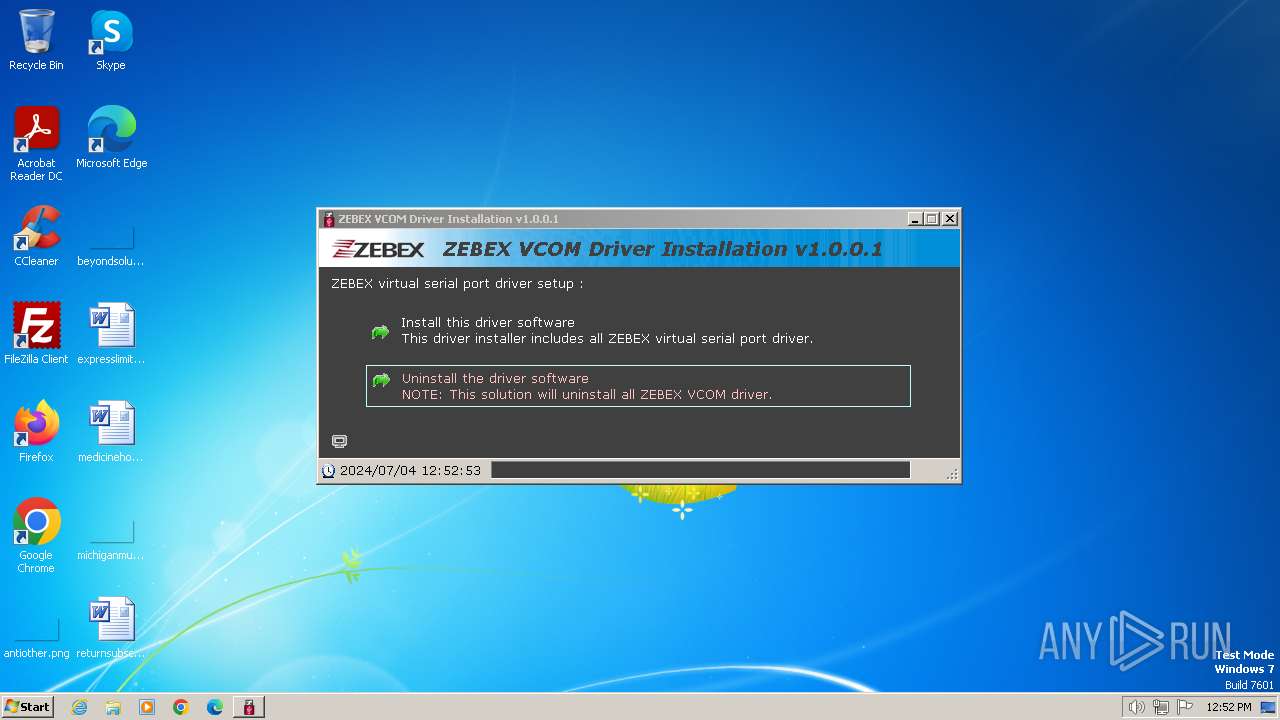
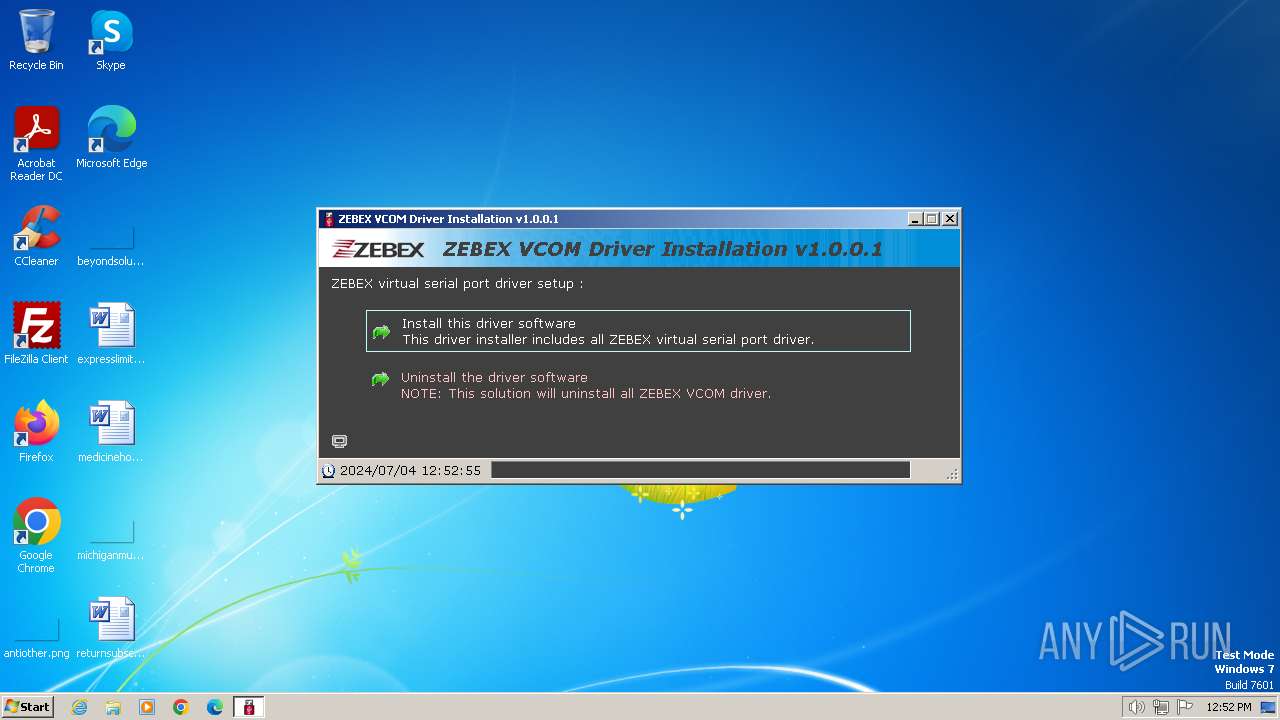
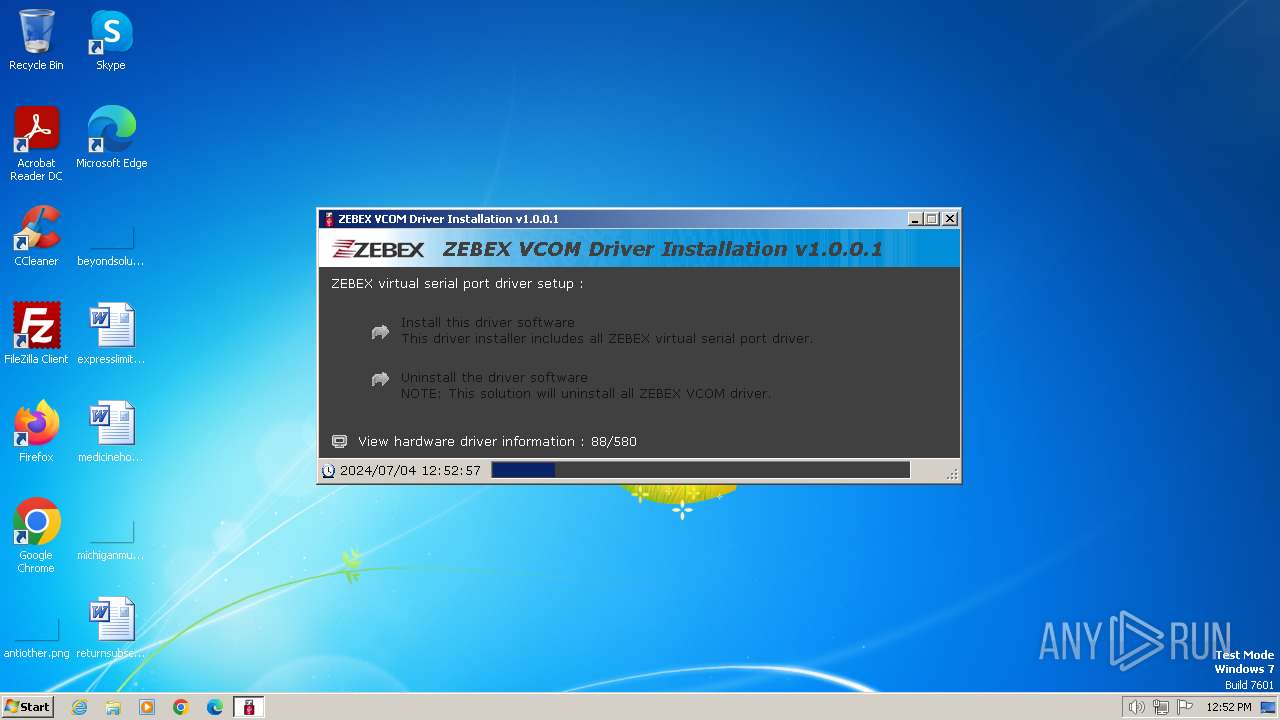
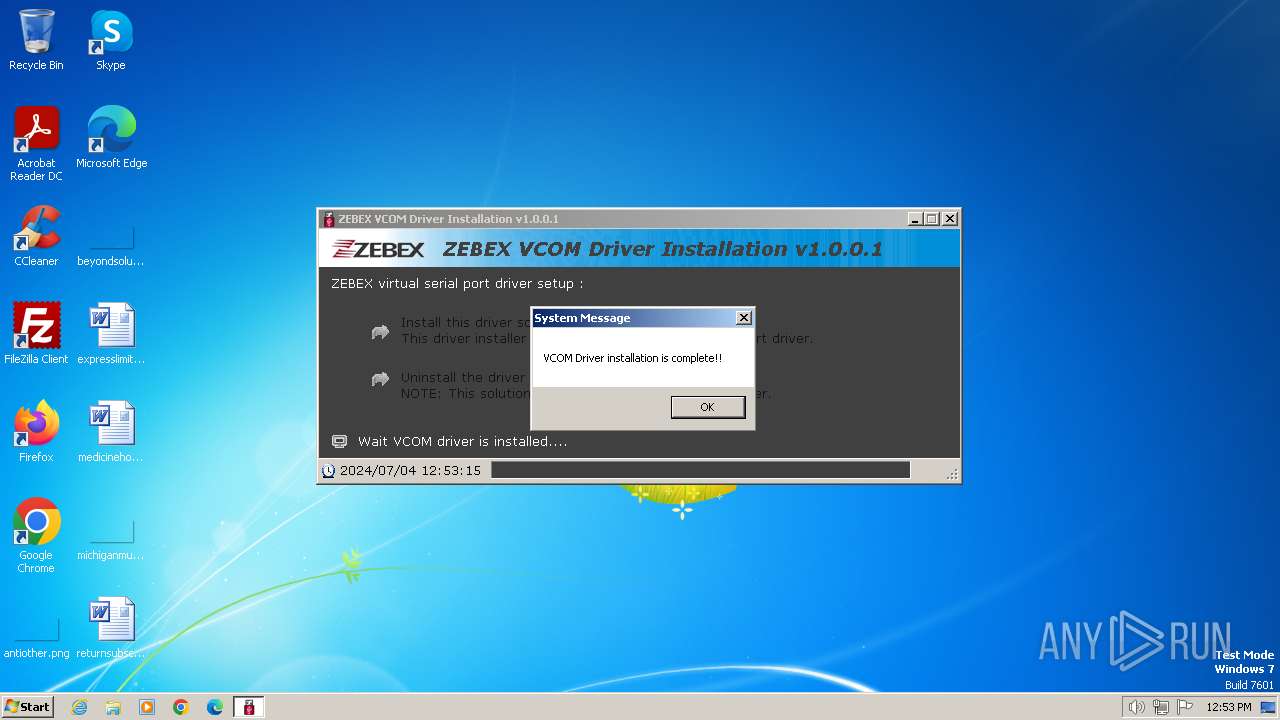
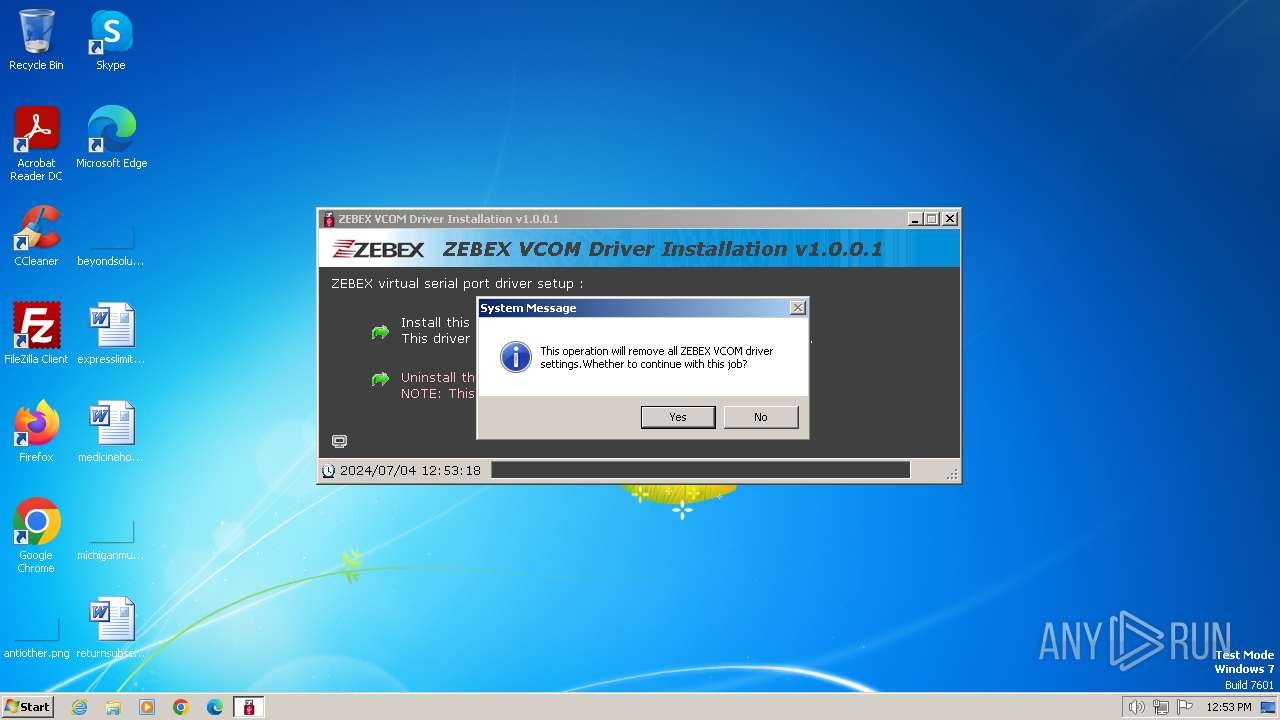
| File name: | ZEBEX VCOM Driver Installation v1.0.0.1.exe |
| Full analysis: | https://app.any.run/tasks/aff56d37-65dc-40d5-a980-e5c50f9a75f1 |
| Verdict: | Malicious activity |
| Analysis date: | July 04, 2024, 11:52:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | FA8354E9715ED8E745403B6F8F163F50 |
| SHA1: | B2F9A493A5390006AAE5A5C93DA49C9B7EF27B3F |
| SHA256: | 98A835C2BE0B56DF2A4A165BB9F437F18EDD844E90E0E3A9EF5A6140476CCD9C |
| SSDEEP: | 12288:Lvxut3+kd7Bc1MOQ2utW1XhG9RcY5n+Bo8ugZwP2MgaE1asCZc1yBmMKY3MpdONh:9ut3+kd61y2utqw3ya0+4Q+kd7F+kd |
MALICIOUS
Drops the executable file immediately after the start
- ZEBEX VCOM Driver Installation v1.0.0.1.exe (PID: 540)
- PsExec.exe (PID: 3128)
Creates a writable file in the system directory
- Anti-Registration.exe (PID: 2852)
- drvinst.exe (PID: 3588)
SUSPICIOUS
Executable content was dropped or overwritten
- PsExec.exe (PID: 3128)
- ZEBEX VCOM Driver Installation v1.0.0.1.exe (PID: 540)
Executes as Windows Service
- PSEXESVC.exe (PID: 3160)
- VSSVC.exe (PID: 3716)
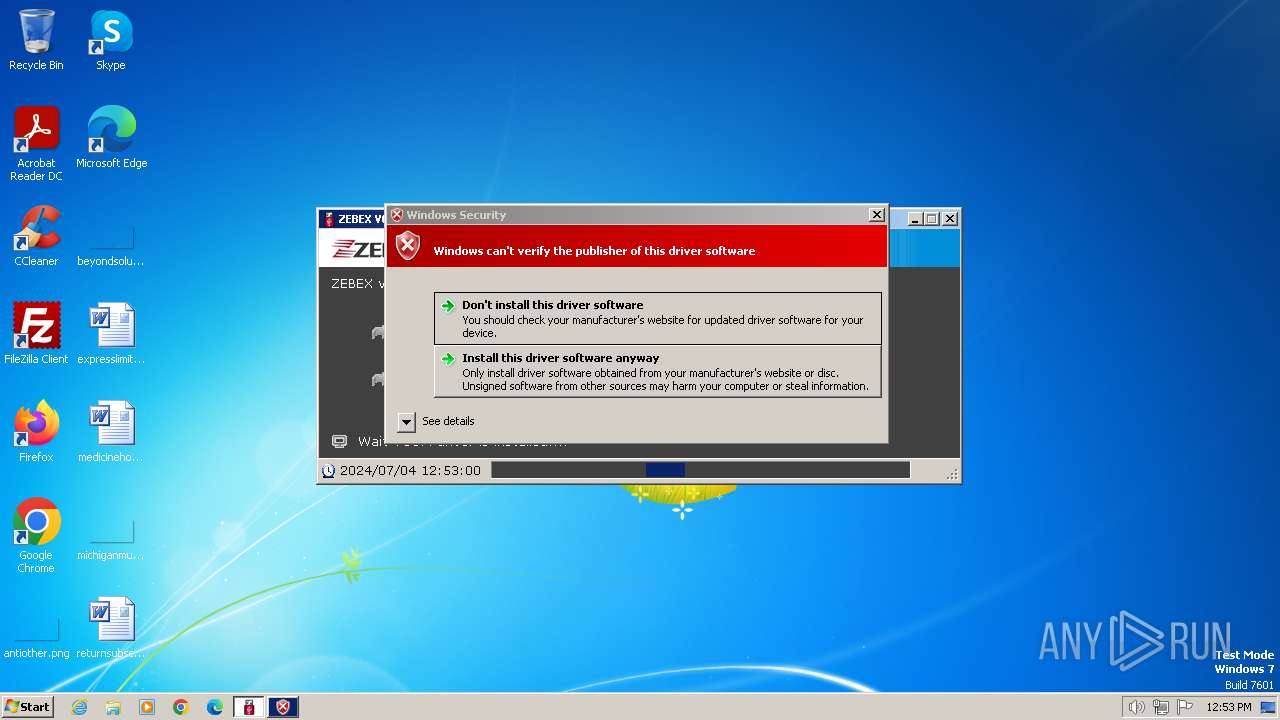
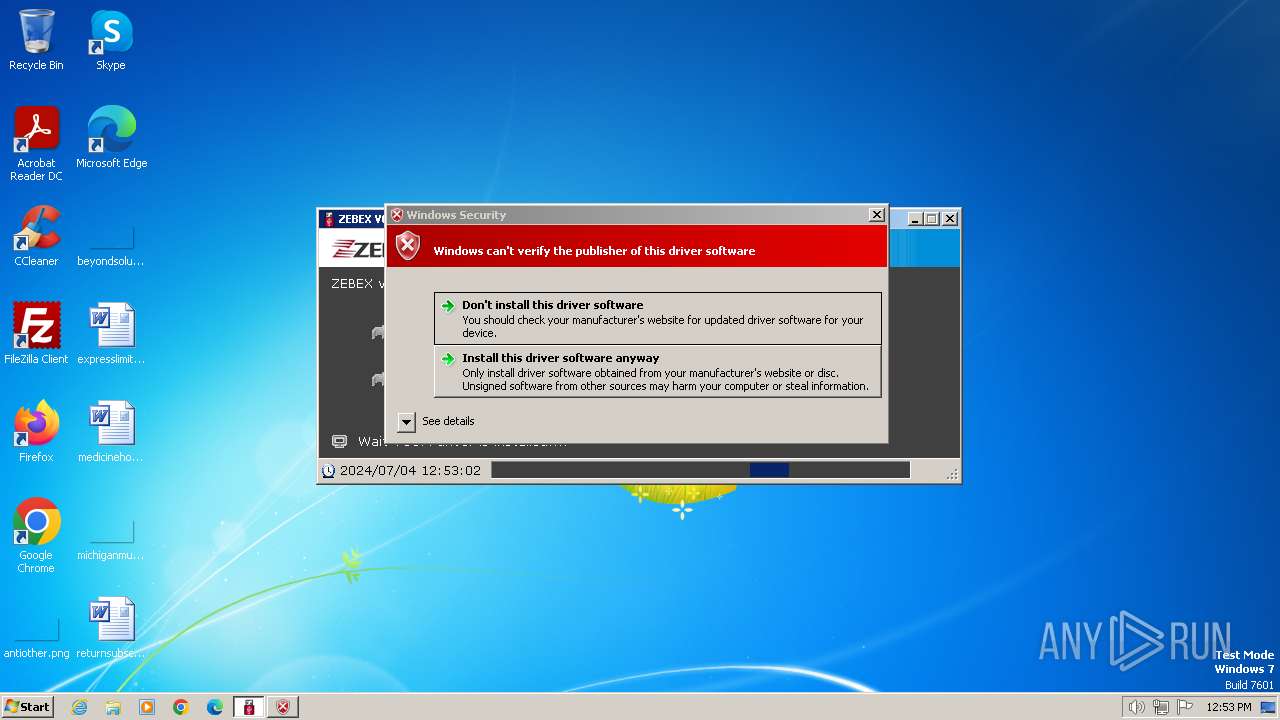
Checks Windows Trust Settings
- drvinst.exe (PID: 3588)
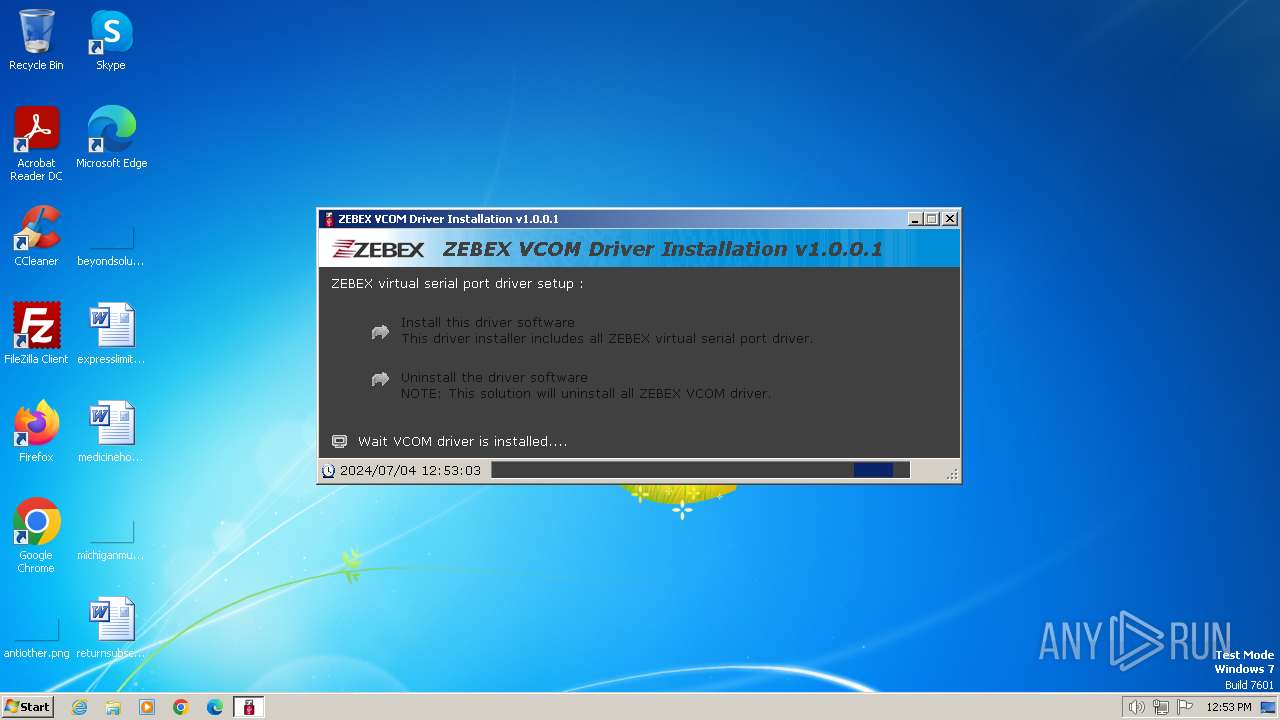
Creates files in the driver directory
- drvinst.exe (PID: 3588)
INFO
Reads the computer name
- PsExec.exe (PID: 3128)
- PSEXESVC.exe (PID: 3160)
- drvinst.exe (PID: 3588)
- Anti-Registration.exe (PID: 2852)
Checks supported languages
- ZEBEX VCOM Driver Installation v1.0.0.1.exe (PID: 540)
- PsExec.exe (PID: 3128)
- PSEXESVC.exe (PID: 3160)
- Anti-Registration.exe (PID: 2852)
- drvinst.exe (PID: 3588)
Reads the machine GUID from the registry
- drvinst.exe (PID: 3588)
Reads the software policy settings
- drvinst.exe (PID: 3588)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (49) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (20.9) |
| .exe | | | Win64 Executable (generic) (18.5) |
| .dll | | | Win32 Dynamic Link Library (generic) (4.4) |
| .exe | | | Win32 Executable (generic) (3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2014:01:16 08:32:31+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 1064960 |
| InitializedDataSize: | 172032 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x105c6e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.1 |
| ProductVersionNumber: | 1.0.0.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | ZEBEX VCOM Driver Installation v1 |
| FileVersion: | 1.0.0.1 |
| InternalName: | ZEBEX VCOM Driver Installation v1.exe |
| LegalCopyright: | Copyright © 2014 |
| OriginalFileName: | ZEBEX VCOM Driver Installation v1.exe |
| ProductName: | ZEBEX VCOM Driver Installation v1 |
| ProductVersion: | 1.0.0.1 |
| AssemblyVersion: | 1.0.0.1 |
Total processes
52
Monitored processes
9
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 540 | "C:\Users\admin\AppData\Local\Temp\ZEBEX VCOM Driver Installation v1.0.0.1.exe" | C:\Users\admin\AppData\Local\Temp\ZEBEX VCOM Driver Installation v1.0.0.1.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: ZEBEX VCOM Driver Installation v1 Version: 1.0.0.1 Modules
| |||||||||||||||
| 2420 | "C:\Windows\system32\pnputil.exe" -i -a "c:\zbxcdc\template\zbxcdc_nolayout_13121300.inf" | C:\Windows\System32\PnPutil.exe | — | Anti-Registration.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft PnP Utility - Tool to add, delete and enumerate driver packages. Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2732 | "C:\Users\admin\AppData\Local\Temp\ZEBEX VCOM Driver Installation v1.0.0.1.exe" | C:\Users\admin\AppData\Local\Temp\ZEBEX VCOM Driver Installation v1.0.0.1.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: ZEBEX VCOM Driver Installation v1 Exit code: 3221226540 Version: 1.0.0.1 Modules
| |||||||||||||||
| 2852 | "c:\zbxcdc\Anti-Registration.exe" | C:\zbxcdc\Anti-Registration.exe | — | PSEXESVC.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Description: Anti-Registration v1 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3128 | "c:\zbxcdc\PsExec.exe" -accepteula -i -s "c:\zbxcdc\Anti-Registration.exe" | C:\zbxcdc\PsExec.exe | ZEBEX VCOM Driver Installation v1.0.0.1.exe | ||||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: HIGH Description: Execute processes remotely Version: 2.0 Modules
| |||||||||||||||
| 3160 | C:\Windows\PSEXESVC.exe | C:\Windows\PSEXESVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Sysinternals Integrity Level: SYSTEM Description: PsExec Service Version: 2.0 Modules
| |||||||||||||||
| 3588 | DrvInst.exe "4" "0" "C:\Windows\TEMP\{234d7e53-7c9d-77f9-5c33-c921878a8527}\zbxcdc_nolayout_13121300.inf" "0" "628a51cfb" "000003C0" "WinSta0\Default" "00000554" "208" "c:\zbxcdc\template" | C:\Windows\System32\drvinst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3676 | rundll32.exe C:\Windows\system32\pnpui.dll,InstallSecurityPromptRunDllW 10 Global\{2b3cf159-1822-110f-fd1c-e4725f849d7f} Global\{75b7077b-76fc-0ab0-0039-5d4e63104803} C:\Windows\System32\DriverStore\Temp\{4cdd1b8c-3900-4e5d-04b1-ec06f8992333}\zbxcdc_nolayout_13121300.inf C:\Windows\System32\DriverStore\Temp\{4cdd1b8c-3900-4e5d-04b1-ec06f8992333}\zbxcdc.cat | C:\Windows\System32\rundll32.exe | — | drvinst.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3716 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
4 964
Read events
4 786
Write events
178
Delete events
0
Modification events
| (PID) Process: | (3128) PsExec.exe | Key: | HKEY_CURRENT_USER\Software\Sysinternals\PsExec |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (2852) Anti-Registration.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\GDIPlus |
| Operation: | write | Name: | FontCachePath |
Value: C:\Windows\system32\config\systemprofile\AppData\Local | |||
| (PID) Process: | (2420) PnPutil.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\Setup\SetupapiLogStatus |
| Operation: | write | Name: | setupapi.dev.log |
Value: 4096 | |||
| (PID) Process: | (2420) PnPutil.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3588) drvinst.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3676) rundll32.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {D9144DCD-E998-4ECA-AB6A-DCD83CCBA16D} {0C6C4200-C589-11D0-999A-00C04FD655E1} 0xFFFF |
Value: 01000000000000005A161FB808CEDA01 | |||
| (PID) Process: | (3676) rundll32.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {4E77131D-3629-431C-9818-C5679DC83E81} {0C6C4200-C589-11D0-999A-00C04FD655E1} 0xFFFF |
Value: 01000000000000005A161FB808CEDA01 | |||
| (PID) Process: | (3676) rundll32.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {08244EE6-92F0-47F2-9FC9-929BAA2E7235} {0C6C4200-C589-11D0-999A-00C04FD655E1} 0xFFFF |
Value: 01000000000000005A161FB808CEDA01 | |||
| (PID) Process: | (3588) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000A00674B908CEDA01040E0000640E0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3588) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4000000000000000A00674B908CEDA01040E0000640E0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
4
Suspicious files
20
Text files
2
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3588 | drvinst.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 2420 | PnPutil.exe | C:\Windows\TEMP\{234d7e53-7c9d-77f9-5c33-c921878a8527}\SET7855.tmp | binary | |
MD5:6465FDAFE6FF85679644F6AD649AE5CB | SHA256:E10BAD7DB9F7F48EA3FA41E60F23726A86712B91CF8AE6E47247BEDBC2D13EDD | |||
| 540 | ZEBEX VCOM Driver Installation v1.0.0.1.exe | C:\zbxcdc\Anti-Registration.exe | executable | |
MD5:8F5034B13695864B2E6F137CE7BC4F1E | SHA256:32608BF9F26A3E5EC479D9985A55FDE92133E6CD61FFDAB034B01ED8E17977E7 | |||
| 2420 | PnPutil.exe | C:\Windows\Temp\{234d7e53-7c9d-77f9-5c33-c921878a8527}\zbxcdc_nolayout_13121300.inf | binary | |
MD5:908C90F73781D437B2F33744CE23F4D0 | SHA256:2515381F96B65F6FB6EF2E68988EBFA11AD082916A47B5B10CB1C8A5DCE34A7A | |||
| 3588 | drvinst.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:C068B1B4D9CD62D10B3356E99657F882 | SHA256:766CB7B09CF2ADA3449461FF5B5A487636DDC511D32E9E239A5A9317408A88FC | |||
| 3588 | drvinst.exe | C:\Windows\System32\DriverStore\Temp\{4cdd1b8c-3900-4e5d-04b1-ec06f8992333}\zbxcdc_nolayout_13121300.inf | binary | |
MD5:908C90F73781D437B2F33744CE23F4D0 | SHA256:2515381F96B65F6FB6EF2E68988EBFA11AD082916A47B5B10CB1C8A5DCE34A7A | |||
| 3588 | drvinst.exe | C:\Windows\System32\DriverStore\Temp\{4cdd1b8c-3900-4e5d-04b1-ec06f8992333}\SET78D2.tmp | cat | |
MD5:6465FDAFE6FF85679644F6AD649AE5CB | SHA256:E10BAD7DB9F7F48EA3FA41E60F23726A86712B91CF8AE6E47247BEDBC2D13EDD | |||
| 2420 | PnPutil.exe | C:\Windows\Temp\{234d7e53-7c9d-77f9-5c33-c921878a8527}\zbxcdc.cat | cat | |
MD5:6465FDAFE6FF85679644F6AD649AE5CB | SHA256:E10BAD7DB9F7F48EA3FA41E60F23726A86712B91CF8AE6E47247BEDBC2D13EDD | |||
| 540 | ZEBEX VCOM Driver Installation v1.0.0.1.exe | C:\zbxcdc\PsExec.exe | executable | |
MD5:D0DF366711C8B296680002840336B6FD | SHA256:3C26EF3208A8BF6C2A23D46EF15C238197F528C04877DB0BAC2A090D15EC53B2 | |||
| 2420 | PnPutil.exe | C:\Windows\TEMP\{234d7e53-7c9d-77f9-5c33-c921878a8527}\SET7844.tmp | binary | |
MD5:908C90F73781D437B2F33744CE23F4D0 | SHA256:2515381F96B65F6FB6EF2E68988EBFA11AD082916A47B5B10CB1C8A5DCE34A7A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
10
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?11acddbe1ebd82b3 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1372 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1372 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1372 | svchost.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
1372 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
1060 | svchost.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dns.msftncsi.com |
| shared |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |