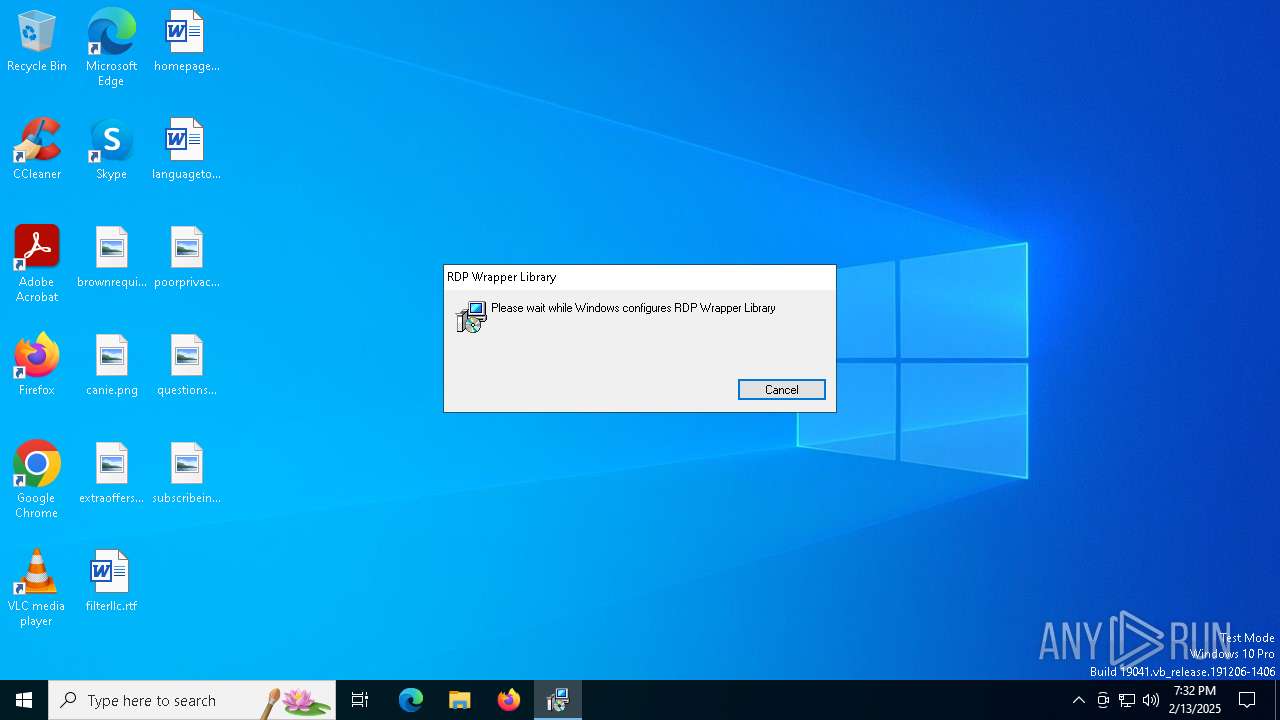
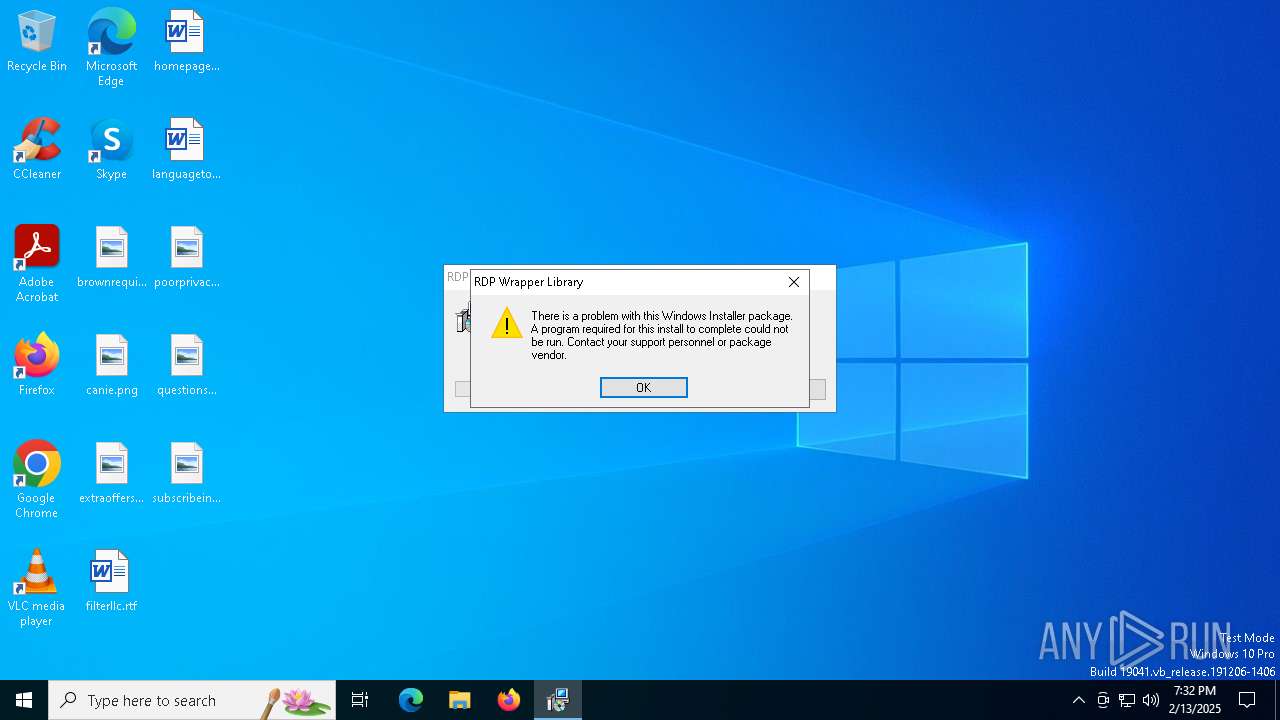
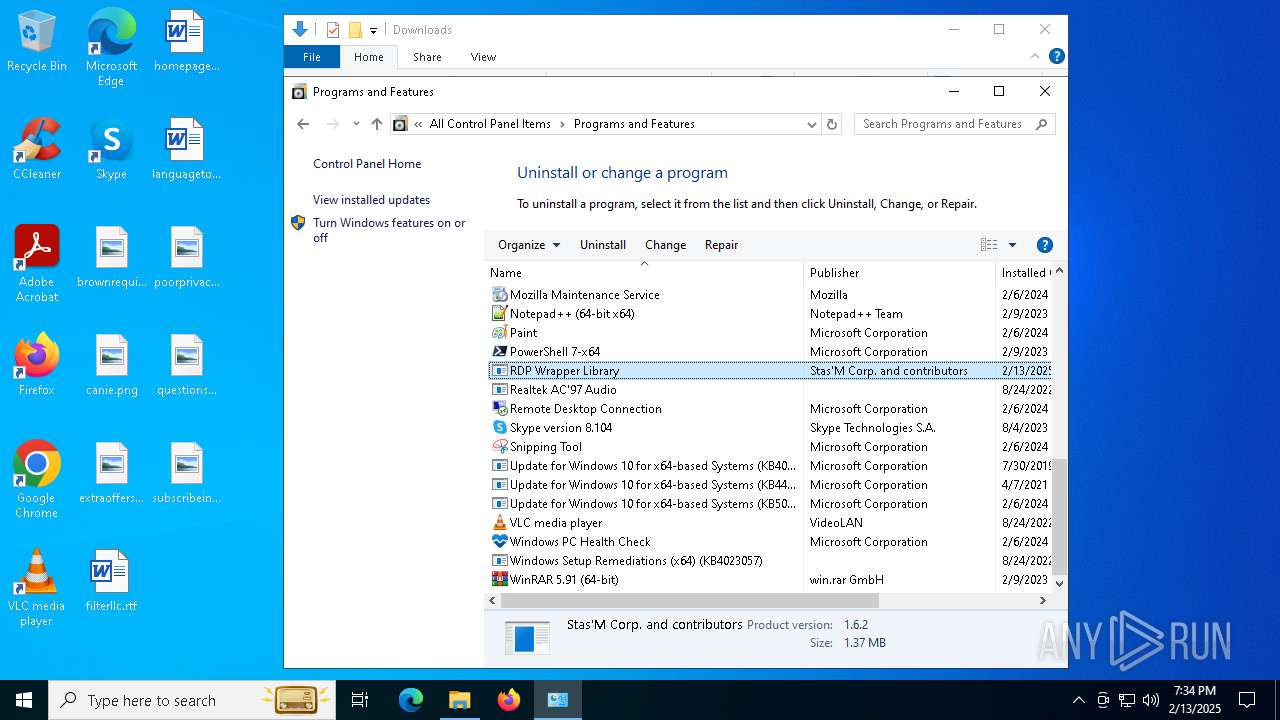
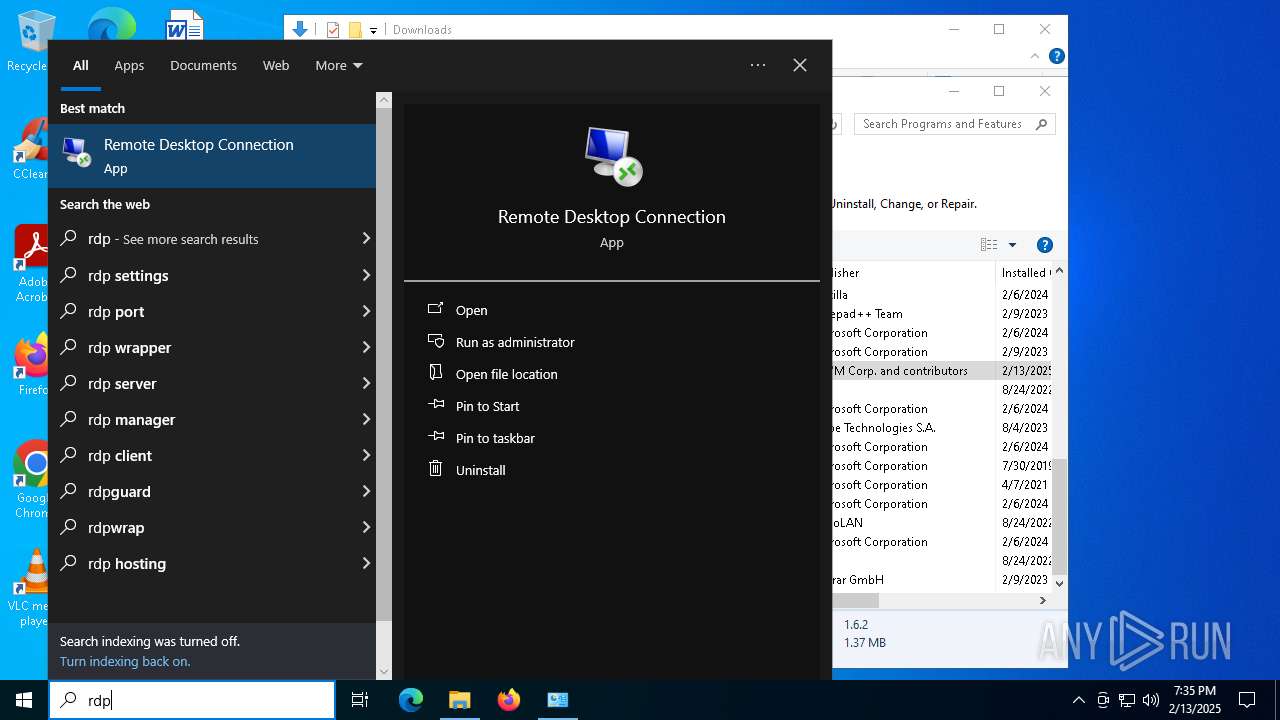
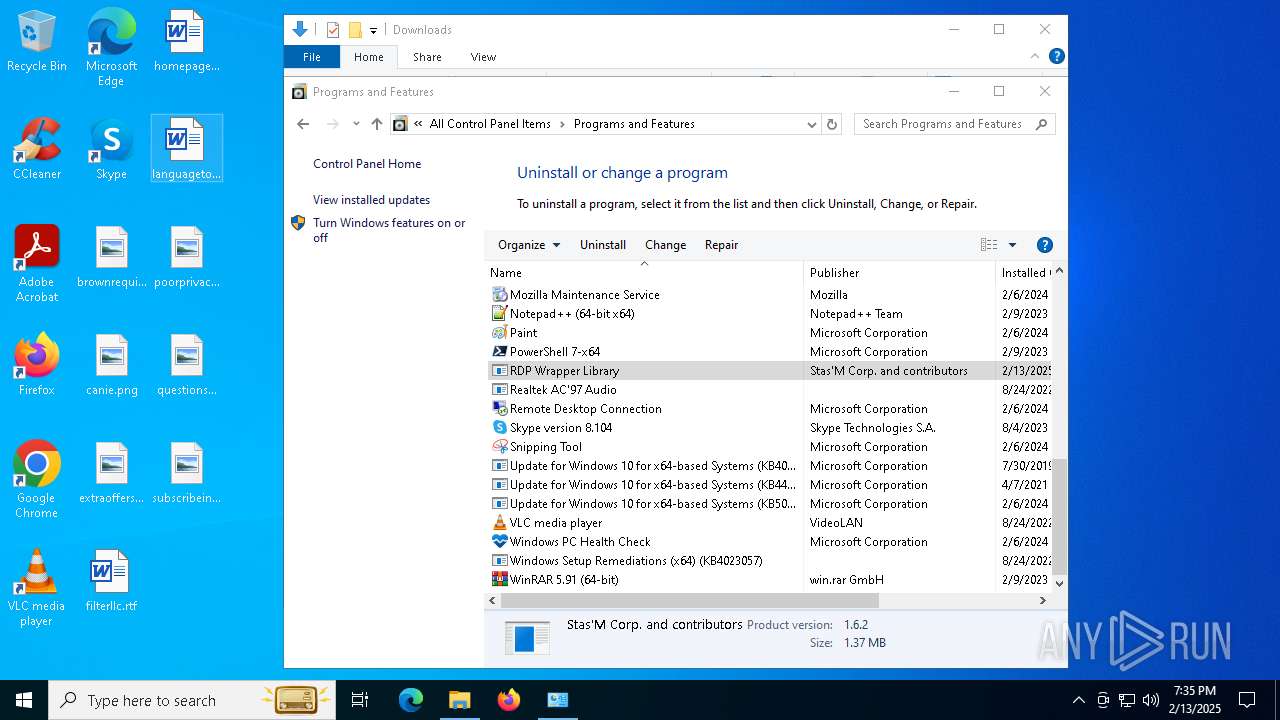
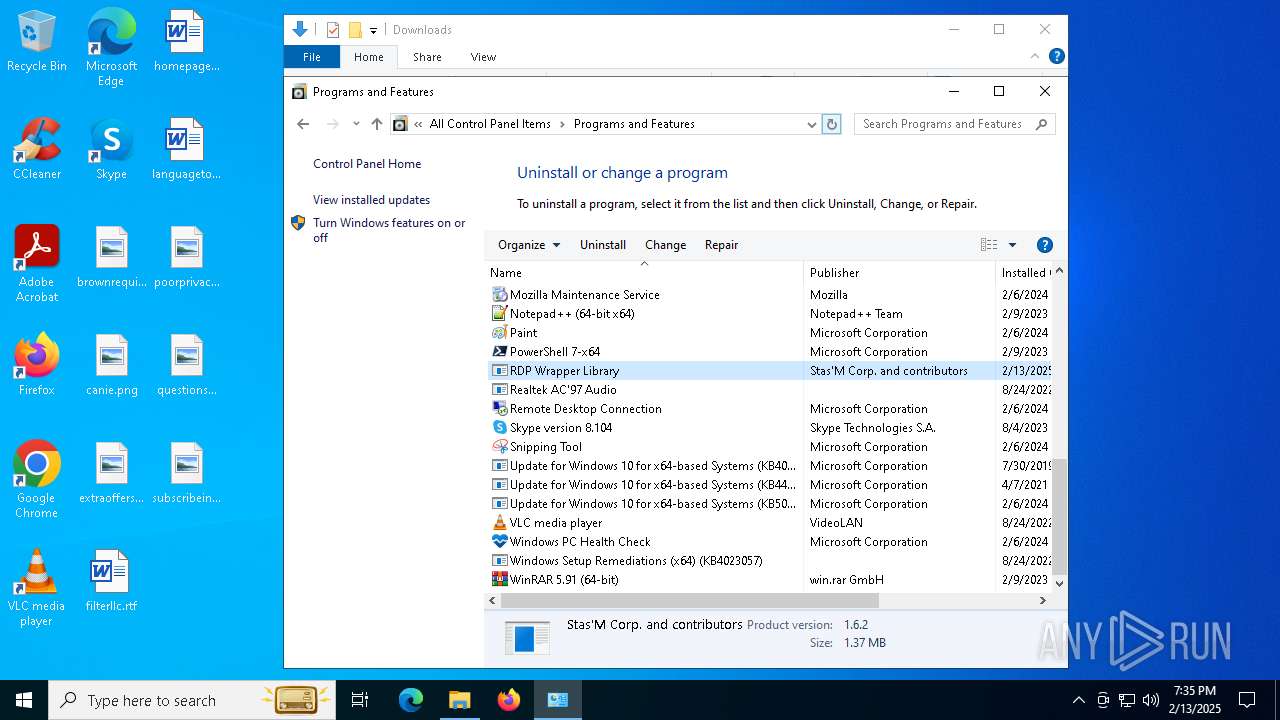
| File name: | RDPWInst-v1.6.2.msi |
| Full analysis: | https://app.any.run/tasks/be157d15-45d4-487f-bf1c-4df7ee40082b |
| Verdict: | Malicious activity |
| Analysis date: | February 13, 2025, 19:32:37 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, MSI Installer, Code page: 1252, Title: Installation Database, Subject: RDP Wrapper Library, Author: Stas'M Corp. and contributors, Keywords: Installer, Comments: This installer database contains the logic and data required to install RDP Wrapper Library., Template: Intel;1033, Revision Number: {DB3018A4-F249-43B2-98B5-79F64E34E88C}, Create Time/Date: Wed Dec 27 20:02:46 2017, Last Saved Time/Date: Wed Dec 27 20:02:46 2017, Number of Pages: 200, Number of Words: 2, Name of Creating Application: Windows Installer XML Toolset (3.11.0.1701), Security: 2 |
| MD5: | 92CBBE2D06D03C156C83AE1A02AB30E3 |
| SHA1: | 7D14F457F193D75DD7F52BECDEE5CF25B948573B |
| SHA256: | 9899FFECF141AB4535EC702FACBF2B4233903B428B862F3A87E635D09C6244DE |
| SSDEEP: | 12288:GnAYhZFoqIVAV0yjNZzucNNZLVk/dJJibRoQu9kzWEYCdrflYemcS1/U6:UASZFKAVbBZzu0Ni49oQu9DuZYebSS6 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the Windows owner or organization settings
- msiexec.exe (PID: 5200)
Searches for installed software
- explorer.exe (PID: 4548)
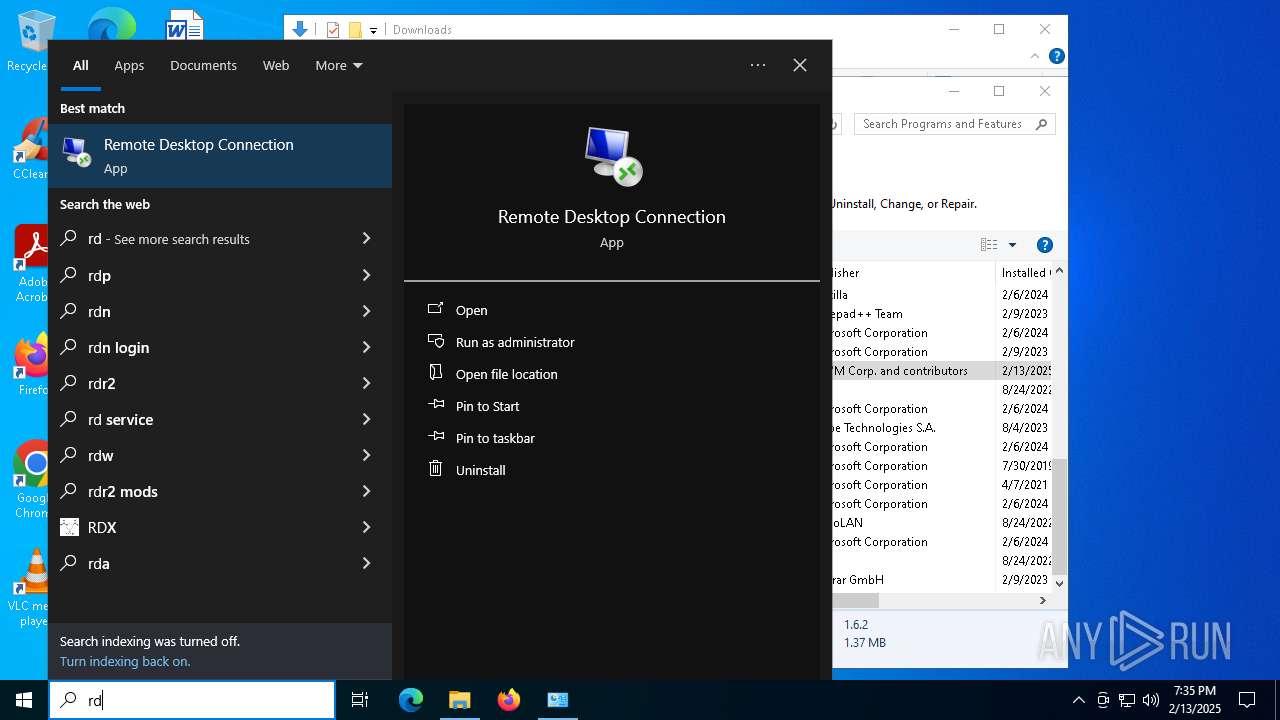
Reads the history of recent RDP connections
- mstsc.exe (PID: 3848)
INFO
Reads the computer name
- msiexec.exe (PID: 5200)
Executable content was dropped or overwritten
- msiexec.exe (PID: 5200)
The sample compiled with english language support
- msiexec.exe (PID: 1944)
- msiexec.exe (PID: 5200)
Reads security settings of Internet Explorer
- explorer.exe (PID: 4548)
Checks supported languages
- msiexec.exe (PID: 5200)
Create files in a temporary directory
- msiexec.exe (PID: 1944)
Creates a software uninstall entry
- msiexec.exe (PID: 5200)
Manual execution by a user
- mstsc.exe (PID: 3848)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Installer (100) |
|---|
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | RDP Wrapper Library |
| Author: | Stas'M Corp. and contributors |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install RDP Wrapper Library. |
| Template: | Intel;1033 |
| RevisionNumber: | {DB3018A4-F249-43B2-98B5-79F64E34E88C} |
| CreateDate: | 2017:12:27 20:02:46 |
| ModifyDate: | 2017:12:27 20:02:46 |
| Pages: | 200 |
| Words: | 2 |
| Software: | Windows Installer XML Toolset (3.11.0.1701) |
| Security: | Read-only recommended |
Total processes
137
Monitored processes
7
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1944 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\RDPWInst-v1.6.2.msi | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 1603 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3640 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3848 | "C:\WINDOWS\system32\mstsc.exe" | C:\Windows\System32\mstsc.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Remote Desktop Connection Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4144 | C:\WINDOWS\SysWOW64\DllHost.exe /Processid:{06622D85-6856-4460-8DE1-A81921B41C4B} | C:\Windows\SysWOW64\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4548 | C:\WINDOWS\explorer.exe /factory,{5BD95610-9434-43C2-886C-57852CC8A120} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5200 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6276 | "C:\ProgramData\Package Cache\{37ea5771-3352-4a52-9fac-9297331daebd}\RDPWInst.exe" -i -o | C:\ProgramData\Package Cache\{37ea5771-3352-4a52-9fac-9297331daebd}\RDPWInst.exe | — | msiexec.exe | |||||||||||
User: admin Company: Stas'M Corp. Integrity Level: MEDIUM Description: RDP Wrapper Library Installer Exit code: 3221226540 Version: 2.5.0.0 Modules
| |||||||||||||||
Total events
19 571
Read events
19 435
Write events
126
Delete events
10
Modification events
| (PID) Process: | (5200) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 50140000D5FECD0E4E7EDB01 | |||
| (PID) Process: | (5200) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 6BD366EF2469E30EB08FB321373998A079ABF7DC13BAC48A33015CDA8010F846 | |||
| (PID) Process: | (5200) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (5200) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Folders |
| Operation: | write | Name: | C:\Config.Msi\ |
Value: | |||
| (PID) Process: | (5200) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | write | Name: | C:\Config.Msi\13807f.rbs |
Value: 31161934 | |||
| (PID) Process: | (5200) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | write | Name: | C:\Config.Msi\13807f.rbsLow |
Value: 282269536 | |||
| (PID) Process: | (5200) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Folders |
| Operation: | write | Name: | C:\Users\admin\AppData\Roaming\Microsoft\Installer\ |
Value: | |||
| (PID) Process: | (5200) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Components\1D77DFFAC53B3F649AF76168CD758B8B |
| Operation: | write | Name: | 1775AE73253325A4F9CA297933D1EADB |
Value: C:\ProgramData\Package Cache\{37ea5771-3352-4a52-9fac-9297331daebd}\RDPWInst.exe | |||
| (PID) Process: | (5200) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Folders |
| Operation: | write | Name: | C:\ProgramData\Package Cache\{37ea5771-3352-4a52-9fac-9297331daebd}\ |
Value: | |||
| (PID) Process: | (5200) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Products\1775AE73253325A4F9CA297933D1EADB\InstallProperties |
| Operation: | write | Name: | LocalPackage |
Value: C:\WINDOWS\Installer\138080.msi | |||
Executable files
3
Suspicious files
15
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5200 | msiexec.exe | C:\Windows\Temp\~DF15BA237448EDB2C1.TMP | binary | |
MD5:89F3F160A0ECE914906DE2EDD9FEA4ED | SHA256:D1D249045D15DB3FD8470DDC40AD3599DC0AD8344F03AA339AAE64F80380417A | |||
| 5200 | msiexec.exe | C:\Windows\Installer\13807e.msi | executable | |
MD5:92CBBE2D06D03C156C83AE1A02AB30E3 | SHA256:9899FFECF141AB4535EC702FACBF2B4233903B428B862F3A87E635D09C6244DE | |||
| 5200 | msiexec.exe | C:\Config.Msi\13807f.rbs | binary | |
MD5:C09A2965E9A9DCFD6684EA6C75A25678 | SHA256:A123FDA44942527E014D1F71FBED58D58BA5BB4EAE81C0726ABBC2666DFB00E0 | |||
| 5200 | msiexec.exe | C:\Windows\Installer\MSI8B3C.tmp | binary | |
MD5:81E02FA0E20C96C2F3A3D0D9E8CDFBEB | SHA256:C5B47E3118CAE0224C2DE784C95B0479E44D55B9CBCAED83F01F2C717EAB4F66 | |||
| 5200 | msiexec.exe | C:\Windows\Temp\~DFEF4E8B88B7455EE1.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 5200 | msiexec.exe | C:\Windows\Temp\~DFEF2A0B278ADDF46C.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 5200 | msiexec.exe | C:\ProgramData\Package Cache\{37ea5771-3352-4a52-9fac-9297331daebd}\RDPWInst.exe | executable | |
MD5:3288C284561055044C489567FD630AC2 | SHA256:AC92D4C6397EB4451095949AC485EF4EC38501D7BB6F475419529AE67E297753 | |||
| 5200 | msiexec.exe | C:\Windows\Installer\138080.msi | executable | |
MD5:92CBBE2D06D03C156C83AE1A02AB30E3 | SHA256:9899FFECF141AB4535EC702FACBF2B4233903B428B862F3A87E635D09C6244DE | |||
| 5200 | msiexec.exe | C:\Windows\Installer\inprogressinstallinfo.ipi | binary | |
MD5:89F3F160A0ECE914906DE2EDD9FEA4ED | SHA256:D1D249045D15DB3FD8470DDC40AD3599DC0AD8344F03AA339AAE64F80380417A | |||
| 5200 | msiexec.exe | C:\Windows\Temp\~DF94517C7B9DCF92A9.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
36
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1176 | svchost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6964 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6964 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6360 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 92.123.104.20:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
1176 | svchost.exe | 20.190.159.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 23.54.109.203:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 23.54.109.203:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1076 | svchost.exe | 69.192.162.125:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6964 | SIHClient.exe | 4.245.163.56:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6964 | SIHClient.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |