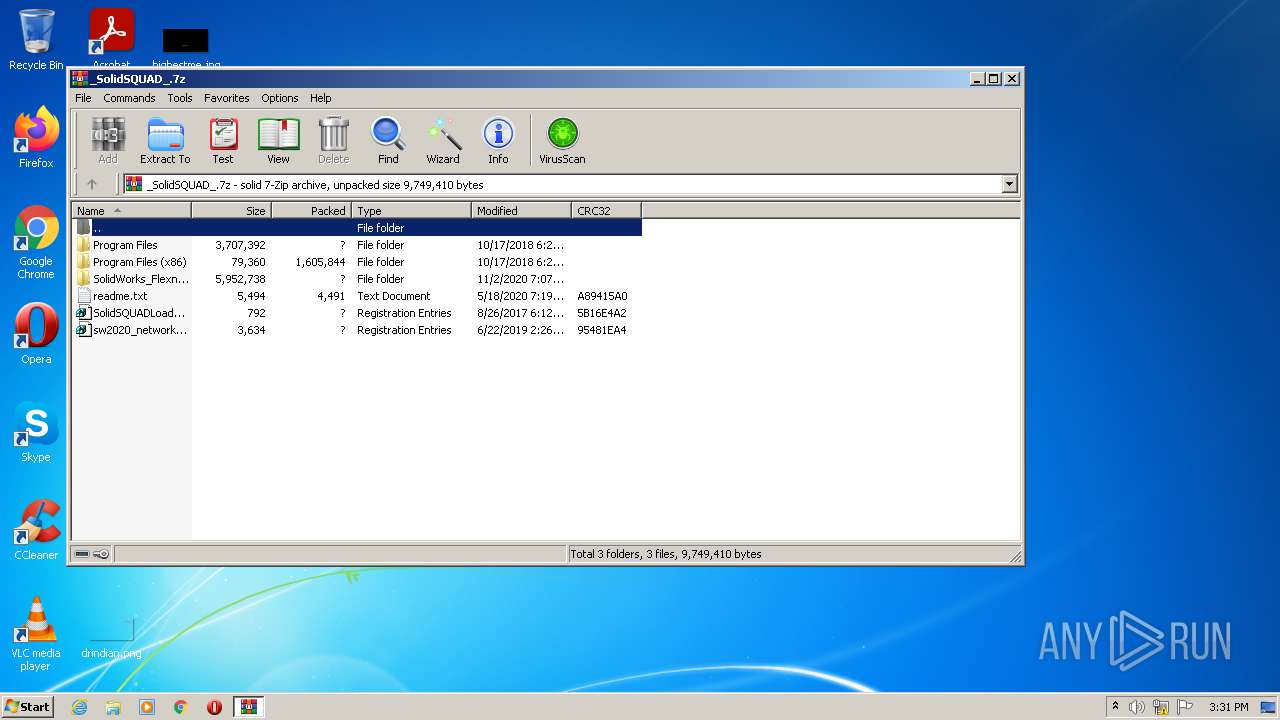
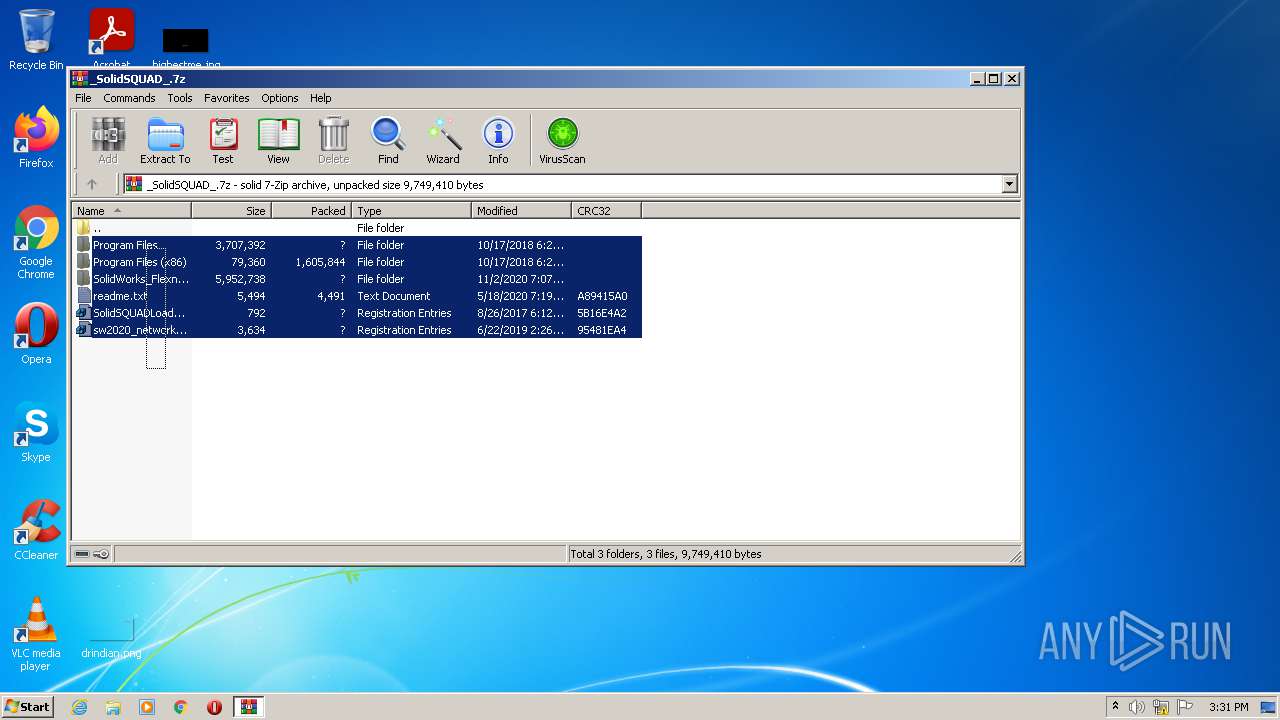
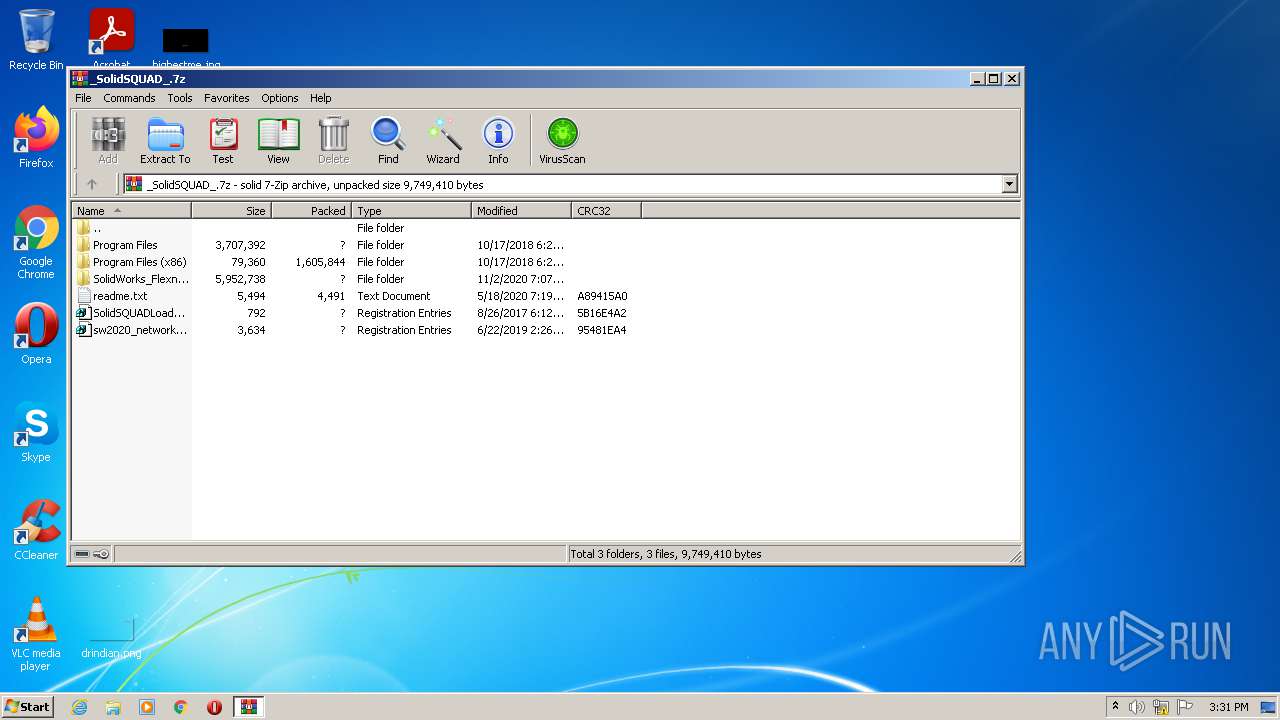
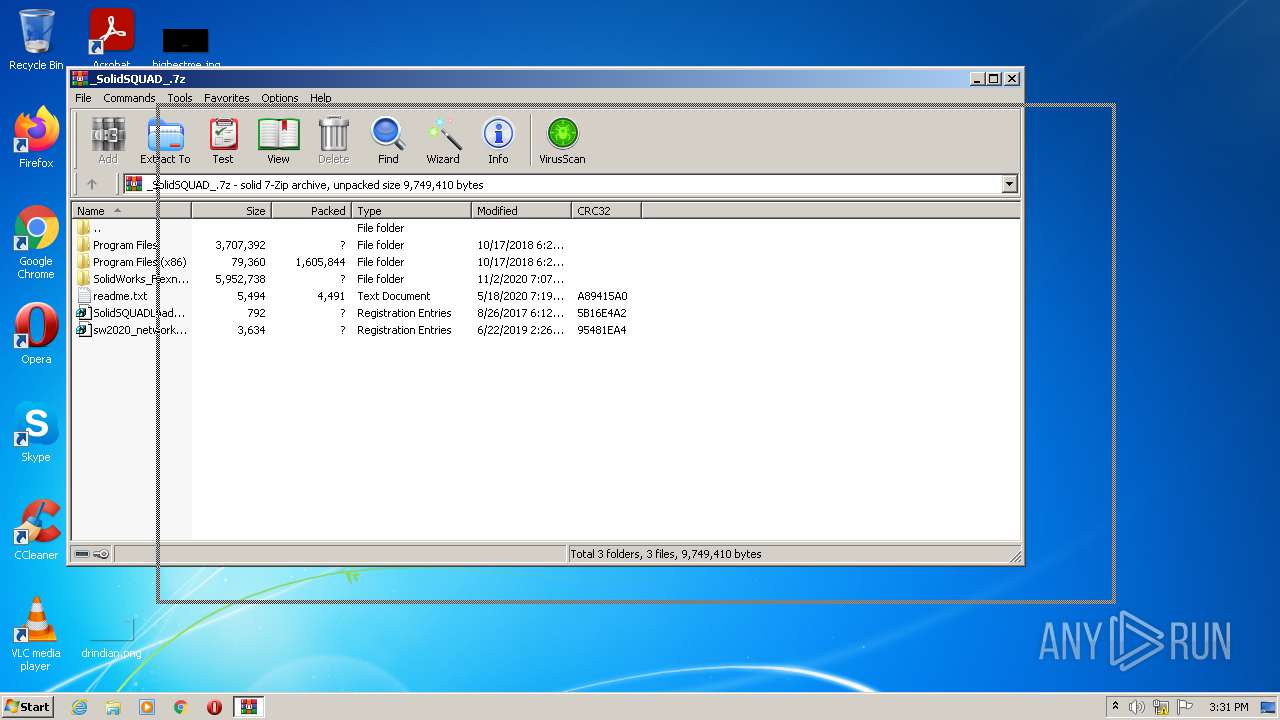
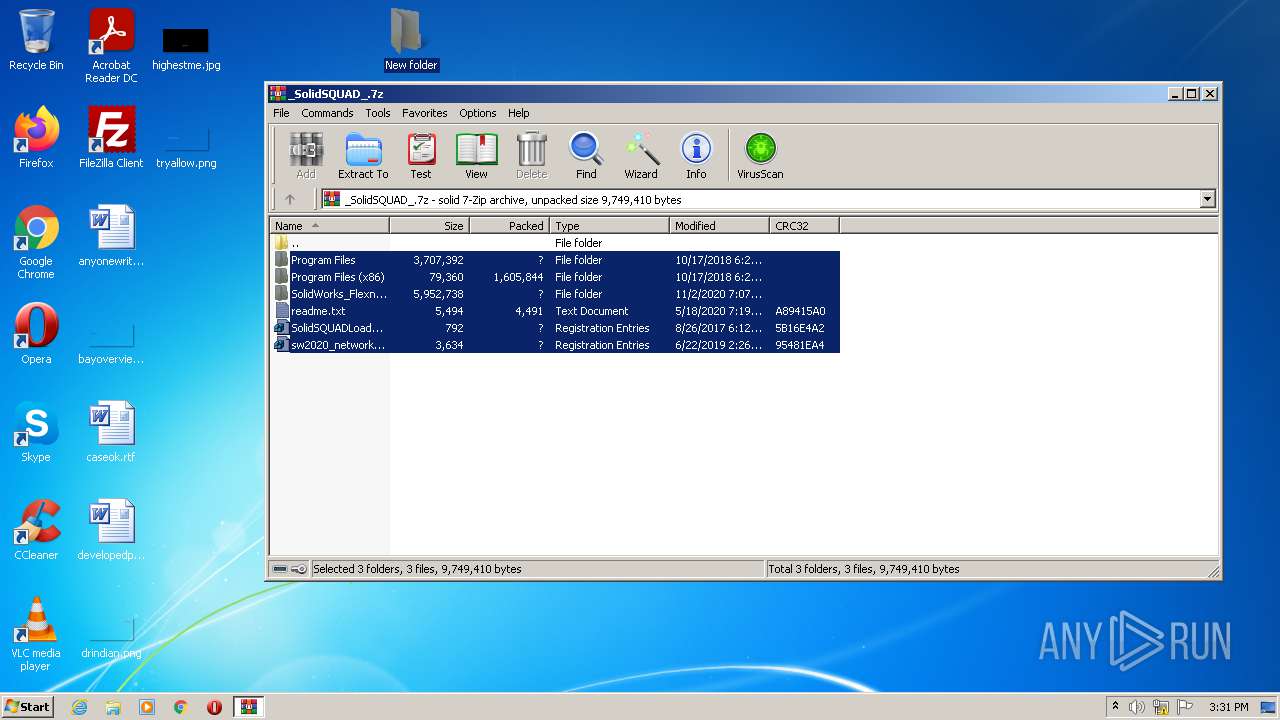
| File name: | _SolidSQUAD_.7z |
| Full analysis: | https://app.any.run/tasks/55333df9-c3eb-4982-939b-b9a3ef833a28 |
| Verdict: | Malicious activity |
| Analysis date: | November 14, 2021, 15:31:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 7B584255A78FD67FEF8784D412D33021 |
| SHA1: | 229BD088D6A52A2DFE4DDDCA1C292D886492E493 |
| SHA256: | 984D72782737937706DAEF1287E0624025EFF497B6959D3F0B88306E8D5B0960 |
| SSDEEP: | 49152:5XzVla2bI3n24bHDXXazK0rTs7CdPG5Sl7K+NS+hIhs:tz7RktX8KqG2PG5BEy+ |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3400)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 3356)
Reads the computer name
- WinRAR.exe (PID: 3356)
Drops a file with too old compile date
- WinRAR.exe (PID: 3356)
Creates a directory in Program Files
- WinRAR.exe (PID: 3356)
Creates files in the program directory
- WinRAR.exe (PID: 3356)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 3356)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3356)
INFO
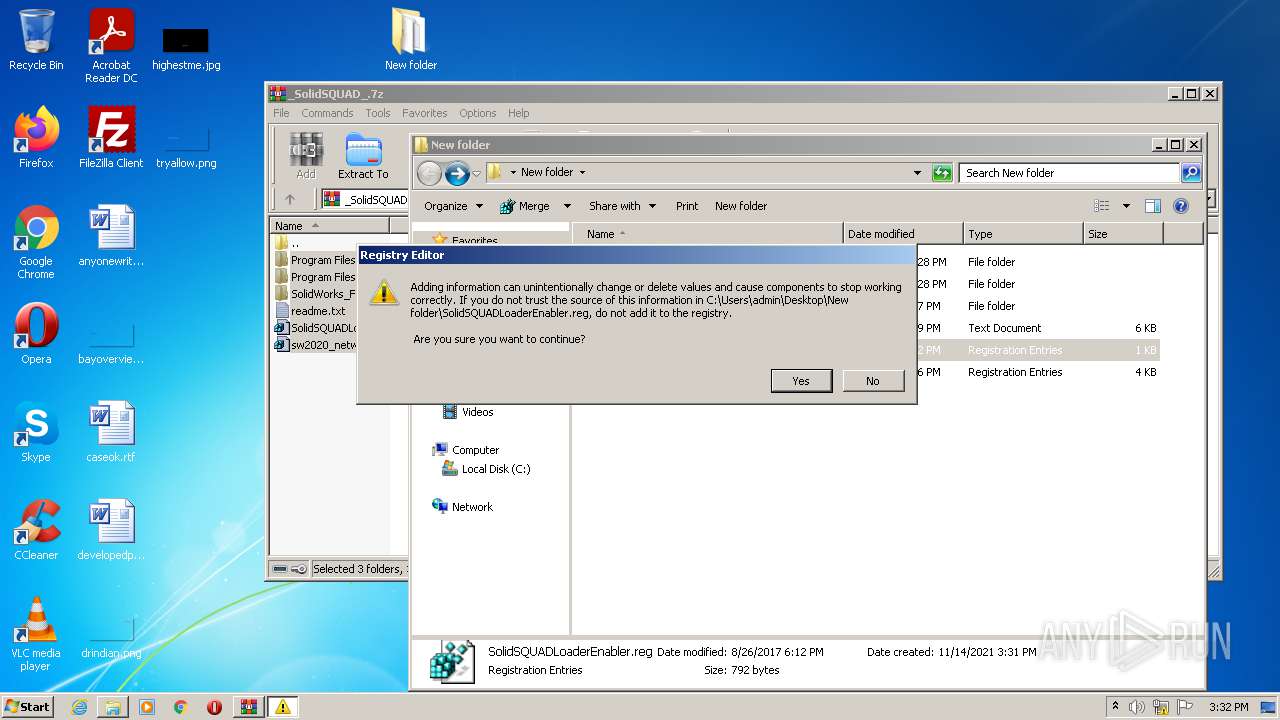
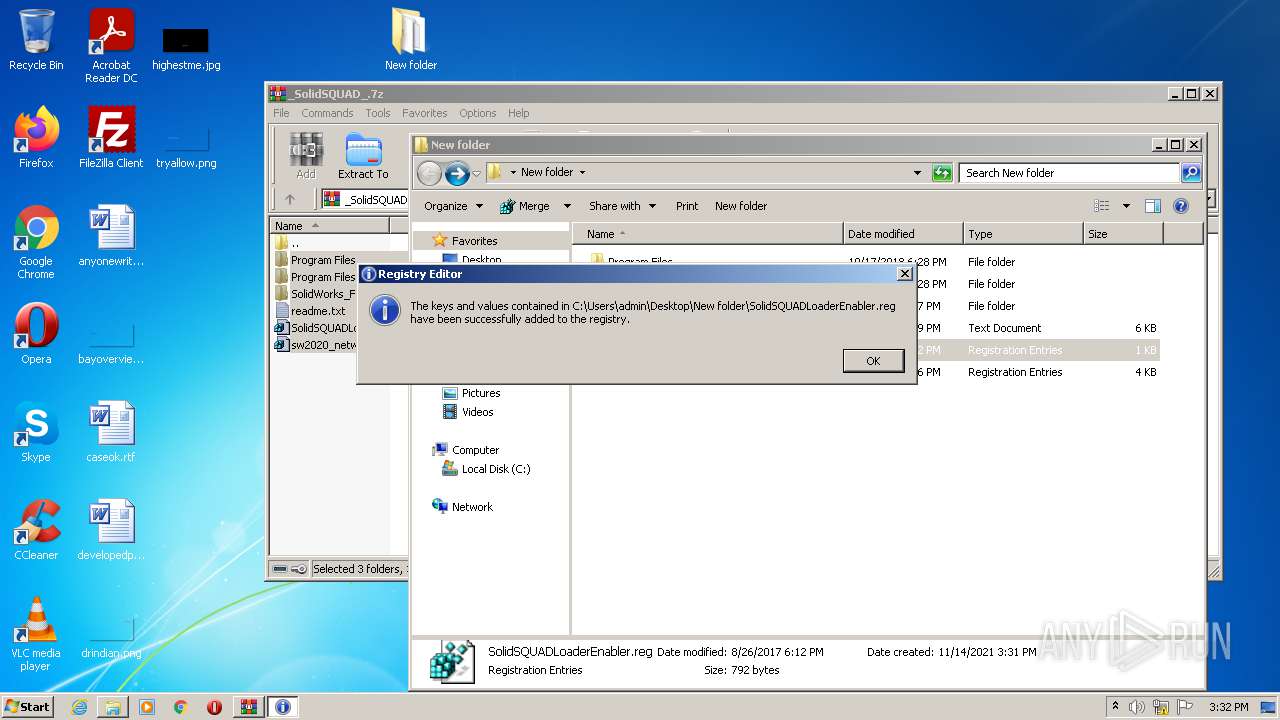
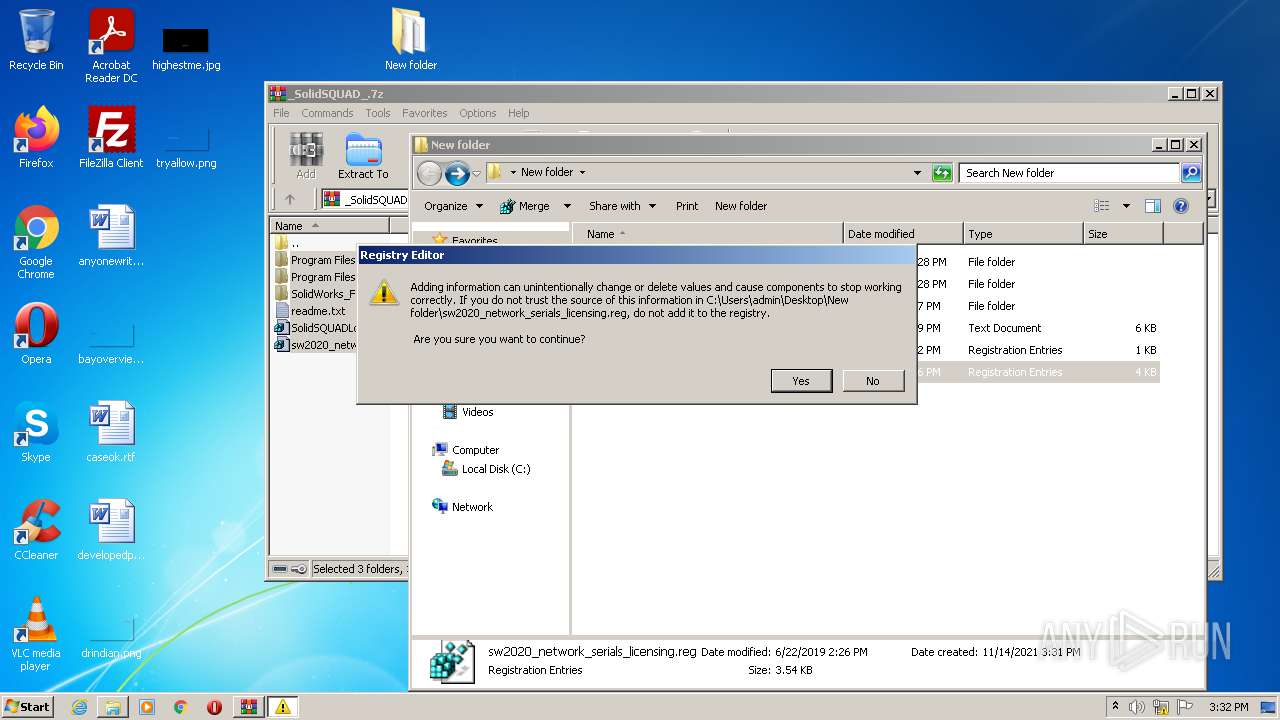
Manual execution by user
- regedit.exe (PID: 1980)
- regedit.exe (PID: 3136)
- regedit.exe (PID: 2348)
- regedit.exe (PID: 3008)
Checks supported languages
- regedit.exe (PID: 3136)
- regedit.exe (PID: 3008)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
47
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
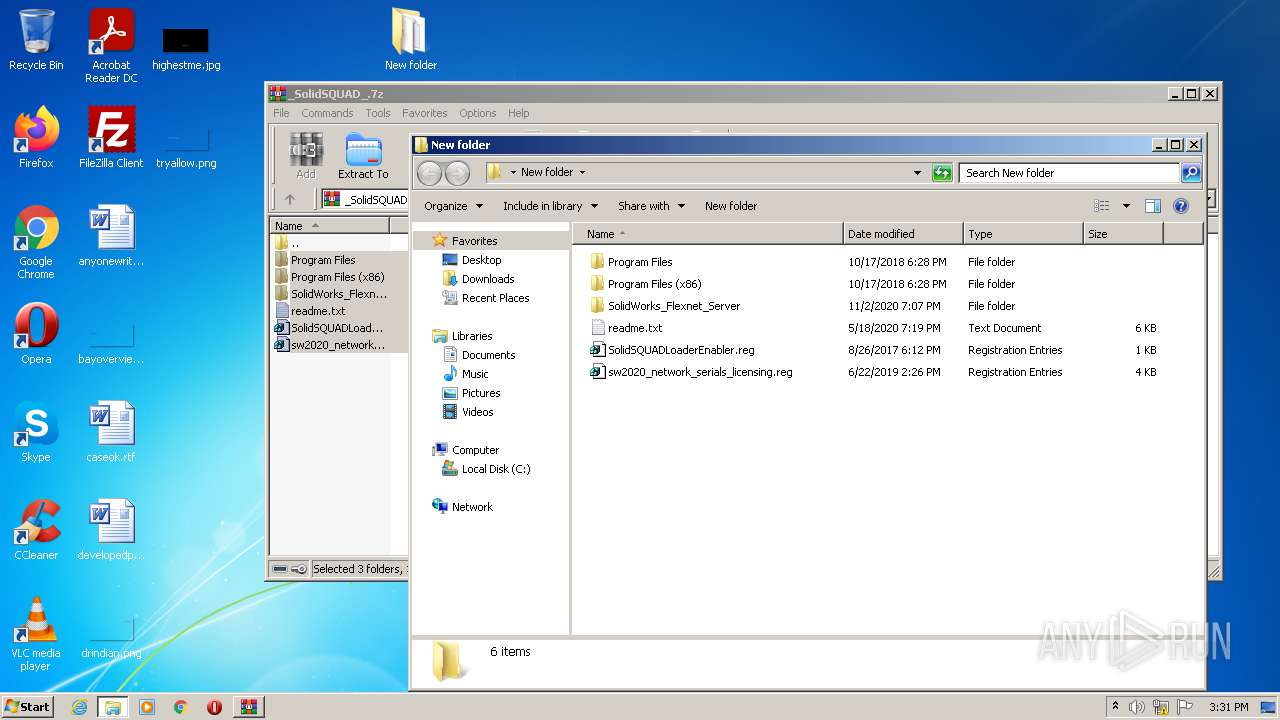
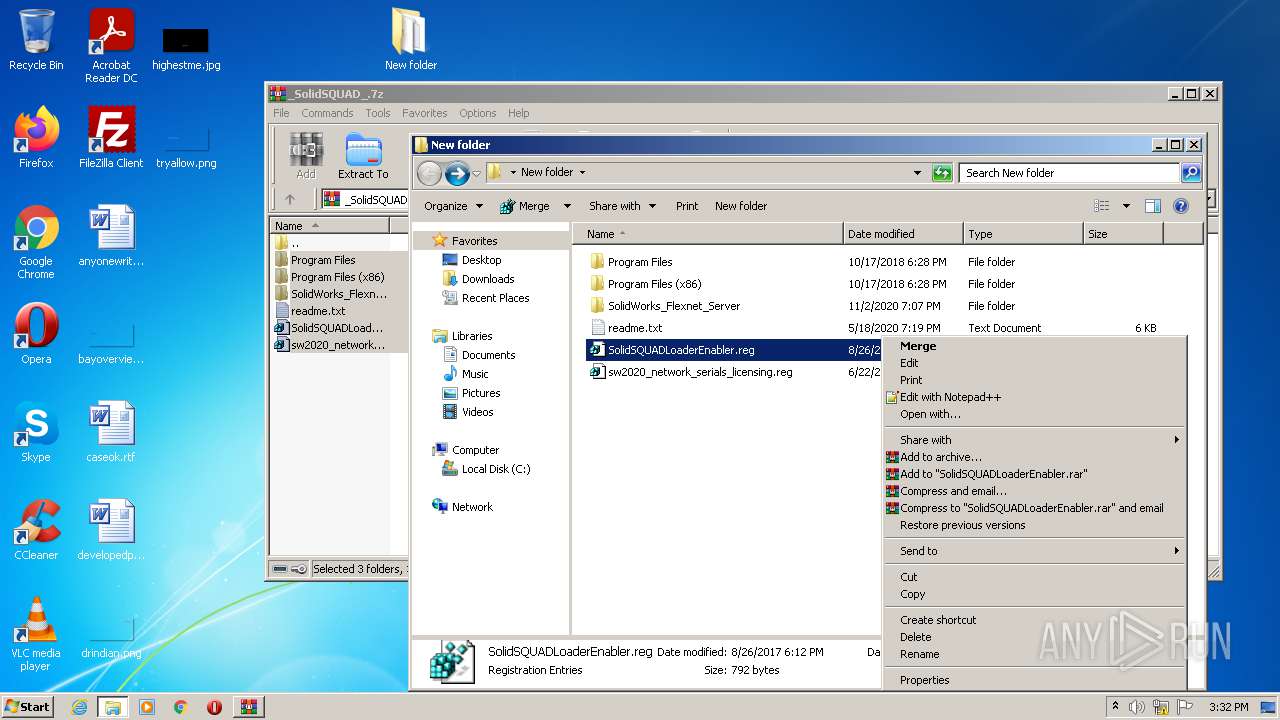
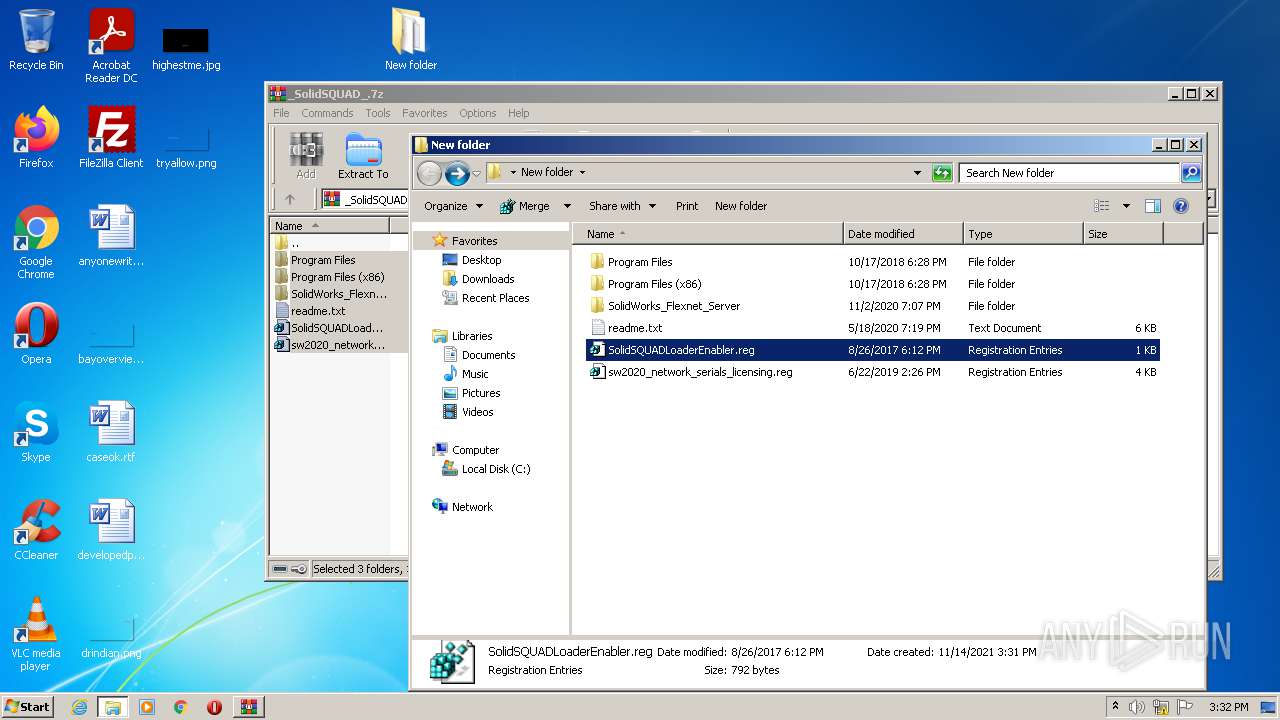
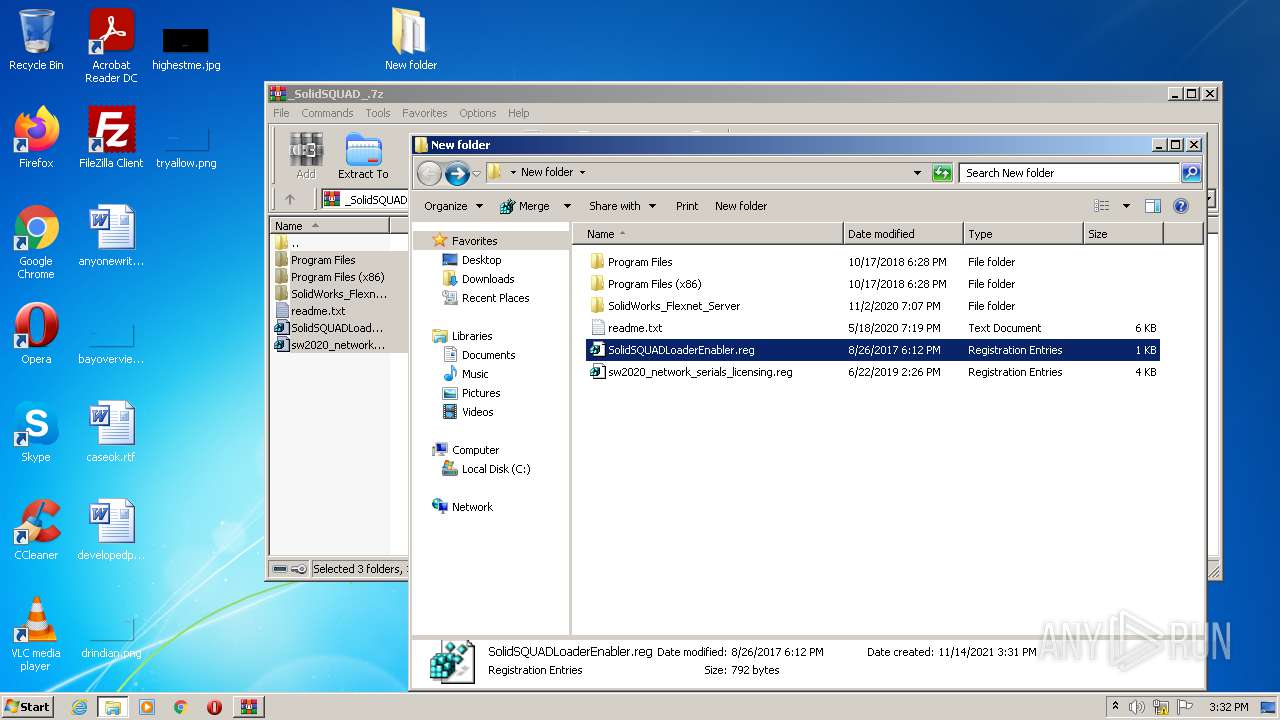
| 1980 | "regedit.exe" "C:\Users\admin\Desktop\New folder\SolidSQUADLoaderEnabler.reg" | C:\Windows\regedit.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Editor Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
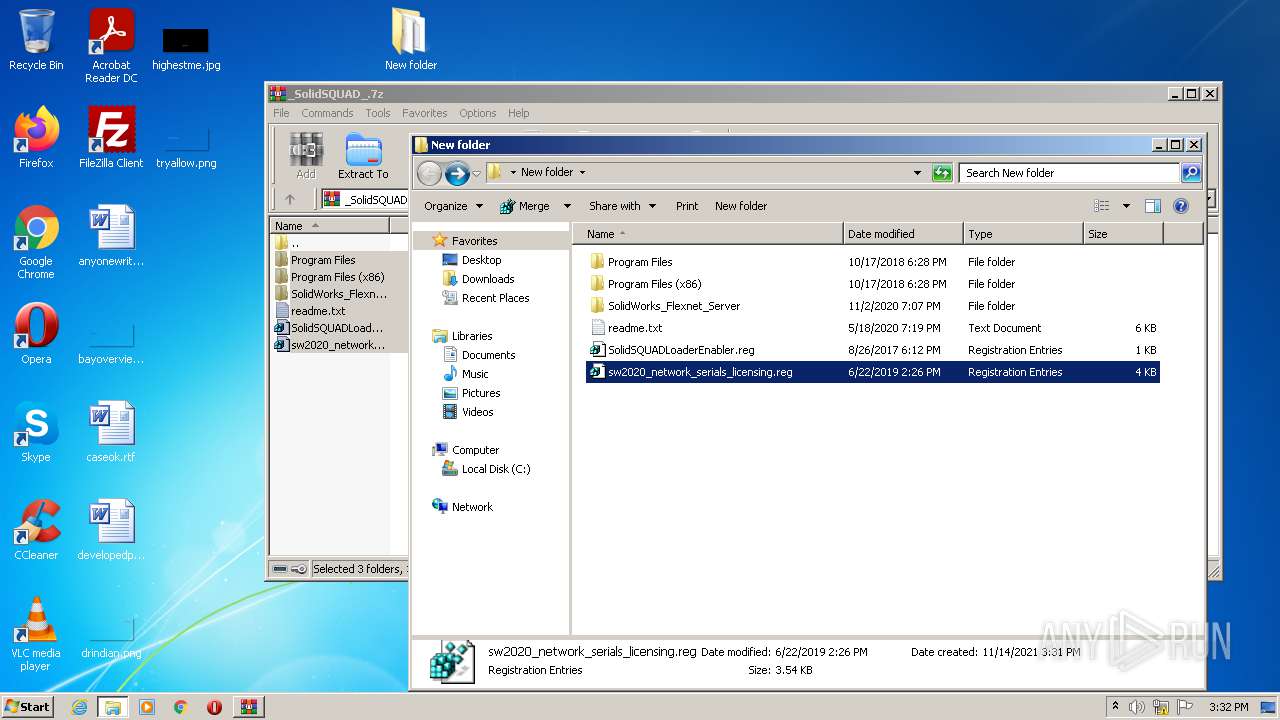
| 2348 | "regedit.exe" "C:\Users\admin\Desktop\New folder\sw2020_network_serials_licensing.reg" | C:\Windows\regedit.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Editor Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3008 | "regedit.exe" "C:\Users\admin\Desktop\New folder\sw2020_network_serials_licensing.reg" | C:\Windows\regedit.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Editor Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3136 | "regedit.exe" "C:\Users\admin\Desktop\New folder\SolidSQUADLoaderEnabler.reg" | C:\Windows\regedit.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Editor Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3356 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\_SolidSQUAD_.7z" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3400 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
Total events
1 792
Read events
1 746
Write events
46
Delete events
0
Modification events
| (PID) Process: | (3356) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3356) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3356) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3356) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3356) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\_SolidSQUAD_.7z | |||
| (PID) Process: | (3356) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3356) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3356) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3356) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3356) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | @C:\Windows\regedit.exe,-309 |
Value: Registration Entries | |||
Executable files
41
Suspicious files
0
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3356 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3356.6826\readme.txt | text | |
MD5:— | SHA256:— | |||
| 3356 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3356.6826\sw2020_network_serials_licensing.reg | text | |
MD5:— | SHA256:— | |||
| 3356 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3356.6826\Program Files (x86)\SOLIDWORKS PDM\netapi32.dll | executable | |
MD5:— | SHA256:— | |||
| 3356 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3356.6826\Program Files\SOLIDWORKS Corp\SOLIDWORKS CAM\netapi32.dll | executable | |
MD5:69559DEA95FB75855D47B07682D709B2 | SHA256:06F5830CFC6284CC1FE5FD3EAEA98B35C61760EC9DDA023C2BDD235DC88F7D84 | |||
| 3356 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3356.6826\SolidWorks_Flexnet_Server\server_install.bat | text | |
MD5:A052A4D56D383704FF24E8E873EF3400 | SHA256:49F922495FE79151E8B1C7E5BFDCA11573EB4AC958888301E7D9126A1F000459 | |||
| 3356 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3356.6826\SolidWorks_Flexnet_Server\sw_d_SSQ.lic | text | |
MD5:6C965362C44B0C4E62D83E68803EB877 | SHA256:AB3D70A082B2F14F9B1BE48CC35C3093E420D1440418C93C32D9436EAF44A65E | |||
| 3356 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3356.6826\SolidWorks_Flexnet_Server\server_remove.bat | text | |
MD5:950D94840CD6B889A8A9ED1FE93FF73B | SHA256:8B0B95E49330C8FC517061AB420E0DA66555A20A270AD88835EEA05A591AF04E | |||
| 3356 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3356.6826\Program Files\SOLIDWORKS Corp\SOLIDWORKS Electrical\bin\netapi32.dll | executable | |
MD5:69559DEA95FB75855D47B07682D709B2 | SHA256:06F5830CFC6284CC1FE5FD3EAEA98B35C61760EC9DDA023C2BDD235DC88F7D84 | |||
| 3356 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3356.6826\Program Files\SOLIDWORKS Corp\SOLIDWORKS Composer\Bin\netapi32.dll | executable | |
MD5:69559DEA95FB75855D47B07682D709B2 | SHA256:06F5830CFC6284CC1FE5FD3EAEA98B35C61760EC9DDA023C2BDD235DC88F7D84 | |||
| 3356 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3356.6826\Program Files\SOLIDWORKS Corp\SOLIDWORKS CAM\setup\i386\netapi32.dll | executable | |
MD5:69559DEA95FB75855D47B07682D709B2 | SHA256:06F5830CFC6284CC1FE5FD3EAEA98B35C61760EC9DDA023C2BDD235DC88F7D84 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report