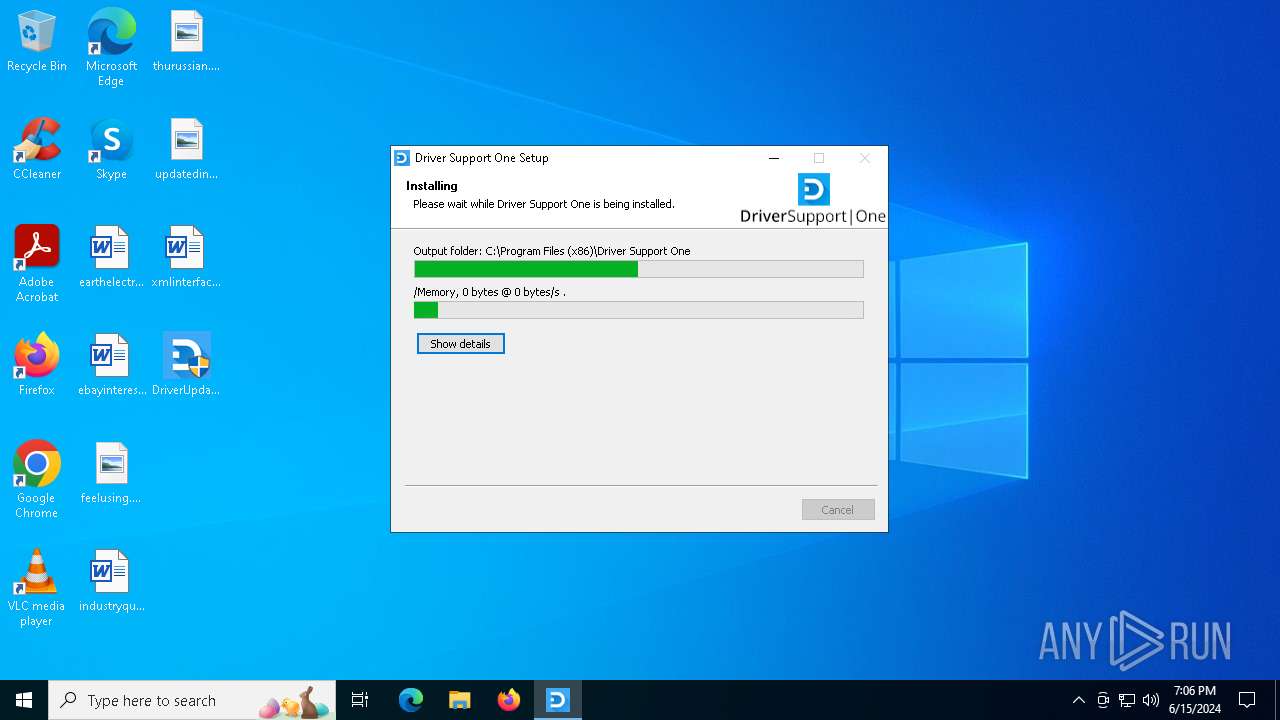
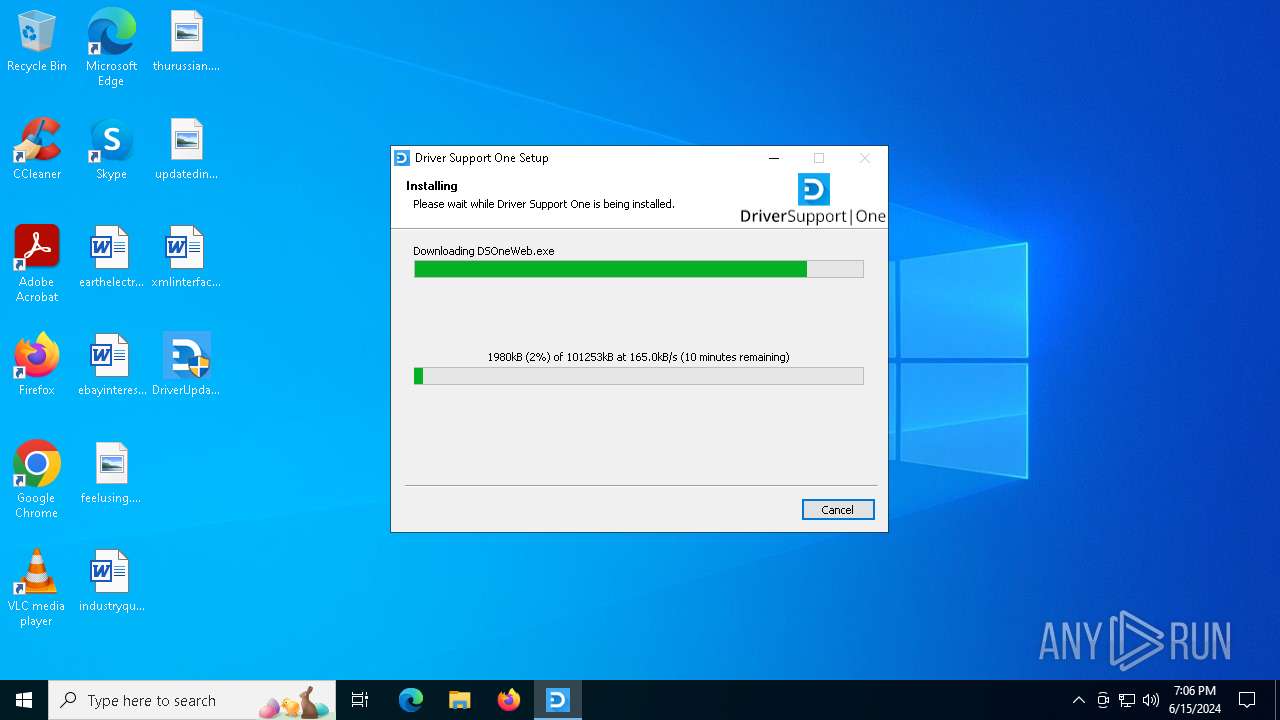
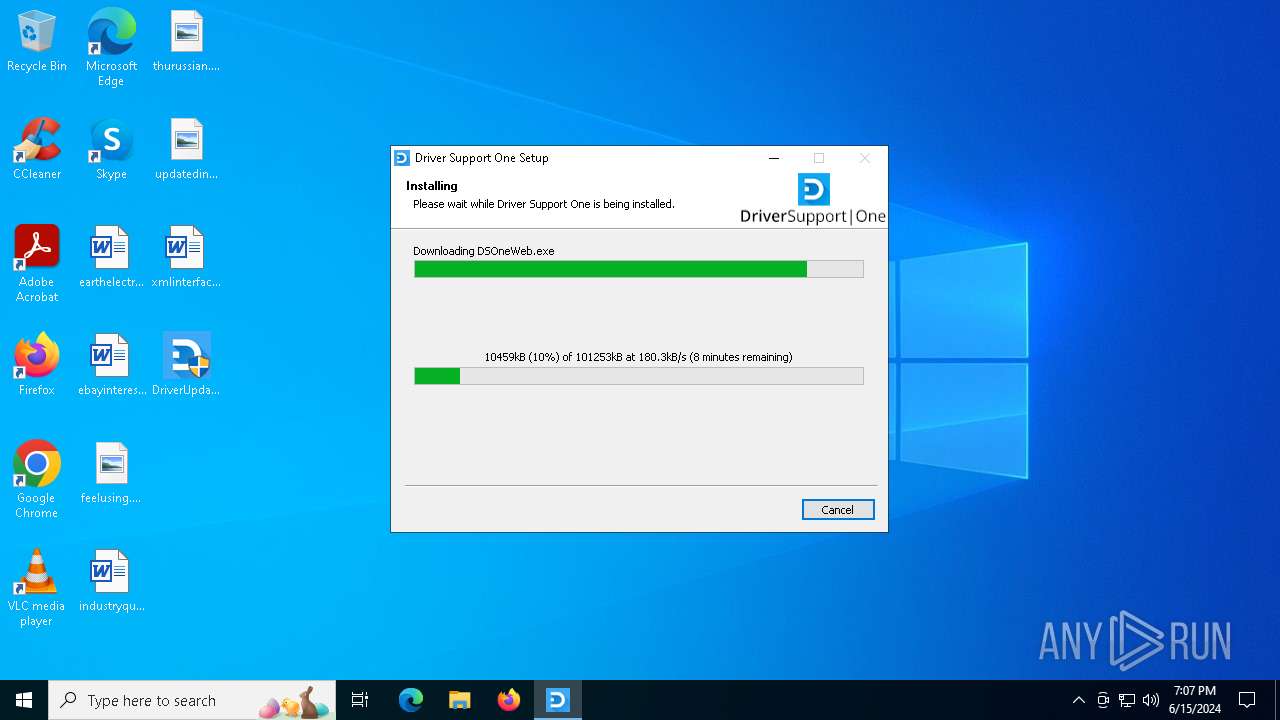
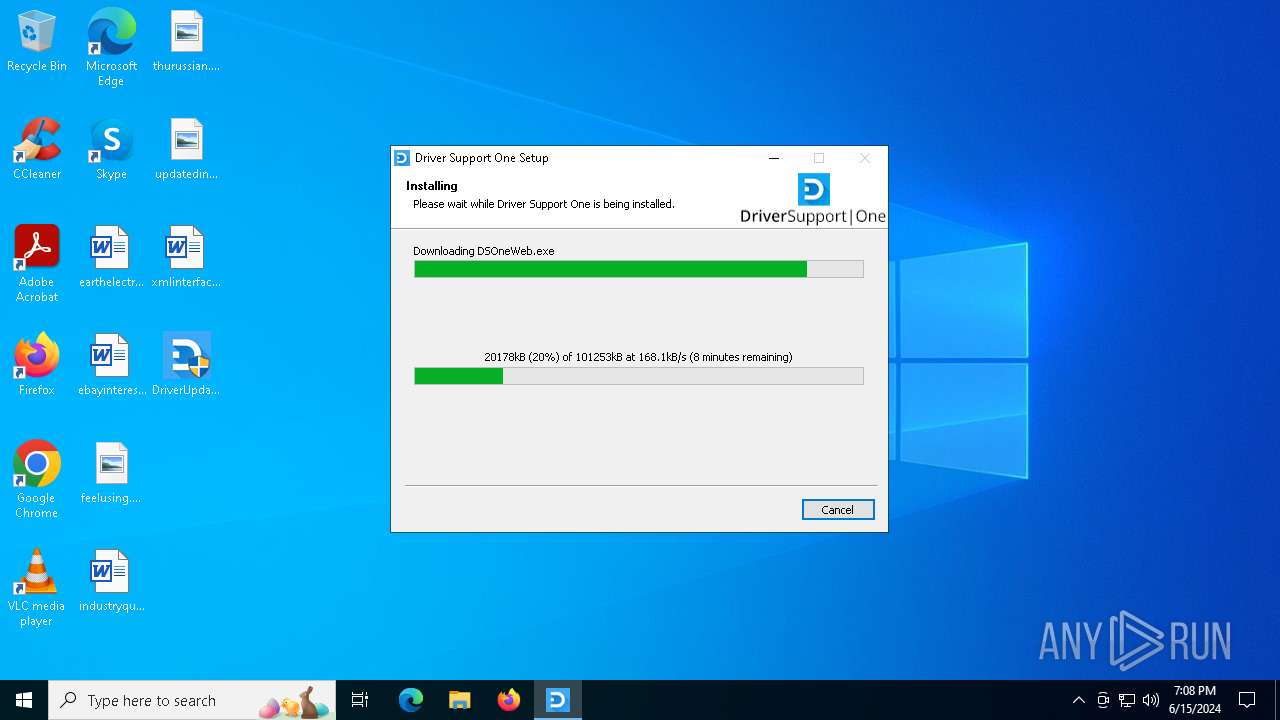
| File name: | DriverUpdate.exe |
| Full analysis: | https://app.any.run/tasks/751a3c1f-f2ad-40da-a0da-49b9c8660aa2 |
| Verdict: | Malicious activity |
| Analysis date: | June 15, 2024, 19:06:00 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 1DBB3736D491A2F652D350F3D535EEF4 |
| SHA1: | 2AFFDF99938BC10D32FA116241941115E0437CE2 |
| SHA256: | 98598C90BD75B930ABA968467F4B540A5784AA28612B8010D8A9CF31992843C6 |
| SSDEEP: | 49152:Tmx65U8vkF/yMrxNnc3rEo+YwOa3EZ4mUDYO97g3PKXUJ/b5n7GieCPzpk7QsDFA:TmYU8kyWxZc3rETD5EZ4jDVxSPKX+/8a |
MALICIOUS
Drops the executable file immediately after the start
- DriverUpdate.exe (PID: 1604)
SUSPICIOUS
The process creates files with name similar to system file names
- DriverUpdate.exe (PID: 1604)
Malware-specific behavior (creating "System.dll" in Temp)
- DriverUpdate.exe (PID: 1604)
Process requests binary or script from the Internet
- DriverUpdate.exe (PID: 1604)
Potential Corporate Privacy Violation
- DriverUpdate.exe (PID: 1604)
Executable content was dropped or overwritten
- DriverUpdate.exe (PID: 1604)
INFO
Checks supported languages
- DriverUpdate.exe (PID: 1604)
Reads the machine GUID from the registry
- DriverUpdate.exe (PID: 1604)
Creates files in the program directory
- DriverUpdate.exe (PID: 1604)
Create files in a temporary directory
- DriverUpdate.exe (PID: 1604)
Checks proxy server information
- DriverUpdate.exe (PID: 1604)
Reads the computer name
- DriverUpdate.exe (PID: 1604)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2017:08:01 00:33:55+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 25088 |
| InitializedDataSize: | 118784 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x330d |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.7.8661.30575 |
| ProductVersionNumber: | 2.7.8661.30575 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | Driver Support |
| FileDescription: | Driver Support One |
| FileVersion: | 2.7.8661.30575 |
| LegalCopyright: | Driver Support |
| OriginalFileName: | DSOneWeb.exe |
| ProductName: | Driver Support One |
| ProductVersion: | 2.7.8661.30575 |
Total processes
117
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1604 | "C:\Users\admin\Desktop\DriverUpdate.exe" | C:\Users\admin\Desktop\DriverUpdate.exe | explorer.exe | ||||||||||||
User: admin Company: Driver Support Integrity Level: HIGH Description: Driver Support One Version: 2.7.8661.30575 Modules
| |||||||||||||||
| 3916 | "C:\Users\admin\Desktop\DriverUpdate.exe" | C:\Users\admin\Desktop\DriverUpdate.exe | — | explorer.exe | |||||||||||
User: admin Company: Driver Support Integrity Level: MEDIUM Description: Driver Support One Exit code: 3221226540 Version: 2.7.8661.30575 Modules
| |||||||||||||||
Total events
517
Read events
516
Write events
1
Delete events
0
Modification events
| (PID) Process: | (1604) DriverUpdate.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\DSOneWeb |
| Operation: | write | Name: | NSISInstanceID |
Value: {E218A513-E7EF-4112-8D30-F40FC811D066} | |||
Executable files
8
Suspicious files
0
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1604 | DriverUpdate.exe | C:\Users\admin\AppData\Local\Temp\nsu4006.tmp\NScurl.dll | executable | |
MD5:16E134EC014D74E9B798C9B3FAE3DDCC | SHA256:EDA02E626E8CA71DBFF5389C062F9E9542661B43413B0A37AE3D262567145CE2 | |||
| 1604 | DriverUpdate.exe | C:\Users\admin\AppData\Local\Temp\nsu4006.tmp\System.dll | executable | |
MD5:55A26D7800446F1373056064C64C3CE8 | SHA256:904FD5481D72F4E03B01A455F848DEDD095D0FB17E33608E0D849F5196FB6FF8 | |||
| 1604 | DriverUpdate.exe | C:\Users\admin\AppData\Local\Temp\nsu4006.tmp\modern-header.bmp | image | |
MD5:5E167C6BD5D01F63AD7E7B0C389E12CA | SHA256:16161D986C93DF5E4222AFF2EF2D4128CD15464A4AA9D8D155D5B5903675C817 | |||
| 1604 | DriverUpdate.exe | C:\Users\admin\AppData\Local\Temp\nsu4006.tmp\DotNetChecker.dll | executable | |
MD5:F18364FA5084ADD86C6E73E457404F18 | SHA256:39C43D67F546FC898F7406D213B73DCB1BC30FC811DDFA3A02B6B50C29D11F91 | |||
| 1604 | DriverUpdate.exe | C:\Users\admin\AppData\Local\Temp\nsu4006.tmp\UserInfo.dll | executable | |
MD5:C051C86F6FA84AC87EFB0CF3961950A1 | SHA256:D0949B4C0640EE6A80DB5A7F6D93FC631ED194DE197D79BF080EC1752C6F1166 | |||
| 1604 | DriverUpdate.exe | C:\Users\admin\AppData\Local\Temp\nsu4006.tmp\nsDialogs.dll | executable | |
MD5:EE449B0ADCE56FBFA433B0239F3F81BE | SHA256:C1CC3AA4326E83A73A778DEE0CF9AFCC03A6BAFB0A32CEA791A27EB9C2288985 | |||
| 1604 | DriverUpdate.exe | C:\Users\admin\AppData\Local\Temp\nsu4006.tmp\cacert.pem | text | |
MD5:3F52E40243F5FEDE19A3C8372268E1D5 | SHA256:A3B534269C6974631DB35F952E8D7C7DBF3D81AB329A232DF575C2661DE1214A | |||
| 1604 | DriverUpdate.exe | C:\Users\admin\AppData\Local\Temp\nsu4006.tmp\nsResize.dll | executable | |
MD5:AA849E7407CF349021812F62C001E097 | SHA256:29B0E5792679756A79D501E3A9B317971B08E876FAC1C2476180D0AE83B77BA5 | |||
| 1604 | DriverUpdate.exe | C:\Users\admin\AppData\Local\Temp\nsu4006.tmp\LangDLL.dll | executable | |
MD5:EA60C7BD5EDD6048601729BD31362C16 | SHA256:4E72C8B4D36F128B25281440E59E39AF7EC2080D02E024F35AC413D769D91F39 | |||
| 1604 | DriverUpdate.exe | C:\Users\admin\AppData\Local\Temp\nsu4006.tmp\modern-wizard.bmp | image | |
MD5:DC307178EDCF316064ABB7E099C7B2A5 | SHA256:4497888E6948671B345F762E3C692434290F8E06C7711465529EB413260702D3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
25
DNS requests
8
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1964 | RUXIMICS.exe | GET | 200 | 184.51.127.51:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
5140 | MoUsoCoreWorker.exe | GET | 200 | 184.51.127.51:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1964 | RUXIMICS.exe | GET | 200 | 23.36.69.232:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
636 | svchost.exe | GET | 200 | 23.36.69.232:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
5140 | MoUsoCoreWorker.exe | GET | 200 | 23.36.69.232:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
1604 | DriverUpdate.exe | GET | — | 152.199.21.175:80 | http://cdn2.driversupport.com/dsoneweb/driversupport_ds1web/DSOneWebApp.exe | unknown | — | — | unknown |
— | — | POST | 200 | 40.79.189.59:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 9 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
636 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1964 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | unknown |
5140 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1964 | RUXIMICS.exe | 184.51.127.51:80 | crl.microsoft.com | Akamai International B.V. | IT | unknown |
5140 | MoUsoCoreWorker.exe | 184.51.127.51:80 | crl.microsoft.com | Akamai International B.V. | IT | unknown |
1964 | RUXIMICS.exe | 23.36.69.232:80 | www.microsoft.com | AKAMAI-AS | US | unknown |
636 | svchost.exe | 23.36.69.232:80 | www.microsoft.com | AKAMAI-AS | US | unknown |
1604 | DriverUpdate.exe | 13.84.181.47:443 | api.driversupport.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
5140 | MoUsoCoreWorker.exe | 23.36.69.232:80 | www.microsoft.com | AKAMAI-AS | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
api.driversupport.com |
| unknown |
settings-win.data.microsoft.com |
| whitelisted |
cdn2.driversupport.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1604 | DriverUpdate.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2 ETPRO signatures available at the full report