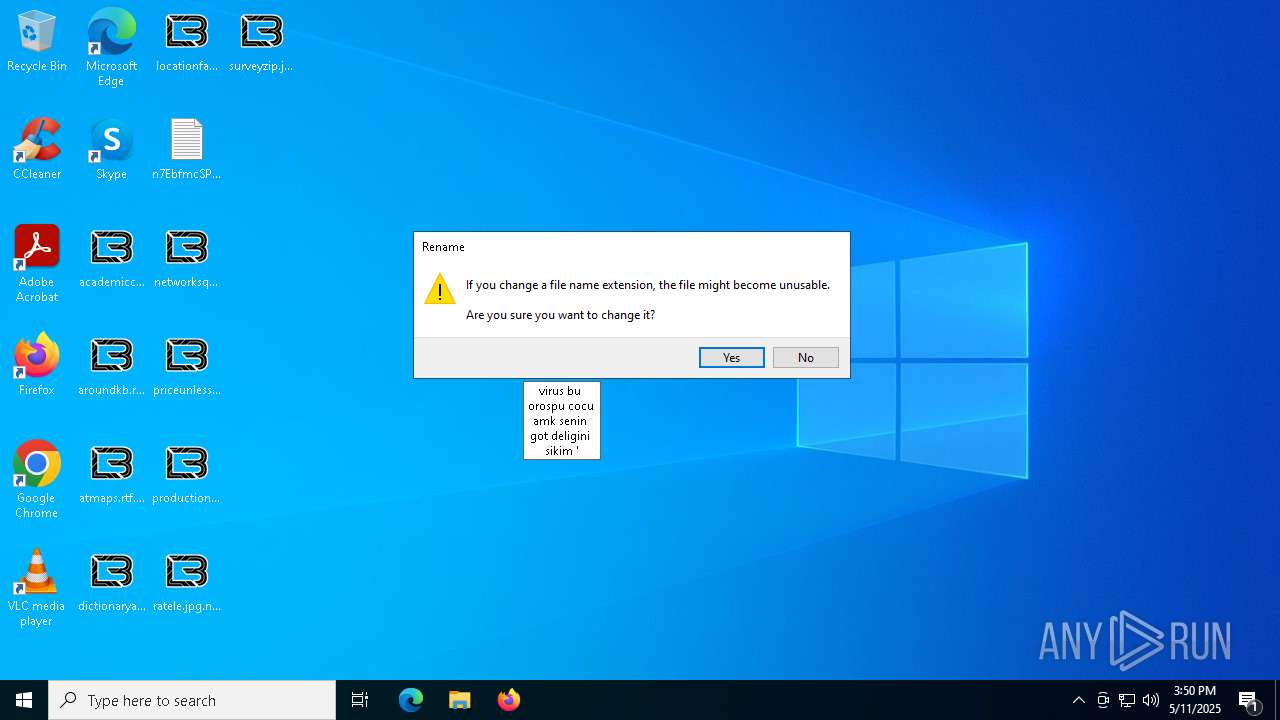
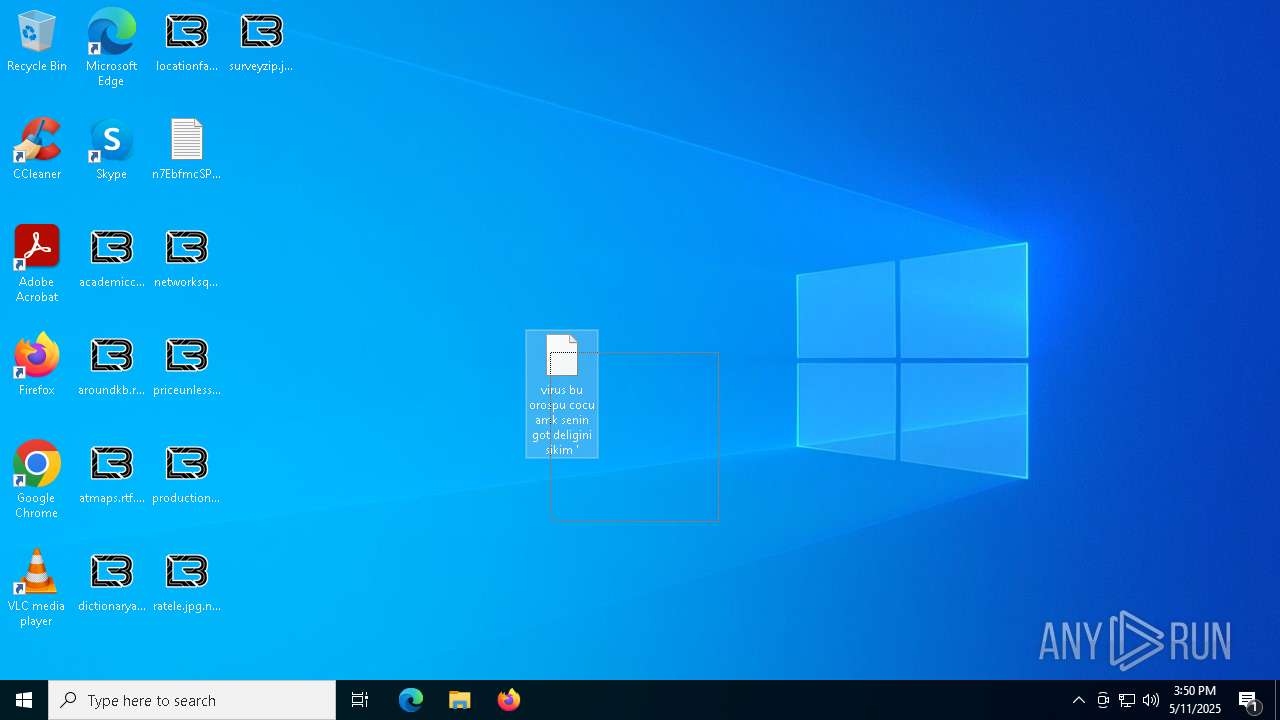
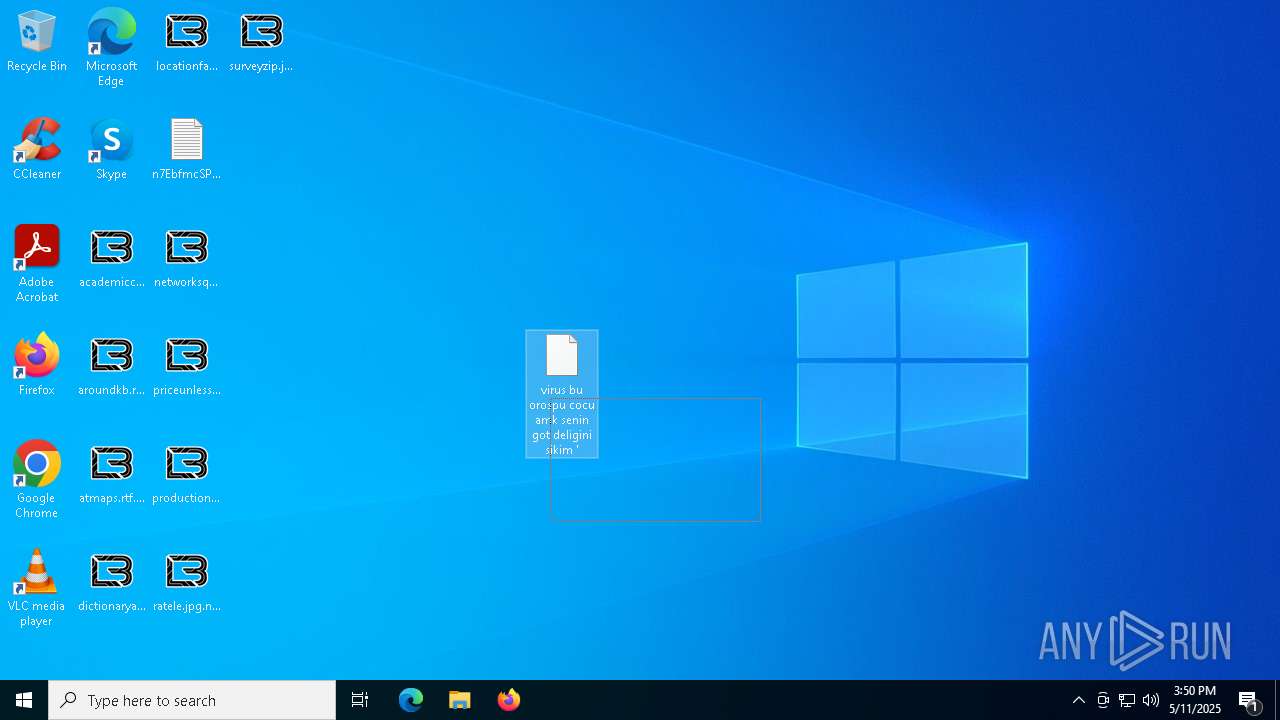
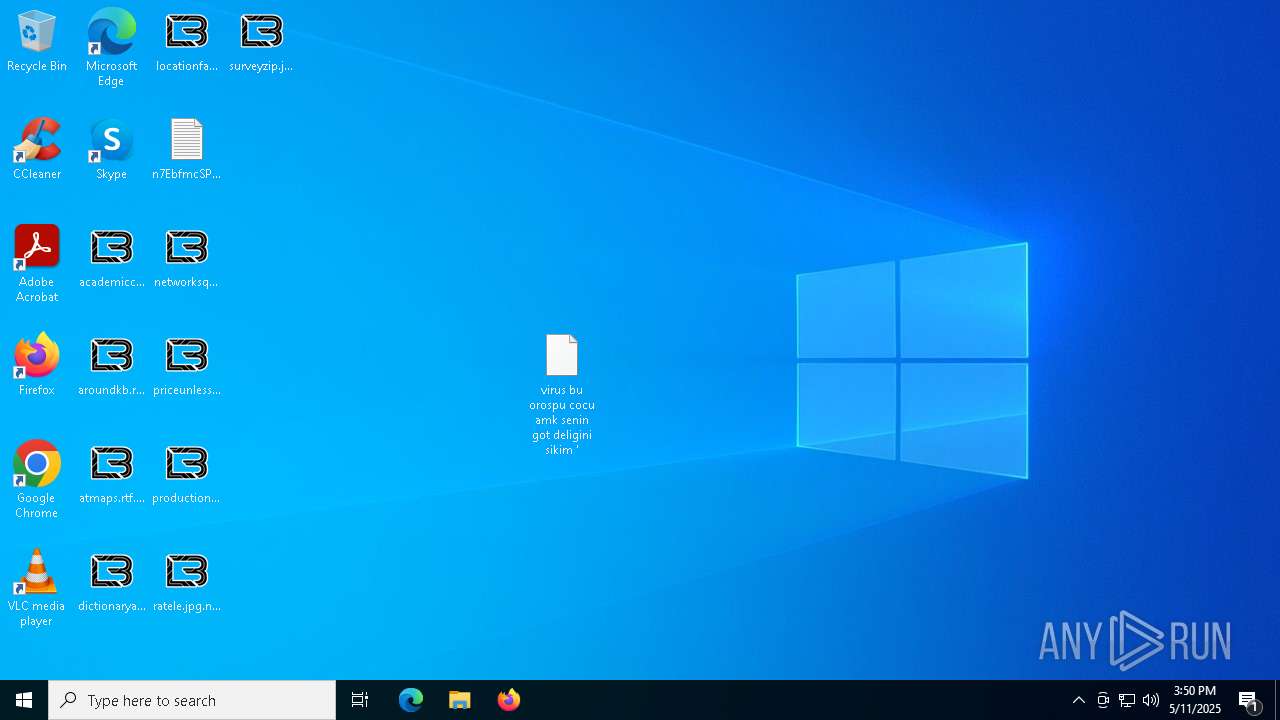
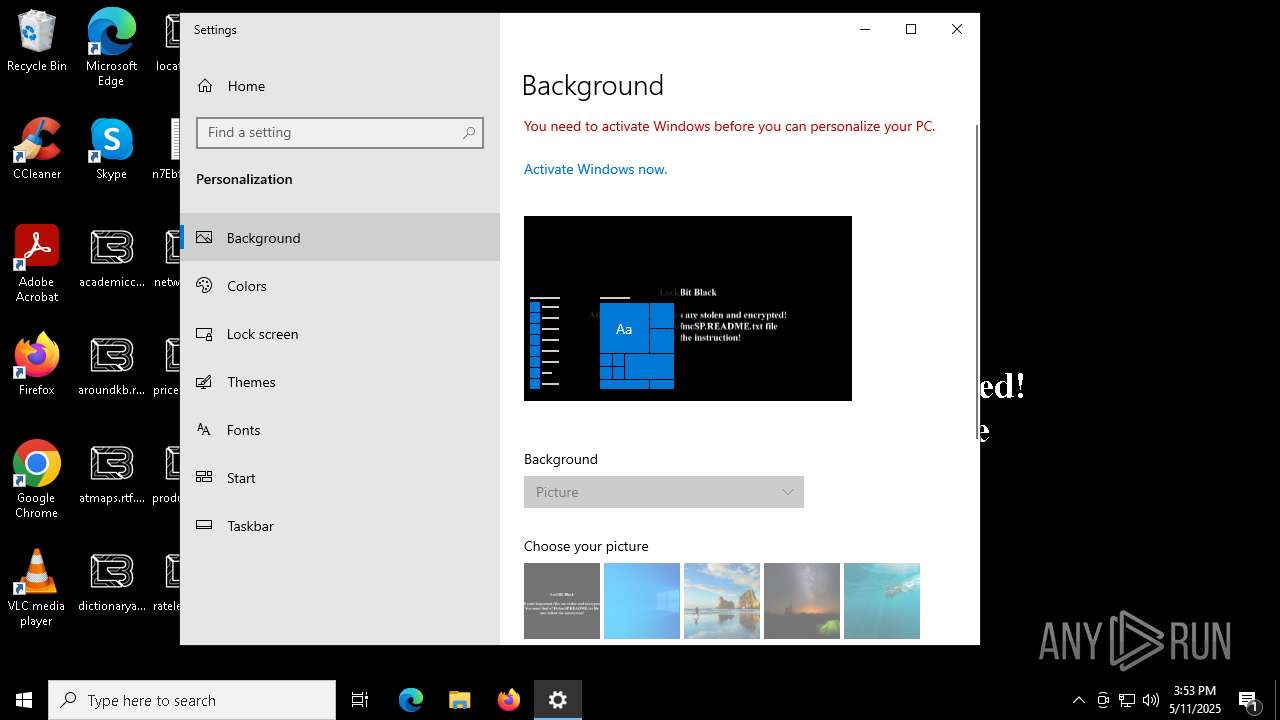
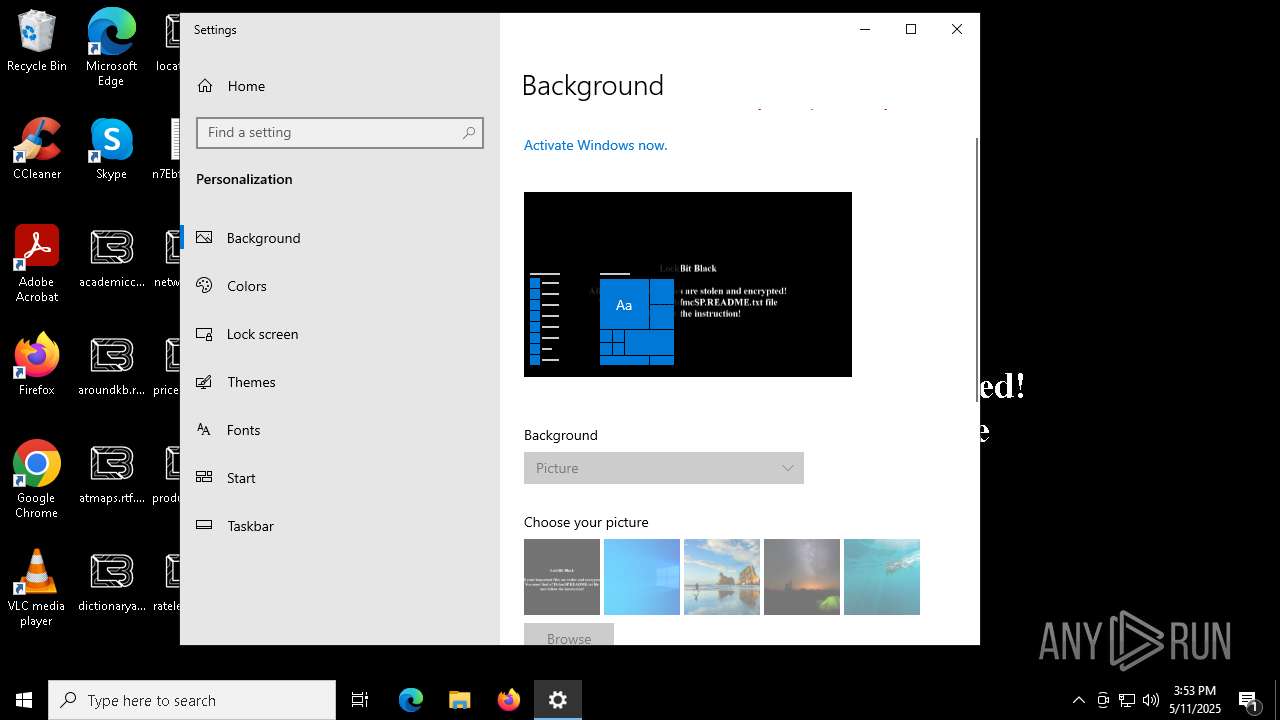
| File name: | ejjSND0.exe |
| Full analysis: | https://app.any.run/tasks/28520f5b-5be7-4edb-a114-0b35616a9861 |
| Verdict: | Malicious activity |
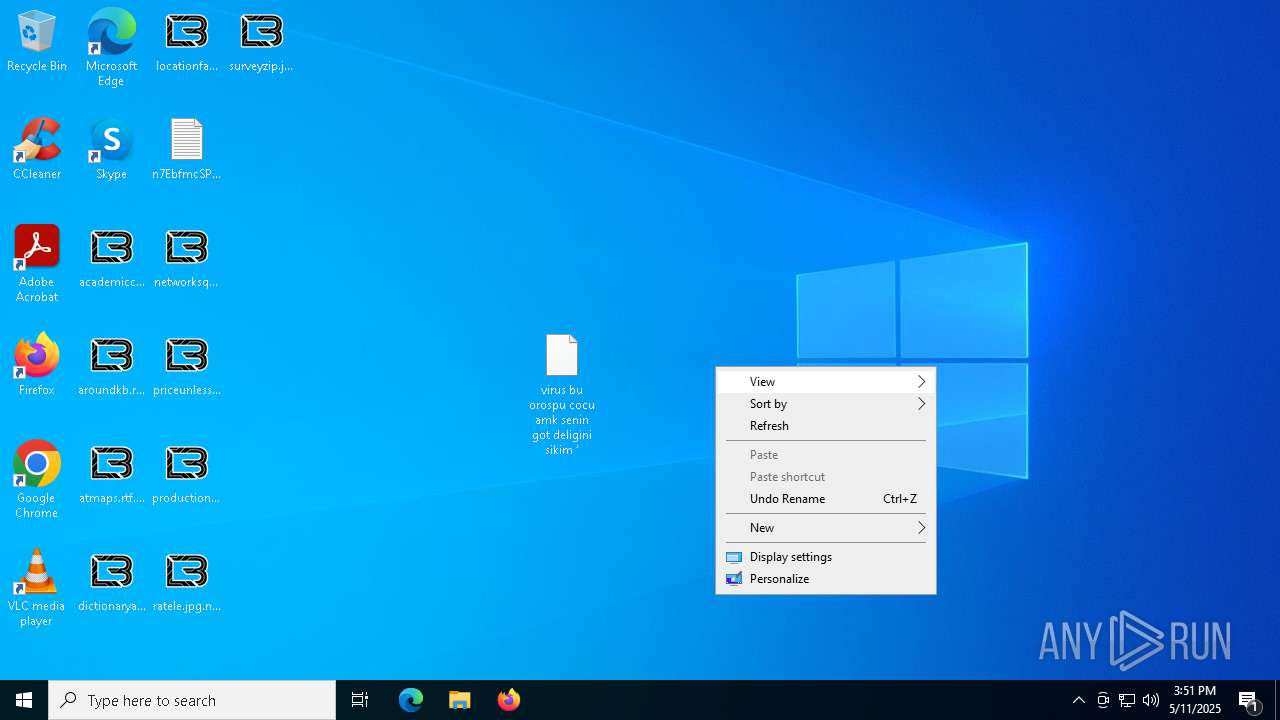
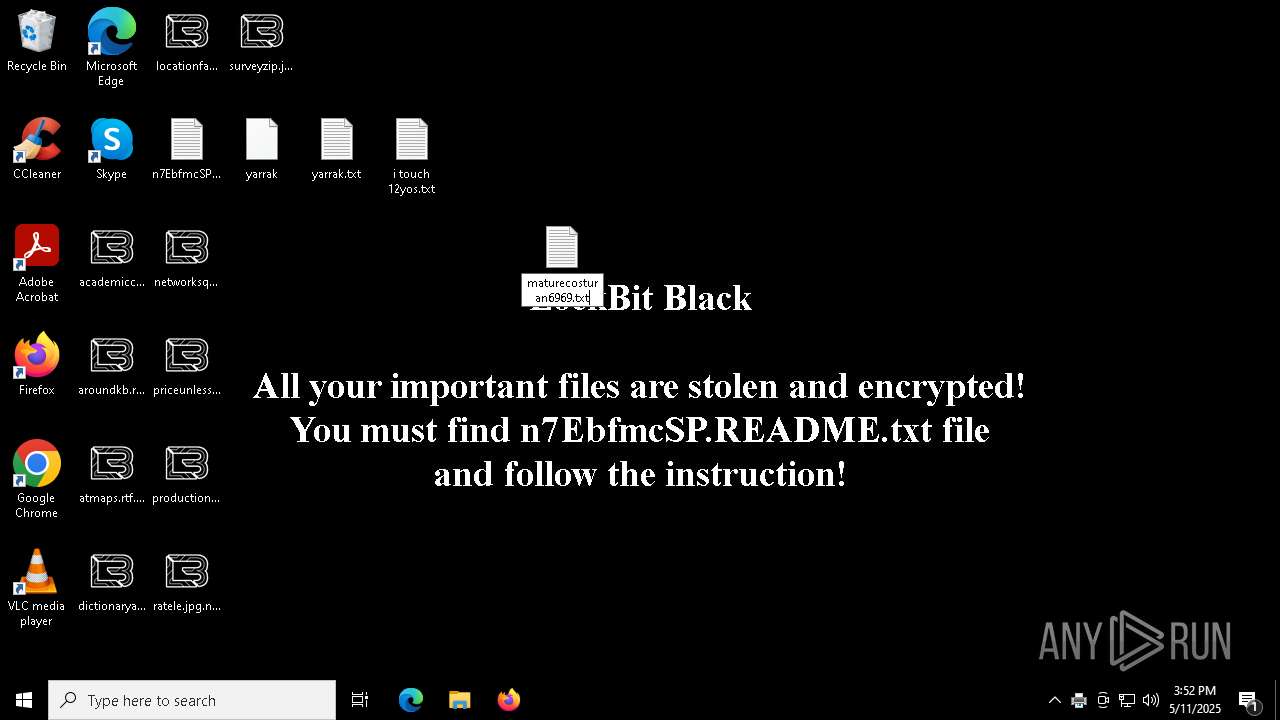
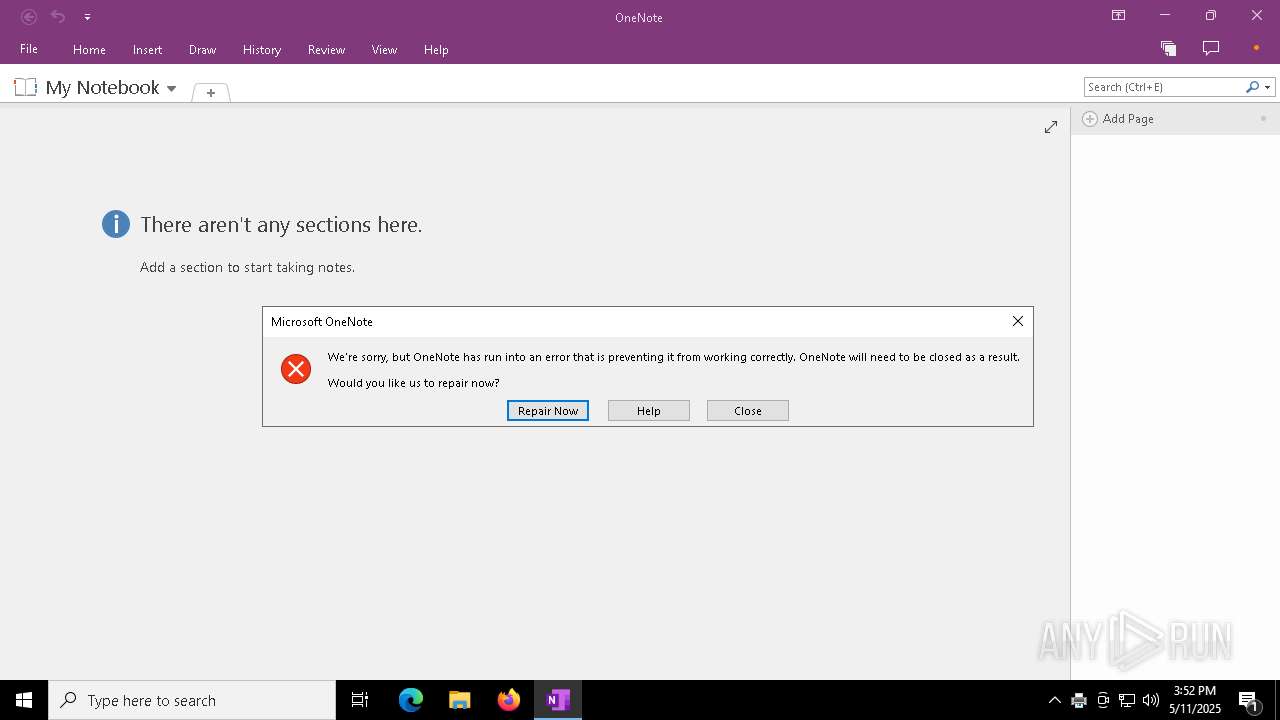
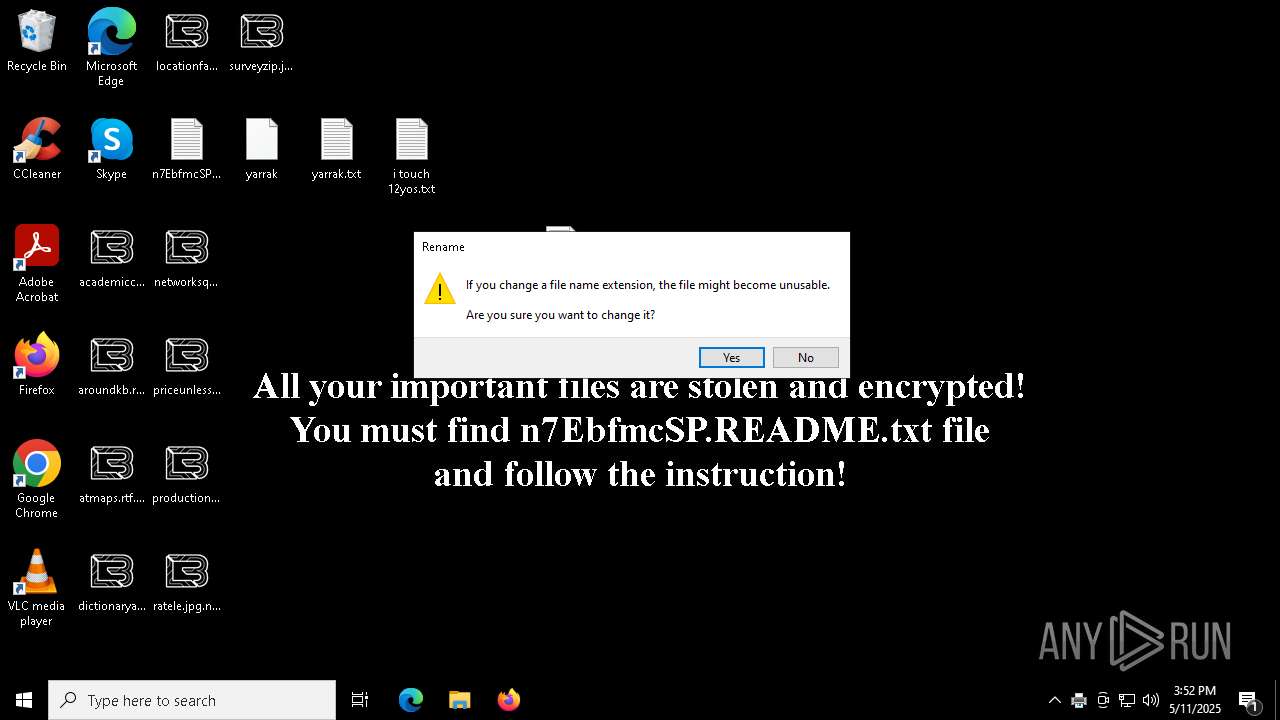
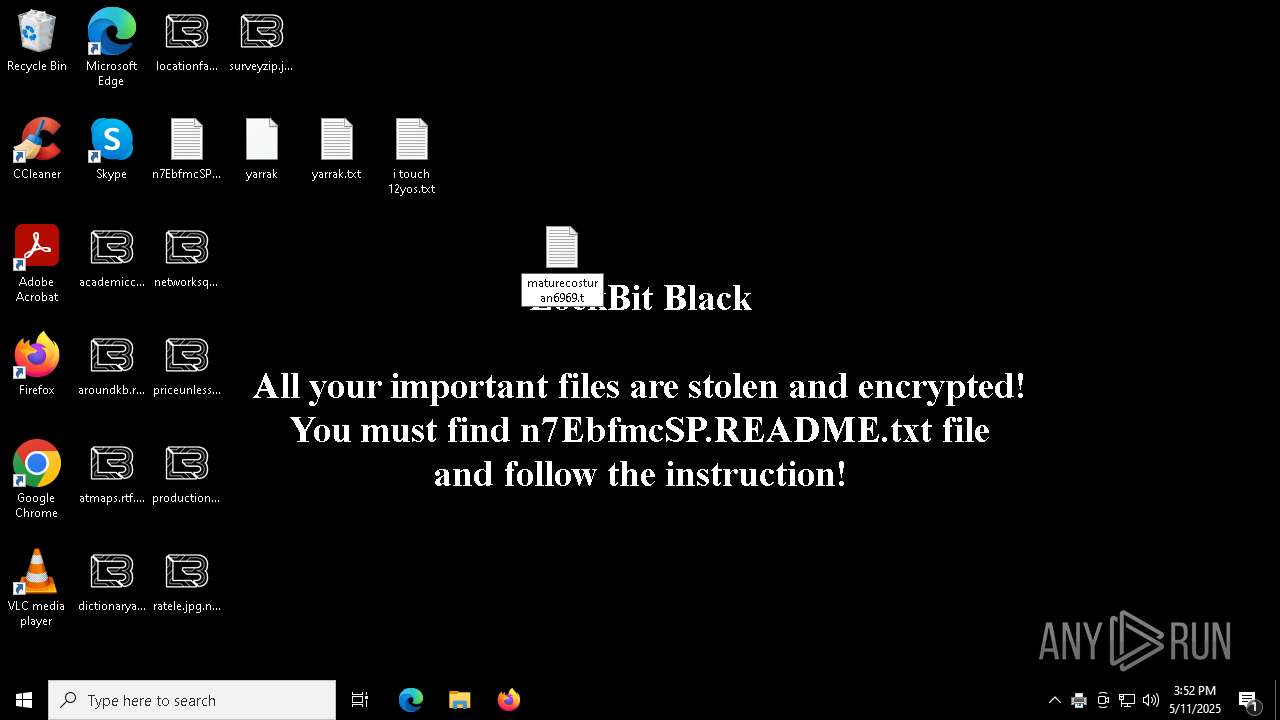
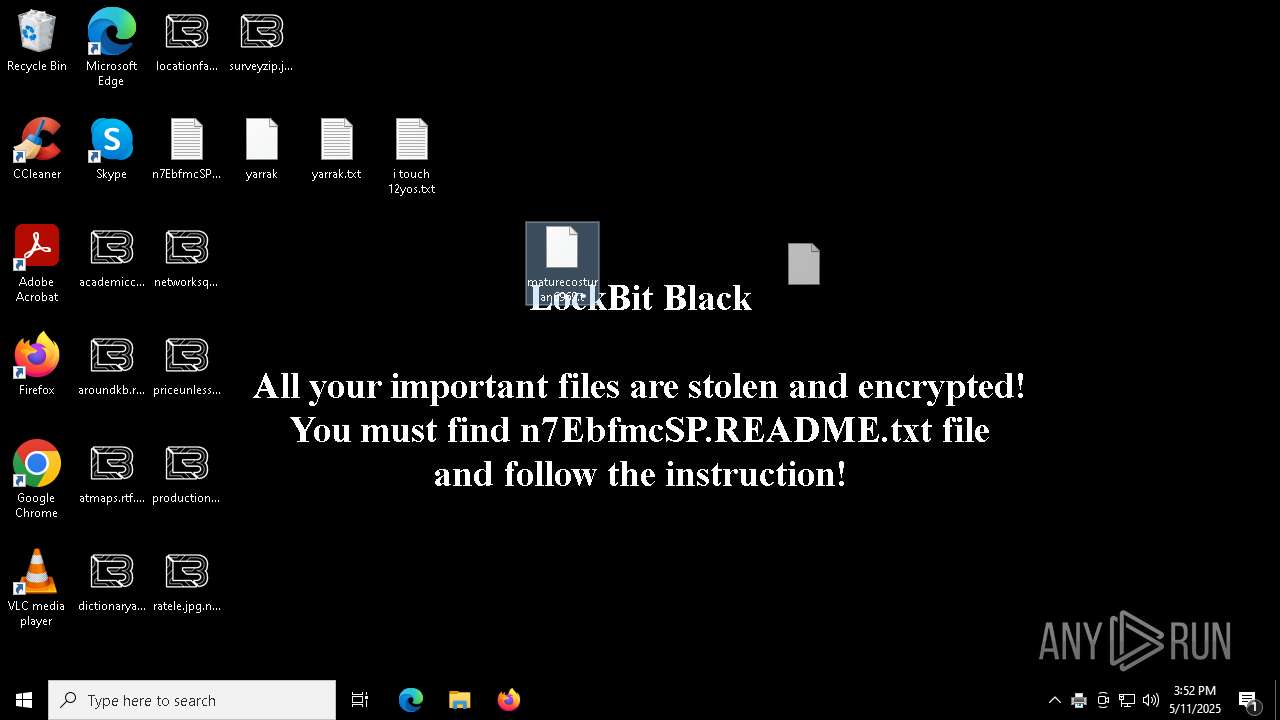
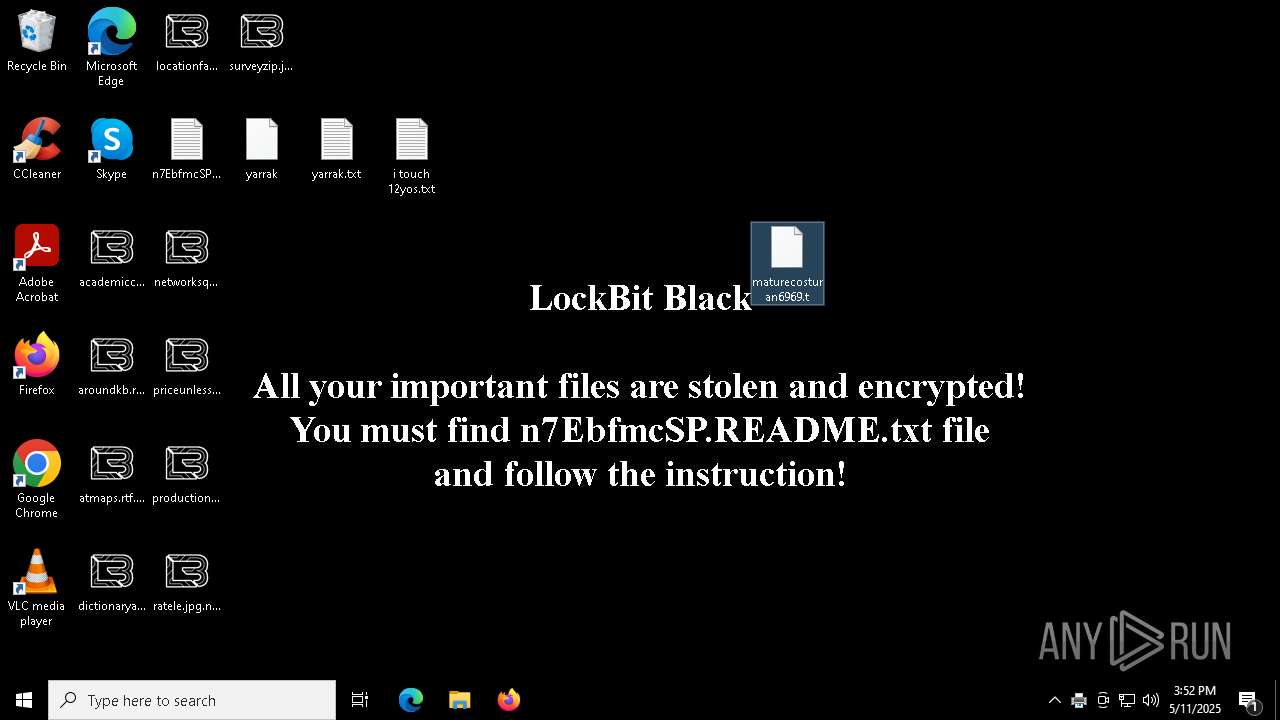
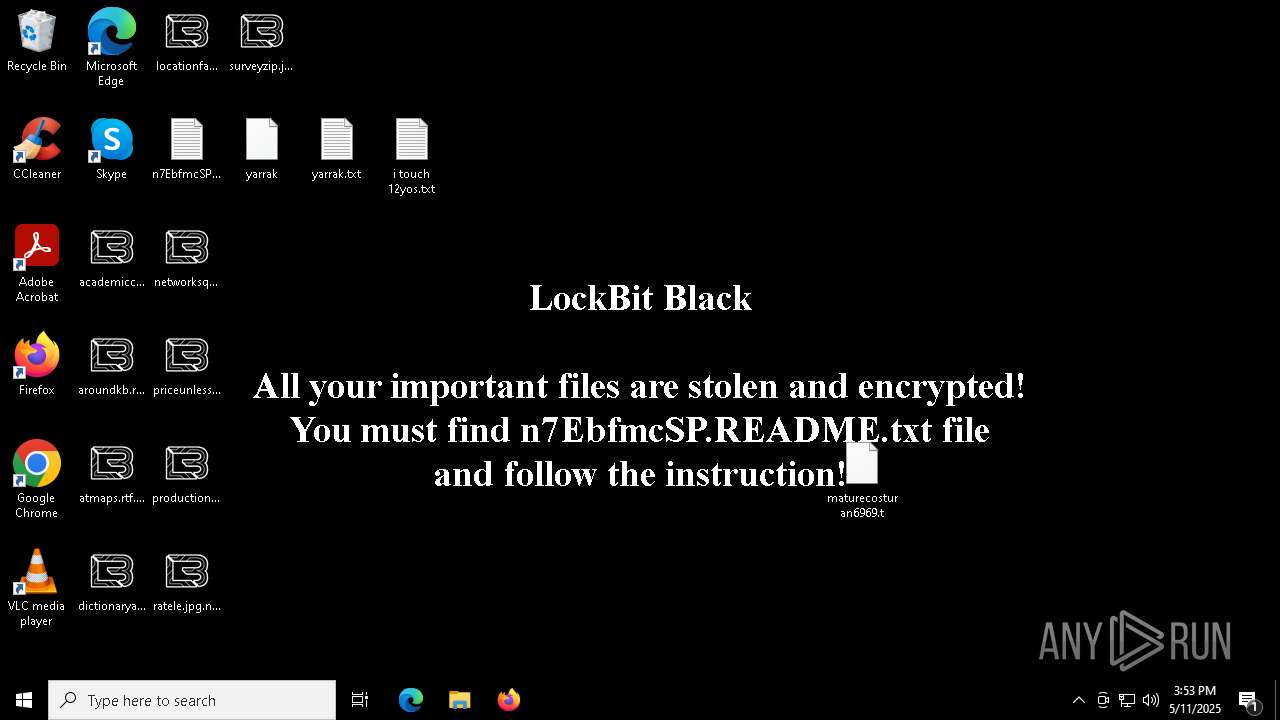
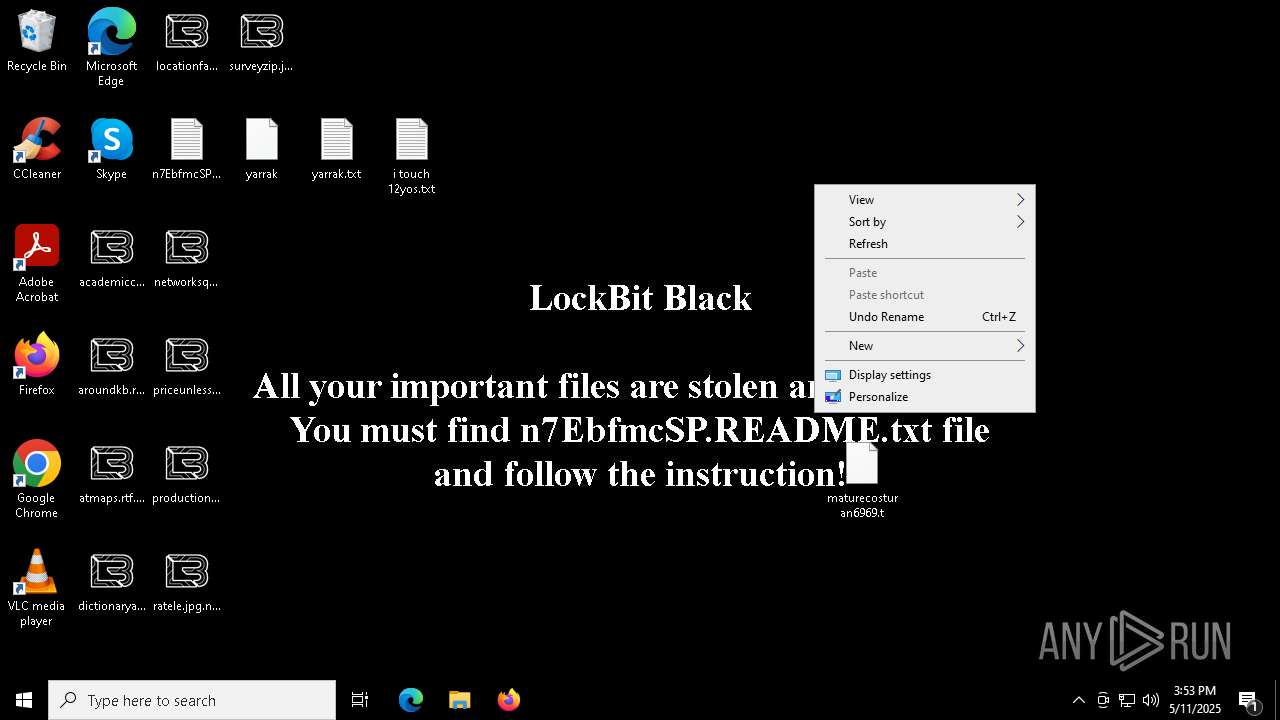
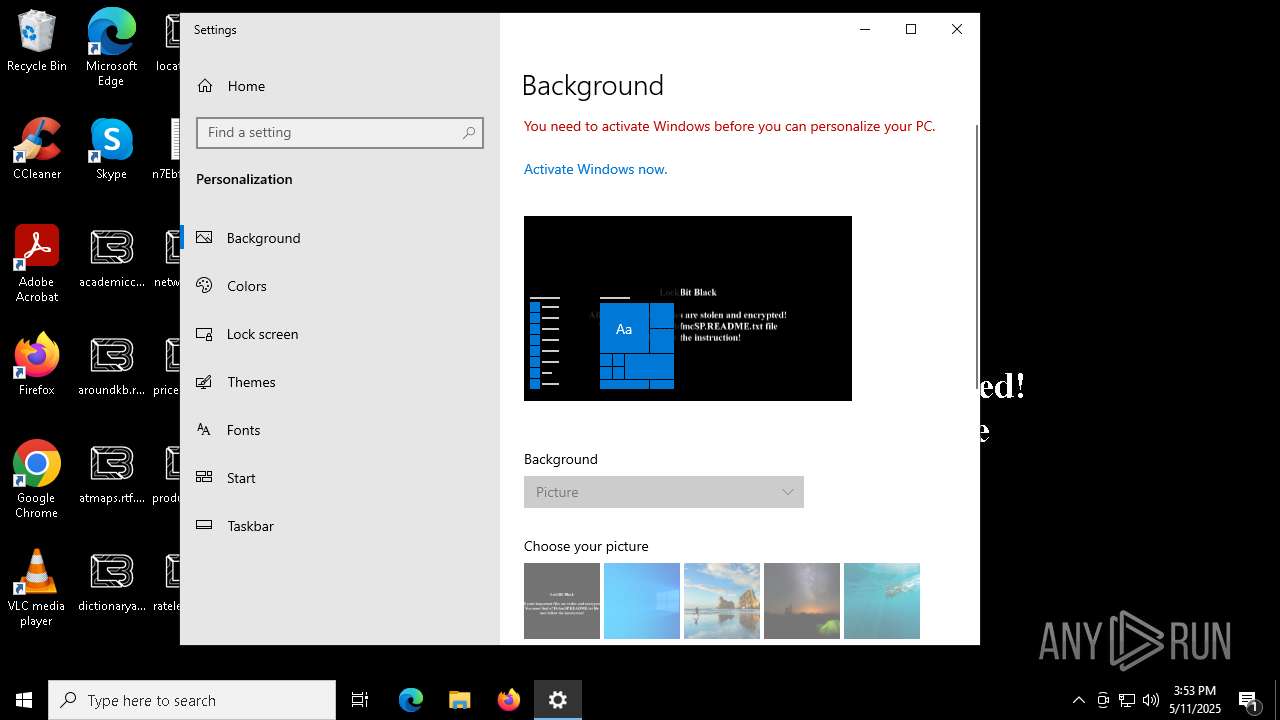
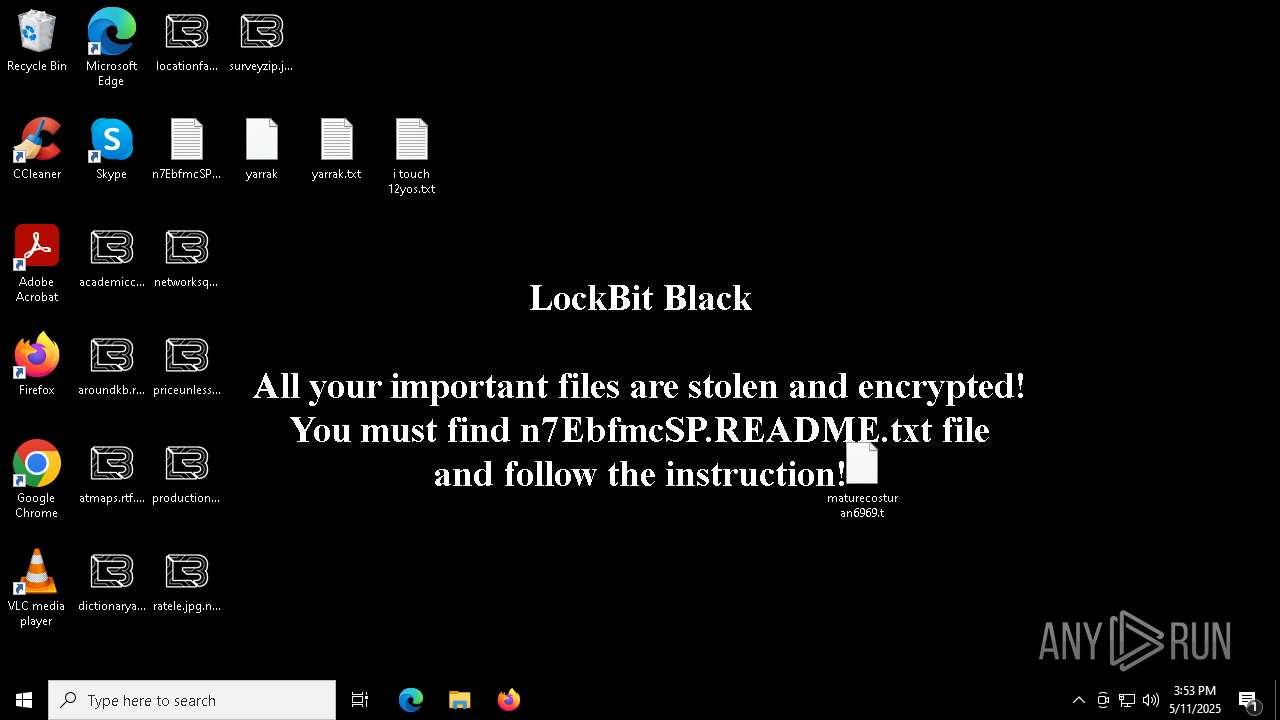
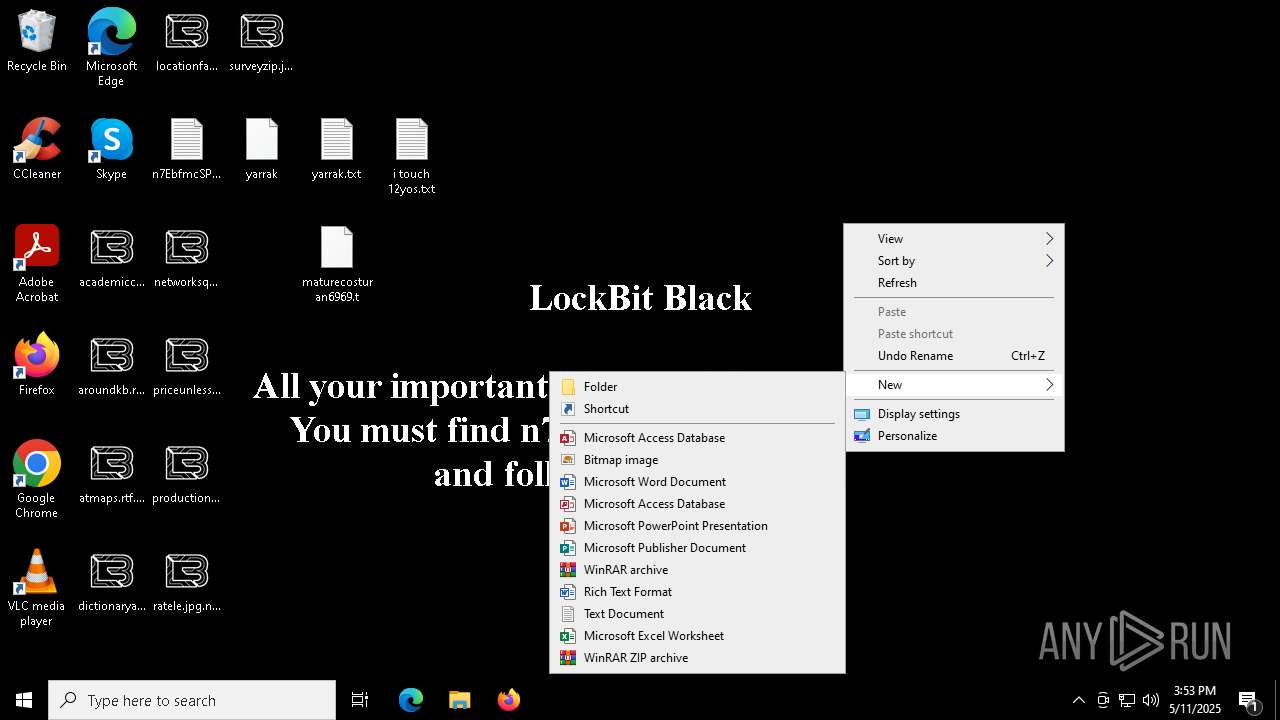
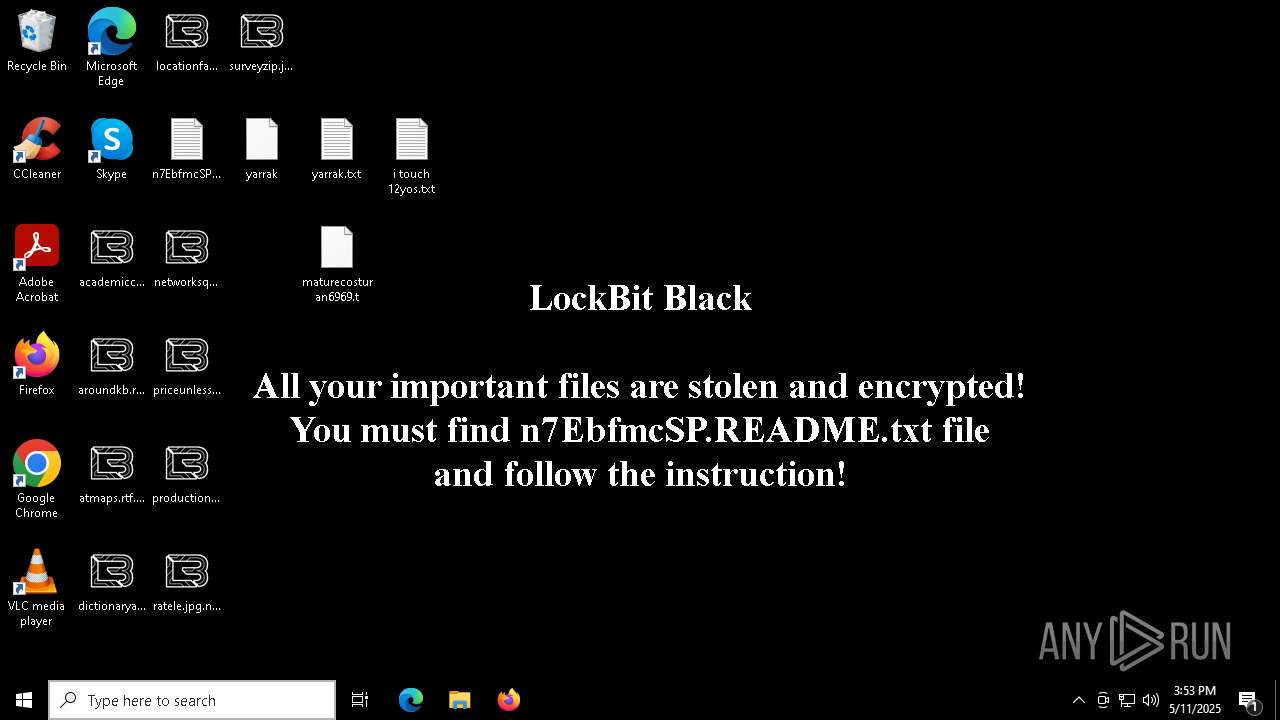
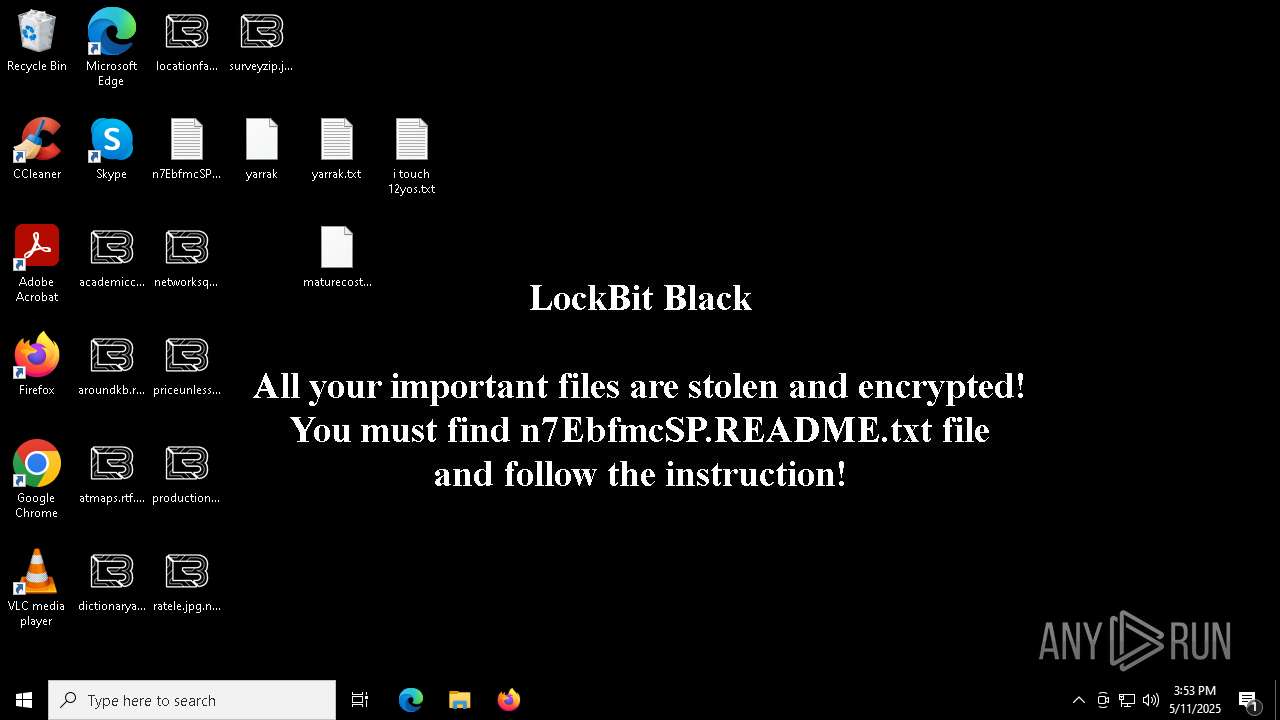
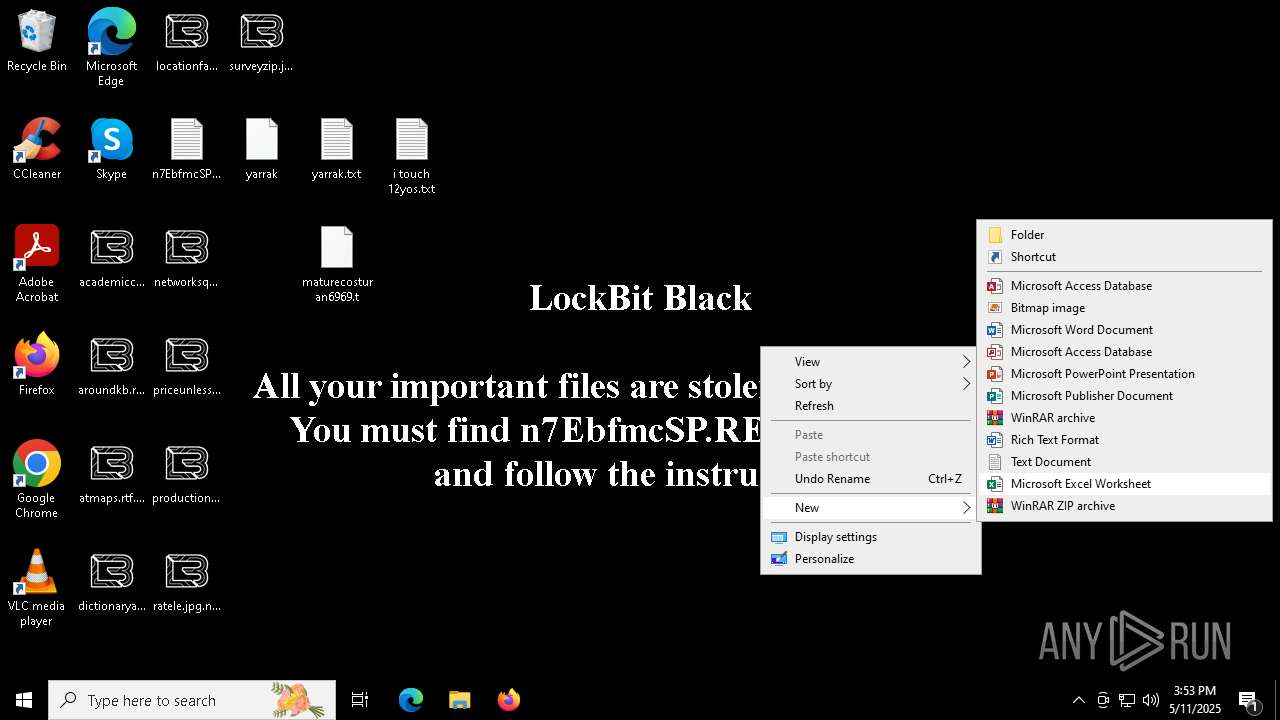
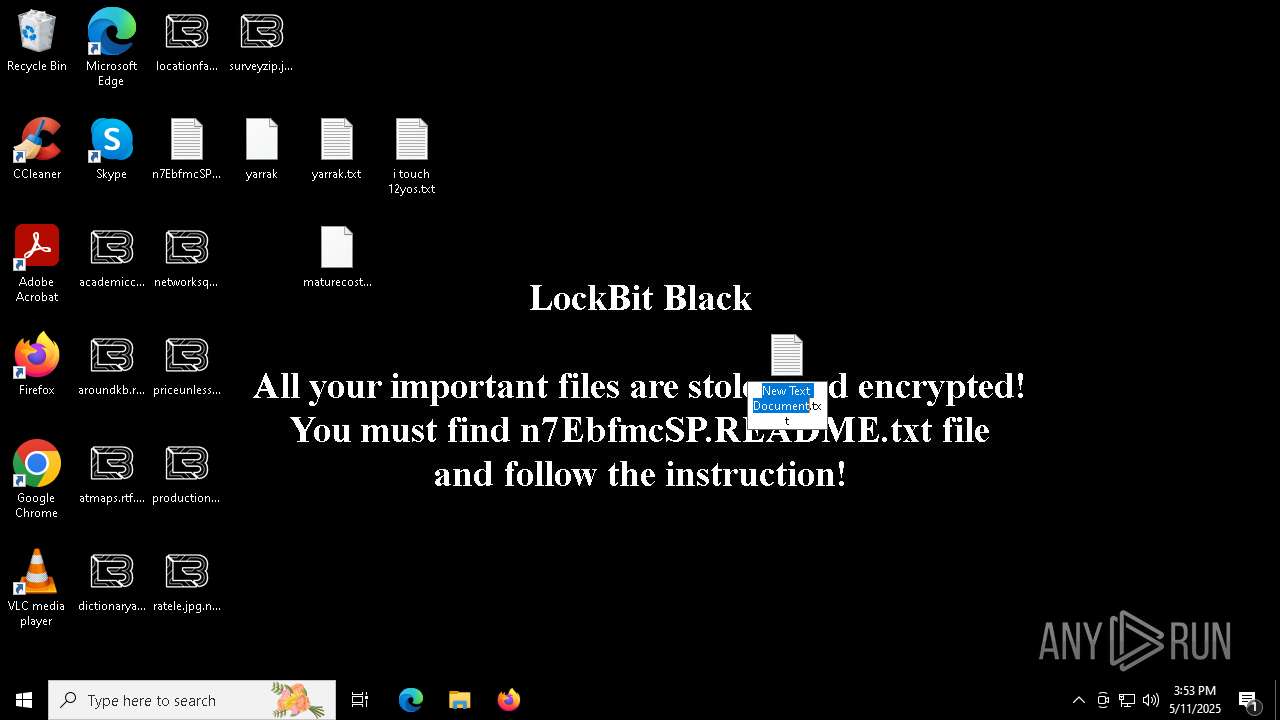
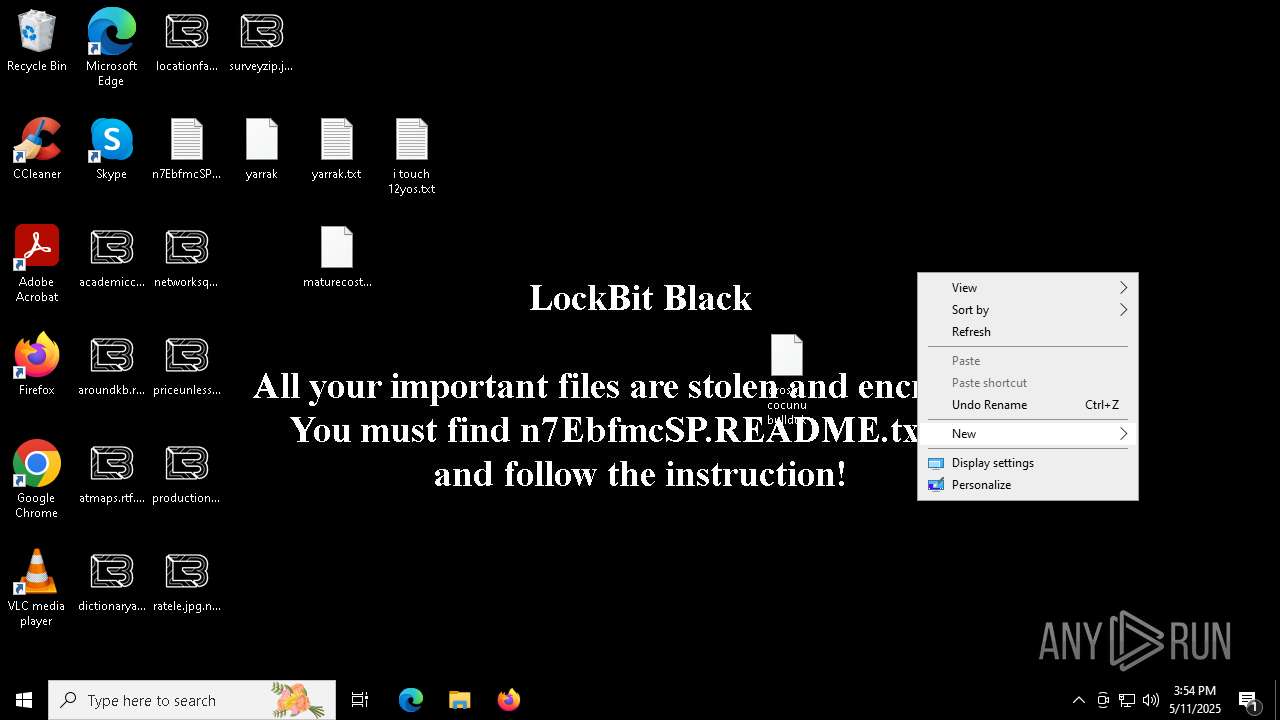
| Threats: | LockBit, a ransomware variant, encrypts data on infected machines, demanding a ransom payment for decryption. Used in targeted attacks, It's a significant risk to organizations. |
| Analysis date: | May 11, 2025, 15:49:18 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | CC869018E9DC4F90CFBCED8990300860 |
| SHA1: | 73FB7A5B04AE90ED99277244F5A69BB39D989369 |
| SHA256: | 98AAD770C17FFFAD072FEF7638EDA3E4500657E5E2F16093F64E2B972B0B8FE7 |
| SSDEEP: | 3072:smhXodguLP/5qUpfDT6zT73ZosetBoF8NoTn9SAP:kKzfetw8NoTno |
MALICIOUS
Known privilege escalation attack
- dllhost.exe (PID: 7552)
[YARA] LockBit is detected
- ejjSND0.exe (PID: 7600)
RANSOMWARE has been detected
- ejjSND0.exe (PID: 7600)
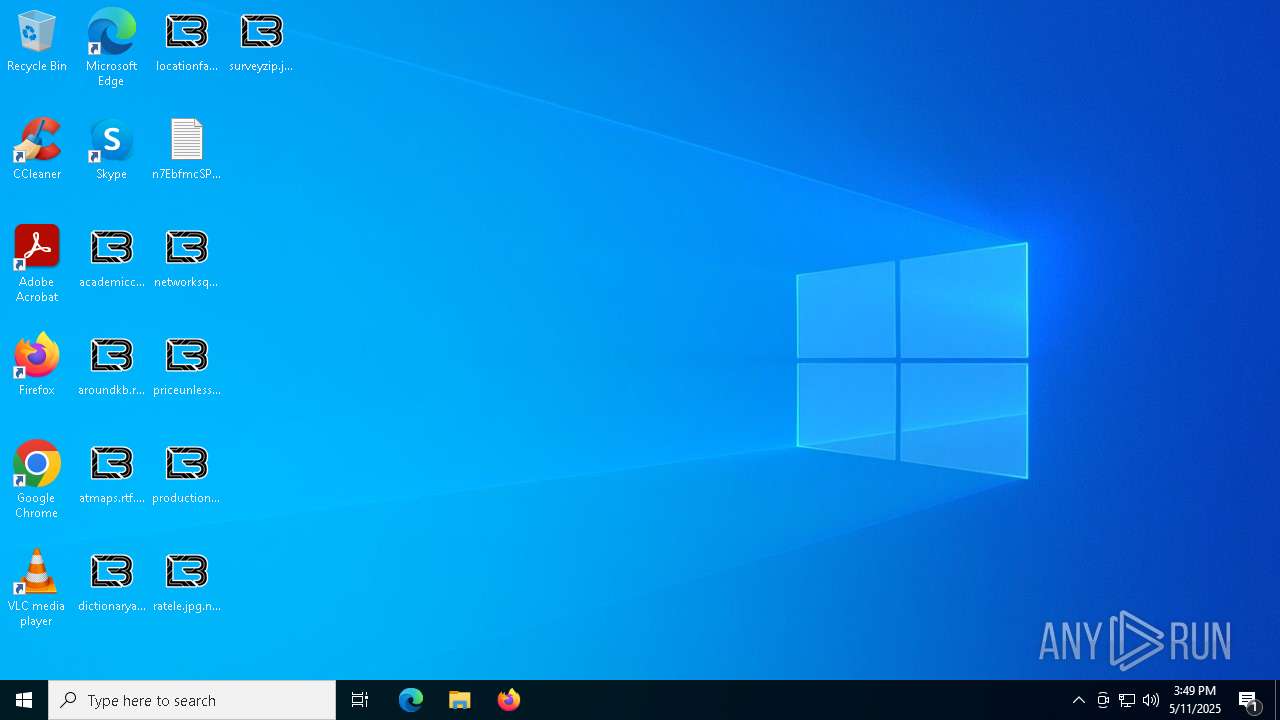
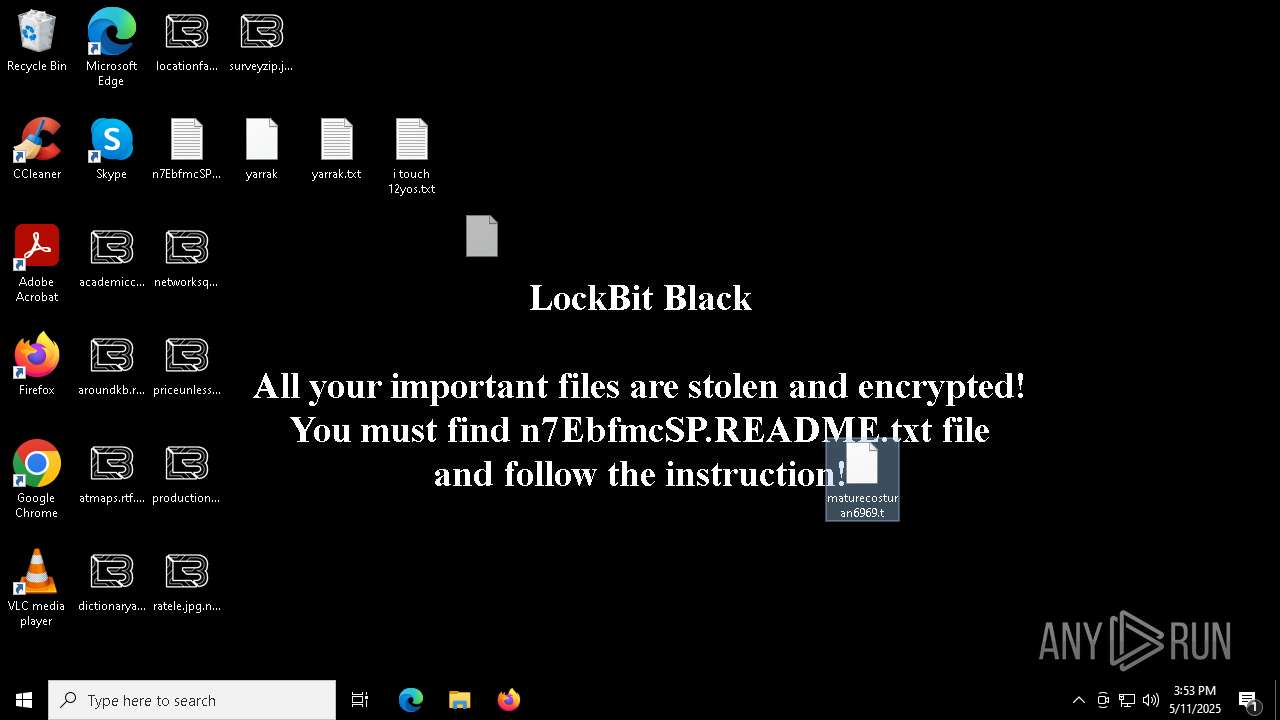
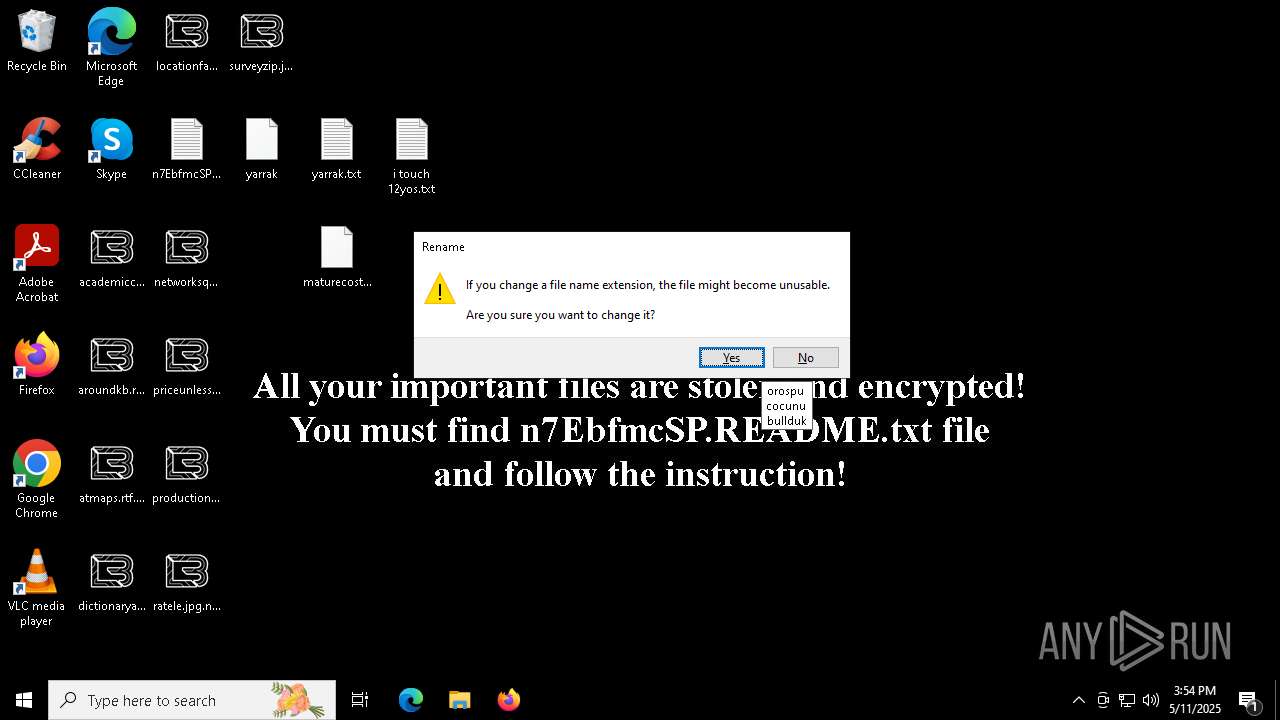
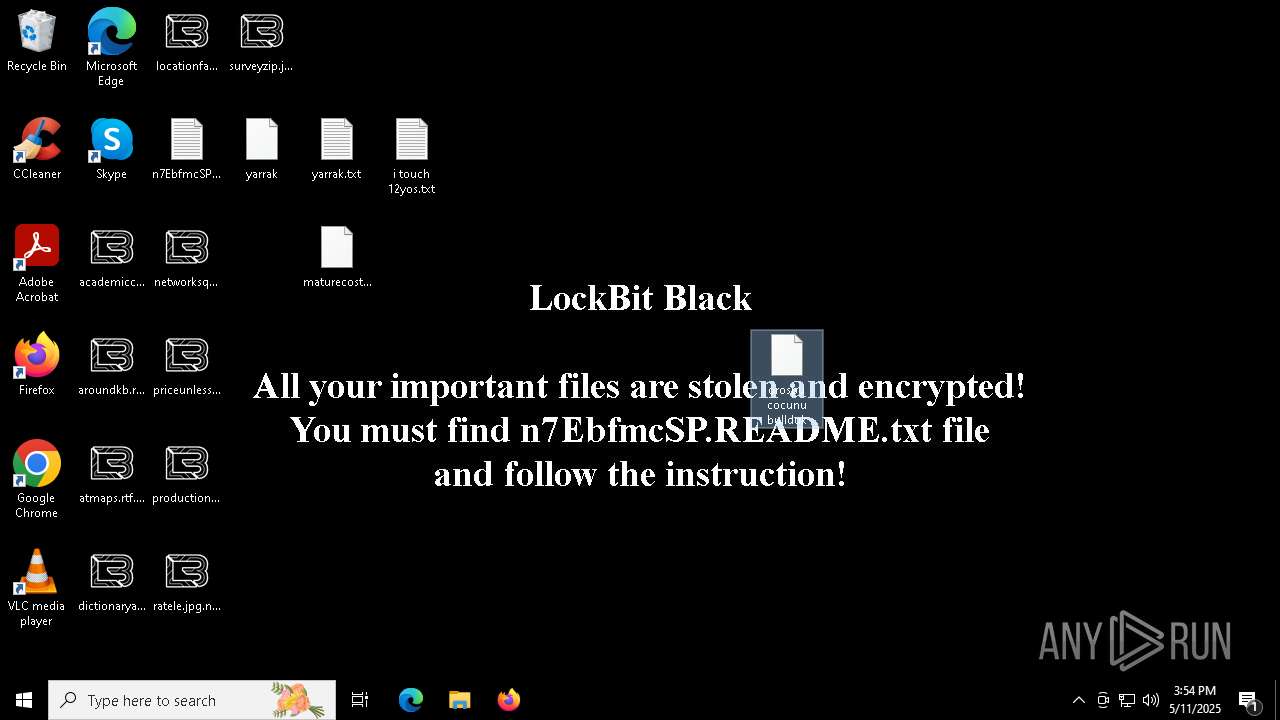
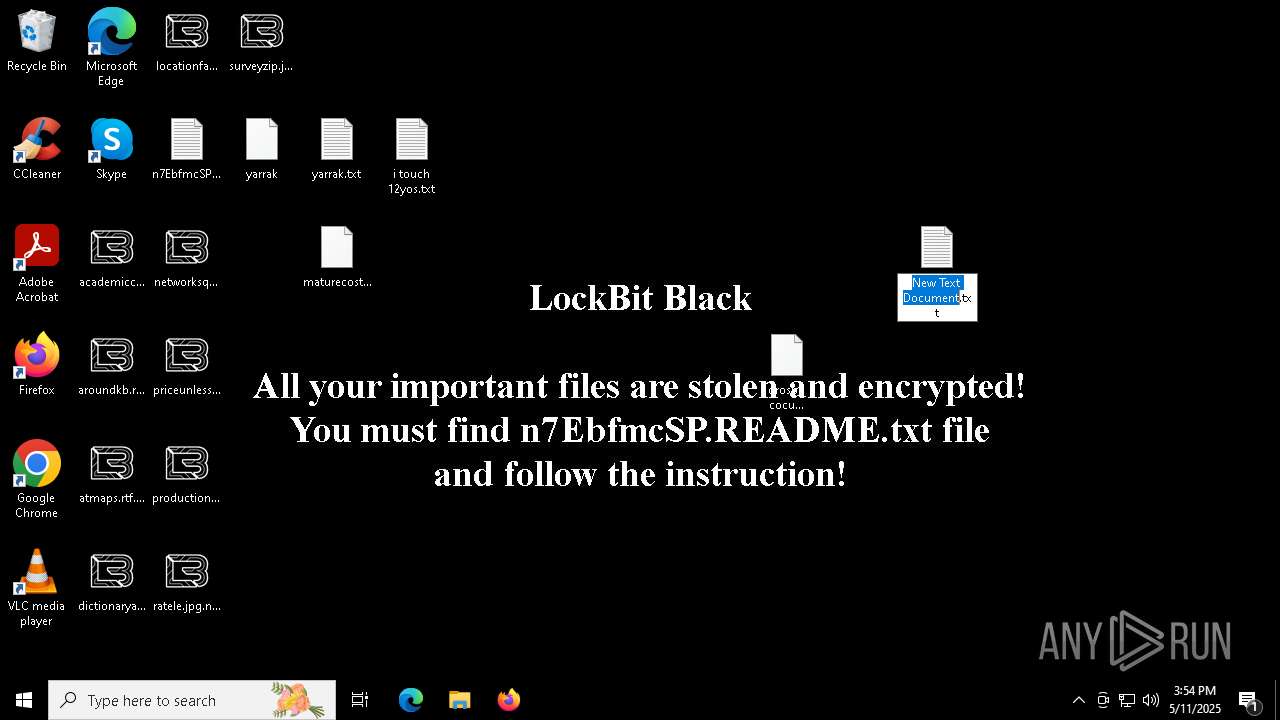
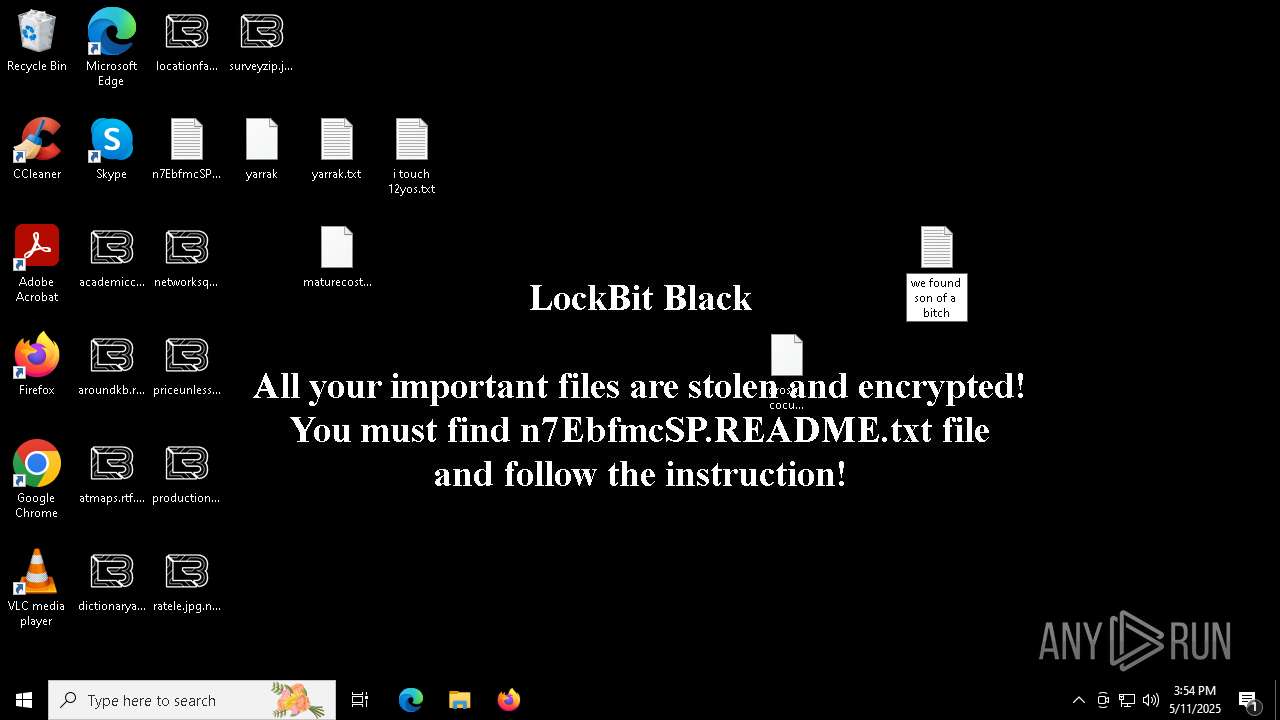
Renames files like ransomware
- ejjSND0.exe (PID: 7600)
LOCKBIT3 has been detected
- 73AD.tmp (PID: 5384)
SUSPICIOUS
Write to the desktop.ini file (may be used to cloak folders)
- ejjSND0.exe (PID: 7600)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 7908)
Executable content was dropped or overwritten
- ejjSND0.exe (PID: 7600)
Hides command output
- cmd.exe (PID: 2136)
Starts application with an unusual extension
- ejjSND0.exe (PID: 7600)
Starts CMD.EXE for commands execution
- 73AD.tmp (PID: 5384)
INFO
Reads the computer name
- ejjSND0.exe (PID: 7376)
- ejjSND0.exe (PID: 7600)
- SearchApp.exe (PID: 2152)
- ShellExperienceHost.exe (PID: 7908)
Checks supported languages
- ejjSND0.exe (PID: 7376)
- ShellExperienceHost.exe (PID: 7908)
- SearchApp.exe (PID: 2152)
- ejjSND0.exe (PID: 7600)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 7552)
- notepad.exe (PID: 1228)
Reads the machine GUID from the registry
- ejjSND0.exe (PID: 7376)
- SearchApp.exe (PID: 2152)
Creates files or folders in the user directory
- ejjSND0.exe (PID: 7600)
Creates files in the program directory
- ejjSND0.exe (PID: 7600)
Manual execution by a user
- notepad.exe (PID: 1228)
Checks proxy server information
- SearchApp.exe (PID: 2152)
Create files in a temporary directory
- ejjSND0.exe (PID: 7600)
Process checks computer location settings
- SearchApp.exe (PID: 2152)
Reads the software policy settings
- SearchApp.exe (PID: 2152)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (38.3) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (26.2) |
| .exe | | | Win16/32 Executable Delphi generic (12) |
| .exe | | | Generic Win/DOS Executable (11.6) |
| .exe | | | DOS Executable Generic (11.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:09:09 01:27:01+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.12 |
| CodeSize: | 99328 |
| InitializedDataSize: | 50688 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1946f |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
161
Monitored processes
15
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 744 | "C:\Windows\ImmersiveControlPanel\SystemSettings.exe" -ServerName:microsoft.windows.immersivecontrolpanel | C:\Windows\ImmersiveControlPanel\SystemSettings.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Settings Exit code: 1 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1228 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\New Text Document.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2136 | "C:\WINDOWS\System32\cmd.exe" /C DEL /F /Q C:\PROGRA~3\73AD.tmp >> NUL | C:\Windows\SysWOW64\cmd.exe | — | 73AD.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2152 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2772 | /insertdoc "C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\{430CEF54-A6B6-490C-9412-58F4D53C7F03}.xps" 133914523363910000 | C:\Program Files\Microsoft Office\root\Office16\ONENOTE.EXE | printfilterpipelinesvc.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft OneNote Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 5384 | "C:\ProgramData\73AD.tmp" | C:\ProgramData\73AD.tmp | ejjSND0.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 5756 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6540 | C:\WINDOWS\splwow64.exe 12288 | C:\Windows\splwow64.exe | — | ejjSND0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Print driver host for applications Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7220 | C:\WINDOWS\system32\printfilterpipelinesvc.exe -Embedding | C:\Windows\System32\printfilterpipelinesvc.exe | — | svchost.exe | |||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Print Filter Pipeline Host Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7376 | "C:\Users\admin\AppData\Local\Temp\ejjSND0.exe" | C:\Users\admin\AppData\Local\Temp\ejjSND0.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
26 020
Read events
23 158
Write events
2 828
Delete events
34
Modification events
| (PID) Process: | (7552) dllhost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (7908) ShellExperienceHost.exe | Key: | \REGISTRY\A\{98480cff-bf6f-9aa0-e24f-b69597041c9d}\LocalState |
| Operation: | write | Name: | PeekBadges |
Value: 5B005D000000D98235478CC2DB01 | |||
| (PID) Process: | (7908) ShellExperienceHost.exe | Key: | \REGISTRY\A\{98480cff-bf6f-9aa0-e24f-b69597041c9d}\LocalState |
| Operation: | write | Name: | PeekBadges |
Value: 5B005D0000009EE737478CC2DB01 | |||
| (PID) Process: | (2152) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\SearchSettings |
| Operation: | write | Name: | SafeSearchMode |
Value: 1 | |||
| (PID) Process: | (2152) SearchApp.exe | Key: | \REGISTRY\A\{04f4ca9c-93bf-9679-1ad9-94ec4bab3469}\LocalState |
| Operation: | write | Name: | BINGIDENTITY_PROP_USEREMAIL |
Value: 00009C8E4B7C8CC2DB01 | |||
| (PID) Process: | (2152) SearchApp.exe | Key: | \REGISTRY\A\{04f4ca9c-93bf-9679-1ad9-94ec4bab3469}\LocalState |
| Operation: | write | Name: | BINGIDENTITY_PROP_ACCOUNTTYPETEXT |
Value: 000058F24D7C8CC2DB01 | |||
| (PID) Process: | (2152) SearchApp.exe | Key: | \REGISTRY\A\{04f4ca9c-93bf-9679-1ad9-94ec4bab3469}\LocalState |
| Operation: | write | Name: | BINGIDENTITY_PROP_ACCOUNTTYPE |
Value: 000058F24D7C8CC2DB01 | |||
| (PID) Process: | (2152) SearchApp.exe | Key: | \REGISTRY\A\{04f4ca9c-93bf-9679-1ad9-94ec4bab3469}\LocalState |
| Operation: | write | Name: | BINGIDENTITY_PROP_ACCOUNTTYPE |
Value: 4E006F006E006500000058F24D7C8CC2DB01 | |||
| (PID) Process: | (2152) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search\Flighting |
| Operation: | delete value | Name: | CachedFeatureString |
Value: | |||
| (PID) Process: | (2152) SearchApp.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.search_cw5n1h2txyewy\SOFTWARE\Microsoft\Speech_OneCore\Isolated\A1hdl50UVDh2ZbG324Nx-6fZgntcGnHOs5kHLdmaJYE\HKEY_CURRENT_USER\SOFTWARE\Microsoft\Speech_OneCore\Recognizers |
| Operation: | write | Name: | DefaultTokenId |
Value: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Speech_OneCore\Recognizers\Tokens\MS-1033-110-WINMO-DNN | |||
Executable files
22
Suspicious files
2 284
Text files
2 468
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7600 | ejjSND0.exe | C:\ProgramData\n7EbfmcSP.ico | image | |
MD5:88D9337C4C9CFE2D9AFF8A2C718EC76B | SHA256:95E059EF72686460884B9AEA5C292C22917F75D56FE737D43BE440F82034F438 | |||
| 7600 | ejjSND0.exe | C:\$Recycle.Bin\S-1-5-18\CCCCCCCCCCC | binary | |
MD5:ACFB5E04747BB9174423FB415E179A76 | SHA256:2FF2F1BFDA55400F0B3D8E475A1C5DA89E9872B178360E6D74EBE4E9CB69618F | |||
| 7600 | ejjSND0.exe | C:\$Recycle.Bin\S-1-5-18\LLLLLLLLLLL | binary | |
MD5:ACFB5E04747BB9174423FB415E179A76 | SHA256:2FF2F1BFDA55400F0B3D8E475A1C5DA89E9872B178360E6D74EBE4E9CB69618F | |||
| 7600 | ejjSND0.exe | C:\$Recycle.Bin\S-1-5-18\BBBBBBBBBBB | binary | |
MD5:ACFB5E04747BB9174423FB415E179A76 | SHA256:2FF2F1BFDA55400F0B3D8E475A1C5DA89E9872B178360E6D74EBE4E9CB69618F | |||
| 7600 | ejjSND0.exe | C:\$Recycle.Bin\S-1-5-18\JJJJJJJJJJJ | binary | |
MD5:ACFB5E04747BB9174423FB415E179A76 | SHA256:2FF2F1BFDA55400F0B3D8E475A1C5DA89E9872B178360E6D74EBE4E9CB69618F | |||
| 7600 | ejjSND0.exe | C:\$Recycle.Bin\S-1-5-18\MMMMMMMMMMM | binary | |
MD5:ACFB5E04747BB9174423FB415E179A76 | SHA256:2FF2F1BFDA55400F0B3D8E475A1C5DA89E9872B178360E6D74EBE4E9CB69618F | |||
| 7600 | ejjSND0.exe | C:\$Recycle.Bin\S-1-5-18\IIIIIIIIIII | binary | |
MD5:ACFB5E04747BB9174423FB415E179A76 | SHA256:2FF2F1BFDA55400F0B3D8E475A1C5DA89E9872B178360E6D74EBE4E9CB69618F | |||
| 7600 | ejjSND0.exe | C:\$Recycle.Bin\S-1-5-18\PPPPPPPPPPP | binary | |
MD5:ACFB5E04747BB9174423FB415E179A76 | SHA256:2FF2F1BFDA55400F0B3D8E475A1C5DA89E9872B178360E6D74EBE4E9CB69618F | |||
| 7600 | ejjSND0.exe | C:\$Recycle.Bin\S-1-5-18\HHHHHHHHHHH | binary | |
MD5:ACFB5E04747BB9174423FB415E179A76 | SHA256:2FF2F1BFDA55400F0B3D8E475A1C5DA89E9872B178360E6D74EBE4E9CB69618F | |||
| 7600 | ejjSND0.exe | C:\$Recycle.Bin\S-1-5-18\NNNNNNNNNNN | binary | |
MD5:ACFB5E04747BB9174423FB415E179A76 | SHA256:2FF2F1BFDA55400F0B3D8E475A1C5DA89E9872B178360E6D74EBE4E9CB69618F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
43
DNS requests
30
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2772 | ONENOTE.EXE | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
2152 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5544 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2152 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4156 | SystemSettings.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.173:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5544 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4156 | SystemSettings.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.173:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 20.190.160.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5544 | SIHClient.exe | 172.202.163.200:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
5544 | SIHClient.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
www.bing.com |
| whitelisted |