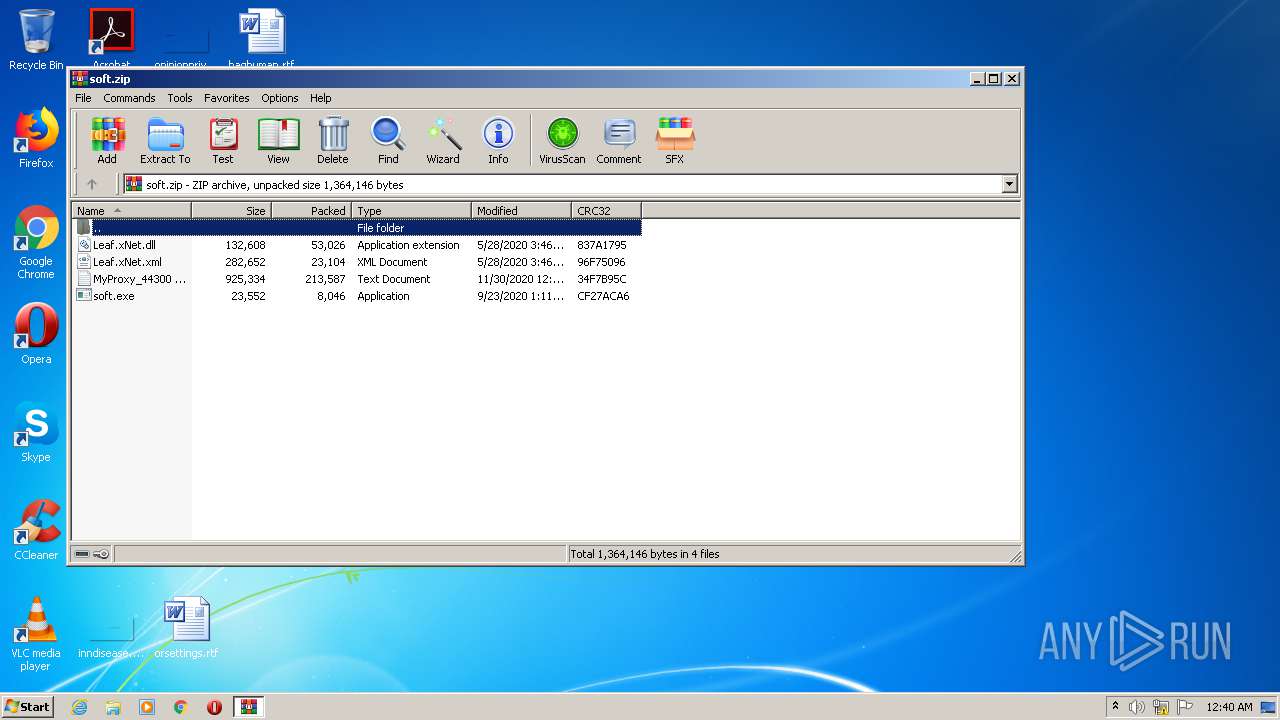
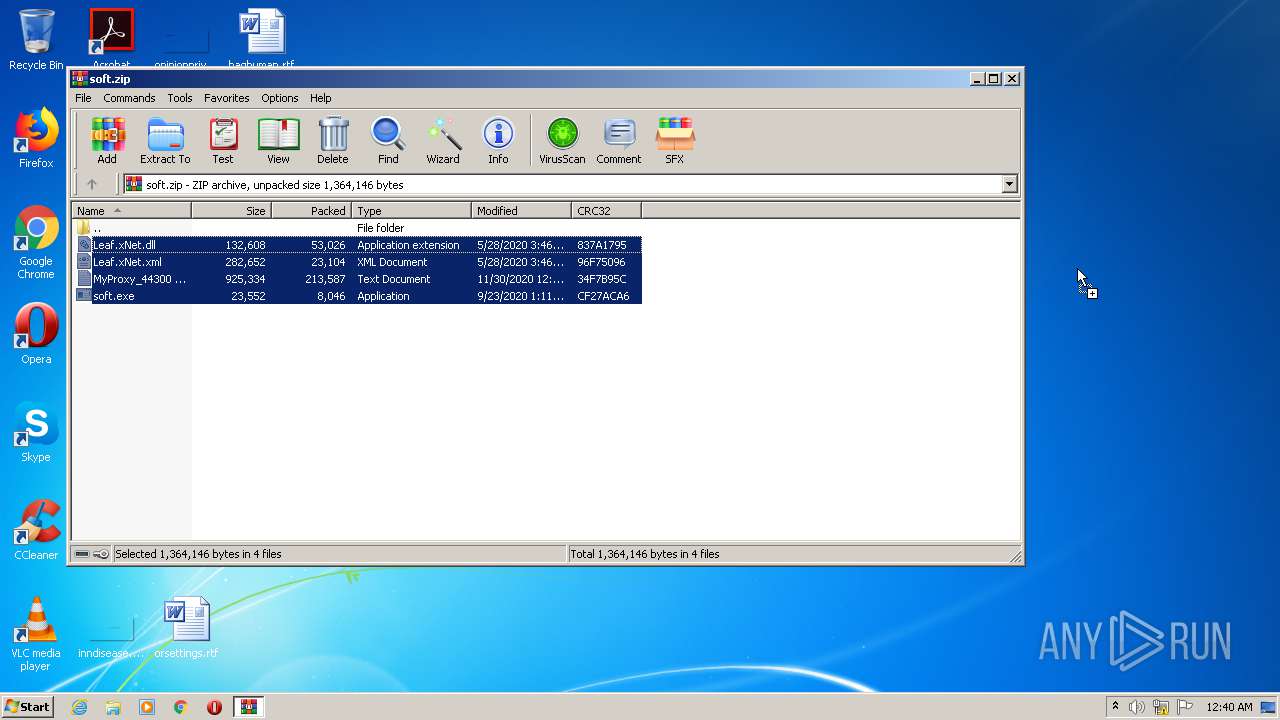
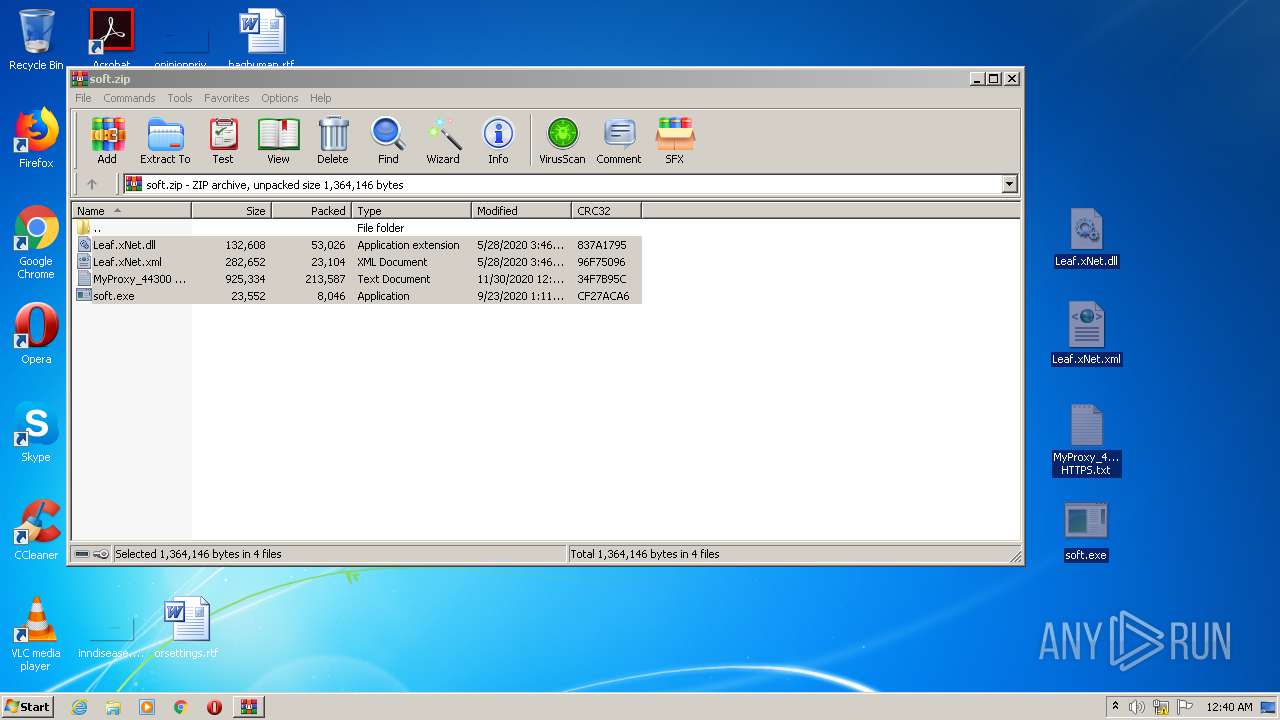
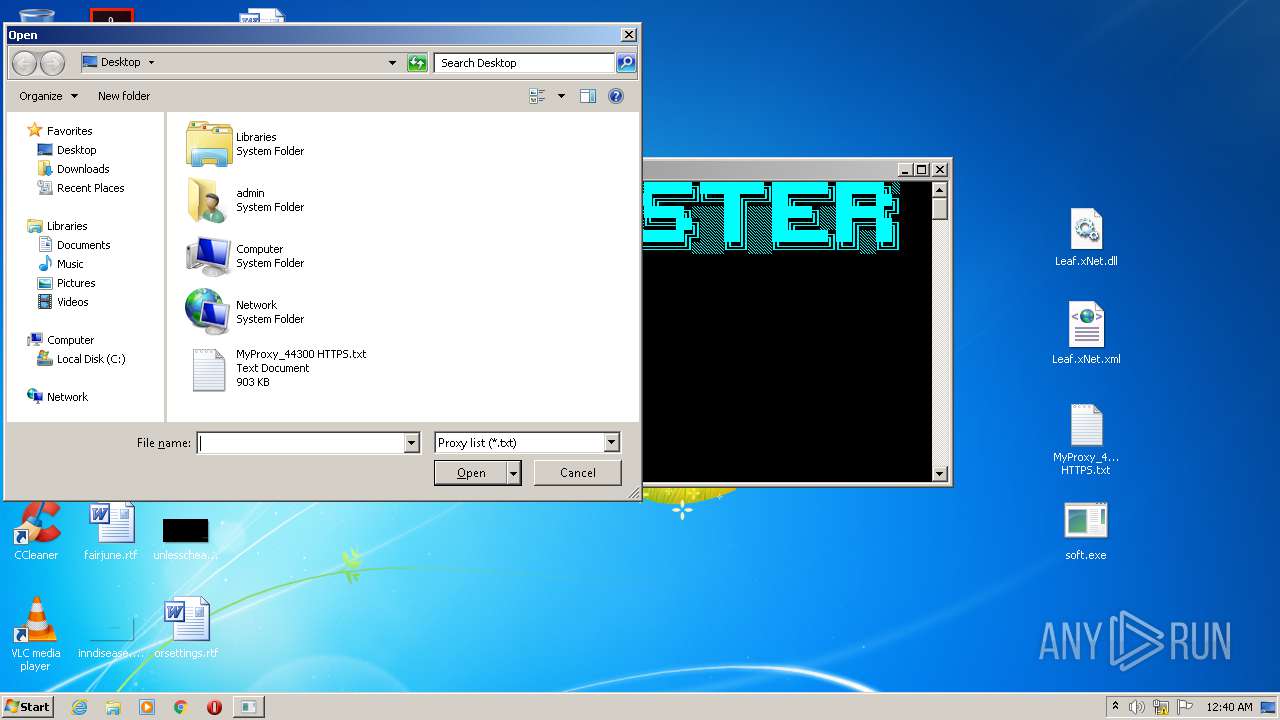
| File name: | soft.zip |
| Full analysis: | https://app.any.run/tasks/f9601416-e771-4135-b1d4-ade7ce513154 |
| Verdict: | Malicious activity |
| Analysis date: | November 30, 2020, 00:39:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 46BCD115D5CD7DDF16E110D98C412B8F |
| SHA1: | A7D40C473130F7D382130C8BF8E90BDD6331A5EF |
| SHA256: | 984CEA30B2B4885258E9BE925283A0E4665A8D454992EB8655465E3929B38154 |
| SSDEEP: | 6144:1nVr9TELeBVT/a7FHHrN5HueRQ0hG6jCjBLqLnlReL4jiUKsahNqZLV:1l9TELSKtrN5OeRQF1jMlReLqiUKsaab |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3448)
- soft.exe (PID: 3324)
Application was dropped or rewritten from another process
- soft.exe (PID: 3324)
SUSPICIOUS
No suspicious indicators.INFO
Manual execution by user
- soft.exe (PID: 3324)
Reads settings of System Certificates
- soft.exe (PID: 3324)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:05:28 17:46:02 |
| ZipCRC: | 0x837a1795 |
| ZipCompressedSize: | 53026 |
| ZipUncompressedSize: | 132608 |
| ZipFileName: | Leaf.xNet.dll |
Total processes
37
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1252 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\soft.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
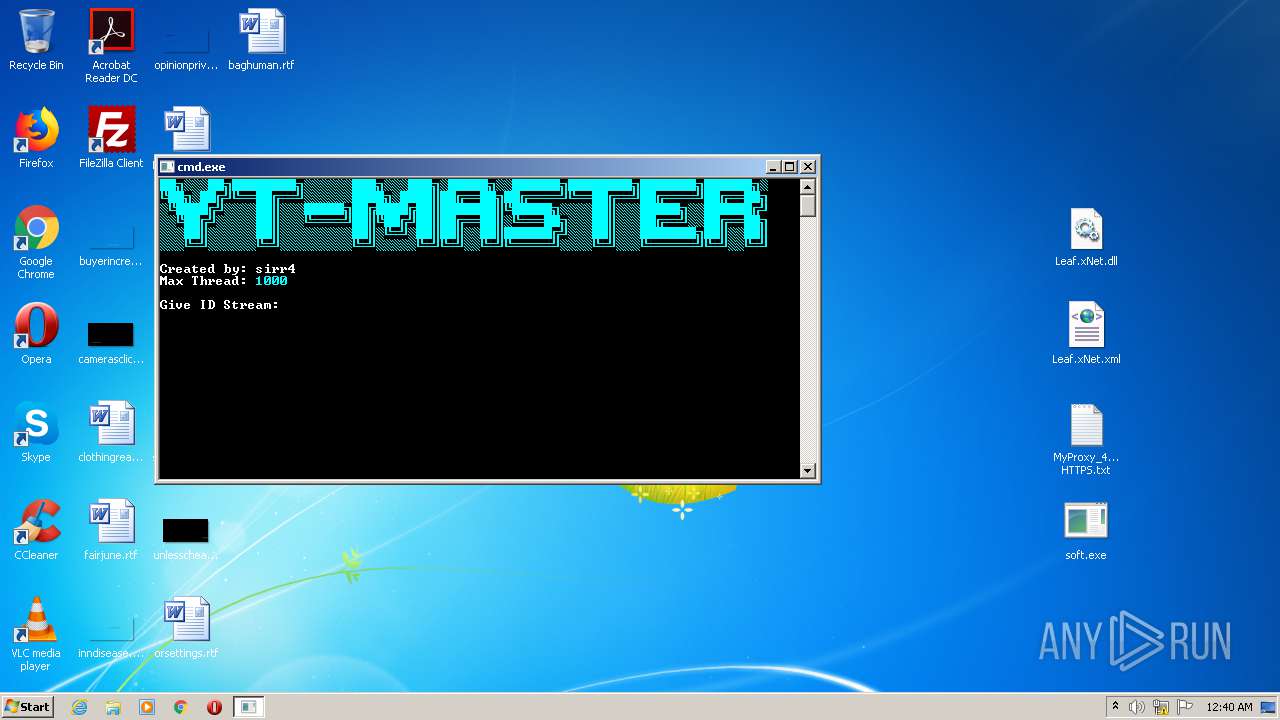
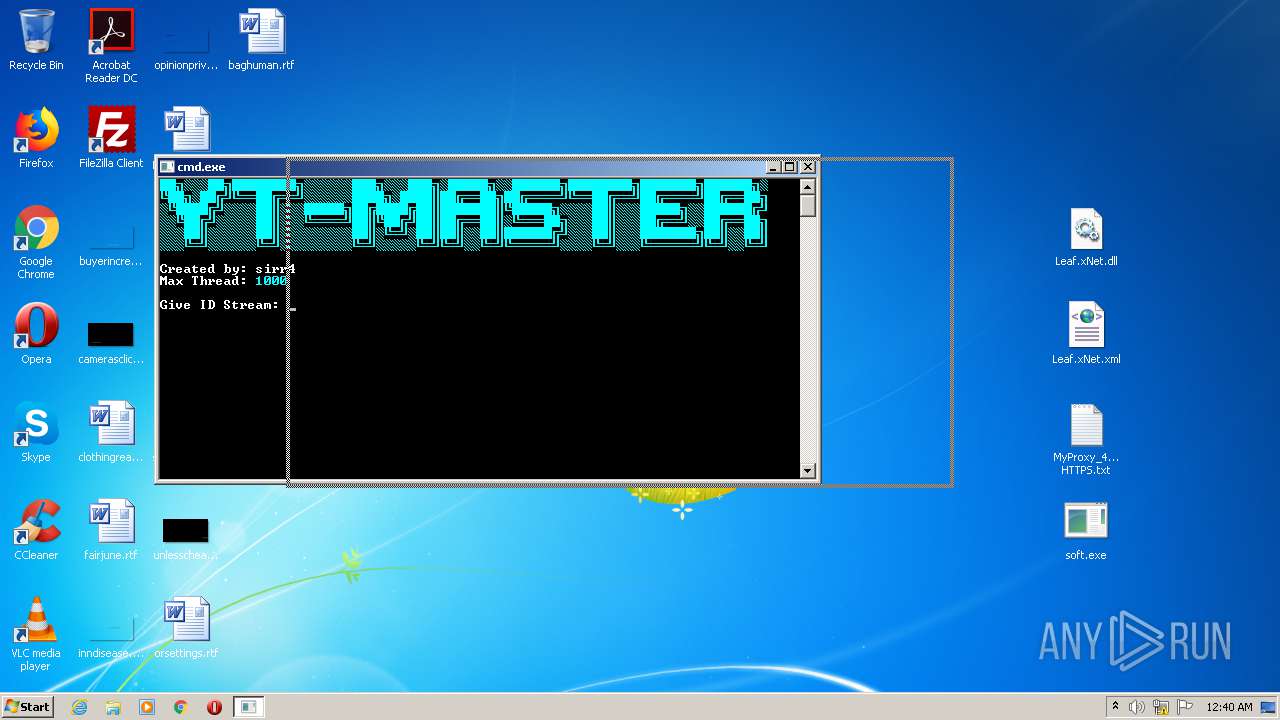
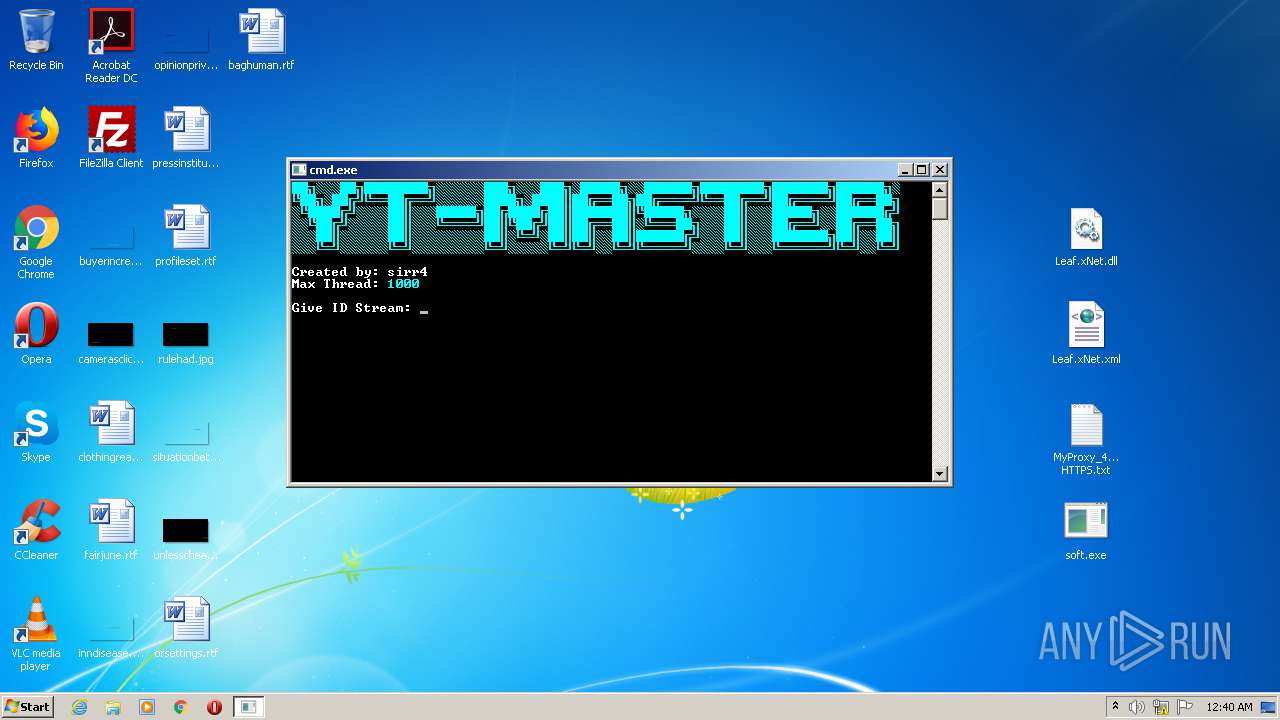
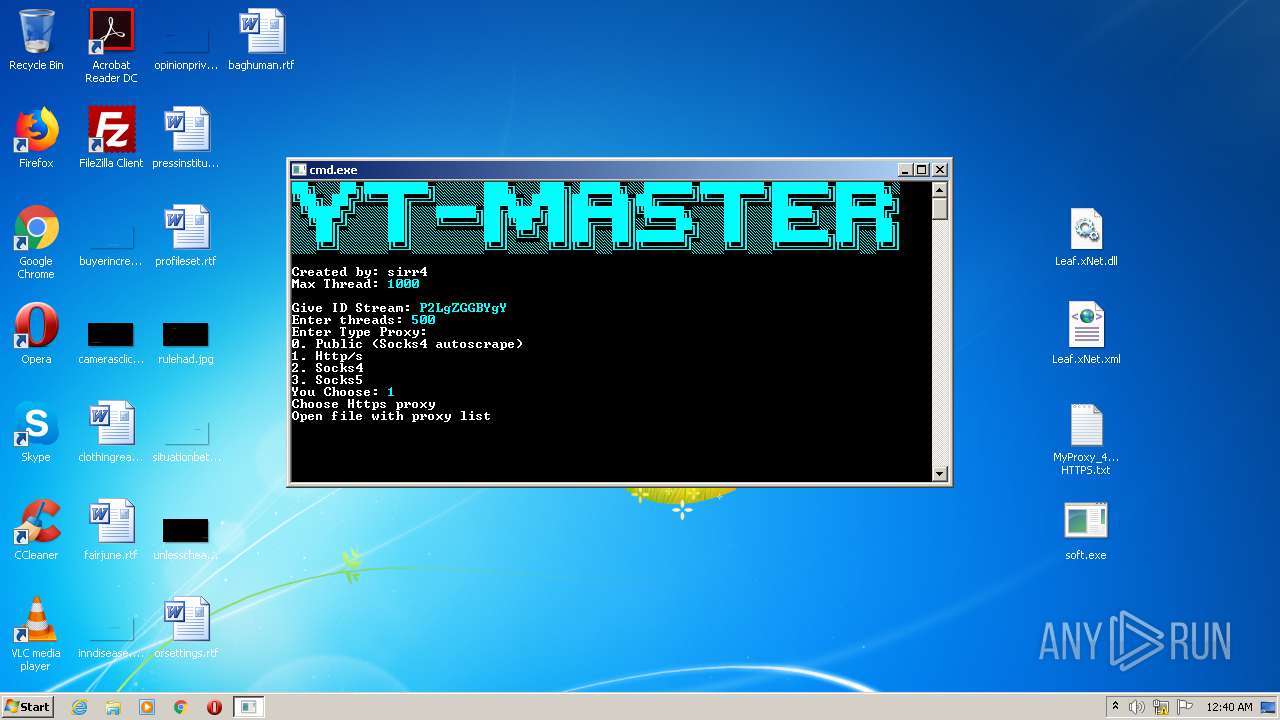
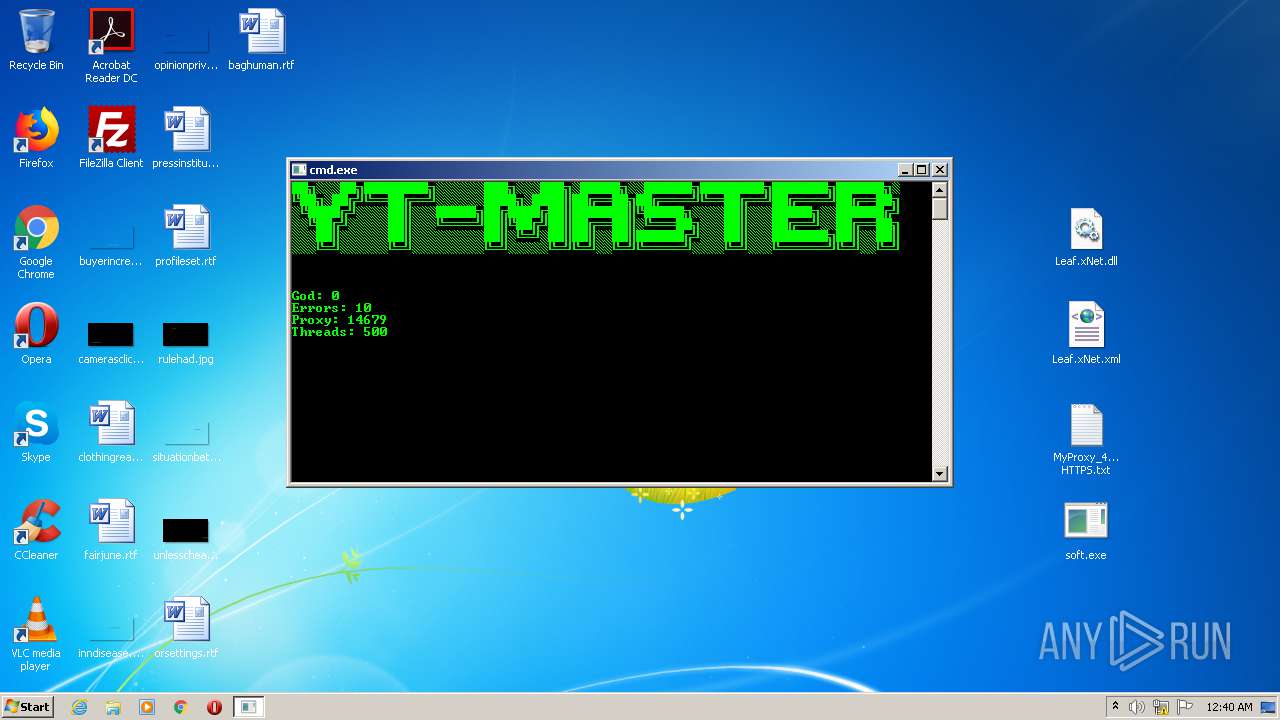
| 3324 | "C:\Users\admin\Desktop\soft.exe" | C:\Users\admin\Desktop\soft.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Youtube-Viewers Exit code: 3221225786 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3448 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe5_ Global\UsGthrCtrlFltPipeMssGthrPipe5 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 001
Read events
924
Write events
76
Delete events
1
Modification events
| (PID) Process: | (1252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1252) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\soft.zip | |||
| (PID) Process: | (1252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1252) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\msxml3r.dll,-1 |
Value: XML Document | |||
| (PID) Process: | (3448) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1252 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1252.13253\Leaf.xNet.dll | — | |
MD5:— | SHA256:— | |||
| 1252 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1252.13253\Leaf.xNet.xml | — | |
MD5:— | SHA256:— | |||
| 1252 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1252.13253\MyProxy_44300 HTTPS.txt | — | |
MD5:— | SHA256:— | |||
| 1252 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1252.13253\soft.exe | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
719
TCP/UDP connections
1 680
DNS requests
0
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3324 | soft.exe | CONNECT | — | 182.71.146.148:8080 | http://m.youtube.com:8080m.youtube.com:443 | IN | — | — | suspicious |
3324 | soft.exe | CONNECT | — | 103.134.213.50:8080 | http://m.youtube.com:8080m.youtube.com:443 | unknown | — | — | unknown |
3324 | soft.exe | CONNECT | — | 186.47.82.138:8080 | http://m.youtube.com:8080m.youtube.com:443 | EC | — | — | unknown |
3324 | soft.exe | CONNECT | — | 143.137.204.6:80 | http://m.youtube.comm.youtube.com:443 | BR | — | — | suspicious |
3324 | soft.exe | CONNECT | — | 175.184.232.74:8080 | http://m.youtube.com:8080m.youtube.com:443 | ID | — | — | suspicious |
3324 | soft.exe | CONNECT | — | 165.16.77.49:8080 | http://m.youtube.com:8080m.youtube.com:443 | LY | — | — | unknown |
3324 | soft.exe | CONNECT | — | 103.112.163.245:8080 | http://m.youtube.com:8080m.youtube.com:443 | unknown | — | — | unknown |
3324 | soft.exe | CONNECT | — | 107.150.22.210:8080 | http://m.youtube.com:8080m.youtube.com:443 | US | — | — | unknown |
3324 | soft.exe | CONNECT | — | 178.250.92.18:8080 | http://m.youtube.com:8080m.youtube.com:443 | TR | — | — | unknown |
3324 | soft.exe | CONNECT | — | 103.123.246.66:8080 | http://m.youtube.com:8080m.youtube.com:443 | unknown | — | — | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3324 | soft.exe | 111.93.59.130:3129 | — | Tata Teleservices ISP AS | IN | unknown |
3324 | soft.exe | 182.53.206.26:45336 | — | TOT Public Company Limited | TH | suspicious |
3324 | soft.exe | 103.78.213.226:45163 | — | — | ID | suspicious |
3324 | soft.exe | 121.101.191.190:63141 | — | PT. BORNEO BROADBAND TECHNOLOGY | ID | unknown |
3324 | soft.exe | 103.4.145.237:8080 | — | Next Online Limited | BD | suspicious |
3324 | soft.exe | 190.6.200.158:38256 | — | CABLECOLOR S.A. | HN | suspicious |
3324 | soft.exe | 103.123.246.66:8080 | — | — | — | suspicious |
3324 | soft.exe | 138.219.251.5:3128 | — | Coop de Prov.Serv.Telef.Obras y Serv Púb y Soc Virrey del Pino Ltda | AR | unknown |
3324 | soft.exe | 134.0.63.134:8000 | — | Agjencia Kombetare Shoqerise se Informacionit | AL | suspicious |
3324 | soft.exe | 118.96.150.115:8080 | — | PT Telekomunikasi Indonesia | ID | unknown |
DNS requests
Threats
PID | Process | Class | Message |
|---|---|---|---|
3324 | soft.exe | Generic Protocol Command Decode | SURICATA STREAM suspected RST injection |
3324 | soft.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |
3324 | soft.exe | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (CONNECT) |
3324 | soft.exe | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (CONNECT) |