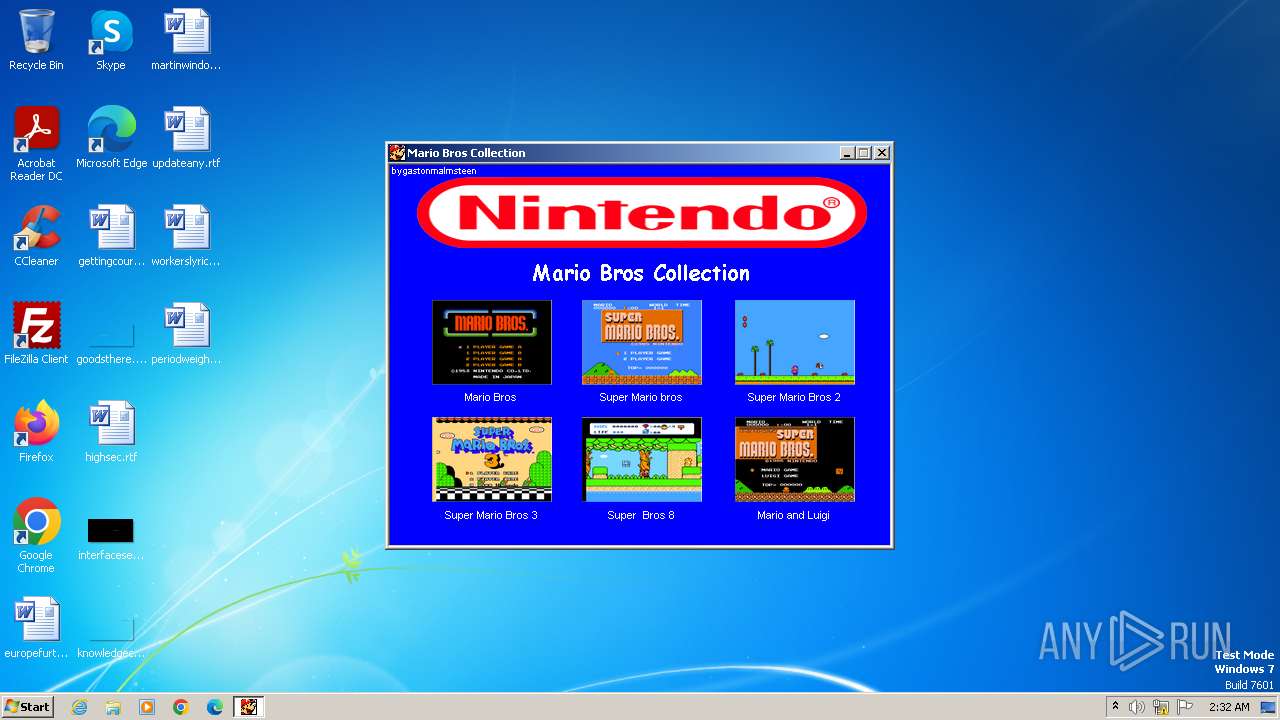
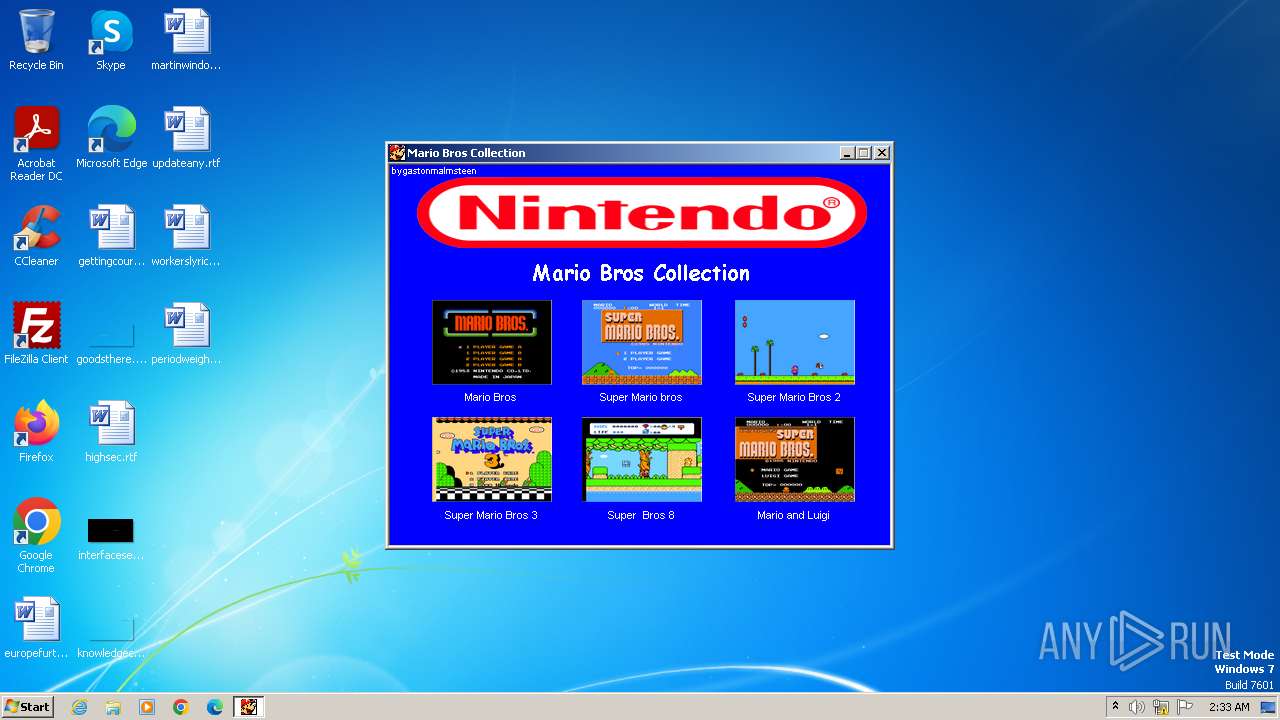
| File name: | Mario Coleccion.exe |
| Full analysis: | https://app.any.run/tasks/5933082c-1f01-44fb-9898-2c7418cba354 |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2024, 01:32:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | EE1AF0FDB25559B16295B45316762C6B |
| SHA1: | 838E282334E22CFD3C80965FB8F114A1DA03419A |
| SHA256: | 985BC1027AD2C2656EDE64CA442A4A264B7A93595BAC07015A03619B3E87D894 |
| SSDEEP: | 98304:xIZaWyCIb6BRxzKgwpPg6MUmOvAuKuz/x6+DTtnlsJJEz0W6ZsdMuDMH/MKrQ2zQ:tjBD+dRm |
MALICIOUS
Drops the executable file immediately after the start
- Mario Coleccion.exe (PID: 3976)
- Mario bros.exe (PID: 124)
- Merio and Luigi.exe (PID: 524)
SUSPICIOUS
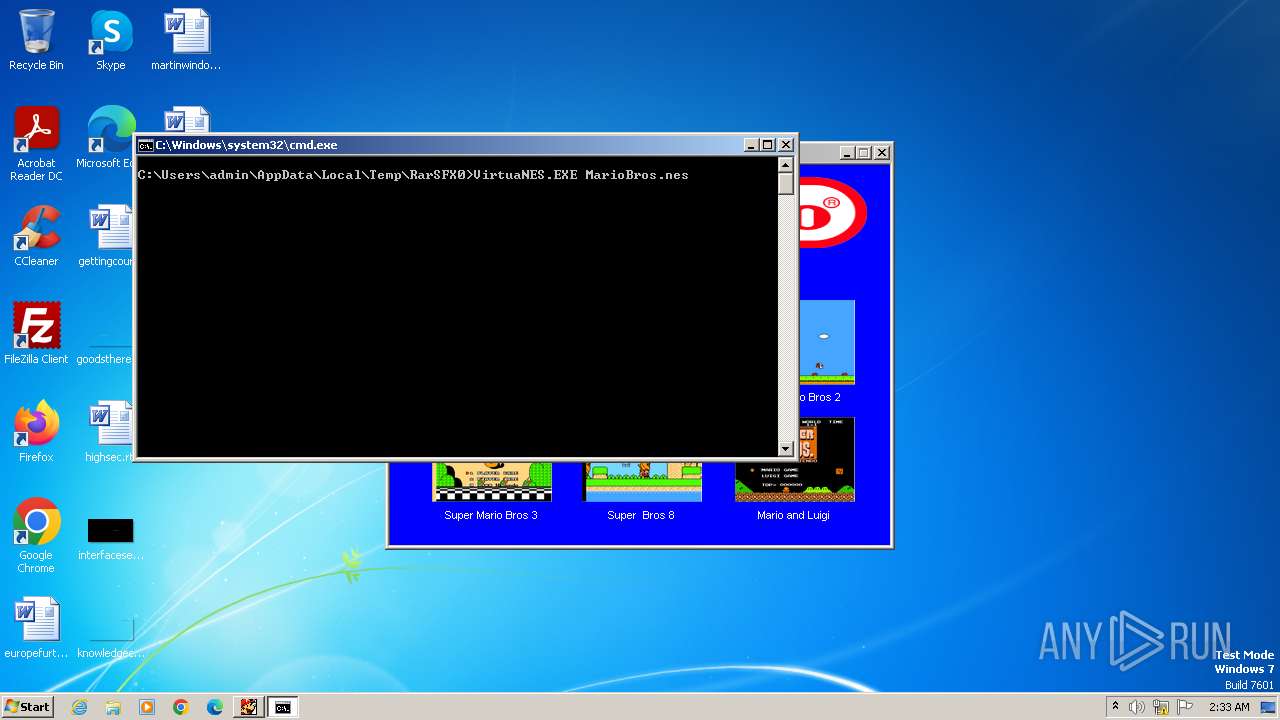
The executable file from the user directory is run by the CMD process
- VirtuaNES.exe (PID: 328)
- VirtuaNES.exe (PID: 616)
Executing commands from a ".bat" file
- Mario bros.exe (PID: 124)
- Merio and Luigi.exe (PID: 524)
Reads security settings of Internet Explorer
- autorun.exe (PID: 3992)
- Mario bros.exe (PID: 124)
- Merio and Luigi.exe (PID: 524)
Executable content was dropped or overwritten
- Mario Coleccion.exe (PID: 3976)
- Mario bros.exe (PID: 124)
- Merio and Luigi.exe (PID: 524)
Reads the Internet Settings
- Mario bros.exe (PID: 124)
- autorun.exe (PID: 3992)
- Merio and Luigi.exe (PID: 524)
Starts CMD.EXE for commands execution
- Mario bros.exe (PID: 124)
- Merio and Luigi.exe (PID: 524)
INFO
Checks supported languages
- VirtuaNES.exe (PID: 328)
- autorun.exe (PID: 3992)
- Mario bros.exe (PID: 124)
- Mario Coleccion.exe (PID: 3976)
- Merio and Luigi.exe (PID: 524)
- VirtuaNES.exe (PID: 616)
Reads the computer name
- autorun.exe (PID: 3992)
- Mario bros.exe (PID: 124)
- VirtuaNES.exe (PID: 328)
- Merio and Luigi.exe (PID: 524)
- VirtuaNES.exe (PID: 616)
Create files in a temporary directory
- Mario bros.exe (PID: 124)
- Mario Coleccion.exe (PID: 3976)
- VirtuaNES.exe (PID: 328)
- VirtuaNES.exe (PID: 616)
- Merio and Luigi.exe (PID: 524)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (35.8) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (31.7) |
| .scr | | | Windows screen saver (15) |
| .dll | | | Win32 Dynamic Link Library (generic) (7.5) |
| .exe | | | Win32 Executable (generic) (5.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2007:11:06 19:06:44+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 192512 |
| InitializedDataSize: | 102400 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x173a6 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 7.1.1000.0 |
| ProductVersionNumber: | 7.1.1000.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | Created with AutoPlay Media Studio 7.0 |
| CompanyName: | - |
| FileDescription: | AutoPlay Application |
| FileVersion: | 7.1.1000.0 |
| InternalName: | ams70_launch |
| LegalCopyright: | Runtime Engine Copyright © 2007 Indigo Rose Corporation (www.indigorose.com) |
| LegalTrademarks: | AutoPlay Media Studio is a Trademark of Indigo Rose Corporation |
| OriginalFileName: | ams70_launch.exe |
| PrivateBuild: | - |
| ProductName: | AutoPlay Media Studio 7.0 Launcher |
| ProductVersion: | 7.1.1000.0 |
| SpecialBuild: | - |
Total processes
42
Monitored processes
8
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
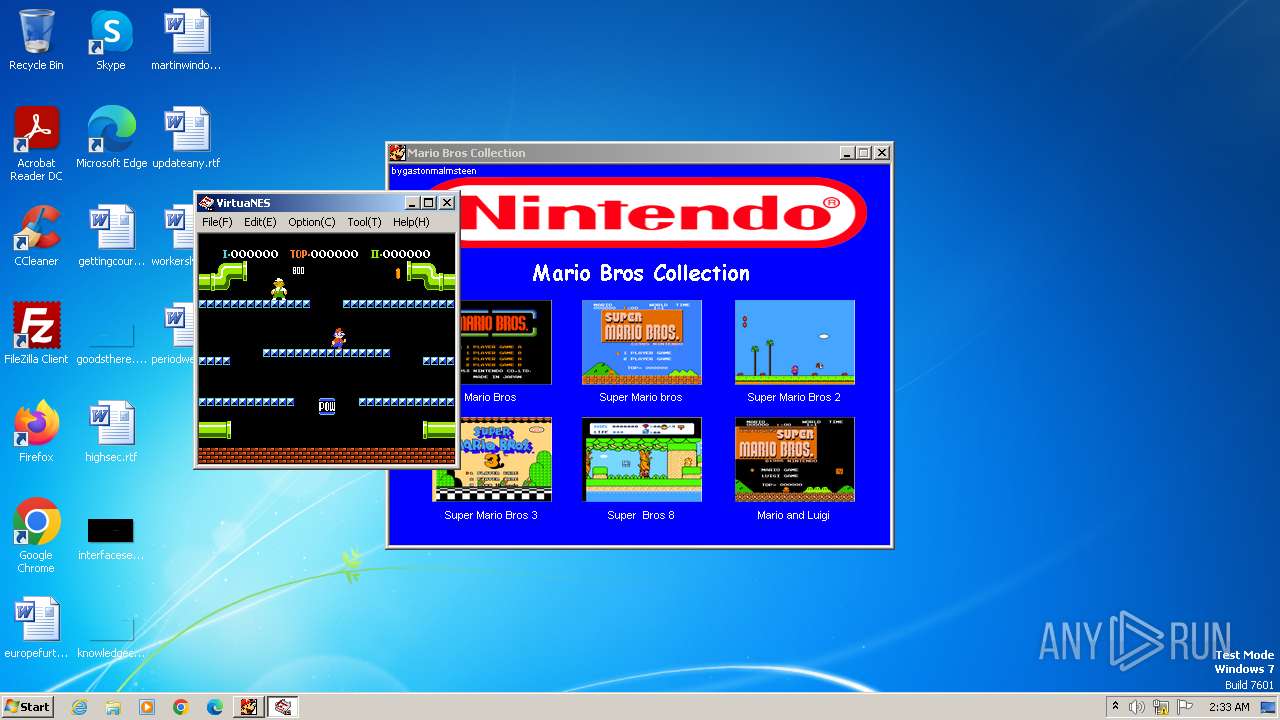
| 124 | "C:\Users\admin\AppData\Local\Temp\ir_ext_temp_0\AutoPlay\Docs\Mario bros.exe" | C:\Users\admin\AppData\Local\Temp\ir_ext_temp_0\AutoPlay\Docs\Mario bros.exe | autorun.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
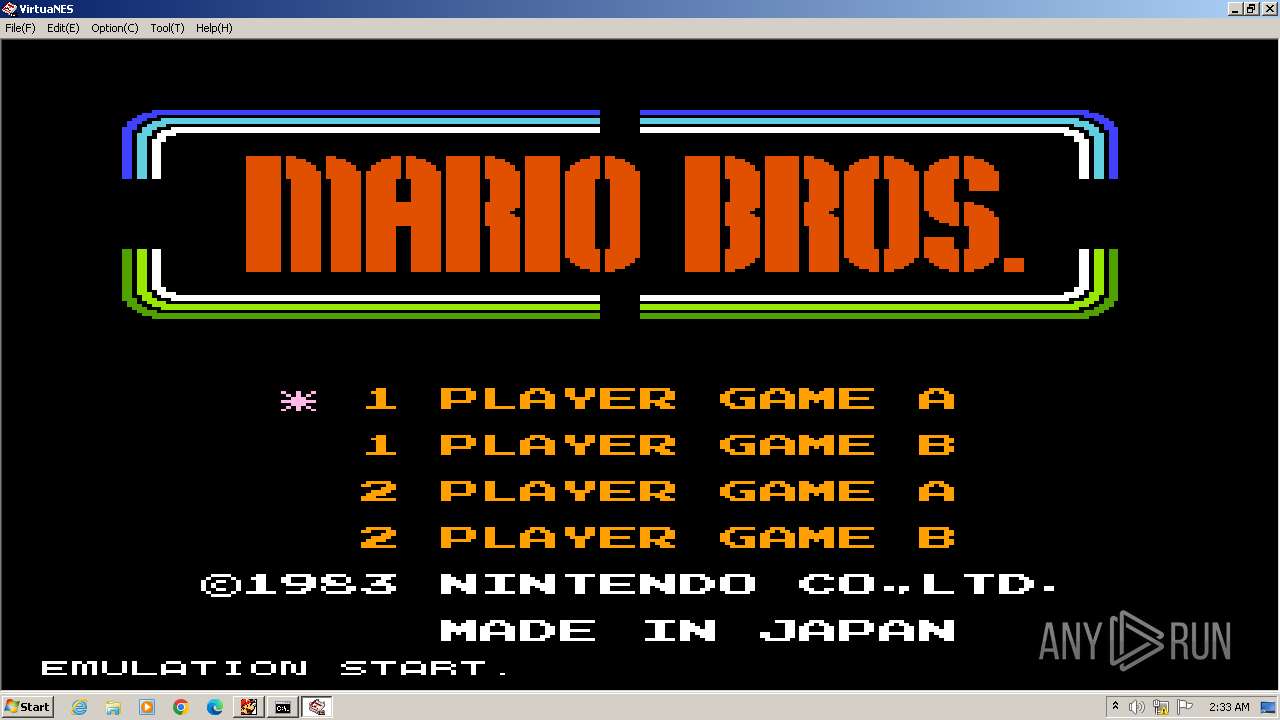
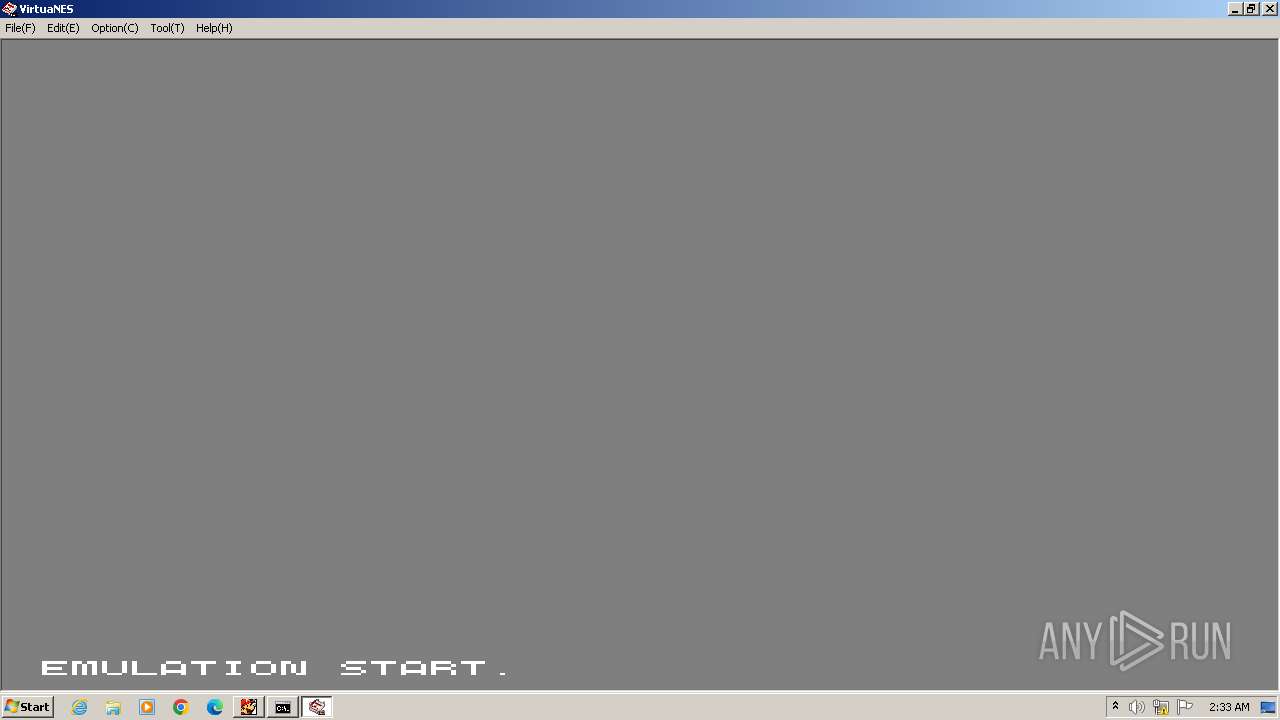
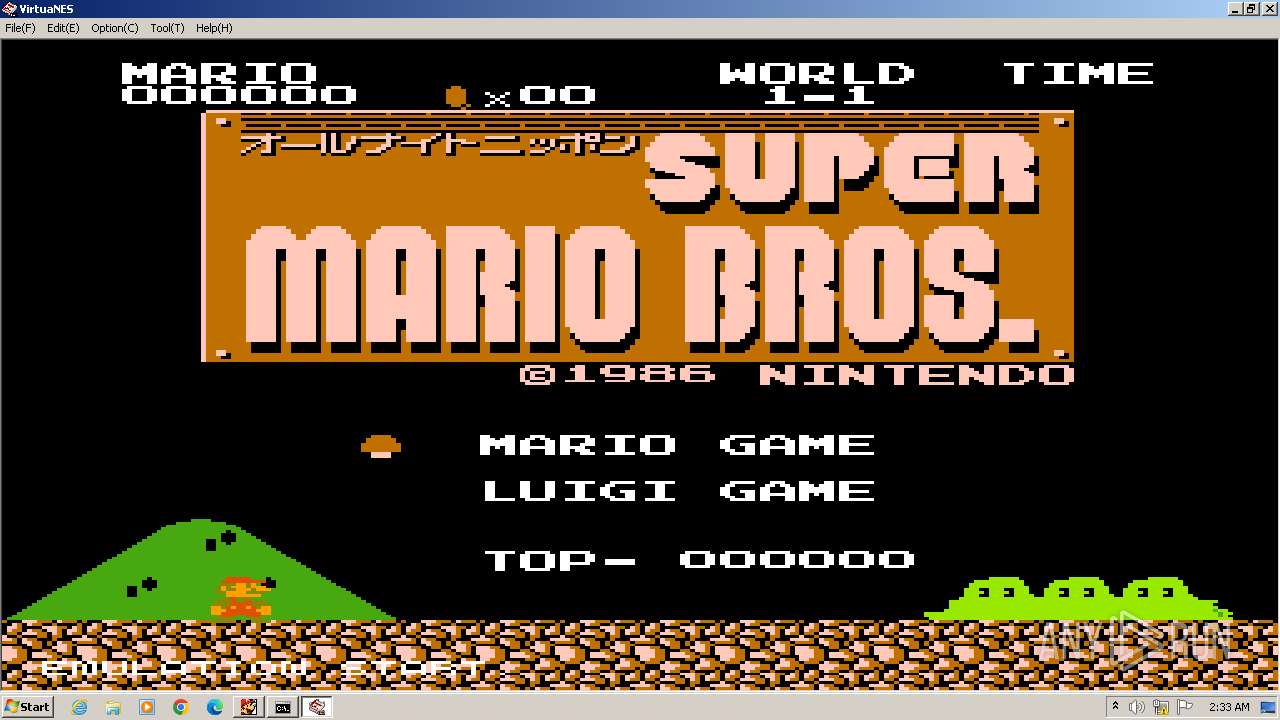
| 328 | VirtuaNES.EXE MarioBros.nes | C:\Users\admin\AppData\Local\Temp\RarSFX0\VirtuaNES.exe | cmd.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: VirtuaNES NES emulator for Win32 Exit code: 0 Version: 0.60 Modules
| |||||||||||||||
| 524 | "C:\Users\admin\AppData\Local\Temp\ir_ext_temp_0\AutoPlay\Docs\Merio and Luigi.exe" | C:\Users\admin\AppData\Local\Temp\ir_ext_temp_0\AutoPlay\Docs\Merio and Luigi.exe | autorun.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 616 | VirtuaNES.EXE MarioandLuigi.nes | C:\Users\admin\AppData\Local\Temp\RarSFX1\VirtuaNES.exe | cmd.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: VirtuaNES NES emulator for Win32 Exit code: 0 Version: 0.60 Modules
| |||||||||||||||
| 1652 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\RarSFX1\Launch.bat" " | C:\Windows\System32\cmd.exe | — | Merio and Luigi.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2028 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\RarSFX0\Launch.bat" " | C:\Windows\System32\cmd.exe | — | Mario bros.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3976 | "C:\Users\admin\AppData\Local\Temp\Mario Coleccion.exe" | C:\Users\admin\AppData\Local\Temp\Mario Coleccion.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: AutoPlay Application Exit code: 0 Version: 7.1.1000.0 Modules
| |||||||||||||||
| 3992 | "C:\Users\admin\AppData\Local\Temp\ir_ext_temp_0\autorun.exe" "SFXSOURCE:C:\Users\admin\AppData\Local\Temp\Mario Coleccion.exe" | C:\Users\admin\AppData\Local\Temp\ir_ext_temp_0\autorun.exe | — | Mario Coleccion.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: By Thunder Hack Gold Exit code: 3221225547 Version: 7.1.1000.0 Modules
| |||||||||||||||
Total events
9 920
Read events
9 884
Write events
36
Delete events
0
Modification events
| (PID) Process: | (3992) autorun.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3992) autorun.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3992) autorun.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3992) autorun.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (124) Mario bros.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (124) Mario bros.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (124) Mario bros.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (124) Mario bros.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (328) VirtuaNES.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\DirectDraw\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: VirtuaNES.exe | |||
| (PID) Process: | (328) VirtuaNES.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\DirectDraw\MostRecentApplication |
| Operation: | write | Name: | ID |
Value: | |||
Executable files
14
Suspicious files
7
Text files
28
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3976 | Mario Coleccion.exe | C:\Users\admin\AppData\Local\Temp\ir_ext_temp_0\mario.ico | — | |
MD5:— | SHA256:— | |||
| 3976 | Mario Coleccion.exe | C:\Users\admin\AppData\Local\Temp\ir_ext_temp_0\AutoPlay\Docs\Super Mario Bros.exe | executable | |
MD5:6A23798D3BA86CE1F532EFDA702E8BD5 | SHA256:D964DF0BC4AD209F9BD2967890D15F73309CDAE932063E09982972BDF0902A40 | |||
| 3976 | Mario Coleccion.exe | C:\Users\admin\AppData\Local\Temp\ir_ext_temp_0\AutoPlay\autorun.cdd | compressed | |
MD5:4A3AEB6F2F6D614A255ED42B06D5DB53 | SHA256:1E83CA84DA872D93D0CBAFD799A24FD6739E938B2D76817D470DB1EA8149F466 | |||
| 3976 | Mario Coleccion.exe | C:\Users\admin\AppData\Local\Temp\ir_ext_temp_0\AutoPlay\Docs\Super mario Bros 2.exe | executable | |
MD5:11F28ABD0AC06067AFC091853C334F10 | SHA256:BEF29632E8FB720D0F4A7BF1CEC7F19A5D233CD441A5BE2F6E312032BD84E195 | |||
| 3976 | Mario Coleccion.exe | C:\Users\admin\AppData\Local\Temp\ir_ext_temp_0\AutoPlay\Audio\Click1.ogg | binary | |
MD5:93270C4FA492E4E4EDEE872A2B961DDE | SHA256:25D49CBBD65D48AD462455F1143F73EE997DF8F747E7D2213DAAB18E321C028B | |||
| 3976 | Mario Coleccion.exe | C:\Users\admin\AppData\Local\Temp\ir_ext_temp_0\AutoPlay\Audio\High1.ogg | binary | |
MD5:FC2A595F574B1EAD82A6DCF06492C985 | SHA256:EE9A4903A8DF90EFF4C5B65A8073E564A3581CF73772A72EB82396E69932E769 | |||
| 3976 | Mario Coleccion.exe | C:\Users\admin\AppData\Local\Temp\ir_ext_temp_0\AutoPlay\Docs\Mario bros.exe | executable | |
MD5:82D7EAED28D78DD9B66EAF72CD3EDE74 | SHA256:BB3A3DA0C9A116080617D91ABB320A67099B20AD6422A162C114E527F2F7EC30 | |||
| 3976 | Mario Coleccion.exe | C:\Users\admin\AppData\Local\Temp\ir_ext_temp_0\AutoPlay\Images\MARIO Y LUIGI.bmp | image | |
MD5:83BBD0EF82683D86E2AD63EDD48868B6 | SHA256:2F1A8A2C65E92DB0EA14C0730BA3442628AB771085908EBFBA5EF483C811A382 | |||
| 3976 | Mario Coleccion.exe | C:\Users\admin\AppData\Local\Temp\ir_ext_temp_0\AutoPlay\Images\Nintendo_Logo.png | image | |
MD5:A3FD6766511018084BE29F7D13B3C68C | SHA256:03B640411B97E8F542E586515E629628729D5F1F2352B24A817C5DFA19B1F33C | |||
| 3976 | Mario Coleccion.exe | C:\Users\admin\AppData\Local\Temp\ir_ext_temp_0\AutoPlay\Docs\Super Bros 8.exe | executable | |
MD5:3053C75DFB724FF30CF13D001A05EF7F | SHA256:5BD90C29CAC64F4DC48BA747599230596A7B97E0CAF8D4148F3E5C36FEDA6AF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Threats
Process | Message |
|---|---|
VirtuaNES.exe | DebugWindow ‚ª‚ ‚è‚Ü‚¹‚ñ
|
VirtuaNES.exe | DebugWindow ‚ª‚ ‚è‚Ü‚¹‚ñ
|