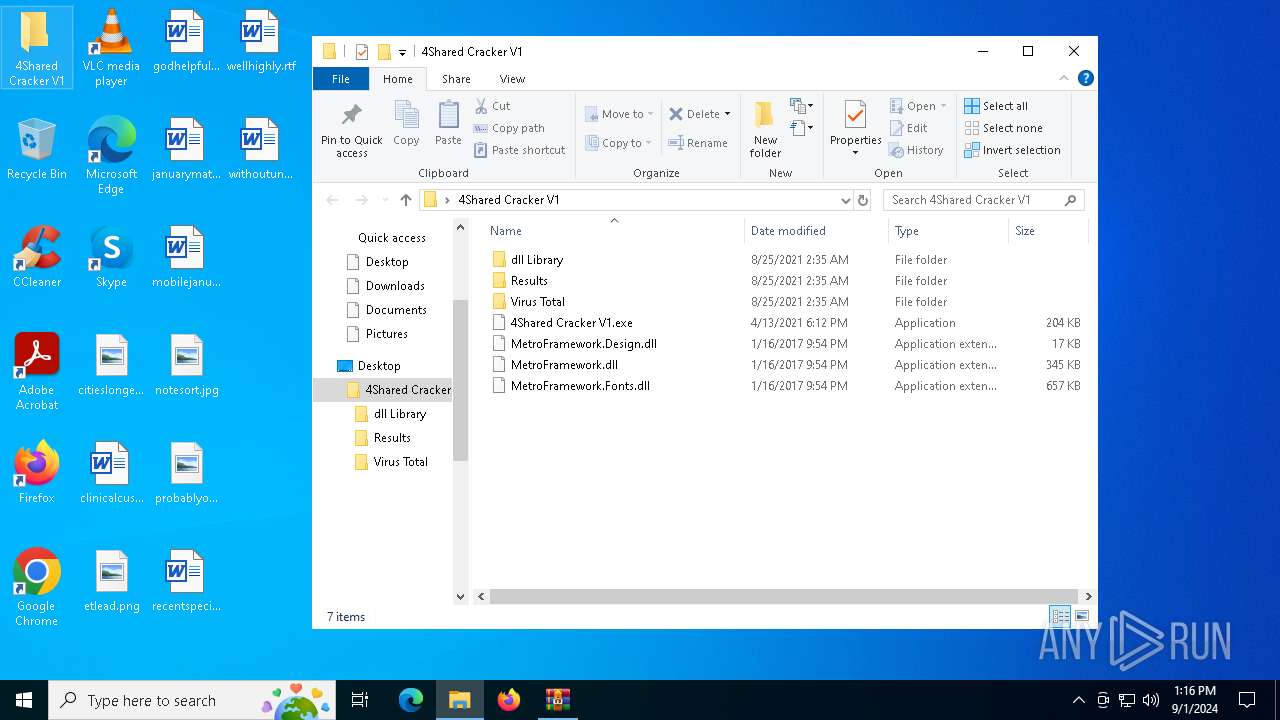
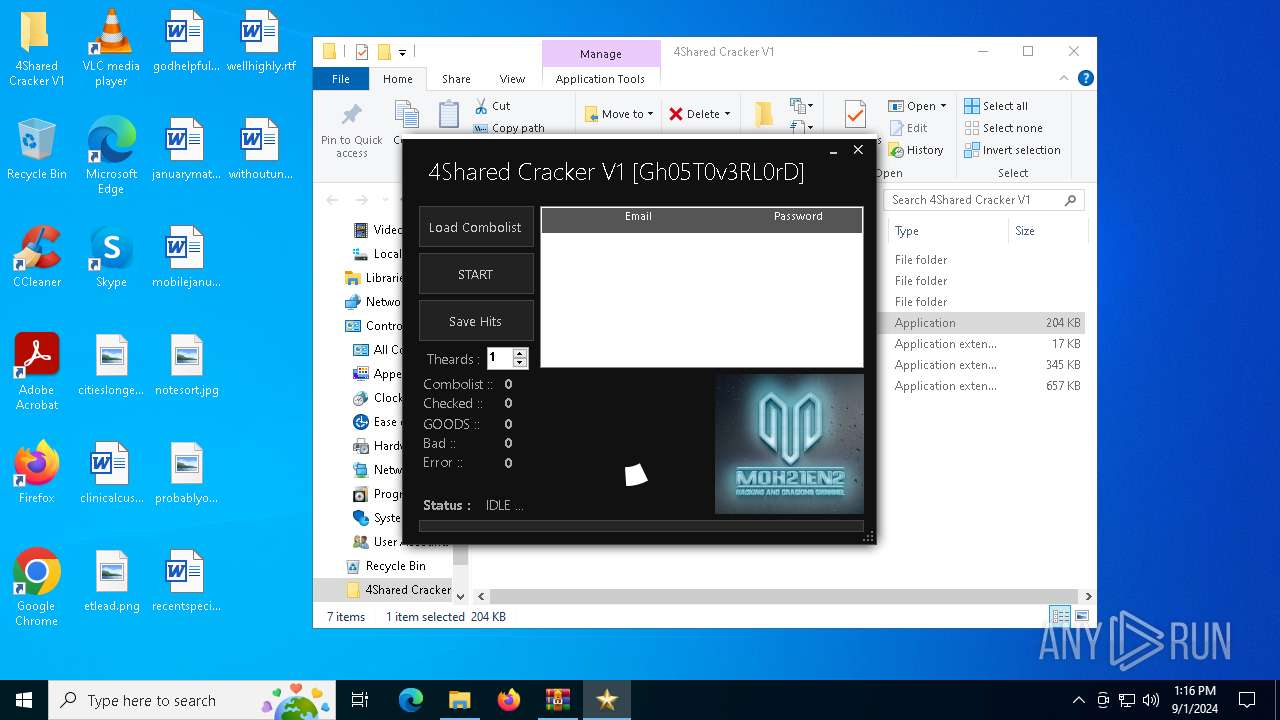
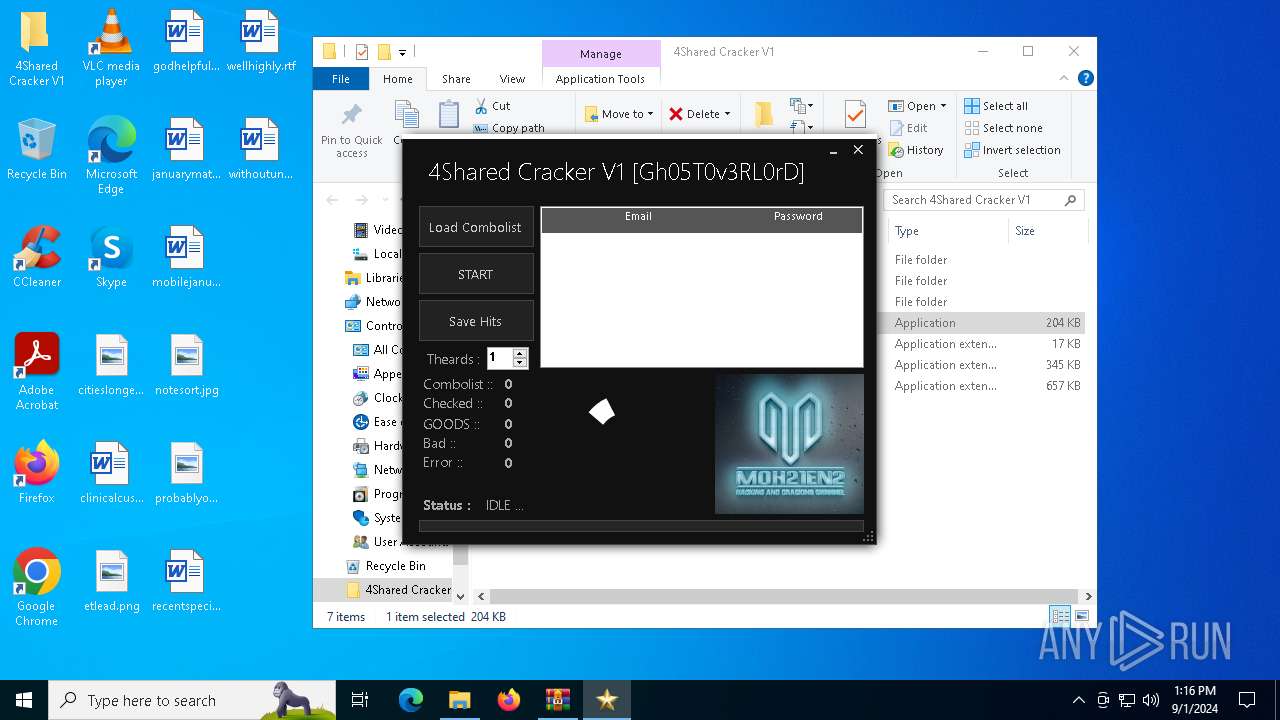
| File name: | 4Shared Cracker V1.rar |
| Full analysis: | https://app.any.run/tasks/a7d68869-85e7-4230-9716-36e63cca4aaf |
| Verdict: | Malicious activity |
| Analysis date: | September 01, 2024, 13:15:47 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 88E2A021D53B7B74D00DDBFCA68EF4D1 |
| SHA1: | D55178B212F2DD38A7FB7B4710D0A7D142CB00F3 |
| SHA256: | 9899FF3034DC223433897000E9C7AF565B62EFB10354A812FEE42FB340681B80 |
| SSDEEP: | 49152:EKHybdzJGl+c6ybDHJ6pYNfdK58+g62Q1PmC/WgVh9SMTuHSd83jwKuhTW/0mx8P:VQzJ63H0pKWg62Q1PHOWhMIdhTW/Ze3f |
MALICIOUS
Adds path to the Windows Defender exclusion list
- Launcher.exe (PID: 2384)
Changes the autorun value in the registry
- Launcher.exe (PID: 2384)
Create files in the Startup directory
- Launcher.exe (PID: 2384)
SUSPICIOUS
Write to the desktop.ini file (may be used to cloak folders)
- WinRAR.exe (PID: 7052)
Reads security settings of Internet Explorer
- 4Shared Cracker V1.exe (PID: 6276)
- Launcher.exe (PID: 2384)
- Windows Services.exe (PID: 2080)
Reads the date of Windows installation
- 4Shared Cracker V1.exe (PID: 6276)
- Launcher.exe (PID: 2384)
- Windows Services.exe (PID: 2080)
Script adds exclusion path to Windows Defender
- Launcher.exe (PID: 2384)
Starts POWERSHELL.EXE for commands execution
- Launcher.exe (PID: 2384)
The process creates files with name similar to system file names
- Launcher.exe (PID: 2384)
Executable content was dropped or overwritten
- Launcher.exe (PID: 2384)
Drops the executable file immediately after the start
- Launcher.exe (PID: 2384)
Found regular expressions for crypto-addresses (YARA)
- Runtime Explorer.exe (PID: 6488)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 7052)
- 4Shared Cracker V1.exe (PID: 6276)
- Launcher.exe (PID: 2384)
- Windows Services.exe (PID: 2080)
- powershell.exe (PID: 6464)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7052)
Reads the computer name
- 4Shared Cracker V1.exe (PID: 6276)
- Launcher.exe (PID: 2384)
- sys.exe (PID: 3316)
- Windows Services.exe (PID: 2080)
- Secure System Shell.exe (PID: 2008)
- Runtime Explorer.exe (PID: 6488)
Manual execution by a user
- 4Shared Cracker V1.exe (PID: 6276)
- notepad.exe (PID: 2400)
Process checks computer location settings
- 4Shared Cracker V1.exe (PID: 6276)
- Launcher.exe (PID: 2384)
- Windows Services.exe (PID: 2080)
Checks supported languages
- Launcher.exe (PID: 2384)
- 4Shared Cracker V1.exe (PID: 6276)
- Windows Services.exe (PID: 2080)
- Secure System Shell.exe (PID: 2008)
- Runtime Explorer.exe (PID: 6488)
- sys.exe (PID: 3316)
Reads the machine GUID from the registry
- Launcher.exe (PID: 2384)
- 4Shared Cracker V1.exe (PID: 6276)
- Windows Services.exe (PID: 2080)
- sys.exe (PID: 3316)
- Secure System Shell.exe (PID: 2008)
Creates files or folders in the user directory
- Launcher.exe (PID: 2384)
Reads Environment values
- Runtime Explorer.exe (PID: 6488)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6464)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6464)
Create files in a temporary directory
- Runtime Explorer.exe (PID: 6488)
Reads security settings of Internet Explorer
- notepad.exe (PID: 2400)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
147
Monitored processes
13
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1448 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1840 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2008 | "C:\Windows\IMF\Secure System Shell.exe" | C:\Windows\IMF\Secure System Shell.exe | — | Windows Services.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Secure System Shell Version: 1.0.0.0 Modules
| |||||||||||||||
| 2080 | "C:\Windows\IMF\Windows Services.exe" {Arguments If Needed} | C:\Windows\IMF\Windows Services.exe | — | Launcher.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Windows Services Version: 1.0.0.0 Modules
| |||||||||||||||
| 2384 | "C:\Users\admin\Desktop\4Shared Cracker V1\dll Library\Launcher.exe" | C:\Users\admin\Desktop\4Shared Cracker V1\dll Library\Launcher.exe | 4Shared Cracker V1.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Launcher Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2400 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\4Shared Cracker V1\Results\hits.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3316 | "C:\Users\admin\Desktop\4Shared Cracker V1\dll Library\sys.exe" | C:\Users\admin\Desktop\4Shared Cracker V1\dll Library\sys.exe | 4Shared Cracker V1.exe | ||||||||||||
User: admin Company: Crackingsat.Com Integrity Level: HIGH Description: Rapidbaz Cracker Version: 1.0.0.0 Modules
| |||||||||||||||
| 6276 | "C:\Users\admin\Desktop\4Shared Cracker V1\4Shared Cracker V1.exe" | C:\Users\admin\Desktop\4Shared Cracker V1\4Shared Cracker V1.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Launcher Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6464 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" add-mppreference -exclusionpath C:\Windows\IMF\ | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | Launcher.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6488 | "C:\Windows\IMF\Runtime Explorer.exe" | C:\Windows\IMF\Runtime Explorer.exe | Windows Services.exe | ||||||||||||
User: admin Company: Microsoft Windows Integrity Level: HIGH Version: 1.00 Modules
| |||||||||||||||
Total events
19 127
Read events
19 085
Write events
42
Delete events
0
Modification events
| (PID) Process: | (7052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (7052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (7052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (7052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\4Shared Cracker V1.rar | |||
| (PID) Process: | (7052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
| (PID) Process: | (6276) 4Shared Cracker V1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
16
Suspicious files
5
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7052 | WinRAR.exe | C:\Users\admin\Desktop\4Shared Cracker V1\dll Library\Launcher.exe | executable | |
MD5:C6D4C881112022EB30725978ECD7C6EC | SHA256:0D87B9B141A592711C52E7409EC64DE3AB296CDDC890BE761D9AF57CEA381B32 | |||
| 7052 | WinRAR.exe | C:\Users\admin\Desktop\4Shared Cracker V1\dll Library\Ionic.Zip.dll | executable | |
MD5:F6933BF7CEE0FD6C80CDF207FF15A523 | SHA256:17BB0C9BE45289A2BE56A5F5A68EC9891D7792B886E0054BC86D57FE84D01C89 | |||
| 7052 | WinRAR.exe | C:\Users\admin\Desktop\4Shared Cracker V1\dll Library\LICENCE.dat | compressed | |
MD5:34FF2DE3F9F106D74DC756CB7537FB00 | SHA256:A03D79C6FCE912E65B1353C03335E845A2504A21500964C1E44BE512AE203747 | |||
| 7052 | WinRAR.exe | C:\Users\admin\Desktop\4Shared Cracker V1\dll Library\sys.exe | executable | |
MD5:A8FEE8F535C073BEC67A9E240E0EFEF7 | SHA256:583112111EC2038D31BD2FC1A6A1F2B77E9CA0306FBF957FFFCFE491E082FB90 | |||
| 7052 | WinRAR.exe | C:\Users\admin\Desktop\4Shared Cracker V1\dll Library\Scan Results.txt | text | |
MD5:F2F4FE7326B9272C91D7AC29A845DBE4 | SHA256:FAFF4A8624535628227C46CA32CD29B2DFBD5614767A794FAB0682DCEA63BE0E | |||
| 7052 | WinRAR.exe | C:\Users\admin\Desktop\4Shared Cracker V1\MetroFramework.Fonts.dll | executable | |
MD5:65EF4B23060128743CEF937A43B82AA3 | SHA256:C843869AACA5135C2D47296985F35C71CA8AF4431288D04D481C4E46CC93EE26 | |||
| 7052 | WinRAR.exe | C:\Users\admin\Desktop\4Shared Cracker V1\MetroFramework.dll | executable | |
MD5:34EA7F7D66563F724318E322FF08F4DB | SHA256:C2C12D31B4844E29DE31594FC9632A372A553631DE0A0A04C8AF91668E37CF49 | |||
| 7052 | WinRAR.exe | C:\Users\admin\Desktop\4Shared Cracker V1\4Shared Cracker V1.exe | executable | |
MD5:E5022266E5CBA902AC2A37DB2A65594B | SHA256:B9299D69379432C2586159B021AE7A93C62C194C01A9A6ADA7BB24D6E5FB4257 | |||
| 7052 | WinRAR.exe | C:\Users\admin\Desktop\4Shared Cracker V1\dll Library\MetroFramework.Design.dll | executable | |
MD5:AB4C3529694FC8D2427434825F71B2B8 | SHA256:0A4A96082E25767E4697033649B16C76A652E120757A2CECAB8092AD0D716B65 | |||
| 7052 | WinRAR.exe | C:\Users\admin\Desktop\4Shared Cracker V1\MetroFramework.Design.dll | executable | |
MD5:AB4C3529694FC8D2427434825F71B2B8 | SHA256:0A4A96082E25767E4697033649B16C76A652E120757A2CECAB8092AD0D716B65 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
47
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5244 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2036 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5244 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
608 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6208 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
608 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2036 | svchost.exe | 20.190.160.20:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2036 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
r.bing.com |
| whitelisted |