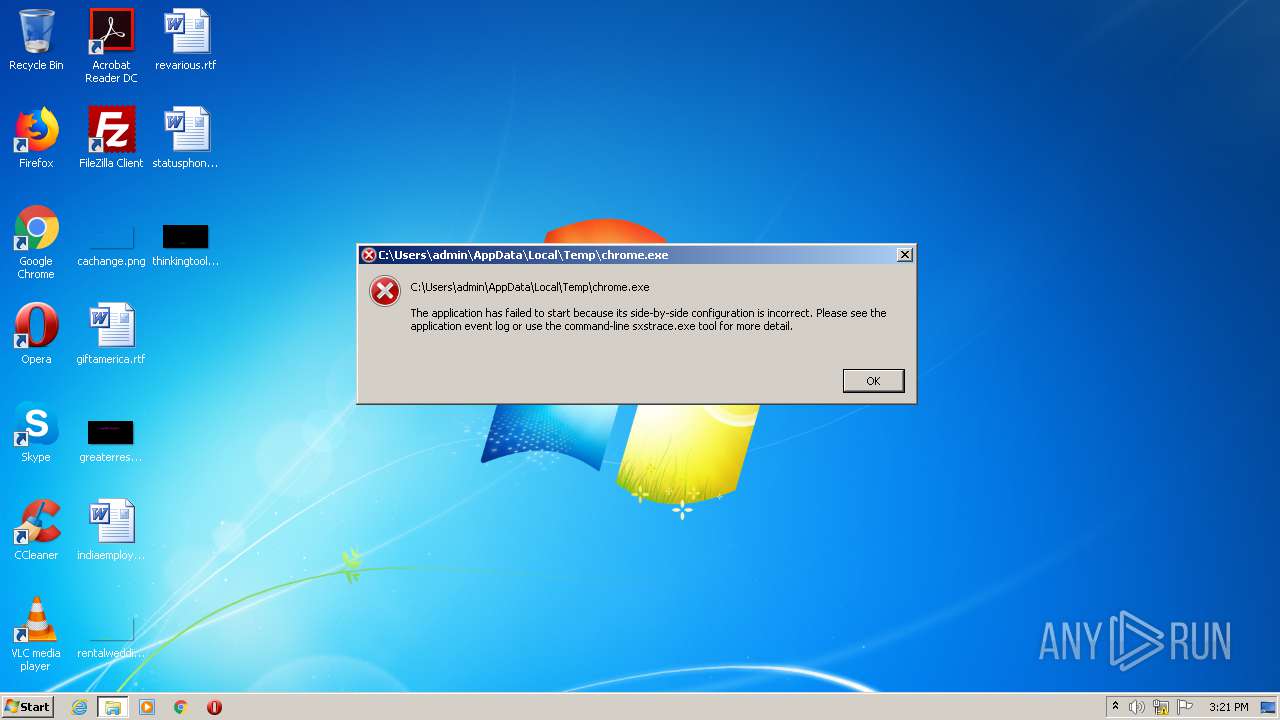
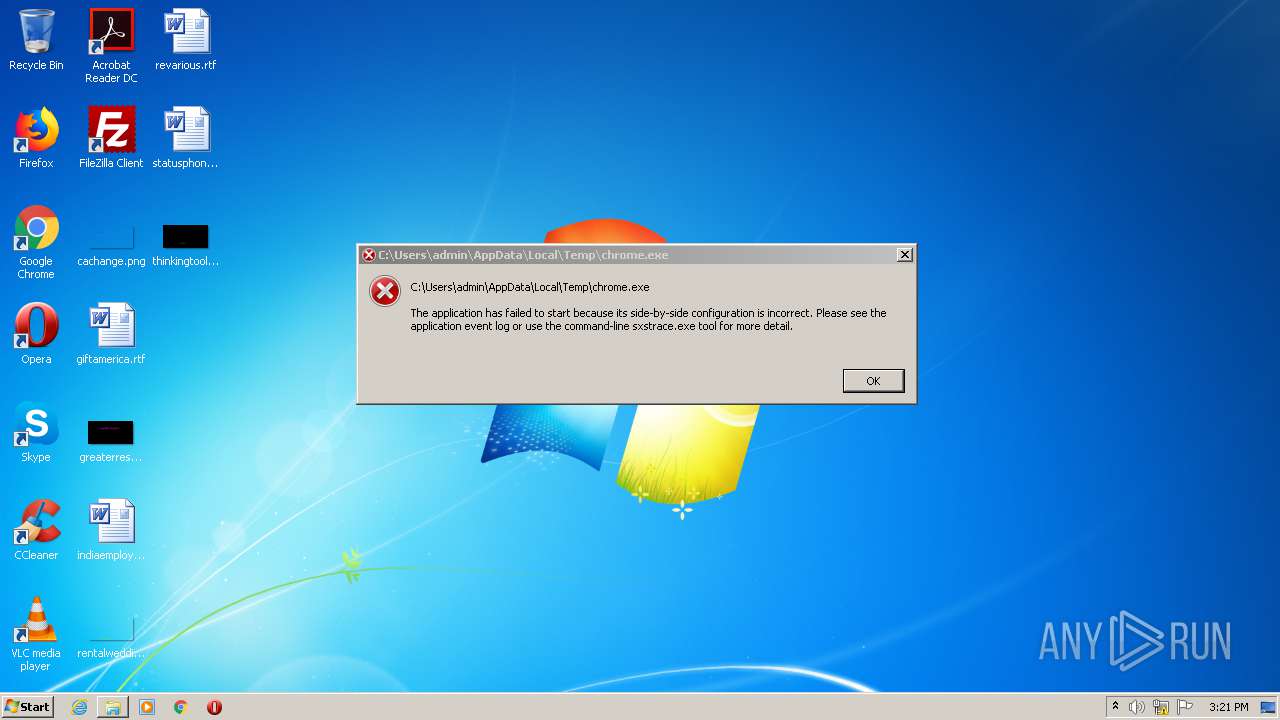
| File name: | chrome.exe |
| Full analysis: | https://app.any.run/tasks/abd2bc0d-747c-4d5e-bc50-3ff6c69187f8 |
| Verdict: | Malicious activity |
| Analysis date: | September 30, 2020, 14:20:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | F3C72A5255C78FD3134A4896AD1FC936 |
| SHA1: | 4266828B057D3DAF2B687C9F985C6946AE22C83A |
| SHA256: | 98615F765E8337555C77DB1BF920ADBBDF2313E6A190FA21C9D98F78533A5386 |
| SSDEEP: | 24576:5zjtNDRr0V/K2rApQDSx0zawm4WwsCOWgfSTuHN44TRcPFzE1:Njt/gRCWa0Lm4WFCOaTut44Ts2 |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:10:06 07:00:00+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 1117184 |
| InitializedDataSize: | 544256 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xe85f0 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 79.0.3945.0 |
| ProductVersionNumber: | 79.0.3945.0 |
| FileFlagsMask: | 0x0017 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | The Chromium Authors |
| FileDescription: | Chromium |
| FileVersion: | 79.0.3945.0 |
| InternalName: | chrome_exe |
| LegalCopyright: | Copyright 2019 The Chromium Authors. All rights reserved. |
| OriginalFileName: | chrome.exe |
| ProductName: | Chromium |
| ProductVersion: | 79.0.3945.0 |
| CompanyShortName: | The Chromium Authors |
| ProductShortName: | Chromium |
| LastChange: | 2509e355c62545bf43497c7ced5c81d01aa66606-refs/heads/master@{#707216} |
| OfficialBuild: | - |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 06-Oct-2019 05:00:00 |
| Detected languages: |
|
| TLS Callbacks: | 3 callback(s) detected. |
| Debug artifacts: |
|
| CompanyName: | The Chromium Authors |
| FileDescription: | Chromium |
| FileVersion: | 79.0.3945.0 |
| InternalName: | chrome_exe |
| LegalCopyright: | Copyright 2019 The Chromium Authors. All rights reserved. |
| OriginalFilename: | chrome.exe |
| ProductName: | Chromium |
| ProductVersion: | 79.0.3945.0 |
| CompanyShortName: | The Chromium Authors |
| ProductShortName: | Chromium |
| LastChange: | 2509e355c62545bf43497c7ced5c81d01aa66606-refs/heads/master@{#707216} |
| Official Build: | 0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0078 |
| Pages in file: | 0x0001 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0x0000 |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x0000 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000078 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 10 |
| Time date stamp: | 06-Oct-2019 05:00:00 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00110A65 | 0x00110C00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.79771 |
.rdata | 0x00112000 | 0x00051D3C | 0x00051E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.13319 |
.data | 0x00164000 | 0x00008334 | 0x00002E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.44232 |
.00cfg | 0x0016D000 | 0x00000004 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 0.0611629 |
.tls | 0x0016E000 | 0x00000019 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0.136464 |
.voltbl | 0x0016F000 | 0x000000FB | 0x00000200 | 3.73622 | |
CPADinfo( | 0x00170000 | 0x00000028 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0.122276 |
prot | 0x00171000 | 0x000000BC | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 0 |
.rsrc | 0x00172000 | 0x000251C8 | 0x00025200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.59209 |
.reloc | 0x00198000 | 0x0000A61C | 0x0000A800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.65961 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.30792 | 1236 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 5.24689 | 2216 | UNKNOWN | English - United States | RT_ICON |
3 | 5.05116 | 3752 | UNKNOWN | English - United States | RT_ICON |
4 | 4.74856 | 1128 | UNKNOWN | English - United States | RT_ICON |
5 | 4.67992 | 4264 | UNKNOWN | English - United States | RT_ICON |
6 | 4.31283 | 9640 | UNKNOWN | English - United States | RT_ICON |
7 | 7.95981 | 19717 | UNKNOWN | English - United States | RT_ICON |
8 | 4.05163 | 3752 | UNKNOWN | English - United States | RT_ICON |
9 | 4.36687 | 2216 | UNKNOWN | English - United States | RT_ICON |
10 | 4.32943 | 1384 | UNKNOWN | English - United States | RT_ICON |
Imports
KERNEL32.dll |
SHELL32.dll (delay-loaded) |
VERSION.dll |
chrome_elf.dll |
Exports
Title | Ordinal | Address |
|---|---|---|
0 | 0x00000000 | |
GetHandleVerifier | 1 | 0x00054100 |
IsSandboxedProcess | 2 | 0x000421D0 |
Total processes
0
Monitored processes
0
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
43
DNS requests
29
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 142.250.74.195:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
— | — | 172.217.22.77:443 | accounts.google.com | Google Inc. | US | whitelisted |
— | — | 216.58.207.35:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
— | — | 172.217.16.150:443 | i.ytimg.com | Google Inc. | US | suspicious |
— | — | 172.217.22.110:443 | ogs.google.com | Google Inc. | US | whitelisted |
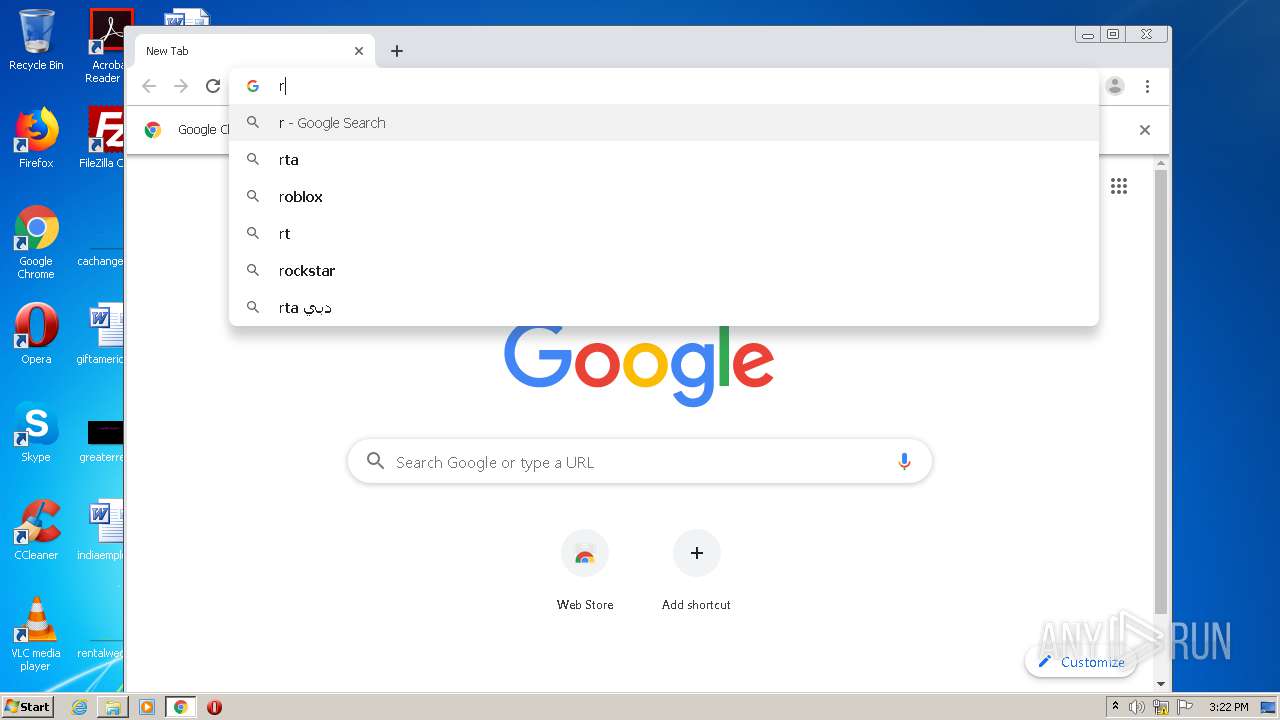
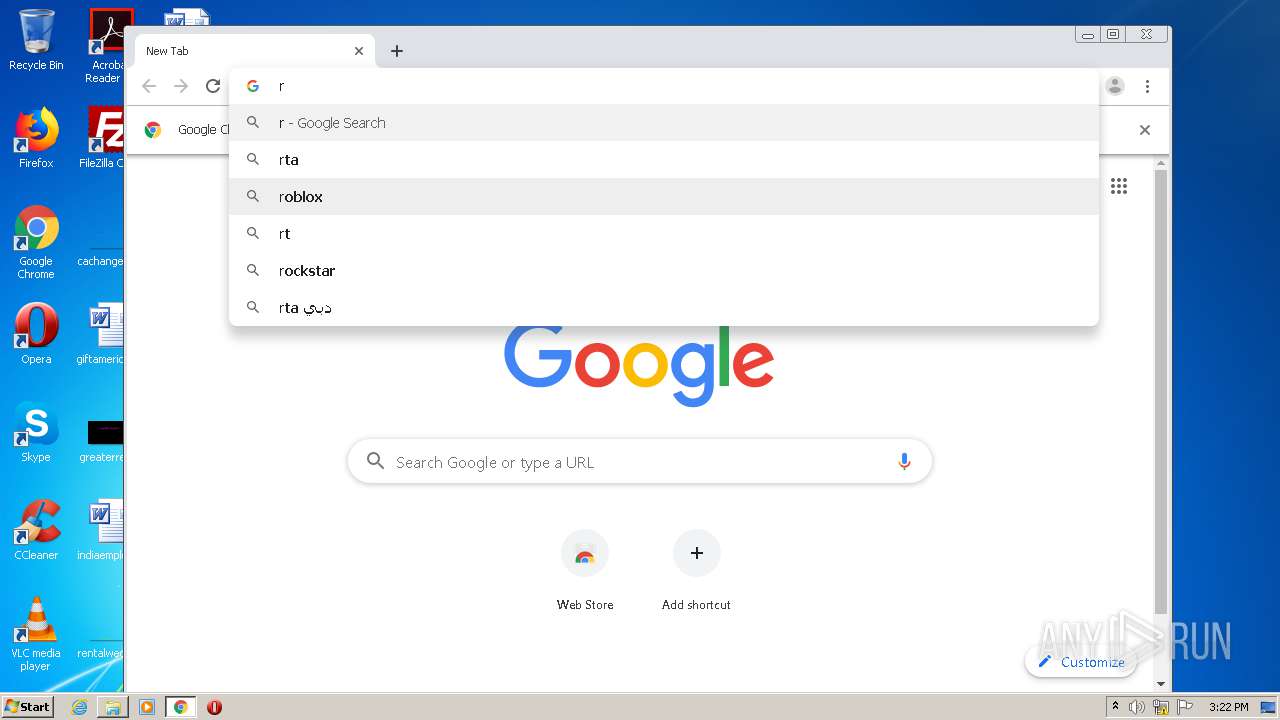
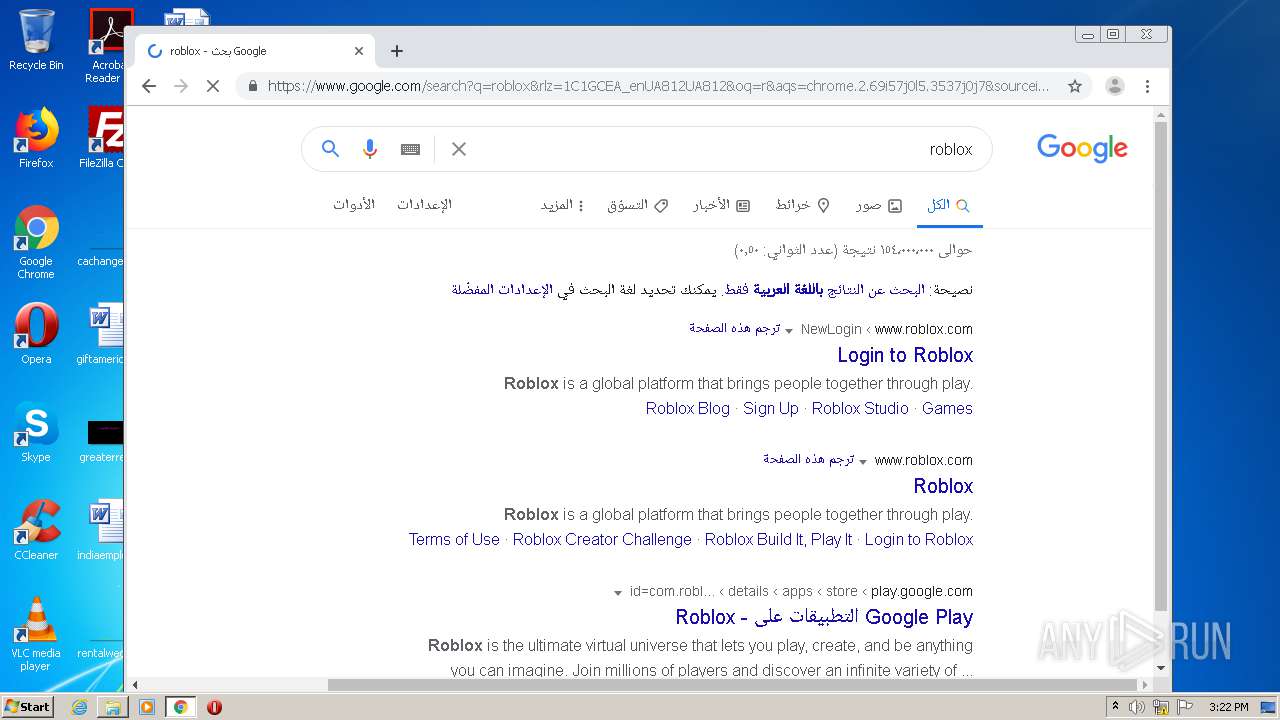
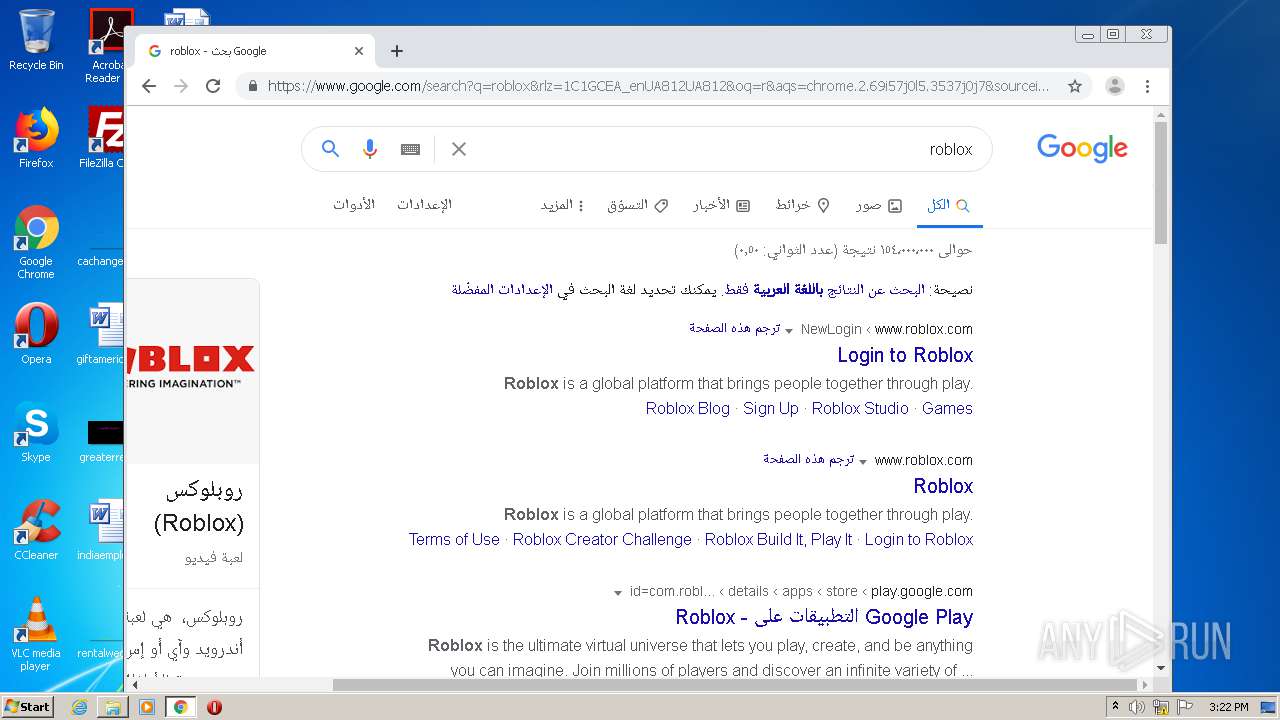
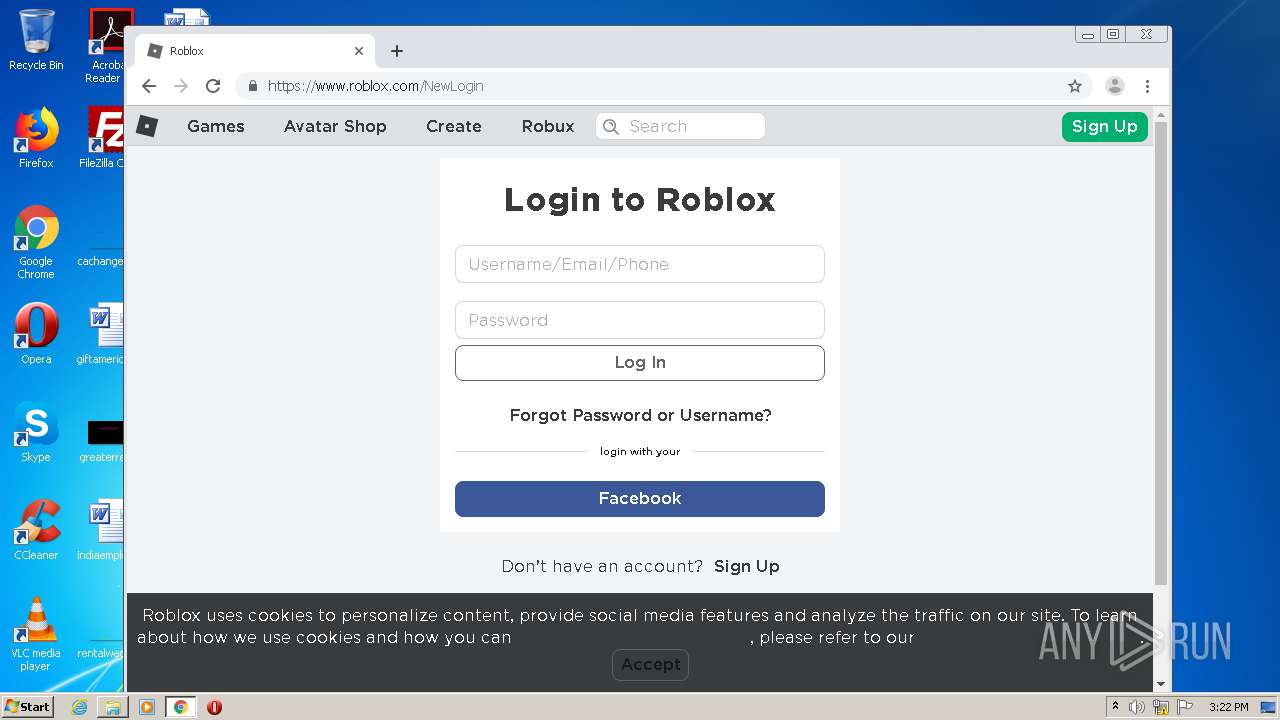
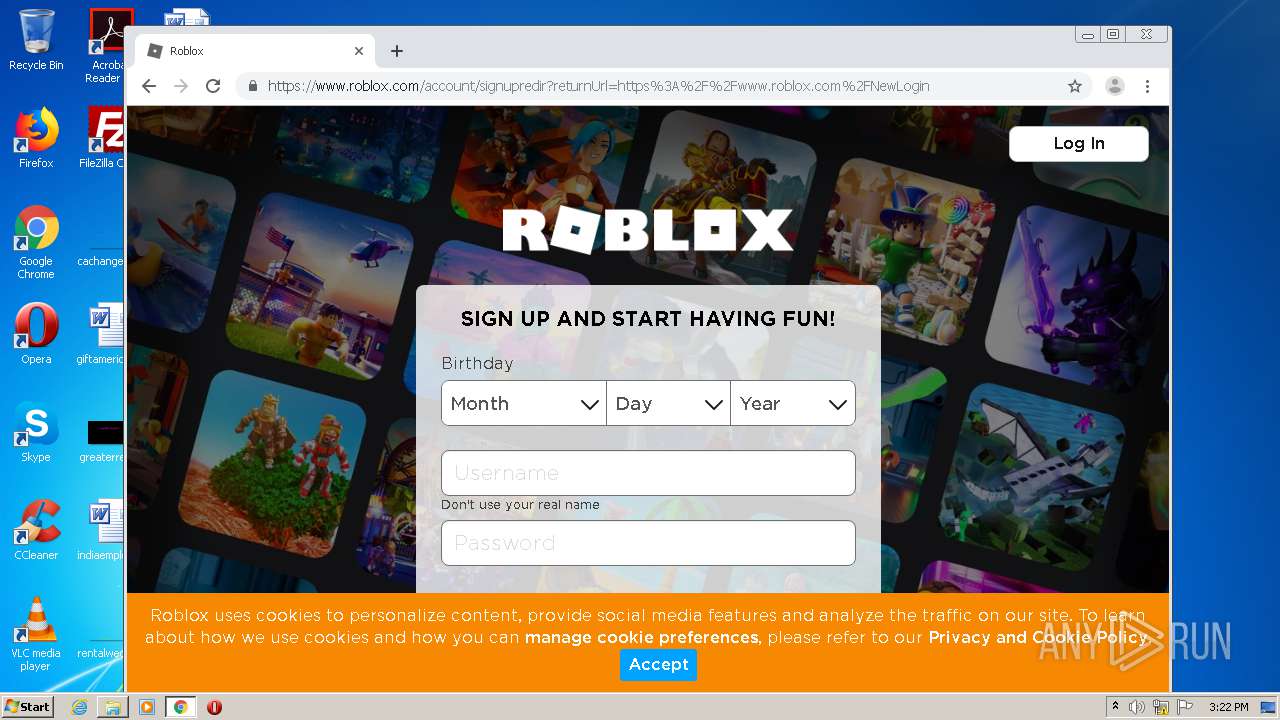
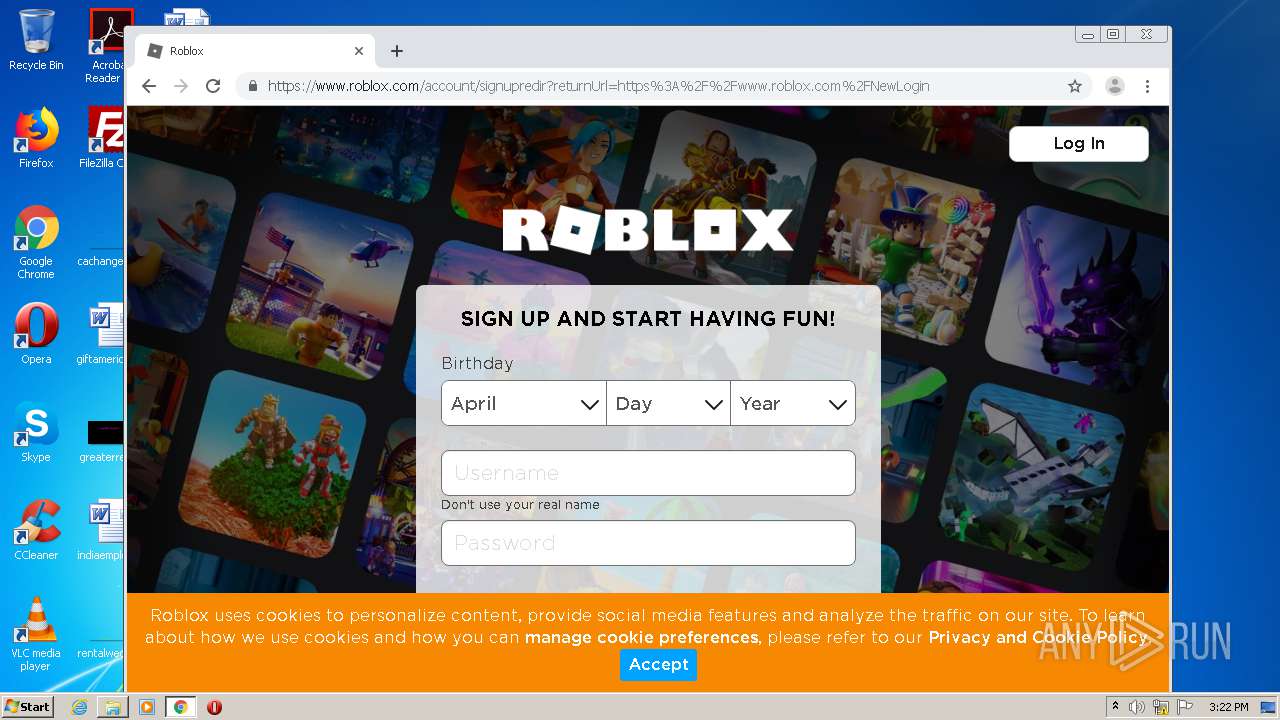
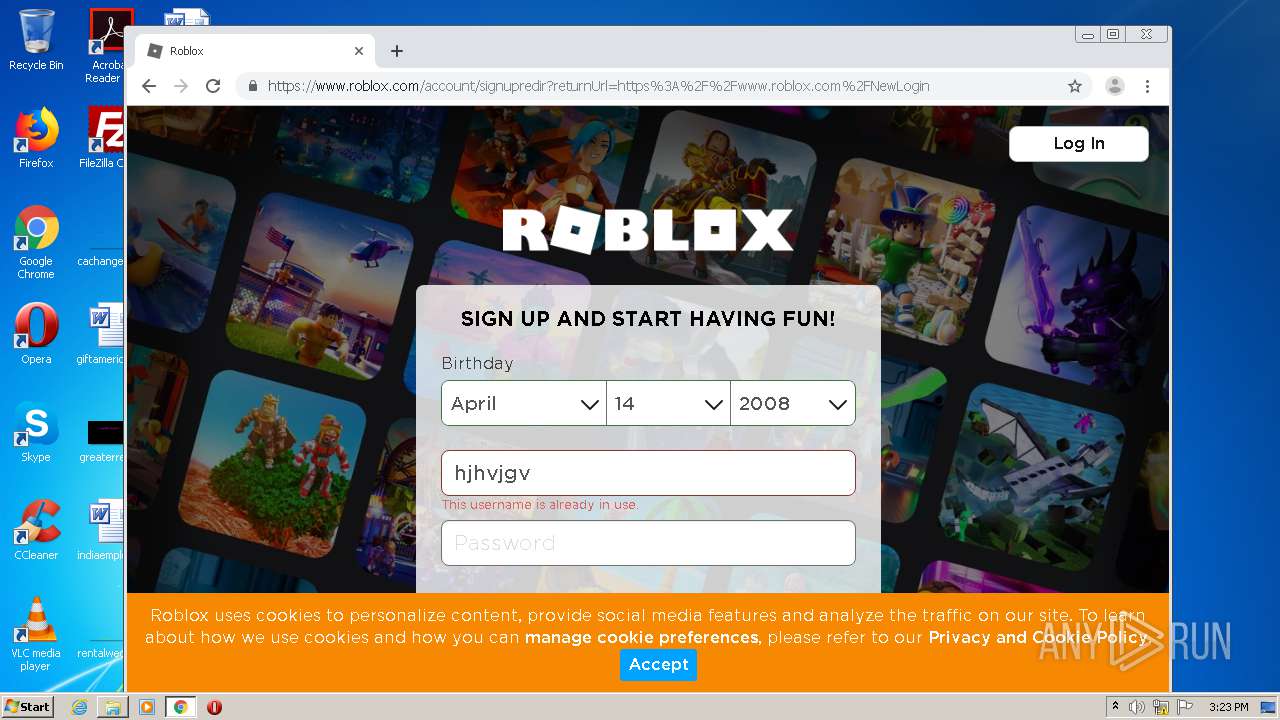
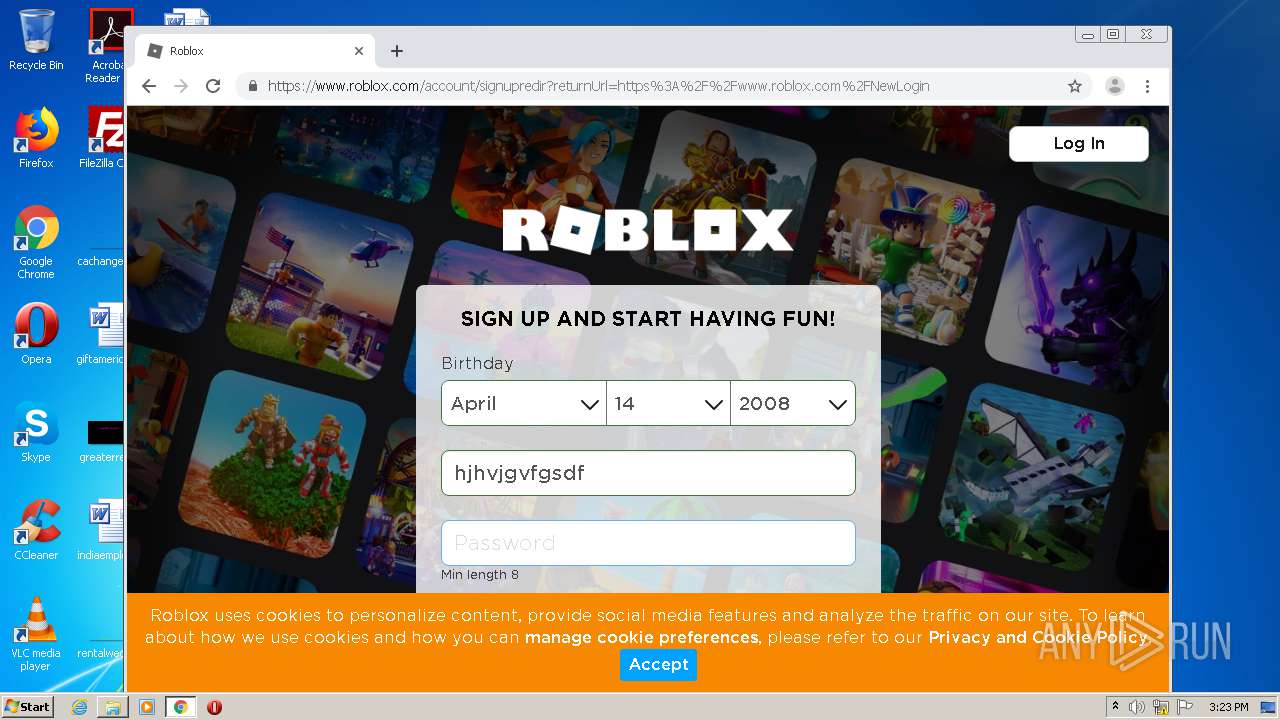
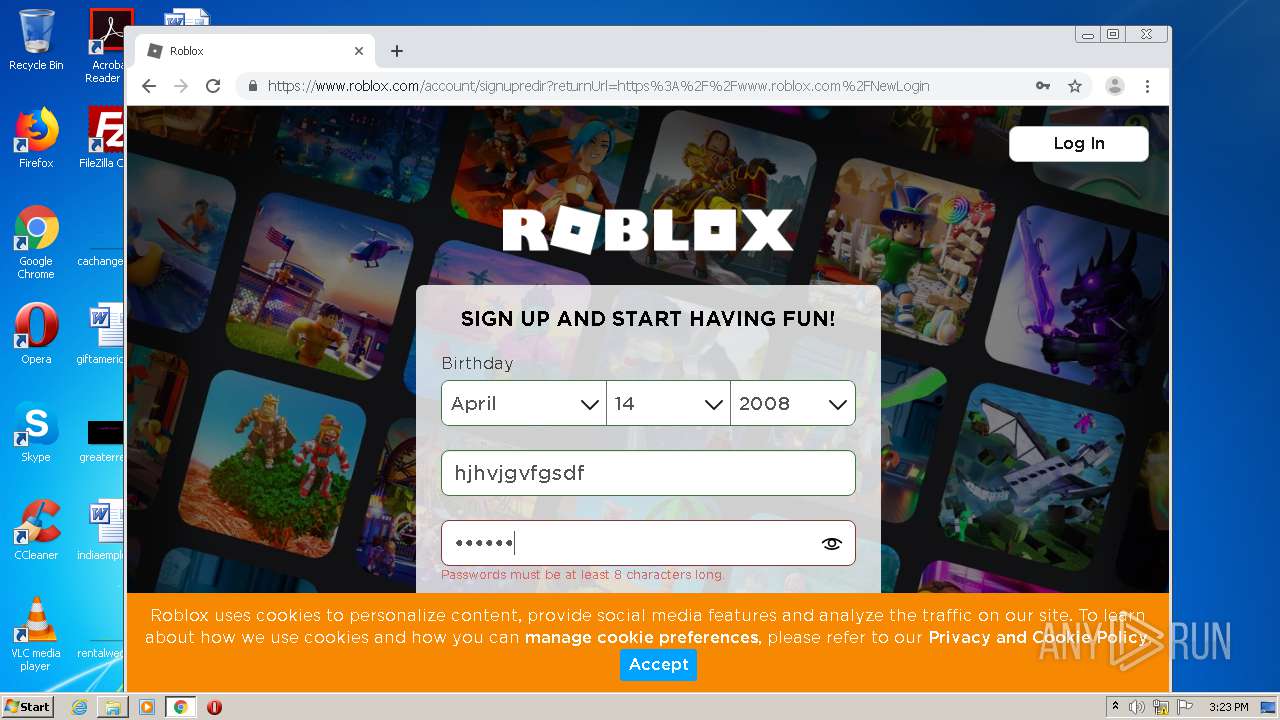
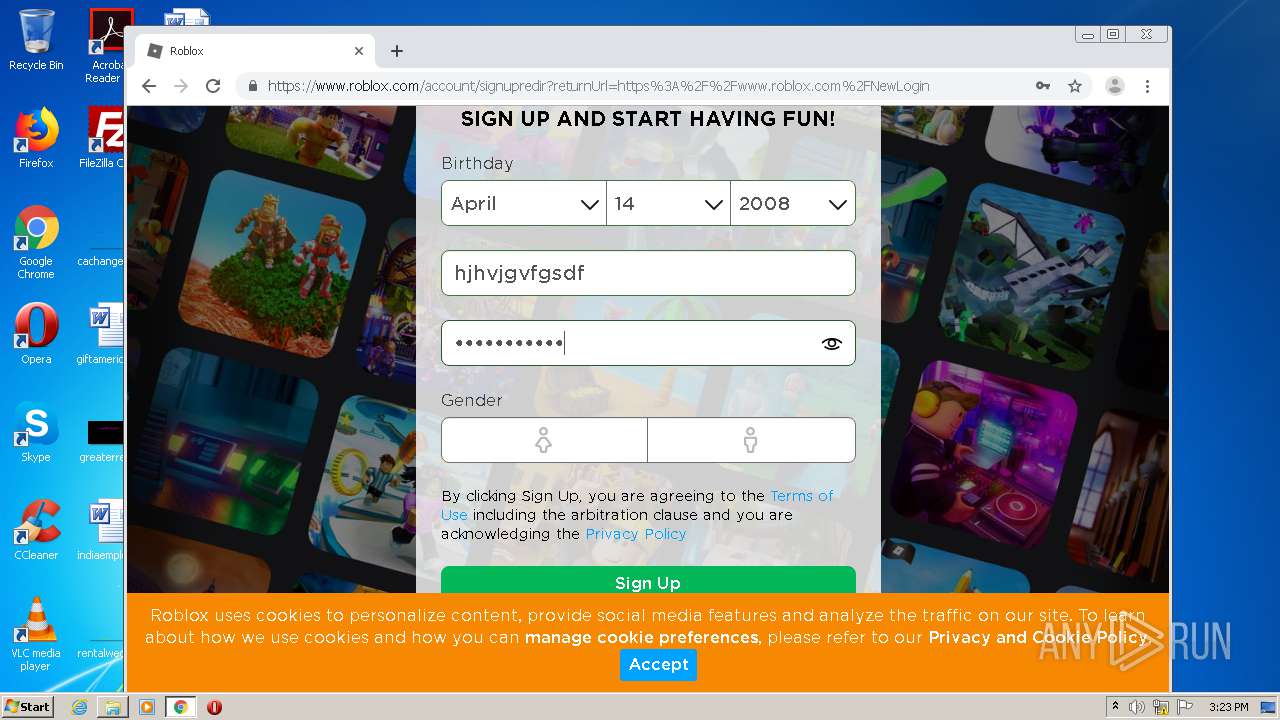
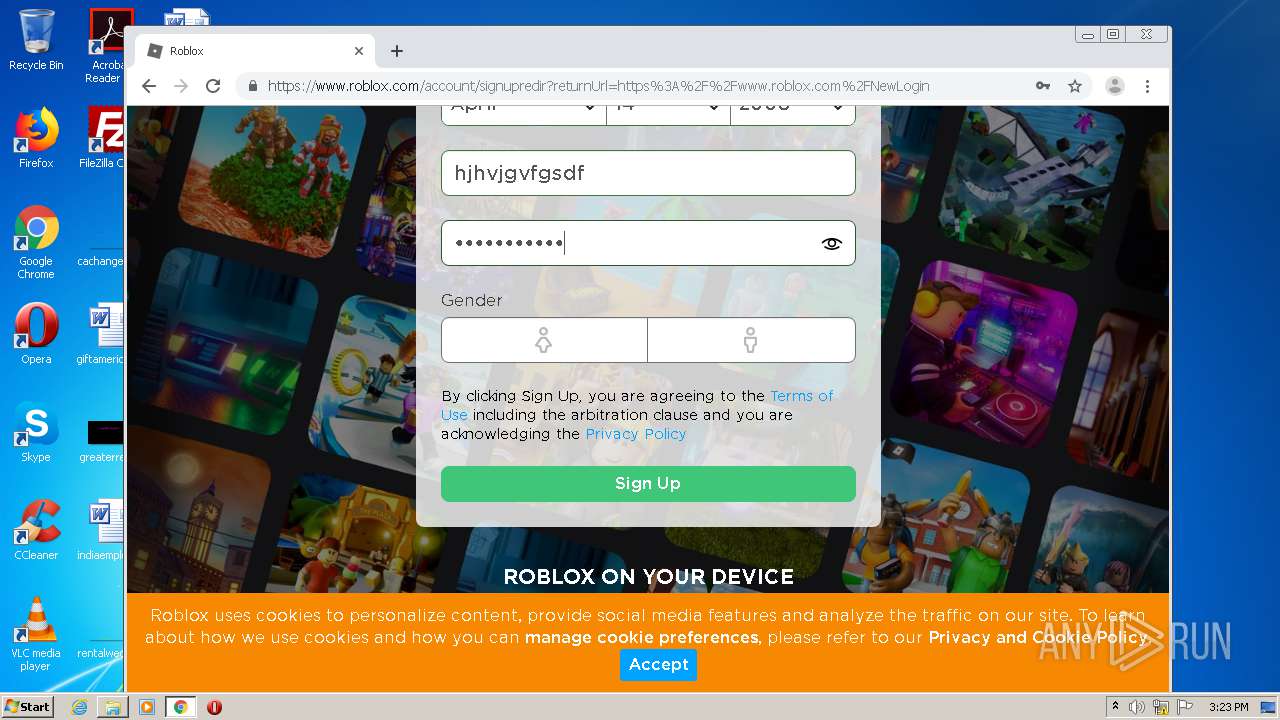
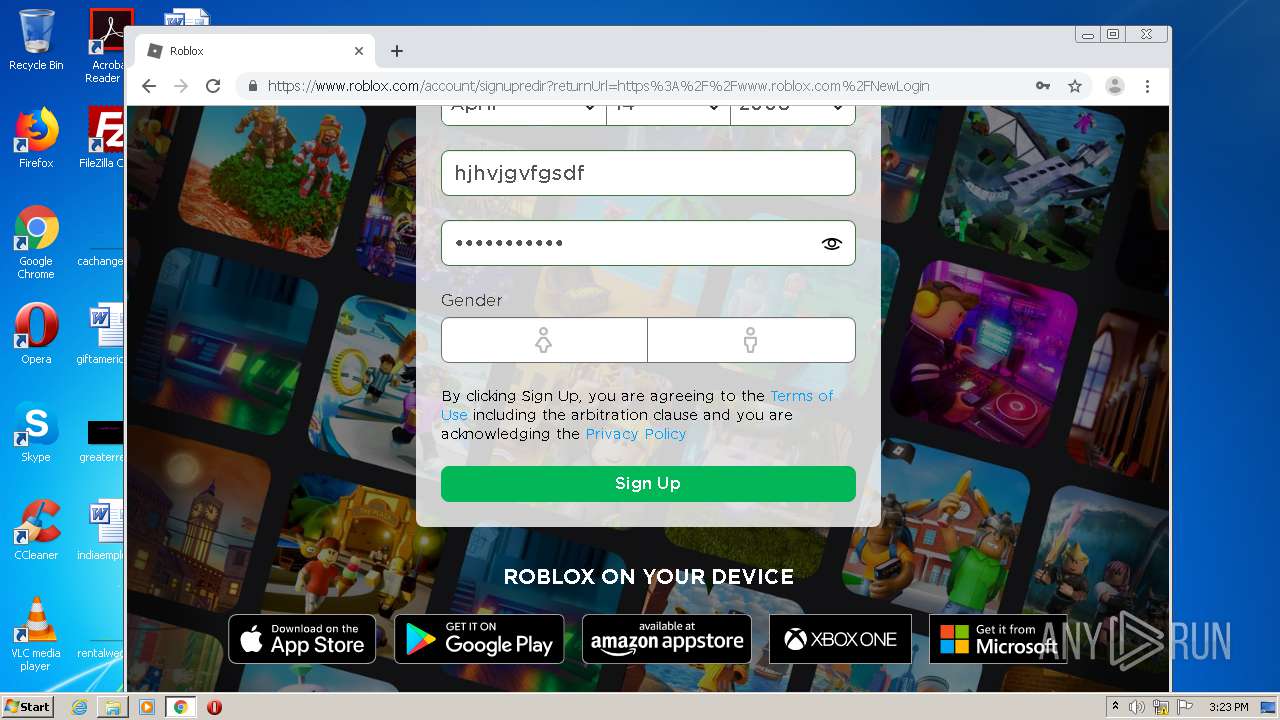
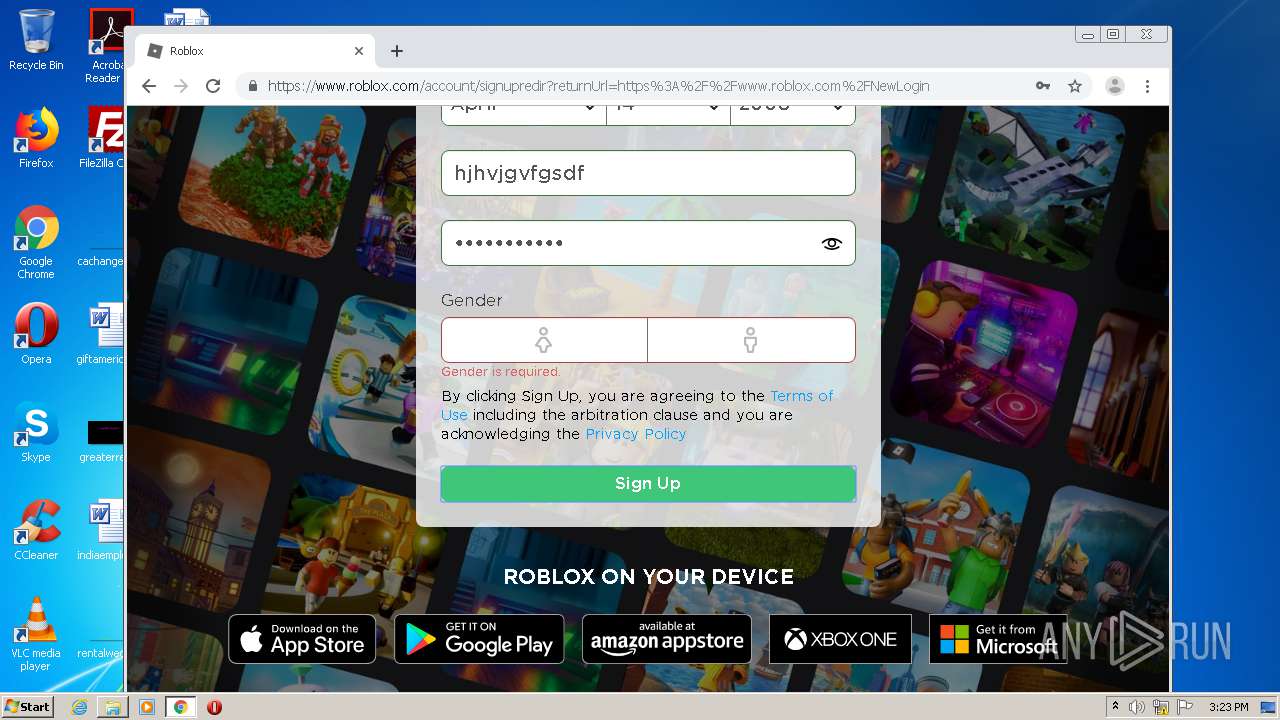
— | — | 128.116.122.3:443 | www.roblox.com | University Corporation for Atmospheric Research | US | suspicious |
— | — | 172.217.22.2:443 | adservice.google.com | Google Inc. | US | whitelisted |
— | — | 216.58.212.170:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
— | — | 54.144.200.62:443 | roblox-api.arkoselabs.com | Amazon.com, Inc. | US | unknown |
— | — | 23.210.249.177:443 | cdns.gigya.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| malicious |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
clients2.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
ogs.google.com |
| whitelisted |
i.ytimg.com |
| whitelisted |