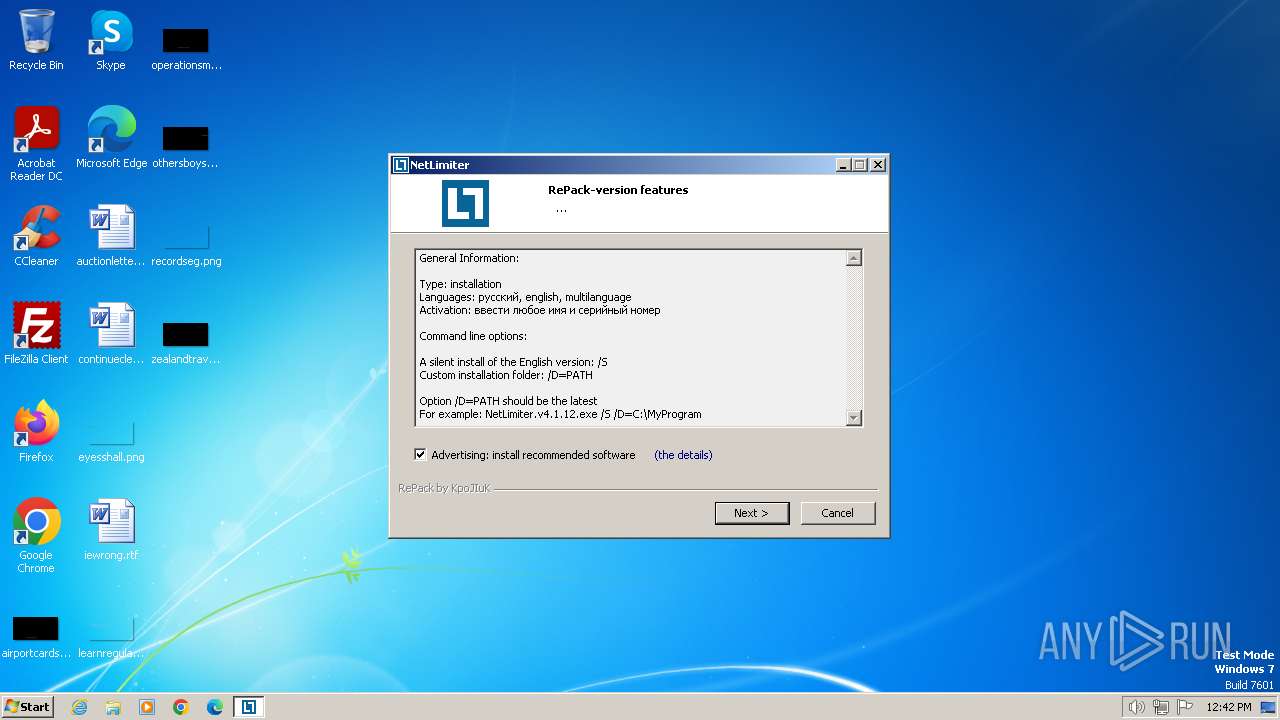
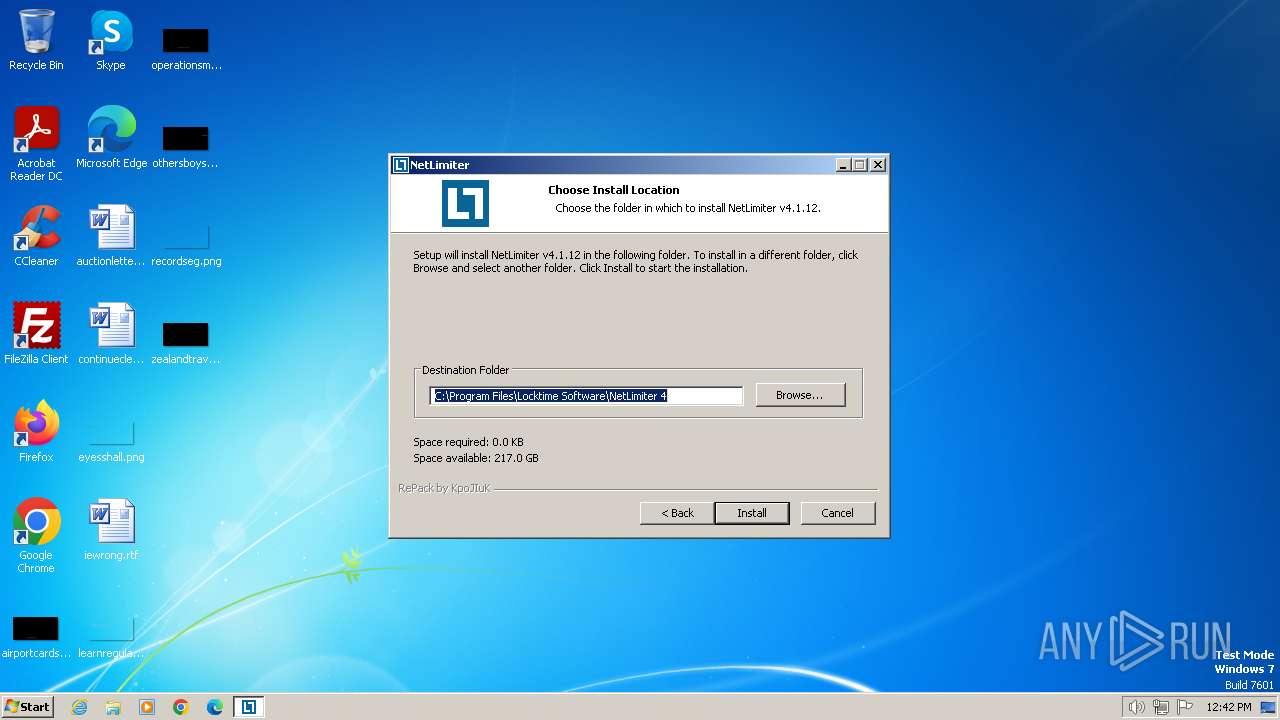
| File name: | NetLimiter.v4.1.12.exe |
| Full analysis: | https://app.any.run/tasks/78be95d2-8ec8-4c58-95f6-f9eff87aa229 |
| Verdict: | Malicious activity |
| Analysis date: | March 16, 2024, 12:41:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 1DF06318EF20C35FECB1D440D2BFB3AC |
| SHA1: | 2E95D67219CB022BA9CBE2D6E778209C7812E116 |
| SHA256: | 984B9B1398E556178AAE9366701CC3E44ECCFCE85EC34B89B246A4349EBCCF41 |
| SSDEEP: | 98304:piDNvhKUua7V4RqwhfWGwKNOutotPGHlUQYYjsv3F+27I9cNiLFq3n/l/9NSQLEM:l3ZkmQbR |
MALICIOUS
Drops the executable file immediately after the start
- NetLimiter.v4.1.12.exe (PID: 3392)
Creates a writable file in the system directory
- NLSvc.exe (PID: 1020)
- NLSvc.exe (PID: 3152)
SUSPICIOUS
Executable content was dropped or overwritten
- NetLimiter.v4.1.12.exe (PID: 3392)
Starts application with an unusual extension
- NetLimiter.v4.1.12.exe (PID: 3392)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- ns225B.tmp (PID: 2408)
Uses ROUTE.EXE to obtain the routing table information
- ns2346.tmp (PID: 696)
Drops 7-zip archiver for unpacking
- NetLimiter.v4.1.12.exe (PID: 3392)
Process drops legitimate windows executable
- NetLimiter.v4.1.12.exe (PID: 3392)
Drops a system driver (possible attempt to evade defenses)
- NetLimiter.v4.1.12.exe (PID: 3392)
The process creates files with name similar to system file names
- NetLimiter.v4.1.12.exe (PID: 3392)
Malware-specific behavior (creating "System.dll" in Temp)
- NetLimiter.v4.1.12.exe (PID: 3392)
Executes as Windows Service
- VSSVC.exe (PID: 2432)
- NLSvc.exe (PID: 1020)
- NLSvc.exe (PID: 3152)
Checks Windows Trust Settings
- NLSvc.exe (PID: 3152)
- NLSvc.exe (PID: 1020)
- NLClientApp.exe (PID: 3544)
Reads security settings of Internet Explorer
- NLSvc.exe (PID: 1020)
- NLSvc.exe (PID: 3152)
- NLClientApp.exe (PID: 3544)
- NetLimiter.v4.1.12.exe (PID: 3392)
Reads the Internet Settings
- NetLimiter.v4.1.12.exe (PID: 3392)
- NLClientApp.exe (PID: 3544)
Reads settings of System Certificates
- NLClientApp.exe (PID: 3544)
Identifying current user with WHOAMI command
- cmd.exe (PID: 3844)
INFO
Reads the computer name
- NetLimiter.v4.1.12.exe (PID: 3392)
- NLSvc.exe (PID: 3152)
- NLClientApp.exe (PID: 3544)
- NLSvc.exe (PID: 1020)
Checks supported languages
- NetLimiter.v4.1.12.exe (PID: 3392)
- ns225B.tmp (PID: 2408)
- ns2346.tmp (PID: 696)
- ns79B4.tmp (PID: 1888)
- NLSvc.exe (PID: 1020)
- NLSvc.exe (PID: 3152)
- NLClientApp.exe (PID: 3544)
- NLSvcCliCnnCheck.exe (PID: 1848)
Create files in a temporary directory
- NetLimiter.v4.1.12.exe (PID: 3392)
- NLClientApp.exe (PID: 3544)
Reads the machine GUID from the registry
- NLSvc.exe (PID: 3152)
- NLSvc.exe (PID: 1020)
- NLClientApp.exe (PID: 3544)
- NetLimiter.v4.1.12.exe (PID: 3392)
Reads the software policy settings
- NLSvc.exe (PID: 3152)
- NLSvc.exe (PID: 1020)
- NLClientApp.exe (PID: 3544)
Creates files in the program directory
- NLSvc.exe (PID: 3152)
Checks proxy server information
- NetLimiter.v4.1.12.exe (PID: 3392)
Manual execution by a user
- taskmgr.exe (PID: 1216)
- explorer.exe (PID: 3336)
- cmd.exe (PID: 3844)
- NLClientApp.exe (PID: 3544)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:12:16 00:54:10+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26112 |
| InitializedDataSize: | 428544 |
| UninitializedDataSize: | 16384 |
| EntryPoint: | 0x350d |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.1.12.0 |
| ProductVersionNumber: | 4.1.12.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | Locktime Software |
| FileDescription: | NetLimiter v4.1.12 |
| FileVersion: | 4.1.12.0 |
| LegalCopyright: | © Locktime Software |
| ProductName: | NetLimiter v4.1.12 |
Total processes
85
Monitored processes
17
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 324 | whoami | C:\Windows\System32\whoami.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: whoami - displays logged on user information Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 696 | "C:\Users\admin\AppData\Local\Temp\nsn221B.tmp\ns2346.tmp" route.exe delete 95.141.193.133 | C:\Users\admin\AppData\Local\Temp\nsn221B.tmp\ns2346.tmp | — | NetLimiter.v4.1.12.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1020 | "C:\Program Files\Locktime Software\NetLimiter 4\NLSvc.exe" | C:\Program Files\Locktime Software\NetLimiter 4\NLSvc.exe | services.exe | ||||||||||||
User: SYSTEM Company: Locktime Software Integrity Level: SYSTEM Description: NLSvc Exit code: 0 Version: 4.1.12.0 Modules
| |||||||||||||||
| 1216 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\System32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1848 | "C:\Program Files\Locktime Software\NetLimiter 4\NLSvcCliCnnCheck.exe" 2f5962515e164c1faabd5211e136f9ec | C:\Program Files\Locktime Software\NetLimiter 4\NLSvcCliCnnCheck.exe | — | NLClientApp.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Modules
| |||||||||||||||
| 1888 | "C:\Users\admin\AppData\Local\Temp\nsn221B.tmp\ns79B4.tmp" msiexec.exe /I "C:\Users\admin\AppData\Local\Temp\NETLIMITER\x86.msi" /qb APPDIR="C:\Program Files\Locktime Software\NetLimiter 4\" | C:\Users\admin\AppData\Local\Temp\nsn221B.tmp\ns79B4.tmp | — | NetLimiter.v4.1.12.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1992 | msiexec.exe /I "C:\Users\admin\AppData\Local\Temp\NETLIMITER\x86.msi" /qb APPDIR="C:\Program Files\Locktime Software\NetLimiter 4\" | C:\Windows\System32\msiexec.exe | — | ns79B4.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2408 | "C:\Users\admin\AppData\Local\Temp\nsn221B.tmp\ns225B.tmp" netsh.exe advfirewall firewall delete rule name="all" remoteip=95.141.193.133 | C:\Users\admin\AppData\Local\Temp\nsn221B.tmp\ns225B.tmp | — | NetLimiter.v4.1.12.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 2432 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2440 | route.exe delete 95.141.193.133 | C:\Windows\System32\ROUTE.EXE | — | ns2346.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Route Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
16 599
Read events
16 311
Write events
266
Delete events
22
Modification events
| (PID) Process: | (2672) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2672) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dhcpqec.dll,-100 |
Value: DHCP Quarantine Enforcement Client | |||
| (PID) Process: | (2672) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dhcpqec.dll,-101 |
Value: Provides DHCP based enforcement for NAP | |||
| (PID) Process: | (2672) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dhcpqec.dll,-103 |
Value: 1.0 | |||
| (PID) Process: | (2672) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dhcpqec.dll,-102 |
Value: Microsoft Corporation | |||
| (PID) Process: | (2672) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\napipsec.dll,-1 |
Value: IPsec Relying Party | |||
| (PID) Process: | (2672) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\napipsec.dll,-2 |
Value: Provides IPsec based enforcement for Network Access Protection | |||
| (PID) Process: | (2672) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\napipsec.dll,-4 |
Value: 1.0 | |||
| (PID) Process: | (2672) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\napipsec.dll,-3 |
Value: Microsoft Corporation | |||
| (PID) Process: | (2672) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\tsgqec.dll,-100 |
Value: RD Gateway Quarantine Enforcement Client | |||
Executable files
96
Suspicious files
6
Text files
10
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3392 | NetLimiter.v4.1.12.exe | C:\Users\admin\AppData\Local\Temp\nsn221B.tmp\PACKAGE.pkg | compressed | |
MD5:7CE9BE9257C9534FF7AE6B4683E13F2D | SHA256:36E5F8F6010A945CDC73AA6F41D2CA4C28B01D6160D5BCCA0679EAE7A0897F13 | |||
| 3392 | NetLimiter.v4.1.12.exe | C:\Users\admin\AppData\Local\Temp\nsn221B.tmp\ns225B.tmp | executable | |
MD5:F27689C513E7D12C7C974D5F8EF710D6 | SHA256:1F18F4126124B0551F3DBCD0FEC7F34026F930CA509F04435657CEDC32AE8C47 | |||
| 3392 | NetLimiter.v4.1.12.exe | C:\Users\admin\AppData\Local\Temp\nsn221B.tmp\nsExec.dll | executable | |
MD5:F27689C513E7D12C7C974D5F8EF710D6 | SHA256:1F18F4126124B0551F3DBCD0FEC7F34026F930CA509F04435657CEDC32AE8C47 | |||
| 3392 | NetLimiter.v4.1.12.exe | C:\Users\admin\AppData\Local\Temp\nsn221B.tmp\LangDLL.dll | executable | |
MD5:109B201717AB5EF9B5628A9F3EFEF36F | SHA256:20E642707EF82852BCF153254CB94B629B93EE89A8E8A03F838EEF6CBB493319 | |||
| 3392 | NetLimiter.v4.1.12.exe | C:\Users\admin\AppData\Local\Temp\nsn221B.tmp\nsis7z.dll | executable | |
MD5:80E44CE4895304C6A3A831310FBF8CD0 | SHA256:B393F05E8FF919EF071181050E1873C9A776E1A0AE8329AEFFF7007D0CADF592 | |||
| 3392 | NetLimiter.v4.1.12.exe | C:\Users\admin\AppData\Local\Temp\NETLIMITER\lang_list.ini | text | |
MD5:D5F69B39569FE29112109402A4E78165 | SHA256:3374FDC9E95F794657002A6027230834E2487667224A6AA2E3A6036FCFD129E5 | |||
| 3392 | NetLimiter.v4.1.12.exe | C:\Users\admin\AppData\Local\Temp\NETLIMITER\x64.msi | executable | |
MD5:935930895CDBDA917B89B6D54685E069 | SHA256:791E232E2BE22B9FD1FA92EABF41C7DE65FF5DFCCF33CA7E9F618916060E4628 | |||
| 3392 | NetLimiter.v4.1.12.exe | C:\Users\admin\AppData\Local\Temp\NETLIMITER\x86.msi | executable | |
MD5:F8CC40EB9D71E3C60CF3596AE7CE4B22 | SHA256:B61EA011975FACC0B47AE326A625F9C494669587E48E1232BAE91F7513777214 | |||
| 3392 | NetLimiter.v4.1.12.exe | C:\Users\admin\AppData\Local\Temp\NETLIMITER\ports.bin | binary | |
MD5:EA74B57F1B0BBA882AE8F3858CA29FD1 | SHA256:D829283BA6495E69949D24B14F66B0D427C13F849A6B8CD6D44D11636BA60FA1 | |||
| 3392 | NetLimiter.v4.1.12.exe | C:\Users\admin\AppData\Local\Temp\NETLIMITER\x86\NLDiag.exe.config | xml | |
MD5:9070D769FD43FB9DEF7E9954FBA4C033 | SHA256:CBAF2AE95B1133026C58AB6362AF2F7FB2A1871D7AD58B87BD73137598228D9B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
21
DNS requests
13
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1020 | NLSvc.exe | GET | 304 | 2.16.100.155:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?65f8ab8788187727 | unknown | — | — | unknown |
1020 | NLSvc.exe | GET | 200 | 104.18.21.226:80 | http://crl.globalsign.com/root-r3.crl | unknown | binary | 2.01 Kb | unknown |
3152 | NLSvc.exe | GET | 200 | 104.18.21.226:80 | http://crl.globalsign.com/gsextendcodesignsha2g3.crl | unknown | binary | 4.49 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1020 | NLSvc.exe | 2.16.100.168:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | whitelisted |
1020 | NLSvc.exe | 104.18.21.226:80 | ocsp2.globalsign.com | CLOUDFLARENET | — | shared |
1020 | NLSvc.exe | 2.16.100.155:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | whitelisted |
3152 | NLSvc.exe | 173.222.108.147:80 | ctldl.windowsupdate.com | Akamai International B.V. | CH | unknown |
3152 | NLSvc.exe | 104.18.21.226:80 | ocsp2.globalsign.com | CLOUDFLARENET | — | shared |
3152 | NLSvc.exe | 173.222.108.243:80 | ctldl.windowsupdate.com | Akamai International B.V. | CH | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
ocsp2.globalsign.com |
| whitelisted |
dns.msftncsi.com |
| shared |
crl.globalsign.com |
| whitelisted |
ad-repack.ddns.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |