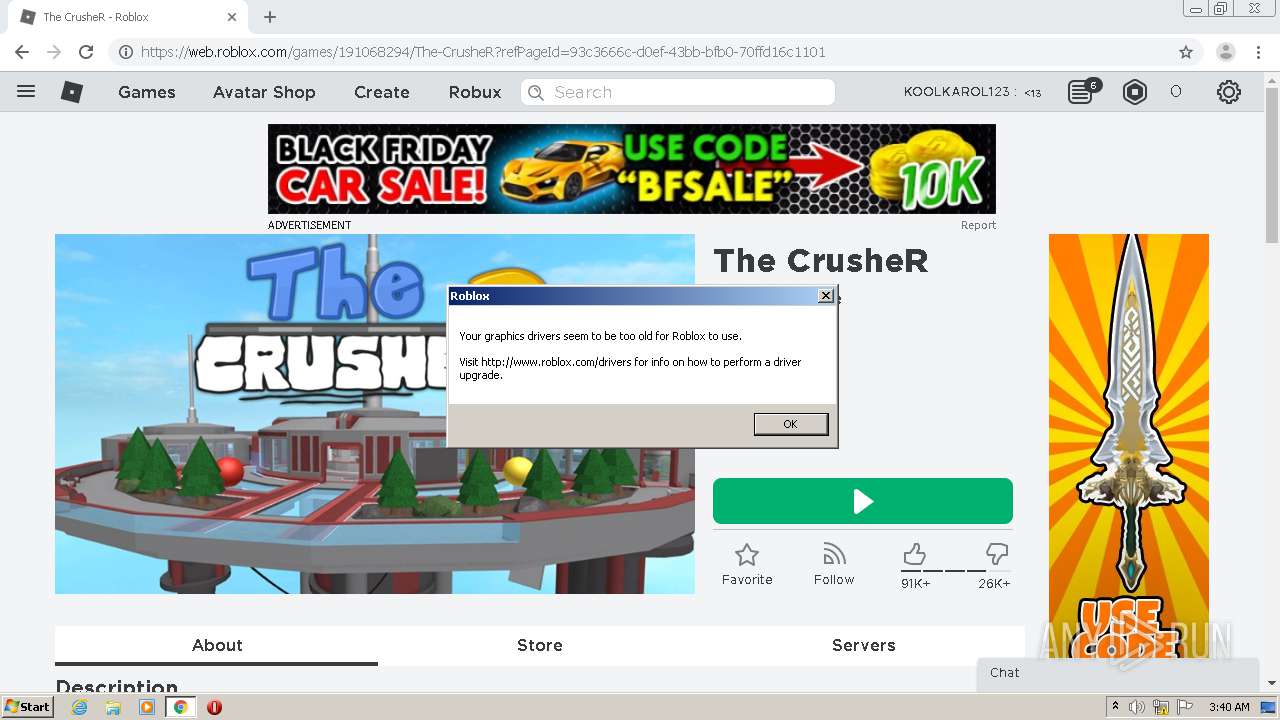
| URL: | https://roblox.com |
| Full analysis: | https://app.any.run/tasks/092d0a99-7b16-4a22-bef9-4c9661c71123 |
| Verdict: | Malicious activity |
| Analysis date: | November 27, 2020, 03:36:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 08E27DB1AA954218EB073F909A254176 |
| SHA1: | 63148FCC23D2BB81557231F73966597B0C88A903 |
| SHA256: | 9893BB1989578C47B64069B5B472BAF1DF1CC03EF2C0D557CDA2919E6D6D32A6 |
| SSDEEP: | 3:N8e0ZIn:2P2n |
MALICIOUS
Application was dropped or rewritten from another process
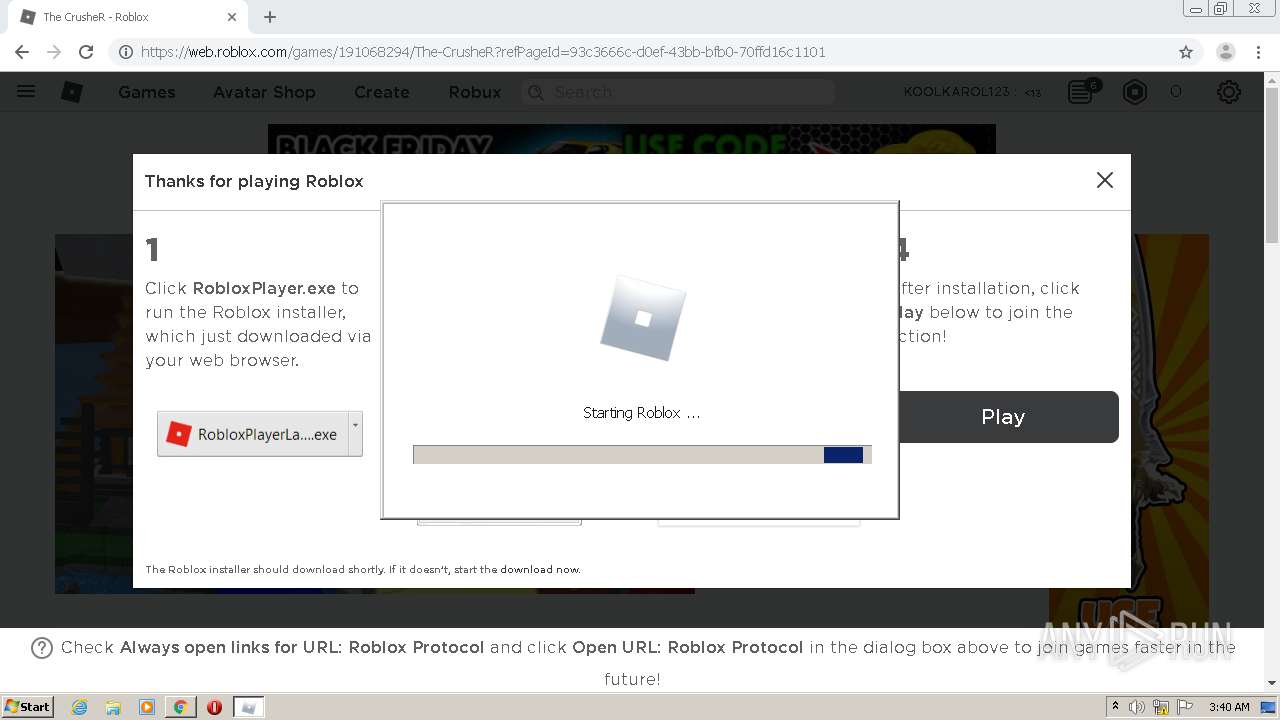
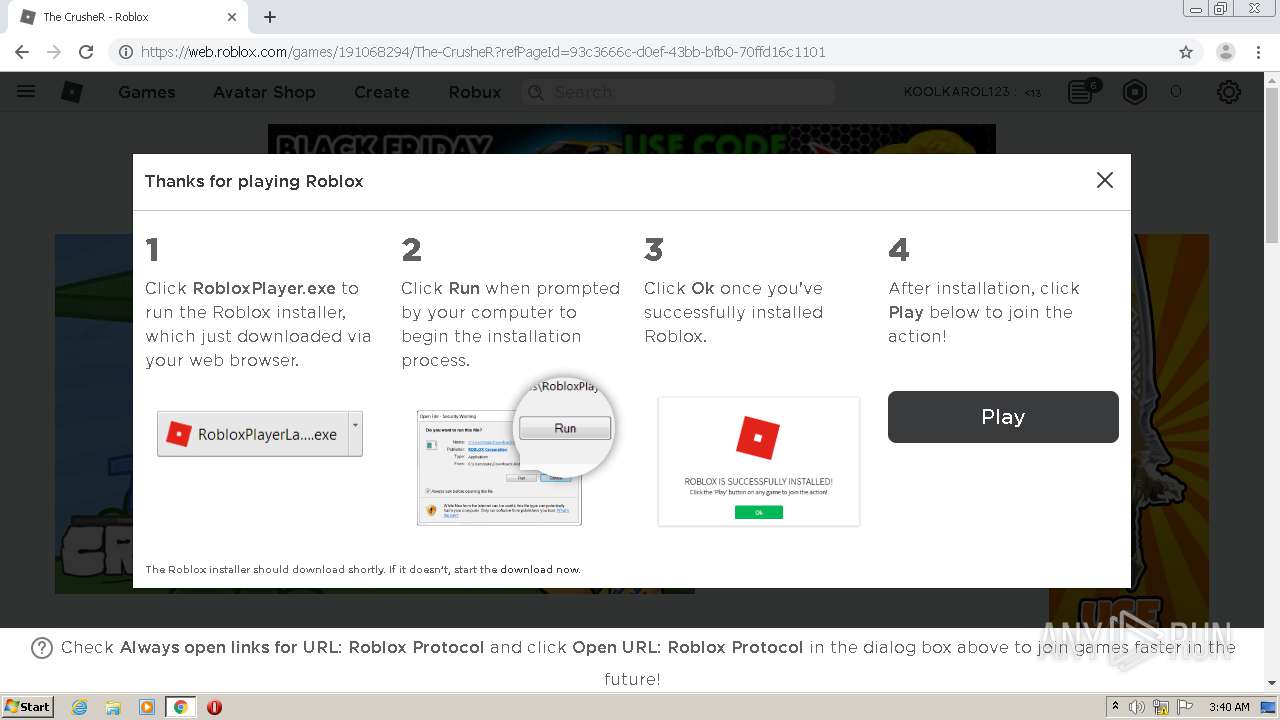
- RobloxPlayerLauncher.exe (PID: 3680)
- RobloxPlayerLauncher.exe (PID: 3232)
- RobloxPlayerLauncher.exe (PID: 2832)
- RobloxPlayerLauncher.exe (PID: 1920)
SUSPICIOUS
Executable content was dropped or overwritten
- chrome.exe (PID: 2204)
- RobloxPlayerLauncher.exe (PID: 3680)
Drops a file with a compile date too recent
- chrome.exe (PID: 2204)
- RobloxPlayerLauncher.exe (PID: 3680)
Application launched itself
- RobloxPlayerLauncher.exe (PID: 3680)
- RobloxPlayerLauncher.exe (PID: 1920)
Drops a file that was compiled in debug mode
- chrome.exe (PID: 2204)
- RobloxPlayerLauncher.exe (PID: 3680)
Creates files in the user directory
- RobloxPlayerLauncher.exe (PID: 3680)
Creates a software uninstall entry
- RobloxPlayerLauncher.exe (PID: 3680)
Modifies the open verb of a shell class
- RobloxPlayerLauncher.exe (PID: 3680)
Changes IE settings (feature browser emulation)
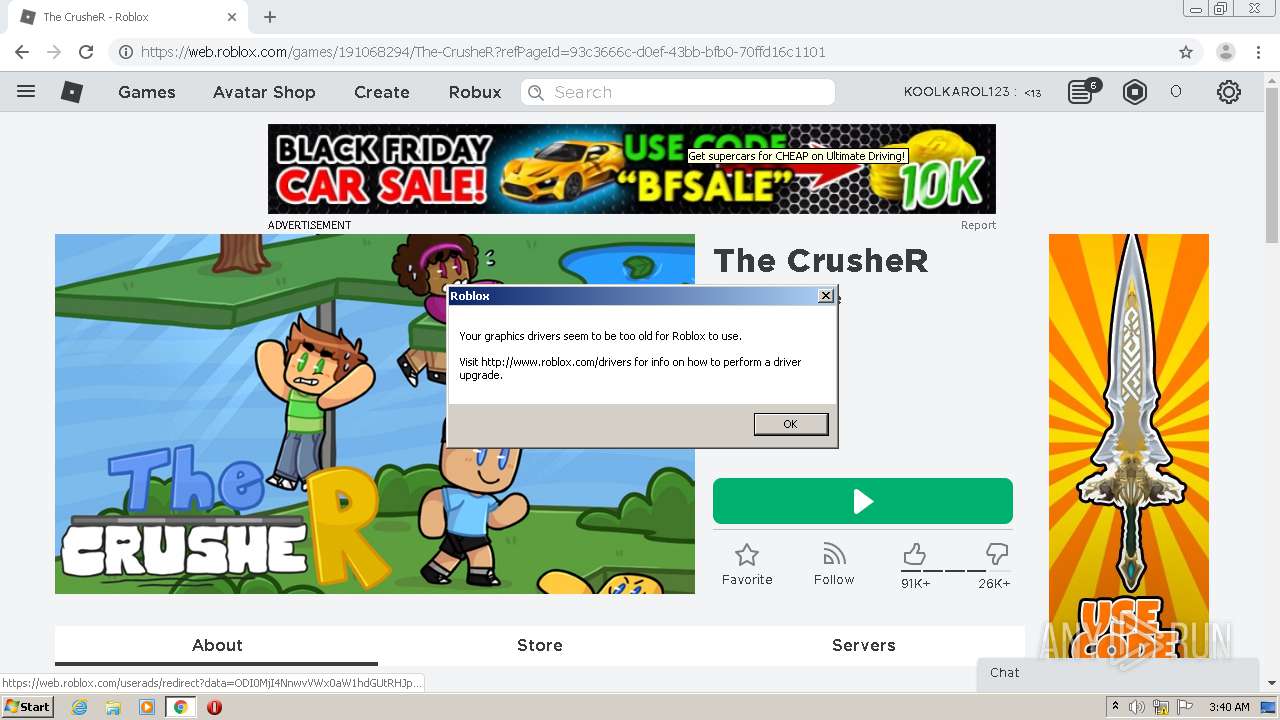
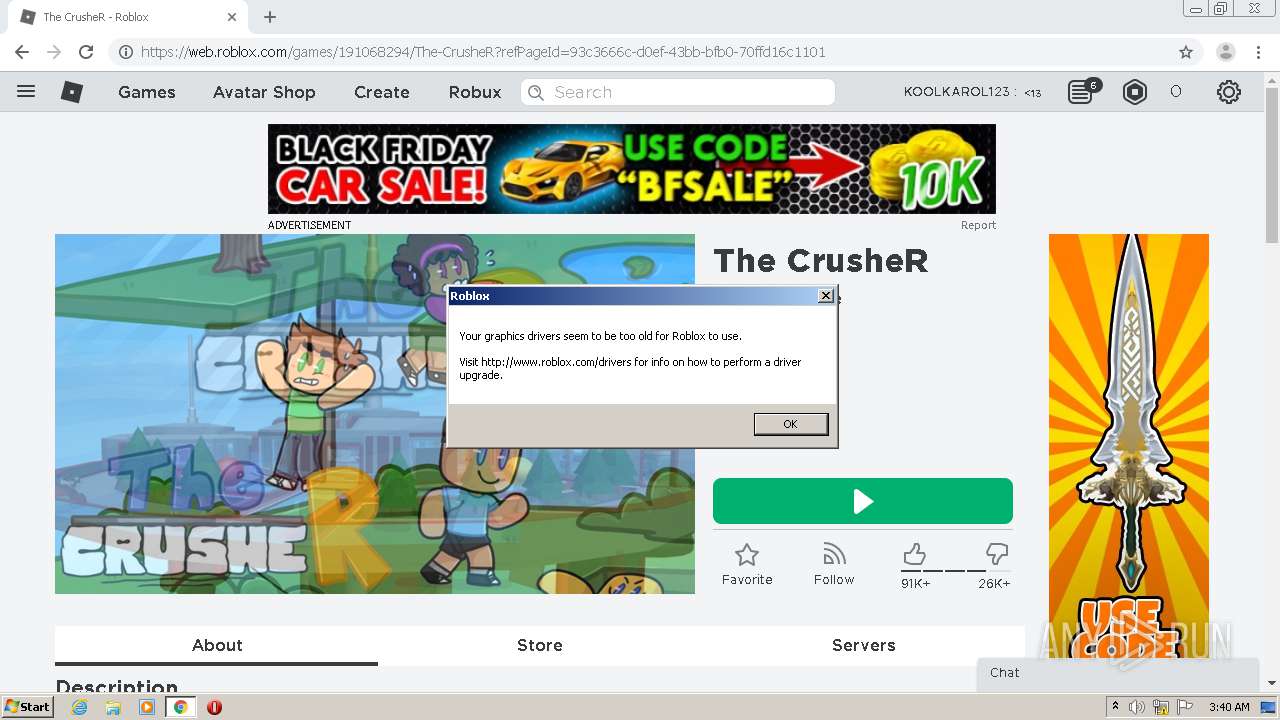
- RobloxPlayerBeta.exe (PID: 3236)
Executed as Windows Service
- vds.exe (PID: 2576)
Executed via COM
- vdsldr.exe (PID: 2288)
Low-level read access rights to disk partition
- vds.exe (PID: 2576)
INFO
Application launched itself
- chrome.exe (PID: 2204)
Reads the hosts file
- chrome.exe (PID: 2204)
- chrome.exe (PID: 4080)
Reads settings of System Certificates
- chrome.exe (PID: 4080)
- chrome.exe (PID: 2204)
- RobloxPlayerBeta.exe (PID: 3236)
Manual execution by user
- cmd.exe (PID: 2708)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
68
Monitored processes
23
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 560 | "C:\Windows\system32\diskpart.exe" | C:\Windows\system32\diskpart.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: DiskPart Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 916 | "C:\Windows\system32\diskpart.exe" | C:\Windows\system32\diskpart.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DiskPart Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1540 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1020,1415009950199311578,6952705216518216422,131072 --enable-features=PasswordImport --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=4889797458543857994 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2348 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1776 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1020,1415009950199311578,6952705216518216422,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=16131763561351366784 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2176 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1840 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=2208 --on-initialized-event-handle=316 --parent-handle=320 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1920 | "C:\Users\admin\AppData\Local\Roblox\Versions\version-5a2a97e1d9794df1\RobloxPlayerLauncher.exe" roblox-player:1+launchmode:play+gameinfo:7264BD3A059013930CB69D07330D9F9A63B7E114A6EDBC63D5C0135B7DD35192B7B5A053E25D8760298A3332B309FFCE6233F7714C3BF70CBF4EB39312934D2946E9089E4B2DB555CA9095FE3143C6CD1BE05A7BB36CE1DD0BEB01B23C4E08943A873DB7507FB66CC942A8B889121AB453928FE68CCA5EFEA9E35CEA07978EE72B262BE3CB40908A5EB23E5E7534187A768F70EA39752166118A6C230261C01949E5B009+launchtime:1606448312016+placelauncherurl:https%3A%2F%2Fassetgame.roblox.com%2Fgame%2FPlaceLauncher.ashx%3Frequest%3DRequestGame%26browserTrackerId%3D68538118189%26placeId%3D191068294%26isPlayTogetherGame%3Dfalse+browsertrackerid:68538118189+robloxLocale:en_us+gameLocale:en_us+channel: | C:\Users\admin\AppData\Local\Roblox\Versions\version-5a2a97e1d9794df1\RobloxPlayerLauncher.exe | chrome.exe | ||||||||||||
User: admin Company: Roblox Corporation Integrity Level: MEDIUM Description: Roblox Exit code: 0 Version: 1, 6, 0, 414557 Modules
| |||||||||||||||
| 1972 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1020,1415009950199311578,6952705216518216422,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=12182276148027451933 --renderer-client-id=7 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2928 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2120 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1020,1415009950199311578,6952705216518216422,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=12993041751314764072 --renderer-client-id=9 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3196 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2204 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking "https://roblox.com" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2288 | C:\Windows\System32\vdsldr.exe -Embedding | C:\Windows\System32\vdsldr.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Virtual Disk Service Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 861
Read events
1 664
Write events
193
Delete events
4
Modification events
| (PID) Process: | (2204) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2204) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2204) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2204) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2204) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1840) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2204-13250921818392250 |
Value: 259 | |||
| (PID) Process: | (2204) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2204) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2204) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3252-13245750958665039 |
Value: 0 | |||
| (PID) Process: | (2204) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
7
Suspicious files
269
Text files
153
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2204 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-5FC0745B-89C.pma | — | |
MD5:— | SHA256:— | |||
| 2204 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\1b6189df-7088-43fc-a541-df5a41bb865f.tmp | — | |
MD5:— | SHA256:— | |||
| 2204 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000048.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2204 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2204 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old~RF14395e.TMP | text | |
MD5:— | SHA256:— | |||
| 2204 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2204 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF143910.TMP | text | |
MD5:— | SHA256:— | |||
| 2204 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF143910.TMP | text | |
MD5:— | SHA256:— | |||
| 2204 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2204 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RF143c1d.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
100
DNS requests
90
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3680 | RobloxPlayerLauncher.exe | GET | 200 | 192.124.249.23:80 | http://ocsp.godaddy.com//MEQwQjBAMD4wPDAJBgUrDgMCGgUABBTkIInKBAzXkF0Qh0pel3lfHJ9GPAQU0sSw0pHUTBFxs2HLPaH%2B3ahq1OMCAxvnFQ%3D%3D | US | der | 1.66 Kb | whitelisted |
3680 | RobloxPlayerLauncher.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
3680 | RobloxPlayerLauncher.exe | GET | 200 | 192.124.249.23:80 | http://ocsp.godaddy.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQdI2%2BOBkuXH93foRUj4a7lAr4rGwQUOpqFBxBnKLbv9r0FQW4gwZTaD94CAQc%3D | US | der | 1.69 Kb | whitelisted |
3236 | RobloxPlayerBeta.exe | POST | 200 | 173.194.200.113:80 | http://www.google-analytics.com/collect | US | image | 35 b | whitelisted |
1052 | svchost.exe | GET | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/GTSGIAG3/MEkwRzBFMEMwQTAJBgUrDgMCGgUABBT27bBjYjKBmjX2jXWgnQJKEapsrQQUd8K4UJpndnaxLcKG0IOgfqZ%2BuksCCCR1UqpKNfC0 | US | binary | 5 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4080 | chrome.exe | 172.217.18.173:443 | accounts.google.com | Google Inc. | US | whitelisted |
4080 | chrome.exe | 205.234.175.102:443 | css.rbxcdn.com | CacheNetworks, Inc. | US | suspicious |
4080 | chrome.exe | 128.116.123.3:443 | roblox.com | University Corporation for Atmospheric Research | US | suspicious |
4080 | chrome.exe | 216.58.212.138:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
4080 | chrome.exe | 128.116.112.44:443 | www.roblox.com | University Corporation for Atmospheric Research | US | malicious |
4080 | chrome.exe | 205.234.175.175:443 | static.rbxcdn.com | CacheNetworks, Inc. | US | suspicious |
4080 | chrome.exe | 104.18.25.64:443 | roblox-api.arkoselabs.com | Cloudflare Inc | US | suspicious |
4080 | chrome.exe | 172.217.16.174:443 | clients1.google.com | Google Inc. | US | whitelisted |
4080 | chrome.exe | 128.116.124.3:443 | www.roblox.com | University Corporation for Atmospheric Research | US | suspicious |
4080 | chrome.exe | 54.88.149.194:443 | gscounters.us1.gigya.com | Amazon.com, Inc. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
roblox.com |
| whitelisted |
accounts.google.com |
| shared |
www.roblox.com |
| whitelisted |
css.rbxcdn.com |
| whitelisted |
static.rbxcdn.com |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
js.rbxcdn.com |
| whitelisted |
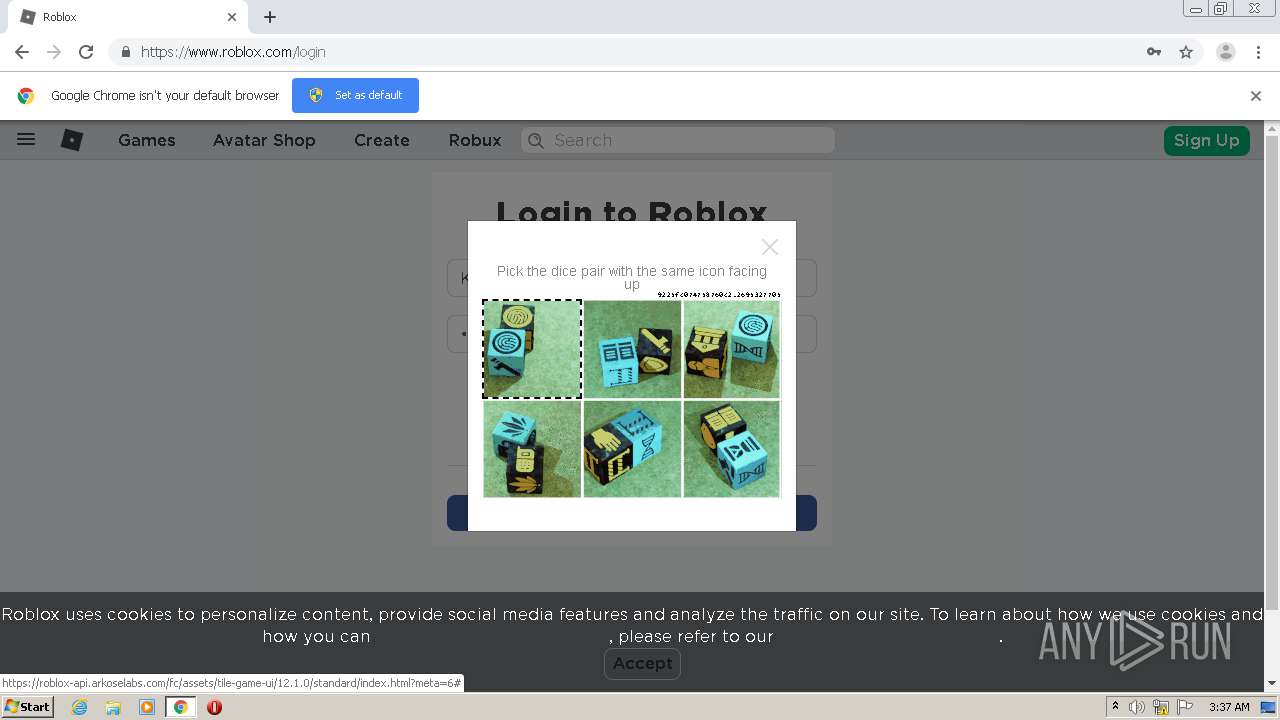
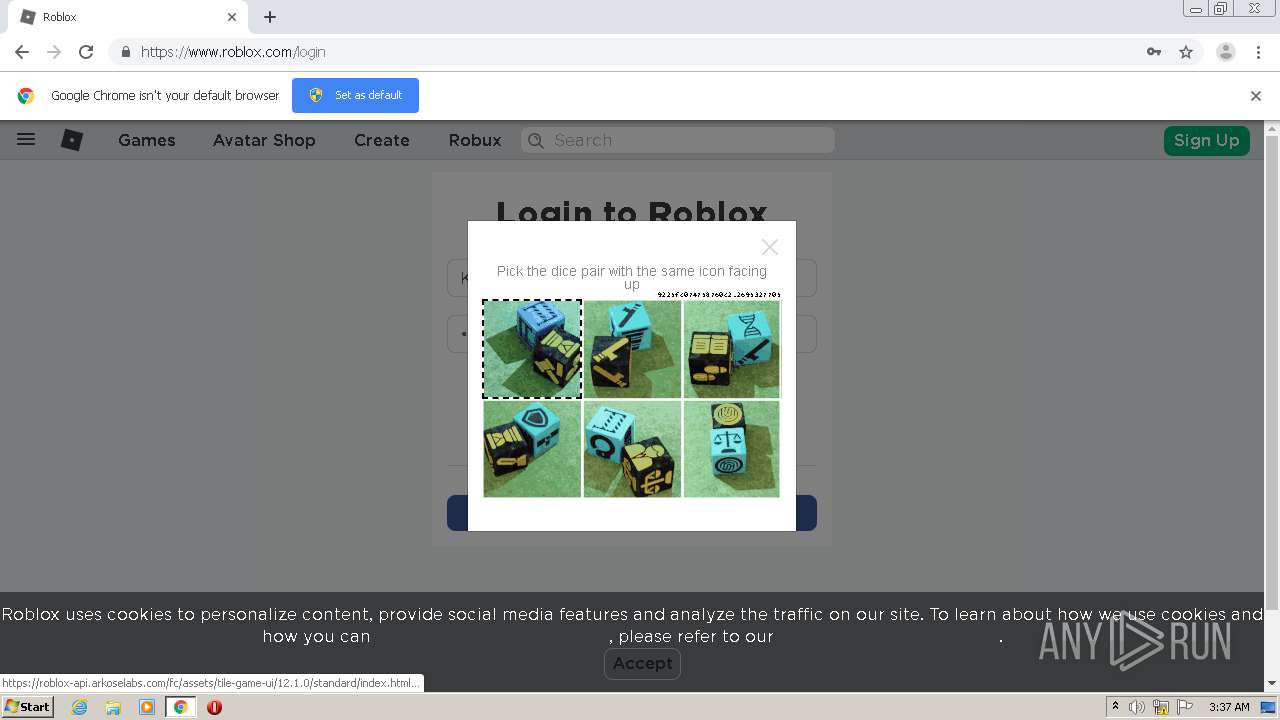
roblox-api.arkoselabs.com |
| whitelisted |
cdn.arkoselabs.com |
| shared |
metrics.roblox.com |
| whitelisted |
Threats
1 ETPRO signatures available at the full report
Process | Message |
|---|---|
RobloxPlayerBeta.exe | 1606448412.17002,0da8,6 The channel is NULL |
RobloxPlayerBeta.exe | |
RobloxPlayerBeta.exe | |
RobloxPlayerBeta.exe | |
RobloxPlayerBeta.exe | 1606448412.29438,0da8,6 TaskSchedulerMk2::applyAsyncTaskThreadCount( 3 ) <req: 3 active: 3> |
RobloxPlayerBeta.exe | |
RobloxPlayerBeta.exe | 1606448412.30515,0da8,6 Loading AppSettings.xml from C:\Users\admin\AppData\Local\Roblox\Versions\version-5a2a97e1d9794df1\AppSettings.xml |
RobloxPlayerBeta.exe | |
RobloxPlayerBeta.exe | 1606448412.30515,0da8,6 setAssetFolder content |
RobloxPlayerBeta.exe | |