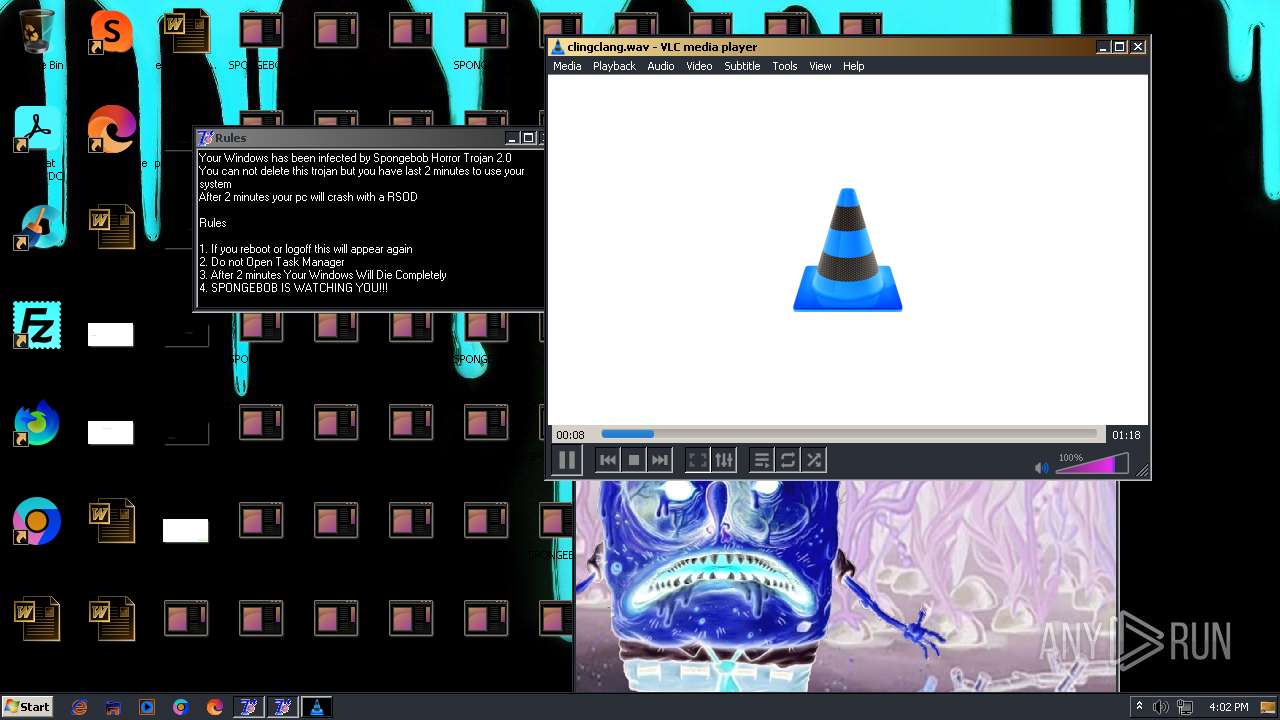
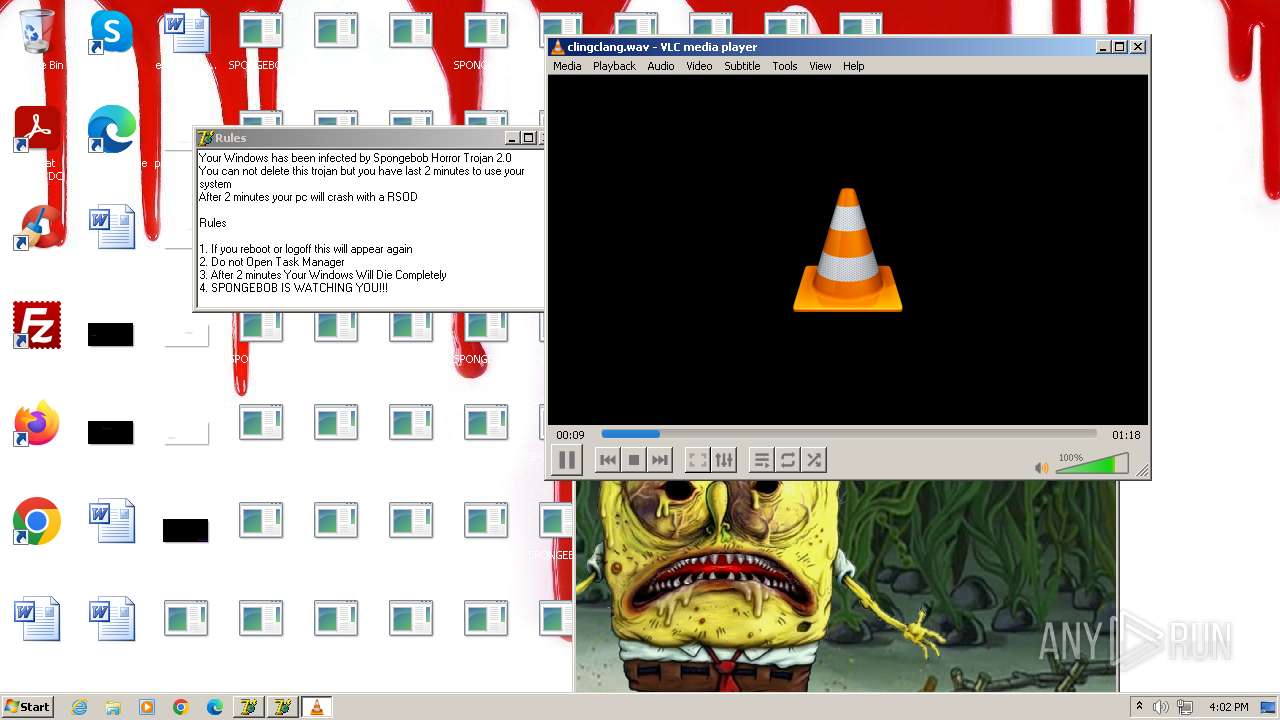
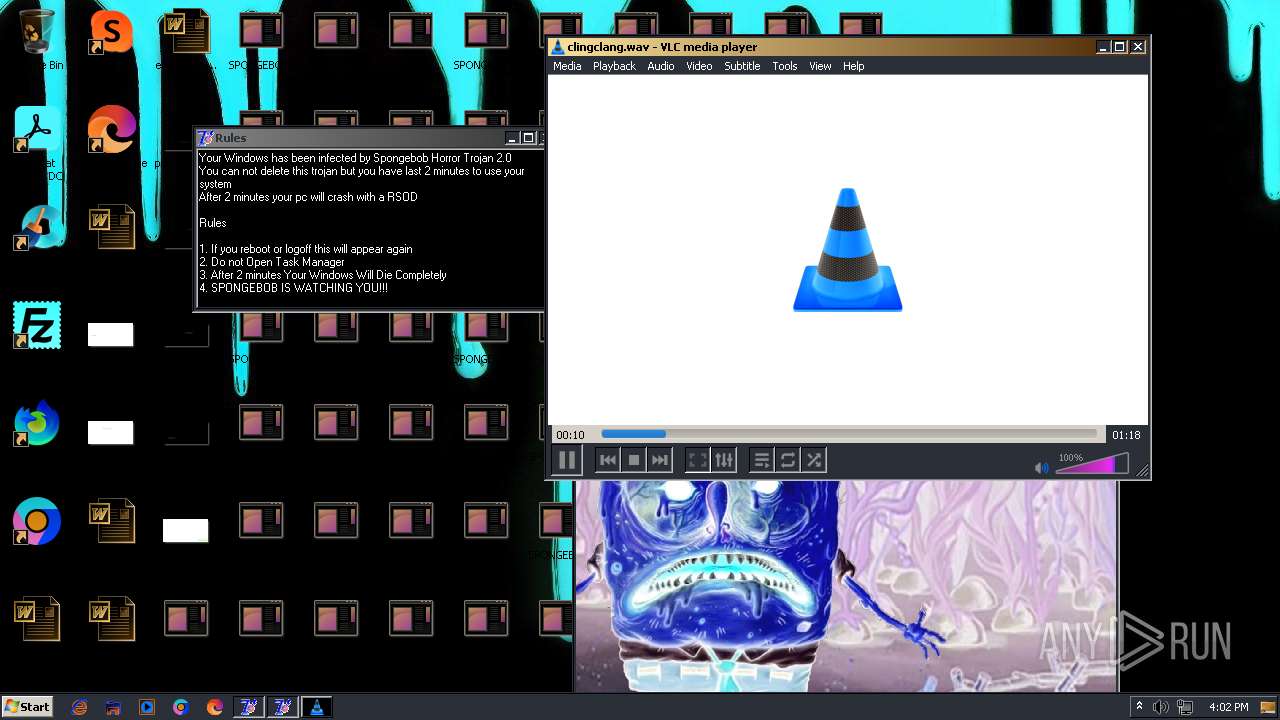
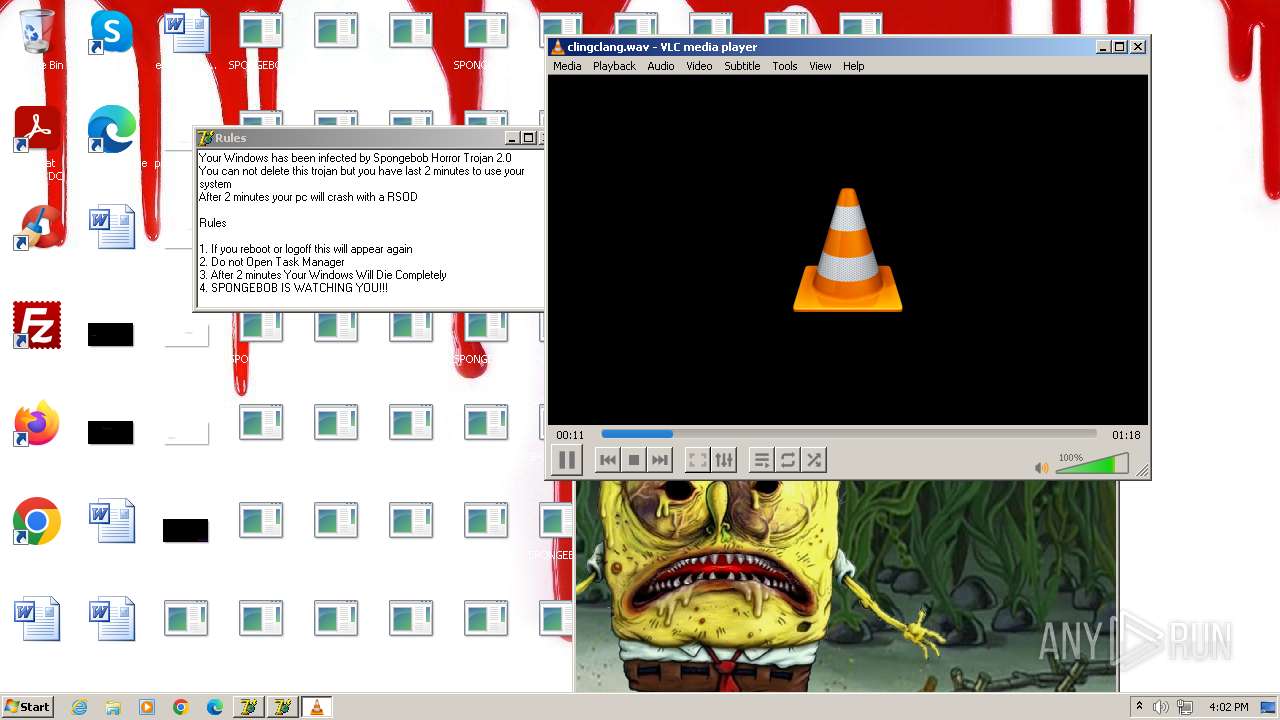
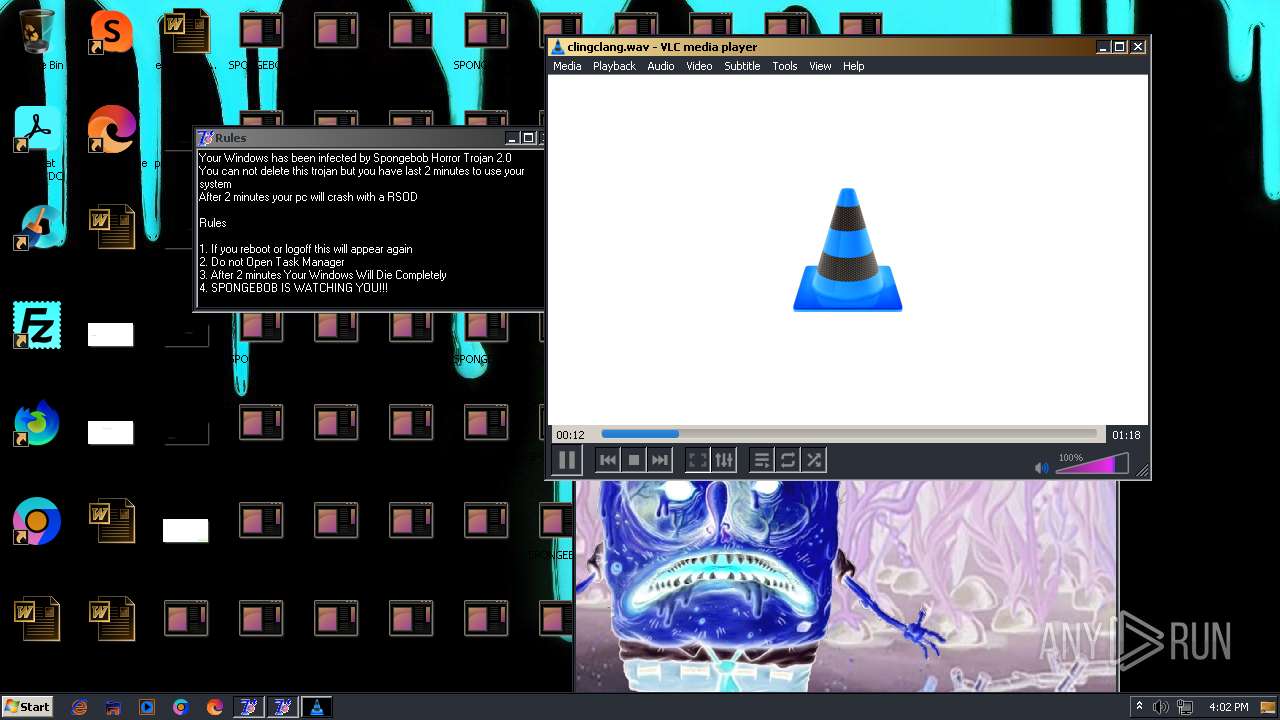
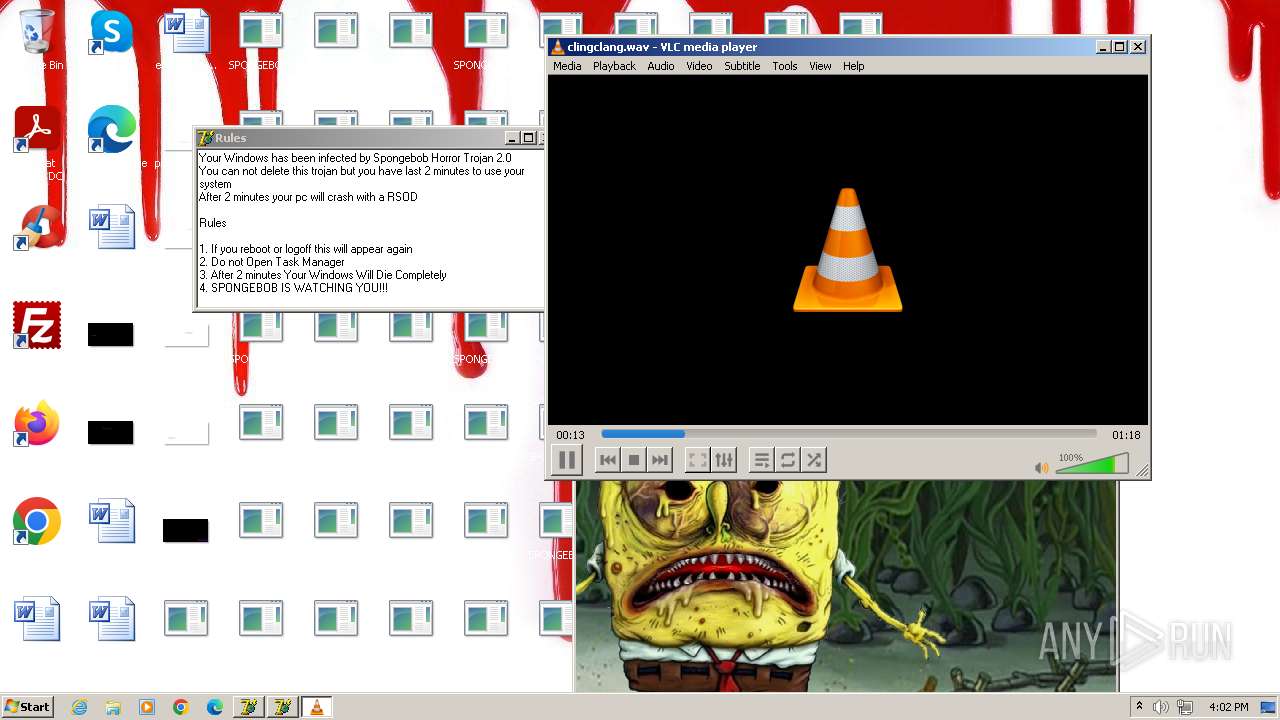
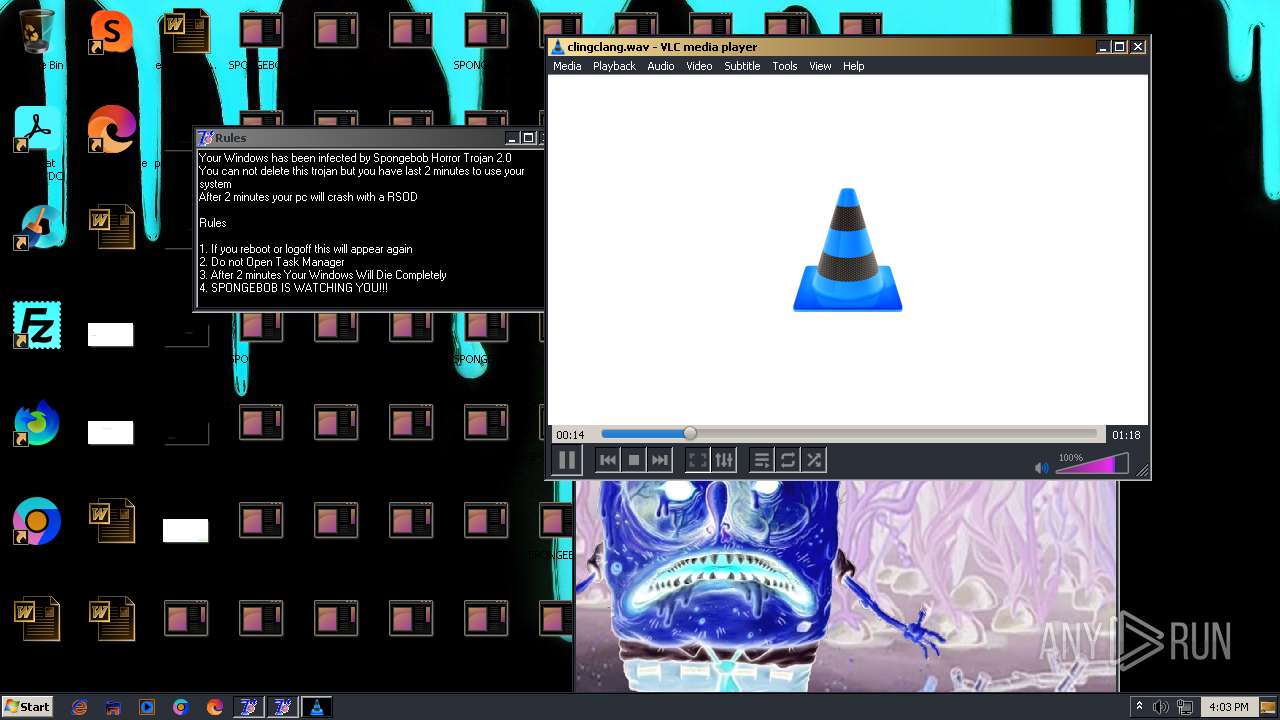
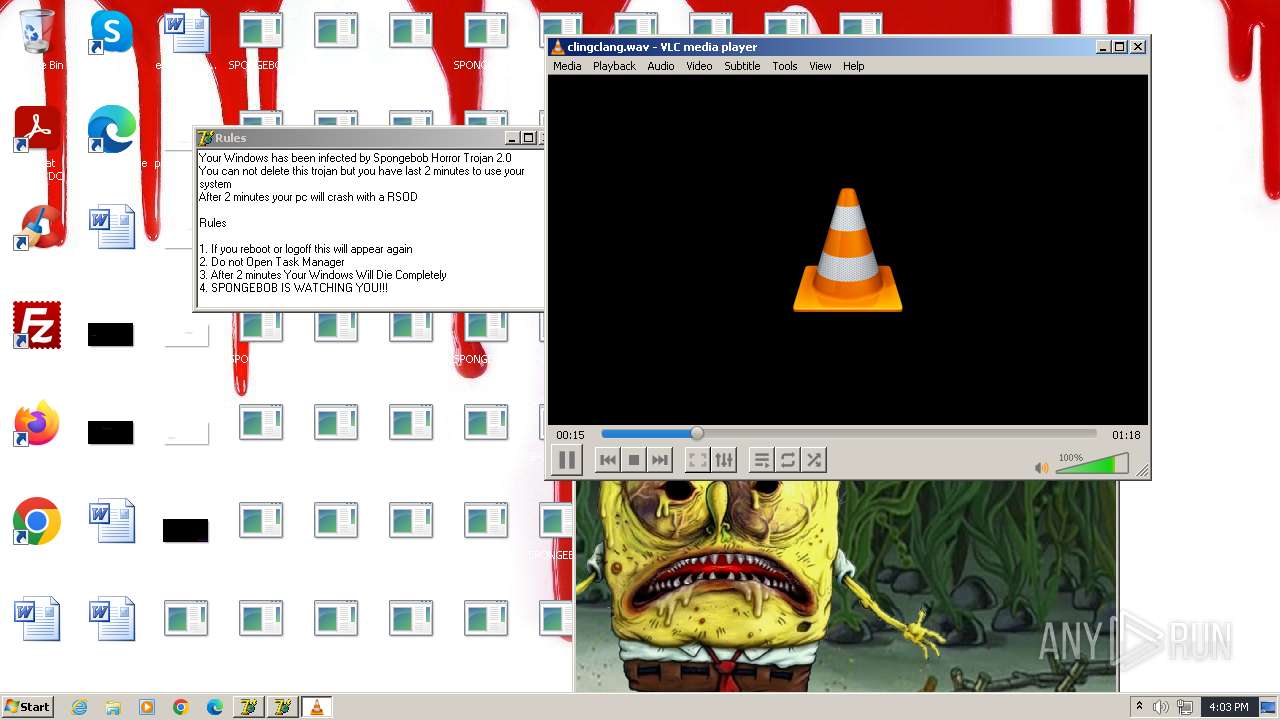
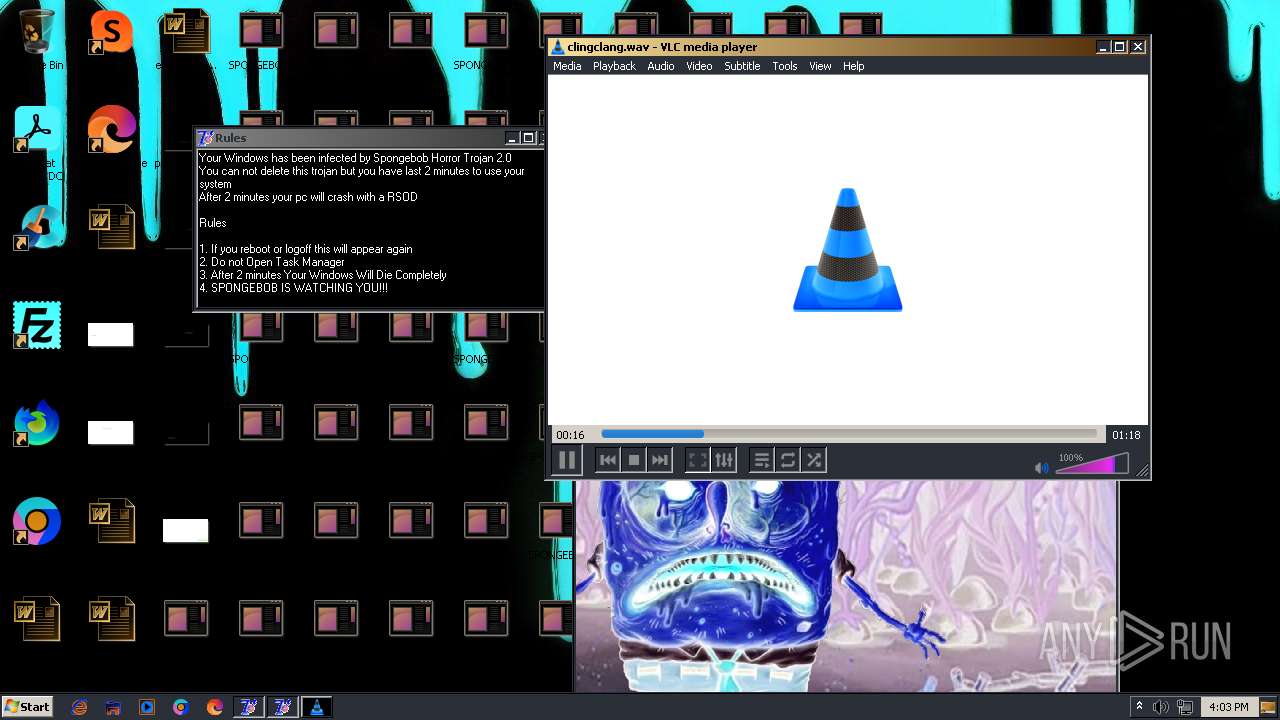
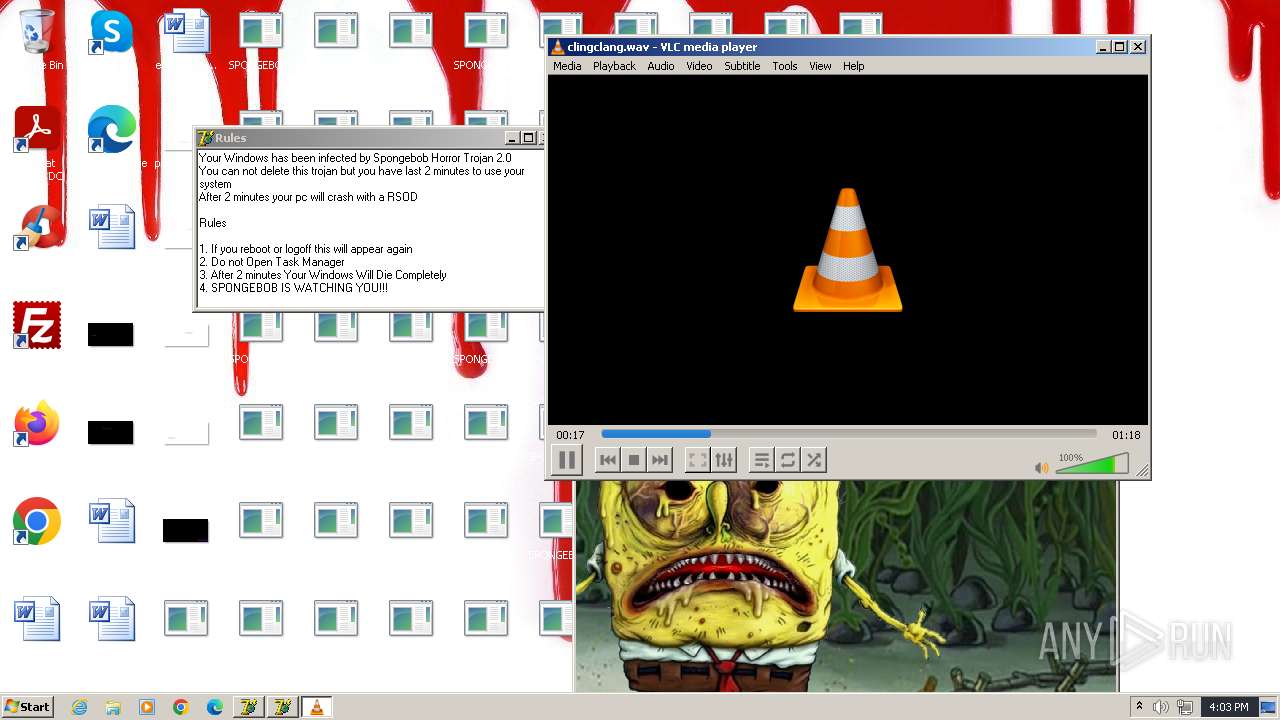
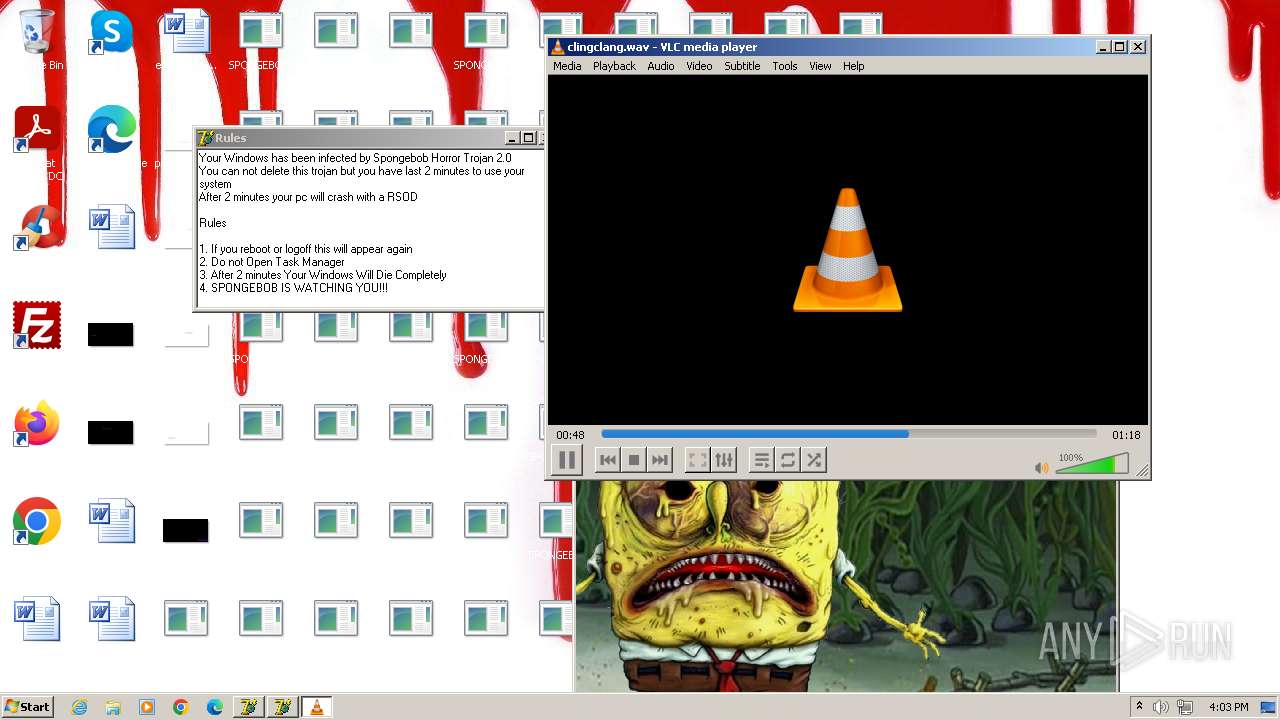
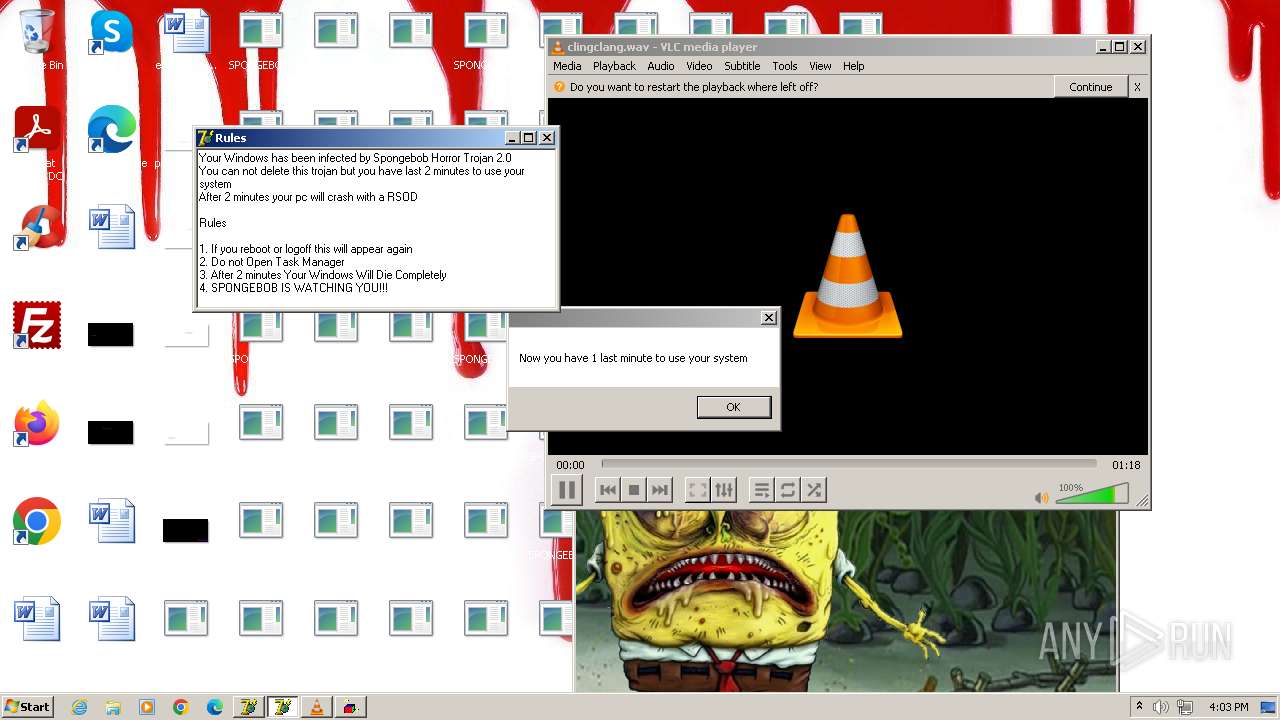
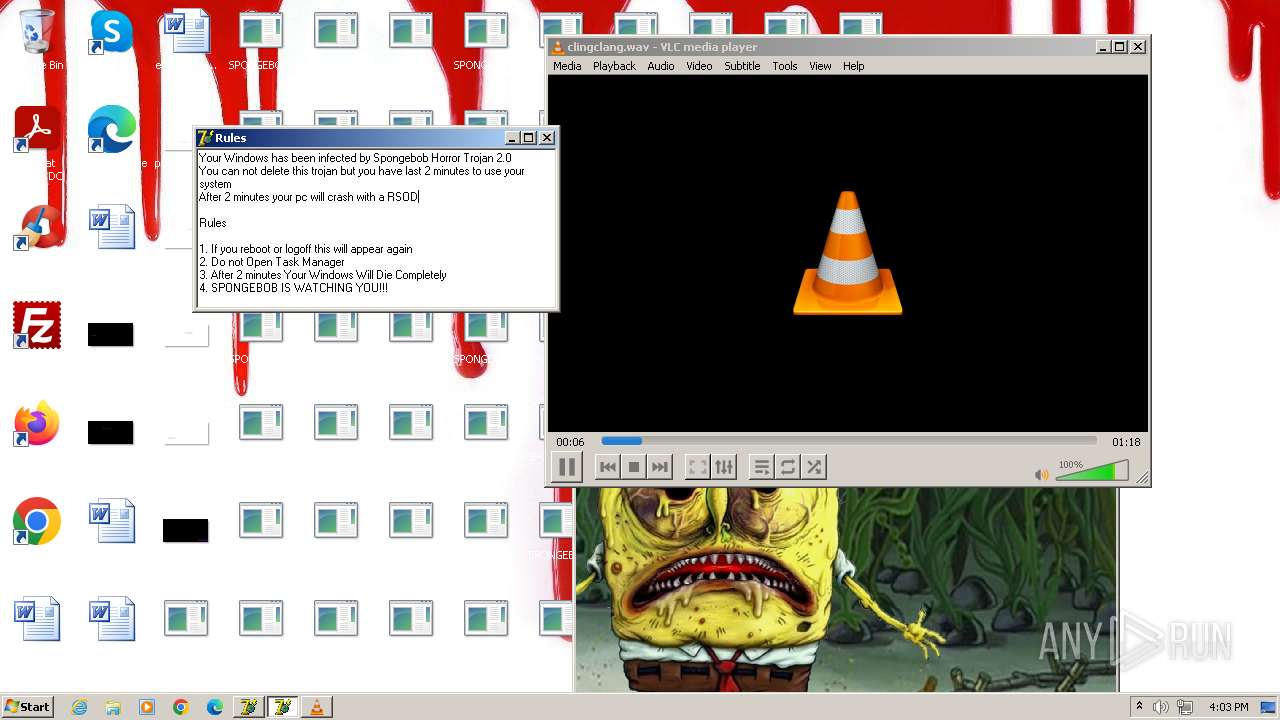
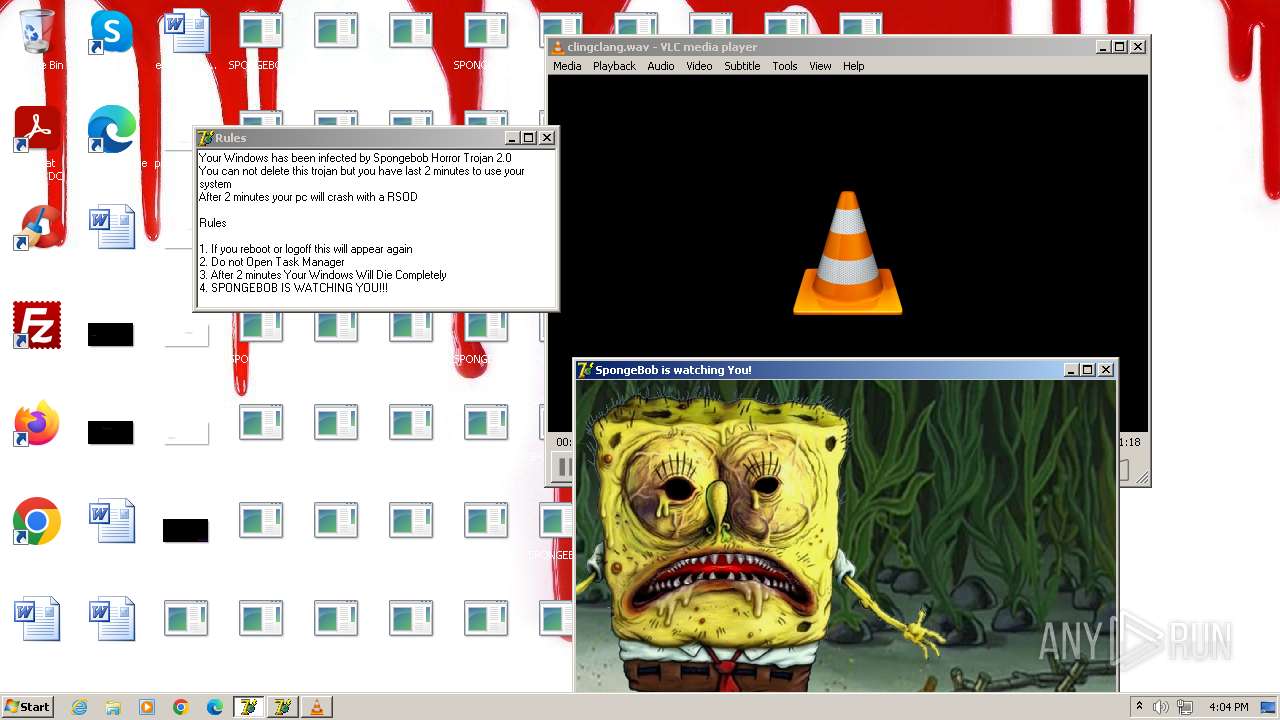
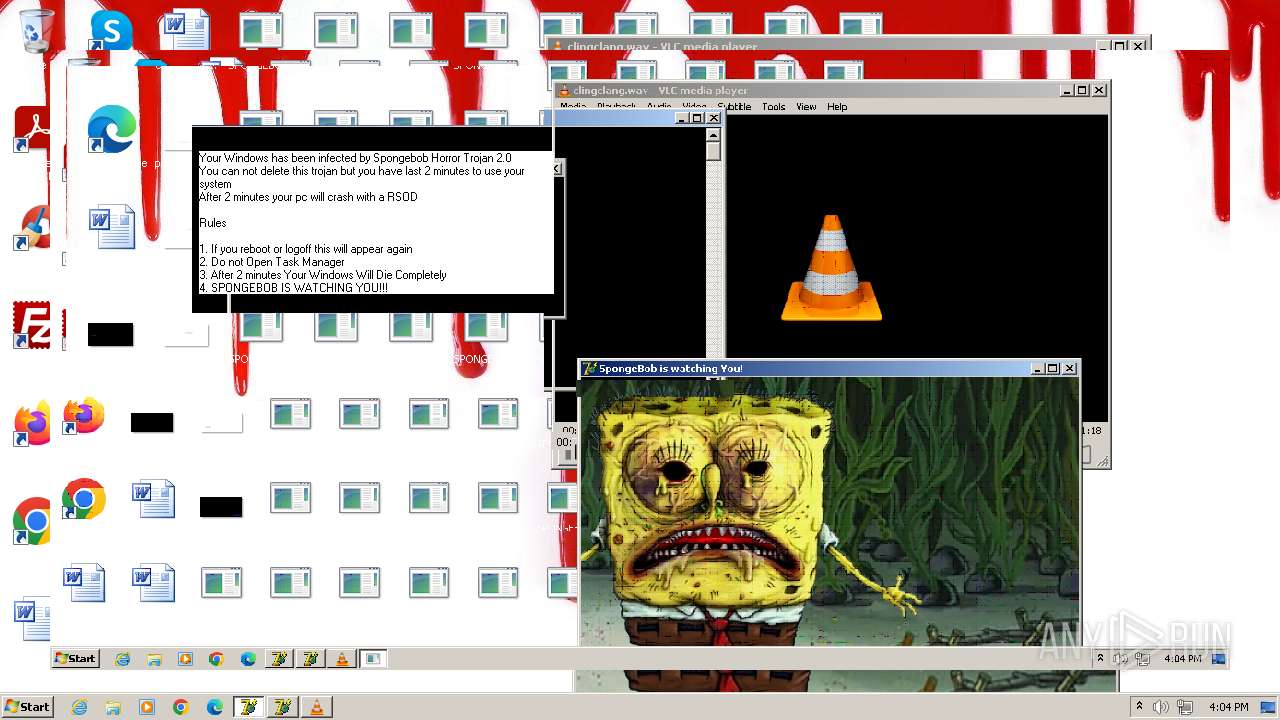
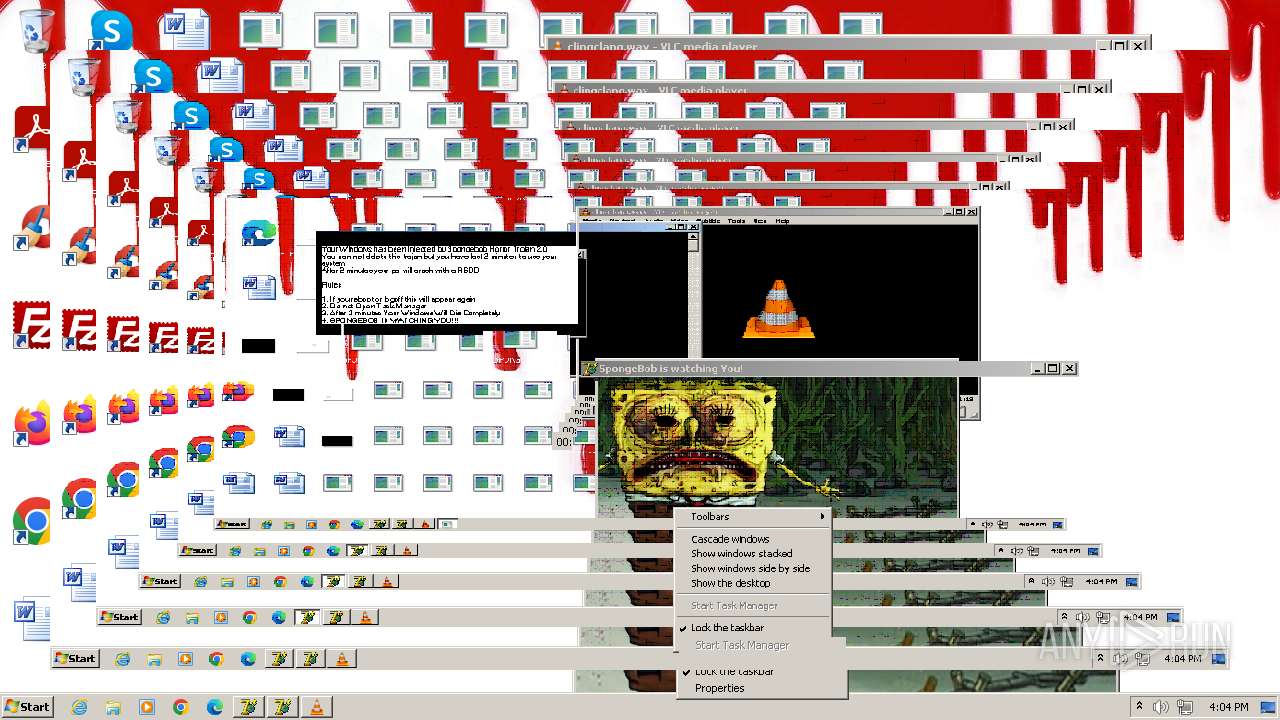
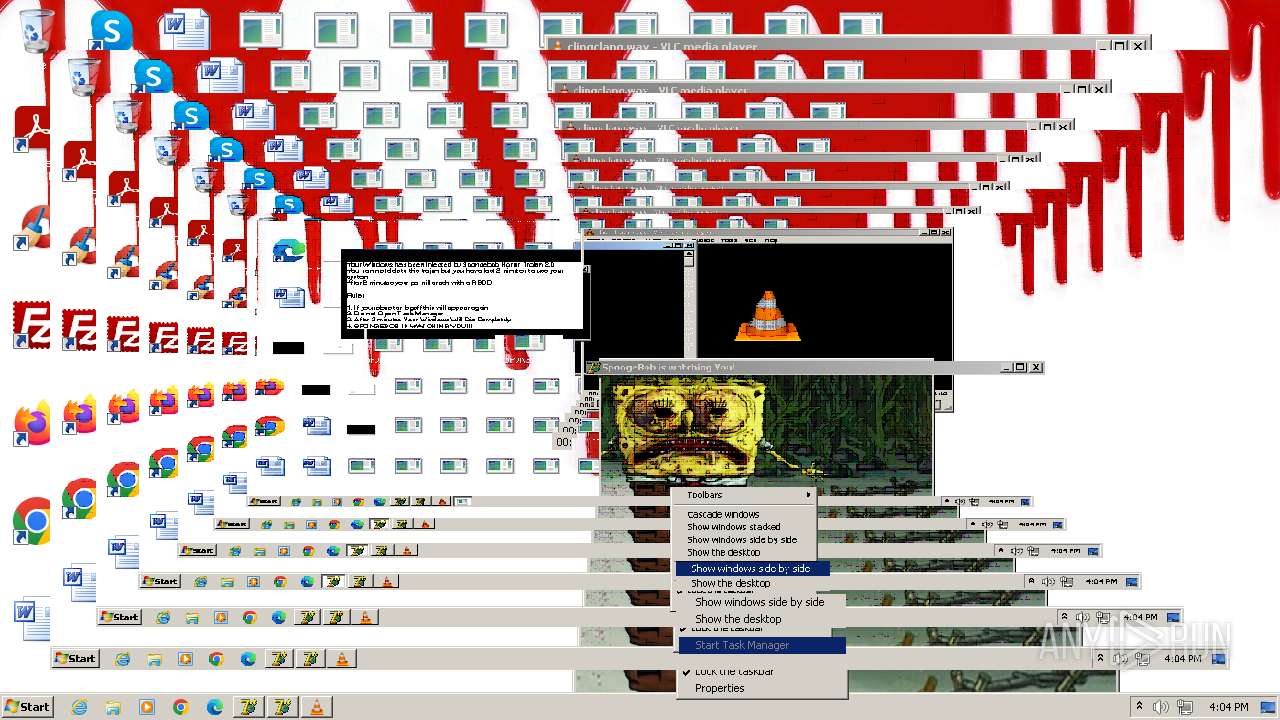
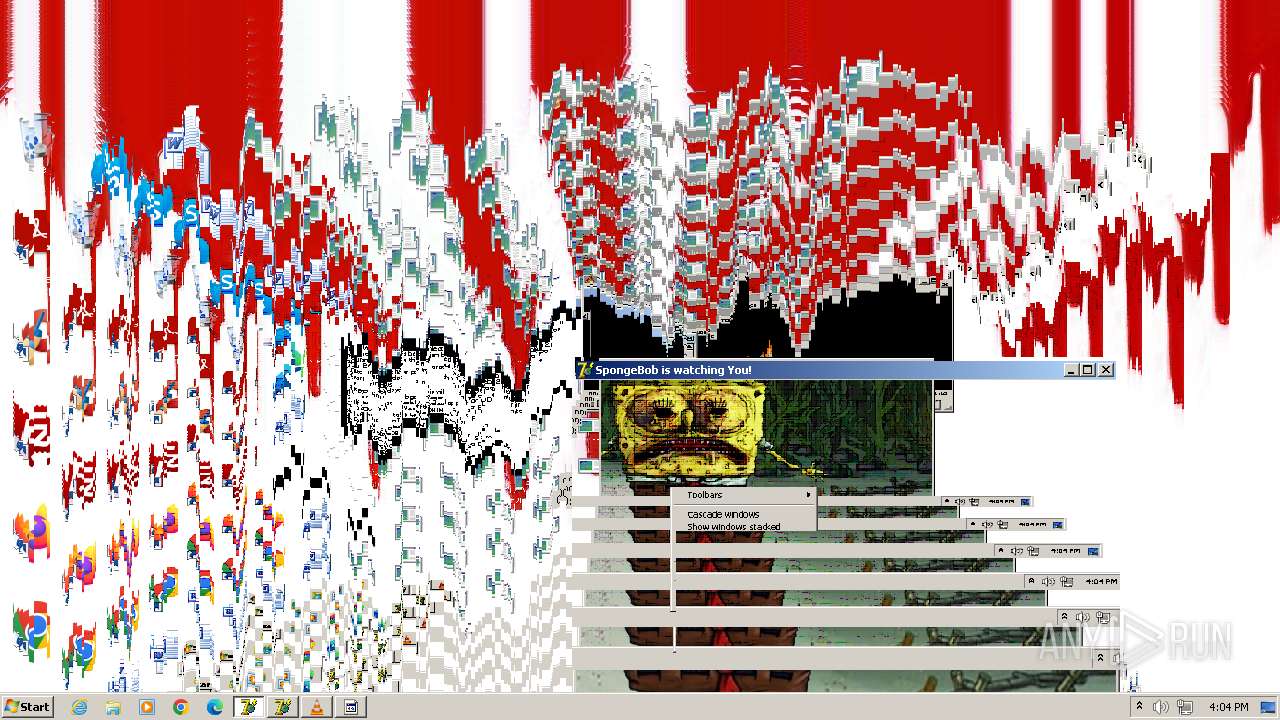
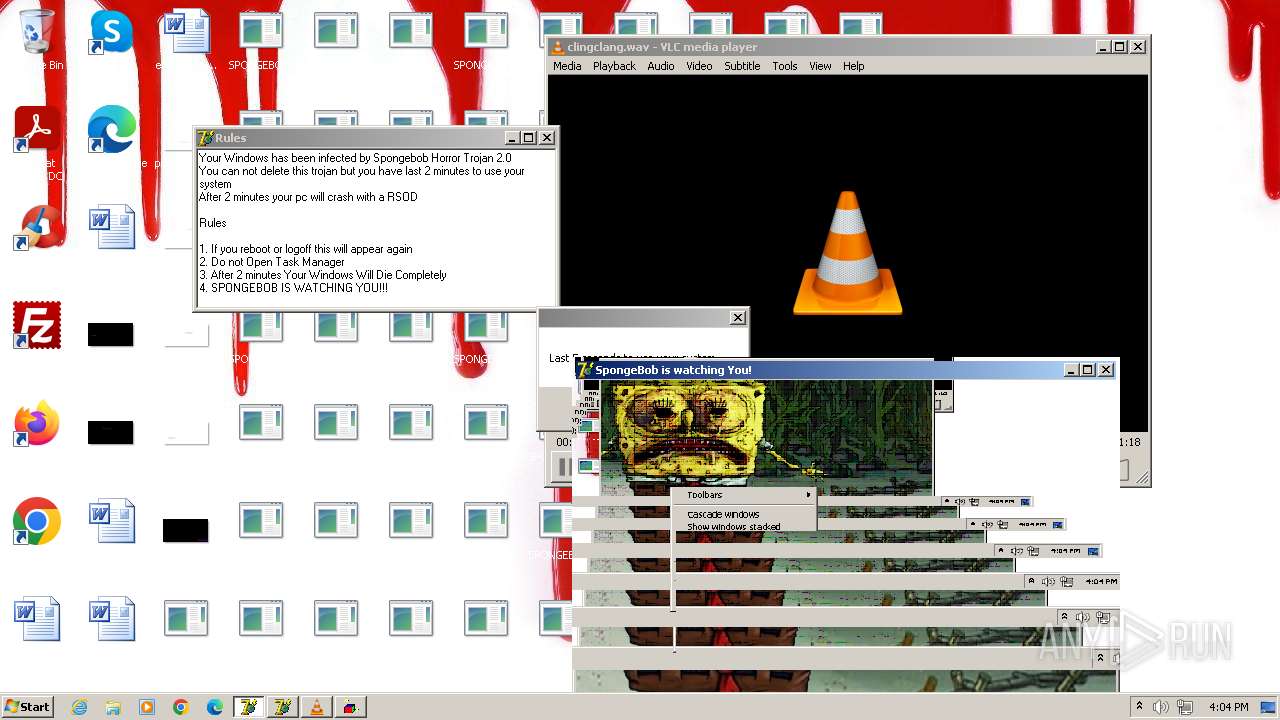
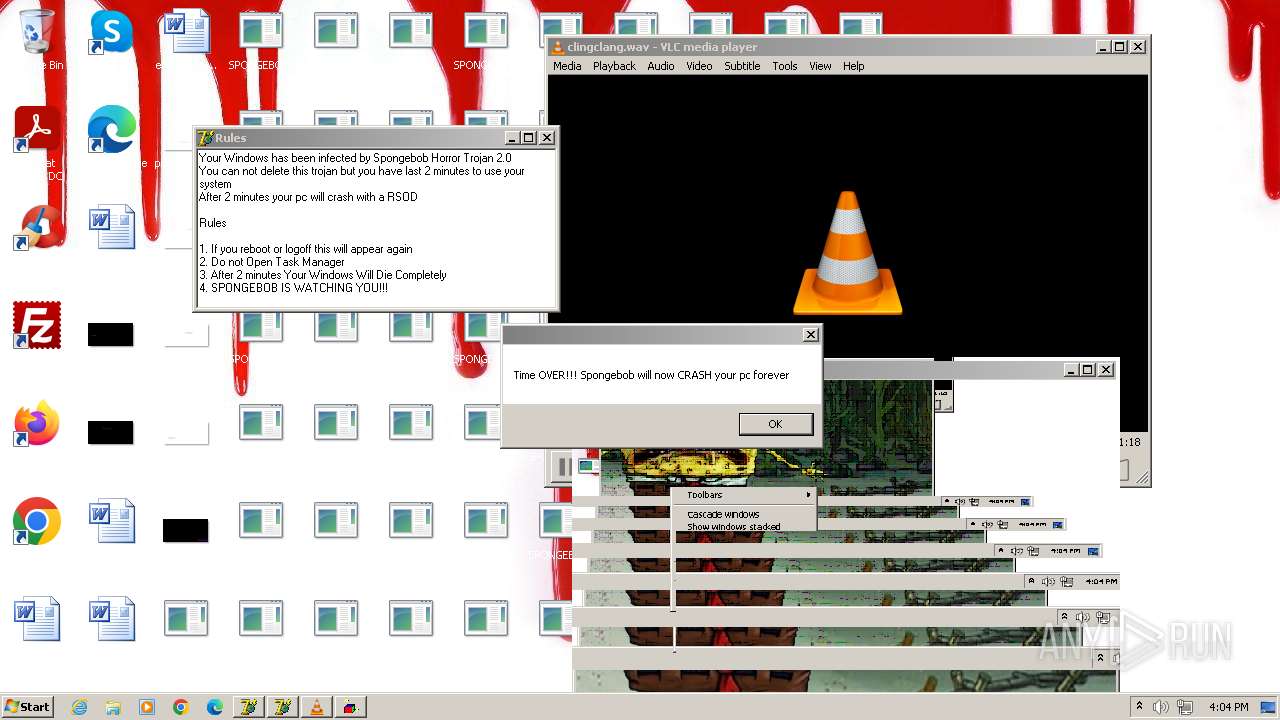
| File name: | HorrorBob2.exe |
| Full analysis: | https://app.any.run/tasks/df545912-b52e-459c-9c48-8da07af6747f |
| Verdict: | Malicious activity |
| Analysis date: | December 01, 2024, 16:01:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed, 3 sections |
| MD5: | 9331B20120075B2685D3888C196F2E34 |
| SHA1: | 1AF7D3DC4576EF8AAA06FA3199CF422B7657950B |
| SHA256: | 98A804D373C7E0E4F80155DF20358436E066ECF31C522C31DF2BA46923AC68C2 |
| SSDEEP: | 196608:zHvwfYWqhZPHE5D7cdPNPi17S+IRTX7UYVlj0EcLnKXanF6eeBUsjD2ABShiFiJj:vZ8R7c5527SpRTXQYVlYEGnKKF6eeWg6 |
MALICIOUS
Disables Windows Defender
- reg.exe (PID: 2840)
UAC/LUA settings modification
- reg.exe (PID: 2816)
Starts NET.EXE to view/add/change user profiles
- cmd.exe (PID: 3016)
- net.exe (PID: 3172)
Changes the autorun value in the registry
- reg.exe (PID: 2052)
SUSPICIOUS
Reads the Internet Settings
- HorrorBob2.exe (PID: 1608)
- sipnotify.exe (PID: 1572)
- Service64.exe (PID: 2116)
- RulesLauncher.exe (PID: 2376)
- BobLauncher.exe (PID: 2368)
- cmd.exe (PID: 2336)
Reads security settings of Internet Explorer
- HorrorBob2.exe (PID: 1608)
- Service64.exe (PID: 2116)
- RulesLauncher.exe (PID: 2376)
- BobLauncher.exe (PID: 2368)
Executable content was dropped or overwritten
- HorrorBob2.exe (PID: 1608)
- cmd.exe (PID: 3016)
- cmd.exe (PID: 2336)
- Service64.exe (PID: 2116)
Executing commands from a ".bat" file
- HorrorBob2.exe (PID: 1608)
- Service64.exe (PID: 2116)
- RulesLauncher.exe (PID: 2376)
- BobLauncher.exe (PID: 2368)
Starts CMD.EXE for commands execution
- HorrorBob2.exe (PID: 1608)
- Service64.exe (PID: 2116)
- RulesLauncher.exe (PID: 2376)
- BobLauncher.exe (PID: 2368)
The process executes VB scripts
- cmd.exe (PID: 3016)
- cmd.exe (PID: 2336)
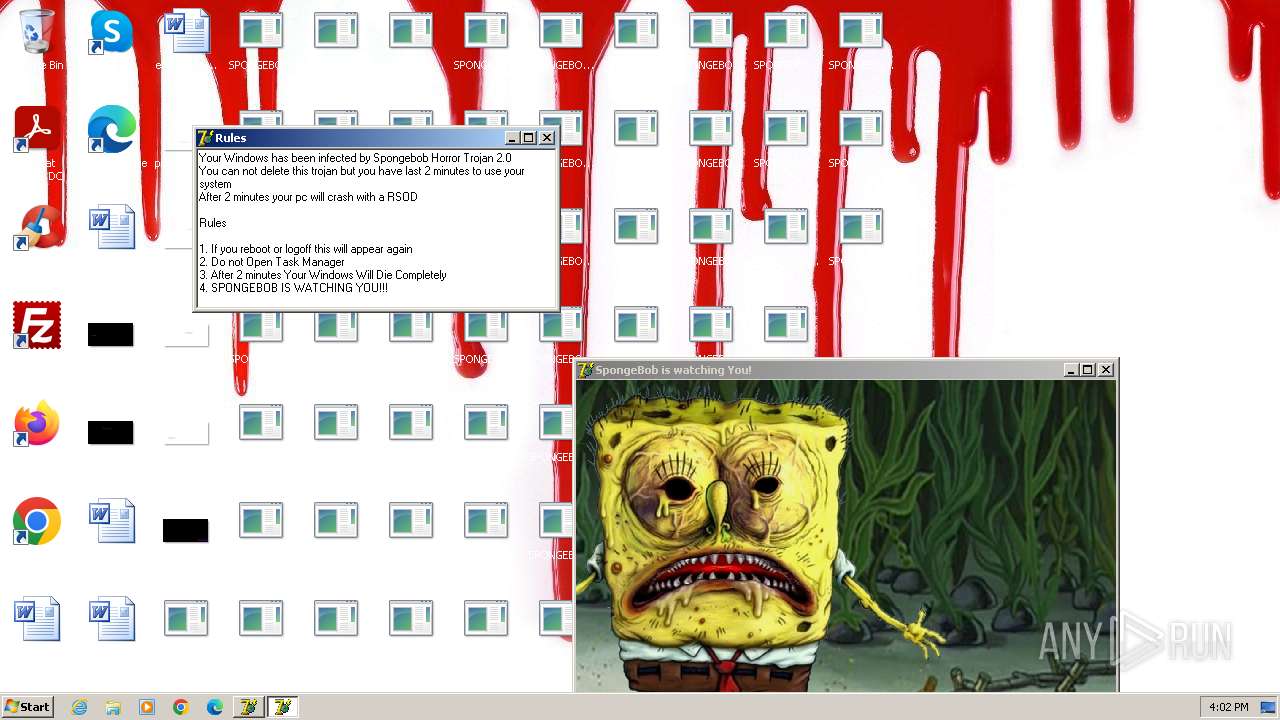
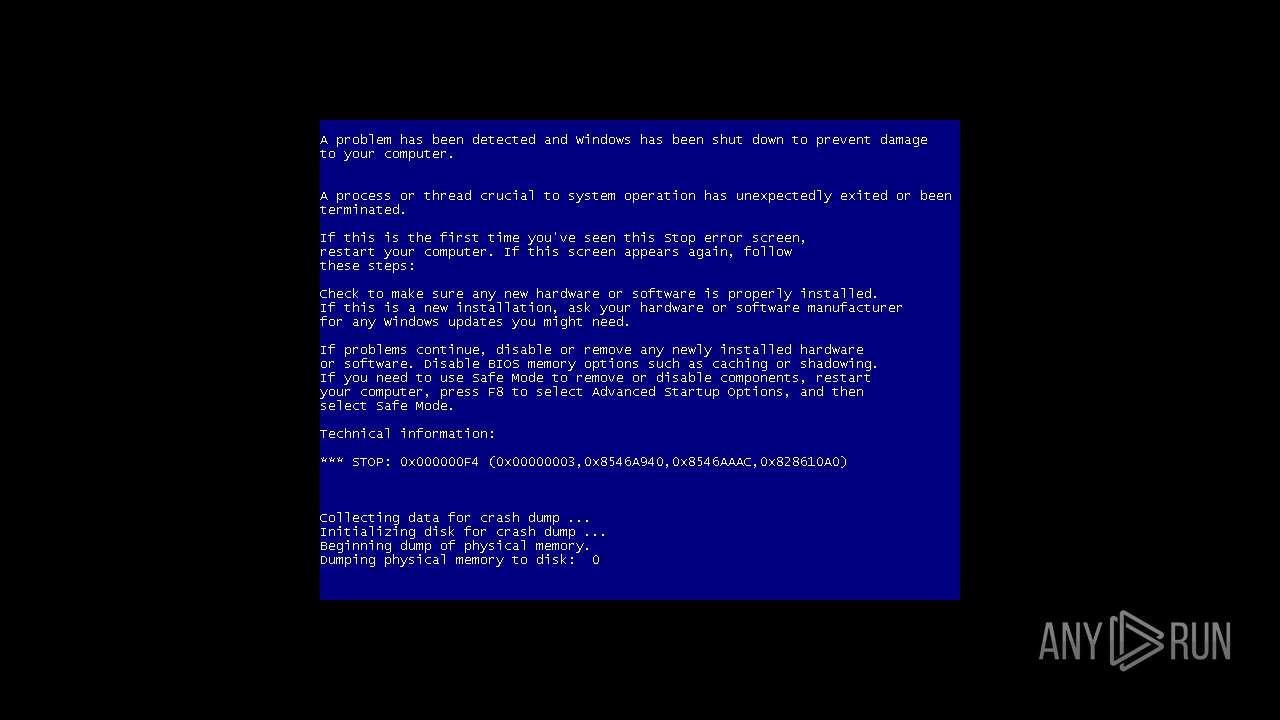
Changes the desktop background image
- reg.exe (PID: 448)
- reg.exe (PID: 1776)
Uses RUNDLL32.EXE to load library
- cmd.exe (PID: 3016)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 3016)
The system shut down or reboot
- cmd.exe (PID: 3016)
The process executes via Task Scheduler
- ctfmon.exe (PID: 1404)
- sipnotify.exe (PID: 1572)
The executable file from the user directory is run by the CMD process
- BobLauncher.exe (PID: 2368)
- RulesLauncher.exe (PID: 2376)
- inv.exe (PID: 2872)
- melter.exe (PID: 3044)
- melter.exe (PID: 3592)
- tunnel.exe (PID: 3328)
- icons.exe (PID: 3932)
- endpc.exe (PID: 3984)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2336)
Reads settings of System Certificates
- sipnotify.exe (PID: 1572)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2336)
INFO
Reads the computer name
- HorrorBob2.exe (PID: 1608)
- IMEKLMG.EXE (PID: 2088)
- IMEKLMG.EXE (PID: 2100)
- Service64.exe (PID: 2116)
- RulesLauncher.exe (PID: 2376)
- BobLauncher.exe (PID: 2368)
- vlc.exe (PID: 2396)
- wmpnscfg.exe (PID: 2712)
- wmpnscfg.exe (PID: 2736)
Checks supported languages
- HorrorBob2.exe (PID: 1608)
- IMEKLMG.EXE (PID: 2088)
- IMEKLMG.EXE (PID: 2100)
- Service64.exe (PID: 2116)
- BobLauncher.exe (PID: 2368)
- RulesLauncher.exe (PID: 2376)
- sbob.exe (PID: 2496)
- vlc.exe (PID: 2396)
- rules32.exe (PID: 2488)
- wmpnscfg.exe (PID: 2712)
- melter.exe (PID: 3044)
- vlc.exe (PID: 3184)
- tunnel.exe (PID: 3328)
- melter.exe (PID: 3592)
- icons.exe (PID: 3932)
- endpc.exe (PID: 3984)
- wmpnscfg.exe (PID: 2736)
- inv.exe (PID: 2872)
Create files in a temporary directory
- HorrorBob2.exe (PID: 1608)
- RulesLauncher.exe (PID: 2376)
- BobLauncher.exe (PID: 2368)
- Service64.exe (PID: 2116)
The process uses the downloaded file
- HorrorBob2.exe (PID: 1608)
- Service64.exe (PID: 2116)
- RulesLauncher.exe (PID: 2376)
- BobLauncher.exe (PID: 2368)
- cmd.exe (PID: 2336)
Reads security settings of Internet Explorer
- cscript.exe (PID: 2248)
- sipnotify.exe (PID: 1572)
Reads the time zone
- net1.exe (PID: 3160)
Process checks whether UAC notifications are on
- IMEKLMG.EXE (PID: 2100)
- IMEKLMG.EXE (PID: 2088)
Manual execution by a user
- IMEKLMG.EXE (PID: 2100)
- IMEKLMG.EXE (PID: 2088)
- Service64.exe (PID: 2116)
- wmpnscfg.exe (PID: 2712)
- wmpnscfg.exe (PID: 2736)
Reads the software policy settings
- sipnotify.exe (PID: 1572)
Sends debugging messages
- vlc.exe (PID: 2396)
- vlc.exe (PID: 3184)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (39.3) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (38.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (9.5) |
| .exe | | | Win32 Executable (generic) (6.5) |
| .exe | | | Generic Win/DOS Executable (2.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2010:11:08 13:12:07+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 12460032 |
| InitializedDataSize: | 4096 |
| UninitializedDataSize: | 3452928 |
| EntryPoint: | 0xf2c6c0 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.0.0.0 |
| ProductVersionNumber: | 2.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug, Pre-release, Private build |
| FileOS: | Windows 16-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| FileDescription: | NO!!! |
| FileVersion: | 2,0,0,0 |
| ProductVersion: | 2,0,0,0 |
Total processes
143
Monitored processes
56
Malicious processes
5
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 448 | reg add "HKEY_CURRENT_USER\Control Panel\Desktop" /v Wallpaper /t REG_SZ /d c:\Service64\blood.bmp /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1404 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CTF Loader Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1572 | C:\Windows\system32\sipnotify.exe -LogonOrUnlock | C:\Windows\System32\sipnotify.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: sipnotify Exit code: 0 Version: 6.1.7602.20480 (win7sp1_ldr_escrow.191010-1716) Modules
| |||||||||||||||
| 1608 | "C:\Users\admin\AppData\Local\Temp\HorrorBob2.exe" | C:\Users\admin\AppData\Local\Temp\HorrorBob2.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1744 | reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System /v DisableTaskMgr /t REG_DWORD /d 1 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1776 | reg.exe ADD HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\ActiveDesktop /v NoChangingWallPaper /t REG_DWORD /d 1 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1824 | "C:\Users\admin\AppData\Local\Temp\HorrorBob2.exe" | C:\Users\admin\AppData\Local\Temp\HorrorBob2.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1868 | shutdown /r /t 00 | C:\Windows\System32\shutdown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Shutdown and Annotation Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2052 | REG ADD "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /V "Acer NitroSense Update" /t REG_SZ /F /D "C:\Service64\Service64.exe" | C:\Windows\System32\reg.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2088 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /JPN /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
Total events
7 364
Read events
7 285
Write events
78
Delete events
1
Modification events
| (PID) Process: | (1608) HorrorBob2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1608) HorrorBob2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1608) HorrorBob2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1608) HorrorBob2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1744) reg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableTaskMgr |
Value: 1 | |||
| (PID) Process: | (448) reg.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | Wallpaper |
Value: c:\Service64\blood.bmp | |||
| (PID) Process: | (1776) reg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\ActiveDesktop |
| Operation: | write | Name: | NoChangingWallPaper |
Value: 1 | |||
| (PID) Process: | (2840) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender |
| Operation: | write | Name: | DisableAntiSpyware |
Value: 1 | |||
| (PID) Process: | (2816) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | EnableLUA |
Value: 0 | |||
| (PID) Process: | (2052) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Acer NitroSense Update |
Value: C:\Service64\Service64.exe | |||
Executable files
16
Suspicious files
1
Text files
17
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
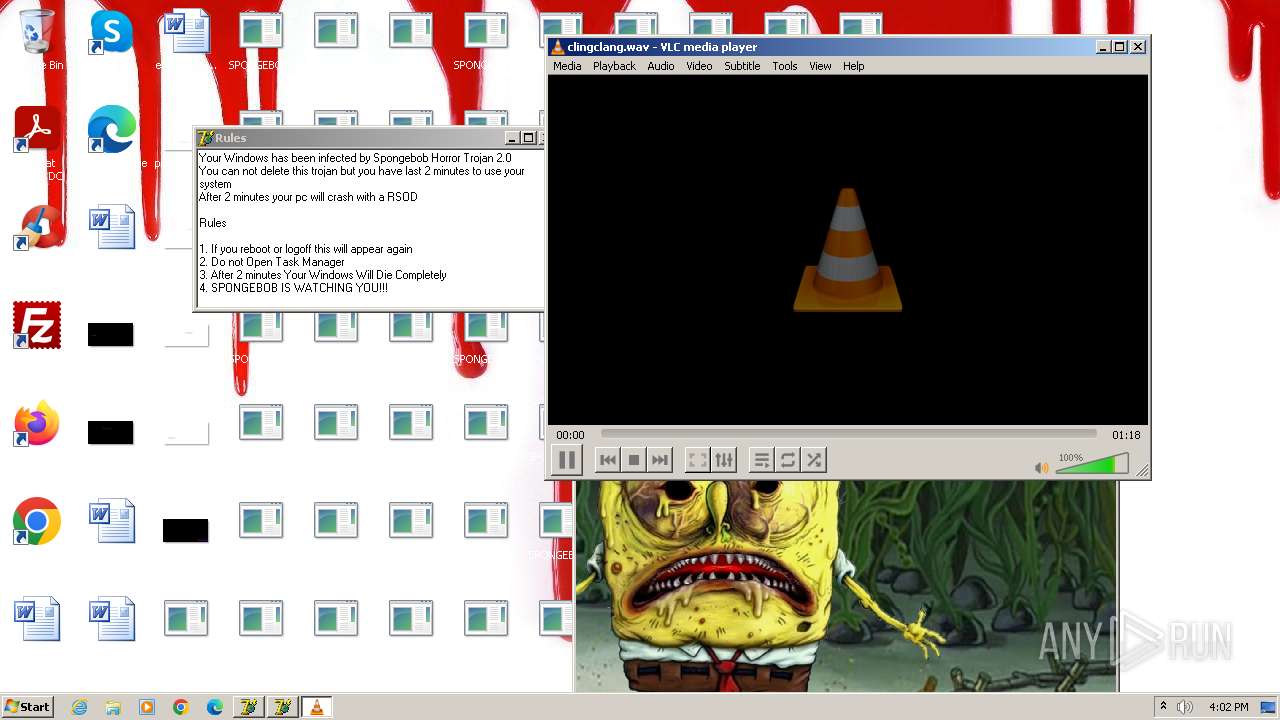
| 2116 | Service64.exe | C:\Users\admin\AppData\Local\Temp\5767.tmp\clingclang.wav | — | |
MD5:— | SHA256:— | |||
| 1608 | HorrorBob2.exe | C:\Users\admin\AppData\Local\Temp\8A02.tmp\blood.bmp | image | |
MD5:040D29B801E3488F7AEE3F9708128EEA | SHA256:FE28980C6E213619A95E5991DE2062A0187FC3054418E670E1C67D3C5B6B01DE | |||
| 3016 | cmd.exe | C:\Service64\Service64.exe | executable | |
MD5:B53852CB556EC28EFC39B986CADDB791 | SHA256:AE8CD9B5396770FA3C77140246365C3C501ECE718B52FD6B7FAED85C26B25D2A | |||
| 2116 | Service64.exe | C:\Users\admin\AppData\Local\Temp\5767.tmp\sbob.exe | executable | |
MD5:FA4B6BE9B66283FF8EC4B2FE856E4A8B | SHA256:9D85D06FCCD76500F5E5E58C1CDBC4781EEAFD4F7ECA0B2EA964531D3B4226F0 | |||
| 1608 | HorrorBob2.exe | C:\Users\admin\AppData\Local\Temp\8A02.tmp\Service64.exe | executable | |
MD5:B53852CB556EC28EFC39B986CADDB791 | SHA256:AE8CD9B5396770FA3C77140246365C3C501ECE718B52FD6B7FAED85C26B25D2A | |||
| 2116 | Service64.exe | C:\Users\admin\AppData\Local\Temp\5767.tmp\Service64.bat | text | |
MD5:141BD03FB7E15FFBF38DB5879F3879C1 | SHA256:61601569A5BA964E81C80E020350C4EB0CF4D3AB30A259BB356A5DEC68871DC5 | |||
| 2116 | Service64.exe | C:\Users\admin\AppData\Local\Temp\5767.tmp\BobLauncher.exe | executable | |
MD5:B44D2B6F7B4351EEB00137B1AEBB83C4 | SHA256:3623BE22B2F67981547E223BDDEC99B8CEEB3FB065212FF3DA076A3EF0A8C813 | |||
| 2116 | Service64.exe | C:\Users\admin\AppData\Local\Temp\5767.tmp\icons.exe | executable | |
MD5:7750B3DC87374EEE0CB0E1D7D60A82BF | SHA256:98FBD2023A64A375ADC537D4BFB403EA5BF81E11DFDA4143163A119D12C33D75 | |||
| 2116 | Service64.exe | C:\Users\admin\AppData\Local\Temp\5767.tmp\endpc.exe | executable | |
MD5:4ACAAA74997F3F2FA44E7FB9CA0CDE57 | SHA256:BFF77D77ECD459BD9002978B47F7B5F2FDB45ECDE752EDB88D101E2E921D0243 | |||
| 2336 | cmd.exe | C:\Service64\rules32.exe | executable | |
MD5:B364D94B2C8197C16EBF1DA95486E587 | SHA256:1BB6E2850C2BFD953DF42F72A4A99C5762E7D005754404FD3E0D8D722CC3947A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
14
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1572 | sipnotify.exe | HEAD | 200 | 104.101.237.73:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133775425603430000 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
1108 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
1096 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
1452 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
1572 | sipnotify.exe | 104.101.237.73:80 | query.prod.cms.rt.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
query.prod.cms.rt.microsoft.com |
| whitelisted |